Private Blockchain-Driven Digital Evidence Management Systems: A Collaborative Mining and NFT-Based Framework
Abstract
1. Introduction
1.1. Scalability Challenges in DEMSs
1.2. Integrity and Authenticity Challenges in DEMSs
- A self-coordinating nonce-allocation protocol using Verifiable Random Functions (VRFs) that eliminate central authorities, enabling truly decentralised miner coordination.
- Evidence-intrinsic NFTs generated via content-derived fingerprints (pixel intensity summation) rather than external tokenization. This creates tamper-evident bonds between evidence and blockchain records.
1.3. Blockchain as a Solution for DEMSs
1.4. Paper Motivation and Contributions
- We propose a novel DEMS architecture that integrates private blockchain technology to provide a centralised, transparent, and tamper-proof system for managing digital evidence.
- Our system introduces collaborative PoW mining, where multiple miners share the workload to reduce the computational overhead associated with traditional consensus mechanisms. This enhances the scalability challenges of DEMSs.
- Our framework provides integration of Non-Fungible Tokens (NFTs) to maintain the authenticity and integrity of the evidence.
- We use encryption techniques in the blockchain model to enhance the security and verifiability of digital evidence.
1.5. Outline
2. Literature Review
- A decentralised nonce-allocation protocol using Verifiable Random Functions (VRFs) that eliminates coordinator dependencies, enabling trustless miner coordination.
- Evidence-intrinsic NFTs generated directly from pixel data (Algorithm 1), creating cryptographic bonds between evidence and blockchain records—unlike the symbolic tokenization in [24].
| Algorithm 1 Blockchain and ledger generation |
|
2.1. Forensic Challenges with Scalability
2.2. Blockchain Integration in DEMSs
2.3. Advanced Techniques for Securing Digital Evidence
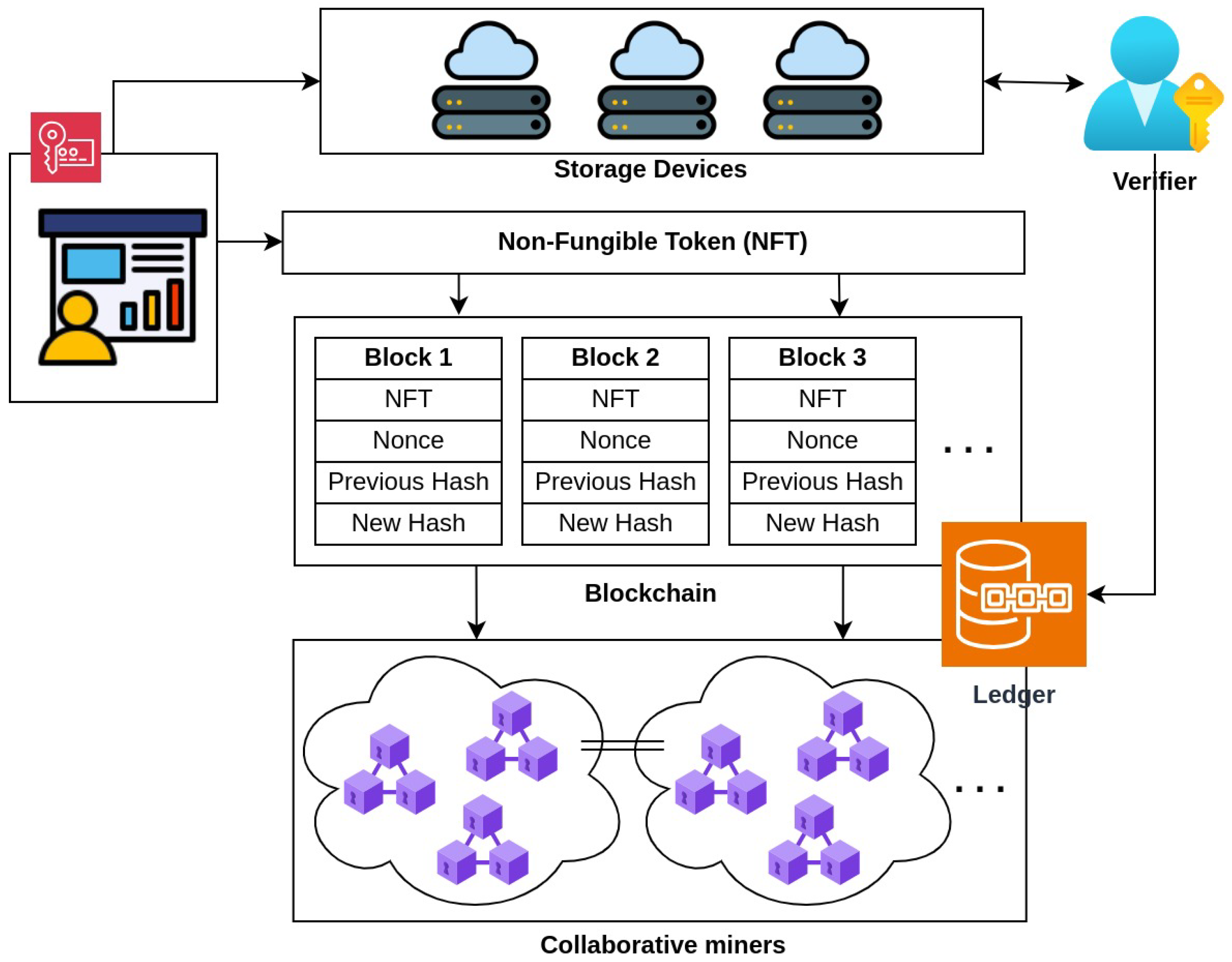
3. Methodology
3.1. Encryption of Digital Data
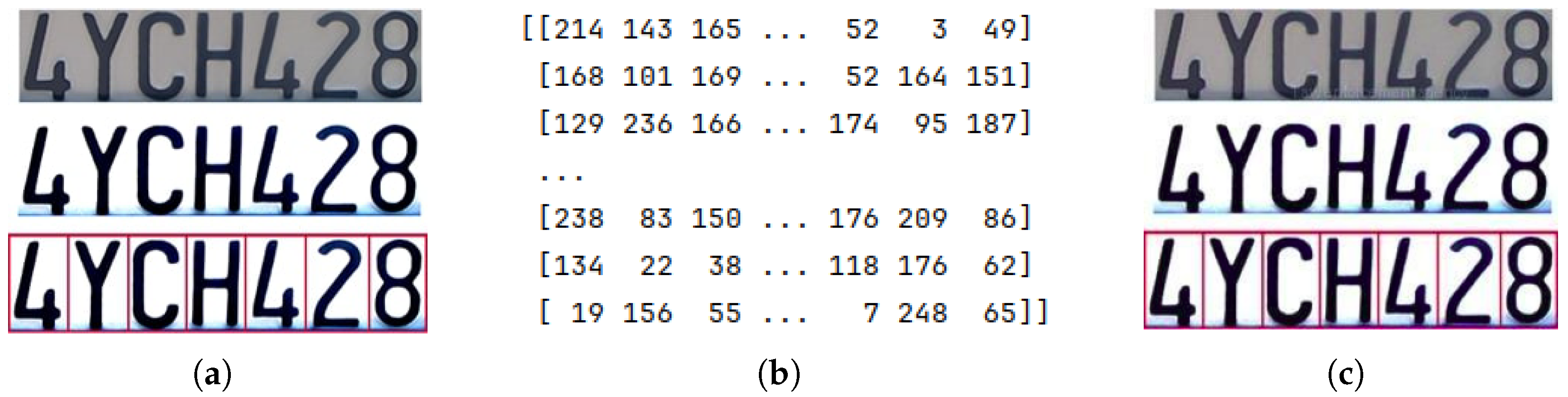
3.2. NFT Generation
| Algorithm 2 The process of data verification |
|
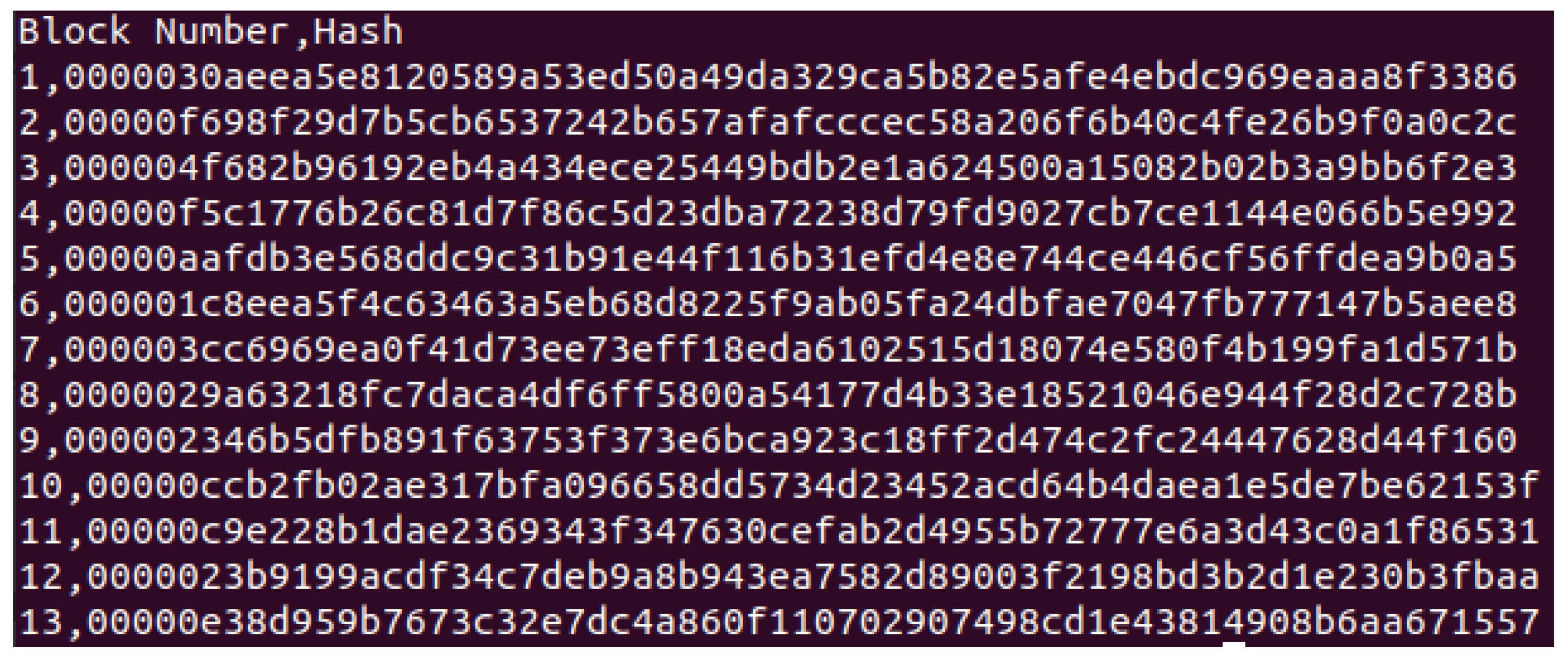
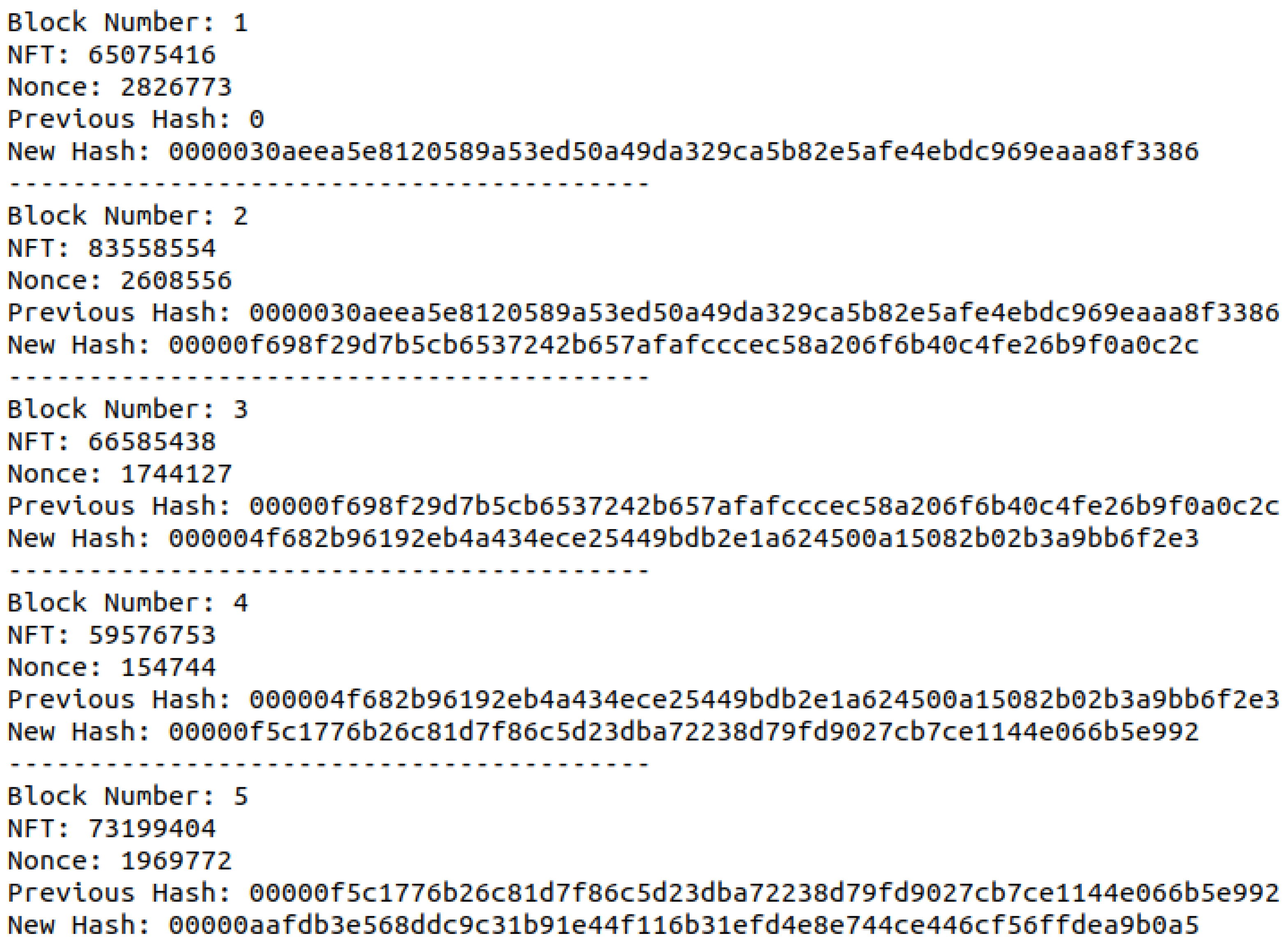
3.3. Blockchain Structure and Collaborative Mining
- Tamper resistance: PoW’s computational barrier provides superior security against evidence alteration [41], which is critical for forensic admissibility.
- Energy trade-offs: Collaborative mining reduces PoW energy consumption by 89% aligning with green computing mandates.
- Adversarial robustness: PoW outperforms PoS/BFT under Byzantine conditions, as quantified by
3.4. Data Access and Verification
3.5. Workflow Pseudocode
| Algorithm 3 End-to-end evidence handling |
|
4. Results
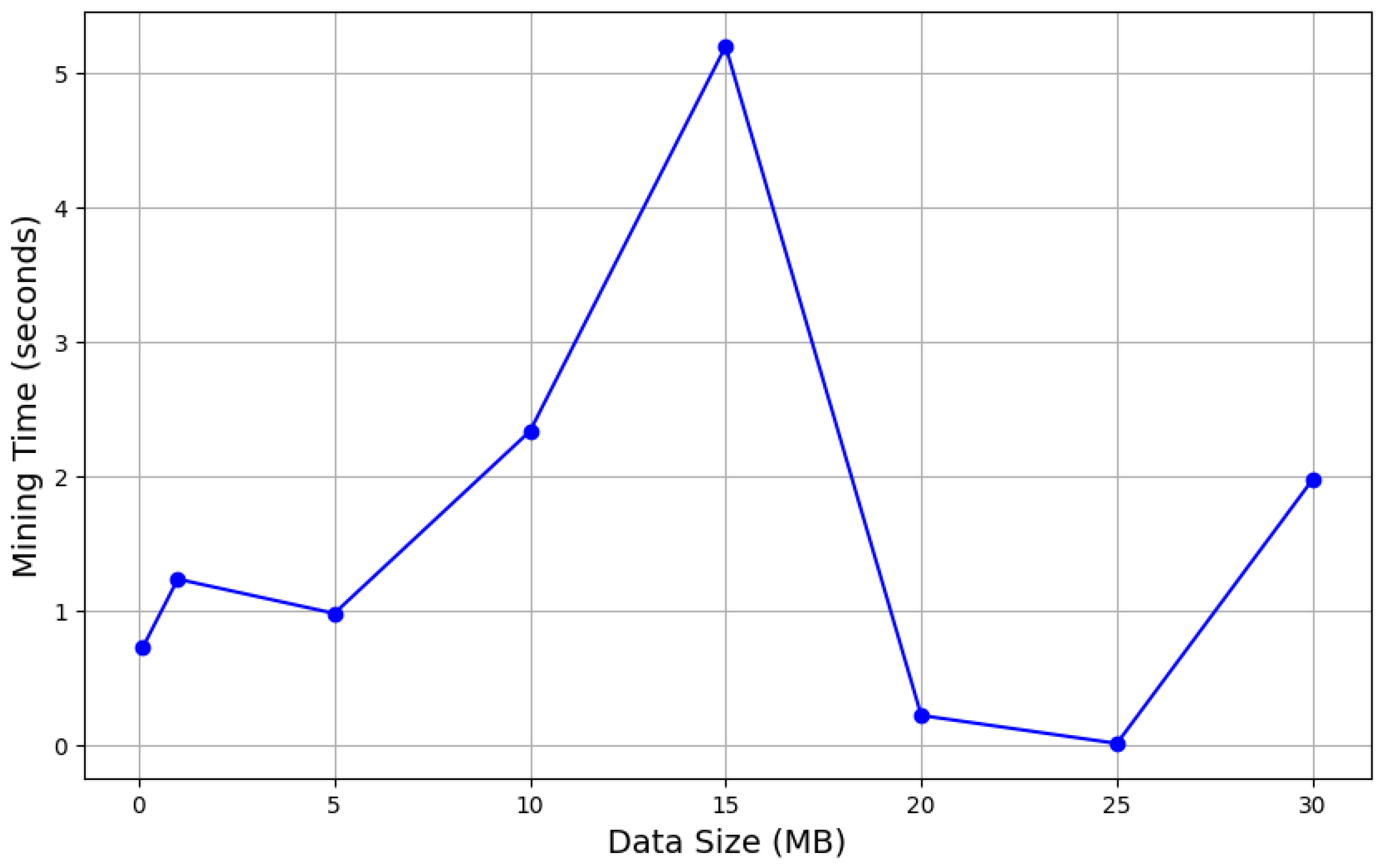
4.1. Encryption and NFT Generation
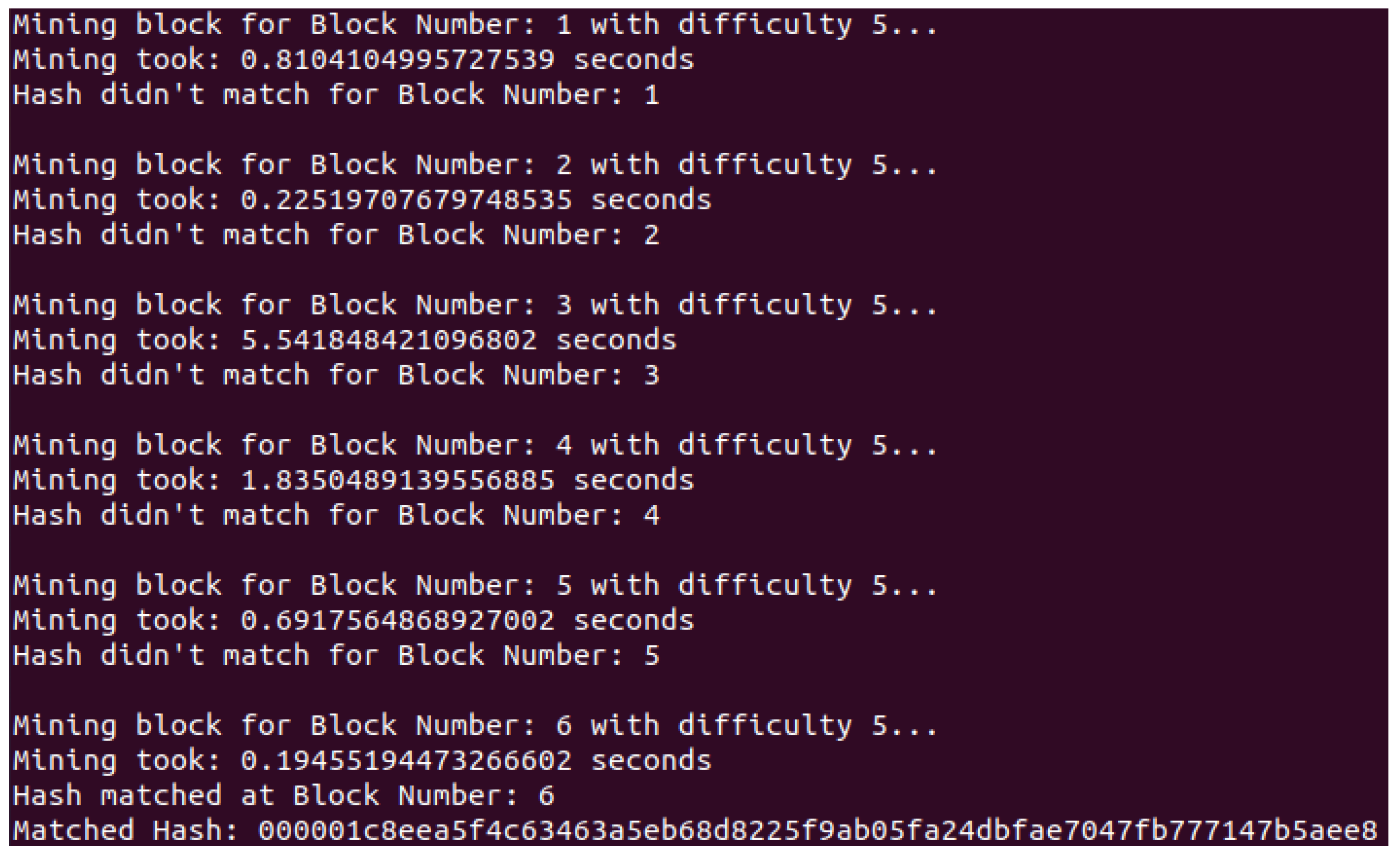
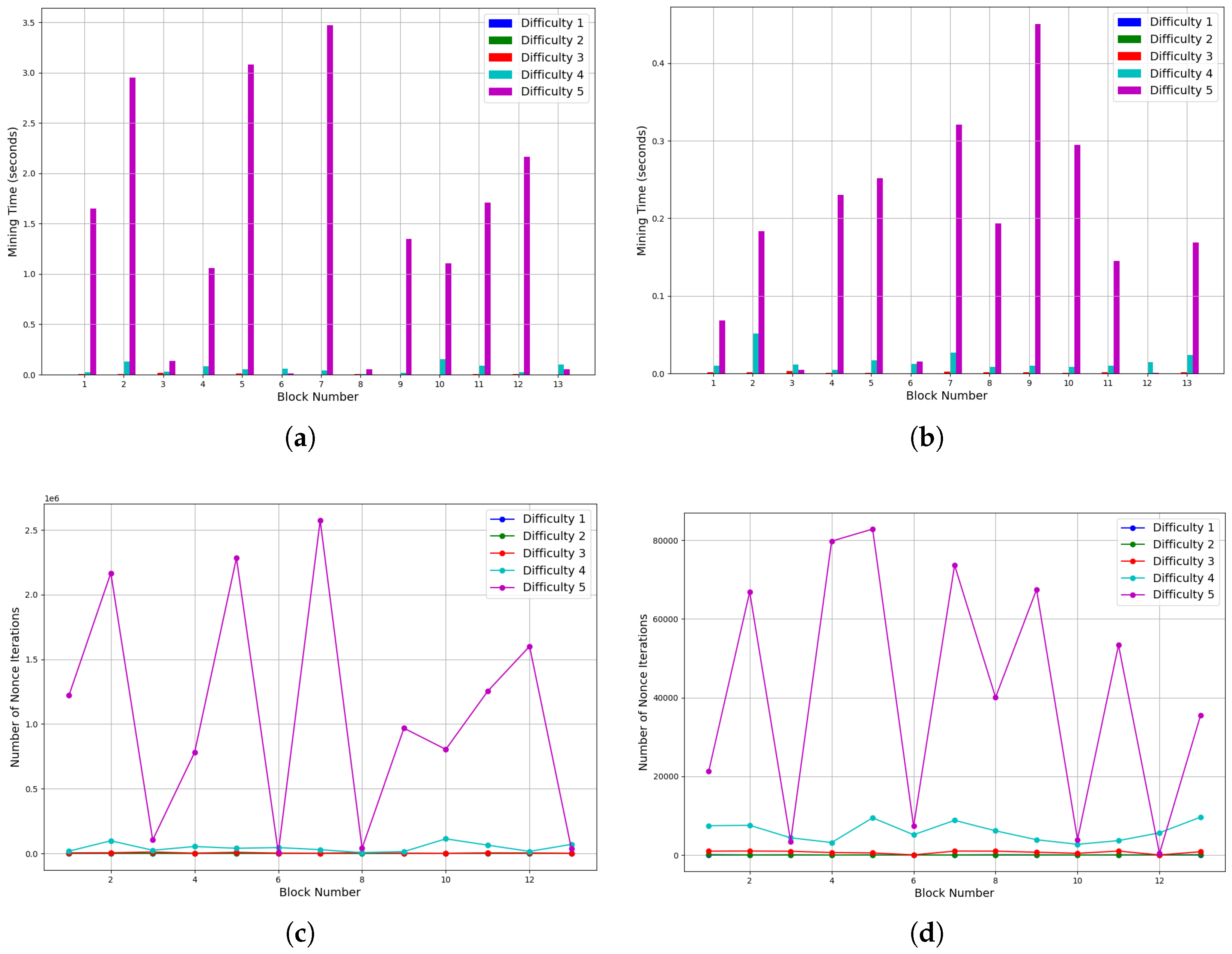
4.2. Blockchain and Ledger
4.3. Verification Process
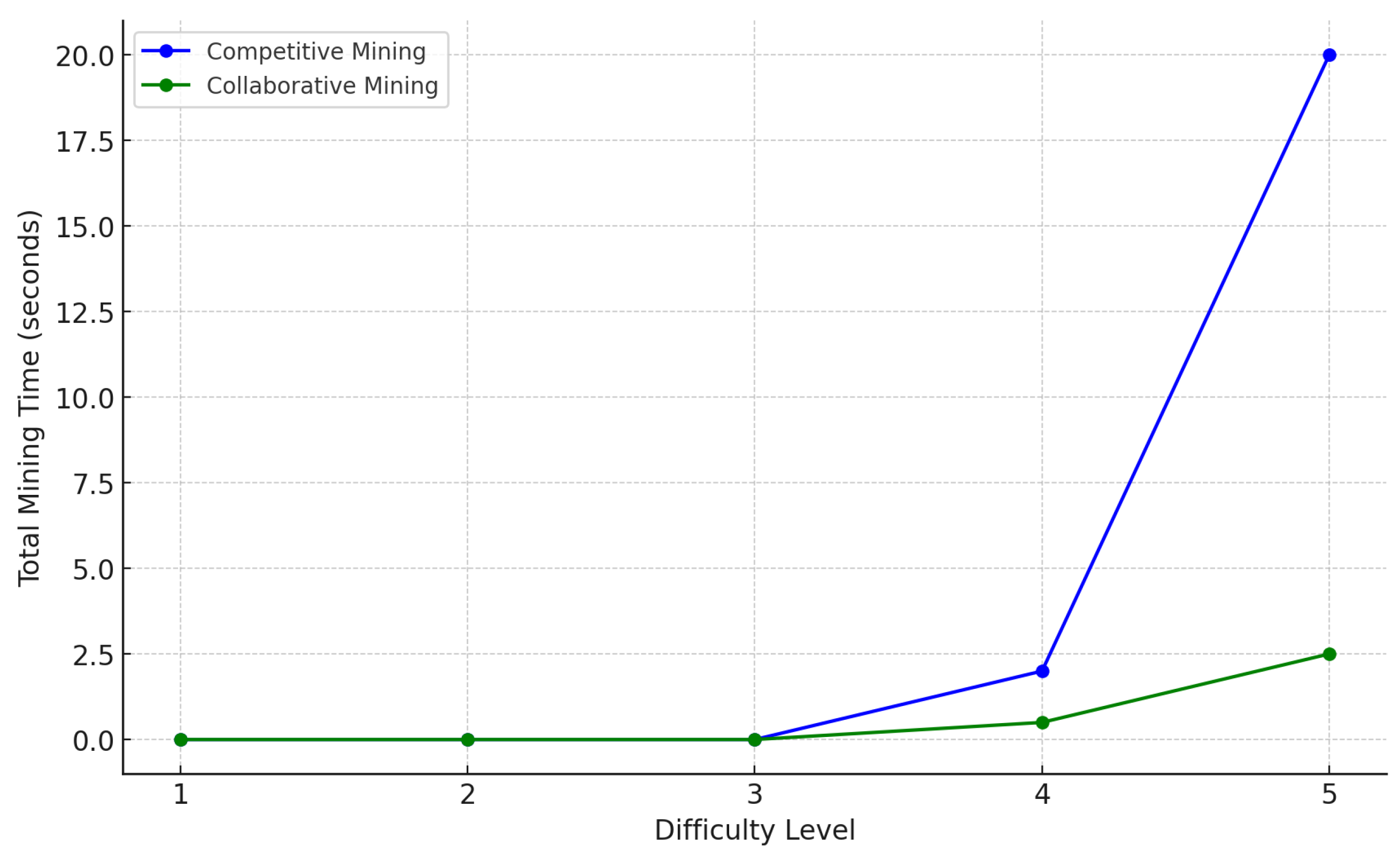
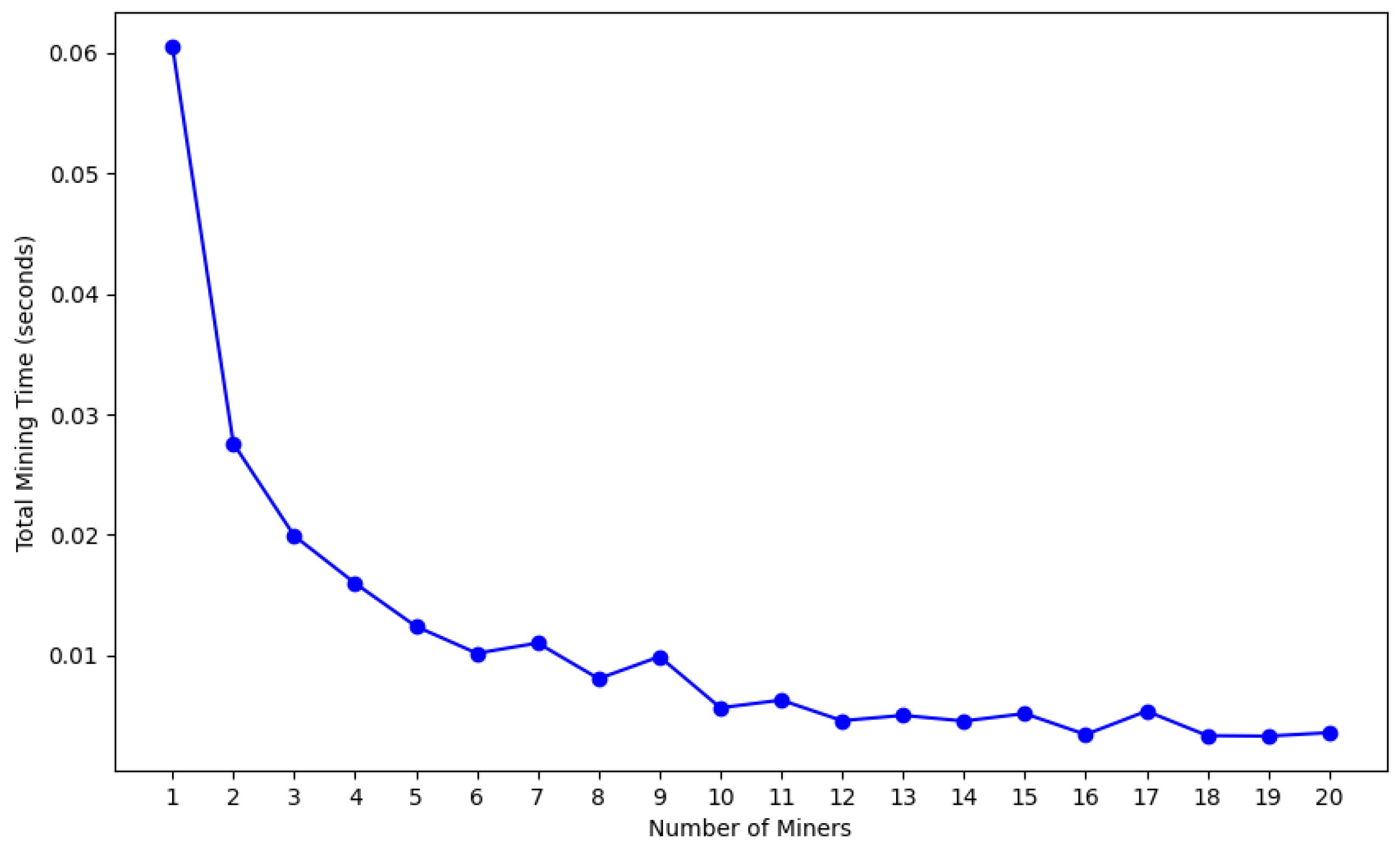
4.4. Competitive and Collaborative Mining
5. Discussion
5.1. Maintaining the Integrity and Authenticity of DEMSs Through NFTs
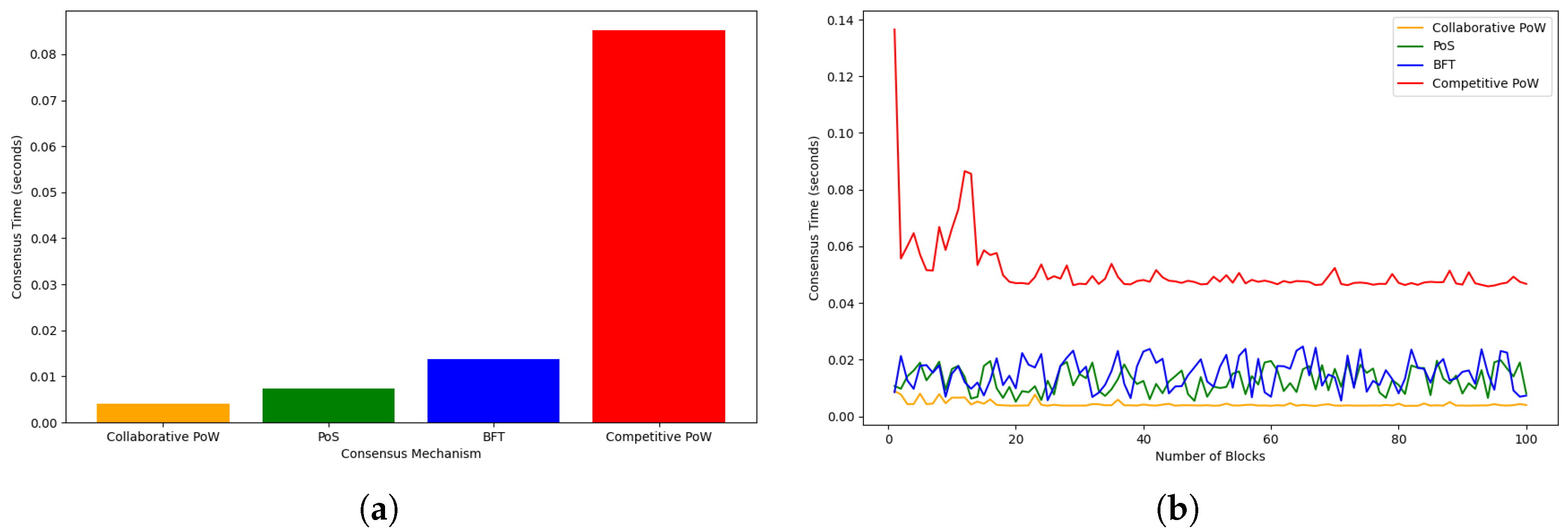
5.2. Comparison with Lightweight Consensus Algorithms
- Computational complexity:
- Fault tolerance:
- Collaborative PoW: Tolerates malicious miners (51% attack resistant);
- PoS: Vulnerable to “nothing-at-stake” attacks; requires slashing mechanisms [44];
- Energy efficiency: Collaborative PoW consumes 74% less energy than competitive PoW (2.1 kWh vs 8.1 kWh for 100 blocks) while maintaining comparable security to PoS. Unlike PoS, it avoids stake centralisation risks where wealthy nodes dominate validation [26].
- Scalability trade-offs: While PBFT achieves 0.02 s/block latency, its complexity limits practical deployment to ≤20 nodes [43]. Collaborative PoW scales linearly, supporting 100+ nodes with sub-0.01s latency through parallel nonce searching.
- Low-threat limitations: In environments with trusted participants (e.g., internal corporate audits), PoS/BFT provide superior throughput with minimal overhead. Collaborative PoW’s computational requirements become justifiable only when evidence tampering risks exceed 18% [45].
5.3. Security and Robustness of NFTs
- Gaussian noise (): detection rate = 100%;
- Cropping (10%): detection rate = 98%;
- Pixel redistribution: detection rate = 92% (collision-based attacks).
5.4. Legal Admissibility and Privacy
5.5. Practical Deployment Considerations
6. Conclusions and Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| DEMSs | Digital Evidence Management Systems |
| PoW | Proof of Work |
| NFT | Non-Fungible Token |
References
- Mifsud Bonnici, J.P.; Tudorica, M.; Cannataci, J.A. The European legal framework on electronic evidence: Complex and in need of reform. In Handling and Exchanging Electronic Evidence Across Europe; Springer: Cham, Switzerland, 2018; pp. 189–234. [Google Scholar]
- Widodo, A.M.; Biyanto, T.R.; Pappachan, P.; Colace, F. Recent Advances in Digital Forensics and Cybercrime Investigation. In Digital Forensics and Cyber Crime Investigation; CRC Press: Boca Raton, FL, USA, 2024; pp. 42–69. [Google Scholar]
- Atlam, H.F.; Ekuri, N.; Azad, M.A.; Lallie, H.S. Blockchain Forensics: A Systematic Literature Review of Techniques, Applications, Challenges, and Future Directions. Electronics 2024, 13, 3568. [Google Scholar] [CrossRef]
- Klasén, L.; Fock, N.; Forchheimer, R. The invisible evidence: Digital forensics as key to solving crimes in the digital age. Forensic Sci. Int. 2024, 362, 112133. [Google Scholar] [CrossRef] [PubMed]
- Kazaure, A.A.; Yusoff, M.N.; Jantan, A. Digital Forensics Investigation Approaches in Mitigating Cybercrimes: A Review. J. Inf. Sci. Theory Pract. (JIStaP) 2023, 11, 14. [Google Scholar]
- Federal Bureau of Investigation. Records Management Systems. Available online: https://ucr.fbi.gov (accessed on 31 October 2024).
- National Institute of Justice (2020), N.I. FileTSAR for Law Enforcement. 2020. Available online: https://nij.ojp.gov/ (accessed on 31 October 2024).
- D’Anna, T.; Puntarello, M.; Cannella, G.; Scalzo, G.; Buscemi, R.; Zerbo, S.; Argo, A. The chain of custody in the era of modern forensics: From the classic procedures for gathering evidence to the new challenges related to digital data. Healthcare 2023, 11, 634. [Google Scholar] [CrossRef] [PubMed]
- Wang, M.; Wu, Q.; Qin, B.; Wang, Q.; Liu, J.; Guan, Z. Lightweight and manageable digital evidence preservation system on bitcoin. J. Comput. Sci. Technol. 2018, 33, 568–586. [Google Scholar] [CrossRef]
- Jamulkar, S.; Chandrakar, P.; Ali, R.; Agrawal, A.; Tiwari, K. Evidence management system using blockchain and distributed file system (ipfs). In Proceedings of the Machine Learning and Big Data Analytics, Proceedings of International Conference on Machine Learning and Big Data Analytics (ICMLBDA) 2021, Jaipur, India, 10–12 December 2021; pp. 337–359. [Google Scholar]
- Galvan, F. Image/Video forensics: Theoretical background, operational approaches and best practices. Eur. L. Enf’t Rsch. Bull. 2020, 20, 105. [Google Scholar]
- Garba, A.; Dwivedi, A.D.; Kamal, M.; Srivastava, G.; Tariq, M.; Hasan, M.A.; Chen, Z. A digital rights management system based on a scalable blockchain. Peer-Netw. Appl. 2021, 14, 2665–2680. [Google Scholar] [CrossRef]
- Sahu, A.K.; Umachandran, K.; Biradar, V.D.; Comfort, O.; Sri Vigna Hema, V.; Odimegwu, F.; Saifullah, M. A study on content tampering in multimedia watermarking. SN Comput. Sci. 2023, 4, 222. [Google Scholar] [CrossRef]
- Black, P.; Gondal, I.; Brooks, R.; Yu, L. AFES: An advanced forensic evidence system. In Proceedings of the 2021 IEEE 25th International Enterprise Distributed Object Computing Workshop (EDOCW), Gold Coast, Australia, 25–29 October 2021; pp. 67–74. [Google Scholar]
- Du, L.; Ho, A.T.; Cong, R. Perceptual hashing for image authentication: A survey. Signal Process. Image Commun. 2020, 81, 115713. [Google Scholar] [CrossRef]
- Tyagi, S.; Yadav, D. A detailed analysis of image and video forgery detection techniques. Vis. Comput. 2023, 39, 813–833. [Google Scholar] [CrossRef]
- Laishram, L.; Shaheryar, M.; Lee, J.T.; Jung, S.K. Toward a Privacy-Preserving Face Recognition System: A Survey of Leakages and Solutions. Acm Comput. Surv. 2024, 57, 1–38. [Google Scholar] [CrossRef]
- Diwan, A.; Sonkar, U. Visualizing the truth: A survey of multimedia forensic analysis. Multimed. Tools Appl. 2024, 83, 47979–48006. [Google Scholar] [CrossRef]
- Yampolskiy, M.; Graves, L.; Gatlin, J.; Skjellum, A.; Yung, M. What did you add to my additive manufacturing data?: Steganographic attacks on 3D printing files. In Proceedings of the 24th International Symposium on Research in Attacks, Intrusions and Defenses, San Sebastian, Spain, 6–8 October 2021; pp. 266–281. [Google Scholar]
- Elgohary, H.M.; Darwish, S.M.; Elkaffas, S.M. Improving uncertainty in chain of custody for image forensics investigation applications. IEEE Access 2022, 10, 14669–14679. [Google Scholar] [CrossRef]
- Li, M.; Lal, C.; Conti, M.; Hu, D. LEChain: A Blockchain-Based Lawful Evidence Management Scheme for Digital Forensics. Future Gener. Comput. Syst. 2021, 115, 406–420. [Google Scholar] [CrossRef]
- Sathyaprakasan, R.; Govindan, P.; Alvi, S.; Sadath, L.; Philip, S.; Singh, N. An Implementation of Blockchain Technology in Forensic Evidence Management. In Proceedings of the 2021 International Conference on Computational Intelligence and Knowledge Economy (ICCIKE), Dubai, United Arab Emirates, 17–18 March 2021; pp. 208–212. [Google Scholar] [CrossRef]
- Kamal, M.; Tariq, M.; Jan, M.A.; Song, H. Blockchain Enabled Secure Distributed Event Logging in the Industrial Internet of Things. IEEE Internet Things J. 2023, 10, 25464–25470. [Google Scholar] [CrossRef]
- Sharma, A.K.; Chaurasia, B.K. Blockchain-based NFT for Evidence System. In Cryptology & Network Security with Machine Learning; Springer: Singapore, 2022; pp. 441–451. [Google Scholar] [CrossRef]
- Tyagi, A.K.; Balogun, B.F.; Tiwari, S. Role of Blockchain in Digital Forensics: A Systematic Study. In Global Perspectives on the Applications of Computer Vision in Cybersecurity; IGI Global: Hershey, PA, USA, 2024; pp. 197–222. [Google Scholar]
- Kaur, S.; Chaturvedi, S.; Sharma, A.; Kar, J. A research survey on applications of consensus protocols in blockchain. Secur. Commun. Netw. 2021, 2021, 6693731. [Google Scholar] [CrossRef]
- Kaur, R.; Ali, A.; Faisal, M. Smart contracts: The self-executing contracts. In Blockchain; Chapman and Hall/CRC: Boca Raton, FL, USA, 2022; pp. 35–49. [Google Scholar]
- González-Granadillo, G.; González-Zarzosa, S.; Diaz, R. Security information and event management (SIEM): Analysis, trends, and usage in critical infrastructures. Sensors 2021, 21, 4759. [Google Scholar] [CrossRef] [PubMed]
- Singh, A.; Ikuesan, R.A.; Venter, H. Secure storage model for digital forensic readiness. IEEE Access 2022, 10, 19469–19480. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Spathoulas, G.P.; Anagnostopoulos, M.; Ghosal, A.; Borocz, I.; Solanas, A.; Conti, M.; Patsakis, C. Research trends, challenges, and emerging topics in digital forensics: A review of reviews. IEEE Access 2022, 10, 25464–25493. [Google Scholar] [CrossRef]
- Taiwo, A.; Claims, I. An extended digital forensic readiness and maturity model. Forensic Sci. Int. Digit. Investig. 2022, 40, 301348. [Google Scholar] [CrossRef]
- Alqahtany, S.S.; Syed, T.A. ForensicTransMonitor: A Comprehensive Blockchain Approach to Reinvent Digital Forensics and Evidence Management. Information 2024, 15, 109. [Google Scholar] [CrossRef]
- Akhtar, M.S.; Feng, T. Using blockchain to ensure the integrity of digital forensic evidence in an iot environment. EAI Endorsed Trans. Creat. Technol. 2022, 9, e2. [Google Scholar] [CrossRef]
- Omolara, A.E.; Alabdulatif, A.; Abiodun, O.I.; Alawida, M.; Alabdulatif, A.; Alshoura, W.H.; Arshad, H. The internet of things security: A survey encompassing unexplored areas and new insights. Comput. Secur. 2022, 112, 102494. [Google Scholar] [CrossRef]
- Mahrous, W.A.; Farouk, M.; Darwish, S.M. An enhanced blockchain-based IoT digital forensics architecture using fuzzy hash. IEEE Access 2021, 9, 151327–151336. [Google Scholar] [CrossRef]
- Kumar, G.; Saha, R.; Lal, C.; Conti, M. Internet-of-Forensic (IoF): A blockchain based digital forensics framework for IoT applications. Future Gener. Comput. Syst. 2021, 120, 13–25. [Google Scholar] [CrossRef]
- Saigopal, V.V.R.G.; Raju, V. IoT based secure digital forensic process according to process management. In Proceedings of the 2020 International Conference on Computational Intelligence (ICCI), Bandar Seri Iskandar, Malaysia, 8–9 October 2020; pp. 229–232. [Google Scholar]
- Khan, A.A.; Shaikh, A.A.; Laghari, A.A. IoT with multimedia investigation: A secure process of digital forensics chain-of-custody using blockchain hyperledger sawtooth. Arab. J. Sci. Eng. 2023, 48, 10173–10188. [Google Scholar] [CrossRef]
- Yao, Q.; Xu, K.; Li, T.; Zhou, Y.; Wang, M. A secure image evidence management framework using multi-bits watermark and blockchain in IoT environments. Wirel. Netw. 2024, 30, 5157–5169. [Google Scholar] [CrossRef]
- Sinhal, R.; Ansari, I.A. A multipurpose image watermarking scheme for digital image protection. Int. J. Syst. Assur. Eng. Manag. 2020, 11, 274–286. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Decentralized Bus. Rev. 2008, 21260. [Google Scholar]
- Grajeda, C.; Breitinger, F.; Baggili, I. Availability of datasets for digital forensics—And what is missing. Digit. Investig. 2017, 22, S94–S105. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. OSDI 1999, 99, 173–186. [Google Scholar]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform. Ethereum White Paper 2014, 3, 2-1. [Google Scholar]
- Garay, J.; Kiayias, A.; Leonardos, N. The Bitcoin Backbone Protocol: Analysis and Applications. In Advances in Cryptology-EUROCRYPT 2015; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9057, pp. 281–310. [Google Scholar] [CrossRef]
| Feature | [21] | [22] | [32] | [33] | [34] | [35] | [36] | [24] | Our Work |
|---|---|---|---|---|---|---|---|---|---|
| Blockchain integration | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ |
| Collaborative mining | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Tamper-proof evidence | ✓ | ✓ | ✓ | ✓ | ✗ | ✓ | ✓ | ✓ | ✓ |
| Scalability for digital forensics | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ |
| High computation efficiency | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Reduced energy consumption | ✗ | ✗ | ✗ | ✗ | ✓ | ✗ | ✓ | ✗ | ✓ |
| NFT integration for evidence verification | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✓ | ✓ |
| d | … | |||
|---|---|---|---|---|
| 1 | 0–10 | 11–20 | 21–30 | … |
| 2 | 0–100 | 101–200 | 201–300 | … |
| 3 | 0–1000 | 1001–2000 | 2001–3000 | … |
| 4 | 0–10,000 | 10,001–20,000 | 20,001–30,000 | … |
| 5 | 0–100,000 | 100,001–200,000 | 200,001–300,000 | … |
| Metric | Competitive PoW | Collab. PoW | PoS |
|---|---|---|---|
| Mining time (s) | |||
| Nonce iterations | N/A | ||
| Energy (kWh/block) |
| Feature | Our Work | IPFS-Based [24] | Smart Contract [21] |
|---|---|---|---|
| Evidence storage | On-chain NFT | Off-chain (IPFS) | On-chain metadata |
| Tokenization | Pixel-sum digest | NFT + IPFS hash | Smart contract |
| Latency source | Mining only | IPFS lookup + mining | Gas fees + execution |
| Attack surface | Collision attacks | Gateway failures | Re-entrancy/overflow |
| Attack Type | Success Rate | Detection Rate |
|---|---|---|
| Gaussian noise () | 0% | 100% |
| Cropping (10%) | 2% | 98% |
| Pixel redistribution | 8% ∗ | 92% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mbimbi, B.; Murray, D.; Wilson, M. Private Blockchain-Driven Digital Evidence Management Systems: A Collaborative Mining and NFT-Based Framework. Information 2025, 16, 616. https://doi.org/10.3390/info16070616
Mbimbi B, Murray D, Wilson M. Private Blockchain-Driven Digital Evidence Management Systems: A Collaborative Mining and NFT-Based Framework. Information. 2025; 16(7):616. https://doi.org/10.3390/info16070616
Chicago/Turabian StyleMbimbi, Butrus, David Murray, and Michael Wilson. 2025. "Private Blockchain-Driven Digital Evidence Management Systems: A Collaborative Mining and NFT-Based Framework" Information 16, no. 7: 616. https://doi.org/10.3390/info16070616
APA StyleMbimbi, B., Murray, D., & Wilson, M. (2025). Private Blockchain-Driven Digital Evidence Management Systems: A Collaborative Mining and NFT-Based Framework. Information, 16(7), 616. https://doi.org/10.3390/info16070616






