Abstract
An active intelligent reflecting surface (IRS)-assisted, secure, multiple-input–single-output communication method is proposed in this paper. In this proposed scheme, a practical and unfavorable propagation environment is considered by assuming that multiple colluding eavesdroppers (Eves) coexist. In this case, we jointly optimize the beamformers of the base station (BS) and the active IRS for the formulated sum secrecy rate (SSR) maximization problem. Because the formulated problem is not convex, we apply the alternating optimization method to optimize the beamformers for maximizing the SSR. Specifically, we use the semi-definite relaxation method to solve the sub-problem of the beamforming vector of the BS, and we use the successive convex approximation method to solve the sub-problem of the power amplification matrix of the active IRS. Based on the solutions obtained using these stated methods, numerical results show that deploying an active IRS is superior compared to the cases of a passive IRS and a non-IRS for improving the physical layer security of wireless communication with multiple colluding Eves under different settings, such as the numbers of users, Eves, reflecting elements, and BS antennas as well as the maximum transmit power budget at the BS.
MSC:
94-10
1. Introduction
The use of an intelligent reflecting surface (IRS) is a highly promising technique with significant potential for future communications. It enables the reconfiguration of a wireless propagation environment by controlling a smart controller connected to the IRS which adjusts the phase shifter of each element [1]. However, in traditional passive architectures, the IRS is only capable of adjusting the phase shift of the incident signal, thus limiting the achievable rate at the receiver. A new IRS architecture referred to as an active IRS can provide an additional power ability to the IRS. This means that the active IRS has the capability to amplify the incident signal in addition to adjusting the phase shift matrix of the incident signal compared with a passive IRS.
Security in the physical layer has emerged as a significant concern for the future of wireless communication [2]. Because wireless communications have a broadcasting nature, there is a possibility of eavesdroppers (Eves) wiretapping the signal transmitted by a BS. In other words, the beamformer at the BS may designed to not only maximize the signal-to-noise ratio (SNR) for users but also for Eves. This is discussed in references [3,4,5,6]. To prevent legitimate information from being leaked to an eavesdropper, the authors of [7] proposed a secure SSK communication scheme for the classical eavesdropping scenario by introducing artificial noise (AN) according to the channel state information (CSI) of the user and the eavesdropper. Subsequently, the authors of [8] considered a more practical scenario by assuming that all CSI in their proposed scheme was imperfect. It is difficult to increase the sum secrecy rate (SSR) due to limited spatial degrees of freedom (DoFs) at the transceivers. Additionally, it is known that an IRS can be used to safeguard communication when there are wiretap channels caused by Eves because it can provide more controllable links to improve the SSR by increasing the achievable rate of legitimate users and preventing information from being leaked to the Eves. Recently, several works have introduced IRSs to secure wireless communication between a transmitter and legitimate receivers [9,10,11]. The authors of [9] formulated a maximization problem for maximizing the secrecy rate for -aided wireless communication involving one user and one Eve. In [10], Ye et al. introduced a jamming UAV to interfere with an Eve to safeguard communication between the user and the information UAV aided by an IRS. The maximum secrecy rate problem in the case of multiple ground nodes, including users and colluding Eves, in an IRS-assisted wireless environment was investigated in [11].
1.1. Related Work
Some previous works [12,13] stated that complicity among Eves can pose a serious threat to the physical layer security of wireless communications. From a security point of view, the case of complicit Eves could be treat as a worst-case scenario, and it is more worthy of research. In this case, in order to better protect communication between a transmitter and a legitimate receiver, one can introduce an IRS and adjust its phase shift matrix to provide multiple coherent links so that the SNR at the users is improved or to provide multiple incoherent links for suppressing the SNR at the Eves; thus, the SSR will be improved. In another research work on resource allocation, Qiao et al. proposed an energy-harvesting jammer and an IRS-aided security enhancement scheme to better combat eavesdroppers [14]. In addition, the authors of [15,16] proposed resource allocation methods for passive-IRS- and -IRS-aided wireless networks, respectively. Specifically, the authors of [15] introduced successive convex approximation (SCA), semi-definite relaxation (SDR), and manifold optimization to deal with the SSR maximization problem for a multiple-input–single-output (MISO) wireless network with one Eve and multiple users aided by passive IRS. The authors of [16] designed an algorithm that minimizes the transmit power of the base station (BS) while considering the constraints of quality-of-service (QoS) requirements for each user and the maximum amplification power of the active IRS for an active-IRS-aided communication system with multiple users. To investigate the impact of AN on passive-IRS-assisted secure communications, the authors of [17] considered a challenging scenario in which multiple Eves are in an IRS-aided communication system with one legitimate user. References [18,19] also considered a challenging scenario in which there are multiple users and Eves in a wireless communication system and a passive IRS is introduced to combat wiretapping from the multiple Eves by jointly optimizing beamformers at the BS and the passive IRS. In [20], Zhang et al. proposed a joint precoding algorithm that maximizes the sum rate of active-IRS-assisted multi-user MISO communication in which the numerical results verify that the active IRS has the ability to handle the multiplicative fading effect (MFE). To achieve better performance for secure, symbiotic radio multicast communication and a secure, wireless energy harvesting network, References [21,22] introduced an active IRS to combat multiple eavesdroppers. Moreover, a comparison of related works with our work is listed in Table 1.

Table 1.
A comparison of previous studies in the literature with our work.
1.2. Motivations and Contributions
These studies show that the active IRS is superior to the passive IRS because the active IRS brings more DoFs to each element than the passive IRS does. Based on the aforementioned discussions, it can be found that the active IRS can be used to handle the MFE and a worsened communication environment caused by colluding Eves. Specifically, we propose the use of an active IRS in the MISO wireless communication system to further suppress information leakage caused by multiple colluding Eves in which multiple users and multiple Eves are all assumed to be equipped with single antennas and the Eves cooperate with each other. To the best of our knowledge, this is the first scheme involving active-IRS-aided downlink MISO communication in which multiple users and multiple colluding Eves exist with direct and cascaded channels between the BS and all ground nodes. The contributions of the scheme proposed this paper are as follows:
- This work proposes a joint optimization framework for optimizing the beamformers of the BS and the active IRS to maximize the system SSR in a secure multi-user MISO wireless network with multiple colluding Eves. Specifically, by considering direct and cascaded links, we can introduce an active IRS to prevent more information from being leaked to the multiple colluding Eves, and it can further improve the SSR of the proposed scheme, as compared with the case with passive IRS.
- The problem of maximizing the SSR involves optimizing the beamforming vectors/ matrices of the BS and the active IRS, while taking into account the constraints of the BS’s maximum transmit power and the active IRS’s maximum amplification power. Given that the original problem is non-convex, we employ the alternating optimization (AO) approach to split it into two sub-problems. This allows us to separate the optimization variables. We then utilize the efficient SDR method to address the sub-problem of optimizing the beamformer vector of the BS. Furthermore, we employ SCA method to address the non-convex constraint in the sub-problem of optimizing the beamforming matrix of the active IRS.
- The proposed scheme is shown to be superior through numerical and simulation results. In other words, the proposed scheme offers a significant improvement in the SSR compared to other baselines, such as the case without an IRS and the case with a passive IRS. This demonstrates that an active IRS is highly effective when dealing with unfavorable wireless communication environments involving multiple colluding Eves.
1.3. Notations
The primary symbols iused n this study are enumerated in Table 2. Specifically, the boldface, uppercase letters denote matrixes, and the italic, boldface lowercase letters denote vectors. indicates the diagonalization of a vector. Complex and real spaces are denoted by and , respectively. , , , , and represent the trace of a matrix, the rank of the matrix, the norm of the vector, a conjugate transpose operation, and a transpose operation, respectively. returns the largest value in the set of . and denote an all-zero matrix with a size of and a unit matrix with a size of , respectively. denotes an element of a matrix at the a-th row and b-th column. Finally, is a big O notation for computational complexity.

Table 2.
Definitions of the main symbols used in the proposed scheme.
2. System Model
This section presents a scenario of secure communication facilitated by an active IRS with multiple colluding Eves. The scenario is illustrated in Figure 1 and includes a BS with M antennas, an IRS with N elements, K users, and L Eves. Both the users and Eves are each equipped with a single antenna. Define as the set of users in which . Similarly, define as the set of Eves in which . The confidential information tended to the users is wiretapped by multiple colluding Eves. The perfect CSI of all communication channel in Figure 1 is assumed to be accurately obtained because of the following reasons. In practice, cascaded and direct channels can be accurately estimated using the least-squares method and by optimizing training reflection patterns [23]. In addition, multiple colluding Eves can be treated as untrusted users and may be periodically active in the wireless communications. Hence, the CSI of multiple colluding Eves can be accurately obtained via the central control of the active IRS. Moreover, in order to further explore the capabilities of active IRS-assisted wireless communication when faced with multiple colluding Eves, we make the assumption that the perfect CSI is available for the proposed scheme, the SSR value of which serves as an upper bound for the scenario in which imperfect CSI is assumed. Furthermore, the channel estimation of the proposed scheme is beyond the scope of this work. Based on this assumption, the signal transmitted by the BS is given by
where represents the beamforming vector tended for the k-th user, and denotes the corresponding signal. Without a loss of generality, we assume that , , and , . We denote the channel from the BS to the active IRS, the channel from the BS to the k-th user, the channel from the BS to the l-th Eve, the channel from the active IRS to the k-th user, and the channel from the active IRS to the l-th Eve as , , , , and , respectively. Then, because of the controller attached to the active IRS and the independent amplifiers connected to each element at the active IRS, the reflected signal adjusted for the phase shifts and amplified for the power can be expressed as
where the matrix depicts the amplification coefficients of the active IRS. It is a diagonal matrix with non-negative elements denoted as . The matrix belongs to the set of non-negative real numbers denoted as . The phase shift matrix at the active IRS is represented by , where denotes the phase shift of the n-th reflecting element at the active IRS. Since each element of the active IRS is connected to the amplification component, additional amplification power will be consumed, which accounts for amplifying the reflected signal; thus, non-negligible thermal noise will also be amplified, as shown as in (2). Specifically, represents the thermal noise and the inherent device noise of the active IRS elements. The thermal noise introduced by the active IRS elements cannot be neglected because of the amplifier, which is connected to the active IRS and amplifies thermal noise. We assume that the thermal noise vector satisfies the distribution as . Based on the above, the received signals at the k-th user and at the l-th Eve can be expressed as
respectively, where the variables and stand for the additive white Gaussian noise at the k-th user and the l-th Eve followed by the circularly symmetric complex Gaussian distribution with a mean of 0 and variance of and a mean of 0 and a variance of , respectively. Let and be the equivalent channels from the BS to the k-th user and the l-th Eve, respectively, including both the direct link and the reflected link, shown as follows:
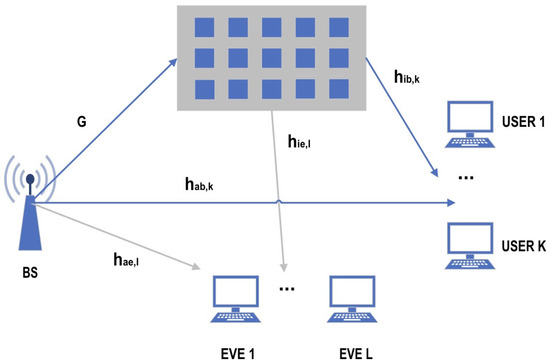
Figure 1.
An active-IRS-aided secure communication system with multiple colluding Eves.
The achievable rate of the k-th user is given as , where is the signal-to-interference-plus-noise ratio (SINR) of the k-th user, which is given in [20]
When L colluding Eves work together to wiretap the k-th user, they can be regarded as an Eve with L antennas. Then, the achievable rate of the l-th Eve is represented by , where represents the SINR of the l-th Eve given by
By applying Jensen’s inequality, we have the lower bound of as follows:
With in (9), we have the following tractable upper bound of the SSR of the proposed scheme [12]:
where . The transmit power of the BS and the amplification power coefficient of the active IRS, namely, and , can, respectively, be written as
Note that the proposed scheme always involves the presence of and in a multiplied form. Thus, and can be combined into a single matrix , with . The objective is to maximize the SSR by optimizing the beamformers, and , with two considered constraints, shown as follows:
Because the objective value of (13a) is always non-negative due to the DoF of the power control or resource allocation [9], we omit the operation for the objective function in (13a); thus, its smoothness is attained. In other words, if , we can allocate power to other users or let so that the objective value is 0. Compared with a passive IRS, the active IRS introduces an additional amplification factor in addition to the phase shifts at the IRS, thus avoiding the unit-modulus constraint and adding a power budget constraint (13c), accounting for the active IRS. However, it is worth investigating whether the newly introduced non-negligible thermal noise at the active IRS will cause a performance loss in the proposed scheme.
3. Proposed Methods
In this section, we employ the AO approach to optimize the beamformers of the BS and the active IRS because of the coupling between and . In other words, we optimize and alternately while keeping the other variable fixed. The flow chart of the proposed algorithm is shown in Figure 2. Specifically, for sub-problem 1, to circumvent non-convexity, we begin by introducing Lemma 1, as shown in Section 3.1, to convert the objective function into a more manageable form. Next, we employ the AO approach to decouple and the newly introduced slack variables. Finally, we apply a Gaussian randomization-based SDR method to obtain a rank-one solution, . For sub-problem 2, the SCA method is used to approximate non-convex terms in the objective functions.

Figure 2.
A flow chart of the proposed algorithm.
3.1. Optimize with Given
To tackle the difficulty arising because the fraction in the logarithm function is complex, we let and then rewrite as follows:
Noting that (14) is not convex, we resort to using the SDR method to transform the numerator and denominator of the logarithmic function into a linear form. To proceed, we first define , and ; then, the linear form of is given by
Let , ; we rewrite in (14) as
Lemma 1.
Considering the function , the maximum value of is , where .
Proof.
Please refer to Lemma 1, [17]. □
To tackle the non-convex terms in (13a), we need to convert the convex part of (16) into the form shown in Lemma 1. By defining the set , we have
where . By using the SDR method, the original convex function can be transformed into a more tractable concave function. We can use the same method to handle part of the achievable rate of the Eves in (13a). Let , , and . can be written as follows:
By defining , (18) can be rewritten as
Similarly, by applying Lemma 1, we can obtain the minimum of (19) as follows:
where . To obtain the solution, , the AO method can be used to tackle the coupling between and or . The detailed steps of using the AO-based method to optimize are described in Algorithm 1. By utilizing the SDR method and removing the rank-1 constraint for convexity, problem (13) with respect to optimizing is given by
where . Note that “” is neglected in the objective function without compromising its optimality. Since we omit the rank-1 constraint for tractability, if the rank of the solution of problem (21) satisfies , we can recover the solution for the beamformer at the BS using eigenvalue decomposition. Otherwise, if the rank of the solution to the problem (21) is larger than 1, i.e., , the Gaussian randomization method can be employed to construct a suboptimal solution with a rank of one [24]. In addition, the convex problem (21) can be effectively solved using the CVX solver [25].
| Algorithm 1 Optimize with given . |
|
3.2. Optimize with Given
For any given , , we first define for tractability in the sequel. To obtain the form of a quadratically constrained quadratic problem (QCQP), the terms in the numerator and denominator of (14) can be re-expressed as
where
Additionally, constraint (13c), which is related to the active IRS, can be rewritten as
in which . Accordingly, the SINR of l-th Eve for wiretapping the k-th user in (8) can be re-expressed as
where
in which
To tackle the non-convexity of and , we first introduce some slack variables as follows:
We observe that (29), (30), (32), and (35) are not convex. To tackle this issue, we can utilize the SCA technique to approximate these constraints in a convex form. In particular, by employing the first-order Taylor expansion for these constraints, we have [26]
where denotes the temporary variable, which is obtained in the last iteration. Then, by defining and , problem (13), with respect to optimizing , can be approximated as
We approximate all non-convex terms in problem (13) to convex terms in problem (40) for optimizing with the given . The convex problem (40) can be solved by a CVX solver. Moreover, in order to obtain the solution to problem (40) based on the SCA method, we iteratively optimize . Detailed steps are described in Algorithm 2.
| Algorithm 2 Optimize with given . |
|
3.3. Overall Algorithm
3.3.1. Convergence Analysis
The overall algorithm is an iterative optimization algorithm, as shown in Algorithm 3, which alternately optimizes and using iterative updates in each iteration. It can be easily seen that the AO-based algorithm generates a non-decreasing sequence of objective values in each iteration. In particular, by denoting the objective value of the original problem (13) as , it follows that
where (b) holds because the maximum of the objective value of the original problem (13) is achieved when optimizing for any given . Similarly, (a) holds following the same reason as stated before. Therefore, the monotonically non-decreasing sequence for the objective value of the original problem (13) can be obtained. Moreover, because of limited resources, i.e., the bounded maximum transmit power budget of the BS and the maximum amplification power budget of the active IRS, has a finite upper bound; thus, it can converge to a stationary point.
| Algorithm 3 AO algorithm for the proposed scheme. |
|
3.3.2. Complexity Analysis
The computational complexity of solving the SDR for the problem (21) is [27], where is the convergence accuracy for problem (21), and the computational complexity of solving problem (40) is , where denotes the convergence accuracy for problem (40). Therefore, the complexity of the overall AO algorithm is
4. Numerical and Simulation Results
In this section, we present simulation and numerical results from evaluating the performance of the proposed scheme in an active-IRS-aided secure communication system with multiple colluding Eves. Unless specified otherwise, the simulation parameters of the proposed scheme are listed in Table 3. The locations of the k-th user and l-th Eve are randomly generated within 3 m of the center locations of (20,5) and (20,−5), respectively. All channels in the proposed scheme are assumed to follow Rician channels, and we take the channel as an example; it is shown below:
where dB is the large-scale path loss; is the path loss exponent; d is the distance in meters between the BS and the active IRS; is the Rician factor; is the line-of-sight link between the BS and the active IRS; and the non-line-of-sight (NLoS) link between the BS and the active IRS is denoted as in (43), where each entry follows the distribution . Moreover, for small-scale fading, the Rician factor of the active-IRS-related channels is 10, and that of the direct channels is 0 due to the unfavourable communication conditions in an urban environment. For large-scale fading, i.e., the LoS components, it is determined by multiplying the steering vectors of the transmitter with that of the receiver [27]. Other parameters are described in the specific simulation experiments. The benchmark schemes for comparison are as follows:

Table 3.
Values of simulation parameters [20,28].
- w/o an IRS [12]: We assume that no IRS is deployed, as compared with the proposed scheme. Then, we optimize the beamforming vector , of the BS to maximize the SSR. We set and to obtain simulation diagrams of this case.
- With a passive IRS [13]: We replace active IRS with passive IRS for the proposed scheme. Then, we optimize the beamforming vector of the BS and the phase shift matrix of the passive IRS to maximize the SSR. We set and to obtain simulation diagrams of this case.
- With an active IRS: the proposed scheme.
We first show the convergence behaviour of the proposed algorithm in Figure 3 by running the proposed algorithm once. Specifically, all curves are obtained by changing related parameters in the proposed algorithm. We can see in Figure 3 that our proposed algorithm demonstrates a favourable convergence behaviour, which verifies the validation of the proposed algorithm.

Figure 3.
Convergence behaviour of proposed algorithm.
Figure 4 shows the influence of the number of legitimate users on security performance. It can be seen that when the number of Eves remains constant and the number of users increases, the interference ability of the multiple colluding Eves will decrease compared to the cases of a passive IRS and w/o an IRS. In addition, Figure 4 shows that when the number of users k increases while the number of Eves remains constant, the SSR of the proposed scheme shows an increasing trend, and the proposed scheme is superior to other two baseline schemes. Specifically, when the number of users is 4, the SSR value of the proposed scheme is about and higher than in the cases with a passive IRS and without an IRS, respectively, which indicates that deploying an IRS in a wireless communication network can improve the SSR, especially when the power amplification of each element of the IRS is applied.

Figure 4.
The SSR values versus the number of users, k.
Figure 5 shows that when the number of Eves, l, increases, the SSR value of each scheme monotonically decreases. This is because when the number of users remains constant and the number of Eves increases, more colluding Eves can jointly eavesdrop on users and decode confidential information transmitted by the BS, which significantly degrades the system’s security performance. Although the SSR values of all schemes decrease, the proposed scheme is superior to the other baselines. Specifically, when the number of Eves is 4, the SSR value of the proposed scheme is about and higher than in the schemes with and without a passive IRS, respectively. Among the three schemes, our proposed active IRS method consistently outperforms the other two baseline schemes.
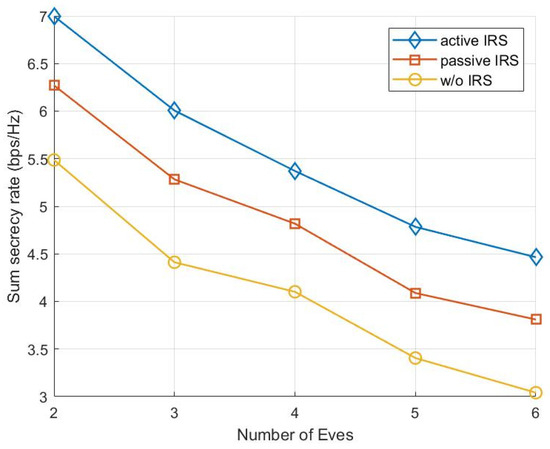
Figure 5.
The SSR values versus the number of Eves.
Figure 6 and Figure 7 depict SSR values versus the number of passive/active IRS elements and the number of antennas, respectively. From Figure 6, it can be seen that the SSR values of all IRS-aided schemes increase as the reflecting elements N increase. In particular, our proposed scheme outperforms other schemes, and we can see that when the numbers of elements are 8 and 40, the SSR values of the proposed scheme are about and higher than in the cases with a passive IRS and without a passive IRS, respectively. This result also indicates that increasing the number of reflecting elements can provide more adjustable links to enhance the SSR. From Figure 7, it can be seen that the SSRs of all schemes increase as the number of BS antennas M increases. In particular, we can see that when the number of antennas is 4, the SSR value of the proposed scheme is about and higher than in the cases with a passive IRS and without an IRS, respectively. This indicates that increasing the number of transmit antennas can significantly improve the SSR for all schemes because more transmit antennas can provide more spatial DoFs to realize strong beam-focusing for the specific user, thereby enhancing the SSR values.

Figure 6.
The SSR values versus the number of reflecting elements.

Figure 7.
The SSR values versus the number of antennas.
Figure 8 shows the SSR values versus the maximum power budget of the BS. We can notice that as the maximum transmit power increases, the SSR values of all schemes tend to increase. This is because a larger maximum transmit power budget at the BS leads to more DoFs for the optimization problem; thus, a higher SSR is achieved. Our proposed scheme is always superior to other benchmark schemes. In particular, when the maximum transmit power at the BS is 28 dBm, the SSR value of the proposed scheme is about and higher than in the schemes with and without a passive IRS, respectively. Compared with a passive IRS, an active IRS can overcome the fundamental limitation of the MFE. In other words, we can further optimize the power amplification of each element in an active IRS compared to a passive IRS. Simulation results show that the proposed scheme can enhance the values of the SSR in different scenarios with the assistance of the active IRS. These discussions demonstrate the effectiveness of the proposed scheme.

Figure 8.
The SSR values versus the maximum transmit power at the BS.
Although perfect CSI is assumed in the proposed scheme, we present Figure 9 to show the impact of imperfect CSI on the security performance of the proposed scheme. Specifically, we let all channels in the proposed scheme be , where the real channel can be replaced by , , , , and , used for denoting channels in our work, and and represents the estimated channel and the corresponding channel uncertainty error caused by inaccurate channel estimation, with being the bound of the channel uncertainty error, respectively. The bound can be set to , where denotes the CSI uncertainty level [29]. We can observe that the SSR values of all schemes decrease with an increasing CSI uncertainty level since the inaccurate channel estimation leads to difficulty in designing favourable beamformers for the BS and the active IRS. Although the SSR values of all schemes decrease, the proposed scheme is superior to other schemes. In addition, the performance saturation of the active IRS is achieved when the CSI uncertainty increases as compared with other schemes with a passive IRS and without an IRS, indicating that the introduction of an active IRS in the proposed scheme results in greater robustness compared with other schemes.

Figure 9.
The SSR values versus the channel uncertainty level, .
5. Conclusions
In this paper, we introduced an active IRS for secure wireless communications with multiple users and Eves and focused on investigating the potential of such a scenario with the help of the active IRS. For the non-convex problem formulated based on the AO algorithm, we first used the SDR method to deal with non-convex terms in an objective function for optimizing the beamforming vectors of the BS with any given beamforming matrix of the active IRS and then used the SCA method to transform the non-convex terms in the objective function into the convex terms for optimizing the beamforming matrix of the active IRS with any given beamforming vectors of the active IRS by applying a first-order Taylor expansion. Furthermore, numerical and simulation results verified that the active IRS in the proposed scheme can enhance SSR values in different settings when compared with other benchmark schemes, which shows that by deploying an active IRS in a scenario of secure resource allocation with multiple users and Eves, the security performance shows the most significant improvement when compared with schemes with and without a conventional passive IRS and different settings, such as numbers of users, Eves, reflecting elements, and BS antennas as well as the maximum transmit power budget of the BS.
Author Contributions
Conceptualization, J.X.; methodology, J.X. and Y.P.; software, J.X. and W.G.; validation, J.X. and Y.P.; formal analysis, J.X., Y.P. and R.Y.; investigation, J.X.; resources, Y.P., F.A.-H.,and M.M.M.; writing—original draft preparation, J.X.; writing—review and editing, Y.P., R.Y., W.G., F.A.-H. and M.M.M.; visualization, J.X.; supervision, Y.P.; project administration, Y.P.; funding acquisition, Y.P., F.A.-H. and M.M.M. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported in part by The Science and Technology Development Fund, Macau SAR (0108/2020/A3).
Data Availability Statement
No new data were created or analyzed in this study. Data sharing is not applicable.
Acknowledgments
The authors would like to acknowledge the Deanship of Graduate Studies and Scientific Research, Taif University, for funding this work.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Cui, T.J.; Qi, M.Q.; Wan, X.; Zhao, J.; Cheng, Q. Coding metamaterials, digital metamaterials and programmable metamaterials. Light. Sci. Appl. 2014, 3, e218. [Google Scholar] [CrossRef]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Di Renzo, M. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Pei, Y.; Liang, Y.C.; Zhang, L.; Teh, K.C.; Li, K.H. Secure communication over MISO cognitive radio channels. IEEE Trans. Wirel. Commun. 2010, 9, 1494–1502. [Google Scholar] [CrossRef]
- Cumanan, K.; Alexandropoulos, G.C.; Ding, Z.; Karagiannidis, G.K. Secure communications with cooperative jamming: Optimal power allocation and secrecy outage analysis. IEEE Trans. Veh. Technol. 2017, 66, 7495–7505. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.C. Secrecy wireless information and power transfer with MISO beamforming. IEEE Trans. Signal Process. 2014, 62, 1850–1863. [Google Scholar] [CrossRef]
- Nasir, A.A.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. Secrecy rate beamforming for multicell networks with information and energy harvesting. IEEE Trans. Signal Process. 2016, 65, 677–689. [Google Scholar] [CrossRef]
- Huang, Z.; Peng, Y.; Li, J.; Tong, F.; Zhu, K.; Peng, L. Secrecy Enhancing of SSK Systems for IoT Applications in Smart Cities. IEEE Internet Things J. 2021, 8, 6385–6392. [Google Scholar] [CrossRef]
- Zhu, H.; Peng, Y.; Xu, H.; Tong, F.; Jiang, X.Q.; Mirza, M.M. Secrecy Enhancement for SSK-Based Communications in Wireless Sensing Systems. IEEE Sens. J. 2022, 22, 18192–18201. [Google Scholar] [CrossRef]
- Cui, M.; Zhang, G.; Zhang, R. Secure wireless communication via intelligent reflecting surface. IEEE Wirel. Commun. Lett. 2019, 8, 1410–1414. [Google Scholar] [CrossRef]
- Ye, R.; Peng, Y.; Al-Hazemi, F.; Boutaba, R. A Robust Cooperative Jamming Scheme for Secure UAV Communication via Intelligent Reflecting Surface. IEEE Trans. Commun. 2024, 72, 1005–1019. [Google Scholar] [CrossRef]
- Zhang, Y.; Shen, Y.; Wang, H.; Yong, J.; Jiang, X. On secure wireless communications for IoT under eavesdropper collusion. IEEE Trans. Autom. Sci. Eng. 2015, 13, 1281–1293. [Google Scholar] [CrossRef]
- Choi, J.; Park, J. Sum secrecy spectral efficiency maximization in downlink MU-MIMO: Colluding eavesdroppers. IEEE Trans. Veh. Technol. 2021, 70, 1051–1056. [Google Scholar] [CrossRef]
- Wang, Y.; Shi, W.; Huang, M.; Shu, F.; Wang, J. Intelligent Reflecting Surface Aided Secure Transmission with Colluding Eavesdroppers. IEEE Trans. Veh. Technol. 2022, 71, 10155–10160. [Google Scholar] [CrossRef]
- Qiao, T.; Cao, Y.; Tang, J.; Zhao, N.; Wong, K.K. IRS-Aided Uplink Security Enhancement via Energy-Harvesting Jammer. IEEE Trans. Commun. 2022, 70, 8286–8297. [Google Scholar] [CrossRef]
- Xu, D.; Yu, X.; Sun, Y.; Ng, D.W.K.; Schober, R. Resource allocation for secure IRS-assisted multiuser MISO systems. In Proceedings of the 2019 IEEE Globecom Workshops (GC Wkshps), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Xu, D.; Yu, X.; Kwan Ng, D.W.; Schober, R. Resource Allocation for Active IRS-Assisted Multiuser Communication Systems. In Proceedings of the 2021 55th Asilomar Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 31 October–3 November 2021; pp. 113–119. [Google Scholar] [CrossRef]
- Guan, X.; Wu, Q.; Zhang, R. Intelligent Reflecting Surface Assisted Secrecy Communication: Is Artificial Noise Helpful or Not? IEEE Wirel. Commun. Lett. 2020, 9, 778–782. [Google Scholar] [CrossRef]
- Chen, J.; Liang, Y.C.; Pei, Y.; Guo, H. Intelligent Reflecting Surface: A Programmable Wireless Environment for Physical Layer Security. IEEE Access 2019, 7, 82599–82612. [Google Scholar] [CrossRef]
- Yang, H.; Xiong, Z.; Zhao, J.; Niyato, D.; Xiao, L.; Wu, Q. Deep Reinforcement Learning-Based Intelligent Reflecting Surface for Secure Wireless Communications. IEEE Trans. Wirel. Commun. 2021, 20, 375–388. [Google Scholar] [CrossRef]
- Zhang, Z.; Dai, L.; Chen, X.; Liu, C.; Yang, F.; Schober, R.; Poor, H.V. Active RIS vs. passive RIS: Which will prevail in 6G? IEEE Trans. Commun. 2022, 71, 1707–1725. [Google Scholar] [CrossRef]
- Lyu, B.; Zhou, C.; Gong, S.; Hoang, D.T.; Liang, Y.C. Robust Secure Transmission for Active RIS Enabled Symbiotic Radio Multicast Communications. IEEE Trans. Wirel. Commun. 2023, 22, 8766–8780. [Google Scholar] [CrossRef]
- Li, P.; Bian, J. Active RIS-Assisted Transmission Design for Wireless Secrecy Network with Energy Harvesting. Math. Probl. Eng. 2023, 2023, 8897781. [Google Scholar] [CrossRef]
- Chen, H.; Li, N.; Long, R.; Liang, Y.C. Channel Estimation and Training Design for Active RIS Aided Wireless Communications. IEEE Wirel. Commun. Lett. 2023, 12, 1876–1880. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Intelligent Reflecting Surface Enhanced Wireless Network: Joint Active and Passive Beamforming Design. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Grant, M.; Boyd, S. CVX: Matlab Software for Disciplined Convex Programming, Version 2.1. Available online: http://cvxr.com/cvx (accessed on 1 February 2024).
- Sun, Y.; Babu, P.; Palomar, D.P. Majorization-Minimization Algorithms in Signal Processing, Communications, and Machine Learning. IEEE Trans. Signal Process. 2017, 65, 794–816. [Google Scholar] [CrossRef]
- Yu, X.; Xu, D.; Sun, Y.; Ng, D.W.K.; Schober, R. Robust and Secure Wireless Communications via Intelligent Reflecting Surfaces. IEEE J. Sel. Areas Commun. 2020, 38, 2637–2652. [Google Scholar] [CrossRef]
- Zhou, G.; Pan, C.; Ren, H.; Wang, K.; Renzo, M.D.; Nallanathan, A. Robust Beamforming Design for Intelligent Reflecting Surface Aided MISO Communication Systems. IEEE Wirel. Commun. Lett. 2020, 9, 1658–1662. [Google Scholar] [CrossRef]
- Zhou, G.; Pan, C.; Ren, H.; Wang, K.; Nallanathan, A. A Framework of Robust Transmission Design for IRS-Aided MISO Communications With Imperfect Cascaded Channels. IEEE Trans. Signal Process. 2020, 68, 5092–5106. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).