1. Introduction
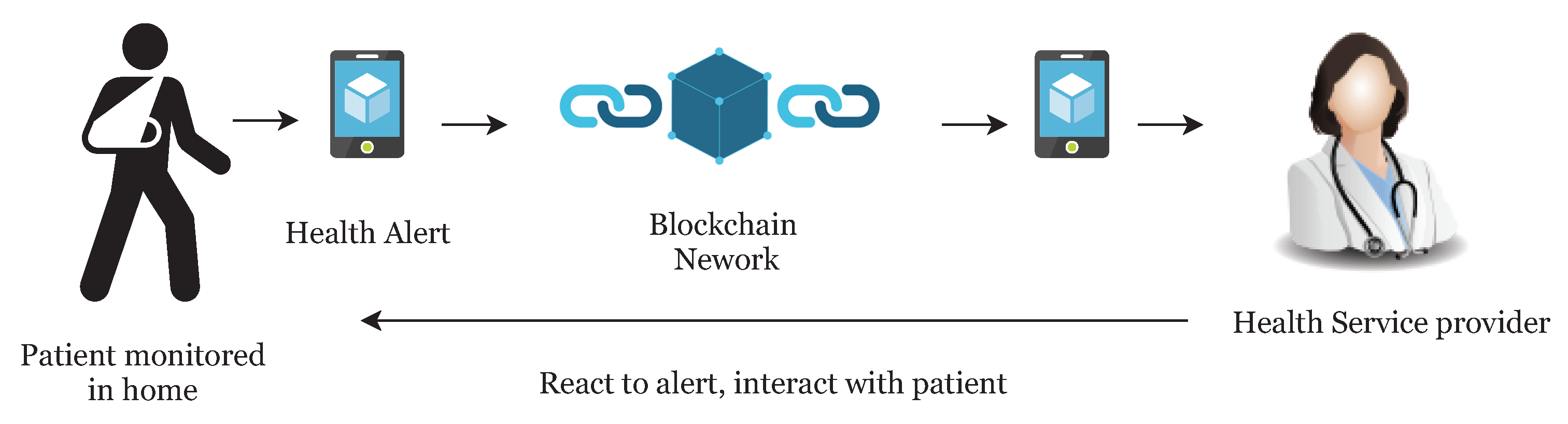
Many countries are suffering from a dramatic increase in the number of medical patients, and it is becoming more difficult for patients to access primary doctors or caregivers. In recent years, the rise of IoT and wearable devices has improved the patient quality of care by remote patient monitoring. It also allows physicians to treat more patients. Remote patient monitoring (RPM) provides monitoring and care of patients outside of the conventional clinical setting (in the home as an example). Firstly, it allows patients an intrinsic convenience of service. Patients can stay connected with health providers as required. It also reduces medical costs and improves the quality of care. This is the main reason that healthcare providers are exploring means by which to provide RPM to the masses. The main component of a RPM system could be, a specially designed monitoring device to monitor and transmit health data to smart contracts, a smartphone with internet connectivity and an RPM application (
Figure 1). Wearable devices and IoT play an important role in RPM and in the current push to develop Smart Cities. Wearable devices collect patient health data and transfer it to hospitals or medical institutions to facilitate health monitoring, disease diagnosis, and treatment. In doing so, we see a Big Data situation develop through all the patient data being analyzed and transferred.
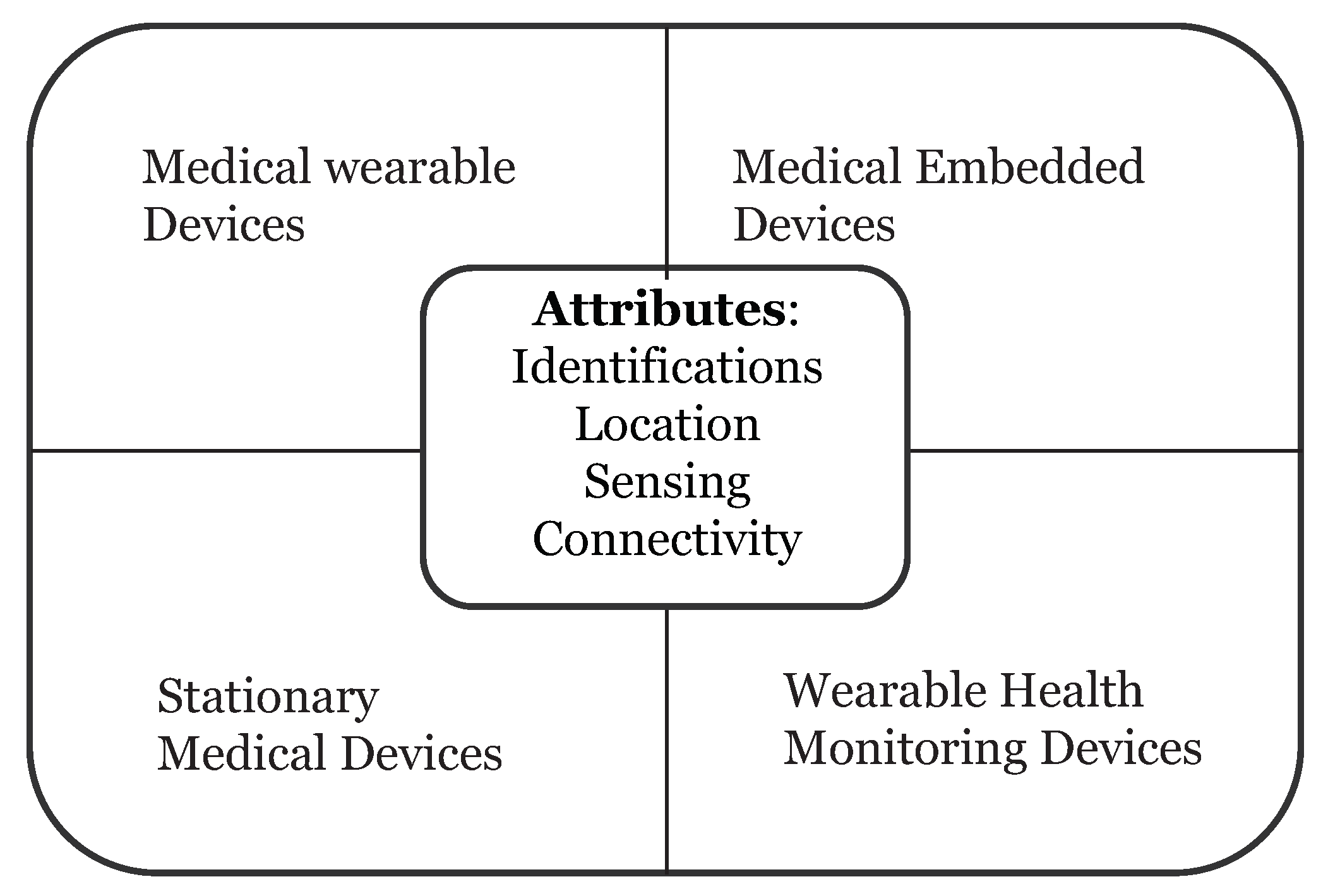
Wearable devices in healthcare are smart electronic devices with micro-controllers that can be embedded into clothing or worn on the body as accessories. They are unobtrusive, user-friendly, and connected with advanced features such as wireless data transmission, real-time feedback and alerting mechanisms built into the device. These devices can provide important information to healthcare providers such as blood pressure, blood glucose levels and breathing patterns just to name a few. Healthcare devices can be categorized into four types (
Figure 2):
Stationary Medical Devices—devices can be used on a specific physical location (e.g., chemotherapy dispensing stations for home-based healthcare)
Medical Embedded Devices—devices which can be implanted inside the body (e.g., pacemakers)
Medical Wearable Devices—prescribed devices by doctors (e.g., insulin pump)
Wearable Health Monitoring Devices—consumer products (e.g., Fitbit, Fuelband, etc.)
On 13 November 2017, the Food and Drug Administration (FDA) approved the first pill with a sensor inside of it (aripiprazole tablets with sensor) that can track if a patient has swallowed it. This pill’s sensor sends messages to a wearable patch, and the patch itself transmits the message to a mobile application on the smartphone. This technology could be a game changer for chronic disease and mental health disorders.
One of the facets of the Internet of Things (IoT) is the network of wearable devices, embedded with software, electronics, sensors, actuators, and connectivity which enables the wearable device to connect and exchange data (
Figure 3). In a futuristic smart city, we will not only see these wearable devices transmitting healthcare data, but it is reasonable to assume that wearable devices can share a myriad of data as we interconnect these devices. Therefore, the reach of the ideas presented here regarding wearable healthcare devices and using blockchain technology are further reaching than we show or can imagine here.
To handle such patient data with other institutions, such infrastructure demands secure data sharing. Health data is highly private and sharing of data may raise the risk of exposure. Furthermore, the current system of data sharing uses a centralized architecture which requires centralized trust.
The solution for data privacy and security could and should very well be blockchain technology. Initially proposed by Satoshi Nakamoto in Ref. [
1], blockchain technology provides the robustness against failure and data exposure. The blockchain is a shared data structure responsible for storing all transactional history. The blocks relate to each other in the form of a chain. The first block of the chain is known as Genesis. Each block consists of a Block Header, Transaction Counter and Transaction. It acts as a decentralized architecture to record the data. The structure of blockchain is summarized in
Table 1.
Blockchain security is based on a proof of work concept, and a transaction is only considered valid once the system obtains proof that a enough computational work has been exerted by authorizing nodes. The miners (responsible for creating blocks) constantly try to solve cryptographic puzzles (named Proof of Work (PoW)) in the form of a hash computation. The process of adding a new block to the blockchain is called mining. Each block in the chain is identified by a hash in the header. The hash is unique and generated by the Secure Hash Algorithm (SHA-256). SHA takes any size plaintext and calculates a fixed size 256-bit cryptographic hash. Each header contains the address of the previous block in the chain. The inability to delete or change information from blocks makes the blockchain the best appropriate technology for the healthcare system. However, adopting blockchain in the context of IoT is not straightforward and entails several problems such as demands of high computational power to solve PoW, low scalability and long latency for transaction confirmation over the network.
We propose a novel model of blockchain and eliminate the concept of PoW to make it suitable for IoT devices. Our model relies on the distributed nature and other additional security properties to the network. Transactions in blockchain are broadcasted publicly in the blockchain network and contain additional information about both the sender and recipient. If we talk about the blockchain that underpins bitcoin, everyone has a public address, and anyone can see what funds they already have stored at that address. This way, users cannot be anonymous in the network. For anonymity and the authenticity of the user, we present a lightweight privacy-preserving ring signature scheme that is suitable for anonymous transactions by authentic users.
On the one hand, a lightweight digital signature guarantees that information has not been modified, as if it were protected by a tamper-proof seal that is broken if the contents were altered. On the other hand, a ring signature [
2] allows a signer to sign a message anonymously. The signature is mixed with other groups (named ring) and no one (except actual signer) knows which member signed the message. We are not using heavy operations such as pairing and exponentiation in ring signature to make it more suitable for blockchain and IoT.
We also use double encryption of data using lightweight encryption algorithms (ARX ciphers) and public encryption schemes. Here double encryption means, we firstly encrypt the data using symmetric key encryption and then we encrypt the symmetric key itself using a public key. Please note that, here we are not encrypting the same data twice with different keys. ARX is a class of cryptographic algorithms which uses three simple arithmetic operations: namely modular addition, bitwise rotation, and exclusive-OR. In both industry and academia, ARX cipher has gained a lot of interest and attention in the last few years. For securely exchanging cryptographic keys over a public channel, we use the Diffie–Hellman key exchange technique. Using both these techniques together will guarantee the security, privacy and anonymity of user’s data using lightweight techniques suitable for small IoT devices.
2. Related Work
In this paper, we pull some of our main motivation to explore blockchain in healthcare from Refs. [
3,
4,
5,
6,
7,
8], where the respective authors systematically mentioned some of the latest trends in blockchain research. Since the introduction of Bitcoin in Ref. [
1], the possibilities are endless of how the underlying technology can be used in other ways outside of the financial realm. There have been numerous attempts at applying blockchain technology outside of the financial realm [
9,
10,
11,
12,
13,
14]. It is easy to imagine the far-reaching applicability of this technology specifically in healthcare, smart cities and IoT.
In Ref. [
15], there was an introduction to methods for using blockchain to provide proof of pre-specified endpoints in clinical trials. Irving and Holden empirically tested such an approach using a clinical trial protocol where outcome switching had previously been reported. They confirmed the use of blockchain as a low cost, independently verifiable method to audit and confirmed the reliability of scientific studies. We use lightweight digital signature schemes in our model inspired by Ref. [
2].
We have to date already heard of many data breaches or data losses with regards to medical data [
16,
17]. Health information is something hackers will seek out as it may contain pertinent information for identity theft. Medical record ownership is another key point when discussing health information. The records themselves come in many forms, reports, images, videos, and raw data. They could potentially also come in many different formats depending on the systems in use by the given provider. The integrity of these records then becomes paramount. There needs to be contingencies in place to ensure the integrity of the data is maintained to ensure the data has not been changed, destroyed, or removed. The access to the data should be controlled by the patients; however, they themselves should not be able to alter it either. The patient records should be consistent and available across institutional boundaries [
18,
19].
In the context of Smart cities and Big Data, we have seen some strong work recently by Wu and Ota in Refs. [
20,
21,
22,
23]. They have really been able to focus on how IoT, Smart Cities, and the resulting Big Data are all important factors going forward with Smart City design and implementation. We have contributed some work already in cryptanalysis of ARX ciphers and other security algorithms [
24,
25,
26,
27,
28,
29,
30].
5. Cryptographic Techniques Used in the Model
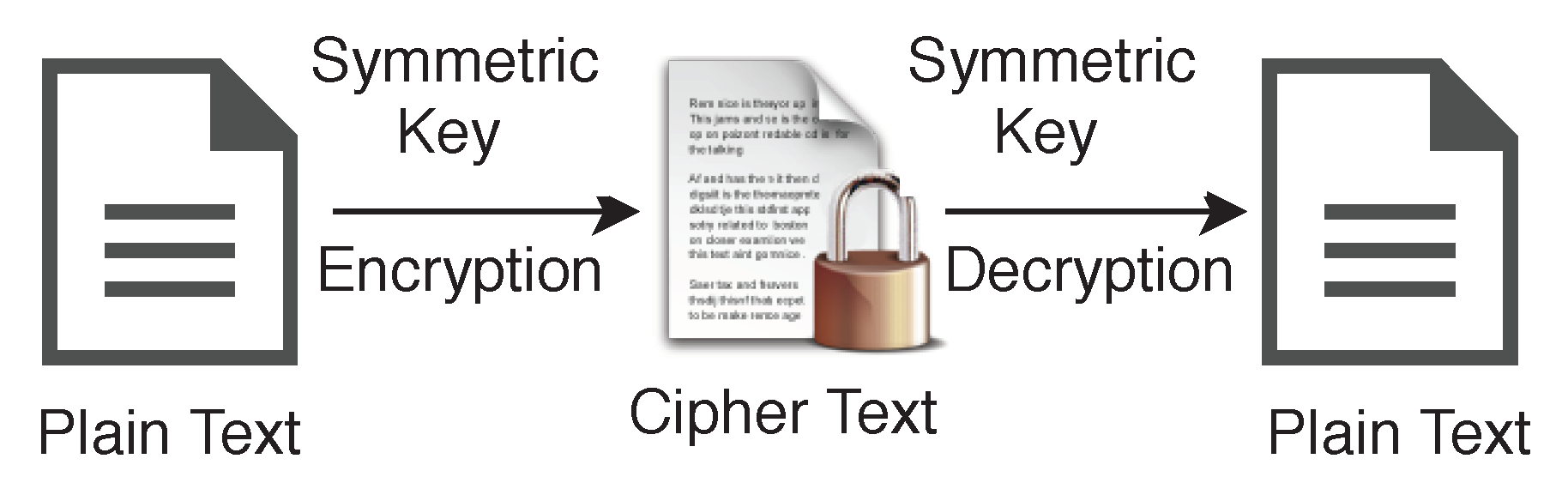
Instead of only one type of encryption technique, we use both encryption schemes, namely Symmetric and Asymmetric for different purposes. A symmetric algorithm (Private key encryption), as shown in
Figure 6, uses the same key for both encryption of plaintext and decryption of ciphertext, whereas asymmetric algorithms (Public key encryption) use different keys for encryption of plaintext and decryption of ciphertext. We use the variable name
for the private key or symmetric key in our algorithms, and the same key will be used for encryption and decryption on both side of the transmission.
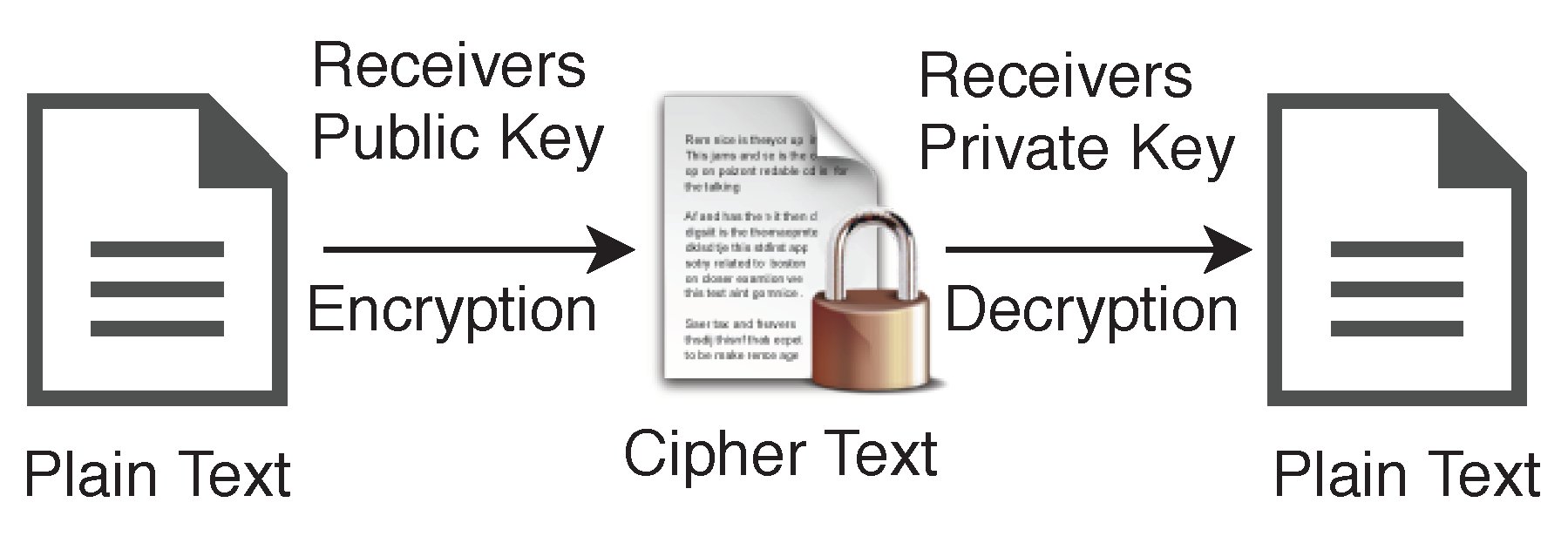
In the case of asymmetric encryption, sender will have one key pair
, and receiver will have another key pair
, shown in
Figure 7. Data can be encrypted using receiver’s public key
and can be decrypted using their private key
. Generally, we use abbreviations plaintext
for the unencrypted data and ciphertext
for the encrypted data.
5.1. ARX Encryption Algorithm
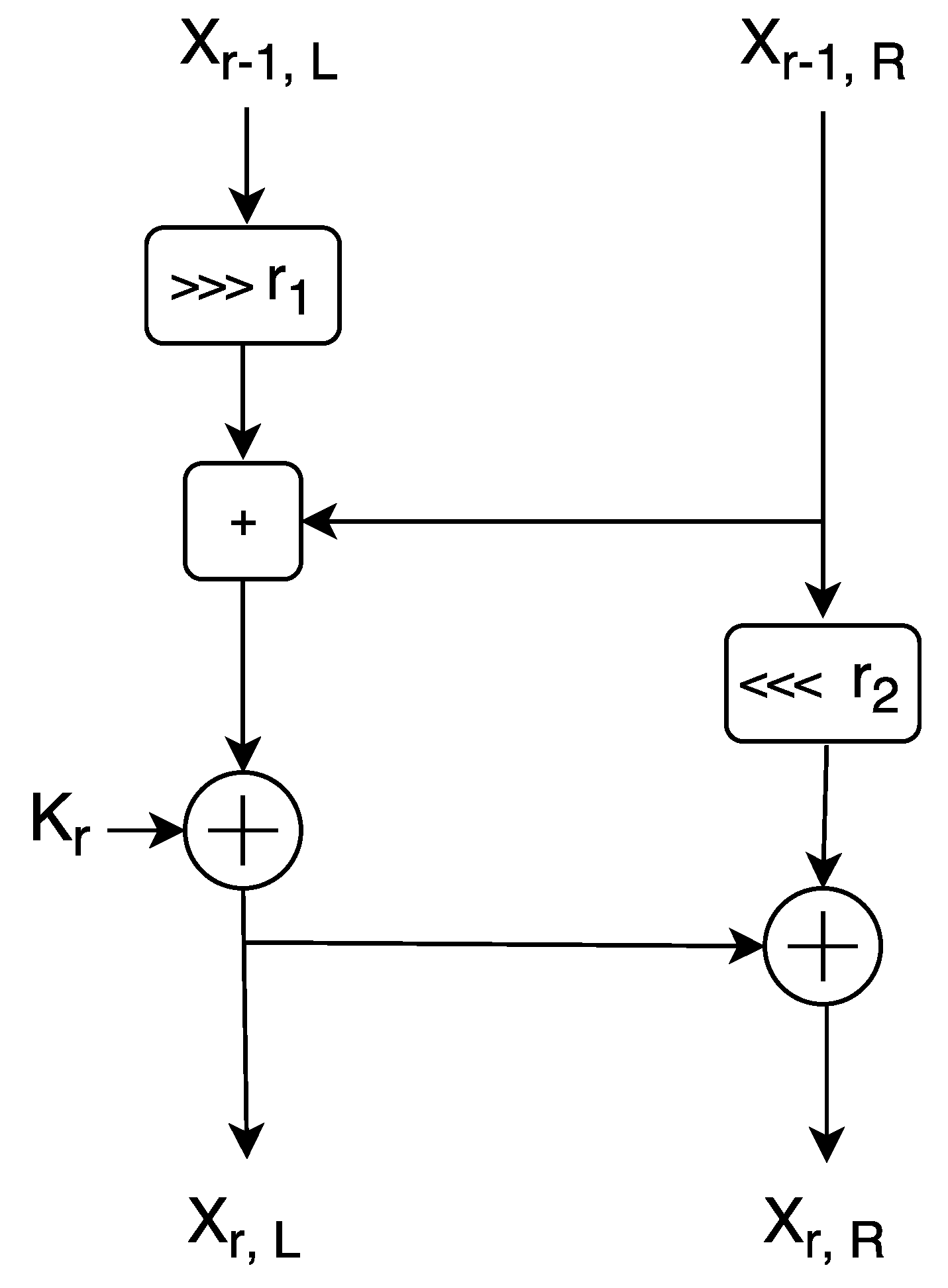
In our model, we are using a particular branch of Symmetric key encryption, called ARX algorithms to encrypt the data for blockchain. These algorithms are made of simple operations Addition, Rotation and XOR and support a lightweight encryption for small devices. Among a few well known examples, the one example of latest usage of ARX cipher is: SPECK [
33], designed by the National Security Agency (NSA), of the United States of America (USA) in June 2013. However, SPECK itself has been severely criticized prior to ISO standardization rejection due to the possibility of the well known cipher backdoor issue, but still, we use it here because it is safe against key recovery attacks. Our model is specifically dedicated to securing the network against various attacks rather than to secure individual nodes. In the case where within the network a defaulter node is found, we can automatically block it. SPECK is a family of lightweight block ciphers with the Feistel-like structure in which each block is divided into two branches, and both branches are modified at every round. We show the round function of SPECK in
Figure 8. Each block size is divided into two parts, the left half and right half.
SPECK Round Function
SPECK uses 3 basic operations on n-bit word for each round:
The left half
n-bit word is denoted by
and the right half
n-bit word is denoted by
to the
r-th round and
n-bit round key applied in the
r-th round is denoted by
.
and
denotes output words from round
r which are computed as follows:
Different key sizes have been used by several instances of the SPECK family and the total number of rounds depends on the key size. The value of rotation constant and are specified as: , or , for various variants of SPECK.
5.2. Digital Signature
We add a digital signature to the data for authentication purposes. However, applying normal digital signatures is not suitable due to resources limit in IoT devices. Therefore, we suggest using lightweight digital signatures suitable for small devices as given in Ref. [
2]. Digital signatures are the public key primitives of message authentication. Each user has a public-private key pair. Generally, the key pairs used for signing/verifying and the key pairs used for encryption/decryption are different. In our case here, sender will have one key pair
, and receiver will have another key pair
.
The senders private key
is used to sign the data, and the key is referred to the signature key while senders public key
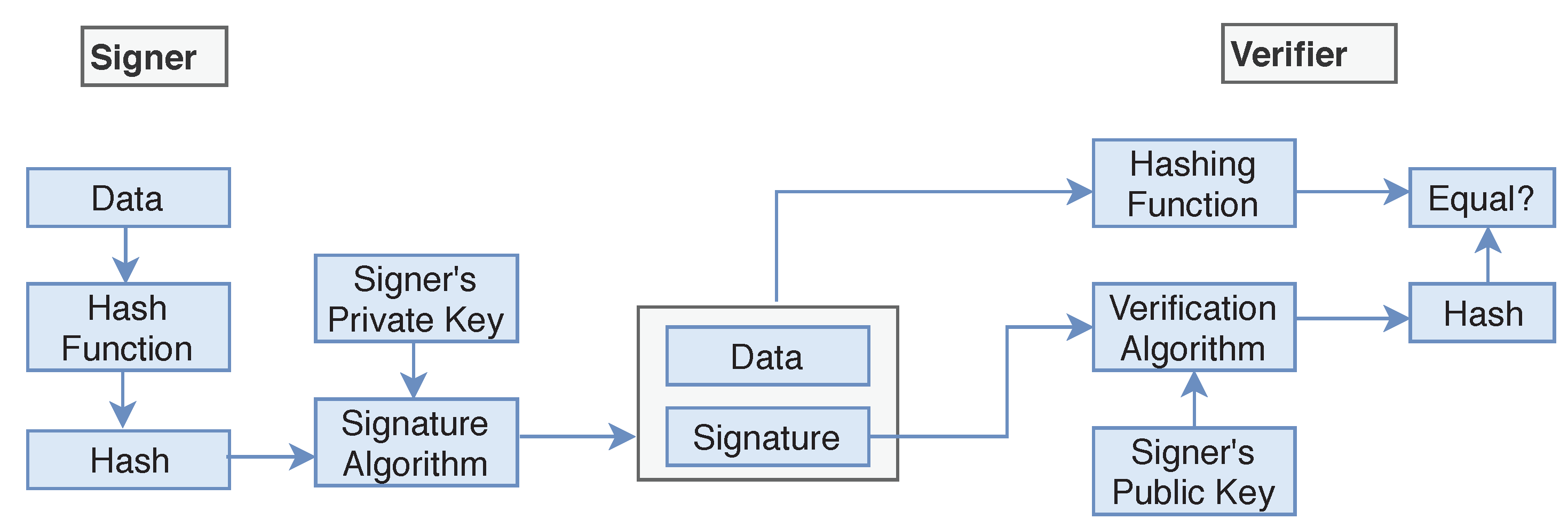
is used for verification on the receiver side of the transmission. Signer feeds the data or plaintext into the
Hash Function and generates the hash value
. Hash value
of plaintext and signature key
are then fed to the signature algorithm and sent along with the encrypted data (
Figure 9). During the verification process, the verifier generates the hash value
of the received data from the same hash function. Using the Verification algorithm and signers public key, he/she also extracts the original hash value
of plaintext and if the value of
and
are the same then the data is verified and not changed during the transmission process.
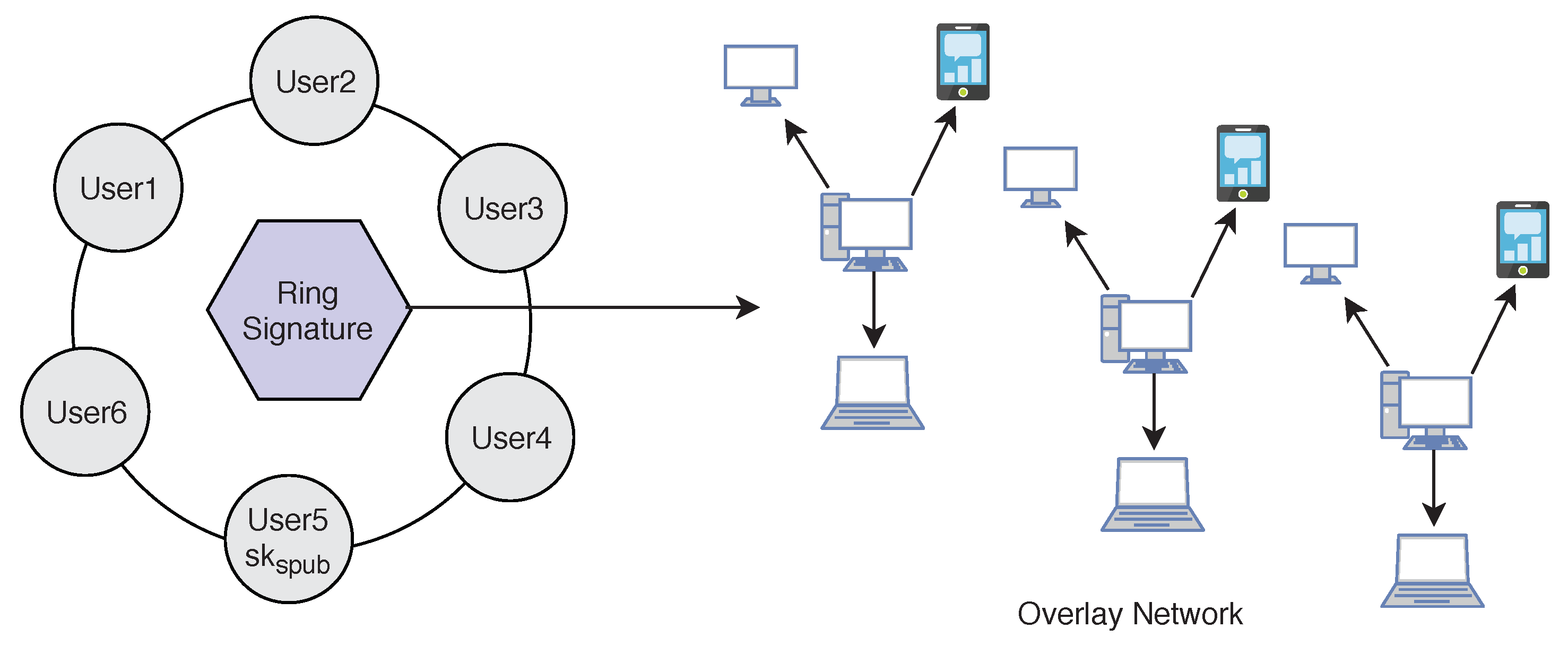
5.3. Digital Ring Signature
We use lightweight
Ring signature technology [
2] which allows a signer to sign data in an anonymous way (
Figure 10). That is the signature is mixed with other groups (named ring) and no one (except the actual signer) knows which member signed the message. Ring Signature was originally proposed by Rivest in 2001 [
34]. A user desiring to mix his transaction sends a request to the blockchain network. The request comprises the public key
. After receiving the request the network sends back a certain amount of public keys
which are collected from other users (
) who also applied for mixing service, including
. Using ring signature in our model we can get two important security properties. We achieve both
Signers Anonymity and
Signature Correctness.
Signature Correctness: A valid signature is always accepted, and an invalid signature is always rejected.
Signers Anonymity: A signature is produced by one member from the set of public key holders. Therefore, the identity of the signer is always hidden in the network, and no one can find out who is the real signer from the signature.
5.4. Diffie–Hellman Key Exchange
In all our previous techniques proposed, we need to transfer the public key through the network. To make data more secure, we also share the public key secretly. To share the public key safely along the network we are using the Diffie–Hellman key exchange technique. A basic Diffie–Hellman exchange of a shared secret between Alice and Bob could take place in the following manner:
Alice could privately calculate , and Bob , allowing them to use this single value as a shared secret. For example, if Alice has a message m to send Bob, she could hash the shared secret , compute , and send x to Bob. Bob computes , calculates , and learns m.
An external observer would not be able to easily calculate the shared secret due to the DLP (discrete logarithm problem), which prevents them from ending or . Since the output of hash functions is ‘random’, the message m is information-theoretic secure from adversaries who know x, , and .
6. Algorithms to Implement Cryptographic Techniques between Sender and Receiver in Our Model
In our encryption Algorithm 1, we encrypt the
by using the symmetric key
and produce a ciphertext file
C. After encryption, we use double encryption technique and encrypt the key
by using public key cryptography. We use the receivers public key
to encrypt the symmetric key
and send the encrypted key along with the ciphertext
C. We denote the encrypted symmetric key with
.
| Algorithm 1 Data Encryption. |
- 1:
functionEncryption () - 2:
if user confirm data preservation over blockchain then - 3:
Generate a symmetric key - 4:
() - 5:
) - 6:
else - 7:
Do nothing - 8:
end if - 9:
end function
|
For the digital signature senders can use two keys
that is different from the encryption/decryption keys. To add the digital signature, the sender first passes the data file to the
Hash Function and creates the hash value
of the data. Then he/she signs the data using his/her private key
by passing the value of the private key and hash value
to the Signature Algorithm. The signers public key
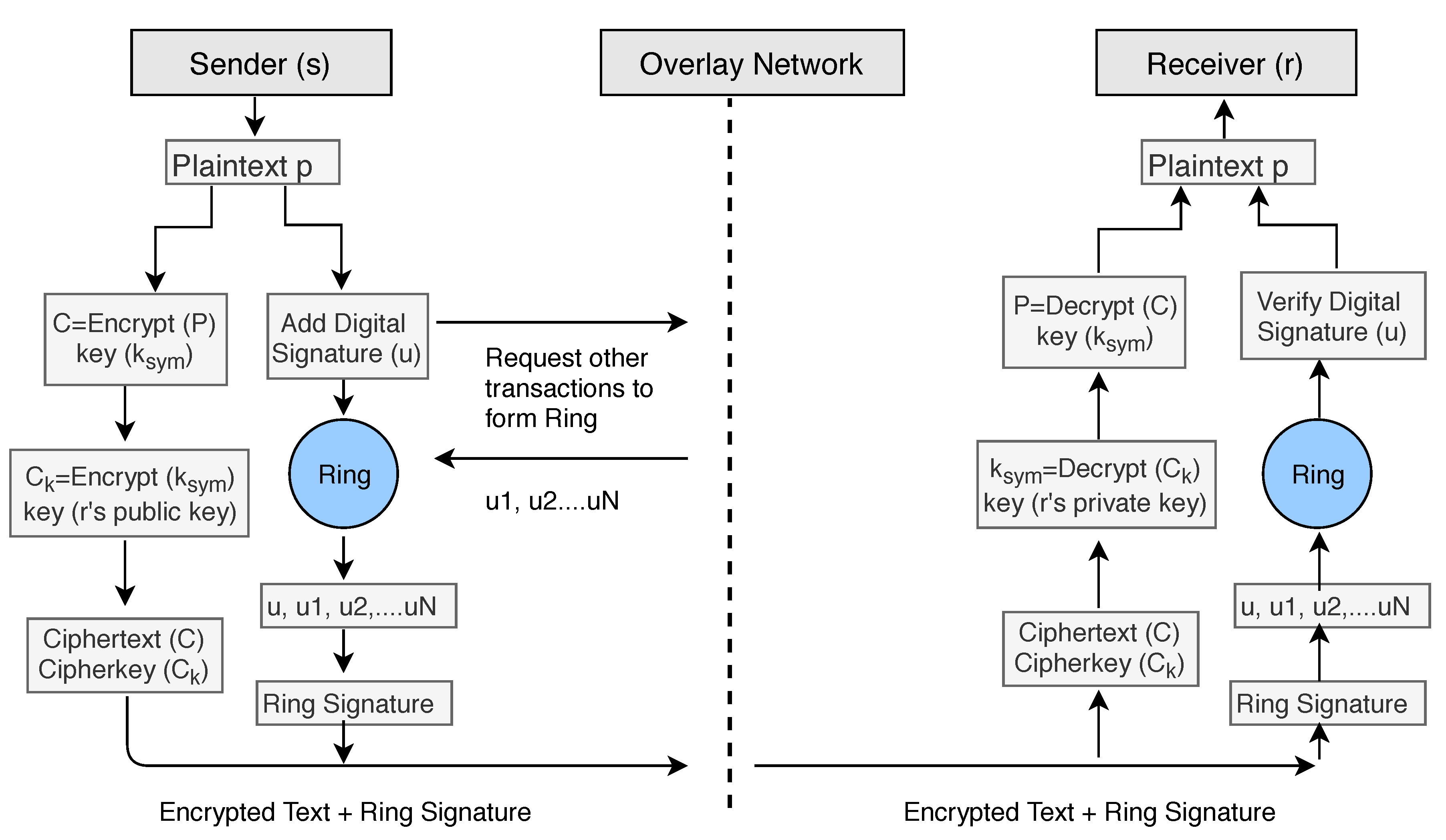
can be used to verify data on the receiver’s side. To apply the Anonymity of the patient or user, we add ring signature in our Algorithm 2. The user will ask the network for other accounts who also want to add ring signature to their transactions. The network will provide him/her a set of users who also wish to apply ring signature. The sender’s transaction is then mixed with other users’ transactions and then send it over the network. No one will be able to identify the original signer of the ring group. The process is described in the block diagram (see
Figure 11) of our model.
| Algorithm 2 Ring Signature and Public Key Sharing. |
- 1:
functionSignature () - 2:
if user chose anonymity over blockchain then - 3:
Generate an asymmetric public-private key pair - 4:
calculate hash of the - 5:
Create the Digital Signature using and signers private key - 6:
Share the public key to the receiver using Diffie–Hellman key exchange - 7:
Mix the signature with another network group to form a ring - 8:
end if - 9:
end function
|
To decrypt the ciphertext data
C (Algorithm 3), we need the symmetric key
. The symmetric key was encrypted using the public key
of the receiver, and therefore receivers private key
can only decrypt the symmetric key. We firstly decrypt the
using the private key
of the receiver and get the original symmetric key
. We apply the key to the ciphertext
C and get the original plaintext or data file.
| Algorithm 3 Data Decryption. |
- 1:
Input: Encrypted file C, Encrypted symmetric key () - 2:
Output: Decrypted - 3:
functionDecryption () - 4:
) - 5:
() - 6:
end function
|
During the verification process (Algorithm 4), Verifier generates the hash value
of received data (ciphertext) using the same hash function. Also, Verifier feeds the digital signature and the verification key into the verification algorithm and extract the hash value
of original data (plaintext). If both hash values are equal, it means data file is not modified during transfer between sender and receiver.
| Algorithm 4 Signature Verification. |
- 1:
Input: Encrypted file C, Signers Public key () - 2:
functionVerification(C, ) - 3:
calculate hash of the received encrypted data file C to be verified - 4:
Using Public key of signer, extract of senders file - 5:
if = then - 6:
return C - 7:
else - 8:
return “Signature incorrect” - 9:
end if - 10:
end function
|
7. Model Implementation
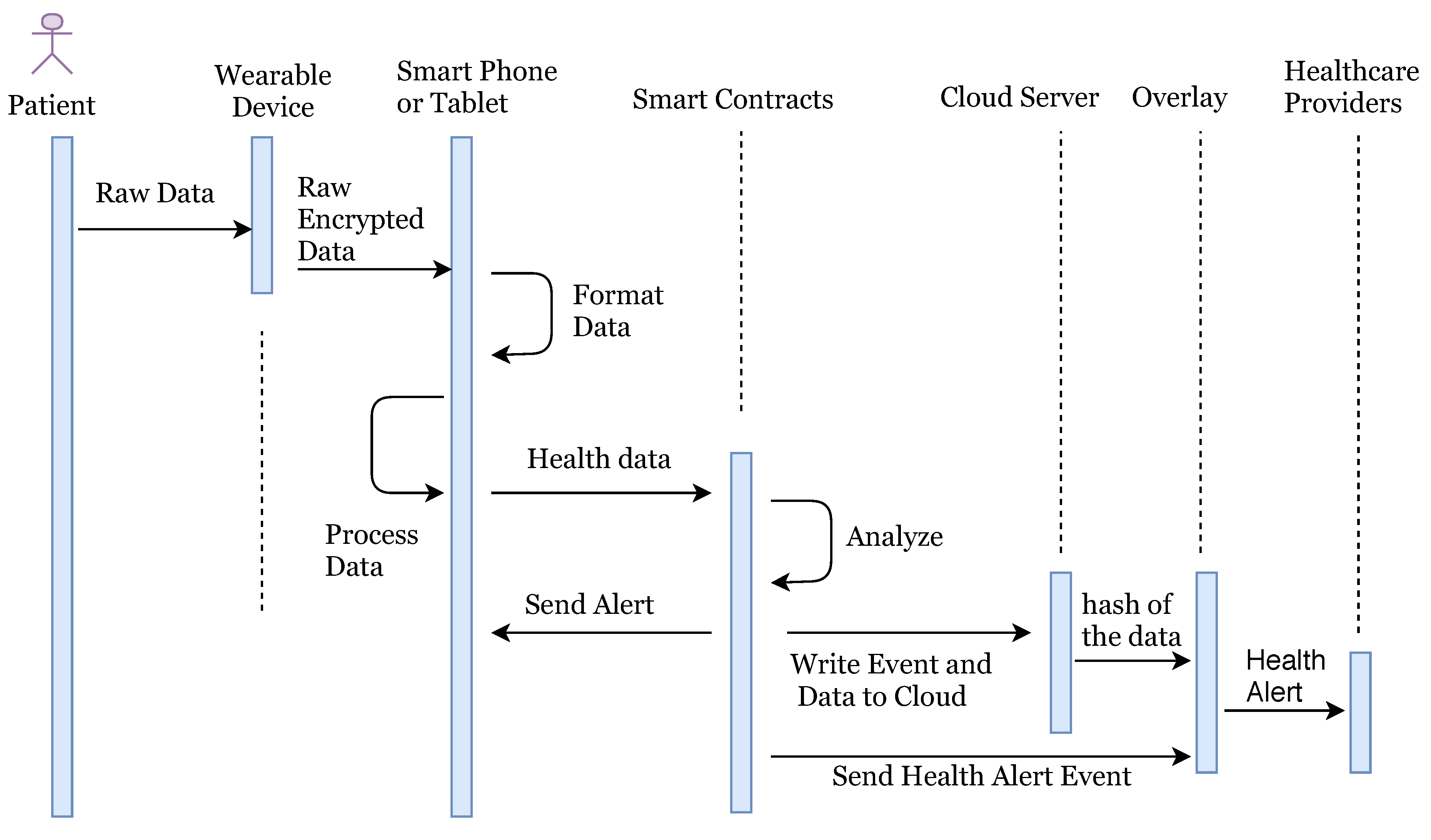
In our system, the patient is equipped with wearable devices such as a blood pressure monitor, insulin pump, or other known devices. Random patients are not allowed to connect with the network, they can only connect once they make an account and provide identity verification documents. Once account verifies the documents provided, users are allowed to access the network. The health information is sent to the smart devices such as a smartphone or tablet for the formatting and aggregation by the application (see
Figure 1). Once complete, the formatted information is sent to the relevant smart contract for full analysis along with the threshold values as required. The threshold value decides whether the health reading is NORMAL as per standard readings or not. If the health reading is ABNORMAL, then the smart contract will create an event and send an alert to the overlay network and to the patient. Also, it stores the abnormal readings to cloud servers and cloud server can then transfer the hash of the stored data to the overlay network. When health data is transferred to the cloud server, the sender adds a digital signature to the data. Overlay network then sends an alert to the health providers. Here, we are not storing the health readings to the overlay network, but we only store the transaction alert to the overlay network.
Health Alert Event should also be anonymous, and privacy preserved to the overlay network. We treat this alert as a transaction of the specific user and apply all advanced cryptographic techniques according to the algorithm explained in
Section 6. Here the entity who is sending the information could be treated as a sender and who is receiving the information could be treated as a receiver. Here we only describe the flow of data in our system and do not describe all encryption/decryption technical details as we have already explained the cryptographic techniques in above sections by taking a general model of the sender, receiver, and network. An overlay network contains the public key information of all connected nodes and hash index of the stored data over the cloud. Once the healthcare provider node gets an alert, he/she access the full health reading of patient for which he/she is authorized over the network. We summarize the logical flow execution of the system in
Figure 12.