Abstract
Data security and privacy have become essential due to the increasingly advanced interconnectivity in today’s world, hence the reliance on cryptography. This paper introduces a new algorithm that uses a novel hybrid Tent–May chaotic map to generate pseudo-random numbers, as well as block encryption. We design a robust S-box by combining the Tent and May Maps, which yields a chaotic system with improved cryptographic properties. This S-box is a critical cryptographic primitive that significantly improves encryption security and leverages the strengths of both maps. The encryption process involves two key steps: block-wise substitution and permutation. First, we divide the image into blocks, then substitute each pixel with the key and S-box. Next, we convert the encrypted image back into vector form, reorganize it using the permutation vector based on the subgroups of , and finally return it to its original form. This approach greatly improves block cipher security when used, especially to protect medical images by guaranteeing their confidentiality and noninterference. Performance measures like PSNR, UACI, MSE, NCC, AD, SC, MD, and NAE prove how immune our method is to various cryptographic and statistical attacks, making it more accurate and more secure than the existing techniques.
Keywords:
group structure; block ciphers; Galois fields cryptography; medical images; chaotic map; S-box MSC:
11T71; 13B25
1. Introduction
The Internet has greatly benefited humanity, mostly by offering a platform for virtual environments. In today’s world, all sectors are making vigorous efforts to virtualize their activities by employing web apps. Despite the general positive perception of the Internet and web apps, they are also associated with illegal activities like online identity theft and fraudulent purchases. Consequently, academia has developed a strong interest in enhancing the security and reliability of the Internet and online applications. Currently, there is a convergence of telemedicine technologies with Internet technologies, leading to the steady development of e-medicine [1]. The human body is subject to computerized tomography, ultrasound, magnetic resonance imaging, and other technologies to assess the condition of different organs and bones [2,3]. The Internet then transfers the image data [4]. Doctors utilize telemedicine technology to assist in diagnosing patients, effectively overcoming the obstacle of distance in delivering medical care [5]. Medical images necessitate a heightened level of security in comparison to regular photographs [6,7]. Medical photographs can compromise patient privacy, and inadequate security of medical image information can lead to issues such as the deterioration of the doctor–patient relationship [8,9]. Medical images have inherent attributes such as a large volume of data, diminished contrast, and an irregular grayscale [10,11,12]. In general, only authorized individuals have access to medical pictures. Furthermore, it is crucial to maintain the integrity of the image’s information during the doctor’s examination [3]. The unauthorized theft or use of confidential medical photographs might have severe repercussions [13]. Several studies [14,15,16,17] have demonstrated the widespread use of the chaos-based encryption method among currently known encryption algorithms. The spatiotemporal chaotic system is particularly suitable for medical imaging because of its high security requirements. This system demonstrates superior security characteristics and provides greater utility in this context [18,19,20]. Some of the latest works relate to the use of chaotic systems for image encryption, and the results show the possibility of encrypting data for transmission. Wei et al. [21] have designed a secure image encryption algorithm using hyperchaotic and the bit-level permutation while Al Sibahee et al. [22] have used a lightweight hyperchaotic map and the conditional least significant bits to hide scrambled text messages in speech signals. Rehman [23] discussed a new quantum-based method for image encryption based on the 1D sine-based chaotic maps and quantum coding. Other researchers have studied the application of chaotic maps integrated with other methods to increase the level of security of images. Abduljabbar et al. [24] presented a fast and secure method of color image encryption by using S-boxes and hyperchaotic maps and Hazzazi et al. [25] present a strong method to encrypt data using chaotic maps, Fibonacci and Tribonacci transformations, and DWT diffusion. Abduljaleel et al. [26] proposed a lightweight hybrid method to embed text messages into color images using LSB, Lah transform, and chaotic methods. Some other types of message maps have also been examined for image encryption with a view to ascertaining their utility. Riaz et al. [27] proposed a novel encryption model that possesses high levels of security and speed through using modified logistic maps while Rahman et al. [28] came up with a new compression-based 2D-chaotic sine map for biometric identification systems. Chai et al. [29] studied the application of 2D-SDMCHM and matching embedding based on flag-shaped hexagon prediction for coherent image cryptosystems in the medical domain.
1.1. Motivation
The imperative need to address the distinct security issues arising from the transmission and storage of medical pictures in digital settings motivates this research. As telemedicine gains immense popularity, there is a growing trend of concerns about the security and privacy of patients’ personal health information when communicating online. Due to the inherent characteristics of medical images, such as their large data sizes and nonuniform grayscale level distribution, the traditional encryption techniques available in the field of medical imaging may not be able to meet the necessary strict level of security. This resulted in the need for advanced cryptographic solutions, vulnerable to both cryptanalytic and statistical security attacks. Another theoretically practical solution could involve incorporating chaos theory into encryption algorithms, as chaotic systems inherently possess unpredictability and complexity, characteristics that cryptosystems seek.
1.2. Contribution
This research’s primary accomplishment is the creation of a novel encryption technique for the protection of medical images.
- The proposed cryptographic solution deals with chaos theory and an approach that combines the complexity and natural unpredictability of chaotic systems to create security models.
- This paper presents a symmetric block encryption technique using a permutation group to operate a set of pseudo-random numbers generated by the chaotic maps.
- The technique iterates the chaotic map between a pair’s changes to produce a binary output. Furthermore, we adjust these sequences to construct a solid substitution box (S-box), a crucial aspect of cryptographic systems.
- Furthermore, block substitution in the encryption process involves unique permutations that are critical for strong encryption because they create confusion and diffusion.
- The proposed method effectively demonstrates its application of medical image confidentiality through a thorough analysis based on several metrics compared to the existing methodologies.
2. Chaos Theory
Chaos theory represents an interesting branch of mathematical discipline, dealing with the behavior of dynamical systems governed by nonlinear equations, which are best known as chaotic maps [30]. These maps clearly indicate the pronounced receptivity to the starting conditions, well-known under the label “butterfly effect”. The system’s high sensitivity to initial conditions can easily cause even the smallest deviation at an earlier time, leading to significantly diverged results later. This can make long-term forecasting extremely challenging or even impossible. Since chaotic maps are nonlinear and deterministic, there is no element of randomness in their behavior, which makes them extremely sensitive to initial conditions and follow precise mathematical laws. The chaotic maps, characterized by fractal patterns and topological mixing, defy prediction. Not only are their properties highly intriguing, but they are also widely applied in various fields, ranging from biology to economics and from physics to cryptography. Rigid theoretical and experimental investigations have dealt with the well-known chaotic maps, such as the May Map, the Tent Map, the Logistic Map, and the Henon Map. Thus, in-depth study of the dynamics of a chaotic system provided researchers with great insight into chaotic systems and advanced our understanding of chaos theory in practical applications to various fields, including engineering and scientific discovery. Complex systems challenge mathematicians and scientists in this area of chaos, while the opportunities for change and innovation captivate them.
2.1. Tent Map
The bifurcation diagram of the Tent Map shows why the map got its name: the tent-like shape. This map shows the chaotic behavior in the interval as indicated by Lyapunov exponent and bifurcation diagrams. In terms of math, it is defined as [30]:
where and parameter . Similar to the logistic map, it has a confined domain and a partially chaotic range with nonuniformity. Additionally, throughout the iteration, the Tent Map tends to remain periodic. Figure 1 displays the Lyapunov exponent and bifurcation diagram of a Tent Map.
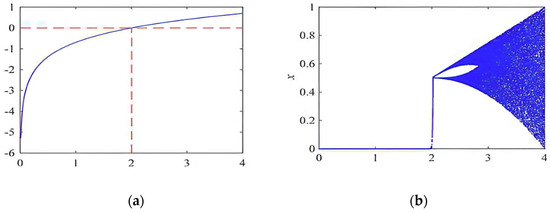
Figure 1.
(a) Lyapunov exponent, (b) Bifurcation Diagram of Tent Map.
2.2. May Map
The May Map behaves similarly to the logistic map and can be represented using the following equation:
where and parameter . This is shown in Figure 2, which displays chaotic features within the previously indicated initial condition range [31].
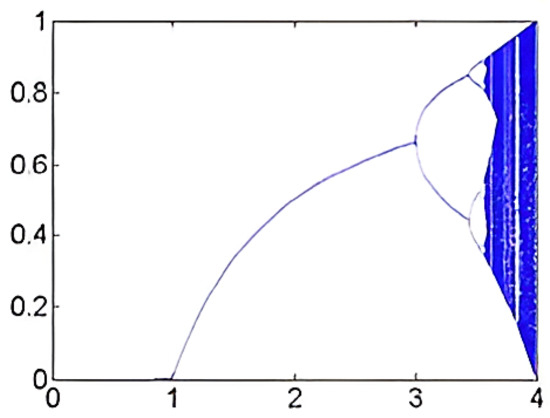
Figure 2.
Bifurcation Diagram of May Map.
3. Novel Tent–May Map
The Novel Tent–May Map is a hybrid chaotic system that combines the dynamics of the Tent Map and the May Map to generate complex and unpredictable behavior suitable for cryptographic applications such as the construction of a substitution box (S-box). This map is defined mathematically as follows:
where and parameter . This combination leverages the distinct chaotic properties of both the Tent Map and the May Map. The Tent Map contributes its well-known piecewise linearity and uniform stretching, which enhance diffusion properties essential for cryptographic strength. On the other hand, the May Map, rooted in population dynamics, introduces nonlinear exponential terms that add complexity and unpredictability. This hybrid approach aims to exploit the strengths of both maps to create a more robust and secure chaotic system.
3.1. Detailed Analysis of the Novel Tent-May Map
The Novel Tent–May Map combines the Tent Map and the May Map in a piecewise manner to generate complex chaotic behavior. The behavior of the Tent–May Map can be characterized as complex and dynamic based on its entropy spectrum, Lyapunov exponent spectrum, and bifurcation diagram. The entropy spectrum shows regions of unpredictability and randomness, especially between and and, after that, , with entropy increasing and stabilizing at higher values for , greater than 2.5, indicating that the system continues to exhibit chaotic behavior. The Lyapunov exponent spectrum exhibits high values for close to , which is due to the strong sensitivity to the initial condition and high chaos, but this decreases near the value of , thus explaining why it depicts less chaotic or periodic behavior before increasing and stabilizing again after . Analyzing the bifurcation diagram, one can note that it exhibits periodic or quasi-periodic oscillations for a ∼ 1.5 to 2.5 depending on its parameters by the discrete clusters of points and the transition to a chaotic behavior for , as is clearly shown by the overlapping and tightly packed points for all values of . These analyses collectively show that the Tent–May Map’s intricate transitions between periodic and chaotic regions are, therefore, useful for applications that need high levels of unpredicted behavior and sensitivity to initial conditions. Figure 3 displays a (a) bifurcation diagram, (b) the entropy spectrum, and (c) Lyapunov exponent spectrum, providing a comprehensive understanding of the Tent–May Map’s dynamics.
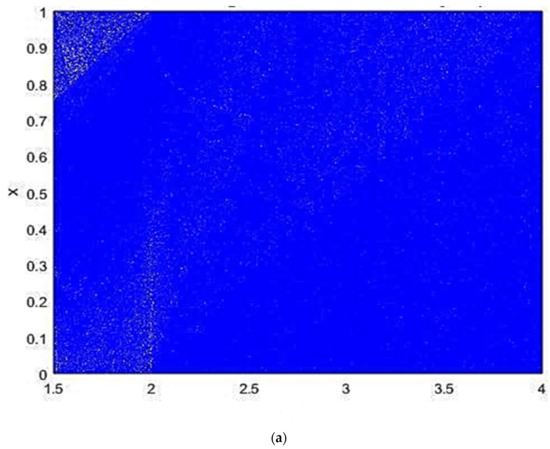
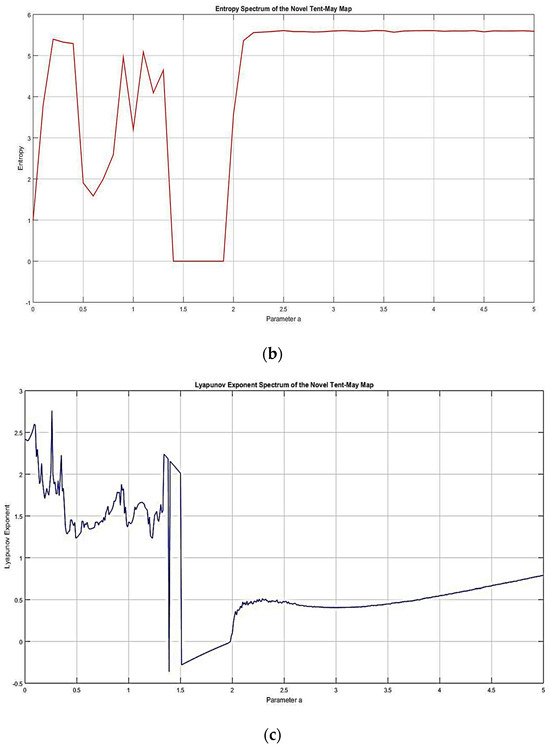
Figure 3.
(a) Bifurcation Diagram, (b) Entropy Spectrum, (c) Lyapunov exponent spectrum.
Conversion between Tent and May Maps
- a.
- Tent Map Region
When is less than , the first part of the equation is used, that is,
This part of the map integrates both the exponential growth and decay from the May Map as well as the stretching and folding behavior characteristic of the Tent Map. The linear term introduces stretching and folding similar to the Tent Map, while the exponential term adds complexity and nonlinearity.
- b.
- May Map Region
When is or greater, the second part of the equation is used, that is,
This part of the map continues to integrate both the exponential growth and decay dynamics of the May Map and the linear transformation aspect of the Tent Map. The term introduces the nonlinear component similar to the May Map, creating a more complex behavior.
This intricate behavior makes the map suitable for cryptographic applications, ensuring high sensitivity to initial conditions and robust chaotic properties.
4. Cryptographic Applications
The proposed Novel Tent–May Map is particularly useful in the construction of S-boxes, which are vital components in various encryption algorithms. An S-box provides nonlinearity and confusion, two critical properties in cryptographic systems. The chaotic nature of the Novel Tent–May Map ensures that the generated S-box is highly unpredictable and resistant to linear and differential cryptanalysis. Algorithm 1 describes in detail the procedure used to develop the proposed S-box .
| Algorithm 1: Construction of | |
| 00 | Input: |
| 01 | Initialize parameter and iterations |
| 02 | |
| 03 | Output: |
| 04 | |
| 05 | |
| 06 | Iterate Tent–May Map: |
| 07 | from to iterations |
| 08 | Calculate by Tent–May Map |
| 09 | |
| 10 | Store each value in array (say) |
| 11 | |
| 12 | Initialize arrays and : |
| 13 | for from to iterations: |
| 14 | Calculate by converting each value to binary |
| 15 | End |
| 16 | |
| 17 | for from to iterations: |
| 18 | Calculate by Transforming values of to binary |
| 19 | End |
| 20 | |
| 21 | Perform the operation between and |
| 22 | Convert to binary string |
| 23 | |
| 24 | Make segments of bits: |
| 25 | Convert each segment to decimal |
| 26 | |
| 27 | Find unique values: |
| 28 | Store the unique values in array |
| 29 | |
| 30 | Update Array : |
| 31 | Add fixed integer to each value and restrict between |
| 32 | Convert each to binary |
| 33 | Reordered the bits with unique pattern. |
| 34 | Convert the rearranged binary string back to decimal. |
| 35 | |
| 36 | Find : |
| 37 | is generated by updated values. |
| 38 | Interchange the position of fix point with first element in |
| 39 | |
| 40 | Tweaking the Nonlinearity: |
| 41 | Take the Action of a permutation group |
| with generators and of order on , through | |
| right mutilation. | |
| 42 | |
| 43 | Update : |
| 44 | |
| 45 | End |
Figure 4 displays the flowchart of Algorithm 1, which creates the proposed S-box. Table 1 provides an illustration of the proposed S-box .
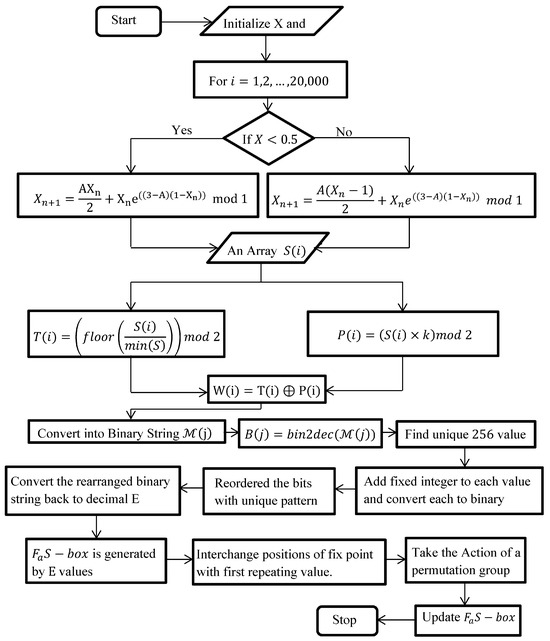
Figure 4.
Flowchart of Proposed Approach.

Table 1.
Proposed .
5. Performance Analysis for Proposed S-Box
New S-boxes represent an important research contribution in information security. Once created, we assess an S-box’s ability to withstand different linear and differential attacks. We have extensively evaluated the proposed S-box based on various criteria.
- —Nonlinearity;
- —Strict Avalanche Criterion;
- —Bit Independent Criterion;
- —Linear Approximation Probability;
- —Differential Approximation Probability.
5.1. Nonlinearity (NL)
Nonlinearity is an important factor to consider when evaluating a substitution box’s efficacy. In particular, the only nonlinear component of modern block ciphers is an S-box. If an S-box’s structure is such that the conversion between the original data and scrambled data is linear, then its resistance to distinct linear and differential attacks is weak. An effective protection against these malicious attempts requires a high value of nonlinearity. We find the nonlinearity value of a Boolean function using the following equation.
where Walsh–Hadamard spectrum of a Boolean function having bits.
Table 2 displays the proposed S-box F_1.6 S-box nonlinearity scores, where the minimum, maximum, and average nonlinearity scores are 110, 112, and 111. Table 3 compares the NL scores of the proposed S-box with those of recently designed S-boxes.

Table 2.
Nonlinearity score of final S-box.

Table 3.
Recent S-boxes and nonlinearity values.
5.2. Strict Avalanche Criterion (SAC)
Tavares and Webster first introduced the Strict Avalanche Criterion (SAC) [46]. To meet this requirement, every change to one of the input bits must result in an alteration of the ciphertext due to the use of a cipher. Using a dependency matrix, we calculate the SAC score of a substitution box. Table 4 displays the calculated and quantified values of the proposed S-box matrix.

Table 4.
SAC dependence values of proposed S-box.
For an S-box, a SAC value of is considered the perfect score. The proposed S-box’s average SAC score is , extremely close to the best value.
5.3. Bit Independence Criterion (BIC)
Tavares and Webster [46] created the Bit Independence Criterion (BIC), another criterion for rating S-box performances. According to this requirement, changes in output bits must occur independently of one another if input bits change in any way. Table 5 lists the proposed S-box’s BIC-NL values, revealing an average BIC-NL score of 111.4286.

Table 5.
BIC-NL scores of proposed S-box.
BIC-SAC values of the proposed S-box are listed in Table 6.

Table 6.
BIC-SAC scores of proposed S-box.
5.4. Linear Approximation Probability
In 1993, Matsui proposed linear cryptanalysis as a statistical attack to evaluate the advantages and disadvantages of the Data Encryption Standard (DES) [47,48]. Linear cryptanalysis identifies linear correlations between a cryptosystem’s inputs (key, plaintext) and outputs (cipher text). These days, cryptanalysts can investigate the weaknesses of contemporary block ciphers using linear cryptography. The National Institute of Standards and Technology (NIST) created the Advanced Encryption Standard (AES) in response to the DES cipher’s demonstrated vulnerability to linear cryptanalysis and severity [49]. Calculating the linear probability of a substitution box’s inputs and outputs and finding it small indicates that the S-box under examination is resistant to linear cryptanalysis. Equations can compute the linear probability (LP) value for an S-box.
where and .
The proposed S-box has a low LP value of , indicating its effectiveness against linear cryptanalysis.
5.5. Differential Approximation Probability
Biham and Shamir [8] first presented differential cryptanalysis as a novel way to break the Data Encryption Standard (DES). Any cryptosystem that employs substitution and permutation operations, like the DES, can launch this attack. By using differential cryptanalysis, a perpetrator aims to exploit the inconsistent differences between plaintext and ciphertext by identifying similarities between related scrambled plaintexts. There may be one or more bits of variation in the original plaintext. We evaluate an S-box’s resistance to this attack using differential uniformity (DU) and differential probability (DP) measurements. We can determine the differential approximation (DP) of a specific substitution box B using the following formula:
In this case, represents all possible inputs, and all input elements are . Also and represent input and output differentials. Table 7 displays the projected S-box’s extremely low DP score of , indicating that it is capable of withstanding differential cryptanalysis.

Table 7.
SAC, BIC-NL, LP, and DP scores.
Table 7 shows the comparison of SAC, BIC-NL, LP, and DP scores with exiting well-known S-boxes.
6. Proposed Algorithm of Image Encryption
In this section, we aim to encrypt a carefully chosen set of four grayscale medical images. Our investigations have provided evidence for the strong resilience and secure qualities of the algorithm we have presented through a series of carefully conducted test experiments. While using the various capabilities of MATLAB software version R2015a, we performed all of our experimental simulations with accuracy and precision. We carefully selected four plaintext images, accessed on Saturday, 30 March 2024 for our research from the MedPix database of the National Library of Medicine (https://medpix.nlm.nih.gov/home), a reputable source. Figure 5, Figure 6, Figure 7 and Figure 8 prominently display side-by-side representations of the original images and their subsequent encrypted versions for comparison. These visual representations clearly highlight the differences, thereby confirming the effectiveness of our encryption approach in effectively protecting the integrity of the analyzed medical images. The produced by Algorithm 1 has demonstrated its security as a substitution box by achieving a high level of efficiency and security against several known attacks. Algorithm 2 displays an image encryption algorithm that utilizes the common structure of confusion and diffusion.
| Algorithm 2: Image Encryption Algorithm | ||
| 00. | Input: | Input image |
| 01. | Substitution box | |
| 02. | Key (8-byte key) | |
| 03. | Output: | Encrypted image |
| 04. | Step 1: | |
| 05. | Perform block-wise substitution for the first round: | |
| 06. | Divide the image into blocks of size | |
| 07. | For each block: | |
| 08. | Extract the block. | |
| 09. | Perform substitution for each pixel in the block using the key. | |
| 10. | Update the encrypted image with the substituted block. | |
| 11. | Write the encrypted image to file Enc_round_1 | |
| 12. | Step 2: | |
| 13. | Perform permutation for the second round: | |
| 14. | Reshape the encrypted image into a vector. | |
| 15. | ||
| 16. | Permute the reshaped vector according to the permutation vector. | |
| 17. | Reshape the permuted vector back into the image shape. | |
| 18. | Write the encrypted image to file Enc_round_2 | |
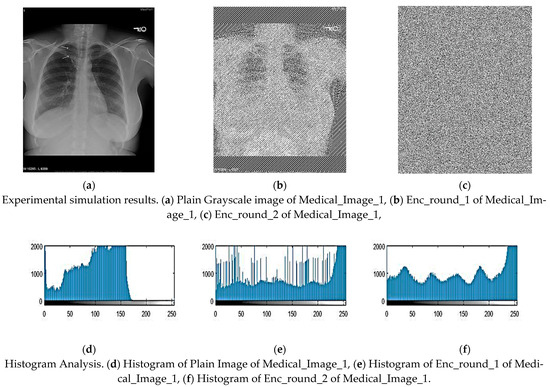
Figure 5.
Experimental simulation results of Medical_Image_1 and Histogram Analysis.
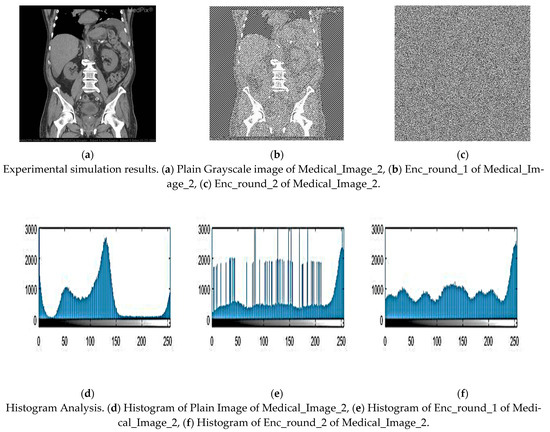
Figure 6.
Experimental simulation results of Medical_Image_2 and Histogram Analysis.
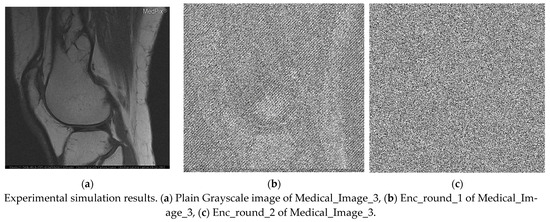
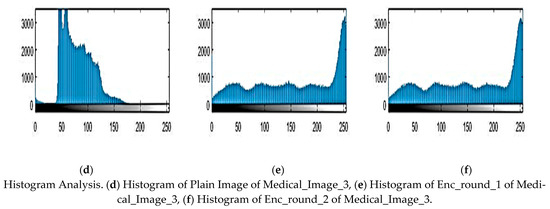
Figure 7.
Experimental simulation results of Medical_Image_3 and Histogram Analysis.
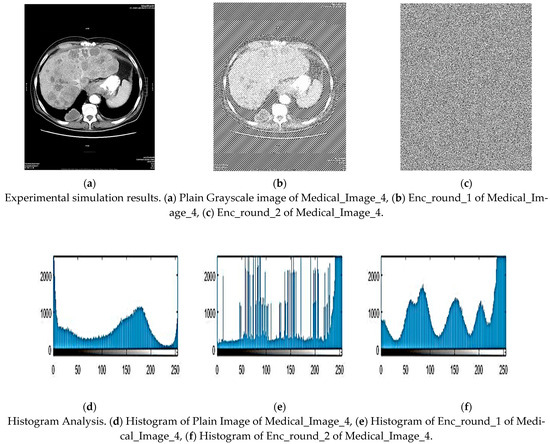
Figure 8.
Experimental simulation results of Medical_Image_4 and Histogram Analysis.
7. Proposed Technique Analysis
Ensuring the security of the encryption technique is of utmost importance. This section examines the security of the method by analyzing information entropy, adjacent pixel correlation, and resistance to differential attacks through a range of experiments and studies. The testing process makes use of a wide range of images of arbitrary size and type.
Histogram
The histogram describes the frequency of each gray-level pixel in a picture and gives details on how light and dark the image is. The encryption method needs to hide the image data from the statistical and visual components of the information. Because of this, a solid encryption technique needs to have a cipher image’s smooth histogram. The encrypted Medical_Image_1, Medical_Image_2, Medical_Image_3, and Medical_Image_4 in Figure 3 have a significantly more consistent distribution of pixel values when compared to the original photos. This result demonstrates how well the suggested technique protects the image and provides support to the notion that it offers great protection against both statistical and differential attacks. These indicate that the developed encryption method is very successful at hiding the plain image’s pixel distribution information.
8. Majority Logical Criterion (MLC)
To assess the effectiveness of the encryption, various tests are employed, including energy, homogeneity, correlation, contrast, and entropy [50]. These tests assess the suitability of an S-box for the encryption process. These investigations calculate the level of unpredictability of the encrypted image. The characteristics of the encrypted image are dictated by its energy and uniformity. Correlation is employed to ascertain the degree of similarity between the original and encrypted images. The encrypted image has experienced a significant modification, as evidenced by the lowest score obtained from the correlation analysis. The luminosity of the main image is determined by its level of contrast. A stronger encryption method is characterized by a greater contrast. The encryption technique alters unencrypted images, while statistical analysis determines the effectiveness of the proposed S-box. The generated S-box is utilized for encrypting digital photographs. To conduct the MLC, we selected four JPEG images at random, namely Medical_Image_1, Medical_Image_2, Medical_Image_3, and Medical_Image_1. The encrypted images have undergone such significant alterations that they are now unrecognizable compared to the originals.
8.1. Homogeneity Analysis
Homogeneity analysis is a method employed to assess the positioning of items adjacent to the diagonal entries in the gray tone spatial dependency matrix (GTSDM) or the gray level co-occurrence matrix (GLCM). The GLCM calculates the statistical parameters of various combinations of pixel brightness values or gray levels to determine the frequencies of gray level patterns in the data. Homogeneity can be quantified by normalizing the gray-level co-occurrence matrices within the GLCM and calculating a measurement.
where are the positions of pixels of the image and is the representation position of the pixels in the image in the gray level co-occurrence matrix (GLCM).
8.2. Energy
The rate at which a picture’s pixels change in brightness or color is known as its energy. Therefore, it is expected that an encrypted image would possess a minimal amount of energy [51]. The energy measure is computed by summing the squared components of the gray-level co-occurrence matrix.
8.3. Contrast
Contrast is related to the variation of intensities of the pixels of the image. It assists viewers in identifying the various entities presented in the image. Enhancing the appearance of an image becomes feasible, making it easier to identify its individual components. The image depicting heightened uncertainty is expected to exhibit a greater level of contrast. A higher contrast level is correlated with a more robust encryption [52]. The mathematical representation is as follows:
We performed this collection of statistical analyses to assess the applicability and stability of our suggested image encryption procedure, which is based on S-boxes. MLC analysis was conducted on the four test images, and the outcomes for both plain and encrypted images generated by our method are presented in Table 8.

Table 8.
MLC Comparison of Different Approaches.
9. Adjacent Pixel Correlation
Correlation coefficient analysis [56,57], which is based on finding the correlation between two random variables, shows that this relationship is independent. Plaintext images typically exhibit robust correlations between pixels in different orientations. The attacker often exploits the connections between neighboring pixels to gather information about a plaintext image. Therefore, an effective encryption technique should minimize the associations between each pixel in an image [58]. The calculation of the pixel correlation coefficient can be carried out with the following formula:
where and are gray values of the adjacent pixels. And is the covariance of and and and denote the standard deviation of and , respectively.
The pixel distribution analysis and pixel correlation constitute the following Figure 9, Figure 10, Figure 11 and Figure 12, which offer the validation of image encryption techniques based on the aspects of pixel information. To compare the original image’s pixel intensity distribution to the encrypted image’s distribution, pixel distribution plots are constructed; these plots illustrate the extent of the randomization of the encryption process. In the original image, such plots give structured patterns because of inherent correlations between pixels while in the encrypted image, these plots are quite random and therefore imply successful scrambling of pixel values. The pixel correlation plots display the correlation of two neighboring pixels at different orientations: horizontal, vertical, and diagonal. High correlation coefficients in the original image imply that there is high local correlation between the corresponding pixels and when these pixels are encrypted, the correlation coefficients indicate that the local relationships are distorted. Both analyses produce a comprehensive evaluation of the encryption’s capability to randomize the image data, thereby providing the required and necessary security to the encrypted data.
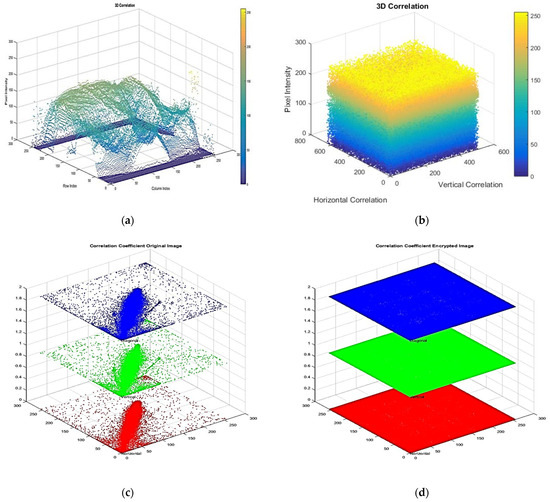
Figure 9.
(a–d) Analysis of pixel distribution and pixel correlation for original Medical_Image_1 and encrypted Medical_Image_1.
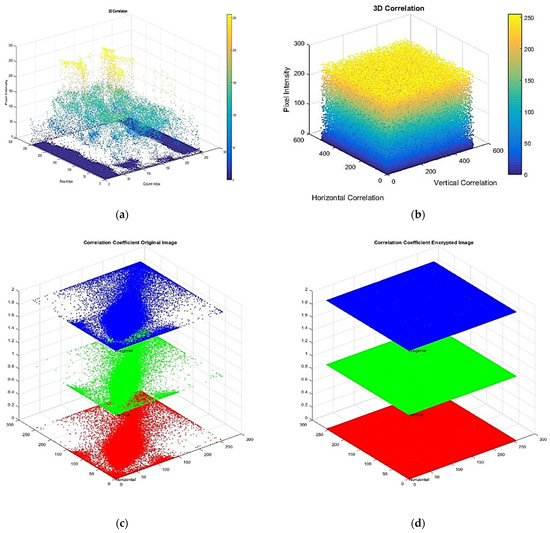
Figure 10.
(a–d) Analysis of pixel distribution and pixel correlation for original Medical_Image_2 and encrypted Medical_Image_3.
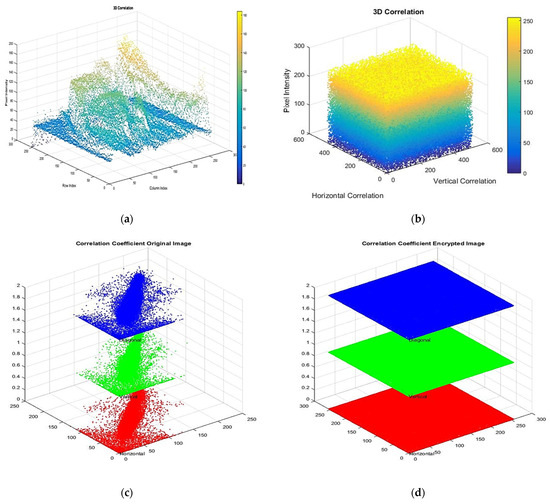
Figure 11.
(a–d) Analysis of pixel distribution and pixel correlation for original Medical_Image_3 and encrypted Medical_Image_3.
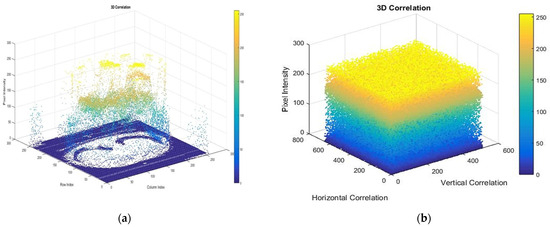
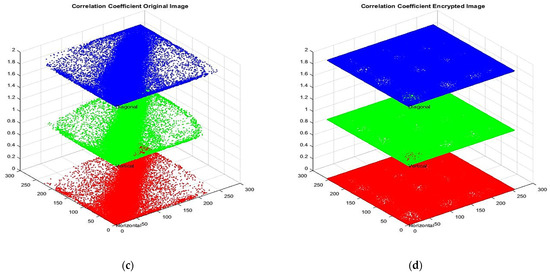
Figure 12.
(a–d) Analysis of pixel distribution and pixel correlation for original Medical_Image_4 and encrypted Medical_Image_4.
Figure 9 and Figure 10: The pixel distribution plots of Medical_Image_1 to Medical_Image_4, where the original image (a) has more structured patterns (having correlations) and the encrypted image (b) is distributed uniformly and randomly, proving effective encryption. The pixel correlations of the original image are high in horizontal, vertical, and diagonal directions as shown in figure (c), while the encrypted image has small correlation coefficients as shown in figure (d), indicating that the local pixel relationship has been disrupted due to encryption.
10. Information Entropy
Information entropy is a widely used measure of information content. The information content of an image is determined through information entropy, with higher entropy indicating a lower amount of visual information in the image. To prevent entropy attacks, it is essential to use a secure encryption method that evenly and unpredictably distributes the pixels of the image. When comparing the encrypted and plain images, the information entropy of the encrypted image should be significantly higher. The theoretical information entropy of a fully random 8-bit pixel image is 7.99 [59], which can be estimated as:
where represents the probability of the information source, , and represents the number of bits of . The information entropy values for the encrypted images that our encryption method determined are shown in Table 9.

Table 9.
Information Entropy Analysis Results.
11. Encrypted Image Quality Measure
This section focuses on the experimental evaluation of the proposed image encryption technique. For these tests, four JPEG images named Medical_Image_1, Medical_Image_2, Medical_Image_3, and Medical_Image_4 of arbitrary size have been selected. The results indicate that the proposed encryption scheme is robust to withstand various attacks.
11.1. Mean Square Error (MSE)
The mean square error (MSE) displays average squared deviations between corresponding elements of two images, usually the original and those for encryption. It is an indication of the overall discrepancy that exists between the two images. A greater mean square error (MSE) value shows greater dissimilarity between the images, which means that there are bigger variations in their content or quality. Mathematically, the mean square error (MSE) is:
N is the number of pixels in the frame, and , are the pixels in the original and processed frames, respectively. Table 10 displays the mean square error (MSE) for a different image obtained using the algorithm mentioned earlier, revealing a greater level of dissimilarity between the original and encrypted images. Table 10 shows the mean square error (MSE) for a different image obtained using the above algorithm, indicating a higher degree of dissimilarity between the original and encrypted images.

Table 10.
Results of different image quality metrics.
11.2. Peak Signal-To-Noise Ratio (PSNR)
Peak signal-to-noise ratio (PSNR) is a quantitative measure used to assess the quality of compressed or reconstructed images by comparing them to the original image. PSNR calculates the signal-to-noise ratio by subtracting the differences between the two images. In short, it offers a more refined metric compared to MSE as it quantifies noise in relation to the intensity of the signal. A higher PSNR value corresponds to higher image quality, indicating a stronger signal relative to the level of noise. In terms of mathematics,
where MSE is mean square error and MAXI is the maximum possible pixel value of the image.
11.3. Structural Similarity Index Method (SSIM)
The structural similarity index [60] method is a perception-based method. This approach considers the loss of quality of an image as a change in the way structural information is perceived. In addition, it is capable of exploiting contrast and brightness masking techniques, along with other notable perception-based factors. The term “structural information” refers to pixels that exhibit a significant level of interconnectivity or are subject to geographical constraints. Moreover, these closely connected pixels offer substantial details regarding the entities that are observable within the image domain. The term “luminance masking” refers to the phenomenon in which the distortion of an image becomes barely apparent as it gets closer to its edges. However, making use of contrast masking reduces the visibility of textural distortions in an image. SSIM is a metric that quantifies the perceived quality of videos and images. It quantifies the level of resemblance. Table 10 displays the structural similarity index (SSIM) values for Medical_Image_1, Medical_Image_2, Medical_Image_3, and Medical_Image_4. The table demonstrates that the similarity between the original and encrypted images is extremely small.
11.4. Average and Maximum Difference (AD and MD)
The purpose of these tests is to compute the average and maximum differences between the encrypted and original images. For the secure encryption process, the AD value must be more than 3 and less than −3 [61]. The AD and MD scores are calculated using the following formulas:
where are dimensions of the image.
11.5. Structural Content (SC)
This test (SC) is essentially a correlation-based metric. It is a metric to compare how structurally comparable the original and encrypted images are. In terms of math concepts,
11.6. Normalized Cross-Correlation (NCC)
The correlation function determines the degree of similarity between two images. The link between the original and ciphered images is discovered by NCC. NCC is calculated using the subsequent formula:
11.7. Normalized Absolute Error (NAE)
The normalized absolute error (NAE) is a performance measure that quantifies the total absolute error relative to the error in determining the mean of the actual values. NAE experiences variability due to its reliance on both the lowest and highest values. The normalized absolute error between the original and encrypted image can be calculated using the given formula:
11.8. Root Mean Square Error (RMSE)
The root mean square error (RMSE) is a commonly employed method for evaluating errors. It estimates the disparities between the predicted and observed values of an estimation. It measures the magnitude of the error. This ideal accuracy metric calculates the differences in forecasting errors between various estimators for a specific variable. The root mean square error (RMSE) is the square root of the mean square error (MSE).
12. NPCR, UACI, and & BACI Analysis
The cryptanalysis techniques of blocked average changing intensity (BACI), unified average changing intensity (UACI), and number of pixels changed rate (NPCR) [62] are employed to evaluate the level of resistance of encryption against distinguishing attacks. It is employed to ascertain the impact of minor alterations to the source images on encryption. NPCR calculates the proportion of distinct pixel values in both the original and encrypted images. The mathematical expression for MPCR is as follows:
where is the original image and the encrypted image is and is a specified array of the same size as A and B.
On the other hand, the unified average changing intensity (UACI) analyzes how much the intensity of the original and encrypted images changes. In terms of math,
In these computations, the image size is denoted by , and displays the average of the absolute values of the difference between the two elements. A small change in the plaintext can have a maximum effect on the encrypted image’s pixel count thanks to the diffusion operation of the image encryption technique. When there is a complete difference between the two photos, the expected value of NPCR is 99.6094%. The expected value of UACI was 33.4635%, while the theoretical value of BACI is 25% [63]. Table 11 makes it evident that the NPCR for encrypted images matches the expected value, and this is also the case for UACI and BACI cases.

Table 11.
UACI, NPCR, and BACI scores of all selected images.
13. Conclusions
This study emphasizes the critical role of substitution boxes, particularly in the context of image encryption within block cipher systems. Through the implementation of a unique symmetric block encryption scheme, we have showcased the effectiveness of incorporating chaotic systems into cryptographic applications. This was achieved by implementing a permutation group on a set of pseudo-random numbers derived from the concatenation of two 8-bit arrays generated by the Tent and May chaotic maps. By employing a series of iterative generation, normalization, and additional processing techniques, we can create an S-box that plays a crucial role in strengthening the resilience of cryptographic algorithms. Specifically for medical images, the image encryption approach, which combines segmentation, block reordering via unique permutations, and pixel value substitution using the S-box, represents a significant advance in block cipher security. This cutting-edge method not only guarantees the privacy and security of medical information but also demonstrates impressive resistance to different types of attacks, both cryptographic and statistical. Our method has been extensively evaluated using various metrics, including PSNR, UACI, MSE, NCC, AD, SC, MD, and NAE. The results consistently show that our approach outperforms existing methods. Our findings confirm the effectiveness and potential of our proposed encryption scheme in enhancing the security of image encryption within block ciphers. Future research directions could explore ways to enhance and optimize our method to adapt to changing cryptographic requirements and challenges.
Author Contributions
Conceptualization, A.Y. and M.A.; methodology, S.A.B. and A.Y.; Software, M.M.H. and S.A.B.; Validation, A.Y.; investigation, M.A.; Formal analysis, M.M.H., S.A.B. and A.Y.; Writing—original draft, S.A.B., A.Y. and M.A.; Writing—review & editing, S.A.B. and A.Y.; supervision, A.Y.; project administration, M.M.H.; funding acquisition, M.M.H. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by scientific research of King Khalid University, under grant R.G.P.2/5/44.
Data Availability Statement
Data are contained within the article.
Acknowledgments
The authors extend their gratitude to the deanship of scientific research of King Khalid University, for funding this work through a research project under grant R.G.P.2/5/44.
Conflicts of Interest
The authors declare that they have no conflicts of interest.
References
- Banning, S.; Höglinger, M.; Meyer, D.; Reich, O. Evaluation of the effect of a multifunctional telemedicine device on health care use and costs: A nonrandomized pragmatic trial. Telemed. E-Health 2023, 29, 510–517. [Google Scholar] [CrossRef]
- Pan, T.; Thomas, M.A.; Luo, D. Data-driven gated CT: An automated respiratory gating method to enable data-driven gated PET/CT. Med. Phys. 2022, 29, 3597–3611. [Google Scholar] [CrossRef] [PubMed]
- Chen, C.; Qin, C.; Qiu, H.; Tarroni, G.; Duan, J.; Bai, W.; Rueckert, D. Deep learning for cardiac image segmentation: A review. Front. Cardiovasc. Med. 2020, 7, 25. [Google Scholar] [CrossRef] [PubMed]
- Chen, Y.; Ding, S.; Xu, Z.; Zheng, H.; Yang, S. Blockchain-based medical records secure storage and medical service framework. J. Med. Syst. 2019, 43, 1–9. [Google Scholar] [CrossRef] [PubMed]
- Nittari, G.; Khuman, R.; Baldoni, S.; Pallotta, G.; Battineni, G.; Sirignano, A.; Ricci, G. Telemedicine practice: Review of the current ethical and legal challenges. Telemed. E-Health 2020, 26, 1427–1437. [Google Scholar] [CrossRef] [PubMed]
- Barney, A.; Buckelew, S.; Mesheriakova, V.; Raymond-Flesch, M. The COVID-19 pandemic and rapid implementation of adolescent and young adult telemedicine: Challenges and opportunities for innovation. J. Adolesc. Health 2020, 67, 164–171. [Google Scholar] [CrossRef] [PubMed]
- Ijaz, M.F.; Woźniak, M. Recent Advances in Deep Learning and Medical Imaging for Cancer Treatment. Cancers 2024, 16, 700. [Google Scholar]
- Olaisen, R.H.; Schluchter, M.D.; Flocke, S.A.; Smyth, K.A.; Koroukian, S.M.; Stange, K.C. Assessing the longitudinal impact of physician-patient relationship on functional health. Ann. Fam. Med. 2020, 15, 422–429. [Google Scholar] [CrossRef] [PubMed]
- Wu, Q.; Jin, Z.; Wang, P. The relationship between the physician-patient relationship, physician empathy, and patient trust. J. Gen. Intern. Med. 2022, 37, 1388–1393. [Google Scholar] [CrossRef] [PubMed]
- Yu, H.; He, F.; Pan, Y. A novel segmentation model for medical images with intensity inhomogeneity based on adaptive perturbation. Multimed. Tools Appl. 2019, 78, 11779–11798. [Google Scholar] [CrossRef]
- Kim, D.W.; Jang, H.Y.; Kim, K.W.; Shin, Y.; Park, S.H. Design characteristics of studies reporting the performance of artificial intelligence algorithms for diagnostic analysis of medical images: Results from recently published papers. Korean J. Radiol. 2019, 20, 405–410. [Google Scholar] [CrossRef]
- Gu, Z.; Cheng, J.; Fu, H.; Zhou, K.; Hao, H.; Zhao, Y.; Liu, J. Ce-net: Context encoder network for 2d medical image segmentation. IEEE Trans. Med. Imaging 2019, 38, 2281–2292. [Google Scholar] [CrossRef] [PubMed]
- Chai, X.; Fu, X.; Gan, Z.; Lu, Y.; Chen, Y. A color image cryptosystem based on dynamic DNA encryption and chaos. Signal Process. 2019, 155, 44–62. [Google Scholar] [CrossRef]
- Wang, X.; Liu, P. A new full chaos coupled mapping lattice and its application in privacy image encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2021, 69, 1291–1301. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X.; Teng, L. Double parameters fractal sorting matrix and its application in image encryption. IEEE Trans. Circuits Syst. Video Technol. 2021, 32, 4028–4037. [Google Scholar] [CrossRef]
- Gao, X.; Mou, J.; Xiong, L.; Sha, Y.; Yan, H.; Cao, Y. A fast and efficient multiple images encryption based on single-channel encryption and chaotic system. Nonlinear Dyn. 2022, 108, 613–636. [Google Scholar] [CrossRef]
- Xian, Y.; Wang, X. Fractal sorting matrix and its application on chaotic image encryption. Inf. Sci. 2021, 547, 1154–1169. [Google Scholar] [CrossRef]
- Dong, Y.; Zhao, G. A spatiotemporal chaotic system based on pseudo-random coupled map lattices and elementary cellular automata. Chaos Solitons Fractals 2021, 151, 111217. [Google Scholar] [CrossRef]
- Roy, M.; Poria, S. Enhancement of synchronized chaotic state in a delay-coupled complex neuronal network. Nonlinear Dyn. 2020, 102, 745–758. [Google Scholar] [CrossRef]
- Tomizawa, F.; Sawada, Y. Combining ensemble Kalman filter and reservoir computing to predict spatiotemporal chaotic systems from imperfect observations and models. Geosci. Model Dev. 2021, 14, 5623–5635. [Google Scholar] [CrossRef]
- Wei, D.; Jiang, M.; Yang, D. A secure image encryption algorithm based on hyper-chaotic and bit-level permutation. Expert Syst. Appl. 2023, 213, 119074. [Google Scholar] [CrossRef]
- Al Sibahee, M.A.; Abduljabbar, Z.A.; Luo, C.; Zhang, J.; Huang, Y.; Abduljaleel, I.Q.; Ma, J.; Nyangaresi, V.O. Hiding scrambled text messages in speech signals using a lightweight hyperchaotic map and conditional LSB mechanism. PLoS ONE 2024, 19, e0296469. [Google Scholar] [CrossRef] [PubMed]
- Rehman, M.U. Quantum-enhanced chaotic image encryption: Strengthening digital data security with 1-D sine-based chaotic maps and quantum coding. J. King Saud Univ. Comput. Inf. Sci. 2024, 36, 101980. [Google Scholar] [CrossRef]
- Abduljabbar, Z.A.; Abduljaleel, I.Q.; Ma, J.; Al Sibahee, M.A.; Nyangaresi, V.O.; Honi, D.G.; Abdulsada, A.I.; Jiao, X. Provably secure and fast color image encryption algorithm based on s-boxes and hyperchaotic map. IEEE Access 2022, 10, 26257–26270. [Google Scholar] [CrossRef]
- Hazzazi, M.M.; Rehman, M.U.; Shafique, A.; Aljaedi, A.; Bassfar, Z.; Usman, A.B. Enhancing image security via chaotic maps, Fibonacci, Tribonacci transformations, and DWT diffusion: A robust data encryption approach. Sci. Rep. 2024, 14, 12277. [Google Scholar] [CrossRef]
- Abduljaleel, I.Q.; Abduljabbar, Z.A.; Al Sibahee, M.A.; Ghrabat, M.J.; Ma, J.; Nyangaresi, V.O. A lightweight hybrid scheme for hiding text messages in colour images using LSB, Lah transform and Chaotic techniques. J. Sens. Actuator Netw. 2022, 11, 66. [Google Scholar] [CrossRef]
- Riaz, M.; Dilpazir, H.; Naseer, S.; Mahmood, H.; Anwar, A.; Khan, J.; Benitez, I.B.; Ahmad, T. Secure and fast image encryption algorithm based on modified logistic map. Information 2024, 15, 172. [Google Scholar] [CrossRef]
- Rahman, M.; Murmu, A.; Kumar, P.; Moparthi, N.R.; Namasudra, S. A novel compression-based 2D-chaotic sine map for enhancing privacy and security of biometric identification systems. J. Inf. Secur. Appl. 2024, 80, 103677. [Google Scholar] [CrossRef]
- Chai, X.; Shang, G.; Wang, B.; Gan, Z.; Zhang, W. Exploiting 2D-SDMCHM and matching embedding driven by flag-shaped hexagon prediction for visually meaningful medical image cryptosystem. Chaos Solitons Fractals 2024, 185, 115153. [Google Scholar] [CrossRef]
- Ullah, A.; Jamal, S.S.; Shah, T. A novel construction of substitution box using a combination of chaotic maps with improved chaotic range. Nonlinear Dyn. 2017, 88, 2757–2769. [Google Scholar] [CrossRef]
- Ali, K.M.; Khan, M. Application based construction and optimization of substitution boxes over 2D mixed chaotic maps. Int. J. Theor. Phys. 2019, 58, 3091–3117. [Google Scholar] [CrossRef]
- Shafique, A. A new algorithm for the construction of substitution box by using chaotic map. Eur. Phys. J. Plus 2020, 135, 1–13. [Google Scholar] [CrossRef]
- Majid, M.A.; Alhadawi, H.S.; Lambić, D.; Ahmad, M. A novel method of S-box design based on discrete chaotic maps and cuckoo search algorithm. Multimed. Tools Appl. 2021, 80, 7333–7350. [Google Scholar]
- Ibrahim, S.; Alhumyani, H.; Masud, M.; Alshamrani, S.S.; Cheikhrouhou, O.; Muhammad, G.; Abbas, A.M. Framework for efficient medical image encryption using dynamic S-boxes and chaotic maps. IEEE Access 2020, 8, 160433–160449. [Google Scholar] [CrossRef]
- Long, M.; Wang, L. S-box design based on discrete chaotic map and improved artificial bee colony algorithm. IEEE Access 2021, 9, 86144–86154. [Google Scholar] [CrossRef]
- Zahid, A.H.; Arshad, M.J.; Ahmad, M.; Soliman, N.F.; El-Shafai, W. Dynamic S-Box Generation Using Novel Chaotic Map with Nonlinearity Tweaking. Comput. Mater. Contin. 2023, 75, 7516. [Google Scholar]
- Ali, T.S.; Ali, R. A novel color image encryption scheme based on a new dynamic compound chaotic map and S-box. Multimed. Tools Appl. 2022, 81, 20585–20609. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Z.; Ding, Q. Construction of an S-box based on chaotic and bent functions. Symmetry 2021, 13, 671. [Google Scholar] [CrossRef]
- Farah, T.; Rhouma, R.; Belghith, S. A novel method for designing S-box based on chaotic map and teaching–learning-based optimization. Nonlinear Dyn. 2017, 88, 1059–1074. [Google Scholar] [CrossRef]
- Lambić, D. A new discrete-space chaotic map based on the multiplication of integer numbers and its application in S-box design. Nonlinear Dyn. 2020, 100, 699–711. [Google Scholar] [CrossRef]
- Lambić, D. S-box design method based on improved one-dimensional discrete chaotic map. J. Inf. Telecommun. 2018, 2, 181–191. [Google Scholar] [CrossRef]
- Lambić, D. A novel method of S-box design based on discrete chaotic map. Nonlinear Dyn. 2017, 87, 2407–2413. [Google Scholar] [CrossRef]
- Lambić, D. A novel method of S-box design based on chaotic map and composition method. Chaos Solitons Fractals 2014, 58, 16–21. [Google Scholar] [CrossRef]
- Masood, F.; Masood, J.; Zhang, L.; Jamal, S.S.; Boulila, W.; Rehman, S.U.; Ahmad, J. A new color image encryption technique using DNA computing and Chaos-based substitution box. Soft Comput. 2022, 26, 7461–7477. [Google Scholar] [CrossRef]
- Liu, J.; Tong, X.; Zhang, M.; Wang, Z. The design of S-box based on combined chaotic map. In Proceedings of the 3rd International Conference on Advanced Electronic Materials, Computers and Software Engineering (AEMCSE), Nanchang, China, 24–26 April 2020. [Google Scholar]
- Williams, H.; Webster, A.; Tavares, S. On the design of s-boxes. In Advances in Cryptology—CRYPTO’85 Proceedings; Springer: Berlin/Heidelberg, Germany, 1986. [Google Scholar]
- Biham, E.; Shamir, A. Differential cryptanalysis of DES-like cryptosystems. J. Cryptol. 1991, 4, 3–72. [Google Scholar] [CrossRef]
- Matsui, M. Linear cryptanalysis method for DES cipher. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1993. [Google Scholar]
- Heys, H.M. A tutorial on linear and differential cryptanalysis. Cryptologia 2002, 26, 189–221. [Google Scholar] [CrossRef]
- Hussain, I.; Shah, T.; Gondal, M.A.; Mahmood, H. Generalized majority logic criterion to analyze the statistical strength of S-boxes. Z. Für Naturforschung A 2012, 65, 282–288. [Google Scholar] [CrossRef]
- Naseer, Y.; Shah, T.; Javeed, A. Advance image encryption technique utilizing compression, dynamical system and S-boxes. Math. Comput. Simul. 2020, 178, 207–217. [Google Scholar] [CrossRef]
- Ahmad, J.; Hwang, S.O. Chaos-based diffusion for highly autocor related data in encryption algorithms. Nonlinear Dyn. 2015, 82, 1839–1850. [Google Scholar] [CrossRef]
- Razzaque, A.; Razaq, A.; Farooq, S.M.; Masmali, I.; Faraz, M.I. An efficient S-box design scheme for image encryption based on the combination of a coset graph and a matrix transformer. Electron. Res. Arch. 2023, 31, 2708–2732. [Google Scholar] [CrossRef]
- Zhu, S.; Deng, X.; Zhang, W.; Zhu, C. Secure image encryption scheme based on a new robust chaotic map and strong S-box. Math. Comput. Simul. 2023, 207, 322–346. [Google Scholar] [CrossRef]
- Su, Y.; Tong, X.; Zhang, M.; Wang, Z. Efficient image encryption algorithm based on dynamic high-performance S-box and hyperchaotic system. Phys. Scr. 2023, 98, 065215. [Google Scholar] [CrossRef]
- Pareek, N.K.; Patidar, V.; Sud, K.K. Image encryption using chaotic logistic map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Artuğer, F.; Özkaynak, F. A new algorithm to generate aes-like substitution boxes based on sine cosine optimization algorithm. Multimed. Tools Appl. 2024, 83, 38949–38964. [Google Scholar]
- Liu, H.; Kadir, A.; Xu, C. Color image encryption with cipher feedback and coupling chaotic map. Int. J. Bifurc. Chaos 2020, 30, 2050173. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Mahmood, H.; Gondal, M.A. An efcient method for the construction of block cipher with multi-chaotic systems. Nonlinear Dyn. 2013, 71, 489–492. [Google Scholar] [CrossRef]
- Huynh-Thu, Q.; Ghanbari, M. Scope of validity of PSNR in image/video quality assessment. Electron. Lett. 2008, 44, 800–801. [Google Scholar] [CrossRef]
- Baowidan, S.A.; Alamer, A.; Hassan, M.; Yousaf, A. Group-Action-Based S-box Generation Technique for Enhanced Block Cipher Security and Robust Image Encryption Scheme. Symmetry 2024, 16, 954. [Google Scholar]
- Liang, H.; Zhang, G.; Hou, W.; Huang, P.; Liu, B.; Li, S. A novel asymmetric hyperchaotic image encryption scheme based on elliptic curve cryptography. Appl. Sci. 2021, 11, 5691. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).