Abstract
Dual receiver encryption (DRE), being originally conceived at CCS 2004 as a proof technique, enables a ciphertext to be decrypted to the same plaintext by two different but dual receivers and becomes popular recently due to itself useful application potentials such secure outsourcing, trusted third party supervising, client puzzling, etc. Identity-based DRE (IB-DRE) further combines the bilateral advantages/facilities of DRE and identity-based encryption (IBE). Most previous constructions of IB-DRE are based on bilinear pairings, and thus suffers from known quantum algorithmic attacks. It is interesting to build IB-DRE schemes based on the well-known post quantum platforms, such as lattices. At ACISP 2018, Zhang et al. gave the first lattice-based construction of IB-DRE, and the main part of the public parameter in this scheme consists of matrices where n is the bit-length of arbitrary identity. In this paper, by introducing an injective map and a homomorphic computation technique due to Yamada at EUROCRYPT 2016, we propose another lattice-based construction of IB-DRE in an even efficient manner: The main part of the public parameters consists only of matrices of the same dimensions, where is a flexible constant. The larger the p and n, the more observable of our proposal. Typically, when and according to the suggestion given by Peikert et al., the size of public parameters in our proposal is reduced to merely 12% of Zhang et al.’s method. In addition, to lighten the pressure of key generation center, we extend our lattice-based IB-DRE scheme to hierarchical scenario. Finally, both the IB-DRE scheme and the HIB-DRE scheme are proved to be indistinguishable against adaptively chosen identity and plaintext attacks (IND-ID-CPA).
1. Introduction
With the rapid development of the internet of things, more and more user tend to encrypt their data and then outsource their data to the cloud server. These outsourced data may contain some sensitive information such as financial, medical data, national security-related data, etc. Therefore, a reliable third party or government department is required to supervise these data, and if it is necessary, the regulator can decrypt the ciphertext and view the plaintext information of these data. Dual receiver encryption (DRE) [1] allows that a ciphertext can be decrypted to the same plaintext by two independent receivers. For the above scenario, DRE is a good handy tool. It not only guarantees the encrypted transmission and storage of data, but also enables data to be supervised by a reliable third party. In addition, DRE also can form a joint program with other cryptographic scheme. In [1], Diament et al. combined a DRE scheme with a signature scheme to achieve that a user can use a same public/secret key pair to complete the encryption and signature functions. In 2014, Chow et al. [2] proposed a DRE-PKE joint scheme and appended some stable properties to the DRE and made it more practical in the construction of plaintext-awareness public key encryption. Furthermore, DRE also can be used to construct a client puzzles mechanism based on decryption. Design client puzzles mechanism between the clients and severs can prevent servers from suffering from resource-depletion attacks. Diament et al. pointed out in [1] that the client puzzles mechanism can be applied to secure transport protocol, e.g., TLS. The DRE cryptographic primitive can be easily construct a deniable authentication system [3]. As a special kind of PKE, DRE also face the general certificate management problem. To solve the problem of certificate management in the traditional PKE, Zhang et al. [4] gave an identity-based variant version of DRE, named identity-based dual receiver encryption (IB-DRE). In this scheme, they constructed two IB-DRE schemes based on the identity-based encryption (IBE) scheme in [5].
However, all the above (IB)-DRE schemes are based on bilinear pairing groups. Since Shor [6] proposed a polynomial time quantum algorithm in 1997 which can solve discrete logarithm problem (DLP) and prime factorization. This type of bilinear pairing groups based schemes are not secure and can not resist the quantum attack. Since then, scholars have begun to study post-quantum cryptography (PQC). Lattices-based cryptography is a research hotspot for PQC. It has the following properties: high efficiency, simplicity, parallelization and average case/worst case equivalence property. In 1997, Ajtai and Dwork [7] first constructed a public key encryption scheme by using the problem on lattices. This scheme relies on the worst-case hardness of uSVP [8], and the key and ciphertext size is too large. Until 2005, Regev [9] presented another public key encryption scheme which security based on the learning with errors (LWE) problem. He proved that a LWE-based public key encryption can resist quantum attack. Then the researchers begin to study LWE-based public key encryption scheme. Based on LWE, many public key encryption schemes have been proposed, such as LWE-based IBE schemes [10,11,12,13,14], LWE-based attribute-based encryption schemes [15,16,17,18,19]. To our knowledge, the first lattice-based IB-DRE scheme was proposed in 2018 [20] (Next we use how Zhang18 denotes it). The public parameters size in this scheme consists of matrices which lead a high storage cost and communication cost. Additionally, when some users apply for their privacy key to the key generation center (KGC) at the same time, KGC may face great system pressure. Therefore, in order to reduce the storage cost, it is meaningful to construct a lattice-based IB-DRE with short public parameters and then extend it a hierarchical scenario to reduce the stress of KGC.
OUR CONTRIBUTION. In this paper, we firstly propose a new lattice-based construction of IB-DRE scheme which can resist quantum attack. By using a homomorphic computation technique and an injective map function, comparing to the first lattice-based IB-DRE [20], we reduce the public parameters size from matrices to matrices where n is the bit-length of arbitrary identity and is a flexible constant. By choosing appropriate p and n, the size can be reduced by almost at least 88% compared to Zhang18. In addition, considering the hierarchical scenario, we extend it to a hierarchical IB-DRE (HIB-DRE), which is not considered in Zhang18. A HIB-DRE can reduce the stress of the key generation center (KGC). The public parameters size of the HIB-DRE is also reduced from matrices to matrices where d is the maximum hierarchy depth. Finally, our lattice-based IB-DRE scheme and HIB-DRE scheme are proved to be indistinguishable against adaptively chosen identity and plaintext attacks (IND-ID-CPA) in the standard model. Additionally, to improve the encryption efficiency, our two schemes also can convert to a multi-bit encryption scheme by using the same method in [11].
2. Preliminarise
Notation. We use lowercase black italic alphabet for vectors, as in , uppercase black italic alphabet for matrices, as in . denotes a integer set . denotes an integer set of mod q residue class. is a n-dimension column vector. A matrix is denoted by where . denotes the -norm length of the longest column of . denotes the Gram–Schmidt orthogonalization of the vectors . We refer to as the Gram–Schmidt norm of .
2.1. Integer Lattice
Definition 1 (Lattices).
are n linearly independent vectors, and the lattice Λ generated by the following formula:
Note thatis a basis of Λ, n is the rank and m is the dimension.
Definition 2 (Integer lattices).
For prime, and, define:
2.2. Discrete Gaussians
Definition 3 (Discrete Gaussian).
For a positive integerand a vector, we defined a Gaussian distribution with centerand variance s as follow:
whereis a parameter, and.
Lemma 1
([10]). Let , with , be a basis for and . Then for and , we have:
- (1).
- .
- (2).
- There is a probabilistic polynomial-time (PPT) algorithm (,, σ,) that outputs a vectordrawn from a distribution statistically close to.
- (3).
- There is a PPT algorithm (,,,) that outputs a vectorsampled from a distribution statistically close to.
2.3. Related Algorithms
For any integer and q is a prime, there are PPT algorithms such that:
- (1).
- () ([21]): outputs a pair matrices and where is a basis for and for some .
- (2).
- (, , , , ) ([11]): given , , a basis for , and a Gaussian parameter , outputs a vector and the vector is not statistically distinguishable from where and .
- (3).
- (, , , , , ) ([11]): given , , , a basis for , and a Gaussian parameter where , outputs a vector and the vector is not statistically distinguishable from where and .Note that in our scheme, we let where and . Then taking as the input basis for the lattices .
Lemma 2
([22]). For any integer , there is a gadget matrix such that:
- The lattice has a known basis where .
- There is a PPT algorithm that takes input a vector and output a vector where and . Note that is a function, not a matrix.
2.4. Homomorphic Computation
The ideal of homomorphic trapdoor computation is introduced in [14].
Let p be a positive integer, it has a function : which inputs p matrices , ,⋯, and outputs a matrix.
Here is a deterministic function that has the following feature:
Lemma 3
([14]). Let and , for , it has . In addition, assume that , and , there exists algorithm that takeing as input and outputs a matrix such that and .
2.5. LWE Hardness Assumption
Definition 4.
Give a prime q, a positive integer n and a distribution over . A -LWE problem instance consists of access to an unspecified challenge oracle , being either a truly random sampler or a noisy pseudo-random sampler carrying some constant random secret key , whose behaviors are as follows, respectively:
: Outputs samples of the form , where is a uniformly distributed secret key, is a noise component from , and is uniform in .
: Outputs truly uniform random samples from .
The -LWE problem allows a number of queries to the challenge oracle . We say an algorithm decides a -LWE problem if is non-negligible for a random .
Theorem 1
([9]). If there exists an efficient, possibly quantum, algorithm for deciding the -LWE problem for then there is an efficient quantum algorithm for approximating the SIVP and GapSVP problems to within factors in the norm, in the worst case.
Lemma 4
([10]). Let be some vector in and let . Then the quality treated as an integer in satisfies:
with all but negligible probability in m.
As a special case, Lemma 4 shows that if is treated as an integer in satisfies
with all but negligible probability in m.
2.6. Three Basic Lemmas
Lemma 5
([11]). For a random matrix , there is a universal constant C such that:
Lemma 6
(Leftover Hash Lemma [11]). For and a prime . Let , and be uniformly random matrices. Then the distribution (, , ) is -close to the distribution (, , ).
Lemma 7
(Smudging out Lemma [14]). Let be a fixed vector and . is a uniformly random vector. Then the two distributions and are within statistical distance .
2.7. Definitions of (H)IB-DRE and Adaptive-ID Security Model
Identity-based dual receiver encryption (IB-DRE) enables a ciphertext to be decrypted to the same plaintext by two different receivers since it embeds two independent user’s identity in the encrypt phase. Considering the definition of IB-DRE in [20]. We give the following definition of IB-DRE. An IB-DRE scheme consists the following four algorithms.
- (1).
- )→ (): on input the security parameter . This algorithm outputs the public parameters and master secret key .
- (2).
- ): On input the public parameter , a user’s identity and the master secret key . This algorithm KeyGen outputs the secret key . In the scheme, we let , denote the first receiver and the second receiver respectively.
- (3).
- ): on input the public parameter , the user’s identities and the message bit . This algorithm outputs the ciphertext .
- (4).
- ): on input the public parameter , a user’s secret key , and the ciphertext . This algorithm outputs a message .
The definition of IB-DRE can be easily extended to a hierarchical IB-DRE by following the method in [11].
Correctness. For all identities , all message and the ciphertext ←), we have ppcpp.
The definition of adaptive-ID security model is adapted from [11]. It can be described by a IND-ID-CPA game between a challenger and an adversary as follows:
Setup. The challenger runs the ) algorithm to generate the public parameters and the master key , and send to .
Phase 1. The adversary makes secret key queries for different identities adaptively.
Challenge. The adversary sends a message bit and the target identities to , and the target identities should not be asked in Phase 1. The challenger randomly chooses and a randomly ciphertext space . If , it send the challenge ciphertext =Encrypt() to . If , it send a randomly challenge ciphertext to .
Phase 2. The adversary also makes secret key queries for different identities adaptively as Phase 1. It can not ask for .
Guess. The adversary outputs its guess and wins if . We define the advantage of the adversary in attacking IB-DRE scheme as .
3. Adaptively Secure IB-DRE Scheme with Short Public Parameters
As we all know, in the adaptively secure IBE scheme in [11], for an identity , the key generation matrix/encryption matrix is where is the matrices in the public parameters. Thus, if we want to construct an adaptively secure identity based dual receiver encryption (IB-DRE) scheme, the public parameters will be matrices which lead to high storage cost.
In this section, we propose an adaptively secure IB-DRE scheme with short public parameters. There are four algorithms in this scheme: . The main method to reduce the public parameters is that in the Setup phase we introduce an injective map function which can map a n-bits identity to a subset of , and here we let . Additionally, we also introduce a homomorphic computation technique to ensure that our scheme achieves a strong secure notion, i.e., indistinguishability of ciphertext under the adaptive chosen-identity chosen-plaintext attack (IND-ID-CPA). For the key generation matrix/encryption matrix, let , then . In the phase, we use the same SampleLeft algorithm in [11] to generated the two independent users’ secret keys but change the way is generated. is computed by a function : of the public parameters where function is a part of homomorphic computation technique. When encrypting a message bit, it should use two independent receivers’ public keys to encrypt the message. Then the ciphertext can be decrypted to the same message by the two independent receivers.
By doing this, we reduce the size of public parameters from (i.e., ) matrices to (i.e., ) matrices where p is a flexible constant and can affect the reduction cost. Next we will describe our scheme step by step.
3.1. Our Construction
The adaptively secure IB-DRE scheme with short public parameters consists the following four algorithms.
- (1).
- )→ (): on input the security parameter . This algorithm outputs the public parameters and master secret key , do:
- -
- Perform algorithm TrapGen to generate a uniformly matrix and a trapdoor .
- -
- For an identity , select an injective map that maps an identity to a subset of where .
- -
- For , select matrices .
- -
- Select a uniformly random matrices and a uniformly random vector .
The public parameter , the master secret key .Recall that by the function : , for the two identities , we have a deterministic function such that - (2).
- ): On input the public parameter , the user’s identity and the master secret key . This algorithm outputs the secret key , it works as follows:
- -
- It runs algorithm to generate such that where . Then it set .
- -
- For two independent receivers, we let and denote the first and second receiver’s secret key.
The two independent receivers’ secret keys are , . - (3).
- ): On input the public parameter , the user’s identities and the message bit . This algorithm outputs the ciphertext . it works as follows:
- -
- It firstly gets and as above.
- -
- Choose a randomly uniform vector , and error terms , , and , compute
The ciphertext is . - (4).
- ): On input the public parameter , a secret key and the ciphertext , do:
- -
- For , compute .
- -
- if . Otherwise .
- -
- Finally, it outputs the message .
3.2. Correctness
We firstly compute
Let where . Based on Lemma 1 and the formulas in Equations (1) and (2), the error term
To ensure the correctness of decryption and preform the security proof, we need that:
- -
- the error term is less than with overwhelming probability(w.h.p)(i.e., , and ),
- -
- the algorithm can operate (i.e., for some ),
- -
- the Leftover Hash Lemma can be applied to security proof (i.e., ),
- -
- the SampleLeft and SampleRight algorithm can operate (i.e., where ),
- -
- the Regev’s LWE reduction applies (i.e., ) and
- -
- the security reduction applies (i.e., i.e., ).
3.3. Security
Theorem 2.
If the -LWE assumption holds, the above IB-DRE scheme is IND-ID-CPA secure.
Proof.
Let be a probabilistic polynomial-time(PPT) adversary that can break our IB-DRE scheme with advantage . Then there exists a reduction that solves the -LWE problem with an negligible advantage. Let is the upper bound of the number of KeyGen queries and where are the challenge IDs and are the queried IDs. Different from in [11], here we let where . We show the security via the following games. In each game, we define a value and let denote the event that the adversary correctly guesses the challenge bit, i.e., the challenger outputs in . is the adversary’s advantage.
. This is the real IND-ID-CPA game between an adversary and the challenger. We have
. This game is as same as except we add an abort event at the end of the game. The challenger chooses randomly and . Let and . Let H and be two function where
For , the challenger checks whether the following formula holds:
If they do not hold, the game aborts, i.e., the challenger outputs a random . Otherwise, the challenger outputs . By Lemma 8, we have
Lemma 8
([11,14]). Let denotes the non-abort probability, and . denote the minimum and maximum probability of , respectively. Then we have .
Proof of Lemma 8
For -tuple identities, the non-abort probability . As we know, the non-abort probability is taken over and which are chose in . For any and , we can find a such that and are
We have . Therefore, the upper bound of non-abort probability is
Next we give the lower bound of non-abort probability .
Then we calculate the lower bound of and , respectively.
The last equation follows the fact that since , so we have . Then the probability of
Since and is an injective function, then , the equation can be seen as a polynomial with degree p. Since , the probability of
By the same method, we can get . Finally, the non-abort probability
Then we have , . Finally,
The last inequality due to that . ☐
. In this game, we change the way and are generated. The challenger firstly chooses , as and then chooses three matrices . Compute
Based on Lemma 6, the distribution (, , , ) is -close to the distribution (, , , ). Therefore, we have
Before the next game, for any , we make a definition as follow. Let
Based on Lemma 3, we have
is the same as .
. In this game, we show that when we change the ciphertext is generated, the distributions and are within statistical distance where . The challenge ciphertext is generated as follows: the challenger firstly chooses , , , and computes , . The challenge ciphertext
is the message chosen by .
Since , by the formula in Equation (18) we have
By Lemma 7, let be a fixed vector, the distributions and are within statistical distance .
. In this game, we change the way is generated. The challenger chooses a random matrix instead of using the TrapGen algorithm. For the secret key queries, the challenger respond by the SampleRight instead of SampleLeft. By the definition of , we have , . If or , the challenger aborts and returns a random bit. Otherwise, it returns and to where
In particular, the challenger checks if the challenge identity satisfies and . If not, the game aborts as in .
Since in the adversary’s view, and are identical (the public parameters, abort conditions, responses to private key queries and the challenge ciphertext). The advantage of the adversary is identical to , i.e.,
. As we know, the ciphertext space is . In this game, the challenger set the ciphertext as which is uniformly random in in the challenge phase. The advantage of the adversary is 0. As shown in Lemma 9, assuming -LWE holds, and are computationally indistinguishable, i.e., ☐
Lemma 9.
For any PPT adversary , there exists a challenger such that
Proof of Lemma 9.
Suppose has a non-negligible advantage in distinguishing and . We use to construct an LWE algorithm denoted .
Recall from Definition 4 that an LWE problem instance is provided as a sampling oracle which is either a truly random sampler or a noisy pseudo-random sampler for a secret . The challenger uses the adversary to distinguish which the sampler it is given, and proceeds as follows:
Instance. The challenger requests from to obtains LWE samples that we denote as:
Setup. The challenger constructs the public parameters as follows:
- (1)
- Construct a matrix by assembling m LWE samples such that , and let .
- (2)
- Choose as in and constructs the remainder of the public parameters as in .
- (3)
- Send the to .
Queries. makes secret key query. The challenger computes and checks if . If it holds, it aborts. Otherwise it generate the secret key for as in .
Challenge. sends a message bit and the target identities to . The challenger constructs where is the LWE samples. chooses . The challenge ciphertext
sends the challenge ciphertext to .
Note that when , the ciphertext is valid.(We just argue only when no abort happens). Since and , we have where . The same as , we have . By definition of , we know . Then we have
The same as , is also valid. It is also similar to the .
When , and are all uniform. Therefore are uniform in by the Lemma 6.
Guess. After being allowed to make additional secret key queries, guesses if it is interacting with a or challenger. output ’s guess as the answer to the LWE challenge it is trying to solve. Therefore we have . ☐
4. Adaptively Secure Hierarchical IB-DRE Scheme with Short Public Parameter
To lighten the pressure of the KGC, hierarchical IBE (HIBE) scheme was proposed. In HIBE, the user’s identity can be described by an identity tuple, and we let denote an identity at the depth k. There are many users at each depth. In this section, we use and to denote the two arbitrary receivers at the depth k in our HIB-DRE scheme.
As we all know, when convert an selectively secure HIBE scheme in [11] to an adaptively secure HIBE, for an identity at the depth k, the key generation matrix/encryption matrix would be
where is the matrices in the public parameters.
Therefore the public parameters would be matrices which lead to a high storage cost. d is the maximum hierarchy depth.
In this section, we construct an adaptively secure HIB-DRE scheme with short public parameters. There are also four algorithms in this scheme: . In this scheme, we use the same injective map function and homomorphic computation technique to reduce the size of public parameters from matrices to matrices. Different to the adaptively secure IB-DRE scheme in Section 3, we use the [11] algorithm to generate the user’s secret key, and algorithm for the security proof. In the phase, it needs to input a secret key for the identity at depth , and then outputs a secret key for the identity at depth l.
): On input two matrices , , a “short” basis of and a Gaussian parameter . This algorithm outputs a short basis of where .
): On input three matrices , , , a basis of and a Gaussian parameter where and . This algorithm outputs a short basis of where .
4.1. Our Construction
The adaptively secure HIB-DRE scheme with short public parameters consists the following four algorithms.
- (1).
- )→ (): on input the maximum hierarchy depth d and the security parameter . This algorithm outputs the public parameters and master secret key , do:
- -
- Perform algorithm TrapGen to generate a uniformly matrix and a trapdoor .
- -
- For all identities where , select an injective map that maps an identity to a subset of where .
- -
- For and , select matrices , .
- -
- Select a uniformly random vector and a uniformly random matrix .
The public parameter = , , , the master secret key .For two arbitrary receivers , at the depth k. Recall that by the function : , for the two identities , letThen constructNote that for , . - (2).
- ): On input the public parameter , the user’s identity at depth k where , the secret key corresponding to an identity at depth and the master secret key . This algorithm KeyGen outputs a secret key as follow:The secret key is .
- (3).
- ): On input the public parameter , the user’s identities and the message bit . This algorithm outputs the ciphertext . It works as follows:
- -
- It firstly gets and as above.
- -
- Choose a randomly uniform vector , and a uniformly random matrix .
- -
- Choose error terms , . Let , compute
The ciphertext is . - (4).
- ): On input the public parameter , a secret key where at depth k and the ciphertext , do:
- -
- Set .
- -
- For , set . Then and .
- -
- Compute .
- -
- if . Otherwise .
- -
- Finally, it outputs the message .
4.2. Correctness
We firstly compute
Let where . Then we have and where . Since , by Equation (3),
To ensure the correctness of decryption and preform the security proof, for all , we need that:
- -
- the error term is less than with overwhelming probability (w.h.p) (i.e., , and ),
- -
- the algorithm can operate (i.e., for some ),
- -
- the Leftover Hash Lemma can be applied to security proof (i.e., ),
- -
- the SampleBasisLeft and SampleBasisRight algorithm can operate (i.e., where ), and
- -
- the Regev’s LWE reduction applies(i.e., ).
4.3. Security
Theorem 3.
If the -LWE assumption holds, the above HIB-DRE scheme is IND-ID-CPA secure.
Proof.
Let be a probabilistic polynomial-time(PPT) adversary that can break our IB-DRE scheme with advantage . Then there exists a reduction that solves the -LWE problem with an negligible advantage. Let is the upper bound of the number of KeyGen queries and denotes the challenge IDs. Different from in [11], here we let where . We show the security via the following games. In each game, we define a value and let denote the event that the adversary correctly guessed the challenge bit, i.e., the challenger output in . is the adversary’s advantage.
. This is the real IND-ID-CPA game between an adversary and the challenger. So we have
. The same as in Section 3.3, in this game we also add an abort event at the end of the game. The challenger chooses where and . Let and H be a function such that
For the challenge IDs, the challenger checks whether and where . If they do not hold, the game aborts. Otherwise, the challenger outputs .
Different to the Lemma 8, the probability satisfies
Then by , we have
. In this game, we change the way , , are generated. The challenger firstly chooses , as and chooses three matrices . Compute
Based on Lemma 6, the distribution (, , , ) is -close to the distribution (, , , ). Therefore, we have
Before the next game, let
Based on Lemma 3, we have
is the same as .
Then define where . We have .
. In this game, we change the way is generated. The challenger chooses a random matrix instead of using the algorithm. For the secret key queries, the challenger responds by the instead of . By the definition of , we have
Therefore for ,
where and .
If or , the challenger aborts and returns a random bit. Otherwise, it returns and to where
In particular, the challenger checks if the challenge identity satisfies and . If not, the game aborts as in .
Since in the adversary’s view, and are identical (the public parameters, abort conditions, responses to private key queries and the challenge ciphertext). The advantage of the adversary is identical to , i.e.,
. As we know, the ciphertext space is . In this game, the challenger set the ciphertext as which is uniformly random in in the challenge phase. And the advantage of the adversary is 0. As shown in Lemma 10, assuming -LWE holds, and are computationally indistinguishable, i.e., ☐
Lemma 10.
For any PPT adversary , there exists a challenger such that
Proof of Lemma 10.
Suppose has a non-negligible advantage in distinguishing and . We use to construct an LWE algorithm denoted .
Recall from Definition 4 that an LWE problem instance is provided as a sampling oracle which is either a truly random sampler or a noisy pseudo-random sampler for a secret . The challenger uses the adversary to distinguish which the sampler it is given, and proceeds as follows:
Instance. The challenger requests from to obtain LWE samples that we denote as:
Setup. The challenger constructs the public parameters as follows:
- (1)
- Construct a matrix by assembling m LWE samples such that , and let .
- (2)
- Choose as in and constructs the remainder of the public parameters as in .
- (3)
- Send the to .
Queries. makes secret key query. The challenger computes and checks if . If it holds, it aborts. Otherwise it generate the secret key for as in .
Challenge. sends a message bit and the target identities to . The challenger constructs where is the LWE samples. Let and . Then the challenge ciphertext
sends the challenge ciphertext to .
Note that when , the ciphertext is valid.(We just argue only when no abort happens). Since and , we have . The same as , we have . By definition of , we know . Then we have
The same as , is also valid. It is also similar to the .
When , and are all uniform. Therefore are uniform in by the Lemma 6.
Guess. After being allowed to make additional secret key queries, guesses if it is interacting with a or challenger. output ’s guess as the answer to the LWE challenge it is trying to solve. Therefore we have . ☐
Remark 1.
Note that, as in [10,11], the two schemes also can encrypt multiple message bits. To encrypt n-bits message we need to include n vectors in the public parameters. Letand replace the vectorwith. Then taking each element ofas input in the KeyGen phase in the IB-DRE scheme or the Decrypt phase in the HIB-DRE scheme such that,. Moreover, replace the ciphertextwith. The proof of security is basically unchanged, except that in the Instance phase makes times queries of the LWE oracle instead of times.
5. Performance Analysis
Here we firstly give the comparison between lattice-based IB-DRE scheme and other related IB-DRE schemes which are based on bilinear maps. As shown in Table 1, compared to [4], our scheme and [20] can resist quantum attack due to the fact that our scheme and [20] are based on the LWE problem on lattices which is proved by Regev [9] to resist quantum computing attack, but [4] is based on the decisional bilinear Diffie–Hellman (DBDH) problem which can not resist quantum computing attack. In addition, [4,20] and our scheme are all proved to be CPA secure. To lighten the pressure of KGC, we extend our scheme to the hierarchical scenario, but [4,20] can not support hierarchical scenario.

Table 1.
The comparison between lattice-based identity-based device receiver encryption (IB-DRE) and bilinear maps-based IB-DRE.
Next we give the comparison of storage cost, communication cost and computational cost between our construction and the first lattice-based IB-DRE scheme (next we use how Zhang18 denotes it).
Storage costs analysis. Here we give the comparison of storage costs between our construction and the first lattice-based IB-DRE scheme (next we use how Zhang18 denotes it). In Zhang18, the authors propose an adaptively secure IB-DRE scheme based on the LWE problem. In their scheme, to achieve the adaptively-ID secure, they generate matrices in the Setup phase by using the same method of [11]. The size of public parameters is which lead to a high storage overhead. As shown in Table 2, the suggested lattice dimension m in our scheme is smaller than [20] under the same adaptively secure model. Since p is a flexible constant which can directly affect the size, we give the comparison results when p takes different values. Since we introduce an injective map function in our construction, the public parameters size can be reduced from matrices to matrices where is a flexible constant. Namely, the storage cost of public parameters is reduced from to . Moreover, the user’s secret key in our scheme is smaller than [20] and the ciphertext is equal to [20]. Figure 1 shows that when and according to the suggestion given by Micciancio et al. in [22], the size of public parameters in our scheme is reduced by merely 88% of Zhang et al.’s method. Not to mention when or . In addition, from the Figure 1, with the increasing of the bit-length of identity, the size of public parameters in our scheme and [20] are also increase. It is still smaller than [20]. In addition, in our scheme, when , the size of the public parameters in our scheme achieves the largest of our scheme, and it is of [20]. Not to mention when .

Table 2.
The comparison between our scheme and related lattice-based scheme.
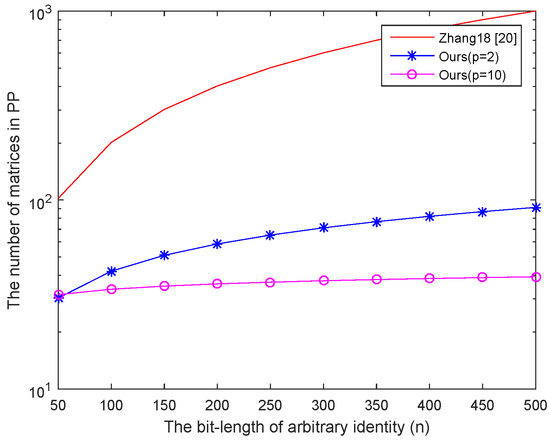
Figure 1.
The number of the matrices in public parameters.
Communication costs analysis. There are four algorithms in our scheme and in Zhang18 [20]. During the operation of the algorithm, three transmissions of public parameters, two transmissions of ciphertext and at least two transmissions of user’s secret key are required. According to the comparison results of Table 2 and Figure 1, under the same transmission bandwidth, it is obvious that communication costs of our public parameters and user’s secret key are faster than in Zhang18 [20]. Communication cost of the ciphertext is equal to Zhang18 [20].
Computational costs analysis. As shown in Table 3, we compared our scheme with Zhang18 on computational costs. The computational cost of encryption in our construction is equal to the related lattice-based IB-DRE scheme in [20]. As for the computational cost of KeyGen, in [20] the user’s secret key is a matrix while it is a dimensions vector in our scheme. Thus, the computational cost of KeyGen in [20] is larger than our scheme. Due to the fact that the size of user’s secret in [20] is n times larger than us, the computational cost is also larger than us.

Table 3.
The comparison of computational cost.
6. Conclusions
Different from the standard cryptographic primitive of public key encryption by which a ciphertext can usually be decrypted by the private-key holders only, dual receiver encryption enables a ciphertext to be decrypted to the same plaintext by two different but dual receivers. In this paper, we propose two more efficient constructions of (hierarchical) identity-based dual receiver encryption schemes from lattices which can resist quantum attack. By combining an injective map and a homomorphic computation technique, the size of public parameters is remarkably reduced from matrices to matrices where is a flexible constant. Compared to the only related work—Zhang18, about 88% = (1–12%) storage cost is saved by using our method. Under the intractability assumption of the learning with errors problem over lattices, our proposal was proved to be semantically secure against adaptively chosen identity and plaintext attacks.
Author Contributions
Conceptualization, X.S. and L.L.; investigation, L.L.; formal analysis and scheme design, Y.L. and X.S.; secure proof and performance analysis, Y.L. and L.W.; methodology, Y.L. and L.W.; writing—original draft preparation, Y.L.; writing—review and editing, X.S. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Shandong Provincial Key Research and Development Program of China (2018CXGC0701), the National Natural Science Foundation of China (NSFC) (No. 61972050), and the BUPT Excellent Ph.D. Students Foundation (Grant Nos. CX2019119 and CX2019233).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Diament, T.; Lee, H.K.; Keromytis, A.D.; Yung, M. The Dual Receiver Cryptosystem and its Applications. In Proceedings of the 11th ACM Conference on Computer and Communications Security 2004 (CCS’04), Washington, DC, USA, 25–29 October 2004; pp. 330–343. [Google Scholar]
- Chow, S.S.M.; Franklin, M.; Zhang, H. Practical Dual-Receiver Encryption. In Proceedings of the Cryptographers’ Track at the RSA Conference (CT-RSA’14), San Francisco, CA, USA, 25–28 February 2014; pp. 85–105. [Google Scholar]
- Dodis, Y.; Katz, J.; Smith, A.; Walfish, S. Composability and on-Line Deniability of Authentication. In Proceedings of the 6th Theory of Cryptography Conference on Theory of Cryptography 2009 (TCC’09), San Francisco, CA, USA, 15–17 March 2009; pp. 146–162. [Google Scholar]
- Zhang, K.; Chen, W.; Li, X.; Chen, J.; Qian, H.F. New application of partitioning methodology: Identity-based dual receiver encryption. Secur. Commun. Netw. 2016, 9, 5789–5802. [Google Scholar] [CrossRef]
- Waters, B. Efficient Identity-Based Encryption without Random Oracles. In Proceedings of the Advances in Cryptology-Eurocrypt 2005, Aarhus, Denmark, 22–26 May 2005; pp. 114–127. [Google Scholar]
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Ajtai, M.; Dwork, C. A Public-Key Cryptosystem with Worst-Case/Average-Case Equivalence. In Proceedings of the 29th Annual ACM Symposium on Theory of Computing(STOC’97), El Paso, TX, USA, 9–11 May 1997; pp. 284–293. [Google Scholar]
- Ajtai, M. Generating Hard Instances of Lattice Problems. In Proceedings of the 28th Annual ACM Symposium on Theory of Computing(STOC’96), Philadelphia, PA, USA, 21–23 May 1996; pp. 99–108. [Google Scholar]
- Regev, O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography. In Proceedings of the 37th Annual ACM Symposium on Theory of Computing(STOC’05), Baltimore, MD, USA, 22–24 May 2005; pp. 84–93. [Google Scholar]
- Gentry, C.; Peikert, C.; Vaikuntanathan, V. Trapdoors for Hard Lattices and New Cryptographic Constructions. In Proceedings of the 40th Annual ACM Symposium on Theory of Computing(STOC’08), Victoria, BC, Canada, 17–20 May 2008; pp. 197–206. [Google Scholar]
- Agrawal, S.; Boneh, D.; Boyen, X. Efficient Lattice (H)IBE in the Standard Model. In Proceedings of the Advances in Cryptology-Eurocrypt’10, French Riviera, France, 30 May–3 June 2010; pp. 553–572. [Google Scholar]
- Agrawal, S.; Boneh, D.; Boyen, X. Lattice Basis Delegation in Fixed Dimension and Shorter-Ciphertext Hierarchical IBE. In Proceedings of the Advances in Cryptology-Crypto’10, Santa Barbara, CA, USA, 15–19 August 2010; pp. 98–115. [Google Scholar]
- Singh, K.; Pandurangan, C.; Banerjee, A.K. Adaptively Secure Efficient Lattice (H)IBE in Standard Model with Short Public Parameters. In Proceedings of the Second International Conference on Security, Privacy, and Applied Cryptography Engineering (SPACE’12), Chennai, India, 3–4 November 2012; pp. 153–172. [Google Scholar]
- Yamada, S. Adaptively Secure Identity-Based Encryption from Lattices with Asymptotically Shorter Public Parameters. In Proceedings of the Advances in Cryptology-Eurocrypty’16, Vienna, Austria, 8–12 May 2016; pp. 32–62. [Google Scholar]
- Agrawal, S.; Boyen, X.; Vaikuntanathan, V.; Voulgaris, P. Functional Encryption for Threshold Functions (or Fuzzy IBE) from Lattices. In Proceedings of the 15th International Conference on Practice and Theory in Public Key Cryptography(PKC’12), Darmstadt, Germany, 18–20 May 2012; pp. 280–297. [Google Scholar]
- Boyen, X. Attribute-Based Functional Encryption on Lattices. In Proceedings of the 10th Theory of Cryptography Conferenc e(TCC’13), Tokyo, Japan, 3–6 March 2013; pp. 122–142. [Google Scholar]
- Gorbunov, S.; Vaikuntanathan, V.; Wee, H. Attribute-Based Encryption for Circuits. In Proceedings of the 44th Annual ACM Symposium on Theory of Computing (STOC’13), Palo Alto, CA, USA, 1–4 June 2013; pp. 545–554. [Google Scholar]
- Boneh, D.; Gentry, C.; Gorbunov, S.; Halevi, S. Fully Key-Homomorphic Encryption, Arithmetic Circuit ABE and Compact Garbled Circuit. In Proceedings of the Advances in Cryptology-Eurocrypt’14, Copenhagen, Denmark, 11–15 May 2014; pp. 533–556. [Google Scholar]
- Liu, Y.; Wang, L.; Li, L.; Yan, X. Security and efficient multi-authority attribute-based encryption scheme from lattices. IEEE Access 2019, 7, 3665–3674. [Google Scholar] [CrossRef]
- Zhang, D.; Zhang, K.; Li, B.; Lu, X.; Xue, H.; Li, J. Lattice-Based Dual Receiver Encryption and More. In ACISP2018: Information Security and Privacy; Springer: Cham, Switzerland, 2018; pp. 520–538. [Google Scholar]
- Alwen, J.; Peikert, C. Generating Shorter Bases for Hard Random Lattices. In Proceedings of the 26th Symposium on Theoretical Aspects of Computer Science (STACS’09), Freiburg, Germany, 26–28 February 2009; pp. 75–86. [Google Scholar]
- Micciancio, D.; Peikert, C. Trapdoors for Lattices: Simpler, Tighter, Faster, Smaller. In Proceedings of the Advances in Cryptology-Eurocrypt’12, Cambridge, UK, 15–19 April 2012; pp. 700–718. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).