Post-Quantum Key Exchange and Subscriber Identity Encryption in 5G Using ML-KEM (Kyber) †
Abstract
1. Introduction
2. Motivation and Background
2.1. Motivation: PQC Transition
2.2. Background on 5G AKA and Cryptographic Primitives
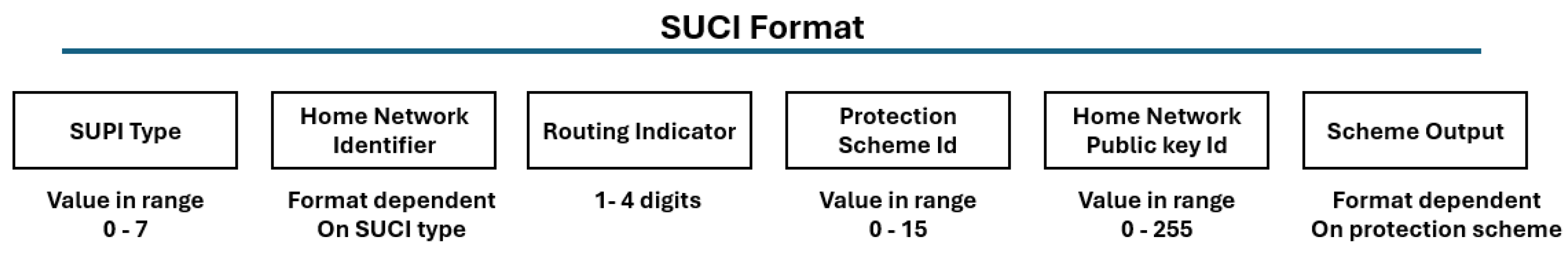
2.2.1. 5G-AKA and SUCI
2.2.2. Pre-Quantum (X25519 and secp256r1)
2.2.3. Post-Quantum, CRYSTALS-Kyber
2.2.4. Key Encapsulation Mechanism (KEM)
- KEM.KeyGen: A probabilistic key generation algorithm, KEM.KeyGen, that generates a public–private key pair.
- KEM.Encapsulation: A probabilistic encapsulation algorithm, KEM.Encapsulate, that takes the public key of the receiver as input. Then, it selects a shared key randomly, encrypts the shared key using the receiver public key, and outputs the ciphertext, which is also known as an encapsulated shared key.
- KEM.Decapsulation: A deterministic decapsulation algorithm that takes as input a ciphertext (encapsulated shared key) and private key of the receiver to generate the shared key or report a failure.
3. Related Work
3.1. SUCI Protection in 5G
3.2. Post-Quantum for 5G KEM
4. Security and Cryptanalysis on PQC KEM: How Kyber Was Selected
4.1. PQC Requirements
4.2. Side-Channel Attack on NIST’s Third Round
5. Our PQC Incorporation and Implementation
5.1. SUCI in Existing 5G
- Public–Private Key Generation at UE: During the registration process, the UE generates the EC public–private key pair. The UE’s public key is used by the CN to de-conceal the SUPI from the received SUCI while the UE’s private key serves as input for the key agreement function in the subsequent step.
- Key Agreement: The input to this function includes the CN’s public key stored in the USIM and the UE’s private key obtained from step 1, resulting in the generation of a shared key. In contrast to the use of ECDH in other contexts that exchange the public keys via digital networking, our key agreement makes use of the public keys shared during the UE registration, as described in Section 2.2.
- Encryption Key: The UE then uses a key derivation function on the shared key to generate an encryption key for the symmetric cipher, an initial counter block (ICB), and a for the message authentication code (MAC).
- Symmetric Encryption: The UE uses the encryption key and the ICB to encrypt the plaintext (SUPI or IMSI) depending on the SUPI type field in the SUCI format. Also, the UE generates the MAC field using . The output ciphertext value becomes the part of the scheme output of the SUCI.The UE then transmits the finalized output of the UE-side encryption process to the CN for registration and identification. This output consists of the concatenation of the UE’s public key, ciphertext, and MAC.
- Decryption: When the CN receives the registration request along with the SUCI, it uses the UE’s public key (from step 1) and CN’s private key to generate the shared key at the CN side. The shared key is further used to generate a decryption key that is the same as to decrypt the SUCI, using a key derivation function.
5.2. Post-Quantum Cryptography for Subscriber Concealed Identifier (SUCI)
- Public–Private Key Generation (UE): The UE generates the public–private key pair using the KEM.KeyGen function.
- Encapsulation (UE): To encrypt SUPI/IMSI, the UE uses the function KEM.Encapsulate to generate initial randomness, derive the shared key from this randomness, and compute a ciphertext using the CN’s public key. The generated ciphertext is the encapsulated shared key.
- Symmetric Encryption: After generating the shared key, the UE encrypts the plaintext (SUPI or IMSI) with a shared key that is computed using function KEM.Encapsulate.The UE then sends the encapsulated shared key and encrypted data to the CN.
- Decapsulation: When the CN receives the registration request, the CN uses its private key and encapsulated shared key to generate a shared key by using the decapsulation function KEM.Decapsulate, and further uses that generated shared key for decryption to verify the subscriber.
5.3. Subscription Concealment Protection Schemes (Modified for Post-Quantum Scheme—Kyber Profile C)
6. Experimentation and Performance Analysis
6.1. Hardware and Software Setup
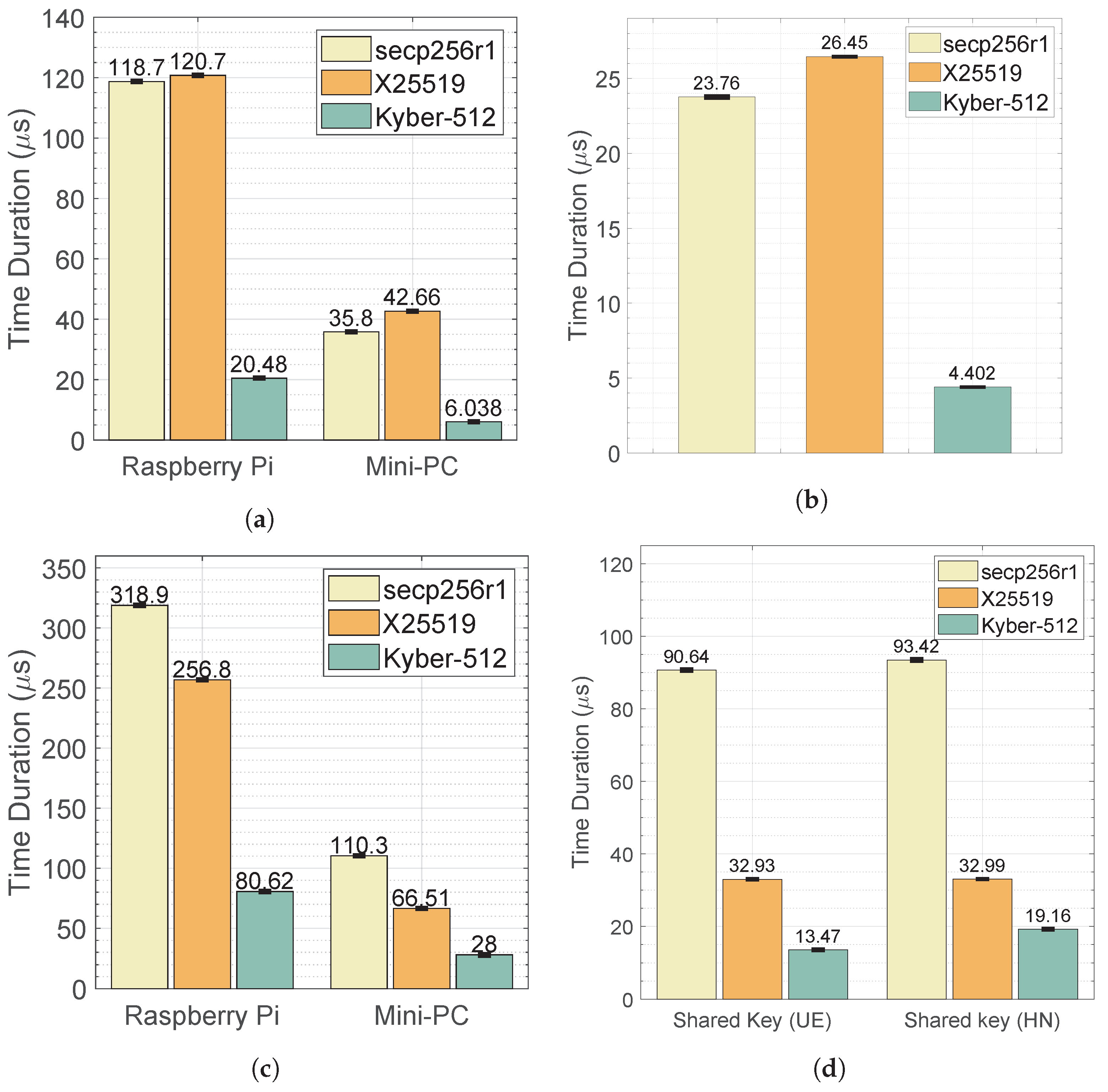
6.2. Computational Time Performance Analysis
- Summary: The above results compare the computational time measurements of public-key generation and shared-key generation for encapsulation/decapsulation operations in the SUCI calculation process as described in Section 5. Regarding the post-quantum KEM, Kyber-512 demonstrates shorter processing times for key generation compared to pre-quantum ciphers X25519 and secp256r1, both at UE and CN sides, across different platforms, including the computer, Mini-PCs, and Raspberry Pi, which can improve the overall performance and responsiveness of mobile devices, crucial for tasks requiring secure communication and data transmission.
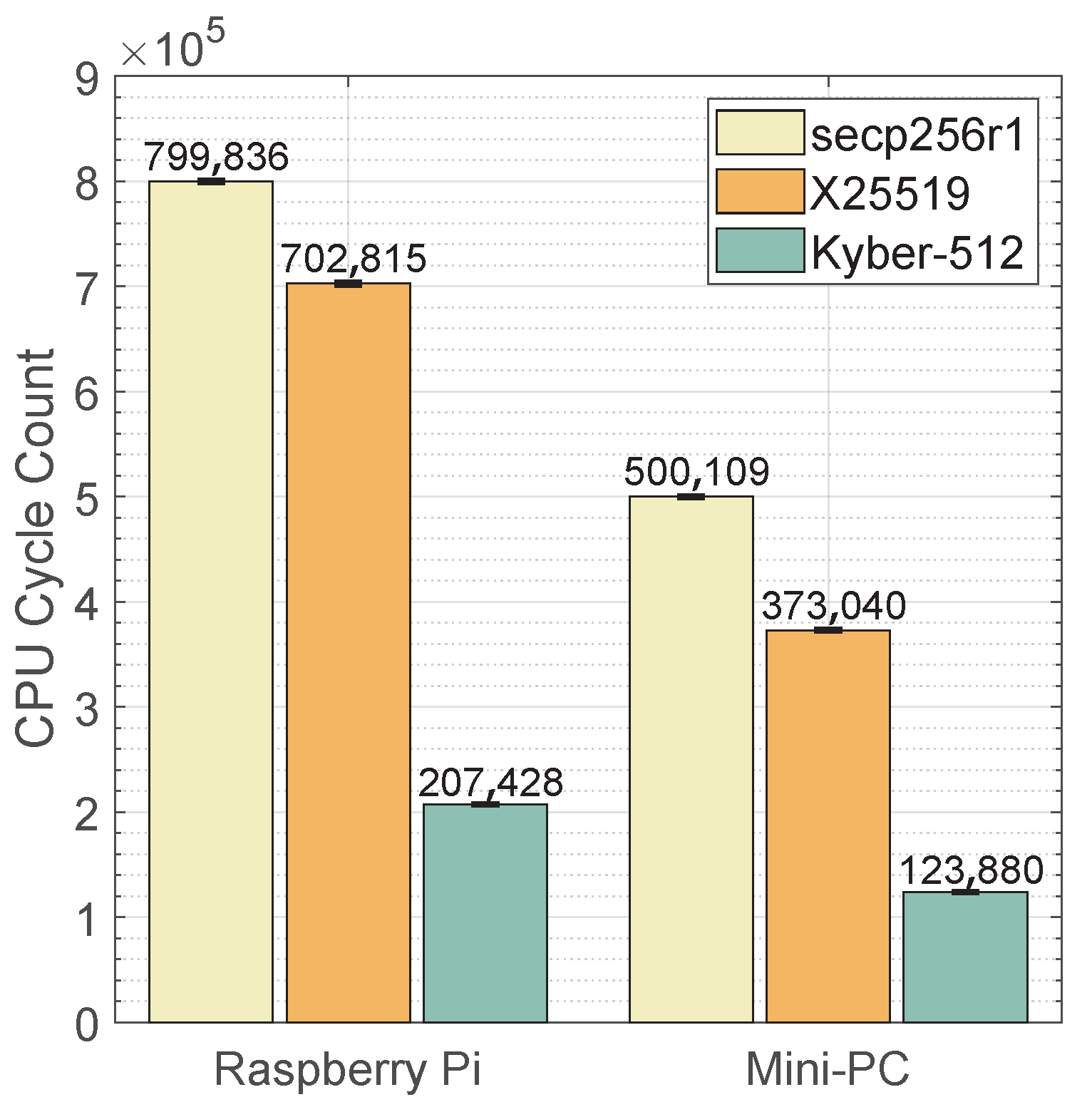
6.3. CPU Processor Analysis
- Summary: The analysis provides significant differences in cycle counts between pre-quantum (X25519 and secp256r1) and post-quantum (Kyber-512) ciphers on both the Raspberry Pi and Mini-PC. Kyber-512 stands out favorably in the CPU cycle comparison for mobile devices due to its relatively lower cycle count compared to other cryptographic ciphers like secp256r1 and X25519. This lower cycle count indicates that Kyber-512 requires fewer computational resources, making it more efficient and suitable for resource-constrained devices like mobile devices. Lower cycle counts enable Kyber-512 to execute cryptographic operations more efficiently, resulting in reduced processing time and low energy, which helps to conserve battery life, as discussed in Section 6.4.
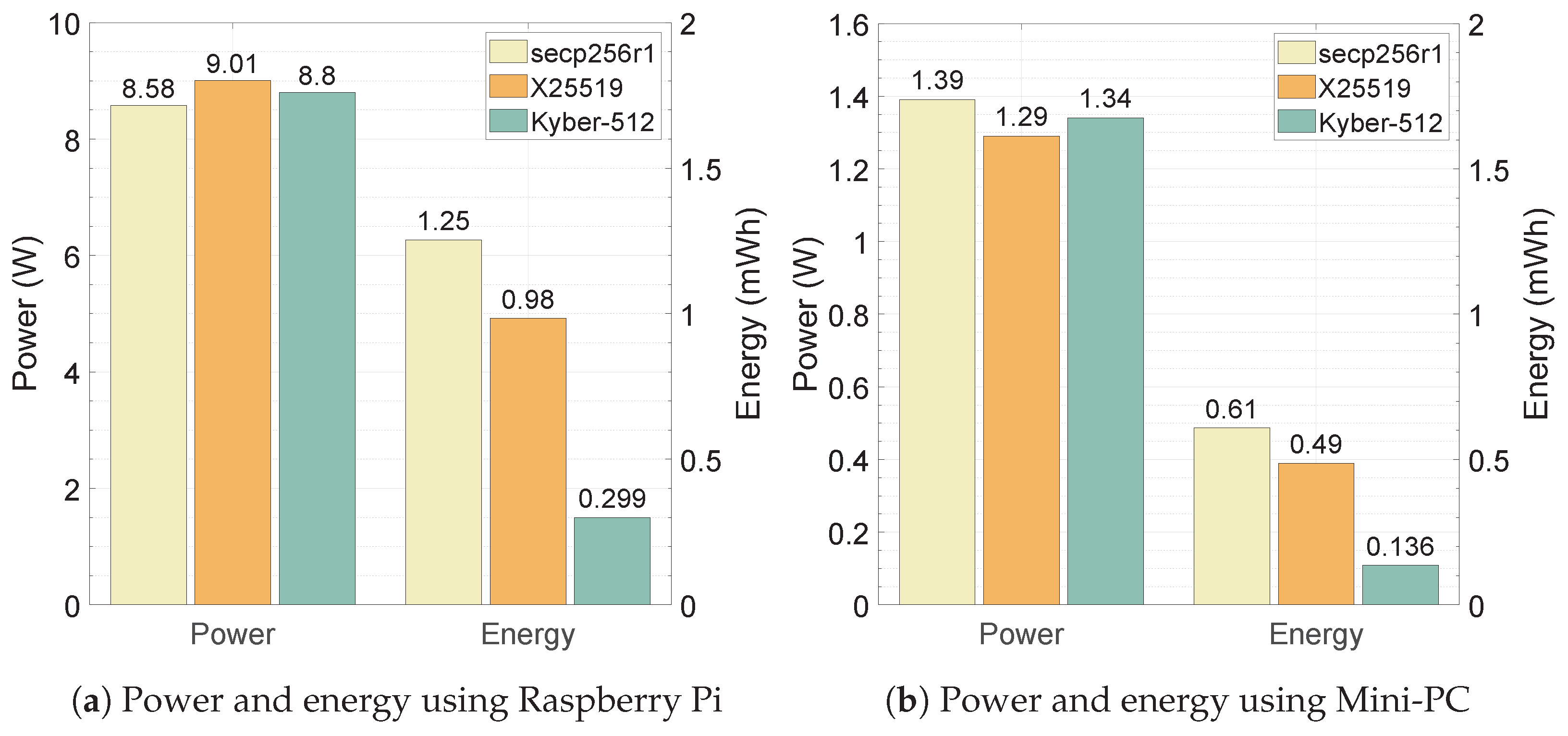
6.4. Computational Battery Performance Analysis
- Summary: We aim to compare the power and energy performances of all three ciphers on resource-constrained devices. The power consumption among all three ciphers is closely comparable on both the Mini-PC and Raspberry Pi, while post-quantum KEM Kyber-512 demonstrates superior energy efficiency, consuming notably less energy compared to pre-quantum ciphers, secp256r1 and X25519, on both Mini-PC and Raspberry Pi platforms, helping to conserve battery life, thereby allowing users to use their devices for longer periods without needing to recharge.
6.5. Byte Overhead Analysis
- Summary: Table 4 describes protection scheme output sizes among cryptographic ciphers, with Kyber-512 having a larger output due to its ciphertext size. While this may increase communication overhead, it remains feasible for the storage of public keys within a standard USIM card (with 256 KB memory), facilitating its practical usage in mobile devices.
7. Conclusions and Future Directions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Strobel, D. IMSI Catcher; Chair for Communication Security; Ruhr-Universität Bochum: Bochum, Germany, 2007. [Google Scholar]
- Van Den Broek, F.; Verdult, R.; De Ruiter, J. Defeating IMSI catchers. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 340–351. [Google Scholar]
- Koutsos, A. The 5G-AKA authentication protocol privacy. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, 17–19 June 2019; pp. 464–479. [Google Scholar]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- NIST. Module-Lattice-Based Key-Encapsulation Mechanism Standard. 2024. Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.203.pdf (accessed on 15 June 2025).
- 3GPP. TS 33.501; Security Architecture and Procedures for 5G System. V18.6.0. 2024. Available online: https://www.etsi.org/deliver/etsi_ts/133500_133599/133501/18.06.00_60/ts_133501v180600p.pdf (accessed on 10 January 2023).
- Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-Kyber: A CCA-secure module-lattice-based KEM. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 353–367. [Google Scholar]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Nature. Work Easier Work Faster. 2023. Available online: https://www.nature.com/articles/d41586-023-03854-1 (accessed on 10 January 2023).
- Martínez, V.G.; Encinas, L.H. A comparison of the standardized versions of ECIES. In Proceedings of the 2010 Sixth International Conference on Information Assurance and Security, Atlanta, GA, USA, 23–25 August 2010; pp. 1–4. [Google Scholar]
- Internet Research Task Force (IRTF). Elliptic Curves for Security. 2016. Available online: https://datatracker.ietf.org/doc/html/rfc7748 (accessed on 29 January 2025).
- Adalier, M.; Teknik, A. Efficient and secure elliptic curve cryptography implementation of curve p-256. In Proceedings of the Workshop on Elliptic Curve Cryptography Standards, NIST, Gaithersburg, MD, USA, 11–12 June 2015; Volume 66, pp. 2014–2017. [Google Scholar]
- Mjølsnes, S.F.; Olimid, R.F. Easy 4G/LTE IMSI catchers for non-programmers. In Proceedings of the Computer Network Security: 7th International Conference on Mathematical Methods, Models, and Architectures for Computer Network Security, MMM-ACNS 2017, Warsaw, Poland, 28–30 August 2017; Proceedings 7. Springer: Warsaw, Poland, 2017; pp. 235–246. [Google Scholar]
- Park, S.; Shaik, A.; Borgaonkar, R.; Seifert, J.P. Anatomy of Commercial IMSI Catchers and Detectors. In Proceedings of the 18th ACM Workshop on Privacy in the Electronic Society (WPES’19), London, UK, 11 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 74–86. [Google Scholar] [CrossRef]
- Dabrowski, A.; Pianta, N.; Klepp, T.; Mulazzani, M.; Weippl, E. IMSI-catch me if you can: IMSI-catcher-catchers. In Proceedings of the 30th Annual Computer Security Applications Conference, Orleans, LA, USA, 8–12 December 2014; pp. 246–255. [Google Scholar]
- Dabrowski, A.; Petzl, G.; Weippl, E.R. The messenger shoots back: Network operator based IMSI catcher detection. In Proceedings of the Research in Attacks, Intrusions, and Defenses: 19th International Symposium, RAID 2016, Paris, France, 19–21 September 2016; Proceedings 19. Springer: Paris, France, 2016; pp. 279–302. [Google Scholar]
- Clancy, T.C.; McGwier, R.W.; Chen, L. Post-quantum cryptography and 5g security: Tutorial. In Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks, Miami, FL, USA, 15–17 May 2019; p. 285. [Google Scholar]
- Chawla, D.; Mehra, P.S. A roadmap from classical cryptography to post-quantum resistant cryptography for 5G-enabled IoT: Challenges, opportunities and solutions. Internet Things 2023, 24, 100950. [Google Scholar] [CrossRef]
- Mehic, M.; Michalek, L.; Dervisevic, E.; Burdiak, P.; Plakalovic, M.; Rozhon, J.; Mahovac, N.; Richter, F.; Kaljic, E.; Lauterbach, F.; et al. Quantum cryptography in 5g networks: A comprehensive overview. IEEE Commun. Surv. Tutor. 2023, 26, 302–346. [Google Scholar] [CrossRef]
- Khan, Q.; Purification, S.; Cheruiyot, R.; Kim, J.; Kim, J.; Chang, S.Y. Toward Post-Quantum Digital Certificate for eSIM. In Proceedings of the 2024 Silicon Valley Cybersecurity Conference (SVCC), Seoul, Republic of Korea, 17–19 June 2024; pp. 1–3. [Google Scholar] [CrossRef]
- Khan, Q.; Purification, S.; Cheruiyot, R.; Kim, J.; Kim, I.; Chang, S.Y. Post-Quantum Digital Signature and Authentication for eSIM in 5G Mobile Networking. In Proceedings of the 2025 Silicon Valley Cybersecurity Conference (SVCC), San Francisco, CA, USA, 23–25 June 2025; pp. 1–7. [Google Scholar]
- Ulitzsch, V.Q.; Park, S.; Marzougui, S.; Seifert, J.P. A post-quantum secure subscription concealed identifier for 6g. In Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks, San Antonio, TX, USA, 16–19 May 2022; pp. 157–168. [Google Scholar]
- Damir, M.T.; Meskanen, T.; Ramezanian, S.; Niemi, V. A beyond-5g authentication and key agreement protocol. In Proceedings of the International Conference on Network and System Security, Denarau Island, Fiji, 9–12 December 2022; pp. 249–264. [Google Scholar]
- NIST. Post-Quantum Cryptography: Proposed Requirements. 2016. Available online: https://csrc.nist.gov/news/2016/post-quantum-cryptography-proposed-requirements (accessed on 15 June 2025).
- NIST. Post Quantum Cryptography. 2022. Available online: https://csrc.nist.gov/Projects/post-quantum-cryptography/selected-algorithms-2022 (accessed on 10 June 2024).
- NIST. CRYSTALS-Kyber—Submission to the NIST Post-Quantum Project. 2017. Available online: https://pq-crystals.org/kyber/data/kyber-specification.pdf (accessed on 15 June 2025).
- NIST. CRYSTALS-Kyber (Version 2.0)—Submission to Round 2 of the NIST Post-Quantum Project. 2019. Available online: https://pq-crystals.org/kyber/data/kyber-specification-round2.pdf (accessed on 15 June 2025).
- NIST. CRYSTALS-Kyber (Version 3.02)—Submission to Round 3 of the NIST Post-Quantum Project. 2021. Available online: https://pq-crystals.org/kyber/data/kyber-specification-round3-20210804.pdf (accessed on 15 June 2025).
- D’Anvers, J.P.; Karmakar, A.; Sinha Roy, S.; Vercauteren, F. Saber: Module-LWR based key exchange, CPA-secure encryption and CCA-secure KEM. In Proceedings of the Progress in Cryptology–AFRICACRYPT 2018: 10th International Conference on Cryptology in Africa, Marrakesh, Morocco, 7–9 May 2018; Proceedings 10. pp. 282–305. [Google Scholar]
- Lee, M.K.; Song, J.E.; Choi, D.; Han, D.G. Countermeasures against power analysis attacks for the NTRU public key cryptosystem. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2010, 93, 153–163. [Google Scholar] [CrossRef]
- Zheng, X.; Wang, A.; Wei, W. First-order collision attack on protected NTRU cryptosystem. Microprocess. Microsyst. 2013, 37, 601–609. [Google Scholar] [CrossRef]
- Huang, W.L.; Chen, J.P.; Yang, B.Y. Power Analysis on NTRU Prime. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2020, 123–151. [Google Scholar] [CrossRef]
- Primas, R.; Pessl, P.; Mangard, S. Single-trace side-channel attacks on masked lattice-based encryption. In Proceedings of the International Conference on Cryptographic Hardware and Embedded Systems, Taipei, Taiwan, 25–28 September 2017; pp. 513–533. [Google Scholar]
- Aysu, A.; Tobah, Y.; Tiwari, M.; Gerstlauer, A.; Orshansky, M. Horizontal side-channel vulnerabilities of post-quantum key exchange protocols. In Proceedings of the 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 30 April–4 May 2018; pp. 81–88. [Google Scholar]
- Bos, J.W.; Friedberger, S.; Martinoli, M.; Oswald, E.; Stam, M. Assessing the feasibility of single trace power analysis of frodo. In Proceedings of the International Conference on Selected Areas in Cryptography, Calgary, AB, Canada, 15–17 August 2018; pp. 216–234. [Google Scholar]
- D’Anvers, J.P.; Tiepelt, M.; Vercauteren, F.; Verbauwhede, I. Timing attacks on error correcting codes in post-quantum schemes. In Proceedings of the ACM Workshop on Theory of Implementation Security Workshop, London, UK, 11 November 2019; pp. 2–9. [Google Scholar]
- Ravi, P.; Roy, S.S.; Chattopadhyay, A.; Bhasin, S. Generic Side-channel attacks on CCA-secure lattice-based PKE and KEM schemes. Cryptology 2019, 2020, 307–335. [Google Scholar]
- Sim, B.Y.; Park, A.; Han, D.G. Chosen-ciphertext Clustering Attack on CRYSTALS-KYBER using the Side-channel Leakage of Barrett Reduction. IEEE Internet Things J. 2022, 9, 21382–21397. [Google Scholar] [CrossRef]
- D’Anvers, J.P.; Guo, Q.; Johansson, T.; Nilsson, A.; Vercauteren, F.; Verbauwhede, I. Decryption failure attacks on IND-CCA secure lattice-based schemes. In Proceedings of the IACR International Workshop on Public Key Cryptography, Beijing, China, 14–17 April 2019; pp. 565–598. [Google Scholar]
- Ravi, P.; Roy, D.B.; Bhasin, S.; Chattopadhyay, A.; Mukhopadhyay, D. Number “not used” once-practical fault attack on pqm4 implementations of NIST candidates. In Proceedings of the International Workshop on Constructive Side-Channel Analysis and Secure Design, Darmstadt, Germany, 3–5 April 2019; pp. 232–250. [Google Scholar]
- Xu, Z.; Pemberton, O.; Roy, S.S.; Oswald, D.; Yao, W.; Zheng, Z. Magnifying side-channel leakage of lattice-based cryptosystems with chosen ciphertexts: The case study of kyber. IEEE Trans. Comput. 2021, 71, 2163–2176. [Google Scholar] [CrossRef]
- Hermelink, J.; Pessl, P.; Pöppelmann, T. Fault-enabled chosen-ciphertext attacks on Kyber. In Proceedings of the International Conference on Cryptology in India, Jaipur, India, 12–15 December 2021; pp. 311–334. [Google Scholar]
- Ravi, P.; Jhanwar, M.P.; Howe, J.; Chattopadhyay, A.; Bhasin, S. Side-channel assisted existential forgery attack on Dilithium-a NIST PQC candidate. IACR Cryptol. ePrint Arch. 2018, 821. [Google Scholar]
- Islam, S.; Mus, K.; Singh, R.; Schaumont, P.; Sunar, B. Signature Correction Attack on Dilithium Signature Scheme. arXiv 2022, arXiv:2203.00637. [Google Scholar] [CrossRef]
- Khan, Q.; Purification, S.; Chang, S.-Y. Experimental Scripts and Data for Post-Quantum Key Exchange and Subscriber Identity Encryption in 5G Using ML-KEM (Kyber). 2025. Available online: https://github.com/NSSL-UCCS/PQKEM-5G (accessed on 13 July 2025).
- Python Cryptographic Authority. Cryptography Version 42-0-5. 2024. Available online: https://github.com/pyca/cryptography/releases/tag/42.0.5 (accessed on 13 July 2025).
- Open-Quantum-Safe. Liboqs Version 0.9.0. 2024. Available online: https://github.com/open-quantum-safe/liboqs-python/releases/tag/0.9.0 (accessed on 13 July 2025).
- Shenzhen Zhurui Technology Co., Ltd. ZHURUI PR10-E Power Recorder User Manual. 2016. Available online: https://manuals.plus/m/8a5a181ee72ab9efe0c8b75a7752d1713f7db211c598f8b596f9069caa4f6ba0_optim.pdf (accessed on 13 July 2025).
- Techredar. SIM Card Storage Memeory. 2020. Available online: https://www.techradar.com/sim-only/what-is-stored-on-a-sim-card (accessed on 10 January 2024).
- Khan, Q.; Purification, S.; Chang, S.Y. Post-Quantum Key Exchange and ID Encryption Analyses for 5G Mobile Networking. In Proceedings of the NOMS 2025-2025 IEEE Network Operations and Management Symposium, Honolulu, HI, USA, 12–16 May 2025; pp. 1–9. [Google Scholar]

| Security Level (bits) | Symmetric | RSA | EC | Post-Quantum (NIST Round 4) |
|---|---|---|---|---|
| 128 | AES-128 | 3072 bits | 256 bits | Kyber-512 |
| 192 | AES-192 | 7680 bits | 384 bits | Kyber-768 |
| 256 | AES-256 | 15,360 bits | 512 bits | Kyber-1024 |
| AKA | Authentication and Key Agreement |
| CN | Core Network |
| ECIES | Elliptic Curve Integrated Encryption Scheme |
| IMSI | International Mobile Subscriber Identity |
| KEM | Key Encapsulation Mechanism |
| KDF | Key Derivation Function |
| MSIN | Mobile Subscriber Identity Number |
| PQC | Post-Quantum Cryptography |
| SUCI | Subscriber Concealed Identifier |
| SUPI | Subscriber Permanent Identifier |
| UE | User Equipment |
| USIM | Universal Subscriber Identity Module |
| Scheme | Scheme ID | Algorithms | Output Scheme |
|---|---|---|---|
| Null scheme | 0 | N/A | Size of MSIN (if using IMSI) |
| Profile A | 1 | ECIES (X25519) | 256 bits public keys + 64 bits MAC + cipher-text value |
| Profile B | 2 | ECIES (secp256r1) | 256 bits public keys + 64 bits MAC + cipher-text value |
| Reserved for future standardization | 3–11 | N/A | N/A |
| Reserved for proprietary (home operator) | 12–15 | N/A | N/A |
| Protection Scheme | Ciphertext (Bytes) | Public Key (Bytes) | Scheme Output (Bytes) |
|---|---|---|---|
| Kyber-512 | 768 | 800 | 847 |
| X25519 | 32 | 32 | 111 |
| secp256r1 | 33 | 33 | 112 |
| Device | Entity | CPU Specs | RAM (GB) | OS |
|---|---|---|---|---|
| Computer | CN & UE | AMD Ryzen 7 5700U 1.8 GHz | 16 | Ubuntu 16.04 LTS |
| MiniPC | UE | Intel 12th N95 3.4 GHz | 8 | Ubuntu 16.04 LTS |
| Raspberry Pi B+ | UE | BCM2711, Quad-core Cortex-A72 1.8 GHz | 4 | Ubuntu 16.04 LTS |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, Q.; Purification, S.; Chang, S.-Y. Post-Quantum Key Exchange and Subscriber Identity Encryption in 5G Using ML-KEM (Kyber). Information 2025, 16, 617. https://doi.org/10.3390/info16070617
Khan Q, Purification S, Chang S-Y. Post-Quantum Key Exchange and Subscriber Identity Encryption in 5G Using ML-KEM (Kyber). Information. 2025; 16(7):617. https://doi.org/10.3390/info16070617
Chicago/Turabian StyleKhan, Qaiser, Sourav Purification, and Sang-Yoon Chang. 2025. "Post-Quantum Key Exchange and Subscriber Identity Encryption in 5G Using ML-KEM (Kyber)" Information 16, no. 7: 617. https://doi.org/10.3390/info16070617
APA StyleKhan, Q., Purification, S., & Chang, S.-Y. (2025). Post-Quantum Key Exchange and Subscriber Identity Encryption in 5G Using ML-KEM (Kyber). Information, 16(7), 617. https://doi.org/10.3390/info16070617






