Abstract
The memristor, a revolutionary electronic component, mimics both neural synapses and electromagnetic induction phenomena. Recent study challenges are the development of effective neural models and discovering their dynamics. In this study, we propose a novel Hopfield neural network model leveraging multistable memristors, showcasing its efficacy in encoding biomedical images. We investigate the equilibrium states and dynamic behaviors of our designed model through comprehensive numerical simulations, revealing a rich array of phenomena including periodic orbits, chaotic dynamics, and homogeneous coexisting attractors. The practical realization of our model is achieved using a microcontroller, with experimental results demonstrating strong agreement with theoretical analyses. Furthermore, harnessing the chaos inherent in the neural network, we develop a robust biomedical image encryption technique, validated through rigorous computational performance tests.
1. Introduction
Hopfield networks have emerged as pivotal models in the field of neuroscience owing to their dynamic behavior and efficient structure [1]. These networks provide a valuable framework for exploring human memory mechanisms, with both continuous and discrete models being extensively studied [2,3,4]. Their practicality lies in their ability to capture associative memory processes, making them indispensable tools for investigating cognition and learning [5,6,7,8].
Recent research has exposed an overabundance of intriguing dynamics within memristor-based Hopfield networks. Notably, Sun et al. introduced the concept of boosting dynamics, amplifying the network’s computational capabilities [9]. Investigations into multistability have shed light on the diverse states these networks can exhibit, offering potential avenues for information storage and retrieval [8,10]. Furthermore, the exploration of chaos and multiple scrolls in memristor-cascaded Hopfield networks underscores their rich dynamical repertoire [11,12,13]. Symmetric behaviors observed in bi-neuron Hopfield networks hint at their robustness and potential for pattern recognition tasks [14]. Synapse-coupled architectures have revealed intriguing phenomena such as initial sensitivity, further enhancing our understanding of network dynamics [15]. Additionally, the incorporation of hidden neurons has bolstered the recognition abilities of Hopfield models, paving the way for more sophisticated cognitive architectures capable of long-term memory storage [16,17,18,19].
The attraction of Hopfield networks lies not only in their theoretical elegance but also in their myriad practical applications. Image encryption utilizing Hopfield networks has garnered considerable attention due to its promise of robust security and efficient encoding schemes [20,21,22,23]. Beyond encryption, these networks have found utility in various artificial intelligence applications, harnessing their associative memory properties for tasks such as pattern recognition and optimization [24]. Implementation-wise, the realization of both continuous and discrete Hopfield networks has been achieved using diverse hardware platforms, ranging from STM32 microcontrollers to DSPs and analog circuits [25,26]. In other papers, authors focus on optimizing the realization of Hopfield networks through both analog and digital circuit implementations, aiming to harness the full potential of these networks in practical applications [27,28,29,30].
This paper introduces a novel approach to a coupled bi-Hopfield network, unraveling its dynamics and laying the groundwork for its practical deployment. By delving into the intricacies of network realization and dynamics, we aim to facilitate its application. A comparison of this work related to published ones is made in Table 1.

Table 1.
A comparison of this work related to published ones.
2. System Description and Mathematical Model
In this work, we consider a multi-state flux-controlled memristor described as
where is the memductance.
In order to characterize the elaborated memristor described above, we apply an external force into the memristor. The I-V characteristics of the considered memristor are presented in Figure 1. All system parameter values are given in the figure caption. From Figure 1c, we can remark that the hysteresis loop areas retain the same shapes and the characteristic has different states depending on the initial conditions. Thus, the considered memristor is multistable.
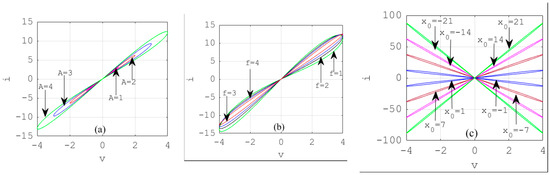
Figure 1.
I-V characteristics of the considered memristor. (a) A = 1 V, 2 V, 3 V, 4 V and f = 1 Hz; (b) f = 1 Hz, 2 Hz, 3 Hz, 4 Hz and A = 4 V. The initial state ; (c) initial states: x0 = ±1, ±7, ±14, ±21, A = 4 V and f = 1 Hz.
We use the multi-state flux-controlled memristor described above to couple two neurons, as shown in Figure 2.
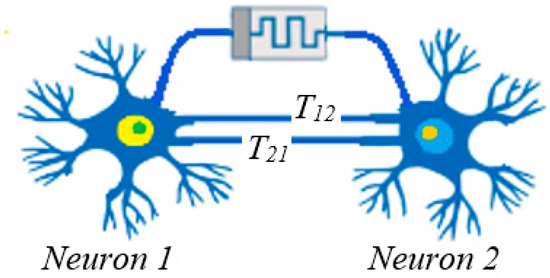
Figure 2.
The designed multistable memristor synapse-based coupled bi-Hopfield neuron model.
In Figure 2, an electromagnetic induction current, created by the difference in membrane potential between the two neurons, flows between the two neurons. This electromagnetic induction current influences the two neurons, and the state equations can be expressed as follows
The parameters , , , and represent the synaptic connection weights considering constant. represents the memristor coupling strength parameter, and are applied to activate the neurons and expressed as
By taking a synaptic weight matrix as follows
We obtain the multistable memristor synapse-based coupled bi-Hopfield neuron model as
In system (5), the auto-connection weights for the two Hopfield neurons are set to zero in order to simplify the final model.
3. Equilibrium Analysis
The equilibrium can be expressed as
in which , and are solved using the following equations
where and are the functions used to activate the neurons.
The Jacobin matrix can be calculated at as
in which .
According to Equation (7), the features of the equilibrium states are studied based on the system parameters and . The two functions and given in Equation (7) with the parameters are plotted in Figure 3. The values of and are determined at the intersections of the two function curves.
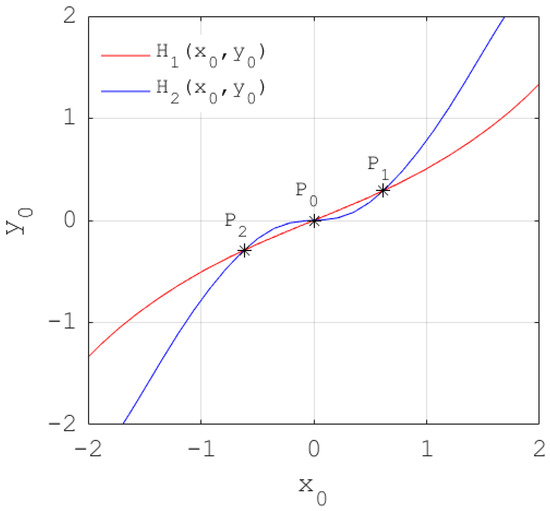
Figure 3.
Determination of the equilibrium states and , which are indicated by the intersections of two function curves.
From Figure 3, system (5) has three equilibrium states for . The analysis of these equilibrium states is presented in Table 2.

Table 2.
Equilibria and their stability.
From the results in Table 2, we can conclude that the equilibrium points are unstable saddle points for the considered values of the system parameters and .
4. Numerical Study
Bifurcation diagrams associated with corresponding Lyapunov exponents as a function of system parameters, as well as initial states, phase portraits, and basin of attraction, are computed to illustrate the complicated behaviors of the model under consideration.
Figure 4 shows the bifurcation diagram and Lyapunov exponents versus computed from 1 to 2, for and .
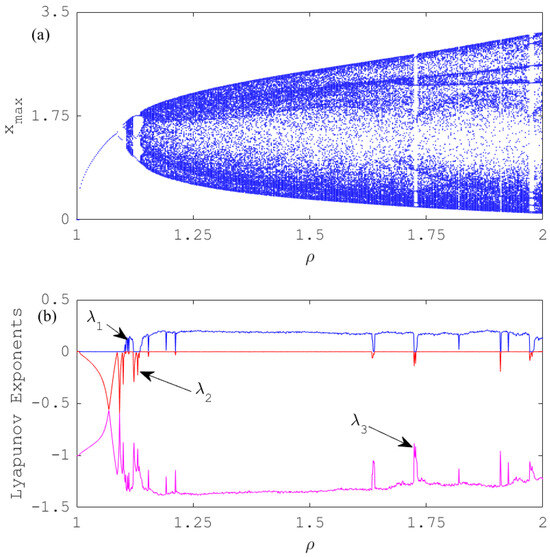
Figure 4.
Influence of on the behaviors of the model: (a) bifurcation diagram (b) Lyapunov exponents for and .
Figure 4 reveals that chaos occurs in the considered model through period-doubling bifurcation. We can identify some windows indicating periodic oscillations intercalated by chaos. The route to chaos is confirmed by plotting phase spaces presented in Figure 5, for and diverse selected values of .
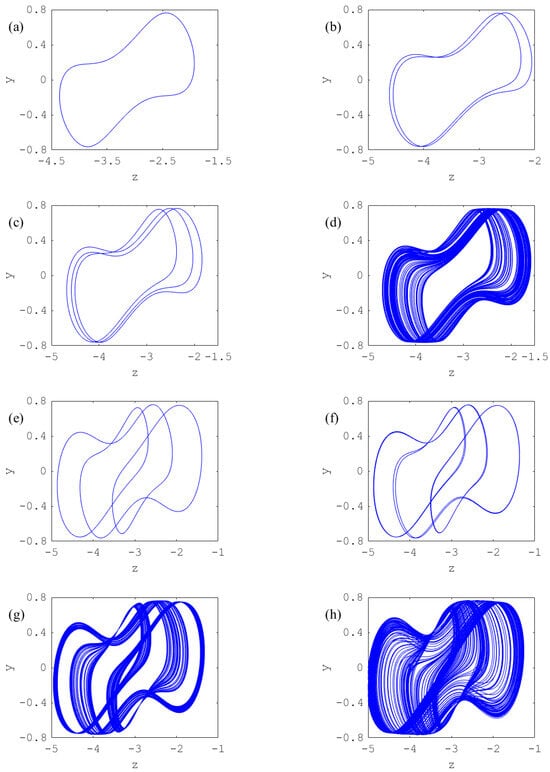
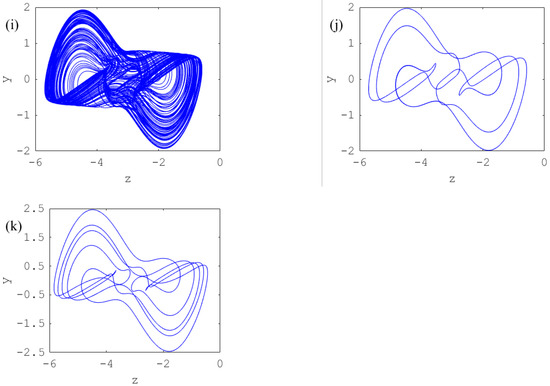
Figure 5.
Phase spaces confirming the occurrence of chaos in the system for , and diverse selected values of : (a) period-1 for , (b) period-2 for , (c) period-3 for , (d) chaos for , (e) period-3 for , (f) period-6 for , (g) chaos for , (h) chaos for , (i) chaos for , (j) period-3 for , (k) period-6 for .
It is very clear from Figure 5 that the system in the study displays complex and abundant patterns.
The impact of the initial state associated with the memristor on the comportments of the model is shown in Figure 6, for and .
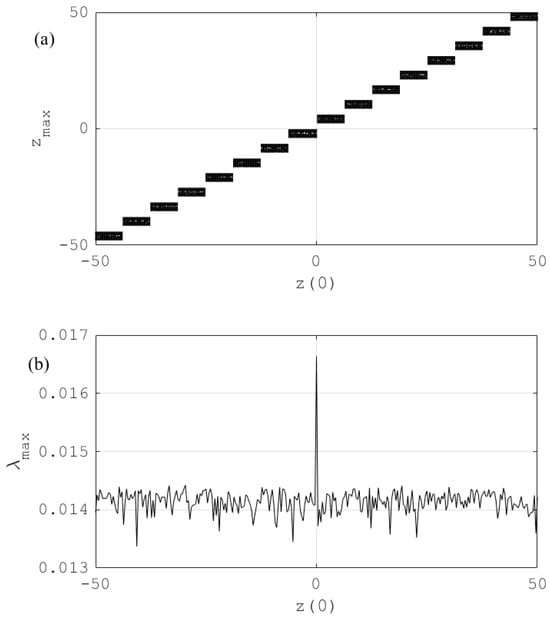
Figure 6.
Impact of the initial state on the comportment of the model: (a) bifurcation diagram and (b) maximum Lyapunov exponent, for , , and .
The initial state considerably impacts the dynamic behavior of the considered model (see Figure 6).
Phase portraits and basin of attraction are shown in Figure 7 and Figure 8 in order to support the result carried out in Figure 6, for and .
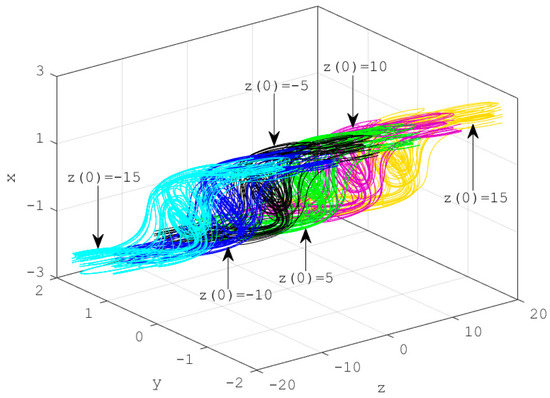
Figure 7.
Several coexisting chaotic attractors at diverse positions for several value initial states with , , and .
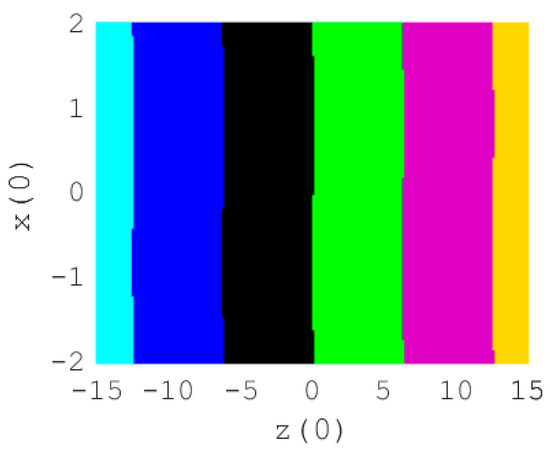
Figure 8.
Cross section of the basin of attraction for , , and . Each domain of initial states leads to a color representing a particular phase space.
5. Experimental Study
We carried out here a microcontroller implementation of the system. Implementing chaotic systems using microcontrollers has many advantages over using electronic components. These advantages include high computing performances, excellent precision, flexibility and stability, and the facility to manage the system parameters conveniently [25,26,27,28,29]. In this work, we use an Arduino Due microcontroller card, which is constructed with an Atmel SAM3X8E ARM Cortex-M3 processor having a clock frequency of 84 MHz. Compared with other boards, this card has the advantage of incorporating two digital-to-analog converters, which makes it easy to implement chaotic systems. The main steps, which describe the implementation procedure of the elaborated multistable memristor synapse-based coupled bi-Hopfield neuron model, are shown in Figure 9.
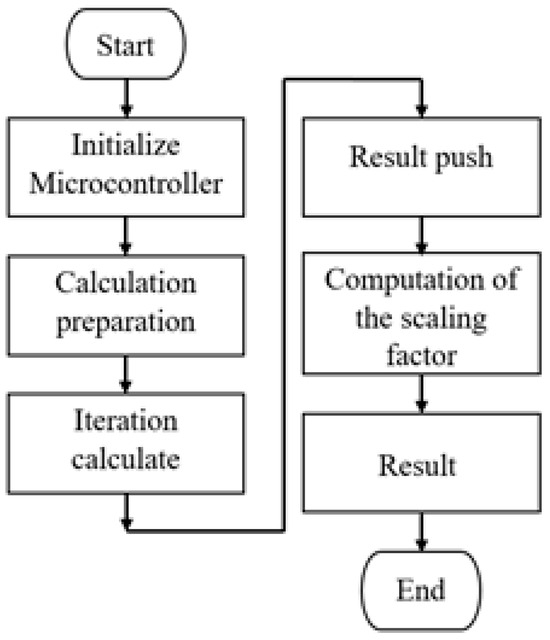
Figure 9.
Implementation procedure of the elaborated multistable memristor synapse-based coupled bi-Hopfield neuron model.
The microcontroller implements the discrete form of system (5) using the Runge–Kutta algorithm with a fixed iteration step size of 0.01. The model parameters and initial conditions are chosen as they have identical values to those used in the numerical simulations. The hardware implementation devices are shown in Figure 10.
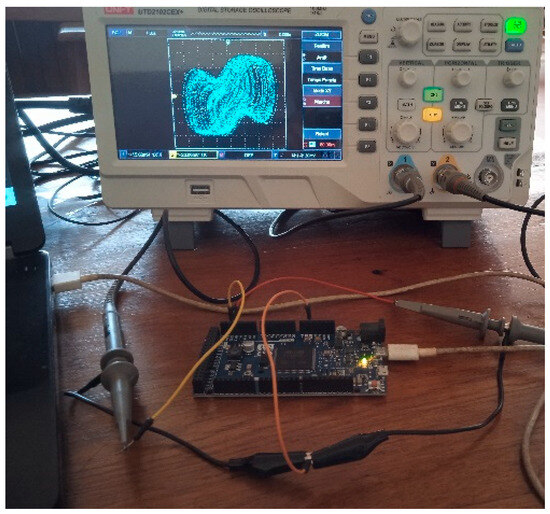
Figure 10.
Hardware implementation devices. The dual-channel digital oscilloscope displays a chaotic attractor in the plane () for , , and .
Figure 11 shows the route to chaos for a fixed value of and specific values of the coupling strength .
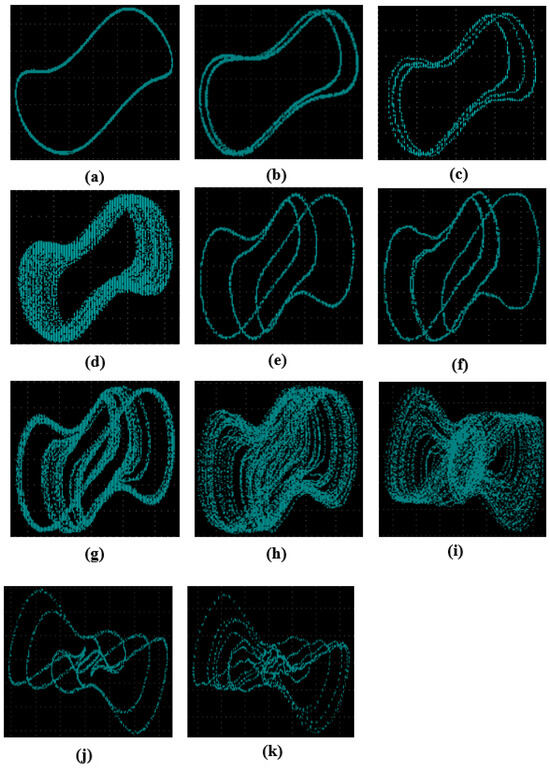
Figure 11.
Phase portraits for and specific values of the coupling strength : (a) period-1 for , (b) period-2 for , (c) period-3 for , (d) chaos for , (e) period-3 for , (f) period-6 for , (g) chaos for , (h) chaos for , (i) chaos for , (j) period-3 for , (k) period-6 for , and .
The results carried out from the microcontroller implementation (see Figure 11) are very similar to those obtained from numerical simulations (see Figure 5). This confirms that the Arduino Due microcontroller card is able to investigate the complete dynamics of the designed multistable memristor synapse-based coupled bi-Hopfield neuron model.
6. Application of the Designed Model for Biomedical Encryption Image
We exploit here the abundant dynamics of the elaborated model for image encryption.
6.1. Designing of Encryption Algorithm
Figure 12 presents the encryption algorithm.
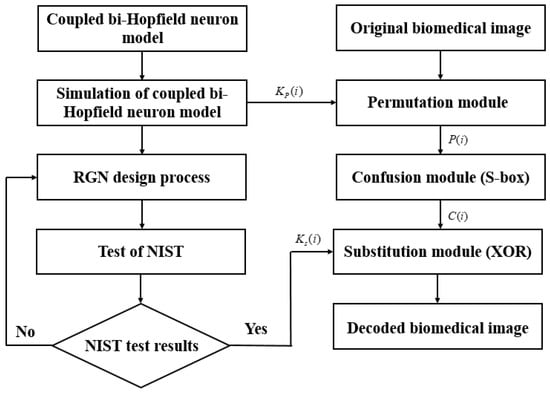
Figure 12.
Complete diagram of the encryption algorithm.
There are five steps in the algorithm:
- (1)
- Integrate the chaotic system and carry out the public key ;
- (2)
- Generate and test the random bits to construct the key ;
- (3)
- In the layer of permutation, build the permuted image with the initial image and the public key ;
- (4)
- Introduce the permuted image into the layer of confusion, which works with the S-box function to construct the confused image ;
- (5)
- Using a substitution operation (XOR), combine the image resulting from the confusion layer with the key to obtain the masked image.
For the decryption process, we apply the reverse of all operations realized during the encryption procedure.
The NIST test results are shown in Table 3.

Table 3.
NIST test results.
6.2. Numerical Results
The numerical results are carried out in MATLAB16b environment. We use biomedical images of size 256 × 256 for cerebrovascular accident, pulmonary fibrosis, and lung cancer. Applying the encryption and decryption algorithm described below, the results for encrypted and decrypted biomedical images are shown in Figure 13.


Figure 13.
Numerical results: (a) initial image of cerebrovascular accident, (b) initial image of pulmonary fibrosis, (c) initial image of lung cancer, (d) encrypted image of cerebrovascular accident, (e) encrypted image of pulmonary fibrosis, (f) encrypted image of lung cancer, (g) decrypted image of cerebrovascular accident, (h) decrypted image of pulmonary fibrosis, (i) decrypted image of lung cancer.
6.3. Analysis of Performances of the Elaborated Biomedical Image Encryption Method
6.3.1. Analysis of Key Space and Key Sensibility
To withstand exhaustive attacks, the key space of the cryptosystem must exceed [31]. Our elaborated multistable memristor synapse-based coupled bi-Hopfield neuron model involves two constant system parameters and three initial states. For a precision of , the key space is , which exceeds the required value. This confirms that the developed algorithm will be able to withstand exhaustive attacks.
The key sensitivity is analyzed by introducing a small perturbation of to all parameters of the system before the decryption of the sending image (cerebrovascular accident), as reported in Figure 14.
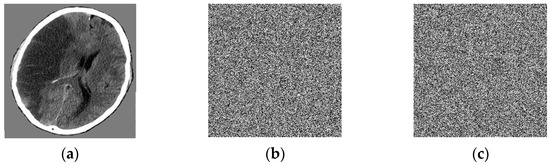
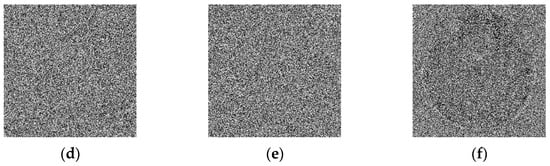
Figure 14.
Results of slight key modification: (a) correct keys, (b) , (c) , (d) , (e) , and (f) .
Looking at Figure 14, the key changes , generating a high impact on the decrypted image. The initial image can no longer be received after a small key modification. We can conclude that this algorithm is very sensitive to secret keys.
6.3.2. Information Entropy
The entropy is examined using its expression [32]
in which and refer to the total number and frequency of occurrences of symbol , respectively.
The entropy is reported in Table 4, and its value for encrypted images approaches the standard value 8, which means that the encrypted image is more random. This confirms the good performance of the scheme.

Table 4.
Information entropies of initial images and their corresponding encrypted versions.
6.3.3. Correlation Analysis
The correlation coefficient (CC) is calculated using its expression [33]
in which x and y are the pixel values. The CC is reported in Table 5.

Table 5.
Computed correlation coefficients.
Looking at the values in Table 5, we can remark that the values of correlation coefficient in horizontal, vertical, and diagonal directions of the image approach the standard values (i.e., CC is 1 for initial biomedical images and 0 for their encrypted versions). This means that the correlation coefficients of the initial image are highly correlated and those for the encrypted image are uncorrelated. In conclusion, the designed encryption algorithm will resist statistical aggressions.
6.3.4. Histogram Study
The histogram should dispose uniformly for an encrypted image and randomly for an unencrypted one. Figure 15 illustrates the distribution of the pixels of biomedical images.
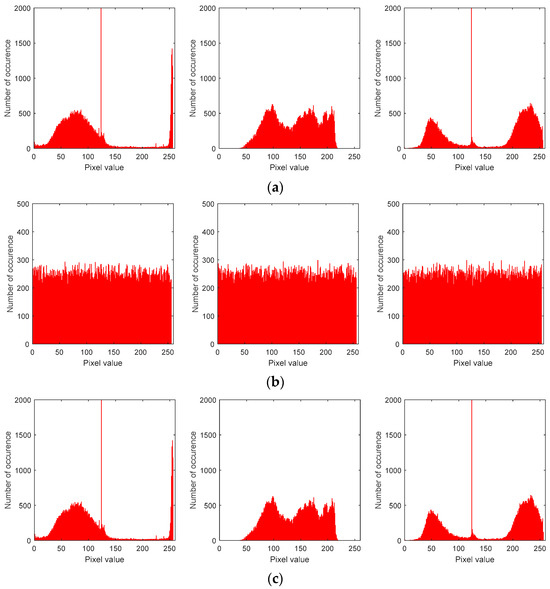
Figure 15.
The distribution of the pixels of the unencrypted images (a), encrypted images (b), and decrypted images (c).
From Figure 15, we can see that the histograms of the unencrypted images and those of the encrypted ones are completely different. The distribution of the pixels of the initial image is random and the one of the encrypted image is uniform, respecting the above characteristics. Thus, the biomedical image encryption system can resist differential attacks.
6.3.5. Impacts of External Perturbations and Information Loss on the Performances of the Scheme
Every encryption system is subjected to external perturbations and information loss. Therefore, it is necessary to study their impacts on the performance of the encryption system. Two different external perturbations, namely, Gaussian and Salt and Pepper noise, are subjected to the initial images before using them in the encryption system. The results for decrypted images are shown in Figure 16(a2(i)–a2(iii)) for Gaussian noise and Figure 16(b2(i)–b2(iii)) for Salt and Pepper noise. The intensity of each noise is indicated in the figure caption. Similarly, a part of the unencrypted image (see Figure 16(c1(i)–c1(iii)) is canceled before encryption. Figure 16(c2(i)–c2(iii)) present decrypted images. The percentage of the canceled data is indicated in the figure caption.
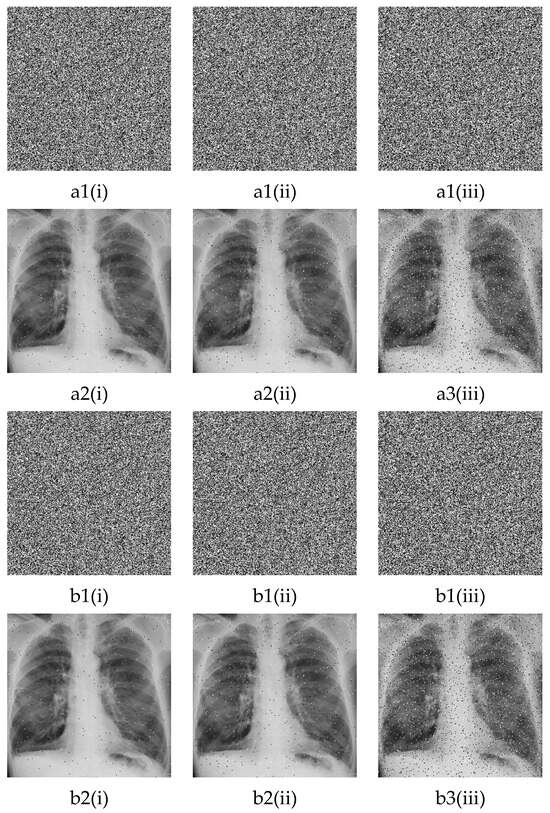
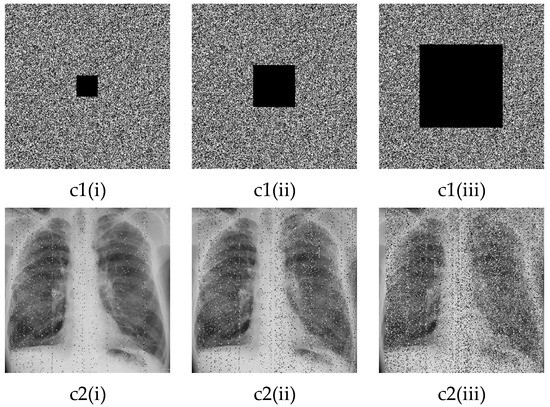
Figure 16.
Impacts of external perturbations and information loss on the performances of the algorithm: (a1(i)–a1(iii)) encrypted images with , , and Gaussian noise, respectively. (a2(i)–a2(iii)) corresponding decrypted images. (b1(i)–b1(iii)) encrypted images with , , and salt and pepper noise, respectively. b2(i)–b2(iii) corresponding decrypted images. (c1(i)–c1(iii)) encrypted image with , , and information loss, respectively. (c2(i)–c2(iii)) corresponding decrypted images.
From Figure 16, we observe that, although a part of the initial image has been canceled and the noise has been subjected to the encryption system, the decrypted images remain exploitable. These results mean that the designed encryption algorithm has the ability to prevent noise and occlusion attacks.
6.3.6. NPCR and UACI Analysis
The performance of an encryption system is influenced by differential attacks. Common methods called NPCR and UACI are used to study their effects on the encryption system. They are expressed as [34]:
in which is defined by:

Table 6.
NPCR and UACI test results.
From the data in Table 6, we can conclude that the encryption system is impacted by small modifications of the image’s pixels. This means that the studied image encryption algorithm has a strong capacity to resist differential attacks.
6.3.7. Comparison of this Scheme with Certain Recent Encryption Methods
The performance of the image encryption scheme is compared with that of certain recent studies and the comparisons are recorded in Table 7.

Table 7.
Comparison of this image encryption scheme with certain recent encryption methods.
7. Conclusions
We designed a Hopfield neural network with a multistable memristor and its use for encoding biomedical image encryption. The equilibrium states, their stability, and the dynamics of the model were studied. Numerical simulations revealed that the model exhibits abundant and complicated comportments such as periodic orbits, chaos, and homogenous coexisting chaotic attractors. The model was realized using a microcontroller board. Numerical results and those obtained from the microcontroller looked very similar. The attractive behaviors of the Hopfield neural network were used to construct a scheme to mask images of cerebrovascular accidents, pulmonary fibrosis, and lung cancer. The performance of the scheme was verified by computing different statistical and security tests.
In future work, to construct a high-order neural network model that is closer to the biological one, we will use a non-polynomial memristor to couple two sub-neural networks. The two sub-neural networks will represent two different encephalic regions in the brain.
Author Contributions
Conceptualization, V.K.T.; Investigation, A.L.M.B.; Methodology, V.K.T.; Resources, V.-T.P.; Software, A.L.M.B.; Visualization, G.G.; Writing—original draft, V.-T.P.; Writing—review and editing, G.G. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Gerstner, W.; Kistler, W.M.; Naud, R.; Paninski, L. Neuronal Dynamics: From Single Neurons to Networks and Models of Cognition; Cambridge University Press: Cambridge, UK, 2014. [Google Scholar] [CrossRef]
- Yu, Z.; Abdulghani, A.M.; Zahid, A.; Heidari, H.; Imran, M.A.; Abbasi, Q.H. An overview of neuromorphic computing for artificial intelligence enabled hardware-based hopfield neural network. IEEE Access 2020, 8, 67085–67099. [Google Scholar] [CrossRef]
- Sun, J.; Sathasivam, S.; Ali, M.K.B.M. Analysis and Optimization of Network Properties for Bionic Topology Hopfield Neural Network Using Gaussian-Distributed Small-World Rewiring Method. IEEE Access 2022, 10, 95369–95389. [Google Scholar] [CrossRef]
- Tsodyks, M.V. Hierarchical associative memory in Neural Networks with Low Activity Level. Mod. Phys. Lett. B 1990, 4, 259–265. [Google Scholar] [CrossRef]
- Miller, N.E.; Mukhopadhyay, S. A quantum Hopfield associative memory implemented on an actual quantum processor. Sci. Rep. 2021, 11, 23391. [Google Scholar] [CrossRef] [PubMed]
- Alway, A.; Zamri, N.E.; Mansor, M.A.; Kasihmuddin, M.S.M.; Jamaludin, S.Z.M.; Marsani, M.F. A novel Hybrid Exhaustive Search and data preparation technique with multi-objective Discrete Hopfield Neural Network. Decis. Anal. J. 2023, 9, 100354. [Google Scholar] [CrossRef]
- Karpov, Y.L.; Karpov, L.E.; Smetanin, Y.G. Some Aspects of Associative Memory Construction Based on a Hopfield Network. Program. Comput. Softw. 2020, 46, 305–311. [Google Scholar] [CrossRef]
- Huang, L.L.; Zhang, Y.; Xiang, J.H.; Liu, J. Extreme Multistability in a Hopfield Neural Network Based on Two Biological Neuronal Systems. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 4568–4572. [Google Scholar] [CrossRef]
- Sun, L.; Luo, J.; Qiao, Y. Initial Offset Boosting Dynamics in A Memristive Hopfield Neural Network and Its Application in Image Encryption. Jisuan Wuli/Chin. J. Comput. Phys. 2023, 40, 106. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Tan, Y. Hidden extreme multistability with hyperchaos and transient chaos in a Hopfield neural network affected by electromagnetic radiation. Nonlinear Dyn. 2020, 99, 2369–2386. [Google Scholar] [CrossRef]
- Lin, H.; Wang, C.; Yao, W.; Tan, Y. Chaotic dynamics in a neural network with different types of external stimuli. Commun. Nonlinear Sci. Numer Simul. 2020, 90, 105390. [Google Scholar] [CrossRef]
- Li, R.; Dong, E.; Tong, J.; Wang, Z. A Novel Multiscroll Memristive Hopfield Neural Network. Int. J. Bifurc. Chaos 2022, 32, 2250130. [Google Scholar] [CrossRef]
- Chen, C.; Min, F.; Cai, J.; Bao, H. Memristor Synapse-Driven Simplified Hopfield Neural Network: Hidden Dynamics, Attractor Control, and Circuit Implementation. IEEE Trans. Circuits Syst. I Regul. Pap. 2024, 71, 2308–2319. [Google Scholar] [CrossRef]
- Chen, C.; Min, F. Memristive bi-neuron Hopfield neural network with coexisting symmetric behaviors. Eur. Phys. J. Plus 2022, 137, 841. [Google Scholar] [CrossRef]
- Biamou, A.L.M.; Tamba, V.K.; Kuate, G.C.G.; Tagne, F.K.; Takougang, A.C.N.; Fotsin, H.B. Initial states-induced complex behaviors in a memristive coupled Hopfield neural network model and its application in biomedical image encryption. Phys. Scr. 2024, 99, 015215. [Google Scholar] [CrossRef]
- Benedetti, M.; Dotsenko, V.; Fischetti, G.; Marinari, E.; Oshanin, G. Recognition capabilities of a Hopfield model with auxiliary hidden neurons. Phys. Rev. E 2021, 103, L060401. [Google Scholar] [CrossRef]
- Wen, L.; Ong, C.K. Study of Short-Term and Long-Term Memories by Hodgkin-Huxley Memristor. Int. J. Bifurc. Chaos 2024, 34, 2450040. [Google Scholar] [CrossRef]
- Chen, C.; Min, F.; Zhang, Y.; Bao, B. Memristive electromagnetic induction effects on Hopfield neural network. Nonlinear Dyn. 2021, 106, 2559–2576. [Google Scholar] [CrossRef]
- Li, C.; Yang, Y.; Yang, X.; Zi, X.; Xiao, F. A tristable locally active memristor and its application in Hopfield neural network. Nonlinear Dyn. 2022, 108, 1697–1717. [Google Scholar] [CrossRef]
- Isaac, S.D.; Njitacke, Z.T.; Tsafack, N.; Tchapga, C.T.; Kengne, J. Novel compressive sensing image encryption using the dynamics of an adjustable gradient Hopfield neural network. Eur. Phys. J. Spec. Top. 2022, 231, 1995–2016. [Google Scholar] [CrossRef]
- Deng, Q.; Wang, C.; Lin, H. Chaotic dynamical system of Hopfield neural network influenced by neuron activation threshold and its image encryption. Nonlinear Dyn. 2024, 112, 1–18. [Google Scholar] [CrossRef]
- Xu, S.; Wang, X.; Ye, X. A new fractional-order chaos system of Hopfield neural network and its application in image encryption. Chaos Solitons Fractals 2022, 157, 111889. [Google Scholar] [CrossRef]
- Venkatesh, J.; Pchelintsev, A.N.; Karthikeyan, A.; Parastesh, F.; Jafari, S. A Fractional-Order Memristive Two-Neuron-Based Hopfield Neuron Network: Dynamical Analysis and Application for Image Encryption. Mathematics 2023, 11, 4470. [Google Scholar] [CrossRef]
- Ji, Y.; Wang, L.; Xie, D. Balance optimization method of energy shipping based on Hopfield neural network. Alex. Eng. J. 2023, 67, 171–181. [Google Scholar] [CrossRef]
- Bao, H.; Ding, R.; Liu, X.; Xu, Q. Memristor-cascaded hopfield neural network with attractor scroll growth and STM32 hardware experiment. Integration 2024, 96, 102164. [Google Scholar] [CrossRef]
- Ma, T.; Mou, J.; Yan, H.; Cao, Y. A new class of Hopfield neural network with double memristive synapses and its DSP implementation. Eur. Phys. J. Plus 2022, 137, 1135. [Google Scholar] [CrossRef]
- Tlelo-Cuautle, E.; Díaz-Muñoz, J.D.; González-Zapata, A.M.; Li, R.; León-Salas, W.D.; Fernández, F.V.; Guillén-Fernández, O.; Cruz-Vega, I. Chaotic image encryption using hopfield and hindmarsh–rose neurons implemented on FPGA. Sensors 2020, 20, 1326. [Google Scholar] [CrossRef]
- Yu, F.; Lin, Y.; Xu, S.; Yao, W.; Gracia, Y.M.; Cai, S. Dynamic Analysis and FPGA Implementation of a New Fractional-Order Hopfield Neural Network System under Electromagnetic Radiation. Biomimetics 2023, 8, 559. [Google Scholar] [CrossRef]
- Chen, C.; Min, F.; Hu, F.; Cai, J.; Zhang, Y. Analog/digital circuit simplification for Hopfield neural network. Chaos Solitons Fractals 2023, 173, 113727. [Google Scholar] [CrossRef]
- Chen, C.; Min, F.; Zhang, Y.; Bao, H. ReLU-type Hopfield neural network with analog hardware implementation. Chaos Solitons Fractals 2023, 167, 113068. [Google Scholar] [CrossRef]
- Seyedzadeh, S.M.; Mirzakuchaki, S. A fast color image encryption algorithm based on coupled two-dimensional piecewise chaotic map. Signal Process 2012, 92, 1202–1215. [Google Scholar] [CrossRef]
- Zhu, S.; Zhu, C. Image encryption algorithm with an avalanche effect based on a six-dimensional discrete chaotic system. Multimed. Tools Appl. 2018, 77, 29119–29142. [Google Scholar] [CrossRef]
- Gao, T.G.; Chen, Z.Q. A new image encryption algorithm based on hyper-chaos. Phys. Lett. A 2008, 372, 394–400. [Google Scholar] [CrossRef]
- Behnis, S.; Akhshani, A.; Ahadpour, S.; Mahnodi, H.; Akhavan, A. A fast-chaotic encryption scheme based on piecewise nonlinear chaotic maps. Phys. Lett. A 2007, 366, 391–396. [Google Scholar] [CrossRef]
- Faragallah, O.S. Efficient confusion–diffusion chaotic image cryptosystem using enhanced stan-dard map. SIViP 2015, 9, 1917–1926. [Google Scholar] [CrossRef]
- De Dieu, N.J.; Ruben FS, V.; Nestor, T.; Zeric, N.T.; Jacques, K. Dynamic analysis of a novel chaotic system with no linear terms and use for DNA-based image encryption. Multimed. Tools Appl. 2022, 81, 10907–10934. [Google Scholar] [CrossRef]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers. Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]
- Wei, X.; Guo, L.; Zhang, Q.; Zhang, J.; Lian, S. A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J. Syst. Softw. 2012, 85, 290–299. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).