Improved Security of E-Healthcare Images Using Hybridized Robust Zero-Watermarking and Hyper-Chaotic System along with RSA
Abstract
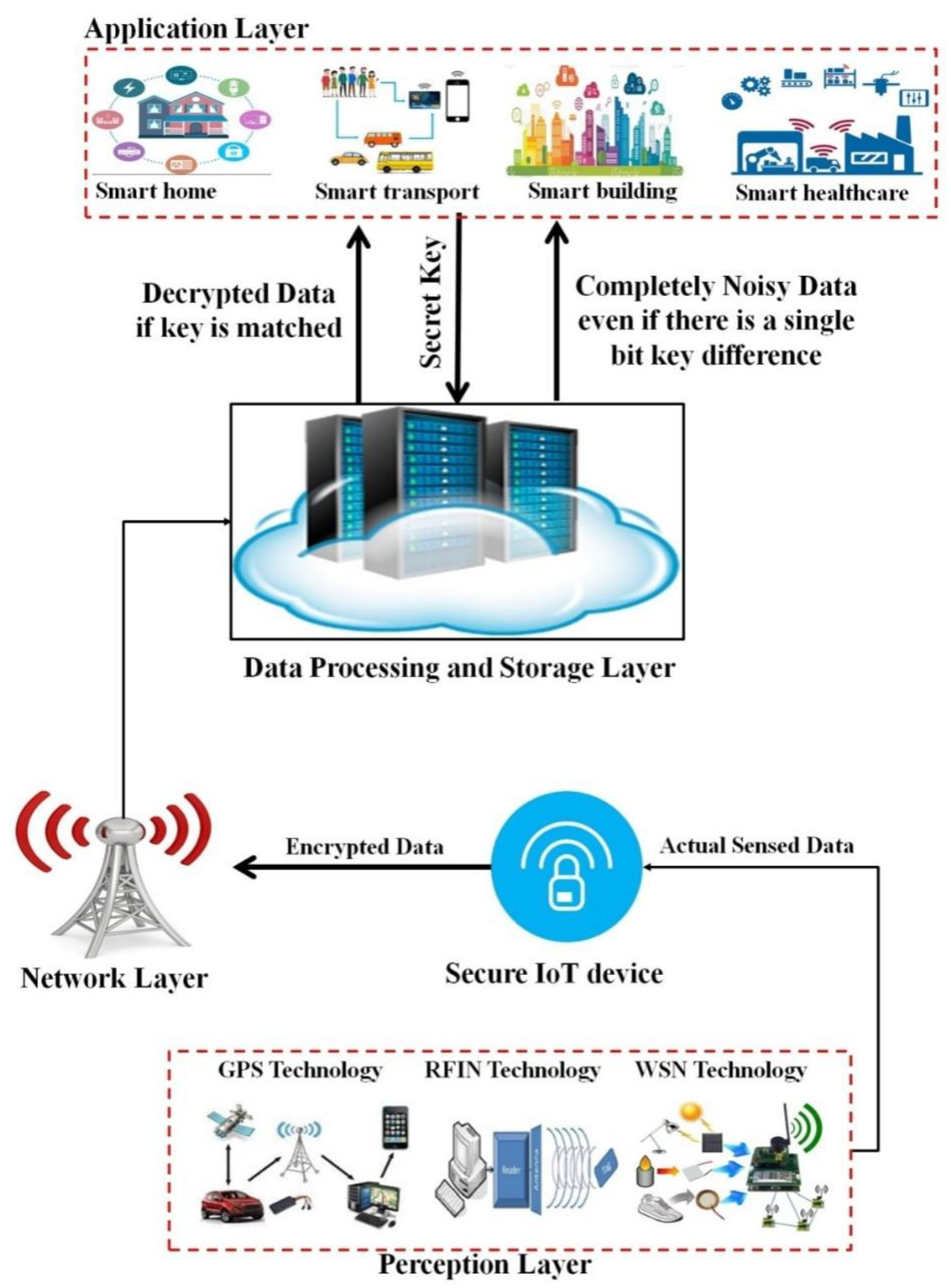
:1. Introduction
- We develop a hybrid technique to encrypt the confidential data related to e-healthcare.
- The hyper-chaotic method and zero-watermarking techniques along with the Rivest–Shamir–Adleman (RSA) algorithm are hybridized to encrypt the data.
- The proposed technique is used to secure multimedia data communications over 6G networks.
2. Literature Review
3. Proposed Model
3.1. Hyper-Chaotic System
yi+1 = bxi − xizi − ui
zi+1 = −czi + xiyi
ui+1 = d(xi + yi)
3.2. Image Encryption Algorithm
Gr(i) = Bn(i + 1) ⊕ Bn(i), 0 ≤ i < j − 1
Gr(i) = Bn(i) i = j − 1
Bn(i) = Gr(i) ⊕ Bn(i + 1), 0 ≤ i < N − 1
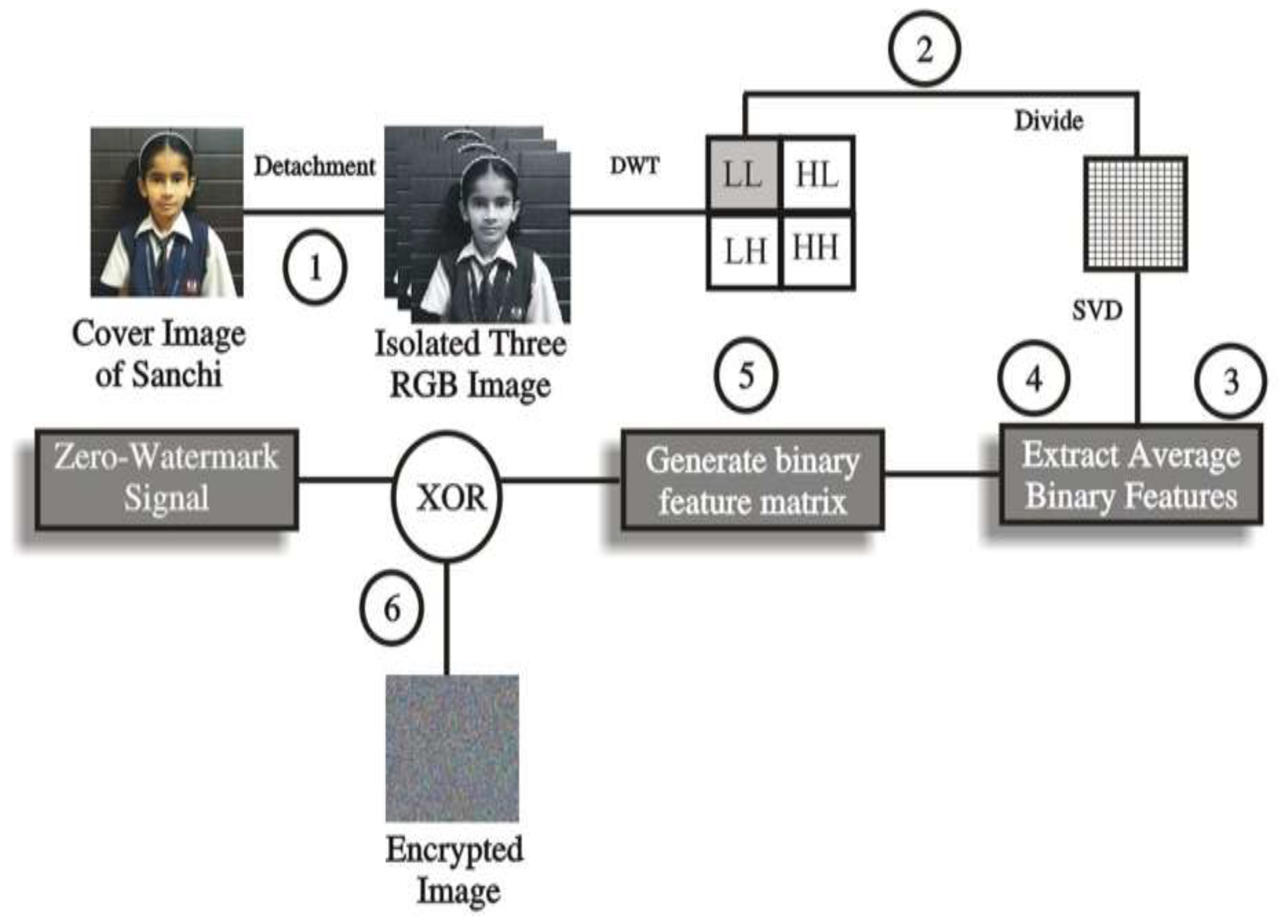
3.3. ZeroWatermarking for the Cover Image
- Stage 1: Decompose the color image into R, G, and B channels.
- Stage 2: With the rotting of DWT, the sub-gatherings and division, which computes the color channels, are decomposed using 2DDWT with the Haar channel and 3 related low-repeat parts, RLL1, GLL1 and BLL1,with a size of (m/2) × (n/2). Thereafter, the computed DWT channels are parceled into non-covering squares Bi,k with sizes b × b and k = 1, 2, 3,..., R × S, while I has a spot with the color channels. The amount of non-covering squares is R × S.
- Stage 3: Computation of the square vitality highlights and the normal vitality highlights of the single channel: The single value decomposition (SVD) method has utilized three segments (RLL1, GLL1, and BLL1) and all squares Bi,k. SVD method decomposes the RGB channels. It has some algebraic properties that give insights into linear transformations. The vitality includes the EFi,k of every square Bi,k, and is processed by its solitary qualities, as indicated by (8). The normal vitality feature AEFi of every part is determined by relating the solitary qualities as far as (9), which is obtained from the traditional force mean.
- Stage 4: Comparison between the square vitality and normal vitality highlights of the single channel: To investigate the neural affective activations during handshakes, we demonstrated that a handshake conveying gentle or aggressive tactile vitality forms produces a stronger activation of the dorso-central insula.The dorso-central insula is activated during imagining as well as during the execution of actions conveying a gentle or rude vitality form. The insula controls autonomic functions through the regulation of the sympathetic and parasympathetic systems. It has a role in regulating the immune system. For each channel, a double trademark network is produced by looking at the vitality, including the EFi,k of each square and the traditional vitality highlight AEFi of the comparing channel, as in (10). The rise of convolution neural networks, accompanying residual learning, has paved the way for the development of single image super resolution (SISR). With the massive number of stacked residual blocks (RBs), the existing deep single image super resolution (SR) models have achieved a great breakthrough in accuracy. However, they cannot be easily utilized to real applications, given their high computational complexity and memory storage. Three channels can be delivered twofold attribute grids as (1) BCHR,(2) BCHG, and (3) BCHB.
- Stage 5: Construction of parallel element network: Two parallel attention modules are used to model the semantic interdependencies in position and channel dimensions, respectively, for scene segmentation. Due to the effectiveness of attention models, we also embed the attention mechanism into the lattice block to combine the RBs adaptively. For a unique cover image, a double component network bond fluctuation model (BFM) (Equation (11)) can be obtained by the larger part casting a ballot of three twofold trademark frameworks using the Bose–Chaudhuri–Hochquenghem code (BCH code) Equation (12). BCHR (BCH-Red), BCHG(BCH-Green), and BCHB(BCH-Blue) are used as in [19,20].
- Stage 6: Copyright images disarray: The parallel copyright image WO of size P × Q is mixed with WS utilizing two decimal hyper-turbulent groupings produced by arrangements of the reasonable introductory states (xo, yo, zo, and wo) and parameter denotations (r); those are viewed as keys K1 and K2.
- Stage 7: The mixed image is additionally encoded to WE by a Wo fold hyper-disorganized succession created by appropriate introductory state (xo, yo, zo, wo). Additionally, where the parameters have (r), i.e., denotes the Key K3.
- Stage 8: The signal WZW of the zero watermark is delivered and checked by the performance of the elite -OR (XOR) process between the encoded watermark WE and the equal component of the element network organizer BFM, as shown by (13). Along these lines, WZW corresponds to the primary spread image. Finally, the obtained WZW, K1, K2, and K3 are selected and spared in the authorized advancement database for copyright affirmation. It can be evaluated as:
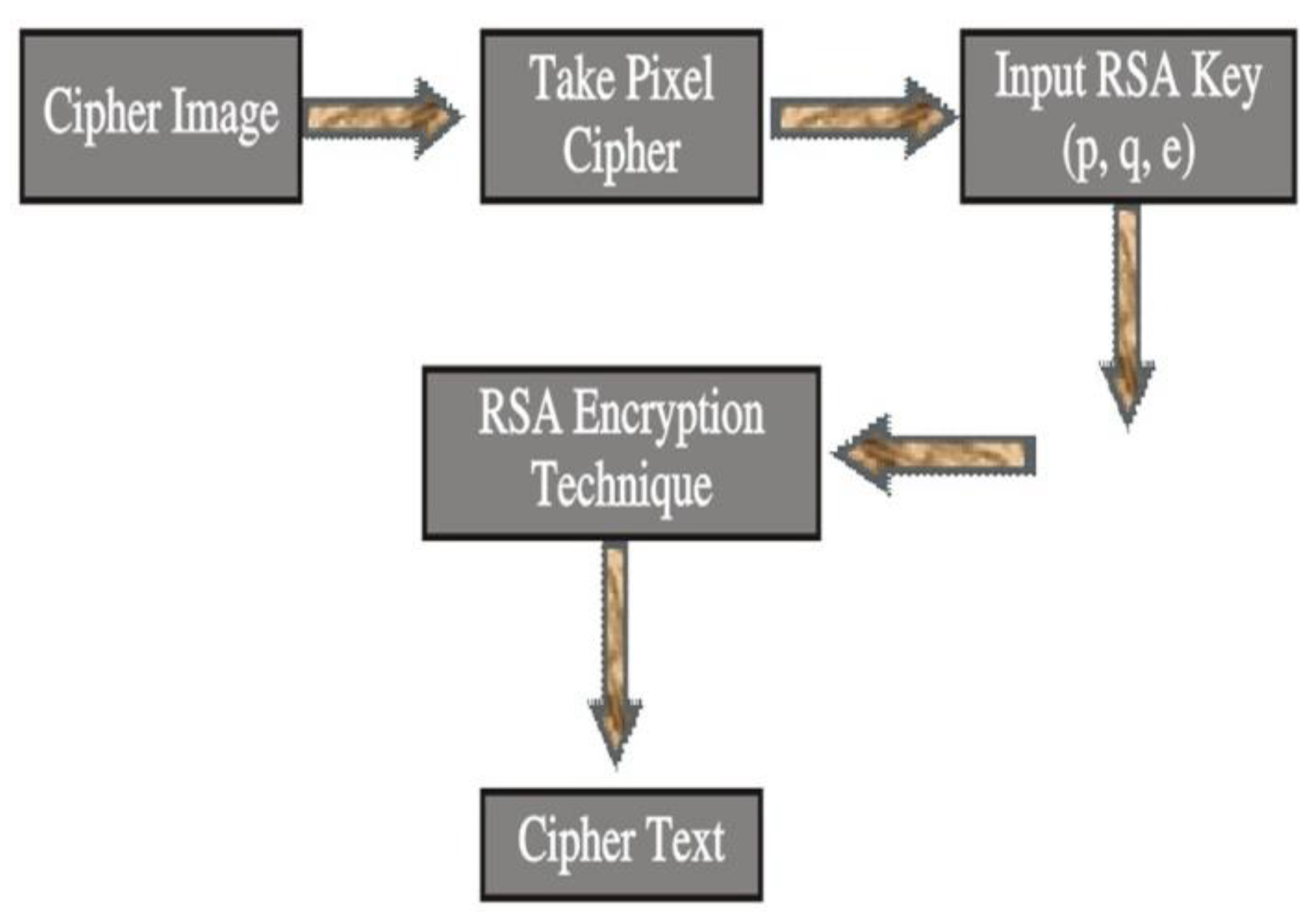
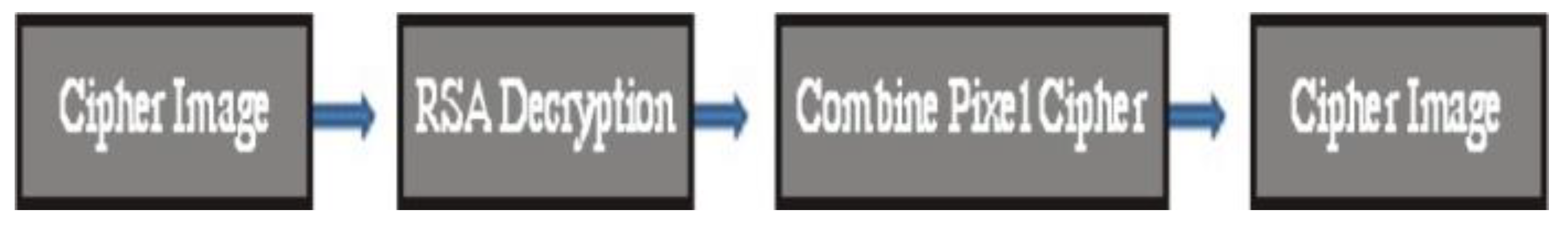
3.4. Rivest–Shamir–Adleman (RSA) Algorithm
4. Performance
4.1. Performance Parameters
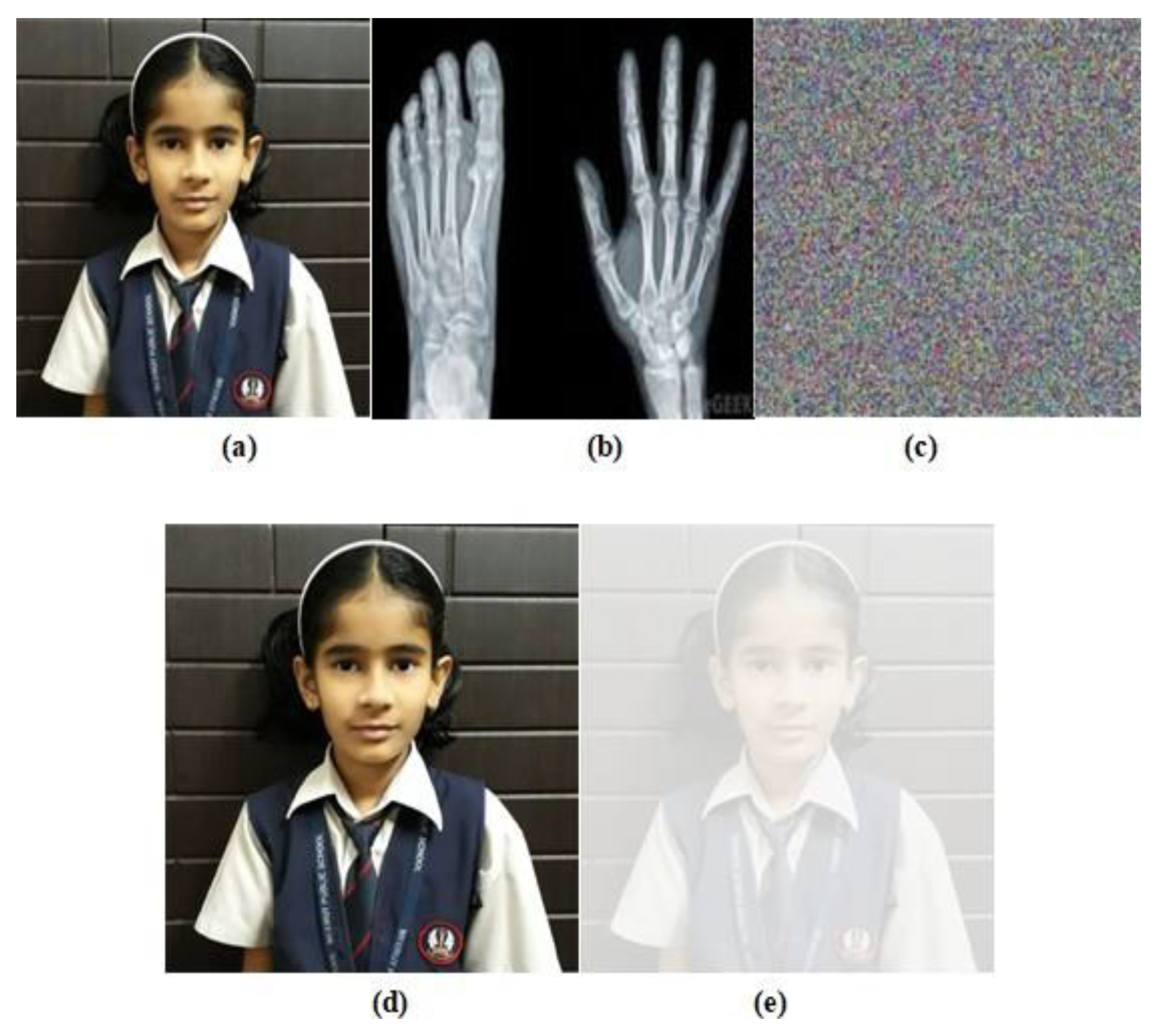
4.2. Visual Analysis
4.3. Quantitative Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- He, D.; Chan, S.; Tang, S. A novel and light weight system to secure wireless medical sensor networks. IEEE J. Biomed. Health Inform. 2014, 18, 316–326. [Google Scholar] [CrossRef] [PubMed]
- Jain, J.; Singh, A. Quantum-based rivest–shamir–adleman (rsa) approach for digital forensic reports. Mod. Phys. Lett. B 2020, 34, 2050085. [Google Scholar] [CrossRef]
- Kaur, M.; Singh, D.; Kumar, V.; Gupta, B.B.; El-Latif, A.A.A. Secure and energy efficient- based e-healthcare framework for green internet of things. IEEE Trans. Green Commun. Netw. 2021, 5, 1223–1231. [Google Scholar] [CrossRef]
- Yi, X.; Bouguettaya, A.; Georgakopoulos, D.; Song, A.; Willemson, J. Privacy protection for wireless medical sensor data. IEEE Trans. Dependable Secur. Comput. 2016, 13, 369–380. [Google Scholar] [CrossRef]
- Jain, J.; Singh, A. Structure of cloudsim toolkit with cloud. Int. J. Eng. Adv. Technol. 2019, 8, 4644–4649. [Google Scholar] [CrossRef]
- Kaur, M.; Singh, D.; Uppal, R.S. Parallel strength pare to evolutionary algorithm-ii based image encryption. IET Image Processing 2020, 14, 1015–1026. [Google Scholar] [CrossRef]
- Ribeiro, L.S.; Viana-Ferreira, C.; Oliveira, J.L.; Costa, C. Xds-I outsourcing proxy: Ensuring confidentiality while preserving interoperability. IEEE J. Biomed. Health Inform. 2014, 18, 1404–1412. [Google Scholar] [CrossRef]
- Jain, J.; Singh, A. Modern and advanced direction on green cloud. J. Eng. Adv. Technol. 2019, 9, 3090–3095. [Google Scholar] [CrossRef]
- Dargan, S.; Kumar, M.A. Comprehensive survey on the biometric recognition systems based on physiological and behavioralmodalities. Expert Syst. Appl. 2020, 143, 113114. [Google Scholar] [CrossRef]
- Drozdowski, P.; Rathgeb, C.; Dantcheva, A.; Damer, N.; Busch, C. Demographic bias in biometrics: A survey on an emerging challenge. IEEE Trans. Technol. Soc. 2020, 1, 89–103. [Google Scholar] [CrossRef]
- Alonso-Fernandez, F.; Farrugia, R.A.; Bigun, J.; Fierrez, J.; Gonzalez-Sosa, E.A. Survey of super- resolution in iris biometrics with evaluation of dictionary-learning. IEEE Access 2019, 7, 6519–6544. [Google Scholar] [CrossRef]
- Czajka, A.; Bowyer, K.W. Presentation attack detection for iris recognition: An assessment of the state-of-the art. ACM Comput. Surv. (CSUR) 2018, 51, 1–35. [Google Scholar] [CrossRef]
- Ding, Y.; Wu, G.; Chen, D.; Zhang, N.; Gong, L.; Cao, M.; Qin, Z. Deepedn: A deep-learning-based image encryption and decryption network for internet of medical things. IEEE Internet Things J. 2021, 8, 1504–1518. [Google Scholar] [CrossRef]
- Wang, F.; Feng, J.; Zhao, Y.; Zhang, X.; Zhang, S.; Han, J. Joint activity recognition and indoor localization with wifi fingerprints. IEEE Access 2019, 7, 80058–80068. [Google Scholar] [CrossRef]
- Liu, X.; Yang, X.; Luo, Y.; Zhang, Q. Verifiable multi- keyword search encryption scheme with anonymous key generation formedical internet of things. IEEE Internet Things J. 2021, 1. [Google Scholar] [CrossRef]
- Haddad, S.; Coatrieux, G.; Moreau-Gaudry, A.; Cozic, M. Joint watermarking-encryption-jpeg-ls for medical image reliability control in encrypted and compressed domains. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2556–2569. [Google Scholar] [CrossRef]
- Qiu, H.; Qiu, M.; Liu, M.; Memmi, G. Secure health data sharing for m edical cyber-physical systems for the healthcare 4.0. IEEE J. Biomed. Health Inform. 2020, 24, 2499–2505. [Google Scholar] [CrossRef]
- Jiang, L.; Chen, L.; Giannetsos, T.; Luo, B.; Liang, K.; Han, J. Towards practical privacy-preserving processing over encrypted data in IOT: An assistive healthcare use case. IEEE Internet Things J. 2019, 6, 10177–10190. [Google Scholar] [CrossRef] [Green Version]
- Puriwat, W.; Tripopsakul, S. Explaining an adoption and continuance intention to use contactless payment technologies: During the COVID-19 pandemic. Emerg. Sci. J. 2021, 5, 85–95. [Google Scholar] [CrossRef]
- Park, U.; Ross, A.; Jain, A.K. Periocular biometrics in the visible spectrum: A feasibility study. In Proceedings of the 2009 IEEE 3rd International Conference on Biometrics: Theory, Applications, and Systems, Washington, DC, USA, 28–30 September 2019; IEEE: Piscataway, NJ, USA, 2009; pp. 1–6. [Google Scholar]
- Park, U.; Jillela, R.R.; Ross, A.; Jain, A.K. Periocular biometrics in the visible spectrum. IEEE Trans. Inf. Forensics Secur. 2011, 6, 96–106. [Google Scholar] [CrossRef] [Green Version]
- Alonso-Fernandez, F.; Bigun, J. Eye detection by complex filtering for periocular recognition. In Proceedings of the 2nd International Workshop on Biometrics and Forensics, Valletta, Malta, 27–28 March 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–6. [Google Scholar]
- Kumari, P.; Seeja, K. Periocular biometrics: A survey. J. King Saud Univ.-Comput. Inf. Sci. 2019, 91, 11. [Google Scholar] [CrossRef]
- Nigam, I.; Vatsa, M.; Singh, R. Ocular biometrics: A survey of modalities and fusion approaches. Inf. Fusion 2015, 26, 1–35. [Google Scholar] [CrossRef]
- Tiong, L.C.O.; Teoh, A.B.J.; Lee, Y. Periocular recognition in the wild with orthogonal combination of local binary coded patternindual-stream convolutional neural network. In Proceedings of the 2019 International Conference on Biometrics (ICB), Crete, Greece, 4–7 June 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Raffei, A.F.M.; Sutikno, T.; Asmuni, H.; Hassan, R.; Othman, R.M.; Kasim, S.; Riyadi, M.A. Fusion iris and periocular recognitions in non-cooperative environment. Indones. J. Electr. Eng. Inform. 2019, 7, 543–554. [Google Scholar]
- Kumar, K.K.; Pavani, M. Periocular region-based age-invariant face recognition using local binary pattern. In Microelectronics, Electromagnetics and Telecommunications; Springer: Andhra Pradesh, India, 2019; pp. 713–720. [Google Scholar]
- Bshi, S.; Sa, P.K.; Wang, H.; Barpanda, S.S.; Majhi, B. Fast periocular authentication in handheld devices with reduced phase intensive local pattern. Multimed. Tools Appl. 2018, 77, 17595–17623. [Google Scholar]
- Castrillon-Santana, M.; Lorenzo-Navarro, J.; Ramon-Balmaseda, E. On using periocular biometric for gender classification in the wild. Pattern Recognit. Lett. 2016, 82, 181–189. [Google Scholar] [CrossRef]
- Zhao, Z.; Kumar, A. Accurate periocular recognition under less constrained environment using semantics assisted convolutional neural network. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1017–1030. [Google Scholar] [CrossRef]
- Mustaqeem Kwon, S. ACNN-assisted enhanced audio signal processing for speech emotion recognition. Sensors 2020, 20, 183. [Google Scholar] [CrossRef] [Green Version]
- Merkow, J.; Jou, B.; Savvides, M. A nexploration of gender identification using only the periocular region. In Proceedings of the 2010 Fourth IEEE International Conference on Biometrics: Theory, Applications and Systems (BTAS), Washington, DC, USA, 27–29 September 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 1–5. [Google Scholar]
- Chahla, C.; Snoussi, H.; Abdallah, F. Dornaika, Discriminant quaternion local binary pattern embedding for personre-identification through prototype formation and colorcategorization. Eng. Appl. Artif. Intell. 2017, 58, 27–33. [Google Scholar] [CrossRef]
- Zhou, Q.; Fan, H.; Yang, H.; Su, H.; Zheng, S.; Wu, S.; Ling, H. Robust and efficient graph correspondence transfer for personre- identification. IEEE Trans. Image Processing 2021, 30, 1623–1638. [Google Scholar] [CrossRef] [Green Version]
- Yoo, Y.; Baek, J.G. A novel image feature for the remaining useful life time prediction of bearings based on continuous wavelet transform and convolutional neural network. Appl. Sci. 2018, 8, 1102. [Google Scholar] [CrossRef] [Green Version]
- Tan, X.; Triggs, B. Fusing gabor and lbp features ets for kernel-based face recognition. In Proceedings of the International Workshop on Analysis and Modeling of Faces and Gestures, Rio de Janeiro, Brazil, 20 October 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 235–249. [Google Scholar]
- Koushkaki, H.R.; Salehi, M.R.; Abiri, E. Color-based feature extraction with application of facial recognition using tensor-matrix and tensor-tensor analysis. Multimed. Tools Appl. 2020, 79, 5829–5858. [Google Scholar] [CrossRef]
- Li, M.; Yuan, X. Adaptive segmentation-based feature extraction and S-STDM watermarking method for color image. Neural Comput. Appl. 2019, 32, 9181–9220. [Google Scholar] [CrossRef]
- Akter, M.S.; Islam, M.R.; Iimura, Y.; Sugano, H.; Fukumori, K.; Wang, D.; Tanaka, T.; Cichocki, A. Multiband entropy-based feature-extraction method for automatic identification of epileptic focus based on high-frequency components ininterictalieeg. Sci. Rep. 2020, 10, 7044. [Google Scholar] [CrossRef] [PubMed]
- Huang, D.; Shan, C.; Ardabilian, M.; Wang, Y.; Chen, L. Local binary patterns and its application to facial image analysis: A survey. IEEE Trans. Syst. Man Cybern. Part C (Appl. Rev.) 2011, 41, 765–781. [Google Scholar] [CrossRef] [Green Version]
- Koh, J.E.; Acharya, U.R.; Hagiwara, Y.; Raghavendra, U.; Tan, J.H.; Sree, S.V.; Bhandary, S.V.; Rao, A.K.; Sivaprasad, S.; Chua, K.C.; et al. Diagnosis of retinal health in digital fundus images using continuous wavelet transform(cwt) and entropies. Comput. Biol. Med. 2017, 84, 89–97. [Google Scholar] [CrossRef]
- Kiranyaz, S.; Avci, O.; Abdeljaber, O.; Ince, T.; Gabbouj, M.; Inman, D.J. 1d convolutional neural networks and applications: A survey. Mech. Syst. Signal Processing 2021, 151, 107398. [Google Scholar] [CrossRef]
- LeCun, Y.; Bottou, L.; Bengio, Y.; Haffner, P. Gradient-based learning applied to document recognition. Proc. IEEE 1998, 86, 2278–2324. [Google Scholar] [CrossRef] [Green Version]
- Krizhevsky, A.; Sutskever, I.; Hinton, G.E. Imagenet classification with deep convolutional neural networks. Adv. Neural Inf. Processing Syst. 2012, 25, 1097–1105. [Google Scholar] [CrossRef]
- Shamsaldin, A.S.; Fattah, P.; Rashid, T.A.; Al-Salihi, N.K. A study of the applications of convolutional neural networks. J. Sci. Eng. 2019, 3, 31–39. [Google Scholar]
- Hosseini, M.S.; Araabi, B.N.; Soltanian-Zadeh, H. Pigmentmelanin: Pattern for iris recognition. IEEE Trans. Instrum. Meas. 2010, 59, 792–804. [Google Scholar] [CrossRef] [Green Version]
- Proença, H.; Filipe, S.; Santos, R.; Oliveira, J.; Alexandre, L.A. The UBIRIS. v2: A database of visible wavelength iris images captured on-the-move and at-a-distance. IEEE Trans. Pattern Anal. Mach. Intell. 2009, 32, 1529–1535. [Google Scholar] [CrossRef] [PubMed]
- Nordstrom, M.M.; Larsen, M.; Sierakowski, J.; Stegmann, M.B. The IMM face database. Environment 2003, 22, 1319–1331. [Google Scholar]
- Haddad Paouh, H.; Dehghantanha, A.; Khayami, R.; Choo, K.K.R. A deep recurrent neural network-based approach for internet of thing small ware threat hunting. Future Gener. Comput. Syst. 2018, 85, 88–96. [Google Scholar] [CrossRef]
- Conti, M.; Dehghantanha, A.; Franke, K.; Watson, S. Internet of things security and forensics: Challenges and opportunities. Future Gener. Comput. Syst. 2018, 78, 544–546. [Google Scholar] [CrossRef] [Green Version]
- Tan, C.-W.; Kumar, A. Towards online iris and periocular recognition under relaxed imaging constraints. IEEE Trans. Image Processing 2013, 22, 3751–3765. [Google Scholar] [CrossRef] [PubMed]
- Jain, A.; Mittal, P.; Goswami, G.; Vatsa, M.; Singh, R. Person identification at a distance vacuolar biometrics. In Proceedings of the IEEE International Conference on Identity, Security and Behavior Analysis (ISBA 2015), Hong Kong, China, 23–25 March 2015; IEEE: Hyderabad, India, 2015; pp. 1–6. [Google Scholar]
- Gangwar, A.; Joshi, A.; Sharma, R.; Saquib, Z. Person identification based on fusion of left and right periocular region. In Proceedings of the International ConferenceonSignal, ImageandVideoProcessing(ICSIVP2012), Daejeon, Korea, 13–15 January 2012; pp. 13–15. [Google Scholar]
- Proenca, H.; Neves, J.C. A re mini scence of mastermind”: Iris periocular biometrics by in-set cnn iterative analysis. IEEE Trans. Inf. Forensics Secur. 2018, 14, 1702–1712. [Google Scholar] [CrossRef]
- Kwon, S. Att-Net: Enhance demotion recognition system using light weight self-attention module. Appl. Sci. 2021, 11, 107101. [Google Scholar]
- Jain, A.; Kumar, A. Desmogging of still smoggy images using a novel channel prior. J. Ambient Intell. Humaniz. Comput. 2021, 12, 1161–1177. [Google Scholar] [CrossRef]
- Kumar, S.; Jain, A.; Kumar Agarwal, A.; Rani, S.; Ghimire, A. Object-Based Image Retrieval Using the U-Net-Based Neural Network. Comput. Intell. Neurosci. 2021, 2021, 4395646. [Google Scholar] [CrossRef]
- Nepomuceno, E.G.; Nardo, L.G.; Arias-Garcia, J.; Butusov, D.N.; Tutueva, A. Image encryption based on the pseudo-orbits from 1 D chaotic map. Chaos Interdiscip. J. Nonlinear Sci. 2019, 29, 061101. [Google Scholar] [CrossRef]
- Nard, L.G.; Nepomuceno, E.G.; Arias-Garcia, J.; Butusov, D.N. Image encryption using finite-precision error. Chaos Solitons Fractals 2019, 123, 69–78. [Google Scholar] [CrossRef]
- Gao, X.; Yu, J.; Banerjee, S.; Yan, H.; Mou, J. A new image encryption scheme based on fractional-order hyper chaotic system and multiple image fusion. Sci. Rep. 2021, 11, 15737. [Google Scholar] [CrossRef] [PubMed]
- Butusov, D.; Karimov, A.I.; Pyko, N.S.; Bogachev, M. Discrete chaotic maps obtained by symmetric integration. Theory Tools Digit. Chaos Gener. Des. 2018, 509, 955–970. [Google Scholar] [CrossRef]
- Alshahrani, H.M. CoLL- IoT: A Collaborative Intruder Detection System for Internet of Things Devices. Electronics 2021, 10, 848. [Google Scholar] [CrossRef]



| Technique | Palm X-ray | Brain Tumor | Ultrasound | Chest X-ray |
|---|---|---|---|---|
| CGAN [13] | 56.62 | 47.31 | 40.16 | 51.86 |
| VMKS [15] | 56.52 | 43.77 | 47.51 | 52.99 |
| PEC [4] | 44.37 | 50.18 | 59.02 | 57.04 |
| JJL [16] | 58.21 | 52.55 | 51.12 | 59.32 |
| SET [17] | 57.12 | 56.94 | 43.53 | 57.02 |
| SHE [18] | 56.76 | 48.92 | 45.59 | 59.22 |
| Proposed | 59.41 | 58.14 | 60.22 | 60.52 |
| Technique | Palm X-ray | Brain Tumor | Ultrasound | Chest X-ray |
|---|---|---|---|---|
| CGAN [13] | 6.18 | 4.25 | 2.44 | 3.73 |
| VMKS [15] | 4.32 | 5.12 | 2.17 | 2.42 |
| PEC [4] | 4.57 | 4.55 | 6.58 | 3.61 |
| JJL [16] | 1.64 | 3.45 | 5.99 | 8.55 |
| SET [17] | 5.05 | 6.92 | 4.61 | 4.32 |
| SHE [18] | 3.29 | 4.94 | 5.31 | 2.08 |
| Proposed | 1.44 | 2.25 | 1.97 | 1.88 |
| Technique | Palm X-ray | Brain Tumor | Ultrasound | Chest X-ray |
|---|---|---|---|---|
| CGAN [13] | 7.76 | 7.26 | 7.54 | 7.6 |
| VMKS [15] | 7.51 | 7.59 | 7.45 | 7.39 |
| PEC [4] | 7.21 | 7.72 | 7.5 | 7.07 |
| JJL [16] | 7.65 | 7.37 | 7.03 | 7.43 |
| SET [17] | 7.6 | 7.7 | 7.52 | 7.53 |
| SHE [18] | 7.16 | 7.53 | 7.55 | 7.14 |
| Proposed | 7.59 | 7.53 | 7.38 | 7.43 |
| Encrypted Images | Horizontal Correlation | Vertical Correlation | Diagonal Correlation |
|---|---|---|---|
| Palm X-ray | 0.0045 | 0.0056 | 0.0034 |
| Brain Tumor | 0.0021 | 0.0015 | 0.0010 |
| Ultrasound | 0.0005 | 0.0013 | 0.0036 |
| Chest X-Ray | 0.0037 | 0.0088 | 0.0078 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jain, J.; Jain, A.; Srivastava, S.K.; Verma, C.; Raboaca, M.S.; Illés, Z. Improved Security of E-Healthcare Images Using Hybridized Robust Zero-Watermarking and Hyper-Chaotic System along with RSA. Mathematics 2022, 10, 1071. https://doi.org/10.3390/math10071071
Jain J, Jain A, Srivastava SK, Verma C, Raboaca MS, Illés Z. Improved Security of E-Healthcare Images Using Hybridized Robust Zero-Watermarking and Hyper-Chaotic System along with RSA. Mathematics. 2022; 10(7):1071. https://doi.org/10.3390/math10071071
Chicago/Turabian StyleJain, Jaishree, Arpit Jain, Saurabh Kumar Srivastava, Chaman Verma, Maria Simona Raboaca, and Zoltán Illés. 2022. "Improved Security of E-Healthcare Images Using Hybridized Robust Zero-Watermarking and Hyper-Chaotic System along with RSA" Mathematics 10, no. 7: 1071. https://doi.org/10.3390/math10071071
APA StyleJain, J., Jain, A., Srivastava, S. K., Verma, C., Raboaca, M. S., & Illés, Z. (2022). Improved Security of E-Healthcare Images Using Hybridized Robust Zero-Watermarking and Hyper-Chaotic System along with RSA. Mathematics, 10(7), 1071. https://doi.org/10.3390/math10071071










