Intentionally Fusing Direct Manipulations into SVG Programs
Abstract
1. Introduction
- We introduce a manipulation-directed programming approach where manipulations represent changes on the SVG. These changes are fused into programs to construct a desired program. Furthermore, a const marker is utilized to guide the propagation and fusion of the manipulation in the intended location.
- We design both the forward evaluation and the backward fusion semantics to preserve manipulations. We have proven that the language semantics satisfy the GetPut and WeakPutGet properties to guarantee correctness, thereby ensuing the validity of our approach.
- We have implemented a prototype, FuseSVG, that supports manipulation-directed programming for SVG. It has been tested with 14 nontrivial benchmark examples to demonstrate the effectiveness of our approach.
2. A Core Language DF
2.1. Syntax of DF
2.2. Semantics of DF
2.3. Updatability of Expression
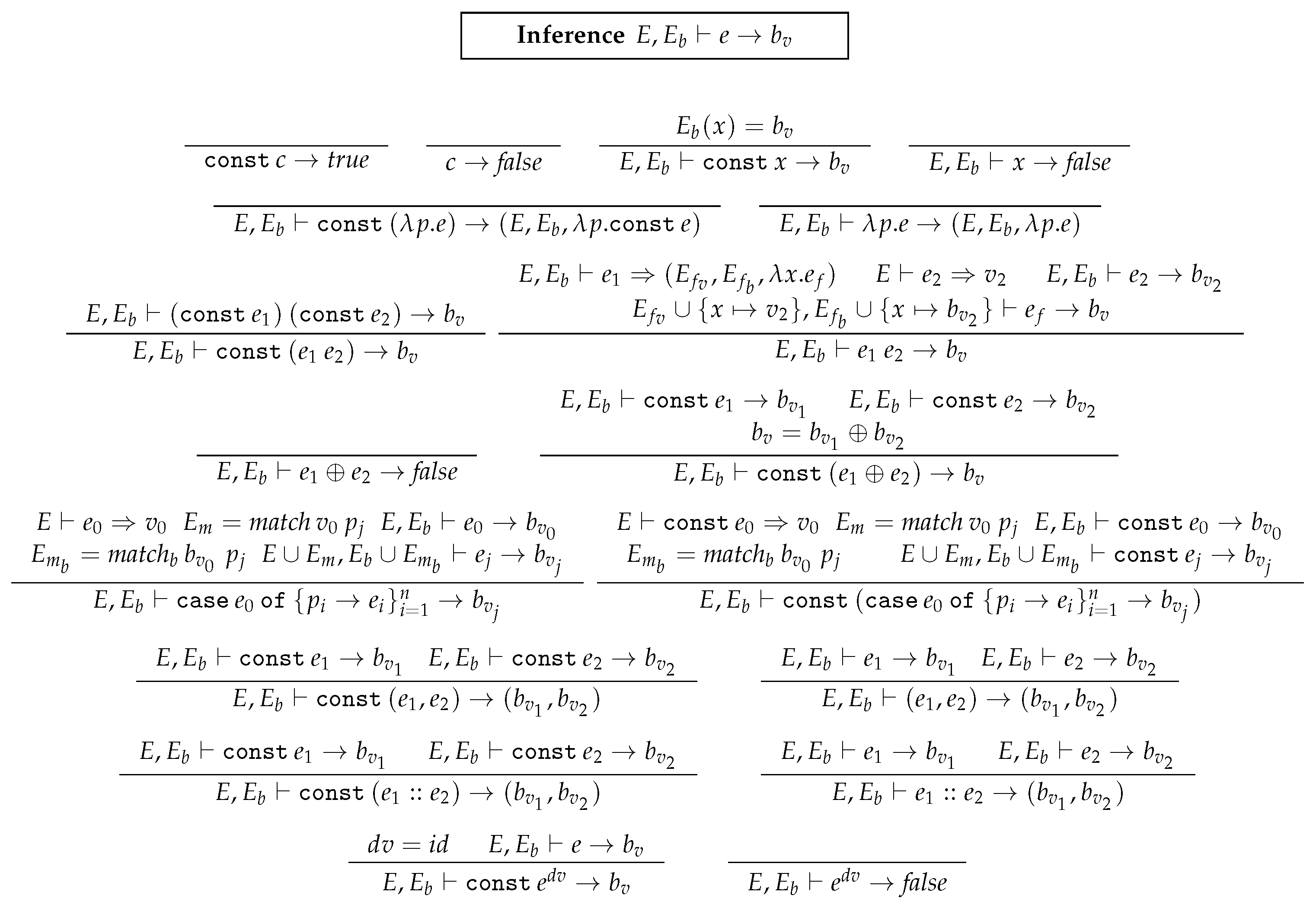
3. A Direct Manipulation Language DM
3.1. Syntax of DM
3.2. Semantics of Language DM
4. Fusing Delta into the Program
4.1. Well-Behavedness
4.2. Fusion Example
4.3. Fusion Rules
- Constants. There are two rules for constant values. If a constant value is marked by the const keyword, it remains immutable (since the inference rule will always yield to true for a constant marked by the const keyword, only is allowed). If the constant value c is not marked by the const keyword, it can be updated to , as demonstrated in P-Con2. Note that we do not directly compute the result of applying to value c, but preserve the delta, which is important for proving the WeakPutGet law.
- Variable Expressions. There are four rules for variable expressions based on whether the variable expression x is marked by the const keyword and whether the bound value for the variable is modifiable. It is crucial to differentiate between the variable expression x and the variable binding for x. The first rule P-Var1 states that if the bound value for the variable is not modifiable and the variable expression is marked by const, then only the delta is permitted. The second rule P-Var2 states that if the bound value for the variable is not modifiable, but the variable expression is modifiable, then modify the expression to . The third rule P-Var3 states that if the bound value for the variable is modifiable, and the variable expression is marked by const, then the variable x in the environment E is bound to a new delta that composes with the original delta . The last rule P-Var4 states that if the bound value for the variable is modifiable, and the variable expression is not marked by const, then despite the fact that updating the variable expression (as in P-Var2) or the variable binding (as in P-Var3) is reasonable, updating the variable, which yields a result identical to P-Var3, is the preferred approach. The last rule P-Var4 is the same as the P-Var defined in FuseDM [9].
- Lambda Abstractions. The rule P-Lam1 states that, when applying the closure , the program becomes . Since the lambda abstraction is marked by the const keyword, the body of the lambda abstraction (e) cannot be modified; only the bindings of the variables in the environment are updated. The lambda abstraction in P-Lam2 is not marked by the const keyword, and the fusion can be decomposed into two updates: replacing the function body with and the environment with the updated one .
- Function Applications. The rule P-App1 states that, if the inference result of the application is true, the application is not modifiable. The rule P-App2 states that, if the inference result of expression is true, then only can be updated. When fusing delta to , even though there exists a possibility to update x, the fusion algorithm will refrain from updating x. We first evaluate to a lambda closure, a tuple of an environment , and a lambda abstraction . For simplicity, we assume only variable patterns in the lambda abstraction. Under the binding of variable x to , which is computed from and environment , we update the expression and environment to and , respectively. And finally, we use the updated expression and environment to update expression to , and environment E to . The rule P-App3 is a bit complicated, since both and can be updated, thus they may encounter conflicts. A merge operation is defined for resolving conflicts. The intuitive idea is explained by the example “fusing into the program ” in Table 1.
- Case Expressions. The rule P-Case1 states that, if the inference result of the case expression is true, the expression is not modifiable. The rule P-Case2 states that, if the inference result of is true, then only the matched case branch expression is updated. The rule P-Case3 first applies the delta to the selected branch , resulting in the updated and . Then, it collects the delta from for , and subsequently fuses it into . Finally, the merge operator is used to resolve any conflicts.
- Binary Expressions. The rule P-C-Oplus1 states that if a binary expression marked with const is inferred as true, then the expression is not modifiable. The rule P-C-Oplus2 states that updating a const marked binary expression is the same as updating the binary expression with each operand marked by const. The rule P-Oplus1 states that if both and are inferred as true, then update the entire binary expression with . The rule P-Oplus2 states that if is inferred as true and is inferred as false, then update the right operand by a computed delta . The rule P-Oplus3 updates instead. The rule P-Oplus4 states that, if both and are inferred as false, then it chooses to update , but a merge operation is needed to resolve conflicts. How to apply deltas to binary expressions varies in different deployments; we give potential heuristic rule (P-Oplus4) for applying deltas to left operands. Other strategies include modifying the right operands, which can be achieved by marking the left operand with const.
- Tuples. The rule P-C-Tuple states that updating a const marked tuple is the same as updating each element marked by const. The rule P-Tuple states that one must update with and with . Since and may share variables, then a conflict-resolving operation is needed. The rule P-C-List (resp. P-List) is similar to the rule P-C-Tuple (resp. P-Tuple).
4.4. Merge Operation
4.5. Well-Behavedness
- The P-Con2 case:
- (a)
- According to P-Con2, the updated program is .
- (b)
- By E-dv, .
- (c)
- The delta is .
- (d)
- By P-Con2, .
- (e)
- Since is the same as , is the same as , which is the goal.
- The P-Var3 case:
- (a)
- According to P-Var3, the updated program is the same as the original one, but the environment changes, .
- (b)
- By E-Const, and E-Var, .
- (c)
- The delta is .
- (d)
- By P-Var3, .
- (e)
- Since is the same as , is the same as , which is the goal.
- The P-App3 case:
- (a)
- According to P-, .
- (b)
- By the induction hypothesis, , , and .
- (c)
- By Lemma 4, and .
- (d)
- By (c) and Lemma 3, .
- (e)
- By E-App, .
- (f)
- By the induction hypothesis, , .
- (g)
- According to definition, and , the updated program is , which is the goal.
5. Evaluation
5.1. Expressiveness
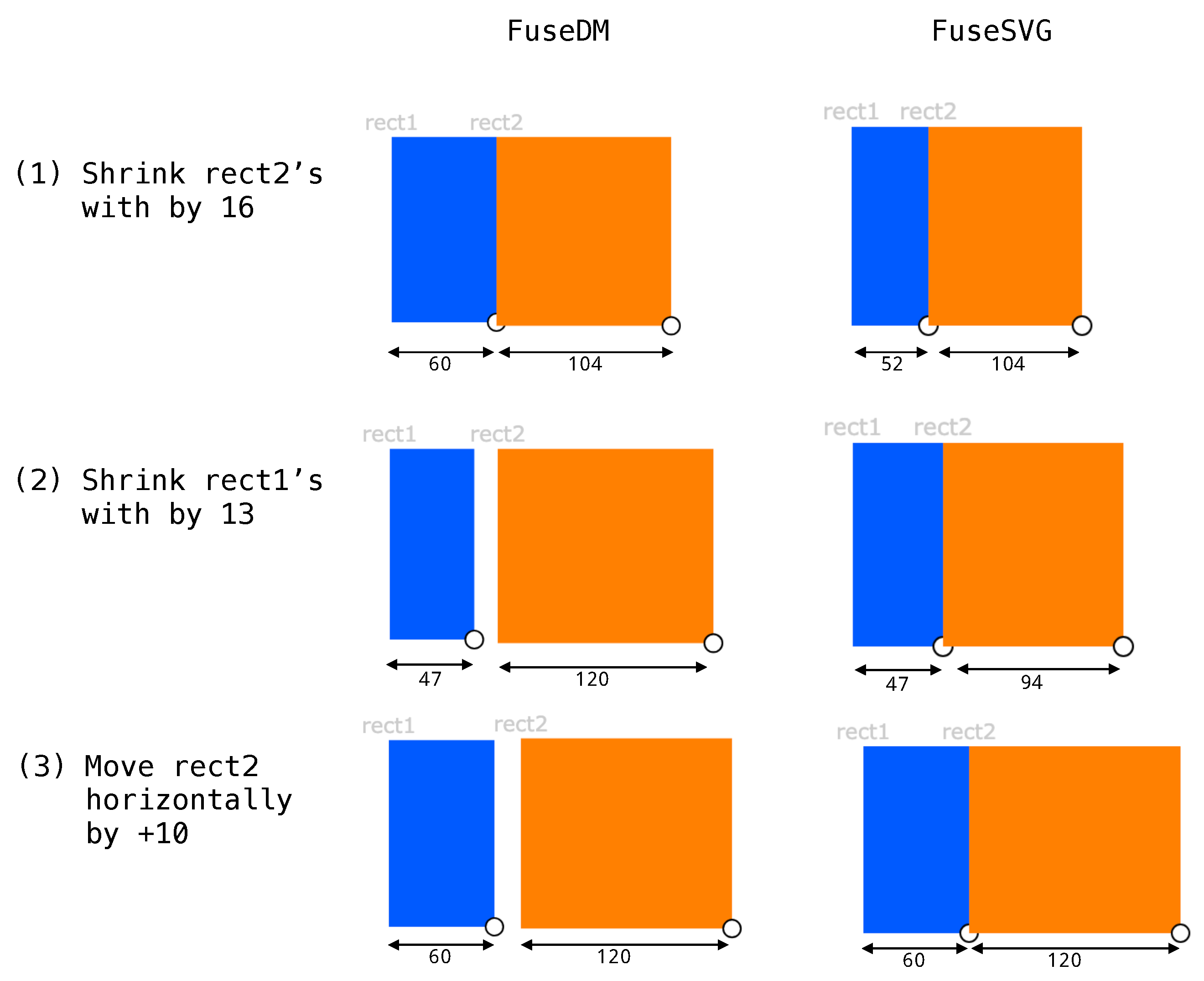
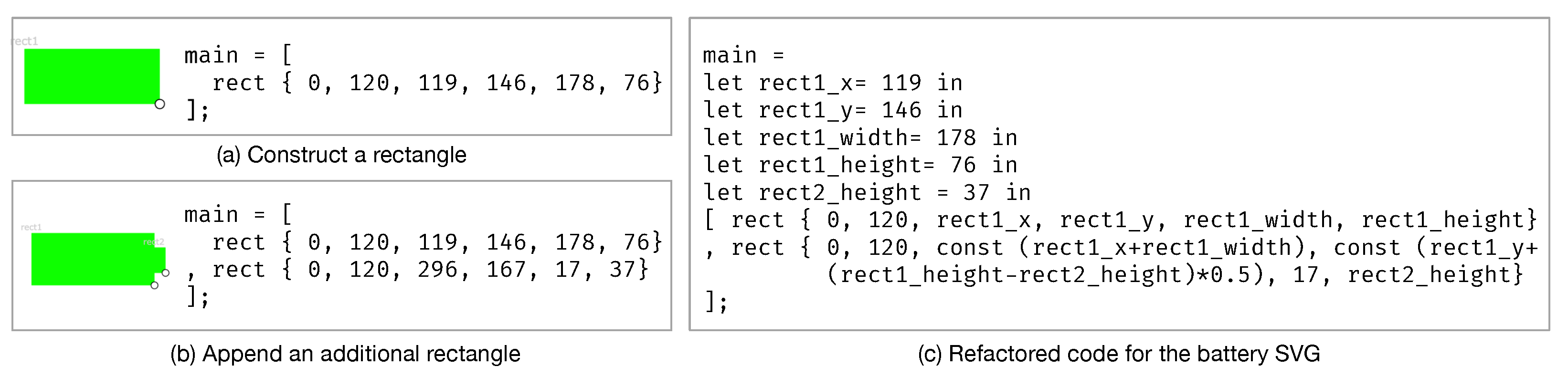
| Listing 1. Precision Floor Plan Example in FuseDM. |
| main = let rect1_x=175 in let rect1_y=239 in let rect1_width=60 in let rect1_height=106 in [ rect[0,219,rect1_x,rect1_y,rect1_width,rect1_height], rect[0,30,rect1_x+rect1_width,rect1_y,rect1_width*2,rect1_height] ]; |
| Listing 2. Precision Floor Plan Example in FuseSVG. |
| main = let rect1_x=175 in let rect1_y=239 in let rect1_width=60 in let rect1_height=106 in { rect{0,219,const rect1_x,rect1_y,rect1_width,rect1_height}, rect{0,30,const(rect1_x+rect1_width),rect1_y,const rect1_width*2,rect1_height} }; |
5.2. Case Study
6. Related Work
6.1. Bidirectional Transformations
6.2. Ambiguity and Updatability
| Listing 3. Sketch-n-Sketch. |
| w = 50 h = !(2*w) |
| Listing 4. FuseSVG. |
| w = 50 h = const (2*w) |
6.3. Constraints on View
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- McDirmid, S. Living it up with a live programming language. In Proceedings of the 22nd Annual ACM SIGPLAN Conference on Object-Oriented Programming Systems, Languages and Applications, OOPSLA ’07, Montreal, QC, Canada, 21–25 October 2007; pp. 623–638. [Google Scholar] [CrossRef]
- Burckhardt, S.; Fahndrich, M.; de Halleux, P.; McDirmid, S.; Moskal, M.; Tillmann, N.; Kato, J. It’s alive! continuous feedback in UI programming. SIGPLAN Not. 2013, 48, 95–104. [Google Scholar] [CrossRef]
- McDirmid, S. The promise of live programming. In Proceedings of the 2nd International Workshop on Live Programming, LIVE, Rome, Italy, 2016; Volume 16. [Google Scholar]
- Chugh, R.; Hempel, B.; Spradlin, M.; Albers, J. Programmatic and direct manipulation, together at last. In Proceedings of the 37th ACM SIGPLAN Conference on Programming Language Design and Implementation, Santa Barbara, CA, USA, 13–17 June 2016. [Google Scholar] [CrossRef]
- Shneiderman. Direct Manipulation: A Step Beyond Programming Languages. Computer 1983, 16, 57–69. [Google Scholar] [CrossRef]
- Hempel, B.; Chugh, R. Semi-Automated SVG Programming via Direct Manipulation. In Proceedings of the 29th Annual Symposium on User Interface Software and Technology, UIST ’16, Tokyo, Japan, 16–19 October 2016; pp. 379–390. [Google Scholar] [CrossRef]
- Mayer, M.; Kuncak, V.; Chugh, R. Bidirectional Evaluation with Direct Manipulation. Proc. ACM Program. Lang. 2018, 2, 1–28. [Google Scholar] [CrossRef]
- Hempel, B.; Lubin, J.; Chugh, R. Sketch-n-Sketch: Output-Directed Programming for SVG. In Proceedings of the 32nd Annual ACM Symposium on User Interface Software and Technology, UIST ’19, New Orleans, LA, USA, 20–23 October 2019; pp. 281–292. [Google Scholar] [CrossRef]
- Zhang, X.; Xie, R.; Guo, G.; He, X.; Zan, T.; Hu, Z. Fusing Direct Manipulations into Functional Programs. Proc. ACM Program. Lang. 2024, 8, 1211–1238. [Google Scholar] [CrossRef]
- Czarnecki, K.; Foster, J.N.; Hu, Z.; Lämmel, R.; Schürr, A.; Terwilliger, J.F. Bidirectional Transformations: A Cross-Discipline Perspective. In Theory and Practice of Model Transformations; Paige, R.F., Ed.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 260–283. [Google Scholar]
- Foster, J.N.; Greenwald, M.B.; Moore, J.T.; Pierce, B.C.; Schmitt, A. Combinators for Bi-Directional Tree Transformations: A Linguistic Approach to the View Update Problem. In Proceedings of the 32nd ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, POPL ’05, Long Beach, CA, USA, 12–14 January 2005; pp. 233–246. [Google Scholar]
- Fischer, S.; Hu, Z.; Pacheco, H. The essence of bidirectional programming. Sci. China Inf. Sci. 2015, 58, 1–21. [Google Scholar] [CrossRef]
- Hofmann, M.; Pierce, B.; Wagner, D. Symmetric Lenses. In Proceedings of the 38th Annual ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, POPL ’11, Austin, TX, USA, 26–28 January 2011; pp. 371–384. [Google Scholar]
- Ko, H.S.; Hu, Z. An Axiomatic Basis for Bidirectional Programming. Proc. ACM Program. Lang. 2017, 2, 1–29. [Google Scholar] [CrossRef]
- Barbosa, D.M.; Cretin, J.; Foster, N.; Greenberg, M.; Pierce, B.C. Matching Lenses: Alignment and View Update. In Proceedings of the 15th ACM SIGPLAN International Conference on Functional Programming, ICFP ’10, Baltimore, MD, USA, 27–29 September 2010; pp. 193–204. [Google Scholar]
- Hu, Z.; Mu, S.C.; Takeichi, M. A programmable editor for developing structured documents based on bidirectional transformations. High.-Order Symb. Comput. 2008, 21, 89–118. [Google Scholar] [CrossRef]
- Zhu, Z.; Ko, H.S.; Zhang, Y.; Martins, P.; Saraiva, J.; Hu, Z. Unifying Parsing and Reflective Printing for Fully Disambiguated Grammars. New Gener. Comput. 2020, 38, 423–476. [Google Scholar] [CrossRef]
- Hidaka, S.; Hu, Z.; Inaba, K.; Kato, H.; Matsuda, K.; Nakano, K. Bidirectionalizing Graph Transformations. In Proceedings of the 15th ACM SIGPLAN International Conference on Functional Programming, ICFP ’10, Baltimore, MD, USA, 27–29 September 2010; pp. 205–216. [Google Scholar]
- Hidaka, S.; Asada, K.; Hu, Z.; Kato, H.; Nakano, K. Structural Recursion for Querying Ordered Graphs. In Proceedings of the 18th ACM SIGPLAN International Conference on Functional Programming, ICFP ’13, Boston, MA, USA, 25–27 September 2013; pp. 305–318. [Google Scholar]
- Tran, V.D.; Kato, H.; Hu, Z. Programmable View Update Strategies on Relations. Proc. VLDB Endow. 2020, 13, 726–739. [Google Scholar] [CrossRef]
- Matsuda, K.; Wang, M. FliPpr: A System for Deriving Parsers from Pretty-Printers. New Gener. Comput. 2018, 36, 173–202. [Google Scholar] [CrossRef]
- Cheney, J.; Gibbons, J.; McKinna, J.; Stevens, P. On principles of Least Change and Least Surprise for bidirectional transformations. J. Object Technol. 2017, 16, 3:1–3:31. [Google Scholar] [CrossRef][Green Version]
- Zhang, X.; Hu, Z. Towards Bidirectional Live Programming for Incomplete Programs. In Proceedings of the 44th International Conference on Software Engineering, ICSE ’22, Pittsburgh, PA, USA, 22–27 May 2022; pp. 2154–2164. [Google Scholar] [CrossRef]
- Zhang, X.; Guo, G.; He, X.; Hu, Z. Bidirectional Object-Oriented Programming: Towards Programmatic and Direct Manipulation of Objects. Proc. ACM Program. Lang. 2023, 7, 230–255. [Google Scholar] [CrossRef]
- Ko, H.S.; Zan, T.; Hu, Z. BiGUL: A formally verified core language for putback-based bidirectional programming. In Proceedings of the 2016 ACM SIGPLAN Workshop on Partial Evaluation and Program Manipulation, PEPM ’16, St. Petersburg, FL, USA, 18–19 January 2016; pp. 61–72. [Google Scholar] [CrossRef]
- Hu, Z.; Ko, H.S. Principles and practice of bidirectional programming in BiGUL. In Bidirectional Transformations: International Summer School, Oxford, UK, July 25–29, 2016, Tutorial Lectures; Springer: Cham, Switzerland, 2018; pp. 100–150. [Google Scholar]
- Jackiw, R.N.; Finzer, W.F. The geometer’s sketchpad: Programming by geometry. In Watch What I Do: Programming by Demonstration; MIT Press: Cambridge, MA, USA, 1993; pp. 293–307. [Google Scholar]
- Xia, H.; Araujo, B.; Grossman, T.; Wigdor, D. Object-Oriented Drawing. In Proceedings of the 2016 CHI Conference on Human Factors in Computing Systems, CHI ’16, San Jose, CA, USA, 7–12 May 2016; pp. 4610–4621. [Google Scholar] [CrossRef]
- Jacobs, J.; Gogia, S.; Mundefinedch, R.; Brandt, J.R. Supporting Expressive Procedural Art Creation through Direct Manipulation. In Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems, CHI ’17, Denver, CO, USA, 6–11 May 2017; pp. 6330–6341. [Google Scholar] [CrossRef]
- Schachman, T. Apparatus. Available online: http://aprt.us (accessed on 17 February 2025).
- Bricault, S. Recursive Drawing. Available online: http://bricault.mit.edu/recursive-drawing (accessed on 17 February 2025).
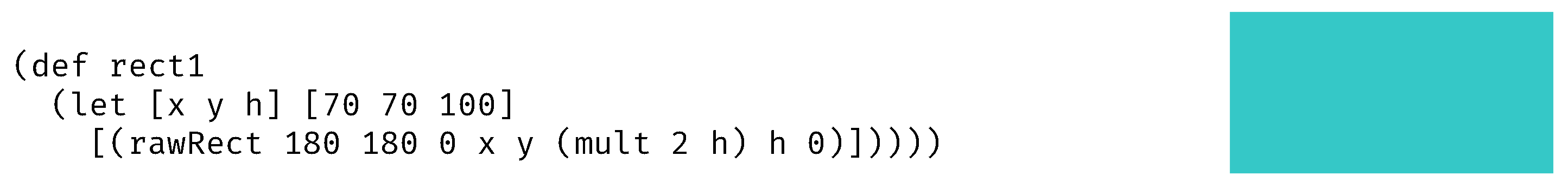
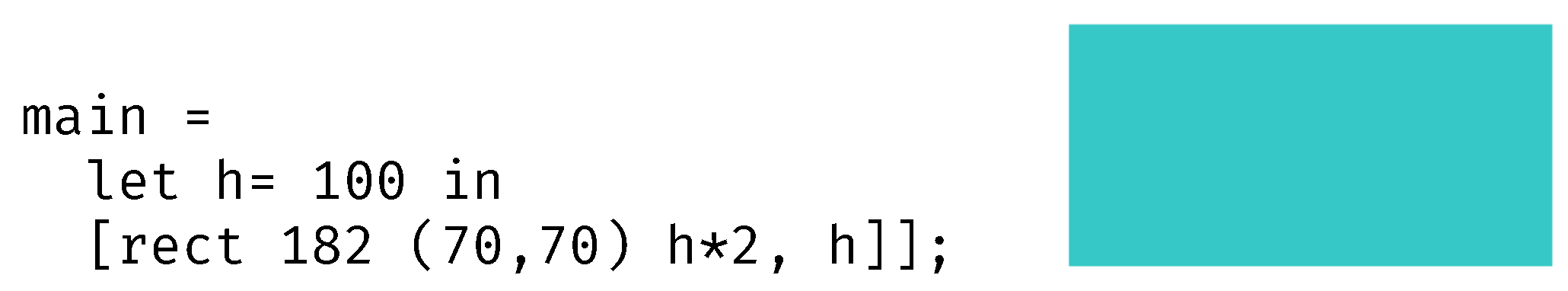
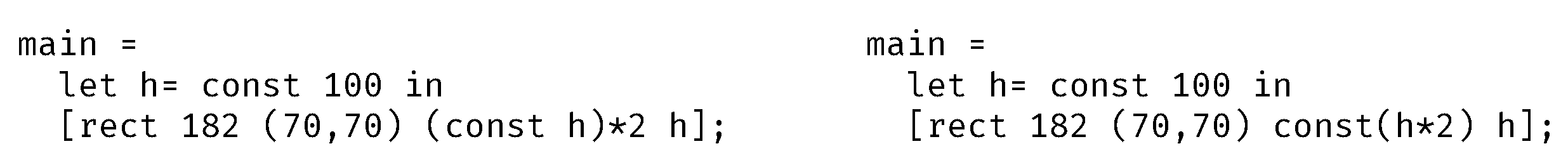
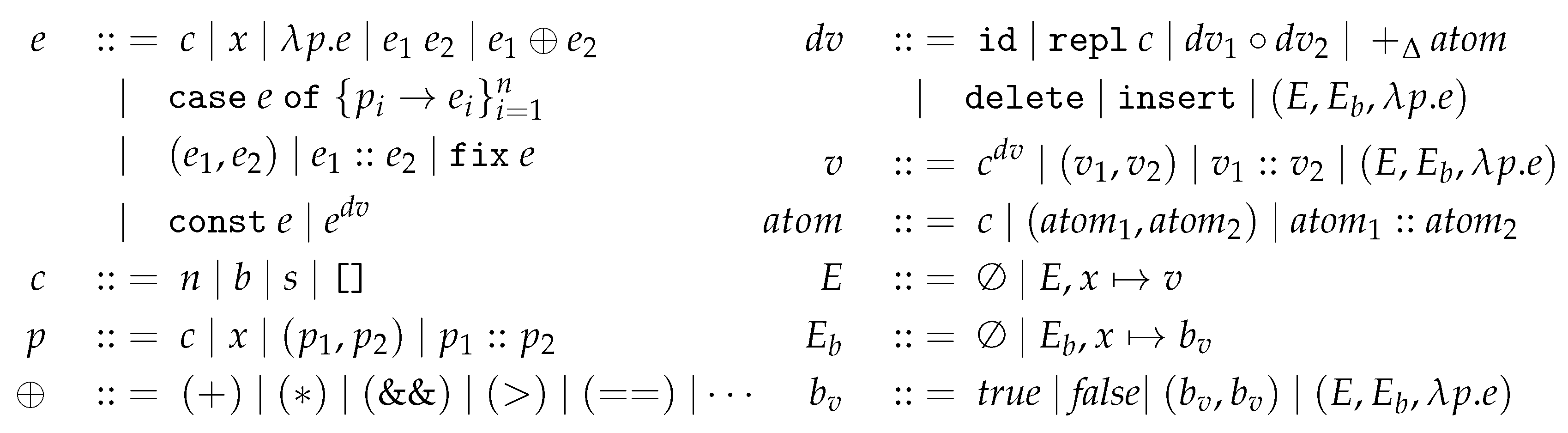
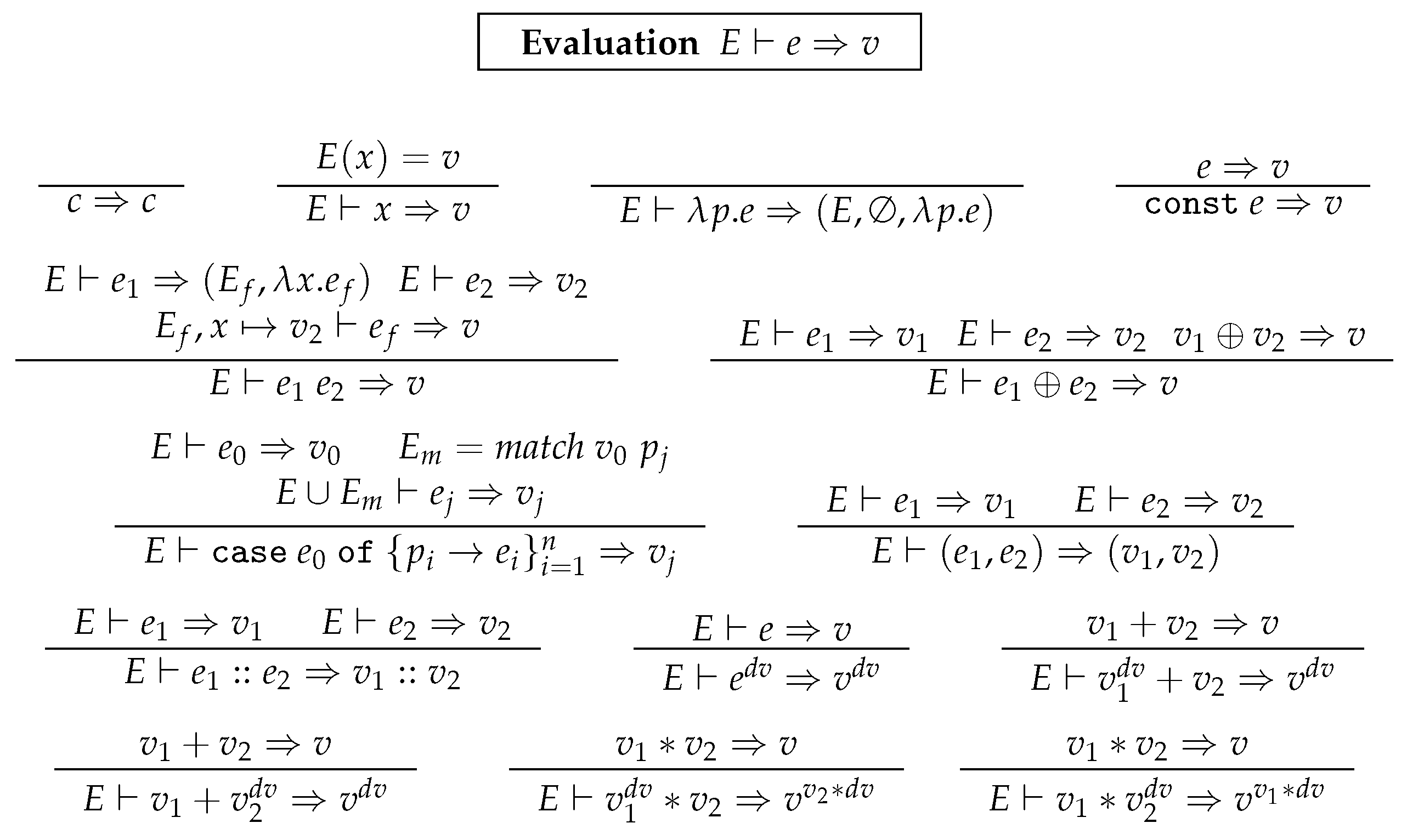
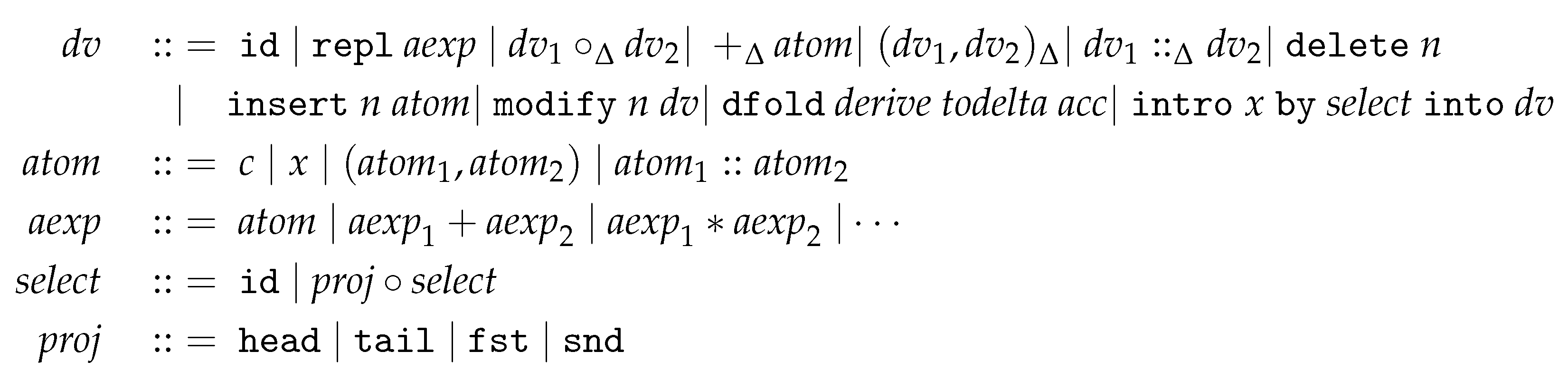

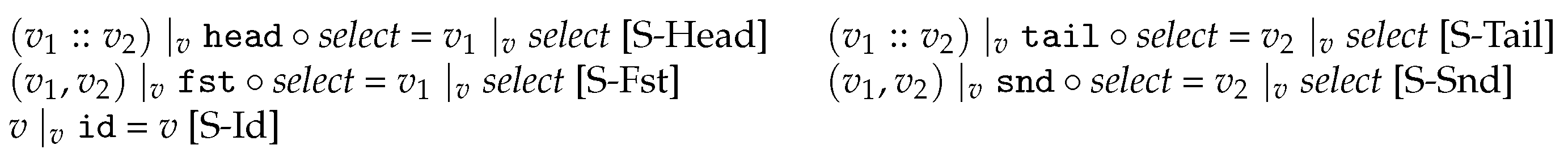

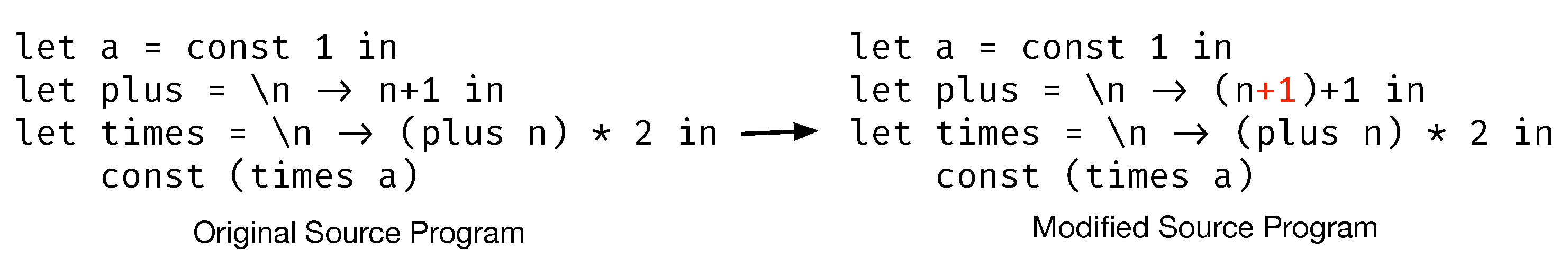

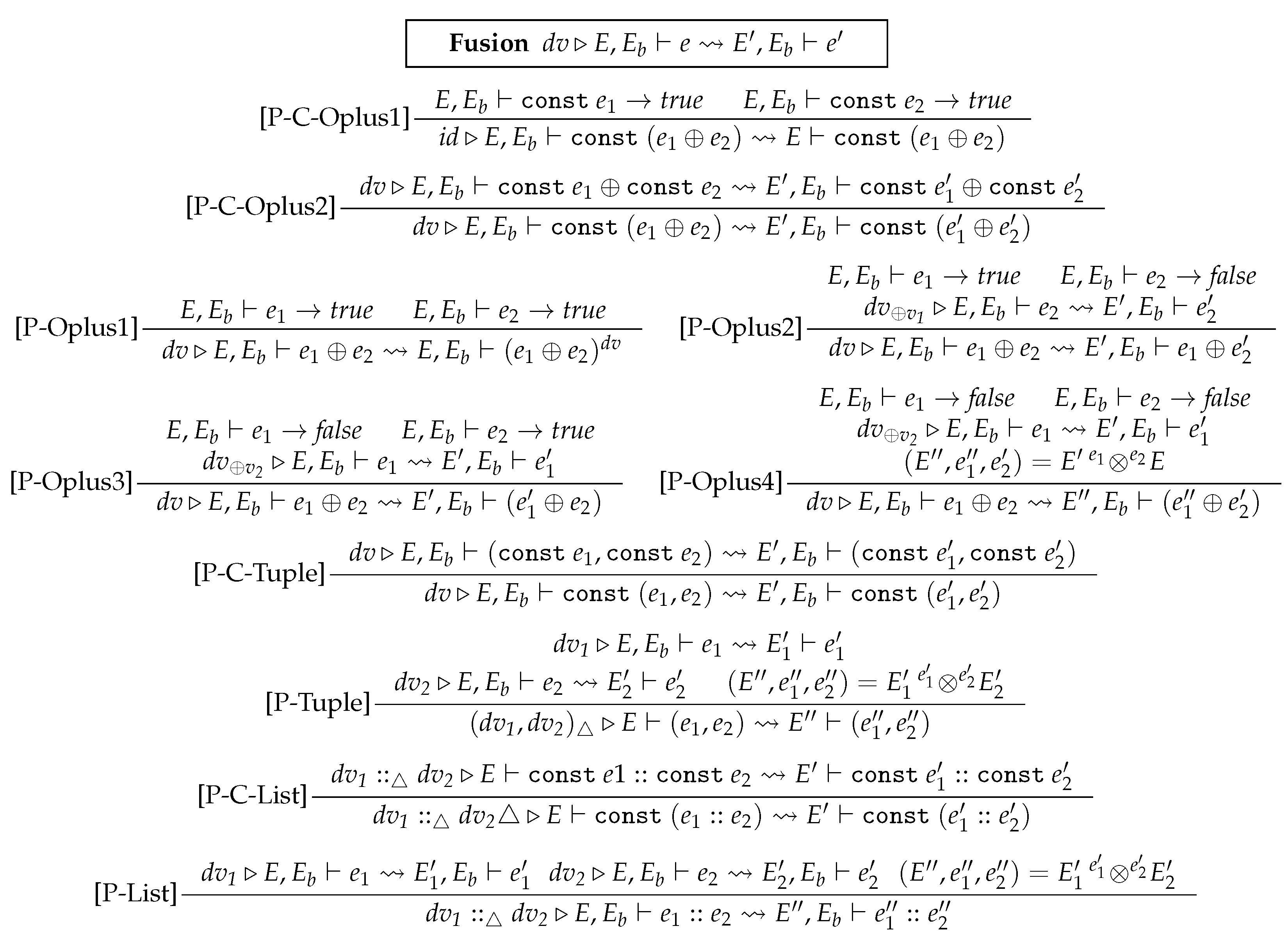

| Detail | Example | |
|---|---|---|
| 1 | Evaluate to value. | |
| 2 | Evaluate to closure. | |
| 3 | Fuse the delta into the function body and obtain . | |
| 4 | Construct the function closure . | |
| 5 | Fuse the modified function closure into . | |
| 6 | Fuse the delta into . | |
| 7 | Merge environments and solve conflicts. |
| ID | Example | Multiple Update Choice | Immutability for Single Value | Number of Relations |
|---|---|---|---|---|
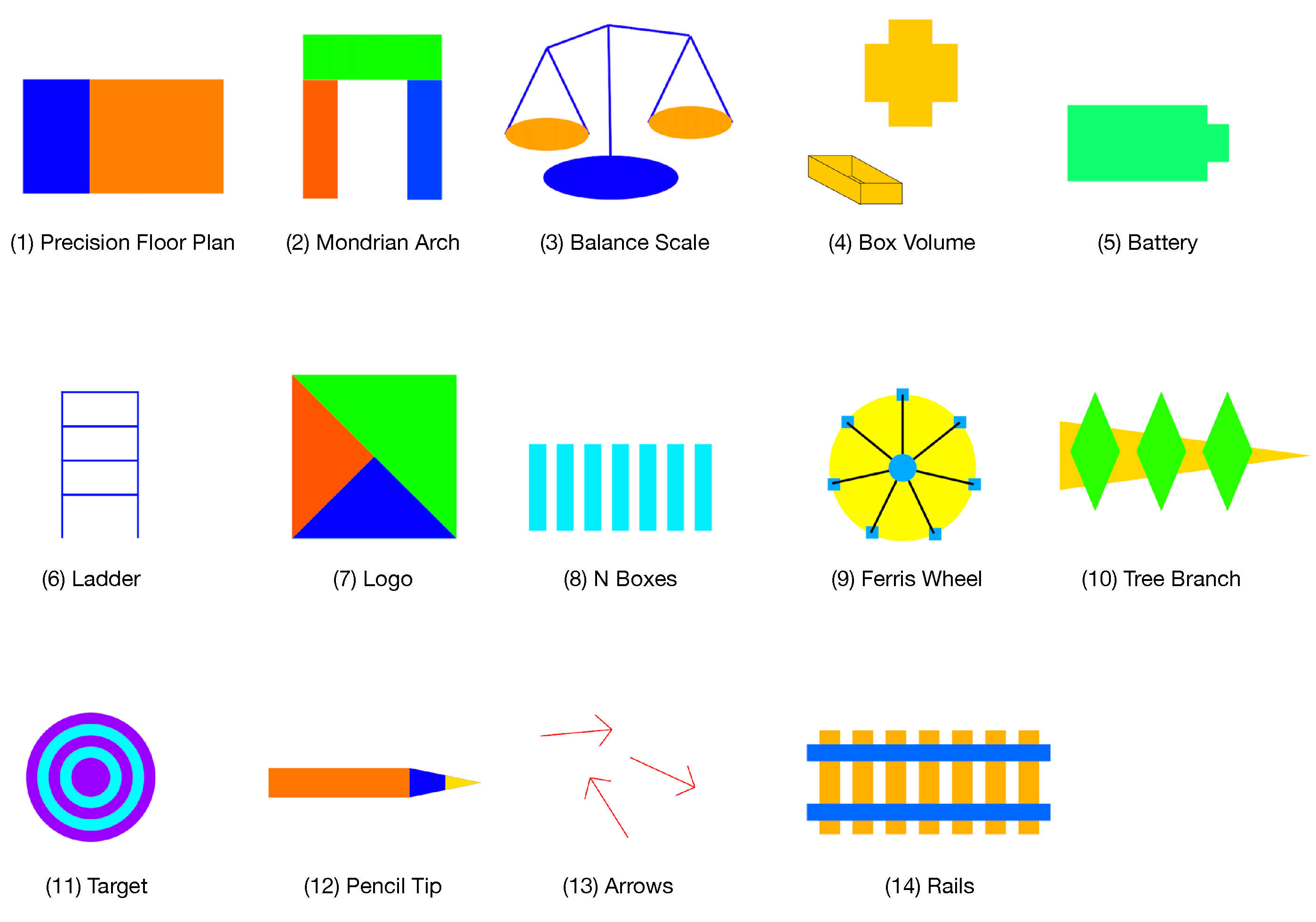
| 1 | Precision Floor Plan | ✓ | ✓ | 3 |
| 2 | Mondrian Arch | ✓ | ✓ | 6 |
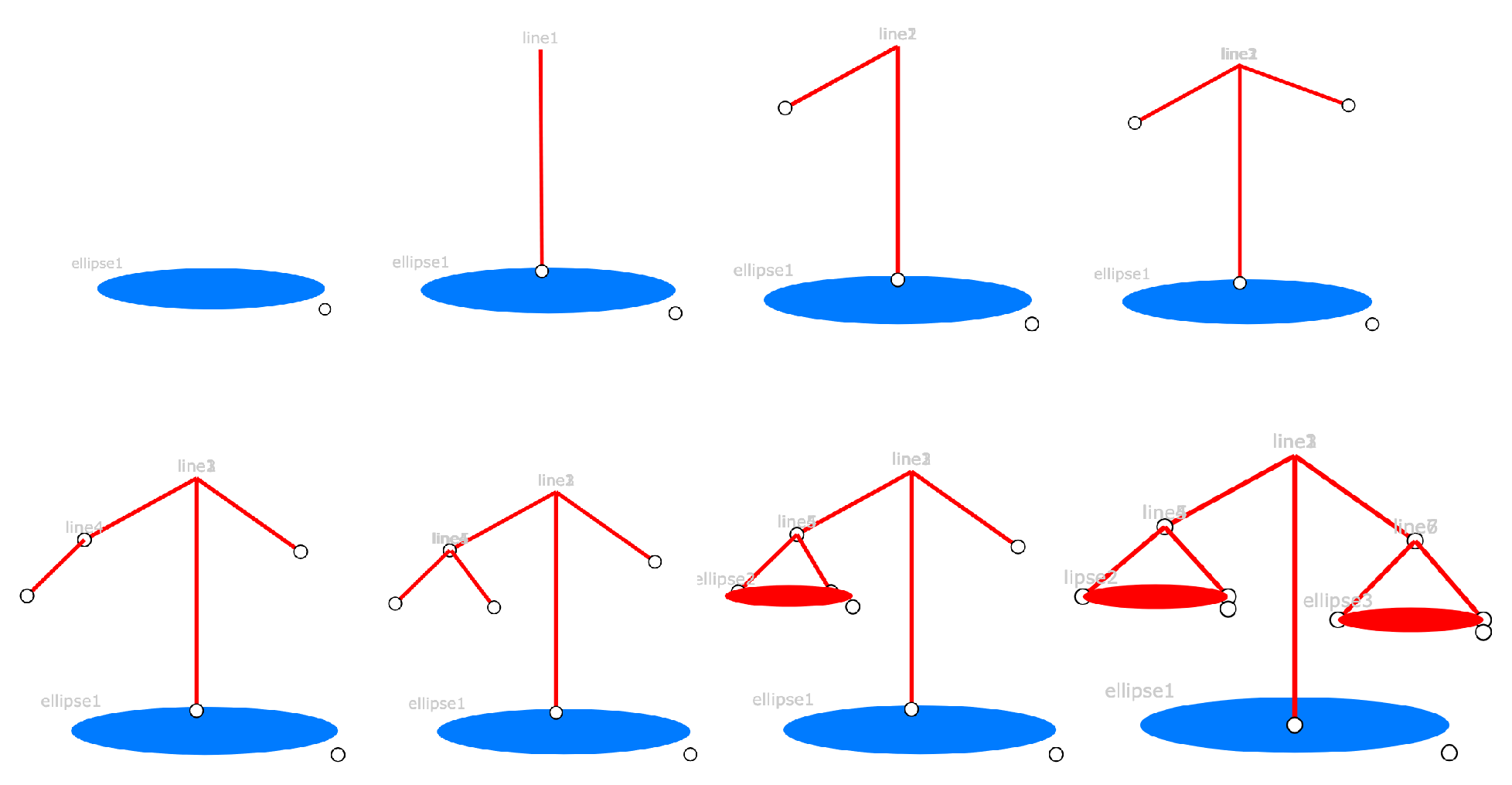
| 3 | Balance Scale | ✓ | ✓ | 15 |
| 4 | Box Volume | ✓ | ✓ | 21 |
| 5 | Battery | ✓ | ✓ | 2 |
| 6 | Ladder | ✓ | ✓ | 10 |
| 7 | Logo | ✓ | ✓ | 6 |
| 8 | N Boxes | ✓ | ✓ | 6 |
| 9 | Ferris Wheel | ✓ | ✓ | 54 |
| 10 | Tree Branch | ✓ | ✓ | 18 |
| 11 | Target | ✓ | ✓ | 6 |
| 12 | Pencil Tip | ✓ | ✓ | 11 |
| 13 | Arrows | ✓ | ✓ | 28 |
| 14 | Rails | ✓ | ✓ | 38 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zan, T.; Zhang, X.; He, X.; Hu, Z. Intentionally Fusing Direct Manipulations into SVG Programs. Information 2025, 16, 169. https://doi.org/10.3390/info16030169
Zan T, Zhang X, He X, Hu Z. Intentionally Fusing Direct Manipulations into SVG Programs. Information. 2025; 16(3):169. https://doi.org/10.3390/info16030169
Chicago/Turabian StyleZan, Tao, Xing Zhang, Xiao He, and Zhenjiang Hu. 2025. "Intentionally Fusing Direct Manipulations into SVG Programs" Information 16, no. 3: 169. https://doi.org/10.3390/info16030169
APA StyleZan, T., Zhang, X., He, X., & Hu, Z. (2025). Intentionally Fusing Direct Manipulations into SVG Programs. Information, 16(3), 169. https://doi.org/10.3390/info16030169






