Blockchain Application Analysis Based on IoT Data Flow
Abstract
1. Introduction
- The entire process of IoT data flow from data receiving to data visualization is divided into five modules from the perspective of the data processing mode. There is no inductive method based on IoT data flow in the current research review.
- This paper analyzes all data processing modules that combine IoT data and blockchain. Compared with the published overview papers in this field, the content is more comprehensive and the classification more specific.
- The analysis method of the reconstruction diagram is adapted to display the various modules of the Internet of Things data stream processing data and to visualize the application of blockchain technology. The combination of graphics and text makes the expression more intuitive.
- The research analyzed and summarized 82 papers from the past five years, showing the latest research progress of blockchain in the Internet of Things system.
2. Overview of Blockchain
2.1. Working Principle
- The encrypted transaction information is uploaded through the node, and the current node broadcasts the information to the nodes of the whole network in the form of relay forwarding;
- Miners verify the signatures of the collected transaction information and write the effective information into the block;
- The transaction information in a given period is formed into a new candidate block, and the node obtains the workload proof meeting the target difficulty through the PoW consensus mechanism;
- The blocks found by this node are broadcast to the whole network;
- The whole network node verifies this node. When the transaction information is valid and has never existed, it will be added to the blockchain after verification, and a new block extension chain will be created behind this block.
2.2. Consensus Algorithm
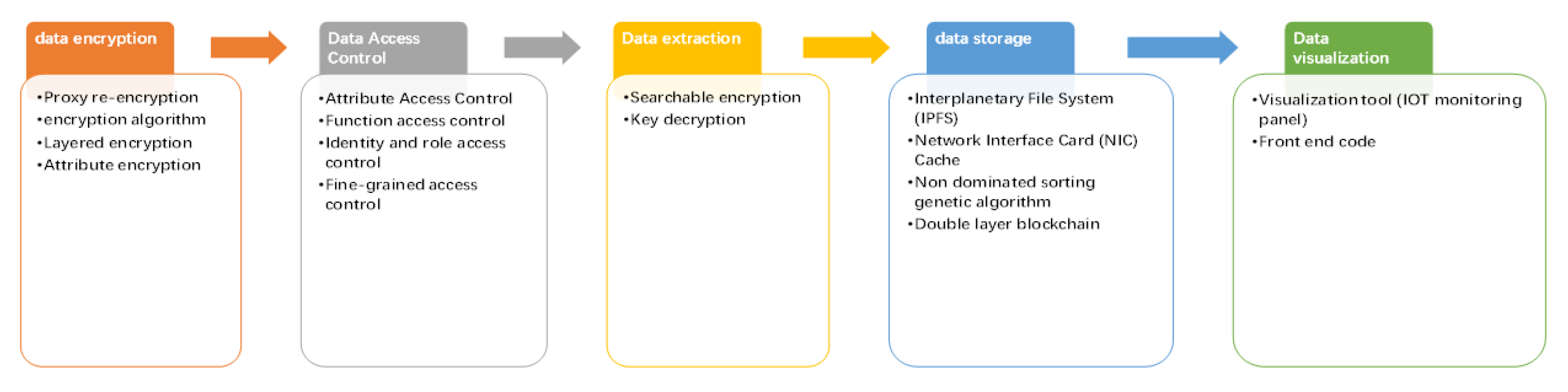
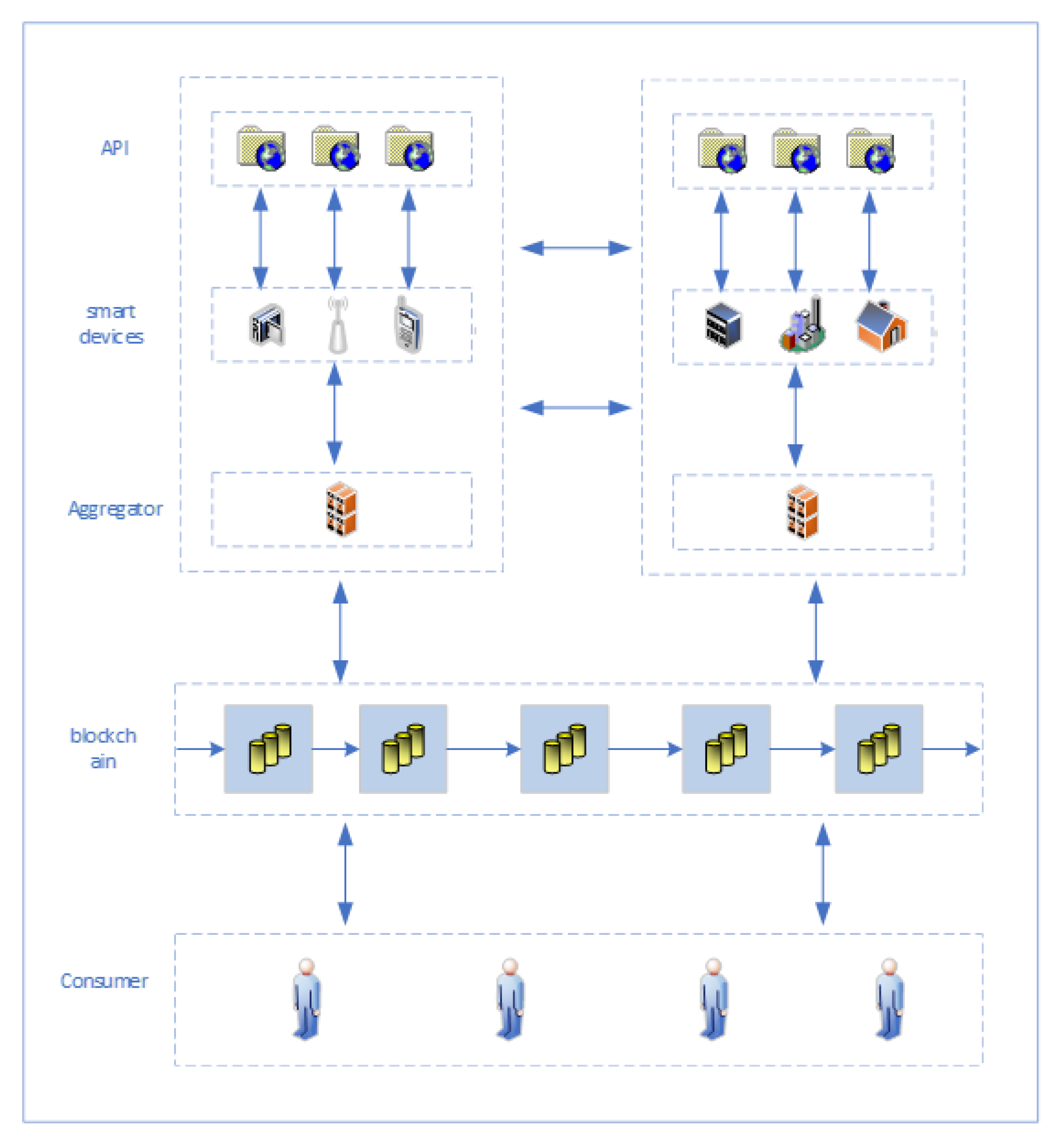
3. Division of IoT Data Flow Module
4. Blockchain Solutions
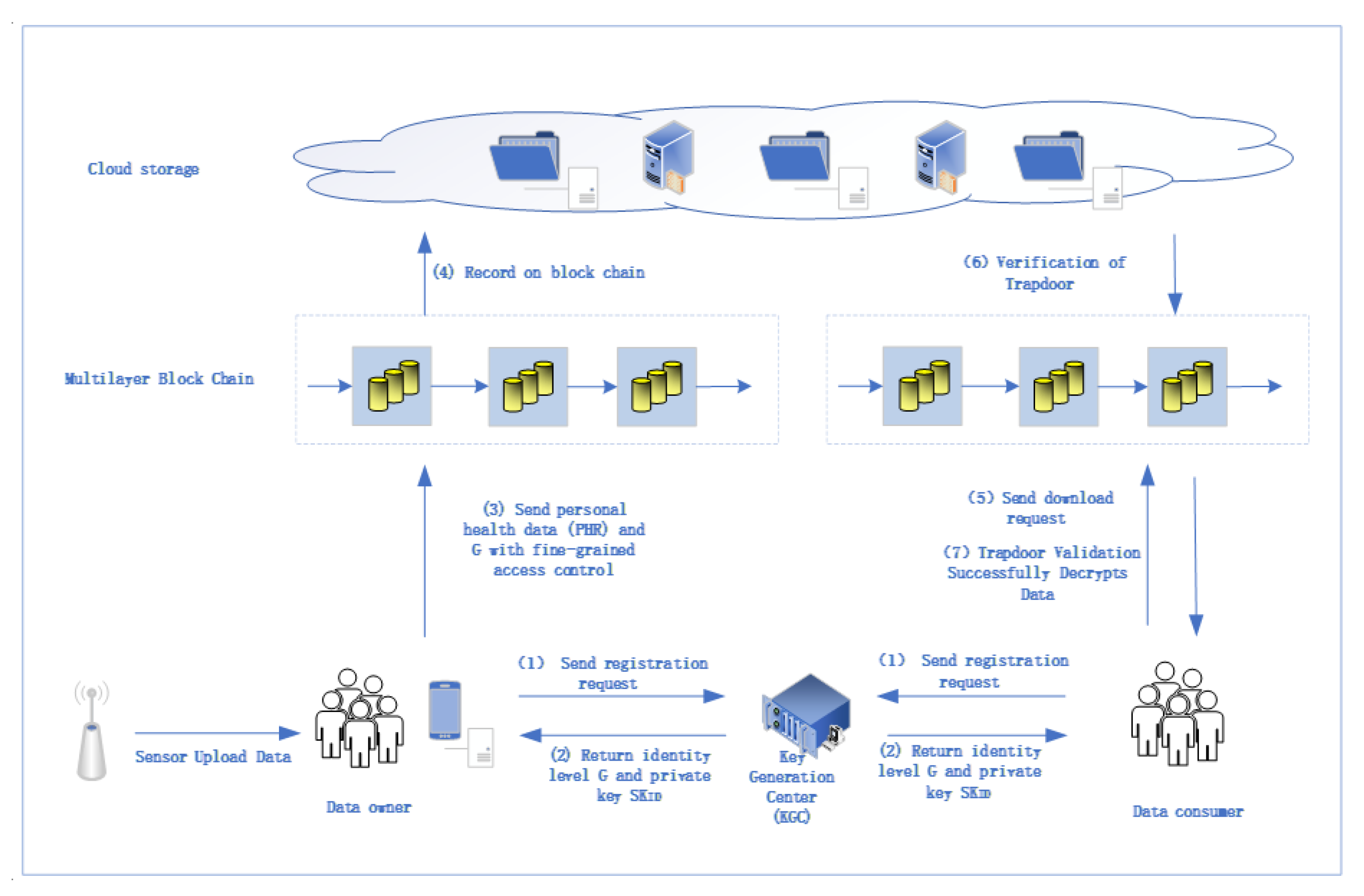
4.1. Data Encryption Module Blockchain Solution
4.1.1. Agent Re-Encryption Technology Based on Blockchain
4.1.2. Blockchain-Based Encryption Algorithm
4.1.3. Hierarchical Encryption Based on Blockchain
4.1.4. Attribute Encryption Based on Blockchain
4.2. Data Access Control Module Blockchain Solution
4.2.1. Attribute Access Control Based on Blockchain
4.2.2. Functional Access Control Based on Blockchain
4.2.3. Blockchain-Based Identity and Role Access Control
4.2.4. Fine-Grained Access Control Based on Blockchain
4.3. Data Extraction Module Blockchain Solution
4.3.1. Searchable Encryption
- Non-degenerate: If A is a generator of G1, e (a, a) maps to a generator of G2, and b, c ∈ G1 exists, satisfying e(b, c) e ≠ 1.
- Bilinear: For any a, b ∈ G1, there exists x, y ∈ , so that the equation e (ax, by) = e (a, b) x y holds.
- Computability: For any a, b ∈ G1, there is a valid algorithm to compute e (a, b).
4.3.2. Key Decryption
| Algorithm 1: PEKS Decryption Algorithm |
| Enter common parameters [params, g], public key, keyword, return ciphertext Trapdoor Generation Algorithm: Enter the public parameter [params], Secret key, keyword to look up, return trapdoor def Trapdoor (params, sk, word): pairing = Pairing(params) hash_value = Element.from_hash (pairing, G1, G2) Hash1(str(word). encode(‘utf-8’)).hexdigest ()) return hash_value ** sk |
4.4. Data Storage Module Blockchain Solution
4.5. Blockchain Data Visualization
5. Challenges and Application
5.1. Blockchain Challenges
- Security (75%), privacy (62.5%), resource limitation (50%), and scalability (50%) are the most important issues in block-based Internet of Things research [78].
- In the blockchain-based Internet of Things, there is a bottleneck in the research process for edge-device distributed trust management [79].
- According to the mapping between the characteristics of the Internet of Things and the blockchain, there is space for each terminal device in the Internet of Things to achieve absolute decentralization through the blockchain. When the blockchain network acts as a complete or lightweight node, different consensus mechanisms will change the effectiveness of the integration of the Internet of Things [80].
- Blockchain technology is used when there are only a few nodes. As it takes some time to read information from the blockchain, it may slow down the speed of information reading.
- Malicious nodes join the blockchain and use the consensus algorithm to obtain all information on the public ledger.
- Blockchain technology is used by the dark net to engage in illegal activities.
5.2. Blockchain Application Scenarios
5.3. Other Data Privacy Protection Methods
5.4. Blockchain Considerations
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Xie, Y.; Shi, j.; Huang, S.; Lei, K. Overview of the research on the Internet of Things for 5G named data network. Comput. Sci. 2020, 47, 217–225. [Google Scholar] [CrossRef]
- Guo, Z.; Lin, Z.; Li, P.; Chen, K. {SkillExplorer}: Understanding the Behavior of Skills in Large Scale. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020. [Google Scholar]
- Wei, S.; Lv, W.; Li, S. Overview of typical security issues in block chain public chain application. J. Softw. 2022, 33, 324–355. [Google Scholar] [CrossRef]
- Yao, Q.; Zhang, D. Overview of identity management technology in block chain system. J. Softw. 2021, 32, 2260–2286. [Google Scholar] [CrossRef]
- Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 November 2008).
- Wang, H.; Zhou, M. Blockchain based medical information security storage model. Comput. Sci. 2019, 46, 174–179. [Google Scholar] [CrossRef]
- Guo, S.; Wang, R.; Zhang, F. Overview of the Principle and Application of Blockchain Technology. Comput. Sci. 2021, 48, 271–281. [Google Scholar] [CrossRef]
- Yuan, Y.; Wang, F. Development Status and Prospect of Blockchain Technology. J. Autom. 2016, 42, 481–494. [Google Scholar] [CrossRef]
- Tian, Z.; Zhao, J. Overview of Blockchain Consensus Mechanism for the Internet of Things. Comput. Appl. 2021, 41, 917–929. [Google Scholar] [CrossRef]
- Leng, Z.; Wang, K.; Liang, W.; Zheng, Y. Overview of research on the application of super ledger in the Internet of Things from the perspective of reconstruction map. Comput. Appl. Res. 2022, 39, 1–13. [Google Scholar] [CrossRef]
- Yang, Y.; Zhou, W.; Zhao, S.; Liu, C.; Zhang, Y.; Wang, H.; Wang, W.; Zhang, Y. Overview of IoT security research: Threats, detection and defense. J. Commun. 2021, 42, 188–205. [Google Scholar] [CrossRef]
- Belfiore, A.; Cuccurullo, C.; Aria, M. IoT in healthcare: A scientometric analysis. Technol. Forecast. Soc. Chang. 2022, 184, 122001. [Google Scholar] [CrossRef]
- Mavrogiorgou, A.; Kiourtis, A.; Kyriazis, D. A pluggable IoT middleware for integrating data of wearable medical devices. Smart Health 2022, 26, 100326. [Google Scholar] [CrossRef]
- Ferrández-Pastor, F.-J.; Mora-Pascual, J.; Díaz-Lajara, D. Agricultural traceability model based on IoT and Blockchain: Application in industrial hemp production. J. Ind. Inf. Integr. 2022, 29, 100381. [Google Scholar] [CrossRef]
- Hu, R.; Shahzad, F.; Abbas, A.; Liu, X. Decoupling the influence of eco-sustainability motivations in the adoption of the green industrial IoT and the impact of advanced manufacturing technologies. J. Clean. Prod. 2022, 339, 130708. [Google Scholar] [CrossRef]
- Gao, Y.; Chen, Y.; Lin, H.; Rodrigues, J.J.P.C. Blockchain Based Secure IoT Data Sharing Framework for SDN-Enabled Smart Communities. In Proceedings of the IEEE INFOCOM 2020-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 6–9 July 2020; pp. 514–519. [Google Scholar] [CrossRef]
- Chen, Y.; Hu, B.; Yu, H.; Duan, Z.; Huang, J. A Threshold Proxy Re-Encryption Scheme for Secure IoT Data Sharing Based on Blockchain. Electronics 2021, 10, 2359. [Google Scholar] [CrossRef]
- Manzoor, A.; Braeken, A.; Kanhere, S.S.; Ylianttila, M.; Liyanage, M. Proxy re-encryption enabled secure and anonymous IoT data sharing platform based on blockchain. J. Netw. Comput. Appl. 2020, 176, 102917. [Google Scholar] [CrossRef]
- Manzoor, A.; Liyanage, M.; Braeke, A.; Kanhere, S.S.; Ylianttila, M. Blockchain Based Proxy Re-Encryption Scheme for Secure IoT Data Sharing. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; pp. 99–103. [Google Scholar]
- Pournaghi, S.M.; Bayat, M.; Farjami, Y. MedSBA: A novel and secure scheme to share medical data based on blockchain technology and attribute-based encryption. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 4613–4641. [Google Scholar] [CrossRef]
- Sharma, S.; Swarnakar, A.; Babu, C.J.; Padmavathy, R.; Kumar, R. An Authenticated Keyword Searchable Conditional Proxy Re-encryption Scheme in Cloud Services. In Proceedings of the 5th IEEE International Conference on Computing, Communication & Security (ICCCS-2020), Patna, Bihar, India, 14–16 October 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Meiliasari, R.P.; Syalim, A.; Yazid, S. Performance Analysis of the Symmetric Proxy Re-encryption Scheme. In Proceedings of the 2019 International Workshop on Big Data and Information Security (IWBIS), Bali, Indonesia, 11 October 2019; pp. 91–96. [Google Scholar] [CrossRef]
- Hussain, S.; Ullah, I.; Khattak, H.; Adnan, M.; Kumari, S.; Ullah, S.S.; Khan, M.A.; Khattak, S.J. A Lightweight and Formally Secure Certificate Based Signcryption With Proxy Re-Encryption (CBSRE) for Internet of Things Enabled Smart Grid. IEEE Access 2020, 8, 93230–93248. [Google Scholar] [CrossRef]
- Loukil, F.; Ghedira-Guegan, C.; Boukadi, K.; Benharkat, A.-N. Privacy-Preserving IoT Data Aggregation Based on Blockchain and Homomorphic Encryption. Sensors 2021, 21, 2452. [Google Scholar] [CrossRef] [PubMed]
- Guo, L.; Xie, H.; Li, Y. Data encryption based blockchain and privacy preserving mechanisms towards big data. J. Vis. Commun. Image Represent. 2019, 70, 102741. [Google Scholar] [CrossRef]
- Priyadarsini, N.R.; Bhama, P.R. B-SCORE–A blockchain based hybrid chaotic signatures for medical image encryption in an IoT environment. Concurr. Comput. Pract. Exp. 2022, 34, e7115. [Google Scholar] [CrossRef]
- Guruprakash, J.; Koppu, S. EC-ElGamal and Genetic Algorithm-Based Enhancement for Lightweight Scalable Blockchain in IoT Domain. IEEE Access 2020, 8, 141269–141281. [Google Scholar] [CrossRef]
- Alshamrani, S.S.; Basha, A.F. IoT data security with DNA-genetic algorithm using blockchain technology. Int. J. Comput. Appl. Technol. 2021, 65, 150–159. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Mehmood, I.; Muhammad, K.; Venegas-Andraca, S.E.; Peng, J. Quantum-Inspired Blockchain-Based Cybersecurity: Securing Smart Edge Utilities in IoT-Based Smart Cities. Inf. Process. Manag. 2021, 58, 102549. [Google Scholar] [CrossRef]
- Makarenko, I.; Semushin, S.; Suhai, S.; Kazmi, S.M.A.; Oracevic, A.; Hussain, R. A Comparative Analysis of Cryptographic Algorithms in the Internet of Things. In Proceedings of the 2020 International Scientific and Technical Conference Modern Computer Network Technologies (MoNeTeC), Moscow, Russia, 27–29 October 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Pang, Z.; Yao, Y.; Li, Q.; Zhang, X.; Zhang, J. Electronic Health Records Sharing Model based on Blockchain with Checkable State PBFT Consensus Algorithm. IEEE Access 2022, 10, 87803–87815. [Google Scholar] [CrossRef]
- Xie, X.; Chen, Y.-C. Decentralized Data Aggregation: A New Secure Framework Based on Lightweight Cryptographic Algorithms. In Proceedings of the 2021 IEEE Conference on Dependable and Secure Computing (DSC), Aizuwakamatsu, Fukushima, Japan, 30 January–2 February 2021; pp. 1–2. [Google Scholar] [CrossRef]
- Pavithran, D.; Al-Karaki, J.N.; Shaalan, K. Edge-Based Blockchain Architecture for Event-Driven IoT using Hierarchical Identity Based Encryption. Inf. Process. Manag. 2021, 58, 102528. [Google Scholar] [CrossRef]
- Zhang, J.; Yang, Y.; Liu, X.; Ma, J. An Efficient Blockchain-Based Hierarchical Data Sharing for Healthcare Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 7139–7150. [Google Scholar] [CrossRef]
- Rahulamathavan, Y.; Phan, R.C.-W.; Rajarajan, M.; Misra, S.; Kondoz, A. Privacy-Preserving Blockchain Based IoT Ecosystem Using Attribute-Based Encryption. In Proceedings of the 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Bhubaneswar, India, 17–20 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Lu, X.; Fu, S.; Jiang, C.; Lio, P. A Fine-Grained IoT Data Access Control Scheme Combining Attribute-Based Encryption and Blockchain. Secur. Commun. Networks 2021, 2021, 1–13. [Google Scholar] [CrossRef]
- Zhang, Y.; Nakanishi, R.; Sasabe, M.; Kasahara, S. Combining IOTA and Attribute-Based Encryption for Access Control in the Internet of Things. Sensors 2021, 21, 5053. [Google Scholar] [CrossRef]
- Yu, G.; Zha, X.; Wang, X.; Ni, W.; Yu, K.; Yu, P.; Zhang, J.A.; Liu, R.P.; Guo, Y.J. Enabling Attribute Revocation for Fine-Grained Access Control in Blockchain-IoT Systems. IEEE Trans. Eng. Manag. 2020, 67, 1213–1230. [Google Scholar] [CrossRef]
- Liu, S.; Yu, J.; Xiao, Y.; Wan, Z.; Wang, S.; Yan, B. BC-SABE: Blockchain-Aided Searchable Attribute-Based Encryption for Cloud-IoT. IEEE Internet Things J. 2020, 7, 7851–7867. [Google Scholar] [CrossRef]
- Guo, R.; Yang, G.; Shi, H.; Zhang, Y.; Zheng, D. O3-R-CP-ABE: An Efficient and Revocable Attribute-Based Encryption Scheme in the Cloud-Assisted IoMT System. IEEE Internet Things J. 2021, 8, 8949–8963. [Google Scholar] [CrossRef]
- Islam, A.; Madria, S. A Permissioned Blockchain Based Access Control System for IOT. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 469–476. [Google Scholar] [CrossRef]
- Yang, Q.; Zhang, M.; Zhou, Y.; Wang, T.; Xia, Z.; Yang, B. A Non-Interactive Attribute-Based Access Control Scheme by Blockchain for IoT. Electronics 2021, 10, 1855. [Google Scholar] [CrossRef]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A Novel Attribute-Based Access Control Scheme Using Blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Zaidi, S.Y.A.; Shah, M.A.; Khattak, H.A.; Maple, C.; Rauf, H.T.; El-Sherbeeny, A.M.; El-Meligy, M.A. An Attribute-Based Access Control for IoT Using Blockchain and Smart Contracts. Sustainability 2021, 13, 10556. [Google Scholar] [CrossRef]
- Wang, P.; Yue, Y.; Sun, W.; Liu, J. An Attribute-Based Distributed Access Control for Blockchain-Enabled IoT. In Proceedings of the 2019 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Barcelona, Spain, 21–23 October 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Gao, S.; Piao, G.; Zhu, J.; Ma, X.; Ma, J. TrustAccess: A Trustworthy Secure Ciphertext-Policy and Attribute Hiding Access Control Scheme Based on Blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5784–5798. [Google Scholar] [CrossRef]
- Sivaselvan, N.; Bhat, V.; Rajarajan, M. Blockchain-Based Scheme for Authentication and Capability-based Access Control in IoT Environment. In Proceedings of the 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 28–31 October 2020; pp. 0323–0330. [Google Scholar] [CrossRef]
- Bouras, M.A.; Xia, B.; Abuassba, A.O.; Ning, H.; Lu, Q. IoT-CCAC: A blockchain-based consortium capability access control approach for IoT. PeerJ Comput. Sci. 2021, 7, e455. [Google Scholar] [CrossRef]
- Liu, Y.; Lu, Q.; Chen, S.; Qu, Q.; O’Connor, H.; Choo, K.-K.R.; Zhang, H. Capability-based IoT access control using blockchain. Digit. Commun. Netw. 2020, 7, 463–469. [Google Scholar] [CrossRef]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. BlendCAC: A Smart Contract Enabled Decentralized Capability-Based Access Control Mechanism for the IoT. Computers 2018, 7, 39. [Google Scholar] [CrossRef]
- Pinjala, S.K.; Sivalingam, K.M. DCACI: A Decentralized Lightweight Capability-Based Access Control Framework Using IOTA for INTERNET of Things. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 13–18. [Google Scholar] [CrossRef]
- Nakamura, Y.; Zhang, Y.; Sasabe, M.; Kasahara, S. Capability-Based Access Control for the Internet of Things: An Ethereum Blockchain-Based Scheme. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Nakamura, Y.; Zhang, Y.; Sasabe, M.; Kasahara, S. Exploiting Smart Contracts for Capability-Based Access Control in the Internet of Things. Sensors 2020, 20, 1793. [Google Scholar] [CrossRef]
- Bouras, M.A.; Lu, Q.; Dhelim, S.; Ning, H. A Lightweight Blockchain-Based IoT Identity Management Approach. Futur. Internet 2021, 13, 24. [Google Scholar] [CrossRef]
- Cui, Z.; Xue, F.; Zhang, S.; Cai, X.; Cao, Y.; Zhang, W.; Chen, J. A Hybrid BlockChain-Based Identity Authentication Scheme for Multi-WSN. IEEE Trans. Serv. Comput. 2020, 13, 241–251. [Google Scholar] [CrossRef]
- Vallois, V.; Mehaoua, A.; Amziani, M. Blockchain-Based Identity and Access Management in Industrial IoT Systems. In Proceedings of the 2021 IFIP/IEEE International Symposium on Integrated Network Management (IM), Bordeaux, France, 17–21 May 2021; pp. 623–627. [Google Scholar]
- Alamri, B.; Crowley, K.; Richardson, I. Blockchain-Based Identity Management Systems in Health IoT: A Systematic Review. IEEE Access 2022, 10, 59612–59629. [Google Scholar] [CrossRef]
- Truong, H.T.T.; Almeida, M.; Karame, G.; Soriente, C. Towards Secure and Decentralized Sharing of IoT Data. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 176–183. [Google Scholar] [CrossRef]
- Gebresilassie, S.K.; Rafferty, J.; Morrow, P.; Chen, L.L.; Abu-Tair, M.; Cui, Z. Distributed, Secure, Self-Sovereign Identity for IoT Devices. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Fotohi, R.; Aliee, F.S. Securing communication between things using blockchain technology based on authentication and SHA-256 to improving scalability in large-scale IoT. Comput. Netw. 2021, 197, 108331. [Google Scholar] [CrossRef]
- Sharma, P.; Moparthi, N.R.; Namasudra, S.; Shanmuganathan, V.; Hsu, C. Blockchain-based IoT architecture to secure healthcare system using identity-based encryption. Expert Syst. 2021, 39, e12915. [Google Scholar] [CrossRef]
- Ameer, S.; Benson, J.; Sandhu, R. An Attribute-Based Approach toward a Secured Smart-Home IoT Access Control and a Comparison with a Role-Based Approach. Information 2022, 13, 60. [Google Scholar] [CrossRef]
- Amoon, M.; Altameem, T.; Altameem, A. RRAC: Role based reputed access control method for mitigating malicious impact in intelligent IoT platforms. Comput. Commun. 2020, 151, 238–246. [Google Scholar] [CrossRef]
- Ding, Y.; Sato, H. Bloccess: Towards Fine-Grained Access Control Using Blockchain in a Distributed Untrustworthy Environment. In Proceedings of the 2020 8th IEEE International Conference on Mobile Cloud Computing, Services, and Engineering (MobileCloud), Oxford, UK, 3–6 August 2020; pp. 17–22. [Google Scholar] [CrossRef]
- Xu, H.; He, Q.; Li, X.; Jiang, B.; Qin, K. BDSS-FA: A Blockchain-Based Data Security Sharing Platform With Fine-Grained Access Control. IEEE Access 2020, 8, 87552–87561. [Google Scholar] [CrossRef]
- Zhu, Y.; Wu, X.; Hu, Z. Fine Grained Access Control Based on Smart Contract for Edge Computing. Electronics 2022, 11, 167. [Google Scholar] [CrossRef]
- Bao, Y.; Qiu, W.; Tang, P.; Cheng, X. Efficient, Revocable, and Privacy-Preserving Fine-Grained Data Sharing With Keyword Search for the Cloud-Assisted Medical IoT System. IEEE J. Biomed. Health Inform. 2021, 26, 2041–2051. [Google Scholar] [CrossRef]
- Chen, L.; Huang, K.; Manulis, M.; Sekar, V. Password-authenticated searchable encryption. Int. J. Inf. Secur. 2020, 20, 675–693. [Google Scholar] [CrossRef]
- Xiang, X.; Zhao, X. Blockchain-assisted searchable attribute-based encryption for e-health systems. J. Syst. Arch. 2022, 124, 102417. [Google Scholar] [CrossRef]
- Subathra, G.; Antonidoss, A.; Singh, B.K. Decentralized Consensus Blockchain and IPFS-Based Data Aggregation for Efficient Data Storage Scheme. Secur. Commun. Networks 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Ye, H.; Park, S. Reliable Vehicle Data Storage Using Blockchain and IPFS. Electronics 2021, 10, 1130. [Google Scholar] [CrossRef]
- Sakakibara, Y.; Morishima, S.; Nakamura, K.; Matsutani, H. A Hardware-Based Caching System on FPGA NIC for Blockchain. IEICE Trans. Inf. Syst. 2018, E101.D, 1350–1360. [Google Scholar] [CrossRef]
- Xu, M.; Feng, G.; Ren, Y.; Zhang, X. On Cloud Storage Optimization of Blockchain With a Clustering-Based Genetic Algorithm. IEEE Internet Things J. 2020, 7, 8547–8558. [Google Scholar] [CrossRef]
- Pal, S.; Rabehaja, T.; Hill, A.; Hitchens, M.; Varadharajan, V. On the integration of blockchain to the internet of things for enabling access right delegation. IEEE Internet Things J. 2019, 7, 2630–2639. [Google Scholar] [CrossRef]
- Song, J.; Nang, J.; Jang, J. Design of Anomaly Detection and Visualization Tool for IoT Blockchain. In Proceedings of the 2018 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 12–14 December 2018; pp. 1464–1465. [Google Scholar] [CrossRef]
- Scarlato, M.; Catte, M.; Massidda, C.; Modica, P.; Pinna, A.; Piras, R.; Tonelli, R.; Jeon, M. BATDIV: A Blockchain-based Approach for Tourism Data Insertion and Visualization. In Proceedings of the 2021 IoT Vertical and Topical Summit for Tourism, Cagliari, Italy, 20–24 September 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Sharma, V.; Lal, N. A Detail Dominant Approach for IoT and Blockchain with their Research Challenges. In Proceedings of the 2020 International Conference on Emerging Trends in Communication, Control and Computing (ICONC3), Lakshmangarh, India, 21–22 February 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Tapia, J.Y.; Avila-Pesantez, D. Blockchain and IoT-Challenges and Its Role in Security: A Brief Overview. In Proceedings of the 2021 IEEE URUCON, Montevideo, Uruguay, 24–26 November 2021; pp. 504–507. [Google Scholar] [CrossRef]
- Fortino, G. Keynote Speech 1: Blockchain-Enabled Trust in Edge-Based Internet of Things Architectures: State of the Art and Research Challenges. In Proceedings of the 2021 Third International Conference on Blockchain Computing and Applications (BCCA), Tartu, Estonia, 15–17 November 2021; p. 1. [Google Scholar] [CrossRef]
- Romashkova, I.; Komarov, M.; Ometov, A. Demystifying Blockchain Technology for Resource-Constrained IoT Devices: Parameters, Challenges and Future Perspective. IEEE Access 2021, 9, 129264–129277. [Google Scholar] [CrossRef]
- Ma, C.; Yuan, L.; Han, L.; Ding, M.; Bhaskar, R.; Li, J. Data Level Privacy Preserving: A Stochastic Perturbation Approach based on Differential Privacy. IEEE Trans. Knowl. Data Eng. 2021, 1. [Google Scholar] [CrossRef]
- Hassan, S.; Fazea, Y.; Habbal, A.; Ibrahim, H. Twisted Laguerre-Gaussian Mode Division Multiplexing to Support Blockchain Applications. In Proceedings of the TENCON 2017-2017 IEEE Region 10 Conference, Penang, Malaysia, 5–8 November 2017; pp. 2050–2421. [Google Scholar] [CrossRef]
- Li, Y. User Privacy Protection Technology of Tennis Match Live Broadcast from Media Cloud Platform Based on AES Encryption Algorithm. In Proceedings of the 2020 IEEE 3rd International Conference on Information Systems and Computer Aided Education (ICISCAE), Dalian, China, 27–29 September 2020; pp. 267–269. [Google Scholar] [CrossRef]
- Jaspin, K.; Selvan, S.; Sahana, S.; Thanmai, G. Efficient and Secure File Transfer in Cloud Through Double Encryption Using AES and RSA Algorithm. In Proceedings of the 2021 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 5–7 March 2021; pp. 791–796. [Google Scholar] [CrossRef]
- Karim, H.; Rawat, D.B. TollsOnly Please—Homomorphic Encryption for Toll Transponder Privacy in Internet of Vehicles. IEEE Internet Things J. 2021, 9, 2627–2636. [Google Scholar] [CrossRef]
- Xu, G.; Zhang, J.; Wang, L. An Edge Computing Data Privacy-Preserving Scheme Based on Blockchain and Homomorphic Encryption. In Proceedings of the 2022 International Conference on Blockchain Technology and Information Security (ICBCTIS), Huaihua China, 15–17 July 2022; pp. 156–159. [Google Scholar] [CrossRef]
- Moqurrab, S.A.; Anjum, A.; Tariq, N.; Srivastava, G. Instant_Anonymity: A Lightweight Semantic Privacy Guarantee for 5G-enabled IIoT. IEEE Trans. Ind. Inform. 2022, 19, 951–959. [Google Scholar] [CrossRef]
- Esmeel, T.K.; Hasan, M.; Kabir, M.N.; Firdaus, A. Balancing Data Utility versus Information Loss in Data-Privacy Protection Using k-Anonymity. In Proceedings of the 2020 IEEE 8th Conference on Systems, Process and Control (ICSPC), Melaka, Malaysia, 11–12 December 2020; pp. 158–161. [Google Scholar] [CrossRef]
- Enam, A.; Sakib, S.; Rahman, S. An Algorithm for l-diversity Clustering of a Point-Set. In Proceedings of the 2019 International Conference on Electrical, Computer and Communication Engineering (ECCE), Cox’sBazar, Bangladesh, 7–9 February 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Ren, W.; Ghazinour, K.; Lian, X. kt-Safety: Graph Release via k-Anonymity and t-Closeness. IEEE Trans. Knowl. Data Eng. 2022, 1–12. [Google Scholar] [CrossRef]
- Si, G.; Zhang, Y.; Sun, Y. Privacy Protection Strategy Based on Federated Learning for Smart Park Multi Energy Fusion System. In Proceedings of the 2021 IEEE 4th International Conference on Computer and Communication Engineering Technology (CCET), Beijing, China, 13–15 August 2021; pp. 392–395. [Google Scholar] [CrossRef]
- Blockchain Technology Overview. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2018/NIST.IR.8202.pdf (accessed on 3 October 2018).




| Symbol | Meaning |
|---|---|
| ET | Ciphertext |
| IoT sensors | Data owner |
| Data consumers | Data user |
| GDC | Grade decision center |
| G | Identity level |
| C | Access condition-set |
| SKID | Secret key |
| RKID | Re-encryption key |
| Blockchain Solutions | References | Performance Analysis |
|---|---|---|
| Interplanetary File System (IPFS) + Blockchain | [70,71] | Capacity expansion + secure storage |
| Network interface card (NIC) + blockchain | [72] | Reduce server overload + secure storage |
| Clustering (NSGA-C) + Genetic Algorithm | [73] | Minimum local space |
| Double-layer blockchain | [74] | Secure storage + Security Access + expansion |
| Module Division of IoT Data Flow | Technology or Method | References |
|---|---|---|
| Data Encryption Module Blockchain Solution | Agent Re-encryption Technology Based on Blockchain | [16,17,18,19,20,21,22,23] |
| Blockchain-Based Encryption Algorithm | [24,25,26,27,28,29,30,31,32] | |
| Hierarchical Encryption Based on Blockchain | [33,34] | |
| Attribute Encryption Based on Blockchain | [35,36,37,38,39,40] | |
| Data Access Control Module Blockchain Solution | Attribute Access Control Based on Blockchain | [41,42,43,44,45,46] |
| Function Access Control Based on Blockchain | [47,48,49,50,51,52,53] | |
| Identity and Role Access Control Based on Blockchain | [54,55,56,57,58,59,60,61] | |
| Fine-grained Access Control Based on Blockchain | [64,65,66,67] | |
| Data Extraction Module Blockchain Solution | Searchable Encryption Technology | [68,69] |
| Key Decryption | ||
| Data Storage Module Blockchain Solution | IPFS + NIC + NSGA-C + Double-Layer Blockchain | [70,71,72,73,74] |
| Blockchain Data Visualization | Visualization Tools | [75,76] |
| Privacy Protection Method | Technique | Small Data Loss | Trusted Third Party | A Small Quantity of Computation | Difficult to Be Attacked by a Third Party |
|---|---|---|---|---|---|
| Blockchain Privacy Protection | Consensus Algorithm, Smart Contract | YES | --- | YES | YES |
| Data Perturbation Privacy Protection | Local Differential Privacy | NO | --- | YES | YES |
| Data Encryption Privacy Protection | AES, RSA, ECC | YES | NO | YES | NO |
| Data Anonymous Privacy Protection | K-anonymity, L-Diversity, T-Closeness | YES | YES | NO | NO |
| Federal Learning Privacy Protection | Deep Learning | YES | --- | NO | NO |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, J.; Zhang, X.; Shi, W. Blockchain Application Analysis Based on IoT Data Flow. Electronics 2022, 11, 3907. https://doi.org/10.3390/electronics11233907
Li J, Zhang X, Shi W. Blockchain Application Analysis Based on IoT Data Flow. Electronics. 2022; 11(23):3907. https://doi.org/10.3390/electronics11233907
Chicago/Turabian StyleLi, Juxia, Xing Zhang, and Wei Shi. 2022. "Blockchain Application Analysis Based on IoT Data Flow" Electronics 11, no. 23: 3907. https://doi.org/10.3390/electronics11233907
APA StyleLi, J., Zhang, X., & Shi, W. (2022). Blockchain Application Analysis Based on IoT Data Flow. Electronics, 11(23), 3907. https://doi.org/10.3390/electronics11233907







