The Impact of Clock Frequencies on Remote Power Side-Channel Analysis Attack Resistance of Processors in Multi-Tenant FPGAs
Abstract
1. Introduction
- To the best of our knowledge, we present the first theoretical analysis of unintended power side-channel leakage caused by changes in the victim circuit’s clock frequency.
- We characterize the performance of CPA with varying clock frequencies and phase relationships between the victim circuit and the TDC of an attacker using three metrics. The results confirm that a successful CPA attack requires fewer power traces when there is a specific relationship between phase and frequency.
- We present the CPA attack results of the AES-128 and SM4 algorithms on a Cortex-M0 operating at different clock frequencies to validate our theoretical analysis. Our study investigates the side-channel leakage phenomena of general-purpose processors on FPGAs when dynamically changing the clock frequencies.
2. Background
2.1. Threat Model of Multi-Tenant FPGAs
2.2. Voltage-Drop Sensors
2.3. Correlation Power Analysis Attack
- Select an appropriate intermediate value v that must be related to both the confidential information and the known input plaintext. The choice of v depends on the targeted encryption algorithm and the leakage characteristics of the target hardware implementation. For the AES algorithm, commonly used intermediate values in CPA attacks are the output of the first round AddRoundKey or the first output of the S-box.
- Compute the intermediate values for all possible keys k, based on the corresponding input plaintext p, to generate an intermediate value matrix V of size .
- Choose an appropriate power model and compute the hypothetical power consumption matrix H for the intermediate value matrix V. Common power models include the Hamming weight (HW) model and the Hamming distance (HD) model. For example, for recovering byte 0 of the AES first round key using the S-box output as intermediate values, the element h of the hypothetical power consumption matrix H can be expressed as follows:where is byte 0 of the plaintext p, and denotes the Hamming weight.
- Calculate the Pearson correlation coefficient between the hypothetical power consumption matrix H and the observed power consumption matrix O, resulting in a correlation coefficient matrix R of size . Each element can be expressed as Equation (2), where represents the value of the t-th sample point in the power trace corresponding to the plaintext p.
- Rank all possible keys k based on the magnitude of their correlation coefficients, with the key having the highest correlation coefficient being ranked first as the guessed key.
3. Theoretical Analysis of Clock Frequency Impact on the Power Side-Channel
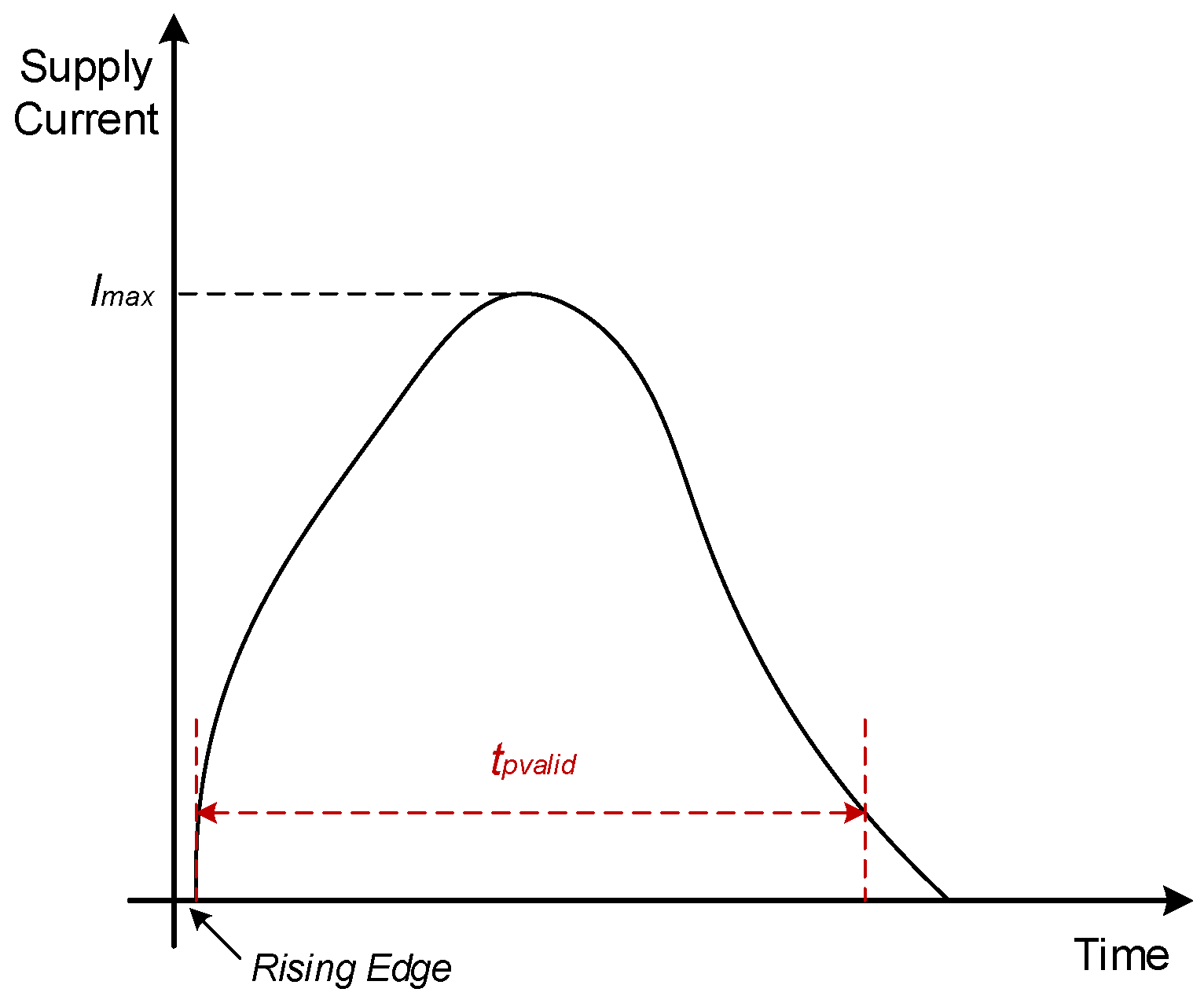
3.1. Power Side-Channel
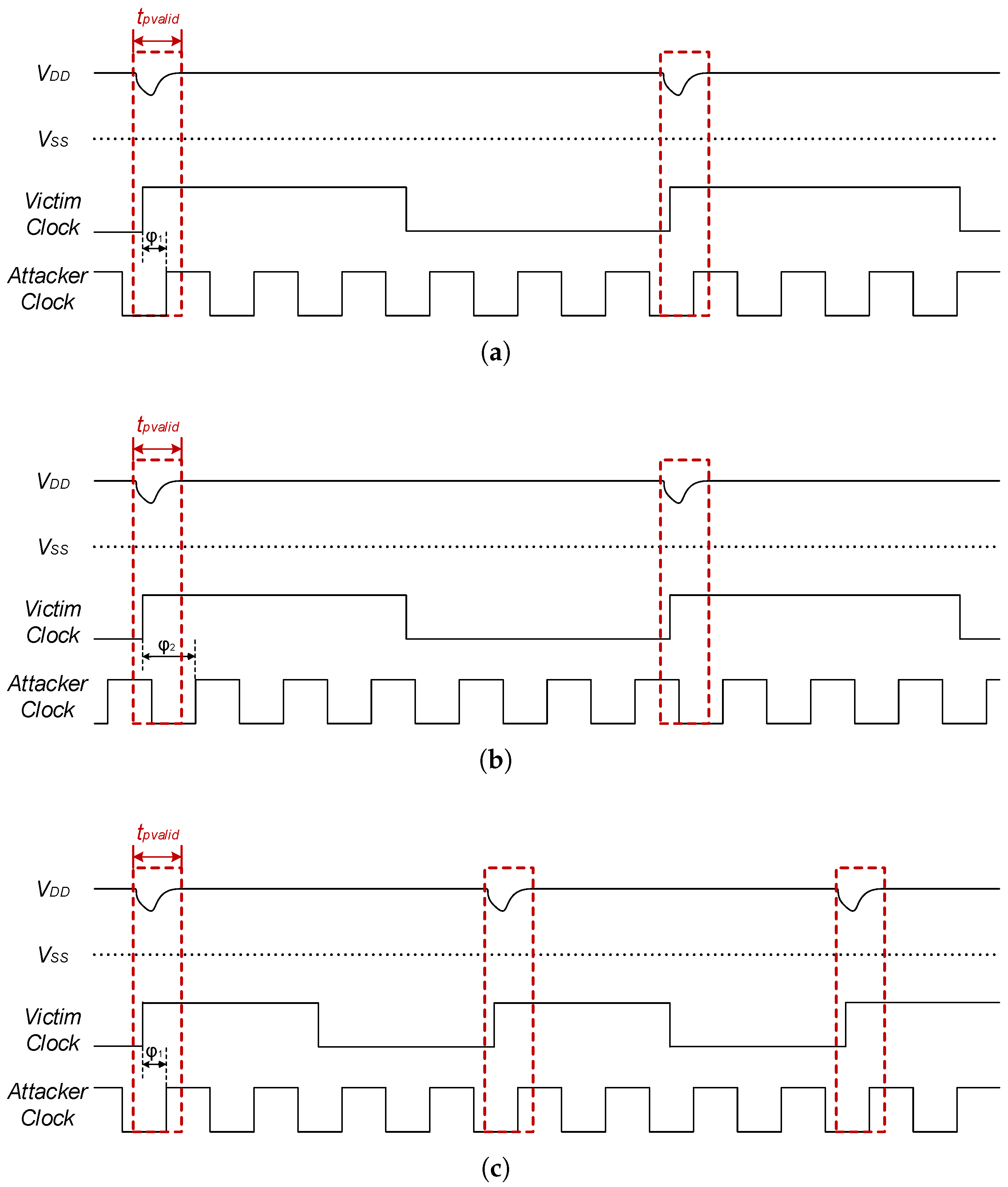
3.2. Mechanism of Clock Frequency Impact
4. Results and Analysis
4.1. Experimental Setup
4.2. CPA Evaluation Metrics
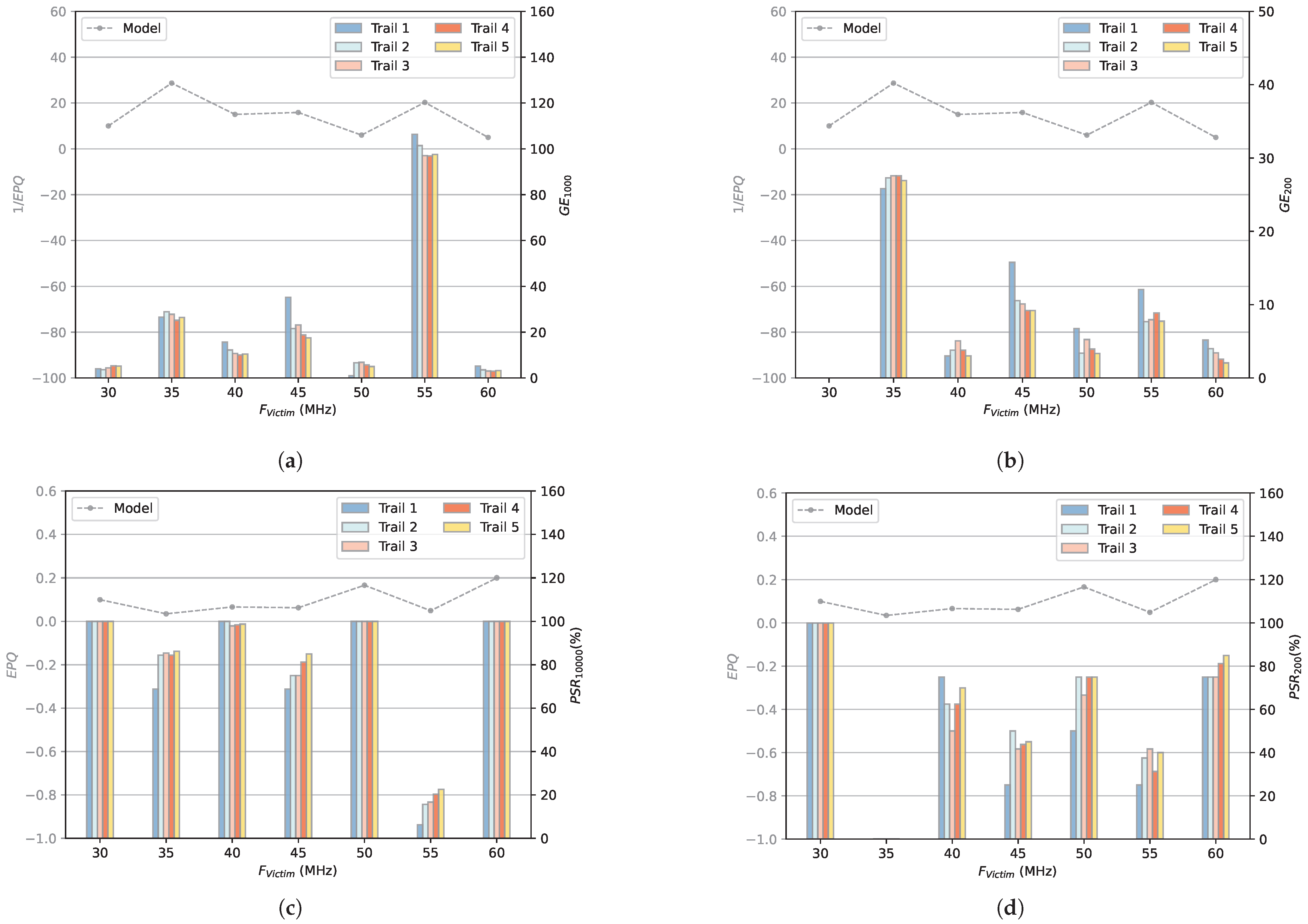
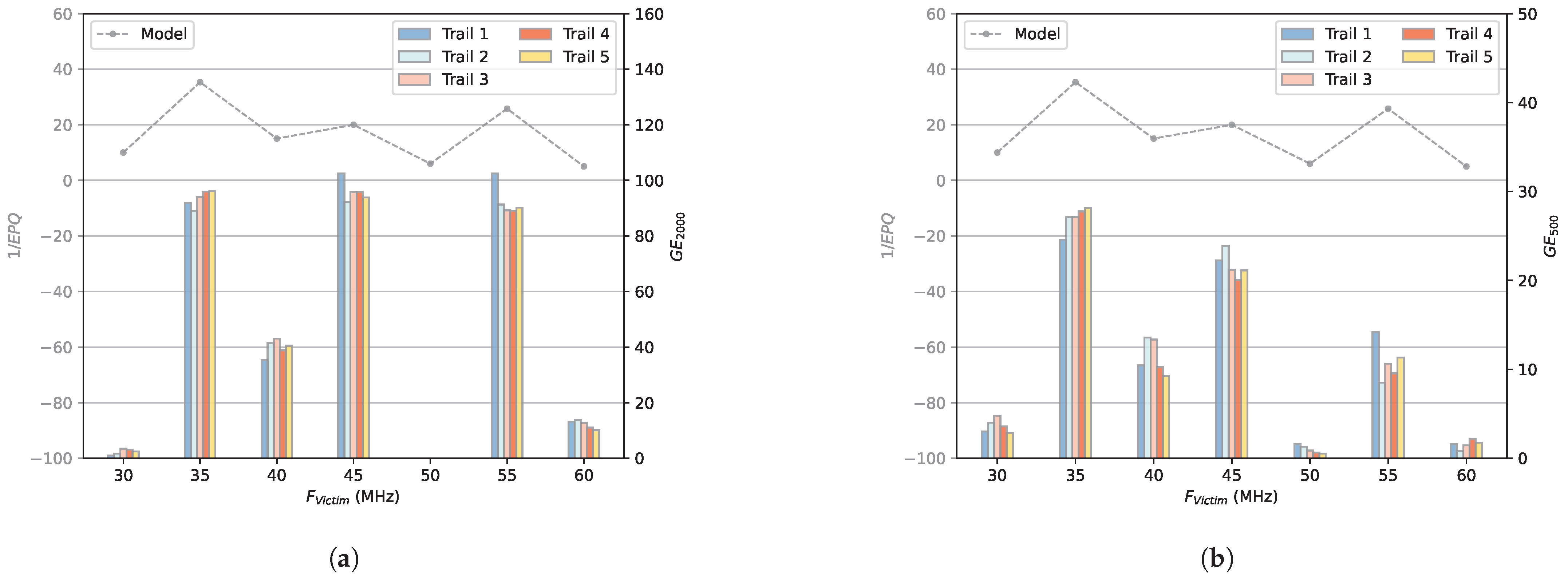
- GE: GE is an indicator based on the correlation coefficient matrix R. For byte i of the round key (referred to as sub-key ), all possible key byte guesses are ordered by their correlation coefficient in descending order to determine the rank of the correct key byte. The ranks for all correct key bytes are then summed logarithmically to calculate the GE, as illustrated in Equation (11). We use t to indicate the number of traces used to calculate this GE.A lower GE signifies lower average ranks across all key bytes, typically indicating that more key bytes have been successfully recovered. A GE value of 0 means that all key bytes have been recovered. In practice, a CPA attack is considered successful if the GE value falls below a predefined threshold, enabling the recovery of key bytes with reasonable computational effort. It should be noted that a low GE value does not guarantee the correct sub-key ranks first, as erroneous sub-keys may still be present. Thus, GE is not a reliable metric for assessing CPA attack performance in recovering all sub-keys. Only GE = 0 indicates full sub-key recovery.
- PSR: We also use the PSR calculated as Equation (12) to evaluate the effectiveness of CPA attacks in recovering the sub-keys.In Equation (12), denotes the number of correctly estimated sub-keys using i traces. denotes the number of total sub-keys. We use t to indicate the number of traces used to calculate this PSR. For example, means that all sub-keys are correctly retrieved using 20,000 traces.
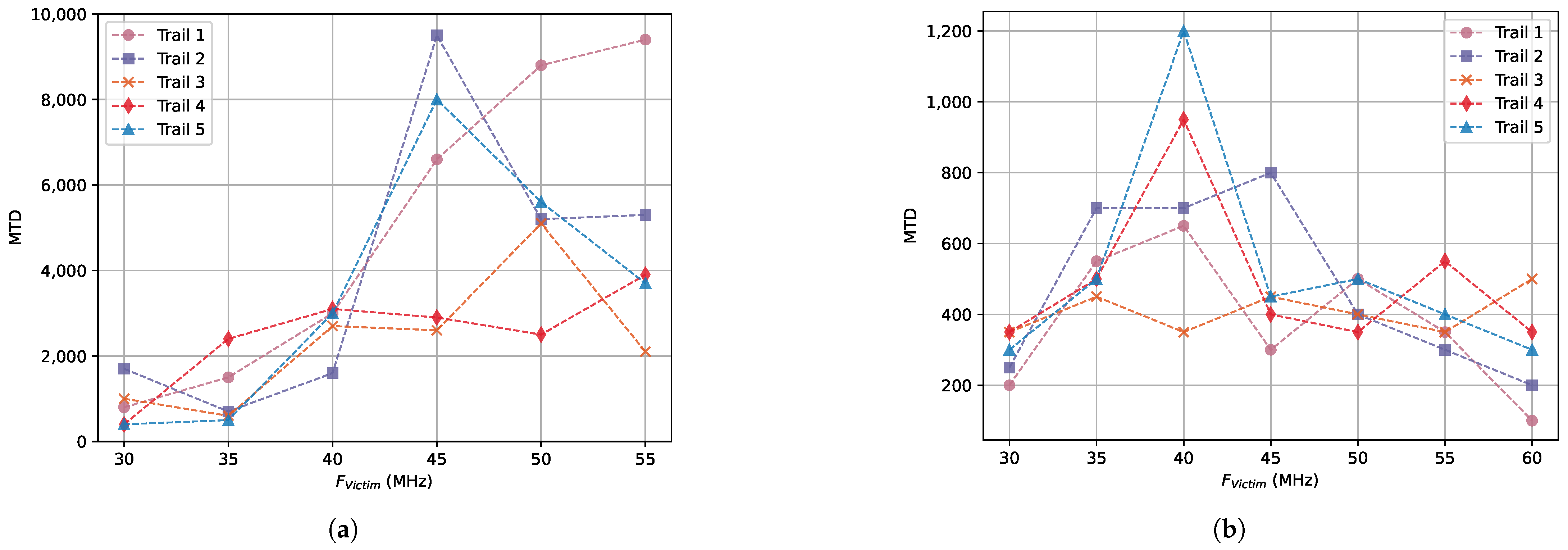
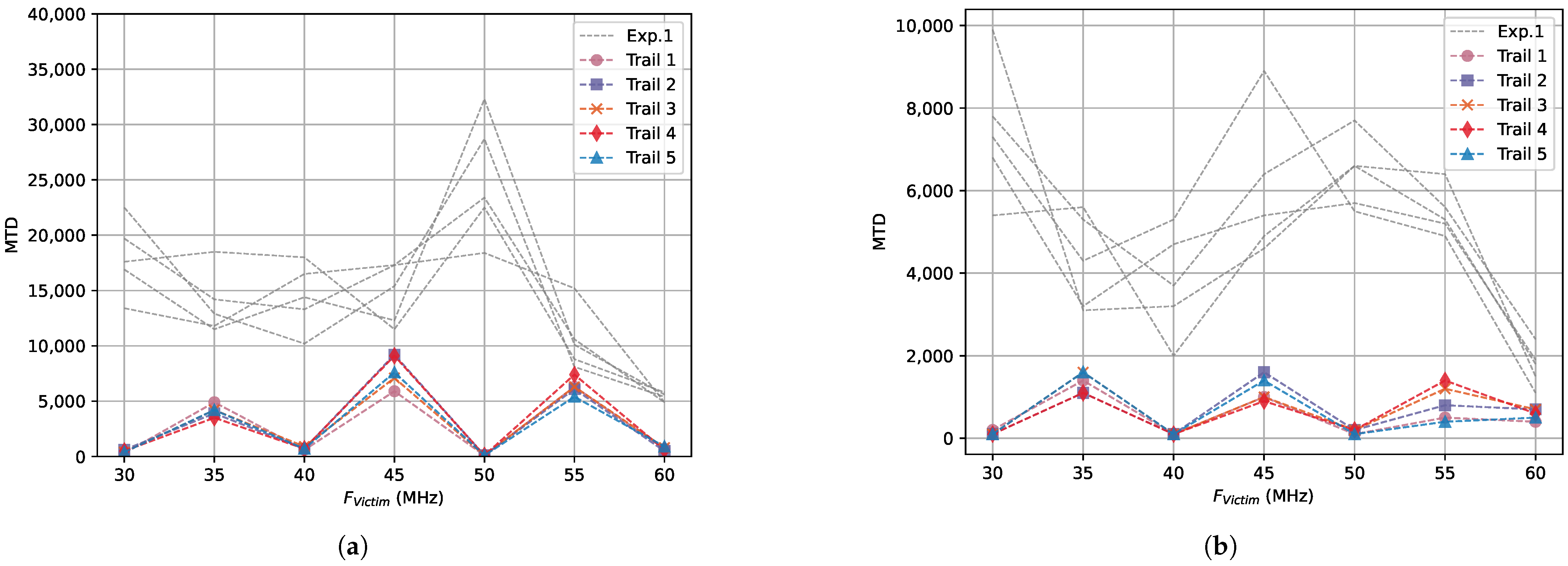
- MTD: The minimum number of traces needed to recover the key. If the MTD value is smaller, it proves that it is easier to recover the key through the CPA attack.
4.3. Random and Fixed
4.4. Fixed and Fixed
4.5. Fixed and Proportional
5. Discussion and Future Works
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Krautter, J.; Gnad, D.R.; Schellenberg, F.; Moradi, A.; Tahoori, M.B. Active fences against voltage-based side channels in multi-tenant FPGAs. In Proceedings of the 2019 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Westminster, CO, USA, 4–7 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–8. [Google Scholar]
- Zhao, M.; Suh, G.E. FPGA-based remote power side-channel attacks. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 21–23 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 229–244. [Google Scholar]
- Schellenberg, F.; Gnad, D.R.; Moradi, A.; Tahoori, M.B. An inside job: Remote power analysis attacks on FPGAs. In Proceedings of the 2018 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 19–23 March 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1111–1116. [Google Scholar]
- Schellenberg, F.; Gnad, D.R.; Moradi, A.; Tahoori, M.B. Remote inter-chip power analysis side-channel attacks at board-level. In Proceedings of the 2018 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Diego, CA, USA, 5–8 November 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–7. [Google Scholar]
- Luo, Y.; Xu, X. A quantitative defense framework against power attacks on multi-tenant FPGA. In Proceedings of the 39th International Conference on Computer-Aided Design, Virtual, 2–5 November 2020; pp. 1–9. [Google Scholar]
- Alam, M.M.; Tajik, S.; Ganji, F.; Tehranipoor, M.; Forte, D. RAM-Jam: Remote temperature and voltage fault attack on FPGAs using memory collisions. In Proceedings of the 2019 Workshop on Fault Diagnosis and Tolerance in Cryptography (FDTC), Atlanta, GA, USA, 24 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 48–55. [Google Scholar]
- Gnad, D.R.; Oboril, F.; Tahoori, M.B. Voltage drop-based fault attacks on FPGAs using valid bitstreams. In Proceedings of the 2017 27th International Conference on Field Programmable Logic and Applications (FPL), Ghent, Belgium, 4–8 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–7. [Google Scholar]
- Provelengios, G.; Holcomb, D.; Tessier, R. Power distribution attacks in multitenant FPGAs. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2020, 28, 2685–2698. [Google Scholar] [CrossRef]
- Zhang, F.; Wang, Z.; Shen, H.; Yang, B.; Wu, Q.; Ren, K. DARPT: Defense against remote physical attack based on TDC in multi-tenant scenario. In Proceedings of the 59th ACM/IEEE Design Automation Conference, San Francisco, CA, USA, 10–14 July 2022; pp. 559–564. [Google Scholar]
- Drewes, C.; Sheaves, T.; Weng, O.; Ryan, K.; Hunter, B.; McCarty, C.; Kastner, R.; Richmond, D. Turn on, Tune in, and Listen up: Maximizing Side-Channel Recovery in Cross-Platform Time-to-Digital Converters. ACM Trans. Reconfigurable Technol. Syst. (TRETS) 2024, 17, 49. [Google Scholar] [CrossRef]
- Glamočanin, O.; Coulon, L.; Regazzoni, F.; Stojilović, M. Are cloud FPGAs really vulnerable to power analysis attacks? In Proceedings of the 2020 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 9–13 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1007–1010. [Google Scholar]
- Krautter, J.; Gnad, D.R.; Tahoori, M.B. FPGAhammer: Remote voltage fault attacks on shared FPGAs, suitable for DFA on AES. Iacr Trans. Cryptogr. Hardw. Embed. Syst. 2018, 2018, 44–68. [Google Scholar] [CrossRef]
- Rakin, A.S.; Luo, Y.; Xu, X.; Fan, D. Deep-Dup: An adversarial weight duplication attack framework to crush deep neural network in Multi-Tenant FPGA. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21), Vancouver, BC, Canada, 11–13 August 2021; pp. 1919–1936. [Google Scholar]
- Das, S.; Whatmough, P.; Bull, D. Modeling and characterization of the system-level Power Delivery Network for a dual-core ARM Cortex-A57 cluster in 28nm CMOS. In Proceedings of the 2015 IEEE/ACM International Symposium on Low Power Electronics and Design (ISLPED), Rome, Italy, 22–24 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 146–151. [Google Scholar]
- Gravellier, J.; Dutertre, J.M.; Teglia, Y.; Loubet-Moundi, P. High-speed ring oscillator based sensors for remote side-channel attacks on FPGAs. In Proceedings of the 2019 International conference on ReConFigurable computing and FPGAs (ReConFig), Cancun, Mexico, 9–11 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–8. [Google Scholar]
- Tian, S.; Moini, S.; Wolnikowski, A.; Holcomb, D.; Tessier, R.; Szefer, J. Remote power attacks on the versatile tensor accelerator in multi-tenant FPGAs. In Proceedings of the 2021 IEEE 29th Annual International Symposium on Field-Programmable Custom Computing Machines (FCCM), Orlando, FL, USA, 9–12 May 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 242–246. [Google Scholar]
- Moini, S.; Deric, A.; Li, X.; Provelengios, G.; Burleson, W.; Tessier, R.; Holcomb, D. Voltage sensor implementations for remote power attacks on FPGAs. ACM Trans. Reconfigurable Technol. Syst. (TRETS) 2022, 16, 1–21. [Google Scholar] [CrossRef]
- Brier, E.; Clavier, C.; Olivier, F. Correlation power analysis with a leakage model. In Proceedings of the Cryptographic Hardware and Embedded Systems-CHES 2004: 6th International Workshop, Cambridge, MA, USA, 11–13 August 2004; Proceedings 6. Springer: Berlin/Heidelberg, Germany, 2004; pp. 16–29. [Google Scholar]
- Baker, R.J. CMOS: Circuit Design, Layout, and Simulation; John Wiley & Sons: Hoboken, NJ, USA, 2019. [Google Scholar]
- Rabaey, J.M.; Chandrakasan, A.; Nikolic, B. Digital Integrated Circuits; Prentice Hall: Englewood Cliffs, NJ, USA, 2002; Volume 2. [Google Scholar]
- Ganeshpure, K.; Sanyal, A.; Kundu, S. A pattern generation technique for maximizing switching supply currents considering gate delays. IEEE Trans. Comput. 2011, 61, 986–998. [Google Scholar] [CrossRef]
- Shan, W.; Zhang, C.; Li, Q.; Yu, J. A Lightweight Countermeasure of SM4 against Side Channel Analysis. In Proceedings of the 2022 8th Annual International Conference on Network and Information Systems for Computers (ICNISC), Hangzhou, China, 16–18 September 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 492–496. [Google Scholar]
- Xilinx, Inc. 7 Series FPGAs Clocking Resources (UG472); Xilinx, Inc.: San Jose, CA, USA, 2018. [Google Scholar]
- Xilinx, Inc. Large FPGA Methodology Guide, Including Stacked Silicon Interconnect (SSI) Technology (UG872); Xilinx, Inc.: San Jose, CA, USA, 2012. [Google Scholar]
- Das, D.; Danial, J.; Golder, A.; Modak, N.; Maity, S.; Chatterjee, B.; Seo, D.H.; Chang, M.; Varna, A.L.; Krishnamurthy, H.K.; et al. EM and power SCA-resilient AES-256 through> 350× current-domain signature attenuation and local lower metal routing. IEEE J. Solid-State Circuits 2020, 56, 136–150. [Google Scholar] [CrossRef]
- Li, Y.; Xu, S.; Luo, Y.; Qin, S.; Zhang, S.; Su, M. A Highly Efficient Profiled Power Analysis Attack Based on Power Leakage Fitting. In Proceedings of the 2021 IEEE 23rd Int Conf on High Performance Computing & Communications; 7th Int Conf on Data Science & Systems; 19th Int Conf on Smart City; 7th Int Conf on Dependability in Sensor, Cloud & Big Data Systems & Application (HPCC/DSS/SmartCity/DependSys), Haikou, China, 20–22 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 791–796. [Google Scholar]
- Liu, C.; Chakraborty, A.; Chawla, N.; Roggel, N. Frequency throttling side-channel attack. In Proceedings of the 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, CA, USA, 7–11 November 2022; pp. 1977–1991. [Google Scholar]
- Kim, Y. Successful Profiling Attacks with Different Measurement Environments for Each Phase. In Proceedings of the Information Security Applications: 15th International Workshop, WISA 2014, Jeju Island, Korea, 25–27 August 2014; Revised Selected Papers 15. Springer: Berlin/Heidelberg, Germany, 2015; pp. 321–330. [Google Scholar]
- Ramesh, C.; Patil, S.B.; Dhanuskodi, S.N.; Provelengios, G.; Pillement, S.; Holcomb, D.; Tessier, R. FPGA side channel attacks without physical access. In Proceedings of the 2018 IEEE 26th Annual International Symposium on Field-Programmable Custom Computing Machines (FCCM), Boulder, CO, USA, 29 April–1 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 45–52. [Google Scholar]
- Ravi, P.; Bhasin, S.; Breier, J.; Chattopadhyay, A. Ppap and ippap: Pll-based protection against physical attacks. In Proceedings of the 2018 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Hong Kong, China, 8–11 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 620–625. [Google Scholar]
- Jayasinghe, D.; Ignjatovic, A.; Parameswaran, S. SCRIP: Secure random clock execution on soft processor systems to mitigate power-based side channel attacks. In Proceedings of the 2019 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Westminster, CO, USA, 4–7 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–7. [Google Scholar]
- Hettwer, B.; Das, K.; Leger, S.; Gehrer, S.; Güneysu, T. Lightweight side-channel protection using dynamic clock randomization. In Proceedings of the 2020 30th International Conference on Field-Programmable Logic and Applications (FPL), Gothenburg, Sweden, 31 August–4 September 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 200–207. [Google Scholar]
- Zhu, Y.; Zhou, P. Protecting Parallel Data Encryption in Multi-Tenant FPGAs by Exploring Simple but Effective Clocking Methodologies. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2024, 32, 1919–1929. [Google Scholar] [CrossRef]
- Yang, J.; Han, J.; Dai, F.; Wang, W.; Zeng, X. A power analysis attack resistant multicore platform with effective randomization techniques. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2020, 28, 1423–1434. [Google Scholar] [CrossRef]
- Fledel, D.; Wool, A. Sliding-window correlation attacks against encryption devices with an unstable clock. In Proceedings of the Selected Areas in Cryptography–SAC 2018: 25th International Conference, Calgary, AB, Canada, 15–17 August 2018; Revised Selected Papers 25. Springer: Berlin/Heidelberg, Germany, 2019; pp. 193–215. [Google Scholar]
- Van Woudenberg, J.G.; Witteman, M.F.; Bakker, B. Improving differential power analysis by elastic alignment. In Proceedings of the Topics in Cryptology–CT-RSA 2011: The Cryptographers’ Track at the RSA Conference 2011, San Francisco, CA, USA, 14–18 February 2011; Proceedings. Springer: Berlin/Heidelberg, Germany, 2011; pp. 104–119. [Google Scholar]
- Batina, L.; Hogenboom, J.; van Woudenberg, J.G. Getting more from PCA: First results of using principal component analysis for extensive power analysis. In Proceedings of the Topics in Cryptology–CT-RSA 2012: The Cryptographers’ Track at the RSA Conference 2012, San Francisco, CA, USA, 27 February–2 March 2012; Proceedings. Springer: Berlin/Heidelberg, Germany, 2012; pp. 383–397. [Google Scholar]
- Mateos, E.; Gebotys, C.H. A new correlation frequency analysis of the side channel. In Proceedings of the 5th Workshop on Embedded Systems Security, Scottsdale, AZ, USA, 24 October 2010; pp. 1–8. [Google Scholar]






| Experiment | ||
|---|---|---|
| 1 | random | 300 MHz |
| 2 | 0 | 300 MHz |
| 3 | 0 | 5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, Q.; Xie, H.; Su, T. The Impact of Clock Frequencies on Remote Power Side-Channel Analysis Attack Resistance of Processors in Multi-Tenant FPGAs. Cryptography 2025, 9, 15. https://doi.org/10.3390/cryptography9010015
Zhou Q, Xie H, Su T. The Impact of Clock Frequencies on Remote Power Side-Channel Analysis Attack Resistance of Processors in Multi-Tenant FPGAs. Cryptography. 2025; 9(1):15. https://doi.org/10.3390/cryptography9010015
Chicago/Turabian StyleZhou, Qinming, Haozhi Xie, and Tao Su. 2025. "The Impact of Clock Frequencies on Remote Power Side-Channel Analysis Attack Resistance of Processors in Multi-Tenant FPGAs" Cryptography 9, no. 1: 15. https://doi.org/10.3390/cryptography9010015
APA StyleZhou, Q., Xie, H., & Su, T. (2025). The Impact of Clock Frequencies on Remote Power Side-Channel Analysis Attack Resistance of Processors in Multi-Tenant FPGAs. Cryptography, 9(1), 15. https://doi.org/10.3390/cryptography9010015







