Abstract
With the rapid development of edge computing and the Internet of Things, the problem of information resource sharing can be effectively solved through multi-party collaboration, but the risk of data leakage is also increasing. To address the above issues, we propose an efficient multi-party private set intersection (MPSI) protocol via a multi-point oblivious pseudorandom function (OPRF). Then, we apply it to work on a specific commercial application: edge caching. The proposed MPSI uses oblivious transfer (OT) together with a probe-and-XOR of strings (PaXoS) as the main building blocks. It not only provides one-sided malicious security, but also achieves a better balance between communication and computational overhead. From the communication pattern perspective, the client only needs to perform OT with the leader and send a data structure PaXoS to the designated party, making the protocol extremely efficient. Moreover, in the setting of edge caching, many parties hold a set of items containing an identity and its associated value. All parties can identify a set of the most frequently accessed common items without revealing the underlying data.
1. Introduction
Co-creation and sharing gained significance in the transition from the era of information technology to the era of digital technology. While information sharing brings convenience, the risk of privacy breaches also rises. The private set intersection (PSI) protocol is a widely used approach to distributed set computation. It is devoted to the joint intersection calculation of data from two or more parties. The PSI protocol guarantees that all parties can collaboratively calculate the intersection of the sets without disclosing anything beyond that intersection. PSI plays an important role in improving pattern matching [1], private contact discovery [2], advertisement conversion rate [3], and edge caching [4]. Edge caching is a key technology for communication networks. In order to utilize cache resources more efficiently, individual operators tend to keep their public items in a shared cache that can be accessed by all parties. However, since the cache is shared among multiple parties, these parties aim to identify the set of most frequently visited common data items and add them to the network edge cache. Their objective is to achieve this without revealing the actual underlying data. This is known as the multi-party shared cache problem, where determining the common term is a typical private set intersection problem.
Most of the current efficient PSI protocols are built on OT [5,6,7]. The OT-based PSI protocols offer greater advantages in terms of communication and computation when compared with PSI based on public key encryption [8,9] and PSI based on a garbled circuit [10,11,12]. Efficient OT extension techniques allow parties to generate many OT protocol instances at a low computational cost through a few public key operations. Chase et al. [5] implemented a two-party PSI protocol with one-sided malicious security. This protocol uses OT and a multi-point OPRF to achieve a good balance between computational and communication overhead. The protocol can only interact between two parties, and multiple runs are required to accomplish the intersection computation with multiple parties involved. Kavousi et al. [13] proposed a MPSI based on OT and multi-point OPRF. This protocol can only be implemented in the semi-honest model. Inbar et al. [14] presented an enhanced semi-honest MPSI protocol based on OT and a garbled Bloom filter (GBF). However, the protocols [13,14] require the transmission of the GBF for communication, creating a certain degree of communication burden.
In response to the above issues, we constructed an MPSI protocol for malicious actors that combines a PaXoS and multi-point OPRF based on OT. The protocol relies only on symmetric keys, hashing, coding techniques, and bitwise operations, thus providing good computational performance. This protocol can solve the problem of privacy-preserving edge cooperative cache sharing by making a simple transformation of this protocol. We show the following contributions:
- Multi-party PSI protocol: We propose a specifically efficient MPSI protocol utilizing OT and a PaXoS. The PaXoS can be seen as a corresponding Encode/Decode algorithm achieving a constant rate. Therefore, our protocol has good computational performance. The protocol has low communication overhead since the clients only need to send a data structure. Theoretical analysis shows that the protocol leads to a better balance between communication and computational cost.
- Security against malicious clients: We present that our protocol uses the data structure PaXoS to hide the key during encoding to resist malicious adversaries, which can achieve one-sided malicious security against the clients with almost no additional overhead. At the same time, we prove that the protocol can also resist any possible collusion attack from malicious clients.
- Multi-party cooperative cache: Our MPSI protocol can be applied to edge caching scenarios by using cuckoo hashing and simple hashing. The protocol supports having data associated with each input and the extension of payloads to multi-party. In a multi-party cooperative cache (MPCCache) setting, the MPCCache protocol allows parties to compute a sum depending on the data associated with the intersection items. Compared with [4], our MPCCache protocol eliminates the computing burden associated with polynomial interpolation and improves computational efficiency.
2. Related Work
PSI. The development of efficient constructions for PSI functionality has received considerable research attention in the last decade or more. Some of the recent relevant works on PSI are illustrated in Table 1. Ghosh et al. [15] presented a MPSI protocol using oblivious linear function evaluation (OLE) with optimal asymptotic communication complexity. However, the balance between communication and computation cost is not good. Kolesniko [16] proposed a two-party PSI protocol against semi-honest adversaries. The protocol is mainly based on OT techniques for security string equivalence testing and is computationally efficient. Pinkas [17] proposed a two-party semi-honest PSI protocol based on OT and a GBF. The parallelized processing of the protocol allows for some improvement in protocol efficiency. Nevo [18] proposed a malicious PSI protocol utilizing oblivious programmable PRF (OPPRF) and oblivious key-value store (OKVS) technology, which solves the problem of multi-party PSI against malicious adversaries. However, this protocol does not lead to a better trade-off between communication and computational overhead. Pinkas [19] also proposed a PSI protocol for two parties in the malicious model which uses a PaXoS to implement, for the first time, a malicious secure PSI using cuckoo hashing. Ben-Efraim et al. [20] implemented malicious MPSI based on a GBF for multiple parties. However, GBFs suffer from a certain false positive rate and their high communication overhead. Bui et al. [21] constructed an optimized semi-honest PSI based on a pseudorandom correlation generator (PCG). Additionally, they can use the PCG to construct protocols with fully malicious security in the standard model.

Table 1.
The related work of PSI.
Function-based PSI. Many studies have focused on developing efficient techniques for PSI construction. In addition, these studies have explored the output results of computing a function over intersections, allowing for potential extensions to various business scenarios. Table 2 shows recent related works on function-based PSI. Ion et al. [3] proposed a PI-Sum Protocol utilizing Diffie–Hellman (DDH) and homomorphic encryption (HE). Thinking about the advertising (Ad) conversion problem: Ad providers want to analyze Ad effectiveness by age, which obviously cannot be solved using the PI-Sum. Chida [22] proposed a new function based on OPRF and DDH assumptions to calculate the weighted sum of two-party privacy sets (PIW-sum), which has more practical application value. Pinkas et al. [11] proposed an idea of calculating payloads based on the circuit, OPPRF, and cuckoo hash constructs, which allows each input item from one party to have payload data attached to it, and finally to calculate some specific functions of the payloads in the intersection set. Based on a new shuffled distributed oblivious PRF (DOPRF), Miao et al. [23] constructed a two-party PSI cardinality (PSI-CA) protocol for malicious settings which achieves a good computation and communication cost. In the above protocols, only one party can own the payload data, which can be applied in limited practical scenarios. Nguyen et al. [4] extended payload data to the multi-party setting and proposed an MPCCache sharing framework based on polynomial interpolation and OPPRF, which enables multiple parties to calculate a sum of data payloads on each of common data items and can identify the most frequently accessed data items.

Table 2.
The related work of function-based PSI.
3. Preliminaries
3.1. Notions
The computational and statistical security parameters are denoted by and . stands in for the set . indicates uniformly random selection. The notation denotes concatenation between strings. denotes the set of strings consisting of 0 and 1, where * means that the strings in the set can be of any length. We use to indicate that the real world is indistinguishable from the ideal world. We denote with the i-th element of a vector of length . The i-th column vector of the matrix is denoted by the symbol . The Hamming weight of the binary string is represented by .
3.2. One-Sided Malicious Security
One-sided malicious security [5] is a security property found in cryptographic protocols wherein one party is allowed to engage in arbitrary malicious behavior in an attempt to compromise security while the other parties follow specified behavioral guidelines. In this context, only the targeted party is vulnerable to malicious action, whereas the other parties maintain their assigned roles and responsibilities. Our MPSI protocol achieves unilateral malicious security against the clients, as they are considered as a whole. We further prove that the proposed MPSI is secure against malicious clients.
3.3. Security Model
MPSI is a unique instance of secure multi-party computation (MPC). We adhere to the MPC standard security definition. The ideal functionality of MPSI is defined in Figure 1.

Figure 1.
Ideal functionality of MPSI .
The security models [24] of secure multi-party computation are divided into semi-honest and malicious models. For the semi-honest model, an adversary can completely obey the protocol execution process, yet might record all the data in the protocol execution process and try to learn more from the data generated during the protocol execution process. The adversary under the malicious model can not only infer the sensitive information through the data of the protocol process but also refuse to participate in the protocol, alter the private input set information, or prematurely stop the protocol from running. Our protocol can achieve one-sided malicious security.
Definition 1.
(Malicious security against the clients) If there is a PPT adversary who might unilaterally depart from the protocol in the real world, there exists a PPT adversary who could modify the input to the ideal functionality and terminate the output in an ideal world. Then, the protocol Π can protect from malicious clients, such that for each input :
3.4. Oblivious Transfer
Rabin et al. [25] proposed a crucial cryptographic primitive OT. In a 1-out-of-2 OT configuration, the receiver can have a choice bit , while the sender can have input strings . The OT acts to prevent the receiver from knowing nothing regarding and prevent the sender from learning anything about . OT necessitates costly public-key operations. Ishai et al. [26] described an OT extension technique that permits many OT executions at the cost of doing few public-key procedures. We can use the instantiation OT in [15]. The ideal functionality of OT is defined in Figure 2.
Figure 2.
Ideal functionality of OT .
3.5. PaXoS
The following is a way to encode key-value mapping into a brief data structure using a PaXoS [19]. The associated Encode/Decode methods are frequently more convenient to describe when describing a PaXoS than the mapping.
: Given items , where and , indicate via the matrix where the i-th row is . Note that is the result of using the mapping to . It is possible to find a data structure (matrix) satisfying . In particular, the subsequent linear system of equations is fulfilled when the ’s are linearly independent:
: Given and , we can extract the corresponding “value” via .
3.6. Multi-Point OPRF
Chase [5] presented a PSI protocol for two parties based on multi-point OPRF. The sender chooses a pseudorandom seed , and the receiver computes a pseudorandom function based on its set elements to construct two matrices: and . For each , the corresponding bits in matrices are the same, while others are different. The sender obtains a matrix depending on seed and runs OTs with the receiver. Each column of the matrix is either or for all . Then, the sender computes according to each element to obtain all the resulting OPRFs and sends them to the receiver. Eventually, the receiver can find the intersection of the two sets based on its computed OPRF value.
3.7. Hamming Correlation Robustness
Under the assumption of correlation robustness for the underlying hash function, our MPSI structure is demonstrated to be secure.
Definition 2.
(Hamming Correlation Robustness [5]) If the distribution produced by the sampling of at random is pseudorandom for , , and has for each , is d-Hamming correlation robust. Namely:
where ⊕ denotes bitwise-AND and bitwise-XOR, respectively, and is a random function.
3.8. Cuckoo Hashing and Simple Hashing
Hash technology is one of the essential tools for optimizing communication and computational complexity in PSI protocols. There are two commonly used construction methods for hash technology: simple hashing and cuckoo hashing [10]. Simple hashing can map elements to positions in a hash table using hash functions, with each bucket being capable of storing multiple elements. Cuckoo hashing can map elements to a specific location in a hash table using a hash function, and its basic idea is to use multiple hash functions to handle collisions. When collisions occur, cuckoo hashing evicts the element occupying the original position, which can be rehomed to alternative positions. If alternative positions are already occupied, the process repeats until all elements can find their homes. Typically, cuckoo hashing and simple hashing are combined to achieve optimal results in PSI protocols.
4. Our MPSI Protocol
4.1. Overview
In this section, we show the MPSI protocol. A couple of parties with respective private input sets desire to collectively compute without disclosing any more information. Note that we regard as the set sizes for parties, as the leader, and as the client. The system model of the MPSI protocol is shown in Figure 3.
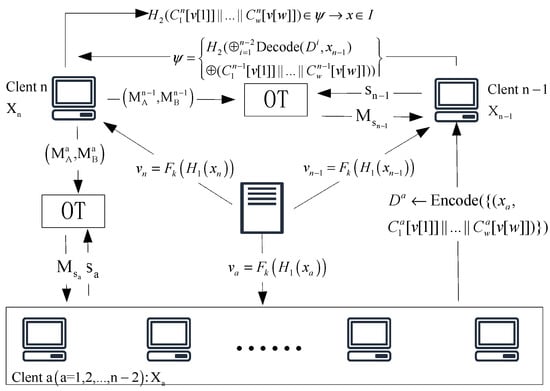
Figure 3.
System model.
constructs a random matrix and chooses strings for to generate the and sets , where . For each , from its input elements, constructs unique matrices . first initializes a matrix to all 1’s. For computing , is designed such that for all , and hence for all and . Then, locally encode a data structure PaXoS of their input sets using the entries of the received matrix and send to . decodes all the . Then, they compute and sends the OPRF values to . After receiving the OPRF values, computes according to its input set, which allows to find the intersection. This implies that, if , the hash function’s input from and will be equal. While the output of the PRF would be pseudorandom to if , the hash function’s input from will be dramatically different from any ’s input.
4.2. Our Protocol
We show our MPSI protocol in Figure 4. The selection of , , , and in our MPSI protocol follows [5] and they show how to choose the parameters concretely.
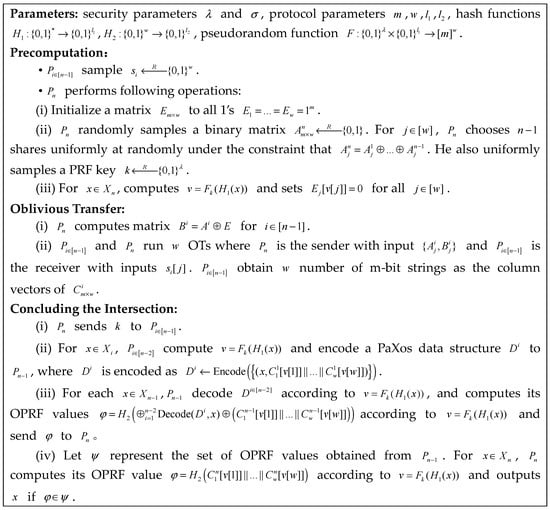
Figure 4.
Our MPSI protocol.
4.3. Protocol Correctness
constructs the special matrices and for such that computed for each satisfies for all . Let be the intersection element. Since each column of matrix is composed of uniform random shares as for , after the client runs OTs with , the matrix is obtained, satisfying . It holds that for each .
Based on the nature of the constructed data structure, we have . So, for , let , and we can always satisfy .
4.4. Protocol Security
Theorem 1.
If is a PRF, and are random oracles, and the underlying OT is protected against malicious receivers, then our MPSI protocol has one-sided malicious security which can be secure against malicious clients when , , , and are chosen appropriately.
Proof of Theorem 1.
We consider any client corrupted by an adversary . Let clients be corrupted, making the number of uncorrupted clients . Given , the simulator interacts with as follows. samples random matrices and performs malicious OT simulator on with outputs . honestly chooses PRF key and sends to . The simulator constructs random data structures representing honest parties according to the randomness of the matrices. and are initialized to an empty table. In ’s query to , records in table . In ’s query to , records in table . When receives OPRF value , finds all such that for some in , and where for . Finally, can send these to ideal functionality.
Let be a set of queries and make to and , respectively, and let , , and . We will misuse notation: for matrix and vector , means . For the set of vectors in , the set is denoted by .
We prove .
- Hyb0
- The outputs of parties in the real world.
- Hyb1
- Similar to , but performs OT simulator on to obtain . If , it randomly chooses string of length and constructs matrix , and it randomly chooses string of length and constructs matrix ; otherwise, it gives to OT simulator as output. is computationally indistinguishable from due to OT security against malicious receiver.
- Hyb2
- Similar to except that the protocol terminates if there exists , such that . Since is a random oracle, the protocol is aborted with negligible probability.
- Hyb3
- Same as , but, for each OPRF value received by , if , then ignores . Since is a random oracle, the probability of changing ’s output is negligible. equals the output of on one of ’s elements with negligible probability.
- Hyb4
- Same as except that the protocol terminates if there exists , with and . Since is a random oracle, the protocol is aborted with negligible probability.
- Hyb5
- Same as , but, for each OPRF value received by , ignores when calculating the set intersection if for some , where .This hybrid changes output only if there exist satisfying , which implies via the terminate condition added in .Note that if and , because of the construction of , we then have . Therefore, we need only think about . For all , , the output of changes only if there exist , satisfying .Suppose there is a PPT adversary that, with non-negligible probability, produces , , and such that there exist , satisfying . Then, [5] shows we can break the security of the PRF.
- Hyb6
- Same as except that the protocol terminates if there exists , such that, but . The protocol is aborted with negligible probability because of the security of the PRF.
- Hyb7
- Same as except that ’s outputs are substituted by its outputs in the ideal world. can change ’s outputs if and only if there exists a value received by and considered by such that for some , and for some , . Because is a random oracle, is aborted via terminate condition in with negligible probability.
- Hyb8
- Same as except that the protocol does not terminate. and are computationally indistinguishable since and are random oracles and is a PRF.
- Hyb9
- The output in the ideal world. The difference between and is that samples a random matrix and encodes a data structure PaXoS, which is identically distributed.
□
5. Performance Evaluation
5.1. Complexity Analysis
To better evaluate the complexity of the protocol, we first need to perform a simple analysis of the overall protocol process. It is important to note that this protocol uses only inexpensive tools such as OTs and bitwise operations, making it concretely efficient. We treat as the set sizes and set as in [5]. So, can be viewed as a value dependent on by fixing and .
Party is referred to as the leader carrying the majority overhead of the protocol, while the others are referred to as clients. Regarding the complexity of the protocol, designs matrices of a particular form, requiring linear complexity in . Then, they perform OTs for clients independently, resulting in linear complexity in the number of OTs. Moreover, just do encoding operations for data structure , and does hashing, bitwise-XOR, and decoding operations, which require linear communication and computation complexities. Although the computational overhead of is larger than that of other clients, they do not need to encode and send a data structure. From this, we can regard the overall communication and computation costs as uniformly distributed across all clients.
Note that our protocol can be divided into offline and online phases. Only lightweight procedures are required in the online phase, and communication and computation costs associated with performing OT can be handled in the offline phase. In addition, the bits exchanged among the parties concerning the random OT and the optimized malicious OT extension are summarized in Table 3.

Table 3.
Bits sent for leader and client.
5.2. Comparison
It should be noted that, due to the variations in architectures and security levels, making a fair comparison is challenging. Nevertheless, we have endeavored to include some recent studies pertaining to diverse security models (e.g., semi-honest, malicious, etc.). So, we contrast the complexity of communication and computation with [13,14,15] in Table 4, where is the number of parties, is the number of hash functions, is the size of input sets, and is the security parameter. In our MPSI protocol, the communication and computation complexity of the leader are , which is linear in the number of parties. Meanwhile, the complexity for the client remains constant regardless of the number of parties involved (namely, ) because the client only needs to compute and send a data structure and does not need to perform additional data transfers with other parties. Therefore, our protocol achieves a good trade-off between communication and computation overhead.

Table 4.
Complexity of MPSI protocols.
Figure 5 shows the security levels of the discussed protocols. Compared with [13], our protocol achieves a stronger security model without sacrificing communication and computation costs. We implement one-sided malicious security and [14] implements the Aug semi-honest model. It is difficult to define which security model is more practical, but our protocol has better computation and communication performance. Although the security model in [15] is higher-performing, our protocol has greater communication performance and achieves a better trade-off between communication and computation.
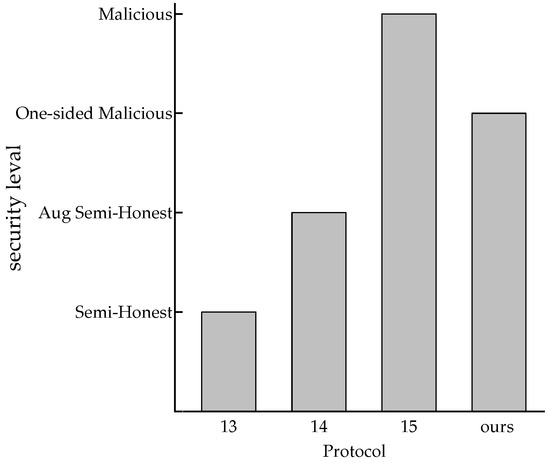
Figure 5.
Comparison of security levels.
5.3. Experimental Evaluation
In order to compare the runtime overhead of each protocol more intuitively, simulation experiments and a results analysis were performed. It should be noted that the time consumed by this protocol is the average time of multiple experiments. The experimental platform was Windows 10, Intel (R) Core (TM) i5-8250U CPU @ 1.60 GHz 1.80 GHz, 8.00 GB of RAM, and a compiled environment of Dev-C++5.11.
We first consider the total time required for each protocol to execute with different numbers of set elements. It is assumed that , , and are chosen for the comparison experiment, and Figure 6 shows the total running time of the protocol as a function of the number of elements contained in the set.
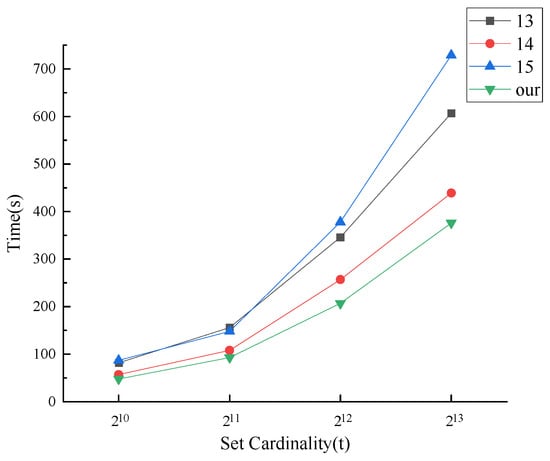
Figure 6.
Running time vs. set cardinality.
From Figure 6, the total time overhead in each protocol grows essentially linearly as the number of set elements continues to increase. However, the time of our MPSI protocol increases the slowest when the fixed set cardinality is small. Our MPSI protocol has the slowest time growth rate.
In addition, the effect of the change in the number of parties on the running time of the protocol is further considered. Suppose that the maximum number of elements contained in the set is , the security parameters are kept fixed at , and the number of parties is selected for the comparison experiment. The total protocol runtime as a function of the number of parties is shown in Figure 7.
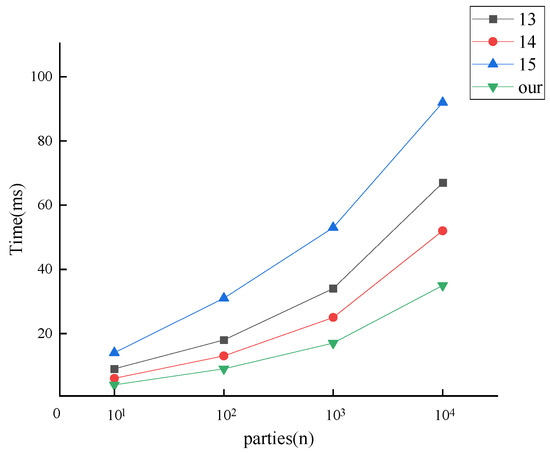
Figure 7.
Running time vs. the number of parties.
From Figure 7, the running time of all protocols increases gradually with the number of parties. The time overheads of our MPSI protocol are lower than those of the other protocols when n is fixed. In addition, our MPSI protocol has the slowest time growth rate.
6. MPCCache in Edge Computing
This section aims to address the problem of edge collaborative content caching, wherein all parties can jointly cache the most frequently accessed common data items in shared caches. Figure 8 shows the difference between the traditional cache model and edge cache model. Our challenge is to find how to determine a set of the most frequently accessed common items without revealing any underlying data.
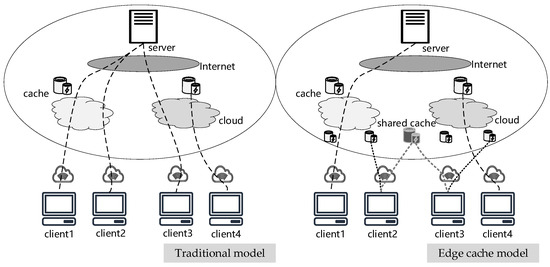
Figure 8.
Traditional cache model and edge cache model.
6.1. Our MPCCache
We describe how to use our MPCCache protocol to handle the edge cache case. The network operators respectively own set , where denotes an identify element and denotes its associated value. Note that the latter may represent the anticipated frequency of content being accessed or the value to network operators of the cached content. Let the common items be the intersection of the identifiers, where is the set of identity for . For each common item , calculate a sum of the associated values ; that is, . The sum of a common item is determined as the total of the individual values of the operators for the item.
We present the MPCCache protocol in Figure 9. conduct simple hashing and conducts cuckoo hashing that maps common items to the same bucket. According to the PaXoS, all the buckets are compressed into a data structure so that can efficiently compute the MPCCache. In detail, choose and uniformly at random for . Notice that for each . For and , compute and , and send the encoding and to , where means that is in bucket. can use to obtain the correct decoding and if ; it is otherwise random. Then, computes and . Finally, input and , respectively, to check whether is based on a garbled circuit, and, if so, obtain the sum of the corresponding common item .
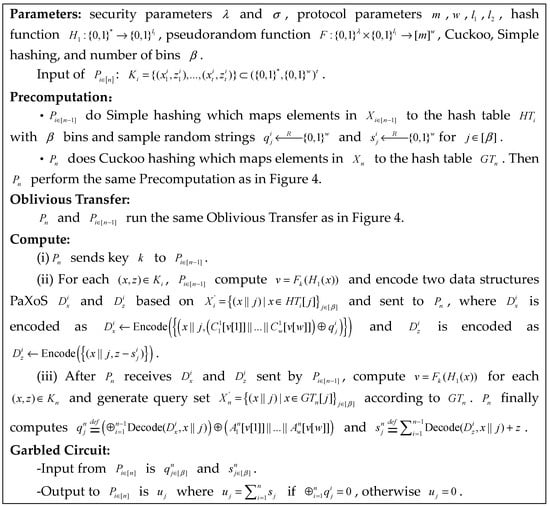
Figure 9.
Our MPCCache protocol.
6.2. Correctness and Security
Correctness: Section 4.3 proves that for each and ; that is, . Via the property of the data structure PaXoSs and constructed by , for , , and , we always have , . At the same time, defines and in terms of the and they receive from . That is, when , it always satisfies that and .
Theorem 2.
If is a PRF and is a random oracle, then the construction of our MPCCache protocol has colluding semi-honest security, given the OT, PaXoS, GC, and appropriate parameters.
Proof of Theorem 2.
If we consider parties to be corrupted by an adversary , then the number of uncorrupted parties is . Given , the simulator interacts with as follows. samples random matrices, performs OT, chooses the PRF key and sends to . The simulator constructs random data structures representing honest parties according to the randomness of the matrices. sends two data structures and constructed on a PaXoS to ideal functionality. We prove .
- Hyb0
- The outputs of parties in the real world.
- Hyb1
- Same as , , and in Section 4.4.
- Hyb2
- Similar to except that the decoding executions of the PaXoS are replaced as follows. When does not contain , receives nothing from the data structure PaXoS. When contains , if , receives and , thus , for the PaXoS involving the non-colluding party and . Note that and are used in the above expression for each bin . Since these values are uniform, so are and . Therefore, we replace the decoding outputs of the PaXoS with random ones. Otherwise, all the decoding outputs of the PaXoS are uniformly random from the perspective of and . is computationally indistinguishable from due to the PaXoS’s security.
- Hyb3
- The output in the ideal world. The only difference between and is that executes the output of the circuit.
□
7. Conclusions
In this work, we design an efficient MPSI protocol and the MPCCache protocol to better solve the information leakage problem in resource sharing. The proposed MPSI protocol derived from multi-point OPRF demonstrates concrete efficiency in achieving one-sided malicious security. The protocol also leads to a better trade-off between communication and computational overhead. It is based on OT and a data structure PaXoS and achieves linear computation and communication complexity concerning the input set size of each party. In our MPSI protocol, the asymptotic communication and computational complexity of the clients are largely determined by the size of the input sets rather than the number of parties (namely, ). Overall, this research has contributed to the development of efficient MPSI protocols for multiple parties in practice. In fact, we apply the MPCCache protocol to edge caching scenarios using a simple transformation of the MPSI protocol. The MPCCache protocol under the semi-honest model can support the computation of specific functions on intersections. It is our belief that future work can improve the fairness of the MPSI protocol, as well as propose more application scenarios with practical application value.
Author Contributions
Conceptualization, J.Z., L.Y. and Y.T.; methodology, L.Y. and Y.T.; validation, J.Z., L.Y. and Y.T.; formal analysis, L.Y. and M.J.; writing—original draft preparation, L.Y.; writing—review and editing, Y.T., S.W. and M.J.; supervision, Y.T. and S.W.; funding acquisition, J.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by Henan Key Laboratory of Network Cryptography Technology (No. LNCT2022-A11), the Henan Province Key R&D and Promotion Special Project (No. 212102210166), and the PhD Foundation of Henan Polytechnic University (No. B2021-41).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wei, X.; Xu, L.; Cai, G.; Wang, H. Secure approximate pattern matching protocol via Boolean threshold private set intersection. Int. J. Intell. Syst. 2022, 37, 9245–9266. [Google Scholar] [CrossRef]
- Kales, D.; Rechberger, C.; Schneider, T.; Senker, M.; Weinert, C. Mobile private contact discovery at scale. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 1447–1464. [Google Scholar]
- Ion, M.; Kreuter, B.; Nergiz, E.; Patel, S.; Saxena, S.; Seth, K.; Shanahan, D.; Yung, M. Private intersection-sum protocol with applications to attributing aggregate ad conversions. Cryptol. ePrint Arch. 2017. preprint. Available online: https://eprint.iacr.org/2017/738 (accessed on 11 September 2023).
- Nguyen, D.T.; Trieu, N. MPCCache: Privacy-preserving multi-party cooperative cache sharing at the edge. In Financial Cryptography and Data Security: 26th International Conference, FC 2022, Grenada; Springer International Publishing: Berlin/Heidelberg, Germany, 2022; pp. 80–99. [Google Scholar] [CrossRef]
- Chase, M.; Miao, P. Private set intersection in the internet setting from lightweight oblivious PRF. In Proceedings of the Advances in Cryptology–CRYPTO 2020: 40th Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2020; pp. 34–63. [Google Scholar] [CrossRef]
- Pinkas, B.; Rosulek, M.; Trieu, N.; Yanai, A. SpOT-light: Lightweight private set intersection from sparse OT extension. In Proceedings of the Advances in Cryptology–CRYPTO 2019: 39th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2019; pp. 401–431. [Google Scholar] [CrossRef]
- Pinkas, B.; Schneider, T.; Zohner, M. Scalable private set intersection based on OT extension. ACM Trans. Priv. Secur. TOPS 2018, 21, 1–35. [Google Scholar] [CrossRef]
- Cong, K.; Moreno, R.C.; da Gama, M.B.; Dai, W.; Iliashenko, I.; Laine, K.; Rosenberg, M. Labeled PSI from homomorphic encryption with reduced computation and communication. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, Republic of Korea, 15–19 November 2021; pp. 1135–1150. [Google Scholar] [CrossRef]
- Chen, H.; Huang, Z.; Laine, K.; Rindal, P. Labeled PSI from fully homomorphic encryption with malicious security. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 1223–1237. [Google Scholar] [CrossRef]
- Pinkas, B.; Schneider, T.; Weinert, C.; Wieder, U. Efficient circuit-based PSI via cuckoo hashing. In Proceedings of the Advances in Cryptology–EUROCRYPT 2018: 37th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tel Aviv, Israel, 29 April–3 May 2018; pp. 125–157. [Google Scholar] [CrossRef]
- Pinkas, B.; Schneider, T.; Tkachenko, O.; Yanai, A. Efficient circuit-based PSI with linear communication. In Proceedings of the Advances in Cryptology–EUROCRYPT 2019: 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, 19–23 May 2019; pp. 122–153. [Google Scholar] [CrossRef]
- Chandran, N.; Gupta, D.; Shah, A. Circuit-PSI With Linear Complexity via Relaxed Batch OPPRF. Proc. Priv. Enhancing Technol. 2022, 1, 353–372. [Google Scholar] [CrossRef]
- Kavousi, A.; Mohajeri, J.; Salmasizadeh, M. Efficient scalable multi-party private set intersection using oblivious PRF. In Proceedings of the Security and Trust Management: 17th International Workshop, STM 2021, Darmstadt, Germany, 8 October 2021; pp. 81–99. [Google Scholar] [CrossRef]
- Inbar, R.; Omri, E.; Pinkas, B. Efficient scalable multiparty private set-intersection via garbled bloom filters. In Proceedings of the Security and Cryptography for Networks: 11th International Conference, SCN 2018, Amalfi, Italy, 5–7 September 2018; pp. 235–252. [Google Scholar]
- Ghosh, S.; Nilges, T. An algebraic approach to maliciously secure private set intersection. In Proceedings of the Advances in Cryptology–EUROCRYPT 2019: 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, 19–23 May 2019; pp. 154–185. [Google Scholar] [CrossRef]
- Kolesnikov, V.; Kumaresan, R.; Rosulek, M.; Trieu, N. Efficient batched oblivious PRF with applications to private set intersection. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 818–829. [Google Scholar]
- Pinkas, B.; Schneider, T.; Zohner, M. Faster private set intersection based on {OT} extension. In Proceedings of the 23rd USENIX Security Symposium (USENIX Security 14), San Diego, CA, USA, 20–22 August 2014; pp. 797–812. [Google Scholar]
- Nevo, O.; Trieu, N.; Yanai, A. Simple, fast malicious multiparty private set intersection. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security, Virtual Event, Republic of Korea, 15–19 November 2021; pp. 1151–1165. [Google Scholar] [CrossRef]
- Pinkas, B.; Rosulek, M.; Trieu, N.; Yanai, A. PSI from PaXoS: Fast, malicious private set intersection. In Proceedings of the Advances in Cryptology–EUROCRYPT 2020: 39th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 10–14 May 2020; pp. 739–767. [Google Scholar] [CrossRef]
- Ben-Efraim, A.; Nissenbaum, O.; Omri, E.; Paskin-Cherniavsky, A. Psimple: Practical multiparty maliciously-secure private set intersection. In Proceedings of the 2022 ACM on Asia Conference on Computer and Communications Security, 30 May–2 June 2022; pp. 1098–1112. [Google Scholar]
- Bui, D.; Couteau, G. Private Set Intersection from Pseudorandom Correlation Generators. IACR Cryptol. ePrint Arch. 2022, 2022, 334. [Google Scholar]
- Chida, K.; Hamada, K.; Ichikawa, A.; Kii, M.; Tomida, J. Communication-Efficient Inner Product Private Join and Compute with Cardinality. Cryptol. ePrint Arch. 2022. preprint. Available online: https://eprint.iacr.org/2022/338 (accessed on 11 September 2023).
- Miao, P.; Patel, S.; Raykova, M.; Seth, K.; Yung, M. Two-sided malicious security for private intersection-sum with cardinality. In Proceedings of the Advances in Cryptology–CRYPTO 2020: 40th Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2020; pp. 3–33. [Google Scholar] [CrossRef]
- Goldreich, O. Foundations of Cryptography: Volume 2, Basic Applications; Cambridge University Press: New York, NY, USA, 2009. [Google Scholar]
- Rabin, M.O. How to exchange secrets with oblivious transfer. Cryptol. ePrint Arch. 2005. preprint. Available online: https://eprint.iacr.org/2005/187 (accessed on 11 September 2023).
- Ishai, Y.; Kilian, J.; Nissim, K.; Petrank, E. Extending Oblivious Transfers Efficiently. Crypto 2003, 2729, 145–161. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).