Abstract
Most existing chaotic systems have many drawbacks in engineering applications, such as the discontinuous range of chaotic parameters, weak chaotic properties, uneven chaotic sequence outputs, and dynamic degradation. Therefore, based on the above, this paper proposes a new method for the design of a three-dimensional chaotic map. One can obtain the desired number of positive Lyapunov exponents, and can also obtain the desired value of positive Lyapunov exponents. Simulation results show that the proposed system has complex chaotic behavior and high complexity. Finally, the method is implemented into an image encryption transmission scheme and experimental results show that the proposed image encryption scheme can resist brute force attacks, correlation attacks, and differential attacks, so it has a higher security.
1. Introduction
Numerous issues prevent the use of chaotic systems in engineering [1,2,3,4,5,6]. Firstly, since classical chaotic systems have a relatively basic structure, it is possible to predict the chaotic system’s control parameters and even the complete sequence as computing power improves. Secondly, these chaotic systems all exhibit weak chaotic phenomena, where small changes in control parameters can lead to the disappearance of chaotic phenomena. Thirdly, due to the issue of dynamic degradation, these chaotic systems pose serious security vulnerabilities, which can affect chaotic-based applications.
The application of chaos in cryptography has become a hot research field owing to its unpredictability, sensitivity to initial values, inherent randomness, ergodicity, topological transitivity, positive Lyapunov exponent, and other good properties [1,2,7,8,9]. Numerous novel chaotic systems have been developed in an effort to enhance the dynamic properties. Two general categories may be used to describe the new chaotic systems. The first category involves making suggestions for enhanced chaotic systems based on current chaotic systems. In reference [10], for the creation of a new two-dimensional chaotic map, a discrete memory model is coupled with a one-dimensional chaotic map. References [11,12] proposed nesting three different one-dimensional maps to generate segmented functions. References [13,14] coupled two one-dimensional chaos maps to generate two-dimensional chaotic maps, etc. The second type is to construct new chaotic maps from linear function or nonlinear functions. A novel two-dimensional polynomial chaotic map constructed according to “periodic three implication chaos” was proposed in reference [15], and subsequently studied the dynamic characteristics of this map. Moreover, reference [16] constructed a chaotic transmission scheme based on a three-dimensional hyperchaotic system. Reference [17] proposed an image encryption based on a three-dimensional piecewise map. However, these system models cannot obtain the desired Lyapunov exponent; that is, the Lyapunov exponent is independent of the control parameters of the system. Next, a multidimensional polynomial chaos system based on the similarity matrix is proposed in reference [18]. However, the elements of the Jacobian matrix of the system are all constant; that is, the expression of the map is linear. This method can only be applied to high-dimensional chaotic maps, but not to two-dimensional chaotic maps. In addition, if you want a different Lyapunov exponent, you have to calculate it all over again. Therefore, there is no generality. Hua et al. [19] proposed a generalized two-dimensional polynomial chaotic map, and based on this construction method, one can obtain a series of two-dimensional chaotic maps with any desired positive Lyapunov exponents. However, the last term of the constructed system is a linear term, so if the initial value and control parameters are improperly selected, then the value of the last term will collapse to a fixed value, and then the dynamic characteristics of the system will degenerate. Hua et al. [20] carried out modular transformation based on two-dimensional Henon map. After the improvement, the Lyapunov exponents of the system was directly determined by the parameter b; when the parameter b is increased, the complexity of the system was further improved. In addition, this reference proposed the optimization of the Henon map model; that is, the optimization of the existing model. In turn, the application is more limited. In order to solve the above problems, a generalized three-dimensional polynomial chaotic system is proposed in this paper.
The following is a summary of the main work of this paper: (1) We propose a generalized three-dimensional polynomial chaotic map model. By giving different control parameters and the highest degree of polynomial through a proposition, a series of three-dimensional chaotic maps can be obtained. Moreover, these systems are robust and can obtain the expected Lyapunov exponent. (2) The theoretical analysis results indicate that the three-dimensional polynomial chaotic map model can generate robust chaos and the expected Lyapunov exponent. (3) The transmission of encryption and decryption images is realized by synchronization of chaotic systems.
The remaining parts of this article are organized as follows. A three-dimensional polynomial chaotic map model is shown in Section 2, and the parameter range for the existence of chaotic behavior is provided by a proposition. A transmission mechanism for image encryption is provided in Section 3. Section 4 provides the related security analysis. The conclusion is presented in Section 5.
2. Construction of 3D Polynomial Chaotic System Model
A new three-dimensional polynomial dynamical map is designed in this section to improve the dynamic properties of the system. One can obtain the desired number of positive Lyapunov exponents, and can also obtain the desired value of positive Lyapunov exponents. The mathematical equations of a three-dimensional polynomial dynamical map proposed in this paper are calculated as follows:
where , and are the state variables of the system (1), and the control parameters of the proposed system are ; moreover, is the highest degree of the polynomial; is the modulus coefficient. In this paper, is taken as a random disturbance to prevent state variable from collapsing into a fixed value. Next, we discuss the range of chaotic parameters of the dynamical system with Proposition 1. The most reliable way to determine whether a map is chaotic or not is to use the Lyapunov exponent; therefore, the map proposed in this paper was evaluated by using the Lyapunov exponent.
Definition 1
([21]). A three-dimensional map is considered chaotic if it is globally bounded, and has at least one positive Lyapunov exponent; if there is more than one positive Lyapunov exponent, it is hyperchaotic.
The three Lyapunov exponents of a three-dimensional discrete dynamic system are calculated as follows [22]:
where is the i-th eigenvalue of matrix , and the expression for is as follows:
where is the Jacobian matrix at the i-th iteration of the system.
Proposition 1.
If any of the three control parameters of system (1) are satisfied such that and , then the system is chaotic; if any two of the three control parameters of system (1) are satisfied such that and
, the system is hyperchaotic.
Proof.
The Jacobian matrix of the i-th iteration of system (1) is as follows:
and the expression for matrix is derived as follows:
where and are specific numbers expressed by the variables and control parameters. Then the two eigenvalues and of the matrix can also be easily solved.
Then, the three Lyapunov exponents of the map are derived as follows:
By the same token, . The output of the system must be globally bounded due to the modulo operation in the model. If control parameter , then the map is chaotic. If control parameter and , the map is hyperchaotic. □
2.1. Numerical Example
In order to facilitate calculation, we take in this paper, and the mathematical expression of the three-dimensional polynomial chaotic map is as follows:
According to Proposition 1, if two or more of , and are true, the system is in hyperchaos; if one of them is true, the system is in a chaotic state; if none of them is true, the system is in a stable state. Figure 1 shows the trajectory of the proposed map with following parameters: , and is a random number between . With the increase of iteration times, the output of the map can randomly visit or approach all the areas of the data range. The bifurcation diagram of a dynamic system shows the points that the system passes through under different parameters, and this process provides an intuitive way for scholars to study the nature of chaos. Figure 2 illustrates in three-dimensional terms the bifurcation diagrams for different parameters, and it can be seen that the state variable is evenly distributed throughout the space for different control parameters. The Lyapunov exponents of the proposed map varying with the control parameters and are shown in Figure 3. One can observe that the proposed map has three positive Lyapunov exponents in the parameter range. In addition, if the control parameters of the map change slightly, the proposed map is still in chaos, which can indicate that the proposed map shows robust hyperchaotic behavior and more complex dynamic properties.
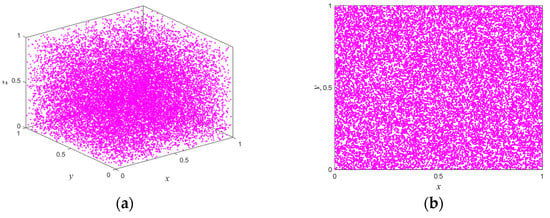
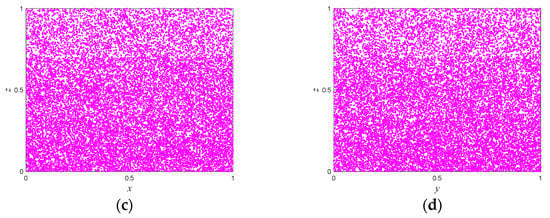
Figure 1.
The phase trajectory of the system with initial conditions : (a) phase diagram; (b) phase diagram; (c) phase diagram; (d) phase diagram.
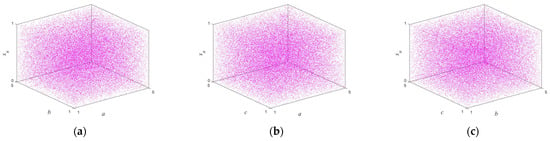
Figure 2.
The bifurcation diagram of the system with two parameters: (a) the bifurcation diagram of state variable with control parameters and ; (b) the bifurcation diagram of state variable with control parameters and ; (c) the bifurcation diagram of state variable with control parameters and .
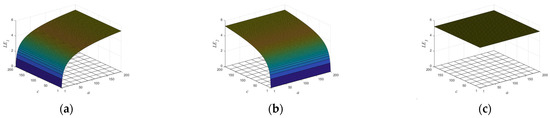
Figure 3.
The Lyapunov exponents of the proposed map varying with the control parameters and with [1, 200]: (a) the values of the proposed map; (b) the values of the proposed map; (c) the values of the proposed map.
2.2. Sample Entropy Analysis
The complexity of dynamical system refers to the degree to which the time sequence is close to the random sequence. The higher the complexity, the closer the sequence is to the random sequence and the higher the corresponding security. In this paper, sample entropy is adopted to calculate the degree of complexity of a time series [23,24]. In order to give a better description, the sample entropy was normalized later. The closer the sample entropy is to 1, the greater the irregularity of the map is. Figure 4 shows the sample entropy values of the three sequences of the map as the parameters change and . It is not difficult to see that the sample entropy values in Figure 4 are close to 1 in the whole interval, indicating that the chaotic sequence generated by the map has high complexity and can be applied to the fields of image encryption, information processing, and secure communication.
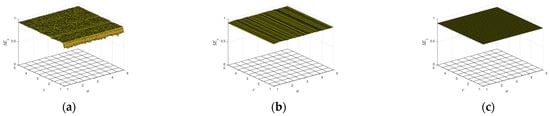
Figure 4.
The sample entropy values of the three sequences of the map as the parameters change and with : (a) the sample entropy values of sequence of the map; (b) the sample entropy values of sequence of the map; (c) the sample entropy values of sequence of the map.
2.3. Pseudo-Randomness Analysis
In this section, the NIST SP 800-22 tests are used to demonstrate the randomness of the output sequences of the proposed maps. The 15 tests include frequency, longest run, approximate entropy test, linear complexity test, and so on. Additionally, these 15 tests focus on whether the binary sequence has an acceptable pseudo-randomness [25]. The binary sequence is considered random if the estimated p-value is 0.01, otherwise it is considered non-random. As the output of the proposed map is in the range [0, 1], it is recommended that a pseudo-random number generator be used, which has the following structure:
where is used to obtain the largest integer smaller than or equal to , and is the three sequences of the proposed map. In addition, is a large number that affects the value of the sequence, and is an integer. Set and we can obtain a binary sequence of 8 bits.
After the system (9) has been quantized by the pseudo-random sequence generator introduced in this paper, there are three pseudo-random sequences generated, for which the first 3000 values are dropped to avoid the initial value effect. Then, 100 sets of sequences of length are taken and tested with the NIST test suite, respectively. Table 1 shows the set with the lowest p-values. Therefore, it is clearly shown in the Table 1 that all 15 tests were successful. This shows that the chaotic sequence generated by this model has strong randomness, which indicates that the sequence produced by this model is random relative to the 15 tests of the NIST suite.

Table 1.
NIST test results of the proposed chaotic sequences.
3. A 3D Polynomial Chaotic Image Encryption Transmission Scheme
3.1. Image Encryption Scheme
The proposed map-based image encryption model is presented in this section. The encryption scheme is based on “confusion” and “diffusion”, with the confusion part working by separating adjacent pixels in the image to different positions and the diffusion part using an invertible function to change the value of a specific pixel. This paper performed the aforementioned process twice. The confusion part is described in detail by Algorithm 1 below. A numerical example is presented in Figure 5. Matrices and are reshaped by the chaotic sequences and , whose lengths are It can be observed that almost all pixels are scrambled after a round of confusion. The diffusion part will process the confusion image again. In one round of encryption, one can rearrange the confusion image into one column matrix , and sort the with as a matrix . Figure 6 shows a numerical example of the scheme, and the current pixel of the diffusion image can be obtained by:
where is used to obtain the largest integer that is smaller than or equal to . In addition, one can rearrange into a matrix with size of . The second round of operations performs the same operation based on another matrix, and the encrypted ciphertext image can be obtained.
| Algorithm 1: The procedure of the confusion part of the proposed image encryption scheme. |
| Input: Plaintext image and initial values , , . |
| Output: Confusion image |
|
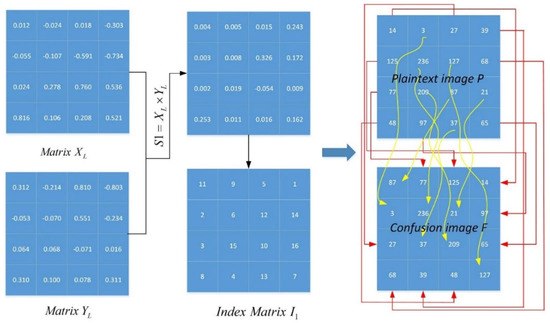
Figure 5.
An example of the confusion part of image encryption.
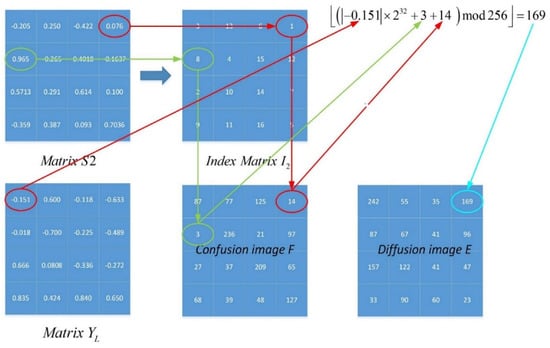
Figure 6.
An example of the diffusion part of image encryption.
3.2. Image Decryption Scheme
Generally speaking, the decryption process is the inverse operation of the encryption process. Thus, the process of diffusion can be described as follows:
Thus, the confusion image can be obtained using the inverse operation of diffusion of image encryption. What is more, the original image can be completely reconstructed using the inverse confusion of image encryption.
3.3. Nonlinear Feedback Synchronization Control Scheme
A polynomial discrete chaotic system is taken as an example to realize the synchronization of the nonlinear feedback method. The driving system is:
and the expression of the response system is:
where is a vector controller. We aim to design a suitable nonlinear controller so that the state trajectory of the slave system is consistent with that of the master system, namely . The vector controller is designed as follows:
Defining systematic errors: , and the synchronous error discrete system of the drive system (12) and the response system (13) is expressed as Equation (15).
Lemma 1
([26]). For linear discrete difference systems , is a coefficient matrix. The system is asymptotically stable if the magnitude of all eigenvalues of matrix a is less than or equal to 1.
Obviously, the Equation (15) is asymptotically stable; that is, system (12) and system (13) can achieve synchronization. We set the initial values of systems (12) and (13) as and , respectively. The performance of the synchronization error is shown in Figure 7. The synchronization error is approaching 0 with a quickly speed, in consequence the transceiver system achieves synchronization.
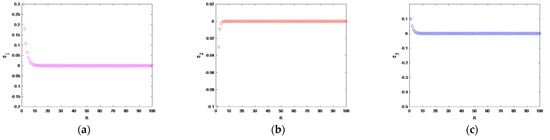
Figure 7.
Synchronization error diagram of drive–response system: (a) ; (b) ; (c) .
3.4. Transmission Scheme
An image encryption transmission based on nonlinear feedback synchronization is proposed in this paper. The framework of the proposed scheme is depicted in Figure 8, in which the proposed three-dimensional polynomial chaotic system (12) is used as the master system and the slave system is system (13). For a gray image, one can rearrange the encrypted image into one column matrix . Then, the sequence and state variable are masked into the signal ; then, the signal is sent to the receiver end via the public channel. At the receiver end, the recovered signal can be obtained through the signal and state variable . In addition, there will inevitably be noise in the channel to break the transmitted signal. Taking Gaussian white noise as an example, we add a DCT transform filter to the receiving end to ensure that the recovered image is as close as possible to the original image. Finally, one can also reshape the recovered signal into an image with size of .
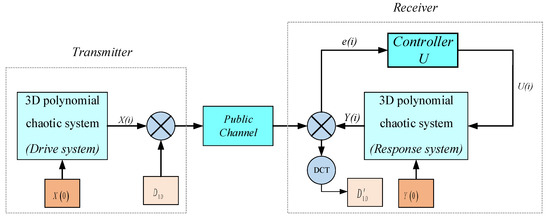
Figure 8.
The framework of the proposed image encryption transmission scheme.
3.5. Simulation Results
Different kinds of encrypted pictures must be transmitted to the receiving side over a public channel in the image encryption transmission system. The receiver must also evenly recreate the original picture. Various kinds of pictures encrypted using the suggested approach are displayed in Figure 9.

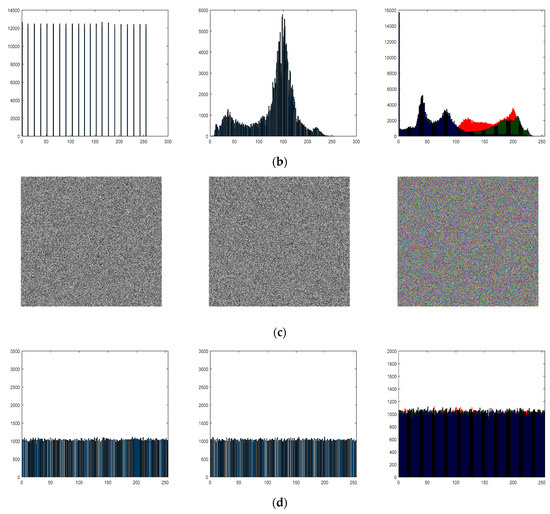
Figure 9.
Simulation results: (a) plaintext images; (b) histograms of plaintext images; (c) images of the receiver end; (d) histogram of images of the receiver end.
4. Security Analysis
There are a number of analyses, such as key security analysis, histogram analysis, the Shannon entropy analysis, correlation analysis, and differential attacks, that can be applied to show the performance of the proposed image encryption scheme. Therefore, this section applies the above methods to measure the performance of the introduced methods.
4.1. Key Sensitivity Analysis
An image encryption scheme should firstly have a large enough key space to resist brute-force attack. The security key of the proposed encryption scheme is a binary string with 320 bits. The security key contains 10 parts , where is the hash value (SHA-256) of the plaintext information. Since their lengths are 32 bits, respectively, and the key space of the proposed scheme can reach since the key length is 320 bits. The key space is much larger than ; that is, the scheme is resistant to brute-force attacks. An incorrect key with a little change from the initial key might also obtain the plaintext information, hence the suggested picture encryption system must be extremely sensitive to the initial key. In other words, each key may decode the encrypted picture when the identical plaintext image is encrypted with two keys that differ by one bit. Hence, an effective encryption technique should be capable of preventing the recovery of the original picture data during decryption using a different key. Figure 10 shows the key sensitivity results. The same plaintext image is encrypted and decrypted by two keys and with one bit difference. Each key can decrypt the original image. If the other key is used for decryption, the original image information cannot be obtained. Thus, the proposed scheme is sensitive to its keys in both encryption and decryption processes.

Figure 10.
The key sensitivity results: (a) the plaintext image; (b) the ciphertext image encrypted by ; (c) the decrypted from using ; (d) the decrypted from using .
4.2. Histogram Analysis
For further evaluation of the uniformity of the pixel values of the encrypted images, in this paper we employed the chi-square test. The statistics value can be defined as
where is the value of the current pixel, and is the expected occurrence frequencies of each pixel. When the calculated value of a ciphertext image does not exceed 293.2478, the encrypted image can pass the chi-square assessment [27]. The chi-square values of virous encrypted images are shown in Table 2. Obviously, those values do not exceed 293.2478, which shows that the distributions of the pixel values of the encrypted images are uniformly distributed.

Table 2.
The values of encrypted images.
4.3. The Shannon Entropy
In order to quantitatively measure the information distribution of the ciphertexts, the Shannon entropy is applied to assess whether an encrypted image is a random-like image with pixel values randomly distributed. Its mathematical expression is defined by:
where and are the maximum and individual pixel values of an image, respectively. In addition, is the discrete probability density function. Take gray images, for example, and each pixel contains 8 binary bits: when , and ; that is, the encrypted image is uniformly distributed. Table 3 lists the Shannon entropy of several test images obtained from the USC-SIPI image database. It can be seen from Table 3 that the average Shannon entropy value of the image after encryption by this scheme is 7.9986, and these values are much closer to 8, which indicates the encrypted images are uniformly distributed.

Table 3.
The Shannon entropy values of several original and encrypted images.
4.4. Correlation Analysis
The pixel correlation of an image covers three directions: horizontal, vertical, and diagonal. Thus, for a good encryption algorithm, the goal should be to reduce the correlation between adjacent pixels. It can be defined as the correlation between two pixel sequences, which is given by:
where and are adjacent pixels values, is correlation coefficient of the adjacent pixels. The 3000 pairs of adjacent pixels—from the plaintext and encrypted images in horizontal, vertical, and diagonal directions—are randomly selected. These distribution of the 3000 pairs are shown in Figure 11. The plaintext image has pixels close to the diagonal while the cipher text image has a random distribution of pixels which can be seen in Figure 10. The comparative results of the correlation obtained by using different encryption schemes are presented in Table 4. It is clear that the proposed method has an value close to zero compared to the other schemes.
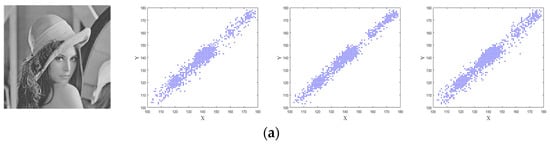
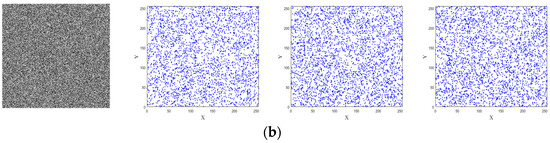
Figure 11.
The correlation distributions: (a) the plaintext image and correlation distributions of three directions; (b) the ciphertext image and correlation distributions of three directions.
4.5. Differential Attack
When little modifications to the source picture cause substantial changes to the encrypted image, differential attacks are largely ineffective. The number-of-pixels change rate (NPCR) and unitary averaged changed intensity (UACI) tests [28] are used to assess the capacity of the proposed picture encryption methods to withstand differential assaults. The NPCR and UACI can be expressed as shown below:
where denotes the two encrypted pictures and , which are identical to the original images except for a single additional pixel, and is the total number of pixels in the encrypted images and The ideal expectations NPCR and UACI values are 99.61% and 33.46%, respectively [12]. The suggested encryption scheme’s mean NPCR and UACI values are shown in Table 5, and the size of all of the pictures is , from the USC-SIPI’s Miscellaneous dataset, along with the comparisons to other methods. The findings are shown in Table 6. These findings are obviously more in line with the intended predicted values, which shows that the suggested method performs better in terms of defending against differential assaults.

Table 4.
Adjacent pixel correlations of the plaintext image “Lena” and its ciphertext image using different encryption schemes.
Table 4.
Adjacent pixel correlations of the plaintext image “Lena” and its ciphertext image using different encryption schemes.
| Schemes | Horizontal | Vertical | Diagonal |
|---|---|---|---|
| “Lena” image | 0.94010 | 0.97689 | 0.95667 |
| Ref. [23] | 0.00030 | 0.00140 | 0.00220 |
| Ref. [28] | −0.00150 | −0.00210 | 0.00190 |
| Ref. [29] | 0.00283 | 0.00183 | 0.00330 |
| Ref. [30] | 0.00340 | 0.00580 | 0.00450 |
| Ref. [31] | −0.00150 | 0.00410 | 0.00690 |
| Proposed method | −0.00091 | −0.00110 | 0.00100 |

Table 5.
The values of NPCR and UACI of ciphered images.
Table 5.
The values of NPCR and UACI of ciphered images.
| Images | NPCR (%) | UACI (%) | ||||
|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |
| 4.1.01.tiff | 99.60 | 99.61 | 99.62 | 33.14 | 33.17 | 33.47 |
| 4.1.03.tiff | 99.61 | 99.62 | 99.63 | 33.34 | 33.67 | 33.42 |
| 4.1.04.tiff | 99.64 | 99.60 | 99.64 | 33.25 | 33.36 | 33.43 |
| 4.2.03.tiff | 99.62 | 99.59 | 99.62 | 33.15 | 33.46 | 33.42 |
| 4.2.07.tiff | 99.58 | 99.61 | 99.61 | 33.24 | 33.53 | 33.43 |
| Lena | 99.60 | 99.58 | 99.63 | 33.41 | 33.32 | 33.45 |

Table 6.
NPCR and UACI comparison of Lena.
Table 6.
NPCR and UACI comparison of Lena.
| Reference | NPCR (%) | UACI (%) | ||||
|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |
| Ref. [32] | 99.62 | 99.60 | 99.64 | 33.50 | 33.47 | 33.43 |
| Ref. [33] | Mean = 99.64 | Mean = 33.49 | ||||
| Ref. [34] | 99.63 | 99.68 | 99.69 | 33.45 | 33.42 | 33.46 |
| Ref. [35] | Mean = 99.63 | Mean = 33.47 | ||||
| This paper | 99.67 | 99.64 | 99.67 | 33.42 | 33.43 | 33.44 |
4.6. Complexity Analysis
Because the system is a discrete time model, that is, a difference equation, the time complexity of this part is O(n), where . The confusing part is the indexed sequential lookup problem, which has a complexity of O(nlogn). The diffusion part is a cycle of n degrees, and the complexity of this part is also O(n). In addition, the complexity of the hash function is O(1). Then, the time complexity of the scheme is O(nlogn). The effectiveness of the encryption technique is also significantly measured by the time complexity, based on the AMD Ryzen 7 5800 H 3.20 GHz CPU model, and the modeling environment is Matlab 2021a. The encryption technique suggested in this research was used to independently encrypt and time-test the Lena pictures of sizes 128 × 128, 256 × 256, 512 × 512 and 1440 × 900. The test results are displayed in Figure 12. The approach suggested in this work also yielded the following results: for the algorithm, the encryption time is related to the size of the picture being encrypted; the larger the image, the longer the encryption time. The scheme processes the required data in two rounds, so the computational complexity is O(n).
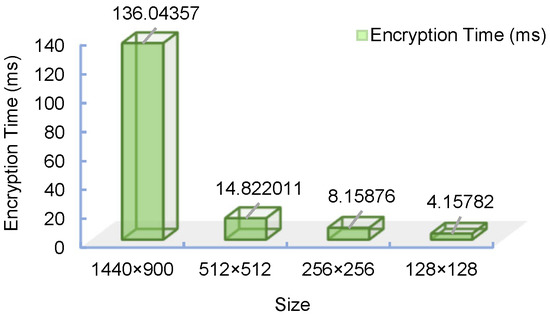
Figure 12.
Histograms of encryption times for different image sizes.
5. Conclusions
This paper presents a new approach to the design of a generalized three-dimensional chaotic model, whose Lyapunov exponents can be constructed directly from system control parameters. In addition, the proposed method was used to construct three-dimensional robust chaotic maps with different Lyapunov exponents. Simulation results showed that the chaotic system has complex chaotic behavior and high complexity. Finally, the method was implemented into an image encryption transmission scheme. Experimental results showed that the original image could be recovered from the receiver, while the proposed algorithm was analyzed for security using initial secret key sensitivity tests, histogram analysis, and differential attacks, and so on, and the simulation results demonstrated the feasibility of the proposed method.
Author Contributions
Y.Z. was in charge of methodology, validation, and writing original draft preparation. W.D. was in charge of software, and validation. J.Z. participated in performing the evaluation methods of the security analysis. Project administration and supervision were by Q.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation of China, and grant number is 61471158.
Institutional Review Board Statement
Not applicable.
Data Availability Statement
All results and data obtained can be found in open access publications.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Dragoi, A.V.; Colutc, D. On local prediction based reversible watermarking. IEEE Trans. Image Process. 2015, 24, 1244–1246. [Google Scholar] [CrossRef]
- Lin, Y.T.; Wang, C.M.; Chen, W.S.; Lin, F.P.; Lin, W. A novel data hiding algorithm for high dynamical range images. IEEE Trans. Multimed. 2017, 19, 196–211. [Google Scholar] [CrossRef]
- Teh, J.S.; Alawida, M.; Sii, Y.C. Implementation and practical problems of chaos-based cryptography revisited. J. Inf. Secur. Appl. 2020, 50, 102421. [Google Scholar] [CrossRef]
- Belazi, A.; Abd El-Latif, A.A.; Diaconu, A.; Rhouma, R.; Belghith, S. Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt. Lasers Eng. 2017, 88, 37–50. [Google Scholar] [CrossRef]
- Wang, Y.; Wong, K.W.; Liao, X.; Xiang, T. A block cipher with dynamic S-boxes based on tent map. Commun. Nonlinear Sci. Numer. Simul. 2009, 14, 3089–3099. [Google Scholar] [CrossRef]
- Lu, X.; Xie, E.Y.; Li, C. Periodicity Analysis of the Logistic Map Over Ring . Int. J. Bifurc. Chaos 2023, 33, 5. [Google Scholar] [CrossRef]
- Yan, W.H.; Ding, Q. A new matrix projective synchronization and its application in secure communication. IEEE Access 2019, 7, 112977–112984. [Google Scholar] [CrossRef]
- Ma, Y.L.; Li, C.Q.; Ou, B. Cryptanalysis of an image block encryption algorithm based on chaotic maps. J. Inf. Secur. Appl. 2020, 50, 102566. [Google Scholar]
- Yan, W.; Dong, W.; Wang, P.; Wang, Y.; Xing, Y.; Ding, Q. Discrete-Time Memristor Model for Enhancing Chaotic Complexity and Application in Secure Communication. Entropy 2022, 24, 864. [Google Scholar] [CrossRef]
- Bao, B.; Rong, K.; Li, H.; Li, K.; Hua, Z.; Zhang, X. Memristor-coupled Logistic hyperchaotic map. IEEE Trans. Circuits Syst. II Exp. Briefs 2021, 68, 2992–2996. [Google Scholar] [CrossRef]
- Pak, C.; Huang, L. A new color image encryption using combination of the 1D chaotic map. Signal Process. 2017, 138, 129–137. [Google Scholar] [CrossRef]
- Zhou, Y.; Bao, L.; Chen, C. Image encryption using a new parametric switching chaotic system. Signal Process. 2013, 93, 3039–3052. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Huang, H. Cosine-transform-based chaotic system for image encryption. Inf. Sci. 2019, 480, 403–419. [Google Scholar] [CrossRef]
- Cao, W.J.; Mao, Y.J.; Zhou, Y.C. Designing a 2D infinite collapse map for image encryption. Signal Process. 2020, 17, 107457. [Google Scholar] [CrossRef]
- Wang, C.F.; Ding, Q. A Class of Quadratic Polynomial Chaotic Maps and Their Fixed Points Analysis. Entropy 2019, 21, 658. [Google Scholar] [CrossRef] [PubMed]
- Li, W.S.; Yan, W.H.; Zhang, R.X.; Ding, Q. A New 3D Discrete Hyperchaotic System and Its Application in Secure Transmission. Int. J. Bifurcat. Chaos 2019, 29, 1950206. [Google Scholar]
- Liu, C.Y.; Ding, Q. A color image encryption scheme based on a novel 3d chaotic mapping. Complexity 2020, 2020, 3837209. [Google Scholar] [CrossRef]
- Wang, C.F.; Ding, Q. Constructing Discrete Chaotic systems with Positive Lyapunov Exponents. Int. J. Bifurcat. Chaos. 2017, 29, 1950206. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Zhang, Y.X.; Zhou, Y.C. Two-dimensional parametric polynomial chaotic system. IEEE Trans. Cybern. 2022, 52, 4402–4414. [Google Scholar] [CrossRef]
- Hua, Z.Y.; Zhang, Y.X.; Zhou, Y.C. Two-dimensional modular chaotification system for improving chaos complexity. IEEE Trans. Singal Process. 2018, 68, 1937–1949. [Google Scholar] [CrossRef]
- Shen, C.W.; Yu, S.M.; Lu, J.H.; Chen, G.R. A systematic methodology for constructing hyperchaotic systems with multiple positive Lyapunov exponents and circuit implementation. IEEE Trans. Circuits Syst. I Reg. Papers 2014, 61, 854–864. [Google Scholar] [CrossRef]
- Chen, G.R.; Lai, D.J. Making a Dynamical System Chaotic: Feedback control of Lyapunov exponents for discrete-time dynamical systems. IEEE Trans. Circuits Syst. I Fund. Theory Appl. 1997, 44, 250–253. [Google Scholar] [CrossRef]
- Richman, J.; Moorman, J. Physiological time-series analysis using approximate entropy and sample entropy. Am. J. Physiol. Heart Circ. Physiol. 2000, 278, 2039–2049. [Google Scholar] [CrossRef] [PubMed]
- Chen, W.; Zhuang, J.; Yu, W.; Wang, Z. Measuring complexity using fuzzyen, apen, and sampen. Med. Eng. Phys. 2009, 31, 61–68. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurcat. Chaos 2006, 16, 2129–2151. [Google Scholar]
- Lu, L.; Li, Y.; Sun, A. Parameter identification and chaos synchronization for uncertain coupled map lattices. Nonlinear Dyn. 2013, 73, 2111–2117. [Google Scholar] [CrossRef]
- Alawida, M.; Samsudin, A.J.; Teh, S. A new hybrid digital chaotic system with applications in image encryption. Signal Process. 2019, 160, 45–58. [Google Scholar]
- Hua, Z.Y.; Zhou, Y.C. Design of image cipher using block-based scrambling and image filtering. Inf. Sci. 2017, 396, 97–113. [Google Scholar] [CrossRef]
- Liu, X.; Tong, X.; Wang, Z.; Zhang, M. A novel hyperchaotic encryption algorithm for color image utilizing DNA dynamic encoding and self-adapting permutation. Multimed. Tools Appl. 2022, 81, 21779–21810. [Google Scholar] [CrossRef]
- Chai, X.; Fu, X.; Gan, Z.; Lu, Y.; Chen, Y. A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process. 2018, 155, 44–62. [Google Scholar] [CrossRef]
- Wang, X.; Guan, N.; Zhao, H.; Wang, S. A new image encryption scheme based on coupling map lattices with mixed multi-chaos. Sci. Rep. 2020, 10, 9784. [Google Scholar] [CrossRef] [PubMed]
- Huang, L.; Cai, S.; Xiong, X.; Xiao, M. On symmetric color image encryption system with permutation-diffusion simultaneous operation. Opt. Laser. Eng. 2019, 115, 7–20. [Google Scholar] [CrossRef]
- Wang, T.; Wang, M. Hyperchaotic image encryption algorithm based on bit-level permutation and DNA encoding. Opt. Laser. Technol. 2020, 132, 106355. [Google Scholar] [CrossRef]
- Zhou, N.R.; Tong, L.J.; Zou, W.P. Multi-image encryption scheme with quaternion discrete fractional Tchebyshev moment transform and cross-coupling operation. Signal Process. 2023, 211, 109107. [Google Scholar] [CrossRef]
- Huang, X.L.; Dong, Y.X.; Ye, G.D.; Shi, Y. Meaningful image encryption algorithm based on compressive sensing and integer wavelet transform. Front. Comput. Sci. 2023, 17, 173804. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).