Abstract
This paper focuses on K-receiver discrete-time memoryless broadcast channels (DM-BCs) with private messages, where the transmitter wishes to convey K private messages to K receivers. A general inner bound on the capacity region is proposed based on an exhaustive message splitting and a K-level modified Marton’s coding. The key idea is to split every message into submessages each corresponding to a set of users who are assigned to recover them, and then send these submessages via codewords chosen from a K-level structure codebooks. To guarantee the joint typicality among all transmitted codewords, a sufficient condition on the subcodebooks’ sizes is derived through a newly establishing hierarchical covering lemma, which extends the 2-level multivariate covering lemma to the K-level case with more intricate dependences. As the number of auxiliary random variables and rate conditions both increase exponentially with K, the standard Fourier–Motzkin elimination procedure becomes infeasible when K is large. To tackle this problem, we obtain a closed form of achievable rate region with a special observation of disjoint unions of sets that constitute the power set of . The proposed achievable rate region allows arbitrary input probability mass functions and improves over previously known achievable (closed form) rate regions for K-receiver () BCs.
1. Introduction
The 2-receiver discrete-time memoryless broadcast channel (DM-BCs) was first introduced by Cover [1], who proposed the prestigious superposition coding that outperforms the traditional time-division strategy. Superposition coding is optimal for certain classes of BCs such as degraded DM-BCs, less noisy DM-BCs, and more capable DM-BCs [2,3]. The best known inner bound on the capacity region of DM-BCs is achieved by Marton’s coding with message splitting [4,5]. The key idea is to split each source message into common and private parts, where the common part is encoded into a cloud-center codeword, and two private parts are encoded into two separate codewords. To enlarge the achievable rate region, the submitted codewords are jointly typical which is guaranteed by a sufficient condition on the sizes of subcodebooks established by the covering lemma [2].
Recently, Gohari [6] improved the outer bounds for two-receiver broadcast channel by introducing an auxiliary receiver to derive the form of the bounds. He also improved Marton’s inner bounds on the cardinalities of the auxiliary variables [7]. For a non-asymptotic view, there are also improvements on the maximum coding rate based on a non-asymptotic converse and achievability bounds with feedback [8] on a two-user broadcast channel and also those bounds on the same coding rate of the common-message K-user DM-BC [9] which extends and strengthen the ones in [10].
There have been efforts on general capacity region without common broadcasting on Gaussian MIMO BCs [11] which coincides with dirty-paper coding (DPC) rate region. The capacity regions of physically degraded Gaussian BCs were further studied for the ergodic or composite situations [12,13,14]. However, the capacity region with a general message set for multi-antenna Gaussian broadcast channels is not known to full extent [15,16,17,18].
For the K-receiver () DM-BCs, most previous works are based either on superposition coding (see in [19,20,21]) which requires certain constraints on Markov chains for auxiliary random variables (RVs), or on the 2-level Marton’s coding where each message is split into one common part and one private part [2,22]. The capacity region of broadcast channels of three receivers was studied with degraded message sets [23,24]. The capacity region of less-noisy broadcast channels with three receivers was determined [25], and superposition coding was justified to be sub-optimal for the more capable 3-receiver broadcast channels [26]. For arbitrary K case, the authors of [21] gave a general inner bound based on superposition coding and rate-splitting using notions from order theory and lattices wherein each receiver decodes its intended message (common or private) along with the partial interference designated to it through rate-splitting. The Marton’s coding with 2-level superposition coding structure (consisting of one cloud-center codebook and K satellite codebooks) can be easily constructed and analyzed by the multivariate covering lemma and packing lemma [2]. In [27], an evolved Marton’s coding scheme based on up-set [28] rate-splitting, superposition coding, and binning was introduced. However, this work failed to to derive a close-form achievable rate region due to the prohibitive complexity of applying the Fourier-Motzkin elimination procedure.
In this paper, we consider the general K-receiver () DM-BCs with private messages. For the case , in order to inherit the characteristics of superposition coding and combine them with Marton’s coding, a general inner bound is proposed based on the exhaustive message splitting and a K-level modified Marton’s coding. More specifically, every message is split into submessages, with each corresponding to a set belonging to the power set of . The submessages respecting to are encoded into an exclusive codeword and will be decoded by receiver j if . We enlarge the subcodebooks sizes and use a K-level Marton’s coding to send all codewords that are jointly typical with each other. This allows arbitrary dependence among the input RVs, rather than satisfying certain Markov chains as in [19,20,21,22]. Based on a newly established hierarchical covering lemma and properties of rate inequalities obtained in the scheme analysis, we obtain a closed-form achievable rate region. To the best of our knowledge, this is the first result of closed-form achievable rate region for general K-receiver DM-BCs allowing arbitrary input probability mass functions (pmfs). The proposed achievable rate region improves over all previously known closed-form achievable rate regions for K-receiver () BCs.
Note that there are mainly two challenges on establishing the closed-form achievable rate region. The first one is how to derive rate conditions such that all transmitted codewords are jointly typical. The solution is related to the covering lemma. Unfortunately, the known multivariate covering lemma in [2] only deals with sequences which are conditionally independent, making it infeasible in our scheme since our inner bound allows arbitrary input pmfs. Additionally, the recursive mutual covering lemma in [27] imposes too many intertwined rate constraints, making it prohibitive to apply the Fourier–Motzkin elimination. To overcome these obstacles, we divide all RVs into K levels and process them hierarchically, leading to a new lemma called hierarchical covering lemma. With this lemma, we can keep joint typicality among all selected sequences, while reducing the number of rate conditions compared to the recursive covering lemma in [27]. The second challenge lies on how to apply Fourier–Motzkin elimination procedure to obtain the final form of the inner bound. Even with the newly hierarchical covering lemma, the number of rate conditions incurred by the packing lemma still increases exponentially with K. To tackle this problem, we aggregate the rate of submessages based on special observations of disjoint unions of sets that constitute the power set of , and finally establish the final form of achievable rate region.
Notations
Throughout the paper, we use the notation in [2]. In particular, we let
for a positive integer K. We use to denote the power set of , e.g., when , .
For any non-empty set , where for , denote as the set including all permutations on , i.e., . We use ⨆ to denote the disjoint union, e.g., means with .
Given a set with , the subtuple of RVs with indices from is denoted by , and the corresponding realizations by . Let represent . For positive integers k and j, we define , and .
We use to denote a function of that tends to zero as . When there are multiple functions , we denote them all by a generic function with the understanding that .
2. Channel Model
Consider a K-receiver DM-BC with only private messages depicted in Figure 1. The setup is characterized by a input alphabet , K output alphabets , and a collection of channel transition pmfs . At time , the transmitter sends the channel input , receiver observes the output .
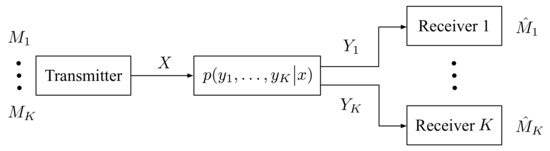
Figure 1.
Broadcast channel for K receivers.
The goal of the communication is that the transmitter conveys private messages to receiver k, for , respectively. Each is independently and uniformly distributed over the set , where denotes the communication rate of receiver k.
The encoder maps the messages to a sequence :
and receiver uses channel outputs to estimate as a guess of messages :
A rate tuple is called achievable if there exists an encoding function and K decoding functions such that the error probability
tends to zero as the block length n tends to infinity. The closure of the set of achievable rate tuple is called the capacity region.
3. Preliminary
Given a set , an element and l, with , define
where represents all subsets belonging to , containing and with cardinality between l and . For simplicity, we omit the , and in if , or , i.e.,
Given a set , write its permutation as , where denotes the i-th element in (i.e., ), and , if for all . Let represent all subsets belonging to and containing with cardinality between l and , i.e.,
In particular, when , we have
Similarly, we omit the if , i.e., It is easy to show that are disjoint sets for any and any subset .
Next, we introduce the following lemma on decomposition among sets.
Lemma 1.
The following decomposition holds:
Proof.
For example, consider the case , and , we have
Figure 2 is given for illustration. To simplify the notation, an arbitrary collection of sets, e.g., , is recognized as
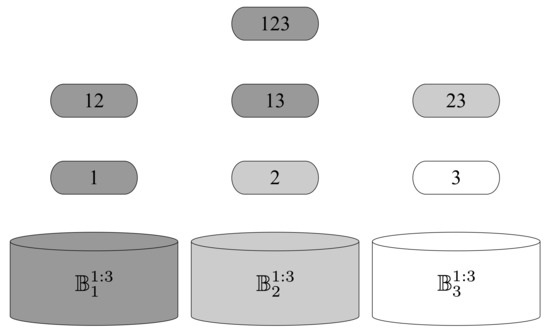
Figure 2.
The illustration of the disjoint decomposition of in the case for , and . The idea is that every time we pick a collection of sets descended from a set in the layer l, the number of unpicked sets in layer is one, where layer l contains all subsets of with cardinality l. Therefore, .
4. Main Results
Theorem 1.
Using the notations presented in Section 3, a rate tuple is achievable for the DM-BC if for all and permutations ,
for some pmf and a function .
Proof.
The achievable scheme is based on an exhaustive message splitting and a K-level Marton’s coding. More specifically, each message , for , is split into submessages with if . The submessages are encoded into a codeword and will be decoded by receiver j if . Then, a K-level Marton’s coding is applied to send codewords that are jointly typical with each other. See detailed scheme in Section 5. □
To ensure arbitrary input pmfs in the inner bound above, we need to establish a sufficient condition on the sizes of subcodebooks, which is related to the covering lemma. The multivariate covering lemma in [2] only consider sequences generated under simple dependence, e.g., given a sequence . In our scheme there are RVs, represented by , and each symbol of codeword is generated conditionally independent according to . In [27], a recursive mutual covering Lemma was introduced, which allows all transmitted codewords to be jointly typical. However, the recursive mutual covering lemma creates around intertwined rate equalities, turning the Fourier–Motzkin elimination procedure to a disastrous problem. To obtain the closed-form achievable rate region, we divide subcodebooks into K levels and process them recursively in a hierarchical manner, which greatly reduces the number of rate inequalities and enables to obtain the closed-form rate region.
Lemma 2
(Hierarchical Covering Lemma). Let and . Let be a random sequence with . For each and , let , , be pairwise conditionally independent sequences, each distributed according to . Assume that are mutually conditionally independent given . Then, there exists that tends to zero as 0 such that
if
for all and .
Proof.
See the proof in Appendix A. □
Remark 1.
The main difference between recursive mutual covering lemma [27] is that our hierarchical covering lemma reduces the number of variables (this is achieved by assuring the typicality of the codewords top-down from level K to level 1 in the proof of hierarchical covering lemma) in almost each inequalities compared with those in [27], which makes it easier for Fourier-Motzkin elimination to derive a closed-form achievable rate region. However, The accurate performance needs to be justified on specific channels, which also requires an optimal choice of the distribution of the auxiliary variables. Thus, it is hard to evaluate the overall performance, and we leave it in our future work.
To briefly investigate the performance of the two covering lemmas, we give an example of the bound on of each.
Utilizing our lemma, we get three inequalities to combine it. Namely,
By adding them all together, we get .
On the other hand, the bound on it by recursive mutual covering lemma is , namely , which leads to a lower upper bound (by conditioning reduces entropy) compared with ours, and our scheme may sacrifice some performance to derive a closed-form achievable rate tuple constraints.
Lemma 3.
Consider the inequality condition in the hierarchical covering lemma:
If the set is split into disjoint pieces satisfying
then for all , we have
With simple justification, the sum of lower bounds for is not greater than the lower bound for , which means combinations of split inequalities will not induce a smaller region bounded by the overall inequalities that simultaneously restrain all variables,
Proof.
It is equivalent to prove that
where (a) follows by the chain rule of entropy and (12); (b) holds because conditioning reduces entropy. □
Corollary 1.
Define
and
A rate region is achievable for 3-receiver DM-BC if
for some pmf and a function .
Proof.
The result directly comes from Theorem 1 with . For example, for and , in (10), then we have , , and,
which satisfy the decomposition . With and , we obtain upper bound for in (13d). The remaining rate constraints are acquired similarly. □
Remark 2
(Comparison with superposition coding and Marton’s coding). Our achievable region generalizes that introduced by standard Marton’s coding and superposition coding, i.e., both of them are special cases of our general-form intended coding. Furthermore, the rate region in Theorem 1 contains the regions resulted from the two aforementioned coding schemes.
- Our coding degenerates into Marton’s coding by setting , , which indicates our rate region contains that derived by Marton’s coding;
- As superposition coding is optimal for degraded/less noisy/more capable DM-BC, which is barely guaranteed in many cases, i.e., without knowing the concrete relation according to the Markov chain, our rate region contains that derived from superposition coding.
In the future work, we will evaluate our rate region for some specific DM-BCs to show that our coding scheme strictly improves previously known inner bounds.
5. Achievable Coding Scheme for Theorem 1
We first present our scheme for 3-receiver DM-BC as an illustration, and then extend it to general K-receiver DM-BC model for .
5.1. Coding Scheme for 3-Receiver DM-BCs
Let an all-one column vector with a specified dimension be denoted by 1. Albeit with an abuse of notation, we use a string of elements to implify the singleton notations in Section 3, e.g., , , , etc. To simplify notations, we denote by and its realization by .
5.1.1. Rate Splitting
Divide , , into four independent messages : . Therefore, . More precisely,
For convenience, let , , , , , , and , , , , , , .
5.1.2. Codebook Generation
Fix a pmf . Randomly and independently generate sequences each according to . For each generate a subcodebook consisting of independent generated sequences , , each according to . In the same way, for each and , generate subcodebooks and , respectively. For each , generate a subcodebook consisting of independent generated sequences , , each according to . For and , generate corresponding subcodebooks similarly.
5.1.3. Encoding
For each , , find an index tuple such that , and
If more than one such index tuple can be found, choose an arbitrary one among those. If no such tuple exists, just choose . Then, the transmitter generates as
5.1.4. Decoding
Decoder declares that is sent if it is the unique message such that
Similarly, receiver uses joint typicality decoding to find the unique message and , respectively.
5.1.5. Analysis of the Probability of Error
Assume without loss of generality that
is sent and let be the index tuple of selected sequences. We note that the subcodebook consists of i.i.d. sequences, . By the hierarchical covering lemma (with ), we obtain a set of constraints for
Again, using hierarchical covering lemma for , we attain the region for :
By the symmetry of decoders, we first consider the average probability of error for decoder 1. To analyze it, the Table 1 list all possible pmfs of message tuple .

Table 1.
Table of joint pmfs of all possible error messages. Symbol * denotes the message or index , and denote joint pmf .
By the conditional typicality lemma, the first term tends to zero as as and .
Considering the second term , note that is independent of for every , then the variables is independent of on condition of . By the packing lemma, tends to zero as if
Similarly, , , and tends to zero as if
For receiver 2 and 3, the corresponding inequalities can be derived in a similar way.
From the lower bound of linear combinations of and the upper bound of linear combinations of about receivers 1–3, eliminating , , , and by our elimination procedure yields the characterization (13a).
The procedure of the elimination for the case where K=3 is as follows, which is based on Lemma 3 that the sum of lower bounds for is not greater than the lower bound for and observation (21) and (22) that shows the properties of the bounds derived from packing lemma. The detailed explanation for the procedure is elaborated in Section 5.2.5.
To start with, and , as and , , , , , , . We can express as
where with composing order , can be expressed as . The additives in the brackets are components from corresponding inequalities resulted from packing lemma, namely,
which is remained to combine the lower and upper bounds of the corresponding combination to derive one upper bound as shown in Equations (13g)–(13i).
Then, for and , we can write as
which is equal to following the order , where can be ignored as they are non-negative. Applying the corresponding bounds again, we obtain one from the Equation (13d).
For and , by following the previous process we get Equation (13a). Thus, after consider and all permutations , we get all inequalities in Equations (13a)–(13i).
5.2. Coding Scheme for
For each , split message into submessages with and if . Similarly to case, we use the following notations:
and . To simplify notations, we denote by and its realization by .
5.2.1. Codebook Generation
Fix a pmf and function and let , . Randomly and independently generate sequences , each according to . For all , construct a subcodebook consisting of i.i.d. generated sequences , , each according to .
5.2.2. Encoding
We iteratively find all indices such that all selected codewords are jointly typical. In each round , given messages and sequences , find indices , such that all
If there is more than one such tuple, pick an arbitrary one among them. If no such tuple exists, pick . Then, generate with
for .
To send the message tuple , transmit .
5.2.3. Decoding
Let . Decoder k, , declares that is sent if it is the unique message such that
for some ∈.
5.2.4. Analysis of the Probability of Error
Assume without loss of generality that and let be the index tuple of the chosen sequences . Then, decoder i makes an error only if one or more of the following events occur:
Therefore, the probability of error for decoder i is upper bounded as
To bound , we utilize the hierarchical covering lemma in Lemma 2. Therefore, tends to zero as if
holds for all and .
To bound , by the conditional typicality lemma [2] it tends to zero as .
To bound , note that and are independent of , , as well as . Furthermore, if or for any subset , then by the conditional coding distribution we have for all . Thus, , by identifying , we obtain inequalities with the help of packing lemma: for all ,
5.2.5. Eliminating
Due to massive numbers of and , using standard Fourier–Motzkin elimination to obtain the achievable rate region is disastrous. We first present observations which help the elimination, and then find all valid constraints for for all .
Observation: Let , denote the right hand term of (19) by , and from (17), (19) can be rewritten as below.
(a) If there exists and such that
then
(b) If there exists and such that then
From the rate-splitting procedure, we have , for all . From (17), (20) and the observations (21) and (22), we can obtain that the valid constraints for will only have form , i.e., any rate constraint , for all can be derived from , for all . Note that this will not hold for DM-BCs with common message (there exists an original source message to be sent to all receivers).
Thus, in order to find rate constraints for , we must find all valid constraints for . By definitions in (17), we have
Now we show that how to obtain the closed-form rate region via set decomposition in (7) and the observations in Lemma 3, (21) and (22).
Consider a permutation . For easy reading, from the decomposition (7), we have
For , it must involve . Since is the largest set with every element containing , by observation in (21) and (22), we have the only valid rate constraint
to support , where the last equality holds by (6).
For , already contains , thus we need to find the rate constraints for . Since , and is second largest sets with every element containing and excluding , by observation in (21) and (22), we obtain the only effective rate constraints
to support +. Iteratively applying the similar steps above and by (23), we find all valid rate constraints under the permutation for :
where (a) hods by (20) and .
Thus, formally we have for all and :
where (a) comes from the disjoint decomposition in (7); (b) holds by letting in Lemma 2 and by Lemma 3.
6. Conclusions
In this paper, we propose new scheme for K-receiver DM-BCs with private messages based on exhaustive message splitting and K-level Marton’s coding. A hierarchical covering lemma is established which extends the 2-level multivariate covering lemma to K-level case. Our works provides a closed-form achievable rate region for the general K-user DM-BCs. In the future, we will find out some examples to justify that K-level Marton’s coding is strictly better than the 2-level one.
Author Contributions
R.T. investigates the related work, carries out the formal analysis, proposes the methodology, and writes the manuscript. Y.W. proposes the main idea, conceptualizes the problem, reviews and edits the manuscripts, and supervises the progess of the work. S.X. carries out the formal analysis, proposes the methodology, and writes some part of the manuscript. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by the National Nature Science Foundation of China (NSFC) under Grant 61901267.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors have no conflict of interest to disclose.
Appendix A. Proof of Hierarchical Covering Lemma 2
Let
Divide the messages and codewords into K levels, where at level , there are messages sets , and codewords
The proof of hierarchical covering lemma starts at level , finding a message tuple such that . Then, with a descending order of , we find a message tuple such that .
For each , we use to denote the element of for , i.e.,
We define, for all , the random events
where
Note that denotes the event that there isn’t any tuple of sequences from level l to K such that they are jointly typical. Correspondingly, denotes the event that there exists such tuple of sequences. denotes the set of messages at level l such that the corresponding codewords are jointly typical with a given tuple of jointly typical codewords from levels to K. denotes a condition that there exists message at level such that the corresponding codewords are jointly typical.
Our goal is to find rate conditions such that there exists a tuple of messages satisfying , which is equivalent to as .
The probability of can be upper bounded as
With recursively upper bounding , we obtain
where the last equality holds by definitions of and . As tends to zero as by the property of typicality, and K is a fixed channel parameter, in order to make tend to 0, it is sufficient to let tend 0 as for all .
To analyze (A2), tends to zero as by the condition of the lemma. Each term is equivalent to , which is upper bounded by a variation of Chebyshev inequality:
Using indicator random variables, can be written as
where
for each .
For all , define
From definition of and independence of codewords, we have . Therefore,
Next, we compute the upper bound of .
where (a) follows by properties of joint typicality and the mutually conditional independence property, i.e., given , and are conditionally independent. The lower bound of can be derived as
where the last equality holds by the properties of jointly typicality. From (A5) and (A6), we have
References
- Cover, T. Broadcast Channels. IEEE Trans. Inf. Theory 1972, 18, 2–14. [Google Scholar] [CrossRef] [Green Version]
- El Gamal, A.; Kim, Y.H. Network Information Theory; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Cover, T.M. Comments on Broadcast Channels. IEEE Trans. Inf. Theory 1998, 44, 2524–2530. [Google Scholar] [CrossRef] [Green Version]
- Marton, K. A Coding Theorem for the Discrete Memoryless Broadcast Channel. IEEE Trans. Inf. Theory 1979, 25, 306–311. [Google Scholar] [CrossRef]
- Korner, J.; Marton, K. General Broadcast Channels with Degraded Message Sets. IEEE Trans. Inf. Theory 1977, 23, 60–64. [Google Scholar] [CrossRef]
- Anantharam, V.; Gohari, A.; Nair, C. On the Evaluation of Marton’s Inner Bound for Two-Receiver Broadcast Channels. IEEE Trans. Inf. Theory 2019, 65, 1361–1371. [Google Scholar] [CrossRef]
- Gohari, A.; Nair, C. New Outer Bounds for the Two-Receiver Broadcast Channel. In Proceedings of the 2020 IEEE International Symposium on Information Theory (ISIT), Los Angeles, CA, USA, 21–26 June 2020; pp. 1492–1497. [Google Scholar]
- Trillingsgaard, K.F.; Yang, W.; Durisi, G.; Popovski, P. Common-Message Broadcast Channels With Feedback in the Nonasymptotic Regime: Full Feedback. IEEE Trans. Inf. Theory 2018, 64, 7719–7741. [Google Scholar] [CrossRef]
- Trillingsgaard, K.F.; Yang, W.; Durisi, G.; Popovski, P. Common-Message Broadcast Channels With Feedback in the Nonasymptotic Regime: Stop Feedback. IEEE Trans. Inf. Theory 2018, 64, 7686–7718. [Google Scholar] [CrossRef]
- Trillingsgaard, K.F.; Yang, W.; Durisi, G.; Popovski, P. Broadcasting a Common Message with Variable-Length Stop-Feedback Codes. In Proceedings of the 2015 IEEE International Symposium on Information Theory (ISIT), Hong Kong, China, 14–19 June 2015; pp. 2505–2509. [Google Scholar]
- Weingarten, H.; Steinberg, Y.; Shamai, S.S. The Capacity Region of the Gaussian Multiple-Input Multiple-Output Broadcast Channel. IEEE Trans. Inf. Theory 2006, 52, 3936–3964. [Google Scholar] [CrossRef]
- Tse, D.N. Optimal Power Allocation over Parallel Gaussian Broadcast Channels. In Proceedings of the IEEE International Symposium on Information Theory, Ulm, Germany, 29 June–4 July 1997; p. 27. [Google Scholar]
- Li, L.; Goldsmith, A.J. Capacity and Optimal Resource Allocation for Fading Broadcast Channels. I. Ergodic Capacity. IEEE Trans. Inf. Theory 2001, 47, 1083–1102. [Google Scholar]
- Li, L.; Goldsmith, A.J. Capacity and Optimal Resource Allocation for Fading Broadcast Channels. II. Outage Capacity. IEEE Trans. Inf. Theory 2001, 47, 1103–1127. [Google Scholar]
- Viswanath, P.; Tse, D.N.C. Sum Capacity of the Multiple Antenna Gaussian Broadcast Channel. In Proceedings of the IEEE International Symposium on Information Theory, Lausanne, Switzerland, 30 June–5 July 2002; p. 497. [Google Scholar]
- Yu, W.; Cioffi, J.M. Sum Capacity of Gaussian Vector Broadcast Channels. IEEE Trans. Inf. Theory 2004, 50, 1875–1892. [Google Scholar] [CrossRef]
- Vishwanath, S.; Jindal, N.; Goldsmith, A. Duality, Achievable Rates, and Sum-Rate Capacity of Gaussian MIMO Broadcast Channels. IEEE Trans. Inf. Theory 2003, 49, 2658–2668. [Google Scholar] [CrossRef] [Green Version]
- Caire, G.; Shamai, S. On the Achievable Throughput of a Multiantenna Gaussian Broadcast Channel. IEEE Trans. Inf. Theory 2003, 49, 1691–1706. [Google Scholar] [CrossRef]
- Salman, M.; Varanasi, M.K. Capacity Results via Message Merging and Superposition Coding in the K-Receiver Broadcast Channel with General Message Sets. In Proceedings of the 2019 IEEE International Symposium on Information Theory (ISIT), Paris, France, 7–12 July 2019; pp. 1642–1646. [Google Scholar]
- Romero, H.; Varanasi, M. Superposition Coding in the Combination Network. In Proceedings of the 2016 IEEE International Symposium on Information Theory (ISIT), Barcelona, Spain, 10–15 July 2016; pp. 2149–2153. [Google Scholar]
- Romero, H.P.; Varanasi, M.K. Rate Splitting and Superposition Coding for Concurrent Groupcasting over the Broadcast Channel: A General Framework. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 1888–1892. [Google Scholar]
- Ganguly, S.; Wang, L. Sliding-Window Gelfand–Pinsker Coding: General K-User Broadcast Channels. In Proceedings of the 2020 IEEE Information Theory Workshop (ITW), Riva del Garda, Italy, 11–15 April 2021; pp. 1–5. [Google Scholar]
- Nair, C.; Wang, Z.V. On 3-Receiver Broadcast Channels with 2-Degraded Message Sets. In Proceedings of the 2009 IEEE International Symposium on Information Theory, Seoul, Korea, 28 June–3 July 2009; pp. 1844–1848. [Google Scholar]
- Nair, C.; El Gamal, A. The Capacity Region of a Class of 3-Receiver Broadcast Channels with Degraded Message Sets. In Proceedings of the 2008 IEEE International Symposium on Information Theory, St. Petersburg, Russia, 31 July–5 August 2008; pp. 1706–1710. [Google Scholar]
- Nair, C.; Wang, Z.V. The Capacity Region of the Three Receiver Less Noisy Broadcast Channel. IEEE Trans. Inform. Theory 2011, 57, 4058–4062. [Google Scholar] [CrossRef]
- Nair, C.; Xia, L. On Three-Receiver More Capable Channels. In Proceedings of the 2012 IEEE International Symposium on Information Theory Proceedings, Cambridge, MA, USA, 1–6 July 2012; pp. 378–382. [Google Scholar]
- Romero, H.P. Fundamental Limits of Network Communication with General Message Sets: A Combinatorial Approach. Ph.D. Thesis, University of Colorado at Boulder, Boulder, CO, USA, 2014. [Google Scholar]
- Davey, B.A.; Priestley, H.A. Introduction to Lattices and Order; Cambridge University Press: Cambridge, UK, 2002. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).