Abstract
Fractional-order chaos has complex dynamic behavior characteristics, so its application in secure communication has attracted much attention. Compared with the design of fractional-order chaos-based cipher, there are fewer researches on security analysis. This paper conducts a comprehensive security analysis of a color image encryption algorithm using a fractional-order hyperchaotic system (CIEA-FOHS). Experimental simulation based on excellent numerical statistical results supported that CIEA-FOHS is cryptographically secure. Yet, from the perspective of cryptanalysis, this paper found that CIEA-FOHS can be broken by a chosen-plaintext attack method owing to its some inherent security defects. Firstly, the diffusion part can be eliminated by choosing some special images with all the same pixel values. Secondly, the permutation-only part can be deciphered by some chosen plain images and the corresponding cipher images. Finally, using the equivalent diffusion and permutation keys obtained in the previous two steps, the original plain image can be recovered from a target cipher image. Theoretical analysis and experimental simulations show that the attack method is both effective and efficient. To enhance the security, some suggestions for improvement are given. The reported results would help the designers of chaotic cryptography pay more attention to the gap of complex chaotic system and secure cryptosystem.
1. Introduction
Nowadays, with the rapid development of optical fiber broadband access network, 5G and other communication technologies, the security of multimedia data, especially digital images, is of particular interest in communication networks [1]. As everyone knows, encryption is an effective means of achieving security enhancements [2]. However, traditional text encryption algorithms such as AES, DES, and IDEA are not suitable for digital images because they featured with strong correlation between adjacent pixels. To deal with the problem, various methodologies are introduced to design different image ciphers. Among them, chaos-based image encryption is the most popular one, because chaos has characteristics of sensitivity to initial values, dense periodic points, and long-term unpredictability of orbits [3,4,5]. In the past two decades, chaotic image encryption technology has been widely discussed and has become a research hotspot [6]. To improve the security performance of chaotic image encryption technology, various chaotic systems with resistance to dynamic degradation are studied, including quantum chaotic map [7], fractional-order chaos [8], non-degenerated hyperchaos [9], economic chaotic map [10], and cascaded chaotic systems [11], etc. However, chaotic cryptography still lacks authoritative metrics, especially in terms of security. Accordingly, many reported chaotic encryption algorithms have been broken [12,13,14,15]. As shown in Table 1, some previous chaos-based ciphers are vulnerable upon various attack methods, including chosen-ciphertext attack [16], chosen-/known-plaintext attack [12], differential cryptanalysis [17], even cipher-only attack [18]. Therefore, research on security is extremely important and has received much attention [19,20,21,22,23,24,25,26,27,28,29,30,31,32,33].

Table 1.
Some chaos-based ciphers broken by various attack methods.
As described in Ref. [39], fractional-order chaotic systems have higher complexity and more optional key parameters and can be used as a competitive encryption scheme. Correspondingly, image encryption algorithms based on fractional-order chaotic systems have attracted the attention of researchers in recent years [35,40,41,42]. In 2013, Wang et al. [40] introduced a fractional-order chaos into image encryption for the first time, and gave some experiments to verify its performance. Since then, many image encryption schemes based on fractional-order chaotic systems have been proposed [35,41,42]. For example, in 2017, Zhang et al. [41] proposed a color image encryption scheme combing with fractional-order hyperchaotic system and DNA encoding. Yet, cryptanalysts have reported that some fractional-order chaotic image encryption algorithms have some fatal security issues. Exactly, Norouzi et al. [36] pointed out that the image cipher that using an improper fractional-order chaotic system was insecure, which was proposed in [35]. As far as we know, there are still few research studies concerning cryptanalysis on the ciphers based on fractional-order chaotic systems. Moreover, considering that each cryptosystem has its intrinsic characteristics, it is necessary and urgent to perform cryptanalysis on these existing ciphers.
In 2015, a color image encryption algorithm based on a fractional-order hyperchaotic system was proposed [42]. In color image encryption algorithm using a fractional-order hyperchaotic system (CIEA-FOHS), using the pseudo-random sequences generated by the fractional-order hyperchaotic system, RGB-inter permutation, RGB-intra permutation and pixel diffusion are successively performed to get cipher images from plain images. Meanwhile, the relevant pixel correlation, histogram and other experimental analysis are given to verify its security performance. However, from the perspective of cryptanalysis, we found some security defects as follows:
- The existence of an equivalent key. CIEA-FOHS encrypts the image using a pseudo-random sequence generated by fractional-order chaos. However, these sequences are not related to plaintext. Thus, these sequences can be considered as equivalent keys.
- Two-stage permutations can be equivalently simplified to only once. The reason is that the two permutations only change the position of the pixel without changing the value of the pixel.
- The paradigm of the diffusion part is insecure. According to the conclusion of Ref. [43], a class of diffusion encryption using module addition and XOR operations can be cracked with only two special plain images and their corresponding cipher images. Unfortunately, CIEA-FOHS is also the case.
Based on the three points, CIEA-FOHS cannot resist against a chosen-plaintext attack method with the divide-and-conquer strategy. More specifically, under the scenario of chosen-plaintext attack, firstly an equivalent diffusion key is obtained, and then an equivalent permutation key is achieved, and finally the original images can be restored from the encrypted images with the equivalent keys.
2. The Encryption Algorithm under Study
In this section, the fractional-order hyperchaotic system used in Reference [42] is presented, and then the specific steps of CIEA-FOHS are introduced.
2.1. Fractional-Order Hyperchaotic System
The fractional-order hyperchaotic system used in CIEA-FOHS is derived from Ref. [39], given as
where are the four state variables, , is the fractional derivative under the definition of Caputo and is the derivative order. The attractor of the fractional-order hyperchaotic system is shown in Figure 1.
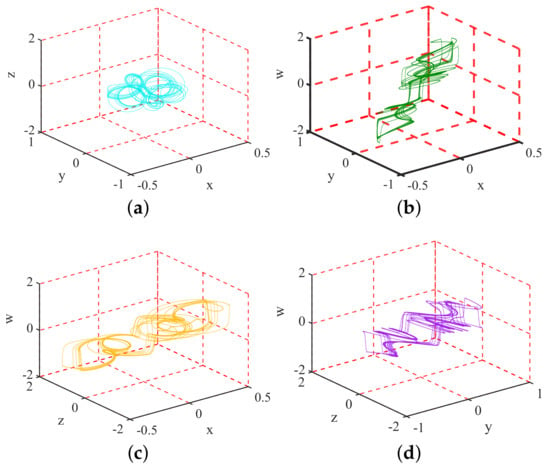
Figure 1.
Attractor phase diagrams of the fractional-order hyperchaotic system with different variables: (a) ; (b) ; (c) ; (d) .
2.2. Description of CIEA-FOHS
As shown in Figure 2, CIEA-FOHS consists of three main parts: inter-permutation, intra-permutation and pixel diffusion. It is noted that, a two-dimensional image is transformed into an one-dimensional sequence in raster scan order. Specifically, a color plain image of size is converted into three sequences of length expressed as: , , and , which correspond to the three RGB channels of the image. The main contents are briefly introduced as follows:
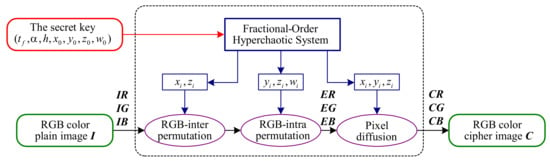
Figure 2.
The block diagram of CIEA-FOHS.
- The Secret Key:
The secret keys of CIEA-FOHS include , where is the fractional derivative defined by Caputo definition, is the dimension, h is the step size for discretization, and are the four initial values of the fractional-order hyperchaotic system defined in Equation (1), respectively. In CIEA-FOHS, these keys are used to generate some chaos-based pseudo-random sequences for encryption [42].
- Initialization:
In Equation (1), by selecting the secret key as the initial values and parameters and iterating L times, one gets four chaos-based pseudo-random sequences , , and , where represents the number of pixels in a single image channel.
- Stage 1. RGB-inter permutation:
The RGB-inter permutation refers to the process of pixel replacement between channels. This stage is implemented by two control vectors and , which are given as
where . More specifically, is used to switch channels, as shown in Table 2, and is to control the position and length of the permutation pixel, given as
where is the starting position, is the length of the permautation pixels, and is the cumulative function.

Table 2.
The stutas of RGB-inter permutation under six rules.
- Stage 2. RGB-intra permutation:
Sort , , and to get three index sequences , , and respectively, and their values range . Use , , and to permute , and respectively, given as , and .
- Stage 3. Pixel diffusion:
Perform pixel diffusion on , and , and then get three channels of the cipher image . Exactly, the three channels , and are defined as
where , ⊕ is bitwise XOR operation, represents modulo operation, and , , and . Here, three diffusion sequences , and are generated by , and respectively, where is a rounding operation on real numbers.
Decryption is the inverse of encryption and is not described in detail here.
3. Security Analysis of CIEA-FOHS
3.1. Preliminary Analysis of CIEA-FOHS
Referring to the basic assumptions of cryptanalysis, everything about the cryptosystem is public and only the secret key is unknown for attackers [13]. Chosen-plaintext attack is a common and powerful method of cryptanalysis. It assumes that attackers can arbitrarily choose the plaintext that is conducive to deciphering and obtain the corresponding ciphertext [12]. Under the scenario of chosen-plaintext attack, attackers can construct special plain images, such as all black and all white, and obtain the corresponding cipher images to analyze the target cipher.
From the perspective of cryptanalysis, two-stage permutations of CIEA-FOHS can be treated as a global pixel permutation because they only change the pixels’ position without their values. The difference is that the number of pixels performing the permutation is instead of . Then, the algorithm structure of CIEA-FOHS is actually a classic single-round permutation-diffusion. Moreover, the generation process of all chaos-based pseudo-random sequences is independent of the plain image, which means that these sequences can be regarded as an equivalent key. The reason is that, in the case of a given secret key, these sequences are fixed for encrypting different plain images with the same size. Then, CIEA-FOHS can be equivalently simplified as Figure 3, where is an equivalent permutation key and three diffusion sequences , and serve as an equivalent diffusion key.
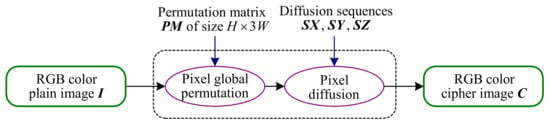
Figure 3.
The block diagram of an equivalent simplified CIEA-FOHS.
Based on the above, under the scenario of chosen-plaintext attack and the strategy of divide and conquer, one can get the equivalent keys and then recover the original plain images. Specifically, firstly choose some plain images with same pixel values to cancel the permutation and get the corresponding plain images to obtain the diffusion key; then achieve the permutation key by the method of Reference [12]; finally, recover the images by the equivalent keys.
3.2. Analysis on the Diffusion Part
In this section, based on chosen-plaintext attack, it is assumed that the plaintext image with the same pixel value is selected, and the corresponding ciphertext image is obtained.
- Step 1. Choose the all-zero plain image and get the corresponding cipher image to determine .
The reason for choosing the all-zero image is that the permutation is invalid at this time, and the diffusion can be eliminated to the greatest extent. Then, Equation (4) becomes
when , one has . Since , thus . Similarly, one further gets and .
- Step 2. Choose two special plain images and get the corresponding cipher images to determine for .
Referring to [43,44], the two chosen plaintexts are pure-color images with pixel values of 85 and 170, represented as and , respectively. Because for the combined operation of module addition and bitwise XOR, choosing these two plain images can minimize the number of solutions for , , . Under the plain image and its corresponding cipher image , one gets
Similarly, given the plain image and its corresponding cipher image , one has
By performing bitwise on Equations (6) and (7), one further gets
where is defined as . It is worth pointing out that the reason why 85 and 170 are chosen as the attack images is that their binary are 01010101 and 10101010 respectively. At this time, the number of possible solutions of is the smallest, which is two. More precisely, the difference between the two solutions is 128. Then, based on Equation (8), we propose Alogrithm 1 to determine , where .
| Algorithm 1: Determining for |
 |
- Step 3. Eliminate the diffusion part by , , .
Corresponding to Equation (4), the decryption process of diffusion is given as
Thus, , , can be restored from , , with , , , respectively.
3.3. Analysis on the Permutation Part
Once the diffusion part is broken, CIEA-FOHS degenerates into a permutation-only cipher. Based on existing research, it cannot resist a chosen-plaintext attack. The basic idea of attacking permutation-only is to construct a special plain image with unequal element values, and get the corresponding permuted image. Taking as an example, the process of solving is described below. First, a chosen plain image and the corresponding permuted image are given as
For ease of explanation, a matrix of size is obtained by connecting three channels of size in a row connection manner. Then, the permutation process can be described by
where is the permutation matrix of size . Finally, is determined as
Obviously, one can recover from with . However, the situation may be more complicated for large size images. For an 8-bit image, the pixel value range is . Thus, when , cannot be determined by only one chosen plain image and its corresponding cipher image. Fortunately, this problem has been solved in our latest research [12,13]. The basic idea is to combine multiple chosen plain images in a weighted manner to form a matrix with different elements, and the number of chosen plain images required for attacking permutation is , where is the rounding up operation.
Based on the above, the steps for attacking permutation are briefly summarized as follows:
- Step 1. Choose some special plain images and get their corresponding cipher images to determine the permutation matrix ;
- Step 2. Use the permutation matrix to recover the original images from the permuted images.
3.4. The Proposed Chosen-Plaintext Attack Method
Following the above-mentioned discussion, CIEA-FOHS cannot resist the attack method proposed in this paper. The flowchart of the attack method is shown in Figure 4, and the specific steps based on chosen-plaintext attack are given as: firstly, get an equivalent diffusion key by the method in Section 3.2; secondly, achieve the permutation matrix by the method in Section 3.3; finally, recover the original images with the equivalent keys.
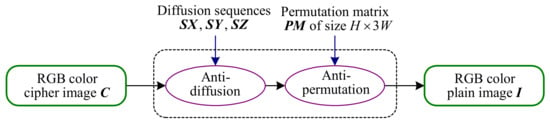
Figure 4.
The overall flowchart of attacking CIEA-FOHS.
Moreover, the complexity required for the attack method is discussed here. In terms of data complexity, for color images of size , the number of chosen plain images required to decipher diffusion and permutation is 3 and , respectively. Hence, the total data complexity required is .
4. Experimental Verifications and Discussions
To verify our security analysis, the algorithm steps of CIEA-FOHS strictly follow Ref. [42]. Although Due to the complexity of fractional-order chaos, some parameters may not be completely consistent, but this does not affect the effectiveness of security analysis. We conduct simulation verification on the proposed image cryptosystem based on a PC (personal computer) with MATLAB r2018b. The running PC is installed with Windows 10 64-bit OS (operating system), Intel(R) Core(TM) i5-8265U CPU @ 1.60 GHz and 8 GB memory. We select some typical images listed in Table 3 for experiments. Among them, the image “Lenna” of size given in Ref. [42] is also included. In Equation (1), we set the experimental secret key parameters for h = 0.001, = 104, = 100, = 1.002, = 0.949, = 0.997 and = 1.103.

Table 3.
The time required for breaking CIEA-FOHS by our proposed attack method (unit: second).
- Case 1. Breaking CIEA-FOHS with an image of size :
In order to better illustrate the attack process, we first adopt an extremely simple image with a size of 2 × 2 × 3. A pair of the given target plain and cipher images and is shown in Figure 5a,c respectively, and their histograms are shown in Figure 5b,d respectively. Accordingly, the numerical matrices of and are:
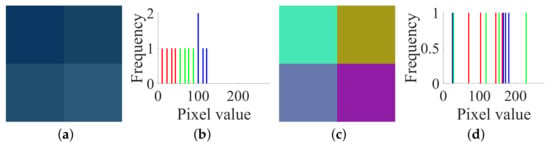
Figure 5.
A pair of plain and cipher images of size : (a) plain image ; (b) histogram of ; (c) cipher image ; (d) histogram of .
Firstly, following Step 1 in Section 3.2, choose the all-zero plain image shown in Figure 6a and temporarily use the encryption machine of CIEA-FOHS, and then get the corresponding cipher image , as shown in Figure 6c. The all-zero plain image and the corresponding cipher image and their histograms are shown in Figure 6b,d, respectively. Similarly, the numerical matrices of and are:
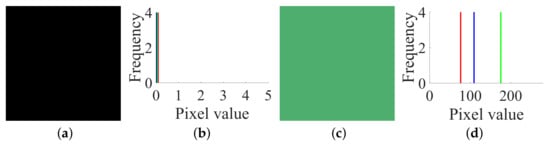
Figure 6.
The all-zero chosen plain image and its corresponding cipher image of size : (a) ; (b) histogram of ; (c) ; (d) histogram of .
Then, one has , and because , and , where .
Secondly, based on Step 2 in Section 3.2, choose the two plain images and , and get the corresponding cipher images, and , which are shown in Figure 7a–d, respectively. The values of their RGB three channels are:
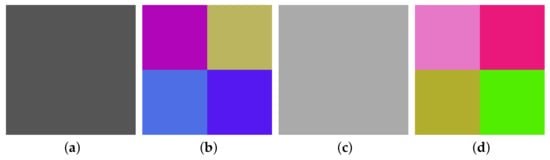
Figure 7.
The two chosen plain images , and their corresponding cipher images , of size : (a) ; (b) ; (c) ; (d) .
Then, combining Algorithm 1, we determine as
or
Thirdly, by Step 3 in Section 3.2, the corresponding permuted image shown in Figure 8c can be restored from the targeted cipher image Figure 8a with . Fourthly, following Step 1 in Section 3.3, construct some special attack images to obtain the permutation matrix . For images of size , the process of solving is exactly the same as Section 3.3. Then, we determine the as Equation (10). Fifth, by Step 2 in Section 3.3, recover from with . Thus, the original plain image shown in Figure 8e can be recovered.
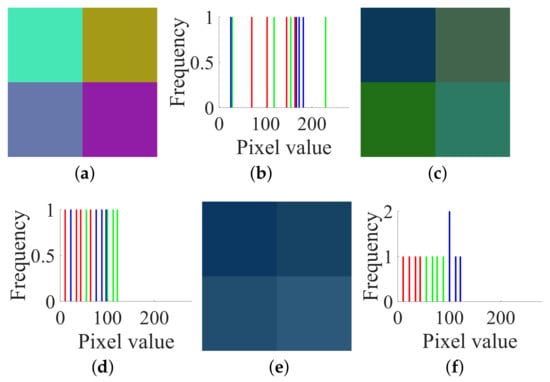
Figure 8.
A target cipher image, the permuted image, the original plain image and their histograms of size : (a) a target cipher image; (b) histogram of (a); (c) its permuted image; (d) histogram of (c); (e) its plain image; (f) histogram of (e).
- Case 2. Breaking CIEA-FOHS with “Lenna” of size :
Firstly, following Step 1 in Section 3.2, choose the all-zero plain image shown in Figure 9a and temporarily use the encryption machine of CIEA-FOHS, and then get the corresponding cipher image , as shown in Figure 9b, and the corresponding three channel images and their histograms of are shown in Figure 9c,d, respectively. Exactly, one has , and owing to , and .
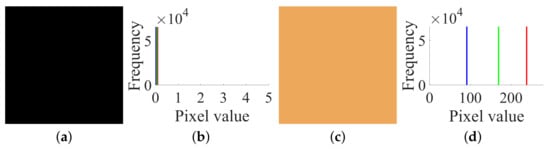
Figure 9.
The all-zero chosen plain image and its corresponding cipher image of size : (a) ; (b) histogram of ; (c) ; (d) histogram of .
Secondly, based on Step 2 in Section 3.2, choose the two plain images, and , and get the corresponding cipher images, and , which are shown in Figure 10a–d, respectively.
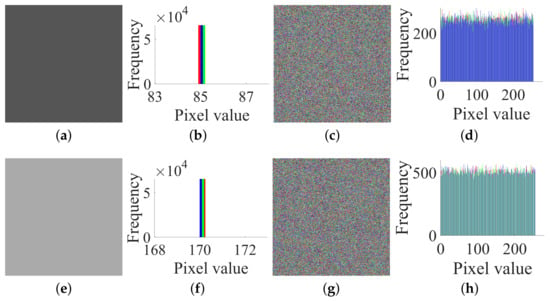
Figure 10.
The two chosen plain images , and their corresponding cipher images , of size : (a) ; (b) histogram of ; (c) ; (d) histogram of ; (e) ; (f) histogram of ; (g) ; (h) histogram of .
Furthermore, one determines for by Algorithm 1.
Thirdly, by the method in Section 3.3, choose the three plain images (shown in Figure 11a–f) and get the corresponding cipher images (shown in Figure 11g–l), and then use Algorithm 1 again to obtain their corresponding permuted images (shown in Figure 11m–r). Then, we can get .
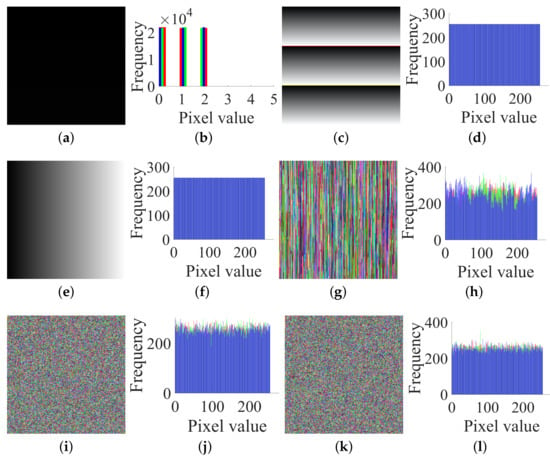
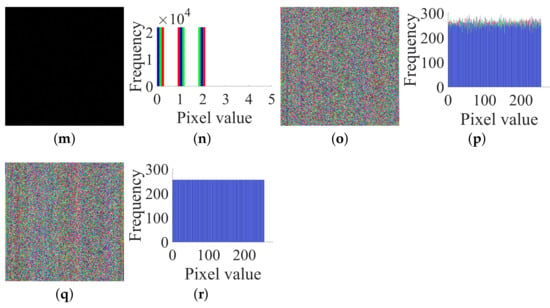
Figure 11.
Three chosen plain images, the corresponding cipher and permuted images for attacking permutation: (a) plain image; (b) The histogram of (a); (c) plain image; (d) The histogram of (c); (e) plain image; (f) The histogram of (e); (g) cipher image; (h) The histogram of (g); (i) cipher image; (j) The histogram of (i); (k) cipher image; (l) The histogram of (k); (m) permuted image; (n) The histogram of (m); (o) permuted image; (p) The histogram of (o); (q) permuted image; (r) The histogram of (q).
Finally, we recover the original image from the cipher image of “Lenna” shown in Figure 12a. First, the permuted image shown in Figure 12c is obtained from the cipher image with (, , ). Then, the plain image is restored by , which is shown in Figure 12e.
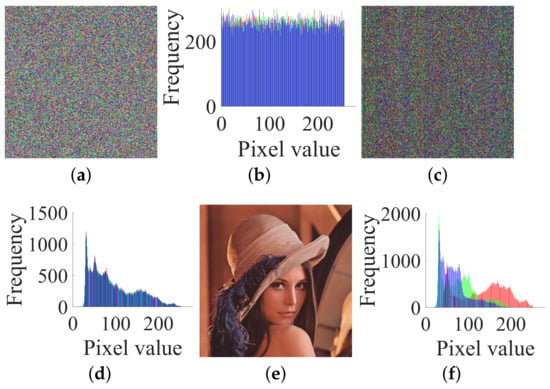
Figure 12.
The cipher image, the permuted image, the original plain image of “Lenna” and their histograms of size : (a) the cipher image; (b) histogram of (a); (c) its permuted image; (d) histogram of (c); (e) its plain image; (f) histogram of (e).
Without loss of generality, we do the experiments based on other images with different sizes. The experimental results are shown in Table 3 and Figure 13. They both verify the effectiveness of our attack method. Besides, it can be seen from Table 3 that the proposed attack is efficient. Taking the image “Lenna” of size as an example, when the encryption time is 0.6391 s, the time needed for the corresponding attack is just 129.4039 s. Even if the image size increases, the time required for the attack is still within an acceptable range. Thus, it verifies that our method is computationally feasible.
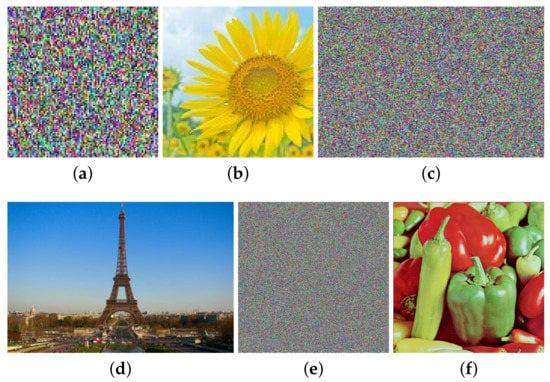
Figure 13.
Attacking results with three images of size , and respectively: (a) cipher image of size ; (b) plain image of (a); (c) cipher image of size ; (d) plain image of (c); (e) cipher image of size ; (f) plain image of (e).
Moreover, we verified the data complexity required for the attack. As discussed in Section 3.4, the total data complexity required for breaking CIEA-FOHS is . In our experiment with chosen-plaintext attack, the number of attack images required for sizes and are 4 and 5, respectively. And for sizes , and , the number of attack images required are all 6. Therefore, the experimental verification is consistent with the theoretical calculation.
5. Suggestions for Improvement
On the basis of the above, CIEA-FOHS is insecure against a chosen-plaintext attack method because of its inherent security defects. To enhance the security, some suggestions for improvement are listed below:
- Suggestion 1. Ensuring the substantial security contribution of the fractional-order chaos to the corresponding cipher. The attractor phase diagram of the fractional-order hyperchaotic system is shown in Figure 1, which shows the extremely complex dynamics. Undoubtedly, fractional-order chaos is one of the preferred sources of entropy for encryption. However, due to the negligence of algorithm design, CIEA-FOHS has serious security defects and is attacked.
- Suggestion 2. Security analysis should be implemented from the perspective of cryptography, not limited to numerical statistical verification. As Ref. [45] points out, many encryption algorithms have excellent statistical analysis results, but they are still insecure. In fact, good statistical analysis results are only a necessary and not a sufficient condition for security. Some security flaws are difficult to reflect with numerical statistical results, but they can be clearly revealed by theoretical security analysis. For example, the existence of an equivalent key makes CIEA-FOHS vulnerable to cryptographic attacks. Given the implementation of detailed cryptographic security analysis, these flaws can be avoided, thereby improving security.
6. Conclusions
In this paper, a detailed security analysis of a color image encryption algorithm named CIEA-FOHS using a fractional-order chaos was performed. From the perspective of cryptanalysis, this paper found that CIEA-FOHS can be broken by a chosen-plaintext attack method, owing to its some inherent security defects. Theoretical analysis and experimental simulations show that the attack method is both effective and efficient for attacking CIEA-FOHS. Although the fractional-order chaotic system has complex dynamics, the algorithm defects may cause insecurity. The reported results would help the designers of chaotic cryptography pay more attention to the gap between complex chaotic system and secure cryptosystem.
Author Contributions
Methodology, H.W.; Software, H.W. and J.K.; Validation, H.W., L.H. and C.Z.; Supervision, C.Z.; Project Administration, C.Z. and D.X.; Funding Acquisition, C.Z., H.W. and D.X. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported partly by the National Science Foundation of China (62071088, 61571092), Project for National Key RD Program of China (2018YFB1801302), Project for Innovation Team of Guangdong University (2018KCXTD033), Project for Zhongshan Social Public Welfare Science and Technology (2019B2007), Zhongshan Innovative Research Team Program (180809162197886), Research Project for Talent of UESTC Zhongshan Institute (418YKQN07, 419YKQN23), Natural Science Project for Young Innovative Talents by the Department of Education of Guangdong Province (2019KQNCX191), Characteristic Innovation Project of Department of Guangdong Province (2017GWTSCX010).
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wu, T.; Zhang, C.; Chen, C.; Hou, H.; Wei, H.; Hu, S.; Qiu, K. Security enhancement for OFDM-PON using Brownian motion and chaos in cell. Opt. Express 2018, 26, 22857–22865. [Google Scholar]
- Wu, T.; Zhang, C.; Chen, Y.; Cui, M.; Huang, H.; Zhang, Z.; Wen, H.; Zhao, X.; Qiu, K. Compressive sensing chaotic encryption algorithms for OFDM-PON data transmission. Opt. Express 2021, 29, 3669–3684. [Google Scholar]
- Wen, H.; Zhang, C.; Chen, P.; Chen, R.; Xu, J.; Liao, Y.; Liang, Z.; Shen, D.; Zhou, L.; Ke, J. A quantum chaotic image cryptosystem and its application in IoT secure communication. IEEE Access 2021, 1. [Google Scholar] [CrossRef]
- Li, C.; Feng, B.; Li, S.; Kurths, J.; Chen, G. Dynamic analysis of digital chaotic maps via state-mapping networks. IEEE Trans. Circuits Syst. I Regul. Pap. 2019, 66. [Google Scholar] [CrossRef]
- Li, C.; Tan, K.; Feng, B.; Lu, J. The Graph Structure of the Generalized Discrete Arnold’s Cat Map. IEEE Trans. Comput. 2021, 1. [Google Scholar] [CrossRef]
- Li, C.; Zhang, Y.; Xie, E.Y. When an attacker meets a cipher-image in 2018: A Year in Review. J. Inf. Secur. Appl. 2019, 48. [Google Scholar] [CrossRef]
- Akhshani, A.; Akhavan, A.; Mobaraki, A.; Lim, S.C.; Hassan, Z. Pseudo random number generator based on quantum chaotic map. Commun. Nonlinear Sci. Numer. Simul. 2014, 19, 101–111. [Google Scholar]
- He, S.; Sun, K.; Wang, H. Complexity analysis and DSP implementation of the fractional-order lorenz hyperchaotic system. Entropy 2015, 17, 8299–8311. [Google Scholar]
- Shen, C.; Yu, S.; Lü, J.; Chen, G. Designing Hyperchaotic Systems With Any Desired Number of Positive Lyapunov Exponents via A Simple Model. IEEE Trans. Circuits Syst. I Regul. Pap. 2014, 61, 2380–2389. [Google Scholar]
- Askar, S.S.; Karawia, A.; Al-Khedhairi, A.; Al-Ammar, F.S. An algorithm of image encryption using logistic and two-dimensional chaotic economic maps. Entropy 2019, 21, 44. [Google Scholar] [CrossRef]
- Zhou, Y.; Hua, Z.; Pun, C.; Philip Chen, C.L. Cascade Chaotic System with Applications. IEEE Trans. Cybern. 2015, 45, 2001–2012. [Google Scholar]
- Wen, H.; Yu, S. Cryptanalysis of an image encryption cryptosystem based on binary bit planes extraction and multiple chaotic maps. Eur. Phys. J. Plus 2019, 134, 1–16. [Google Scholar]
- Wen, H.; Yu, S.; Lü, J. Breaking an Image Encryption Algorithm Based on DNA Encoding and Spatiotemporal Chaos. Entropy 2019, 21, 246. [Google Scholar] [CrossRef]
- Shafique, A.; Shahid, J. Novel image encryption cryptosystem based on binary bit planes extraction and multiple chaotic maps. Eur. Phys. J. Plus 2018, 133, 331. [Google Scholar]
- Song, C.; Qiao, Y. A novel image encryption algorithm based on DNA encoding and spatiotemporal chaos. Entropy 2015, 17, 6954–6968. [Google Scholar]
- Xie, Y.; Li, C.; Yu, S.; Lü, J. On the cryptanalysis of Fridrich’s chaotic image encryption scheme. Signal Process. 2017, 132, 150–154. [Google Scholar]
- Chen, L.; Ma, B.; Zhao, X.; Wang, S. Differential cryptanalysis of a novel image encryption algorithm based on chaos and Line map. Nonlinear Dyn. 2016, 87, 1797–1807. [Google Scholar]
- Li, C.; Lin, D.; Lü, J. Cryptanalyzing an Image-Scrambling Encryption Algorithm of Pixel Bits. IEEE Multimed. 2017, 3, 64–71. [Google Scholar]
- Wang, L.; Sun, K.; Peng, Y.; He, S. Chaos and complexity in a fractional-order higher-dimensional multicavity chaotic map. Chaos Solitons Fractals 2020, 131, 109488. [Google Scholar]
- Peng, D.; Sun, K.; He, S.; Zhang, L.; Alamodi, A.O.A. Numerical analysis of a simplest fractional-order hyperchaotic system. Theor. Appl. Mech. Lett. 2019, 9, 220–228. [Google Scholar]
- He, S.; Sun, K.; Wang, H. Dynamics and synchronization of conformable fractional-order hyperchaotic systems using the Homotopy analysis method. Commun. Nonlinear Sci. Numer. Simul. 2019, 73, 146–164. [Google Scholar]
- Chai, X.; Bi, J.; Gan, Z.; Liu, X.; Zhang, Y.; Chen, Y. Color image compression and encryption scheme based on compressive sensing and double random encryption strategy. Signal Process. 2020, 176, 107684. [Google Scholar]
- Chai, X.; Wu, H.; Gan, Z.; Han, D.; Zhang, Y.; Chen, Y. An efficient approach for encrypting double color images into a visually meaningful cipher image using 2D compressive sensing. Inf. Sci. 2020. [Google Scholar] [CrossRef]
- Wang, X.; Chen, S.; Zhang, Y. A chaotic image encryption algorithm based on random dynamic mixing. Opt. Laser Technol. 2021, 138, 106837. [Google Scholar]
- Hua, Z.; Zhu, Z.; Yi, S.; Zhang, Z.; Huang, H. Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Inf. Sci. 2021, 546, 1063–1083. [Google Scholar]
- Kamal, F.M.; Elsonbaty, A.; Elsaid, A. A novel fractional nonautonomous chaotic circuit model and its application to image encryption. Chaos Solitons Fractals 2021, 144, 110686. [Google Scholar]
- Mani, P.; Rajan, R.; Shanmugam, L.; Joo, Y.H. Adaptive control for fractional order induced chaotic fuzzy cellular neural networks and its application to image encryption. Inf. Sci. 2019, 491, 74–89. [Google Scholar]
- Yang, F.; Mou, J.; Liu, J.; Ma, C.; Yan, H. Characteristic analysis of the fractional-order hyperchaotic complex system and its image encryption application. Signal Process. 2020, 169, 107373. [Google Scholar]
- Lahdir, M.; Hamiche, H.; Kassim, S.; Tahanout, M.; Kemih, K.; Addouche, S. A novel robust compression-encryption of images based on SPIHT coding and fractional-order discrete-time chaotic system. Opt. Laser Technol. 2019, 109, 534–546. [Google Scholar]
- Yang, F.; Mou, J.; Ma, C.; Cao, Y. Dynamic analysis of an improper fractional-order laser chaotic system and its image encryption application. Opt. Lasers Eng. 2020, 129, 106031. [Google Scholar]
- Yu, S.; Zhou, N.; Gong, L.; Nie, Z. Optical image encryption algorithm based on phase-truncated short-time fractional Fourier transform and hyper-chaotic system. Opt. Lasers Eng. 2020, 124, 105816. [Google Scholar]
- Sayed, W.S.; Radwan, A.G. Generalized switched synchronization and dependent image encryption using dynamically rotating fractional-order chaotic systems. AEU–Int. J. Electron. Commun. 2020, 123, 153268. [Google Scholar]
- Yang, Y.; Guan, B.; Li, J.; Li, D.; Zhou, Y.; Shi, W. Image compression-encryption scheme based on fractional order hyper-chaotic systems combined with 2D compressed sensing and DNA encoding. Opt. Laser Technol. 2019, 119, 105661. [Google Scholar]
- Fridrich, J. Symmetric Ciphers Based On Two-Dimensional Chaotic Maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar]
- Zhao, J.; Wang, S.; Chang, Y.; Li, X. A novel image encryption scheme based on an improper fractional-order chaotic system. Nonlinear Dyn. 2015, 80, 1721–1729. [Google Scholar]
- Norouzi, B.; Mirzakuchaki, S. Breaking a novel image encryption scheme based on an improper fractional order chaotic system. Multimed. Tools Appl. 2017, 76, 1817–1826. [Google Scholar]
- Ye, G. Image scrambling encryption algorithm of pixel bit based on chaos map. Pattern Recognit. Lett. 2010, 31, 347–354. [Google Scholar]
- Zhou, G.; Zhang, D.; Liu, Y.; Yuan, Y.; Liu, Q. A novel image encryption algorithm based on chaos and Line map. Neurocomputing 2015, 169, 150–157. [Google Scholar]
- Huang, X.; Zhao, Z.; Wang, Z.; Li, Y. Chaos and hyperchaos in fractional-order cellular neural networks. Neurocomputing 2012, 94, 13–21. [Google Scholar]
- Wang, Z.; Huang, X.; Li, Y.; Song, X. Image encryption based on a delayed fractional-order chaotic logistic system. Chin. Phys. B 2013, 22, 010504. [Google Scholar]
- Zhang, L.; Sun, K.; Liu, W.; He, S. A novel color image encryption scheme using fractional-order hyperchaotic system and DNA sequence operations. Chin. Phys. B 2017, 26, 100504. [Google Scholar]
- Huang, X.; Sun, T.; Li, Y.; Liang, J. A Color Image Encryption Algorithm Based on a Fractional-Order Hyperchaotic System. Entropy 2015, 17, 28–38. [Google Scholar]
- Li, C.; Liu, Y.; Zhang, L.Y.; Chen, M.Z.Q. Breaking a chaotic image encryption algorithm based on modulo addition and XOR operation. Int. J. Bifurc. Chaos 2013, 23, 1350075. [Google Scholar]
- Zhang, L.Y.; Liu, Y.; Pareschi, F.; Zhang, Y.; Wong, K.; Rovatti, R.; Setti, G. On the Security of a Class of Diffusion Mechanisms for Image Encryption. IEEE Trans. Cybern. 2018, 48, 1163–1175. [Google Scholar]
- Preishuber, M.; Hütter, S.K.T.; Uhl, A. Depreciating Motivation and Empirical Security Analysis of Chaos-Based Image and Video Encryption. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2137–2150. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).