1. Introduction
Modern healthcare systems increasingly rely on Electronic Health Records (EHRs), which integrate and transmit medical images as part of patient data management. These images often contain sensitive personal information, exhibit high inter-pixel correlations, and involve large data volumes—especially in grayscale formats. Unauthorized access or misuse can result in serious privacy breaches, highlighting the critical need for secure image transmission to ensure confidentiality, integrity, and privacy [
1,
2].
Conventional data encryption algorithms such as AES (Advanced Encryption Standard), DES (Data Encryption Standard), and IDEA (International Data Encryption Algorithm) are primarily designed for textual data. These methods encrypt binary representations of digital data streams, but they are often inefficient for medical images due to their high redundancy and large size [
3]. To address image-specific security challenges, various alternatives—such as steganography [
4], watermarking [
5], and image encryption [
6]—have been proposed. Among them, image encryption is particularly effective in converting images into noise-like ciphertext, thereby concealing their content during transmission.
Numerous image encryption techniques have been explored, including DNA-based encryption [
7,
8,
9], cellular automata [
10], compressive sensing [
11], fractional Fourier transforms [
12], S-boxes [
13], fractal theory [
14], neural networks [
15], and chaotic systems [
6,
16,
17]. Among these techniques, chaotic systems have shown particular promise due to their inherent features, such as sensitivity to initial conditions, topological transitivity, and unpredictability, which align well with cryptographic principles.
The complexity of a chaotic system directly influences the security of the encryption algorithm. However, when implemented on finite-precision platforms, chaotic systems may suffer from degradation, wherein chaotic behavior deteriorates into periodic or predictable patterns, thereby compromising encryption strength. To overcome this limitation, researchers have explored methods to improve the dynamic complexity and robustness of chaotic systems.
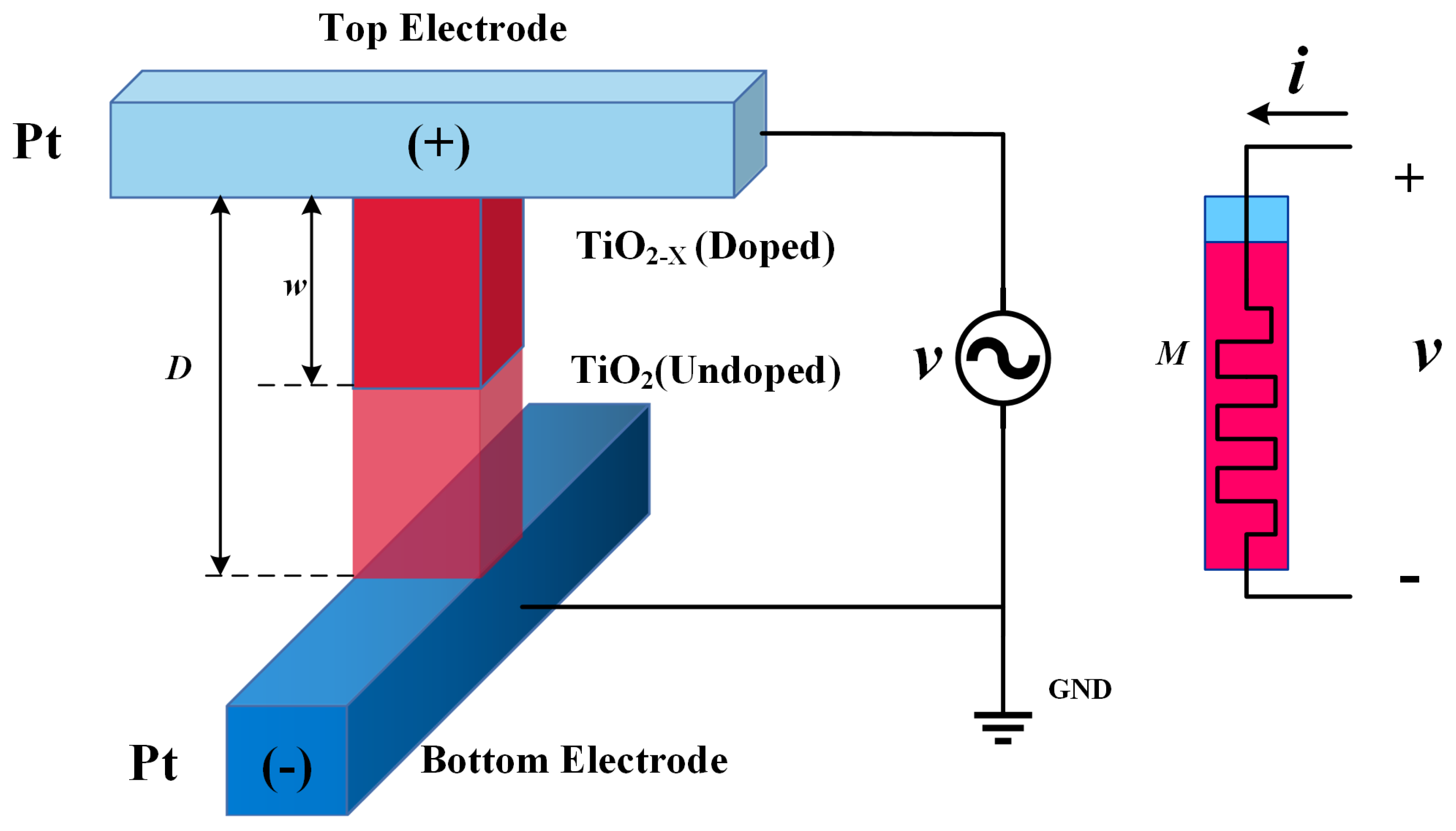
The concept of the memristor was first introduced by Professor Chua in 1971, who theoretically defined it as the fourth fundamental circuit element relating magnetic flux and electric charge [
18]. In 2008, researchers at HP Labs fabricated the first physical memristor using titanium dioxide nanomaterials, reigniting global interest in this field [
19]. Due to their non-volatility, nanoscale structure, and state-dependent behavior, memristors could be applied in various fields, including encryption algorithms [
11,
19], secure communications [
20], neural networks [
21], electrical engineering [
22], and artificial intelligence [
23].
Recent research has shown that integrating memristors into classical chaotic maps, such as sine maps, Hénon maps, and higher-order systems, can effectively improve the diversity of their dynamic behaviors [
21]. By mitigating finite-precision degradation and enhancing system unpredictability, memristor-based chaotic systems provide a more secure foundation for cryptographic applications [
19]. For instance, Yu et al. [
24] proposed a 5-D memristor exponential hyperchaotic system based on a nonlinear flux-controlled model and demonstrated its feasibility for image encryption. Awais et al. [
25] introduced a novel chaotic system constructed from two flux-controlled memristors, exhibiting symmetric bifurcation, multistability, and extreme sensitivity to initial conditions within a 4-D dynamical framework. These works validate the advantages of memristor-based systems in constructing robust chaotic models, though their application to medical image encryption remains underexplored [
26].
Since Fridrich’s introduction of the scrambling–diffusion encryption framework using 2-D discrete chaotic maps, this structure has become foundational in image cryptography. In this model, scrambling alters pixel positions, while diffusion modifies pixel values. To enhance encryption performance, researchers have often combined such frameworks with novel chaotic systems [
27].
Traditional image scrambling methods include row–column scrambling, Arnold transforms, curve transformations, scan-based traversal, and block scrambling. Despite their structural differences, these methods typically suffer from periodicity, limited randomness, and local effects, especially in some block-based algorithms that ignore inter-block correlation. Due to their non-periodic nature and ease of implementation, Josephus-based scrambling methods have gained attraction. Wang et al. [
28] applied Josephus scrambling independently to image rows and columns in three iterative cycles, but the time complexity is relatively high. Guan et al. [
29] enhanced the classical Josephus method by replacing removal operations with shift operations and introduced random step sizes from chaotic sequences, while there is still room for improvement in the robustness of the algorithm. Xie et al. [
30] proposed block-wise Josephus scrambling based on traversal paths, improving global pixel scrambling, albeit at the cost of inter-block correlation. In addition, the above scrambling algorithms are mostly composed of a single Josephus algorithm, and there is still room for improving the complexity of pixel-point obfuscation.
On the diffusion side, DNA-inspired operations have shown promise due to their large storage capacity, low energy consumption, and fast computation [
31,
32]. Nevertheless, several limitations have emerged. Liu et al. [
33] evaluated a DNA encryption algorithm from [
34] and found it deficient in plaintext sensitivity and vulnerable to chosen-plaintext and known-plaintext attacks. Hermassi et al. [
35] similarly identified irreversibility and poor resistance to statistical attacks in the DNA-based algorithm from [
36]. In contrast to the double-helix structure of DNA, RNA operates as a single-stranded molecule, offering greater flexibility. RNA diffusion algorithms exploit base-pairing rules to form temporary helices and use codons—triplets of nucleotides that translate to amino acids—to enrich diffusion strategies [
37]. For instance, Wang et al. [
38] proposed a method involving modular RNA operations and random codon replacement. Zhou et al. [
39] presented a 2-D hyperchaotic map-based RNA diffusion algorithm. However, current RNA-based methods still suffer from overly simplistic operations, redundant encoding rules, and limited variation in processing modes, reducing their resistance to plaintext attacks. Moreover, the potential of amino acid codon mappings remains underexplored in diffusion design.
Cryptography and cryptanalysis are two interrelated branches of cryptology. While encryption focuses on enhancing confusion, diffusion, and efficiency, cryptanalysis evaluates systems from an adversarial perspective, exposing structural vulnerabilities and key management flaws. Recent studies have identified several common weaknesses in chaos-based image encryption schemes, such as static key streams susceptible to chosen-plaintext attacks, over-reliance on external data, and redundant operations [
40,
41]. To address these issues, researchers suggest incorporating image-dependent features (e.g., hash values) into key generation, diversifying chaotic sequence usage, streamlining encryption steps, and applying more comprehensive security evaluations.
In summary, medical image encryption faces two fundamental challenges: (1) Due to the large data volume and high inter-pixel correlation inherent in medical images, conventional scrambling techniques often result in localized scrambling, which fails to sufficiently disrupt global structural dependencies—particularly along diagonal directions; and (2) DNA/RNA-based diffusion methods tend to be structurally simplistic, offering limited diffusion strength and involving redundant transformation rules with insufficient computational diversity. In light of these challenges, there is a growing imperative to develop encryption algorithms tailored to the protection of medical images—algorithms that are not only secure and efficient, but also lightweight, image-adaptive, and resource-conscious, with strong diffusion and high key sensitivity.
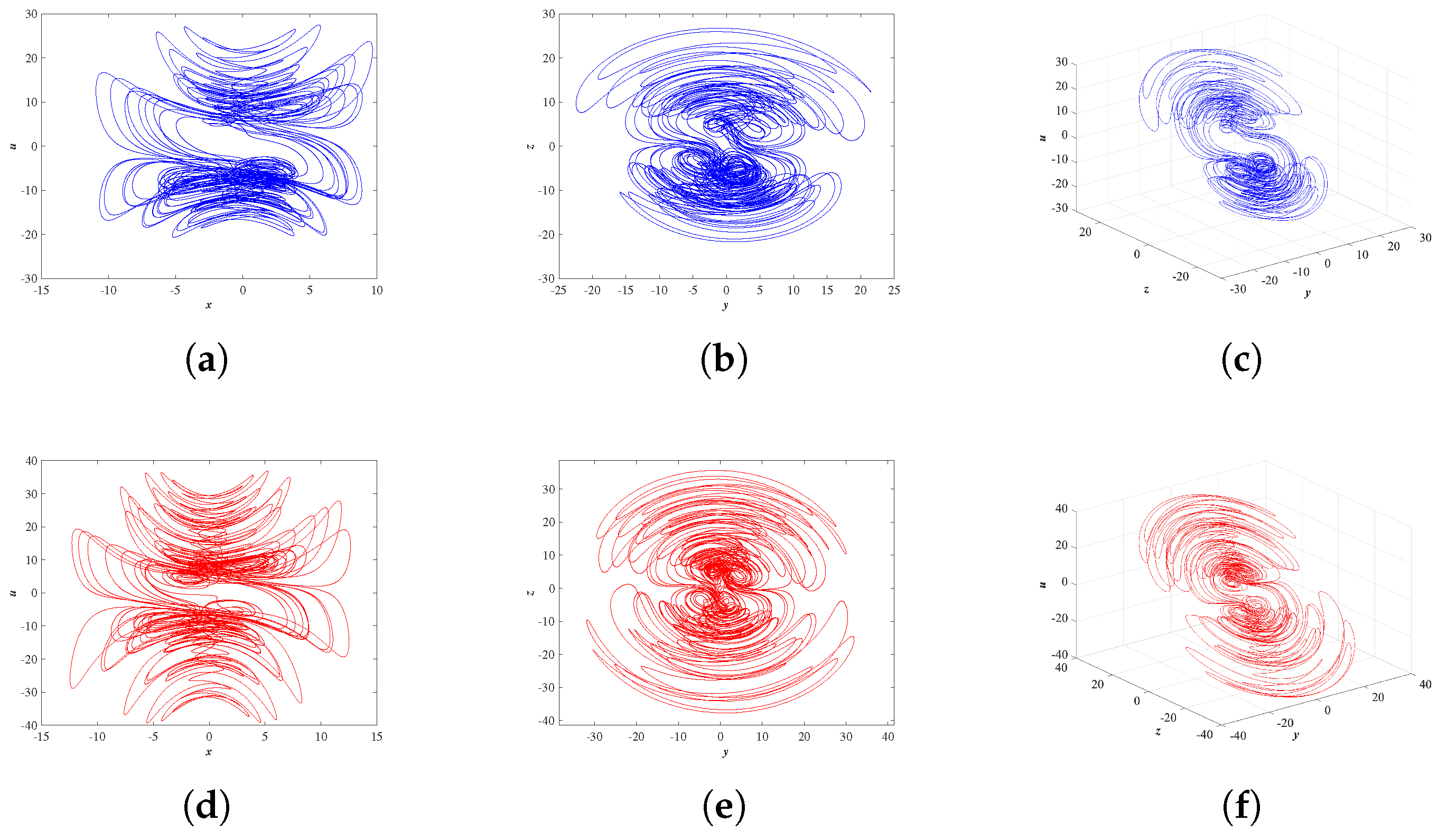
To address these gaps, this study proposes a novel grayscale medical image encryption algorithm. First, we construct a new high-dimensional memristor chaotic system based on the HP memristor model. Through bifurcation diagrams, Lyapunov exponent diagrams, complexity analysis, and histogram analysis, we demonstrate that the system exhibits broader chaotic ranges, superior ergodicity, and higher dynamic complexity. To enhance resistance against chosen-plaintext and equivalent-key attacks, the system’s initial conditions are derived from the plaintext image’s SHA-256 hash. The resulting chaotic sequences are further diversified and integrated into the following stages of encryption, avoiding static or repetitive use. The scrambling stage employs the SLJSS algorithm, which combines L-shaped decomposition, enhanced Josephus traversal, and spiral reconstruction to disrupt global pixel correlations efficiently with minimal redundancy. The diffusion process is implemented via the DCMRD algorithm, featuring dynamic RNA encoding, codon-level substitution, and multiple RNA operations before final reverse decoding. This structure aims to balance complexity and security while avoiding unnecessary computational overhead. Finally, we perform a comprehensive security evaluation beyond conventional statistical and randomness tests. The results collectively suggest that the proposed algorithm achieves strong key dependence, high diffusion strength, and structural robustness.
The main contributions of this work are as follows:
A novel 5-D memristor chaotic system based on the HP model is proposed, offering high complexity and randomness suitable for secure encryption.
In the scrambling phase, we introduce the SLJSS algorithm, which follows a symmetric design combining forward and reverse L-type decomposition, improved Josephus scrambling, and non-deterministic spiral reconstruction. This multi-layered strategy ensures low correlation across rows, columns, and diagonals. In the diffusion phase, the DCMRD algorithm is proposed to combine codon substitution and RNA base operations. In it, we optimize the operation rules to reduce the repetition and redundancy of the results and propose a multiple base operation model that contains addition, subtraction, XOR, multiplication, and custom base functions, which guarantees the diversity, randomness, and security of the whole encryption process.
Simulation results demonstrate that the proposed algorithm achieves high encryption and decryption quality, exhibits strong statistical and differential resistance, and outperforms comparable methods in reducing pixel correlation.
The remainder of this paper is organized as follows.
Section 2 details the construction of the proposed memristor chaotic system.
Section 3 presents the design principles and process of the encryption algorithm.
Section 4 provides simulation results and theoretical analysis regarding security and performance.
Section 5 shows the conclusion of this paper.
3. Proposed Encryption Algorithm
This section introduces a novel encryption algorithm for grayscale medical images of arbitrary size, based on the 5-D memristor chaotic system. The scrambling phase utilizes the SLJSS algorithm, while the diffusion phase employs the DCMRD algorithm. The algorithm achieves efficient encryption without requiring multiple iterative rounds and guarantees lossless recovery of the encrypted image.
Assume the plaintext image I has dimensions . The overall encryption process is summarized as follows and each step would be described in details in sub-sections:
- Step 1:
Input the plaintext image
I and key. As described in
Section 3.1, compute the initial value using the SHA-256 hash of image-derived values. Perform a series of operations to obtain the initial conditions and parameters for the chaotic system.
- Step 2:
As detailed in
Section 3.2, a series of operations are performed on the chaotic system to obtain pseudo-random sequences referred to as the Key Sequence.
- Step 3:
According to
Section 3.3, perform symmetric L-type decomposition, Josephus scrambling, and spiral sequence reconstruction on
I, yielding the scrambled matrix
.
- Step 4:
As shown in
Section 3.4, apply RNA dynamic encoding, codon substitution, multi-base operations, and RNA decoding to
, producing the final ciphertext Encrypted Image.
A flowchart summarizing the full encryption process is provided in
Figure 7.
3.1. Generation of the Initial Values of Chaotic System
In chaos-based encryption systems, the security and sensitivity of the algorithm are closely tied to the choice of the chaotic system’s initial values and control parameters. While the control parameters are defined by the secret key (), the initial values must be dynamically linked to the plaintext image to resist chosen-plaintext and known-plaintext attacks.
To achieve this coupling, the cryptographic SHA-256 hash function is employed. Thanks to its irreversibility and strong avalanche effect, even a single-bit change in the input leads to a completely different hash output. Compared with lighter hash functions such as MD5, SHA-256 provides higher resistance to collision and preimage attacks, making it a more suitable choice for high-security scenarios like medical image encryption. This design ensures that any variation in the plaintext image will result in a different chaotic trajectory, thereby significantly enhancing the encryption algorithm’s plaintext sensitivity and security strength [
45].
The construction process is as follows: the input image is first processed to extract statistical features in three directions—row, column, and diagonal—yielding three summation vectors: SumRow, SumCol, and SumDiag. These are individually hashed and then combined to generate a decimal key vector
as follows:
To further enhance randomness, a key feature value is computed using modular sums of XOR combinations. This value is then used to perturb each initial state, ensuring their dependence on the plaintext.
The initial values of the chaotic system’s five state variables
and the transient iteration count
h are calculated as follows:
This approach ensures that the chaotic initial conditions are uniquely tied to the plaintext image, providing strong one-time randomness and enhancing the encryption system’s ability to withstand differential and statistical attacks. The complete process is illustrated in Algorithm 1.
| Algorithm 1: Key Generation |
Input: Plain Image I Output: - 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
|
3.2. Generation of Key Sequences
In a chaos-based image encryption framework, the core cryptographic operations—such as scrambling and diffusion—require secure and image-dependent pseudo-random sequences to drive nonlinear transformations. Therefore, in this stage, we construct a series of key sequences from the initial conditions and control parameters of the 5-D memristor chaotic system generated in
Section 3.1. Since these chaotic states are directly influenced by the plaintext image, the resulting sequences inherit strong plaintext sensitivity, ensuring that even the slightest change in the input image produces a completely different encryption trajectory.
To further enhance unpredictability and mitigate finite-precision degradation during numerical integration, a periodic perturbation mechanism is introduced to the chaotic system. Meanwhile, the generated sequences are mapped to different rule vectors, which are required in downstream modules such as codon transformation, scrambling, and DNA-level diffusion. For ease of control and modular reuse, we apply expansion, rounding, and modulo operations to generate distinct sub-sequences (e.g., , , , , and ), each serving a dedicated functional role.
The complete generation process is outlined below:
- Step 1:
The 5-D memristor chaotic system is initialized with
,
,
,
, and
and is numerically integrated using the fourth-order Runge–Kutta method. To eliminate transient behavior and enhance randomness, the first
h iterations are discarded. Then, the system is iterated
times to generate five chaotic sequences:
X,
Y,
Z,
U, and
W. To suppress dynamical degradation caused by finite-precision computation, a perturbation is added every 2000 iterations using the following equation:
- Step 2:
These chaotic sequences are processed to derive the operational rule vectors as follows:
- Step 3:
The first elements of U and the first elements of W are concatenated to form a sequence S.
- Step 4:
The first half of
S is used to compute scrambling control parameters
,
,
,
, and
:
- Step 5:
The second half of S is processed similarly to obtain the parameters B1, B2, B3, p2, and sort2 for the second phase of scrambling.
These carefully constructed key sequences and control parameters serve as the backbone of subsequent encryption stages. Because they are generated from chaotic states that are image-dependent and perturbed periodically, they ensure high sensitivity, strong randomness, and resilience against cryptanalytic attacks. The full generation process is summarized in Algorithm 2.
3.3. Symmetric L-Type Josephus Spiral Scrambling
This section introduces the design rationale and implementation steps of the proposed symmetric L-type Josephus spiral scrambling (SLJSS) algorithm, which is responsible for the spatial permutation of pixel positions.
3.3.1. Design Background and Motivation
Traditional image scrambling methods often rely on row-wise, column-wise, or block-wise operations. While these methods disrupt local correlation, they frequently fail to sufficiently break long-range dependencies—especially diagonals and inter-block patterns—leading to potential cryptanalytic weaknesses. To address this limitation, we propose a multi-dimensional scrambling scheme that integrates the following:
L-type stratification, to enable interconnection between row, column, and block regions and avoid local confinement;
Extended Josephus permutation, to increase randomness through flexible control of direction, step size, and starting position;
Spiral reconstruction, to enhance global reorganization and increase scrambling diversity;
Symmetric bidirectional scrambling, to further reduce residual structural patterns.
| Algorithm 2: Chaotic Sequence Generation |
Input: x0: Initial values, N: sequence length, n: transient length Output: CodeRule, CodonRule, KeyImage, opRule, Operation, t1, t2, A1–A3, B1–B3, sort1, sort2, p1, p2 |
| /* Step 1: Solve the chaotic system using RK45 integration | */ |
- 1
;
|
| /* Step 2: Generate primary sequences | */ |
- 2
; - 3
; - 4
; - 5
; - 6
;
|
| /* Step 3: Construct S sequence | */ |
- 7
|
| /* Step 4: Derive scrambling parameters | */ |
- 8
; - 9
; - 10
; - 11
; - 12
; - 13
;
|
| /* Step 5: Derive reverse parameters | */ |
- 14
; - 15
; - 16
; - 17
; - 18
;
|
Each of these components is carefully selected based on extensive experimental evaluation to maximize scrambling entropy and visual unrecognizability. The sequence and structure of each sub-step are determined through iterative testing and design reasoning, with the aim of avoiding insufficient or over-local scrambling.
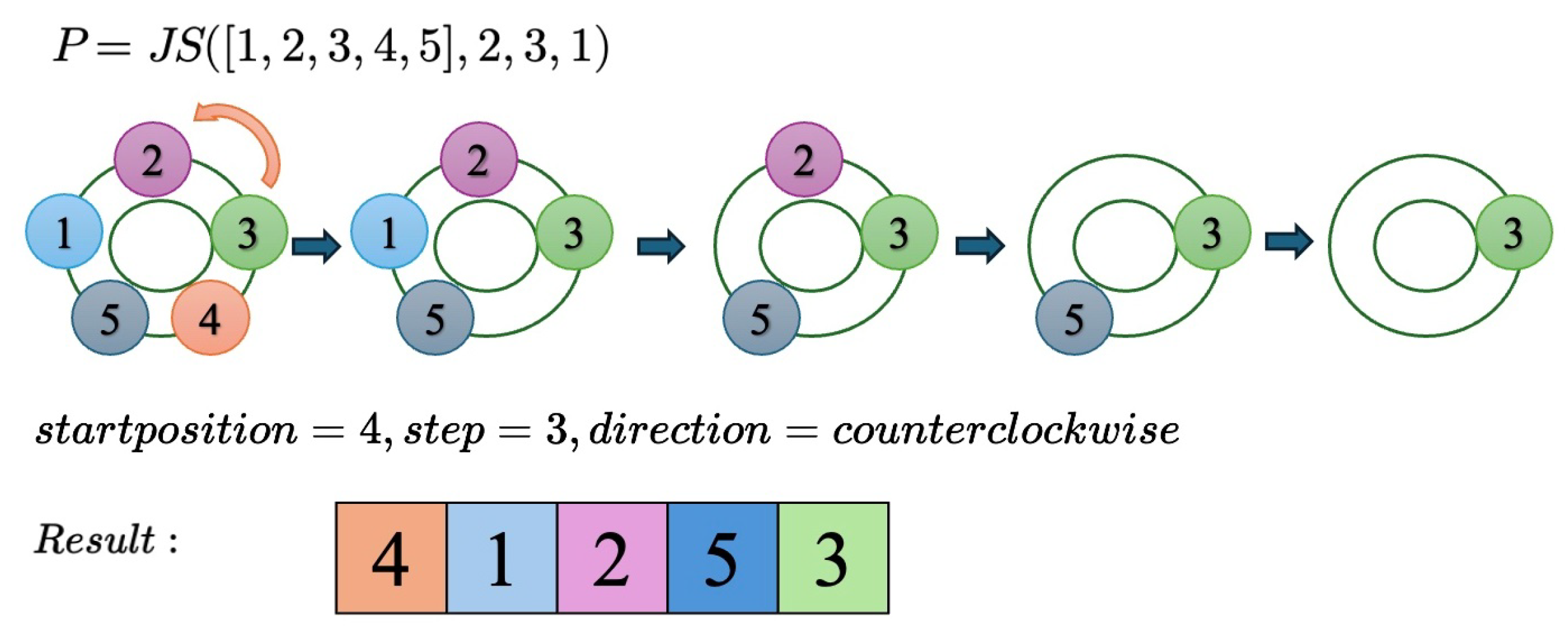
3.3.2. Overview of the Josephus Scrambling Principle
The core permutation logic is based on an extended form of the Josephus scrambling algorithm, which originates from the classical Josephus problem. In the classical variant, elements in a circular array are eliminated in a fixed step-size and direction. However, such static behavior results in limited permutation diversity. To overcome this, we define an extended Josephus function:
where
I is the original sequence,
denotes the starting index,
v is the step size, and
d indicates the traversal direction (odd
d: counterclockwise; even
d: clockwise). By dynamically deriving
from chaotic sequences, each scrambling operation becomes data-dependent and unpredictable, thereby enhancing security.
As an illustrative example, consider
. Starting from index
in a clockwise circular array, we eliminate every 3rd element in counterclockwise order: 4 → 1 → 2 → 5 → 3, yielding the permutation
. A visual demonstration is shown in
Figure 8.
3.3.3. Steps of Scrambling
The SLJSS algorithm integrates L-type decomposition, Josephus scrambling, and spiral reconstruction in a symmetric structure (forward and reverse). The following parameters derived from key sequences are used: , , as well as the plaintext image I. The design flow is as follows:
- Step 1:
By means of Equation (
12), the column scrambling of the plaintext image
I is performed according to the
sequence to achieve the initial randomization of the positions of the boundary and center pixel points to generate intermediate matrix
.
- Step 2:
As illustrated in the upper right corner of
Figure 9, the L-shaped stratification process starts from the top of the first column, traversing downward and then rightward to form the first L-shaped sequence (e.g., green region in
). The starting point then shifts one column to the right, and the process repeats to form the next L-shaped layer, until all elements are covered. This pattern resembles the shape of the letter “L”, hence the name L-shaped stratification.
The
array consisting of k-segment subsequences is first obtained by L-stratification of the
matrix. Then disarrangement is carried out for each subsequence
in
, where
determines the position of the beginning of each disarrangement,
determines the step size, and
determines the direction of each disarrangement, and finally, the
array containing k-segment disarrangement sequences is obtained. The calculation is shown in Equation (
13):
- Step 3:
Concatenate the k scrambled sequences in using , and reshape the resulting one-dimensional array into an matrix using one of four spiral reconstruction paths determined by . The four paths are defined as follows:
Pattern 1: Start from the top-left corner and traverse the matrix in a clockwise spiral.
Pattern 2: Start from the top-right corner and traverse the matrix in a counterclockwise spiral.
Pattern 3: Start from the bottom-left corner and traverse the matrix in a counterclockwise spiral.
Pattern 4: Start from the bottom-right corner and traverse the matrix in a clockwise spiral.
These diversified splicing patterns enhance the diffusion and randomness of pixel positions in the final matrix.
- Step 4:
Through Equation (
14), the
matrix is row transformed according to the
sequence, which further realizes the adjustment of the boundary and center pixel positions to obtain the
matrix.
- Step 5:
Like step 2, apply reverse L-type decomposition to , yielding sub-sequences . Each sub-sequence is scrambled using , producing array .
- Step 6:
Like step 3, assemble using , and apply spiral reconstruction (determined by ) to form the final scrambled matrix .
The complete SLJSS scrambling pipeline is summarized in Algorithm 3. A visualization of each step is shown in
Figure 9, using a
grayscale image. The resulting scrambled image demonstrates significant structural obfuscation across rows, columns, and diagonals.
Figure 9.
Explanation of the scrambling principle.
Figure 9.
Explanation of the scrambling principle.
3.4. Dynamic Codon-Based Multi-RNA Diffusion
To further enhance the sensitivity and complexity of encryption, this section introduces a lightweight yet highly effective diffusion mechanism based on RNA encoding, codon, and arithmetic. Unlike traditional methods that rely solely on numerical diffusion, the proposed strategy leverages bio-inspired structures to achieve high diffusion in a reversible manner.
| Algorithm 3: Scrambling Process |
![Symmetry 17 01255 i001 Symmetry 17 01255 i001]() |
3.4.1. Design Background and Motivation
The core idea stems from the intrinsic diversity and combinatorial complexity of RNA sequences. RNA bases—A, C, G, and U—allow for compact quaternary encoding of pixel values, while codon structures (triplets of bases) offer a naturally classified replacement framework. Compared with conventional byte-level arithmetic, the RNA-based approach enables flexible base-level diffusion with biologically inspired substitution logic.
From a design standpoint, the codon substitution step draws on the diversity of amino acid categories, allowing for local transformation within the same semantic group, thus ensuring both randomness and reversibility. After extensive testing, the chosen amino acid classification scheme showed superior diffusion performance compared to alternative groupings. In the subsequent RNA arithmetic phase, five types of operations—addition, subtraction, XOR, multiplication, and customized random operations—are employed. These operations are designed not only for reversibility but also for output diversity. Through careful experimentation, the final operation set and their sequences were optimized to achieve maximum encryption strength while minimizing computational overhead.
3.4.2. Overview of the RNA Encryption Principle
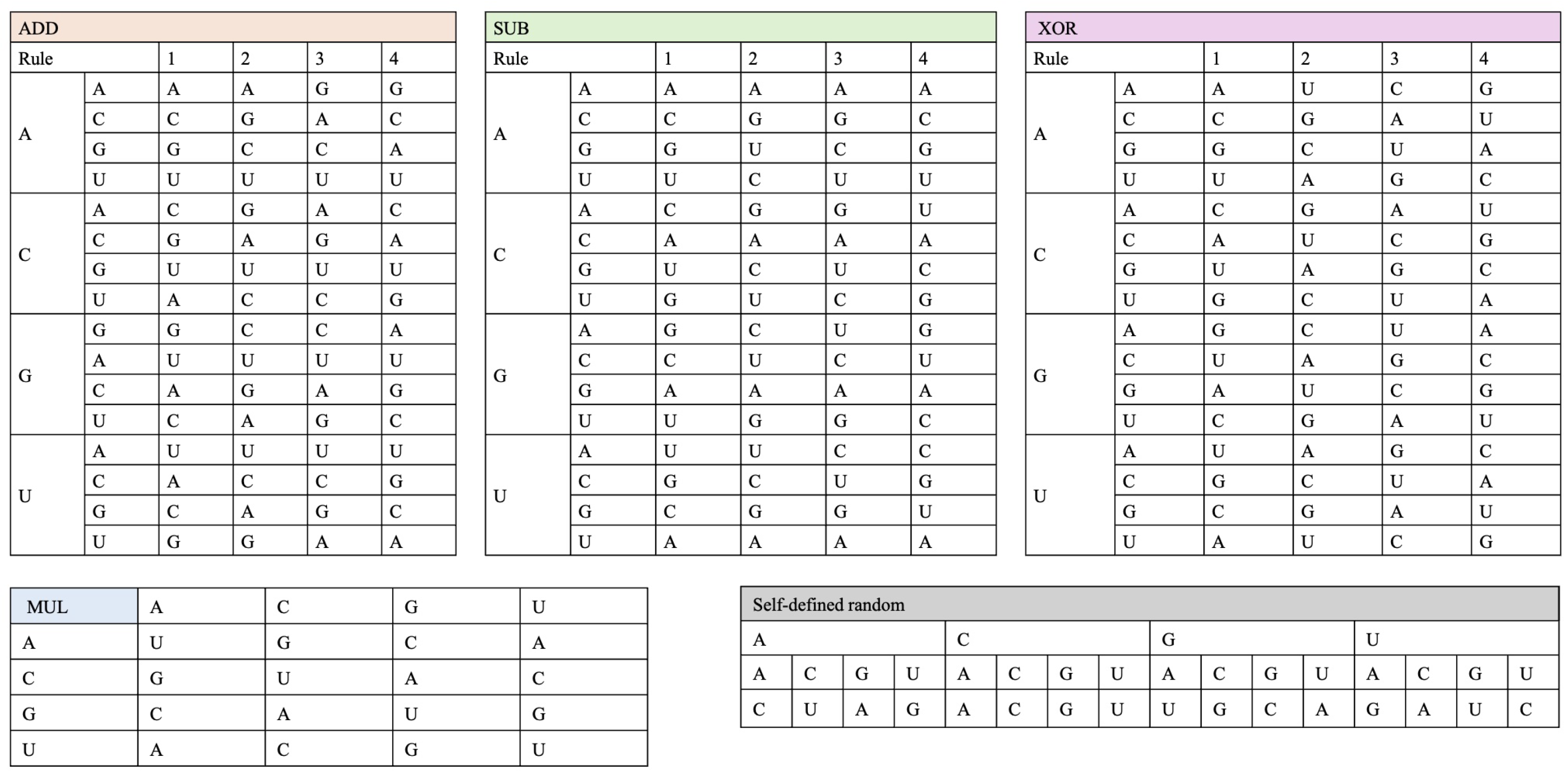
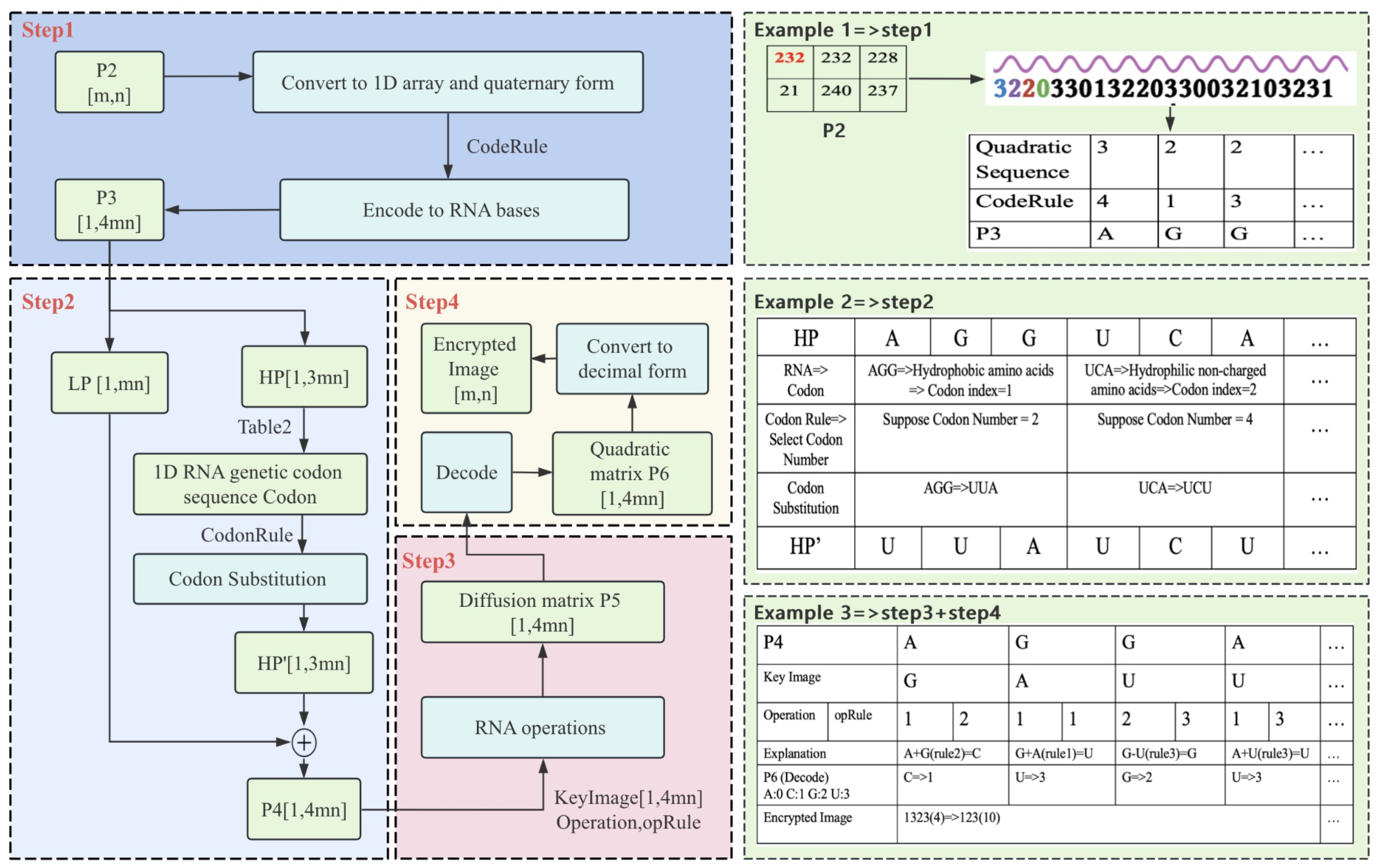
In our algorithm, grayscale pixel values are first converted from decimal to quaternary format and then encoded into RNA base sequences using one of eight encoding rules, as outlined in
Table 1. For example, a pixel value of 220 in decimal corresponds to 3130 in quaternary. Assuming that the encryption rules are 0-A, 1-C, 2-G, and 3-U, the encryption result is UCUA.
Among the RNA types, mRNA (messenger RNA) is relevant here, as every three consecutive bases form a codon, which maps to specific amino acids during protein synthesis [
37,
38]. Theoretically, there are
combinations of three neighboring bases, i.e., corresponding to 64 codons. Meanwhile, according to [
45], these 64 kinds of codons can correspond six kinds of amino acids, as shown in
Table 2. In our codon substitution strategy, each codon in the sequence is first identified by category and then randomly replaced with another codon from the same category to enhance local diffusion.
To reinforce pixel diffusion, the substituted RNA sequences undergo base-level arithmetic. Five operations are defined: addition, subtraction, XOR, multiplication, and a custom randomized operation. These operate under quaternary arithmetic rules and depend on the selected encoding. For instance, when base A (encoded as 00) and C (10) are added, the result varies depending on the encoding rule—demonstrating rule-sensitive behavior and enhancing key sensitivity.
Due to overlap across rule outputs, four distinct rule sets were finalized for addition, subtraction, XOR, and one for multiplication. The custom operation was manually defined to improve base diversity and eliminate bias toward any single nucleotide. All operations are designed to be reversible to ensure lossless decryption.
Figure 10 shows the encryption and decryption implementations of custom randomized computation, in which under the encryption rule, base1 represents the base from the encrypted image, base2 represents the base with which the RNA operation is performed, and Result is the result of the operation; under the decryption rule, base1 represents the base from the ciphertext image, and base2 is the same as that used in the ciphertext rule, and Result represents base1 in the ciphertext rule, e.g., A encrypts with A to get C, and C decrypts with A to get A. A complete list of the five computation rules is in
Figure 11.
3.4.3. Steps of Diffusion
Scrambling completes the rearrangement of pixel positions in the image; after that, we will apply diffusion operation to the disordered image to change the pixel values of different pixels to realize the effect of diffusing the small changes in the plaintext to the whole ciphertext. In this section, we will use the computed from the key sequence.
- Step 1:
Flatten the scrambled matrix into a 1-D array, convert each pixel from decimal to quaternary, and encode it into a corresponding RNA base using . This yields a 1-D RNA base sequence of length .
- Step 2:
Divide
into two parts:
and
, as shown in Equation (
15). Codons are formed from every three bases in
, which are then categorized using
Table 2 and converted to the RNA genetic codon sequence consisting of codon category indexes. Based on
, a replacement codon is randomly selected within the same category using Equation (
16). The updated sequence
is then concatenated with
to produce the full modified RNA base sequence
. For example, one codon composed of three neighboring amino acids in
is GAA; then it corresponds to negatively charged amino acids, and the genetic codon sequence corresponds to its index of 4. There are four kinds of codons (GAA, GAC, GAG, and GAU) under this kind of amino acids, and the new codon will be obtained by the CodonRule using the Equation (
16), assuming that the select codon number obtained is 2, then GAC will be used to replace GAA.
- Step 3:
The RNA bases of
will perform RNA operations by one-to-one correspondence with the RNA sequence
generated by the chaotic system, and the
determines the type of operation (addition, subtraction, XOR, multiplication, or customized random operation). Since there are different results when A, C, G, and U represent different values in each operation, the values of A, C, G, and U are determined by the opRule sequence. In short, each base in
is calculated with the corresponding base in the
according to the set operation type and the value to get a new value, which results in the diffusion matrix P5, as shown in the following equation.
- Step 4:
In order to simplify the arithmetic process, the diffusion matrix is decoded into the quadratic matrix according to A-0, C-1, G-2, and U-3, and finally the quadratic image is converted into decimal form to obtain the final encrypted image .
Algorithm 4 introduces the key steps in the diffusion.
can realize the interconversion of quadrature numbers and RNA sequences,
,
can realize the interconversion of decimal numbers and quadrature numbers, and the calculation results of
are all in accordance with the arithmetic rules shown in
Figure 11.
Figure 12 visualizes the flow information of the diffusion module.
| Algorithm 4: Diffusion Process Based on RNA Operations |
![Symmetry 17 01255 i002 Symmetry 17 01255 i002]() |
3.5. Decryption
The proposed encryption algorithm is fully reversible, and the decryption process involves executing the inverse of each encryption step to recover the original plaintext image.
- Step 1:
Input the encrypted image and key, and calculate the initial values for the chaotic system used in encryption.
- Step 2:
Regenerate the chaotic sequences by performing the same iterations described in
Section 3.2. This includes the generation of all key sequences used in scrambling and diffusion.
- Step 3:
RNA encoding, inverse of multiple base operations, codon inverse substitution, and RNA dynamic decoding are performed sequentially on the to eliminate the effect of RNA-level diffusion and to obtain the image matrix without diffusion effect.
- Step 4:
The same spiral sequence deconstruction, inverse Josephs scrambling, and L-type decomposition are sequentially performed on according to the symmetric structure, and the plaintext image I without scrambling effect can be obtained.
After completing the above steps, the original plaintext image is fully restored without any loss. This demonstrates the proposed algorithm’s reversibility and robustness.
5. Conclusions
This paper presents a secure and efficient grayscale medical image encryption algorithm tailored to the characteristics of medical images, such as large data volume, high inter-pixel correlation, and strong structural redundancy.
The proposed framework integrates a high-dimensional 5-D memristor chaotic system with two specialized modules: Symmetric L-type Josephus Spiral Scrambling (SLJSS) and Dynamic Codon-based Multi-RNA Diffusion (DCMRD). The chaotic system, based on the HP memristor model, generates highly sensitive and ergodic sequences, as confirmed by bifurcation diagrams, Lyapunov exponents, and histogram analysis. SLJSS ensures global and diagonal pixel decorrelation through hierarchical L-shaped partitioning and symmetric spiral scrambling, while DCMRD enhances diffusion through codon substitution and multi-rule RNA operations.
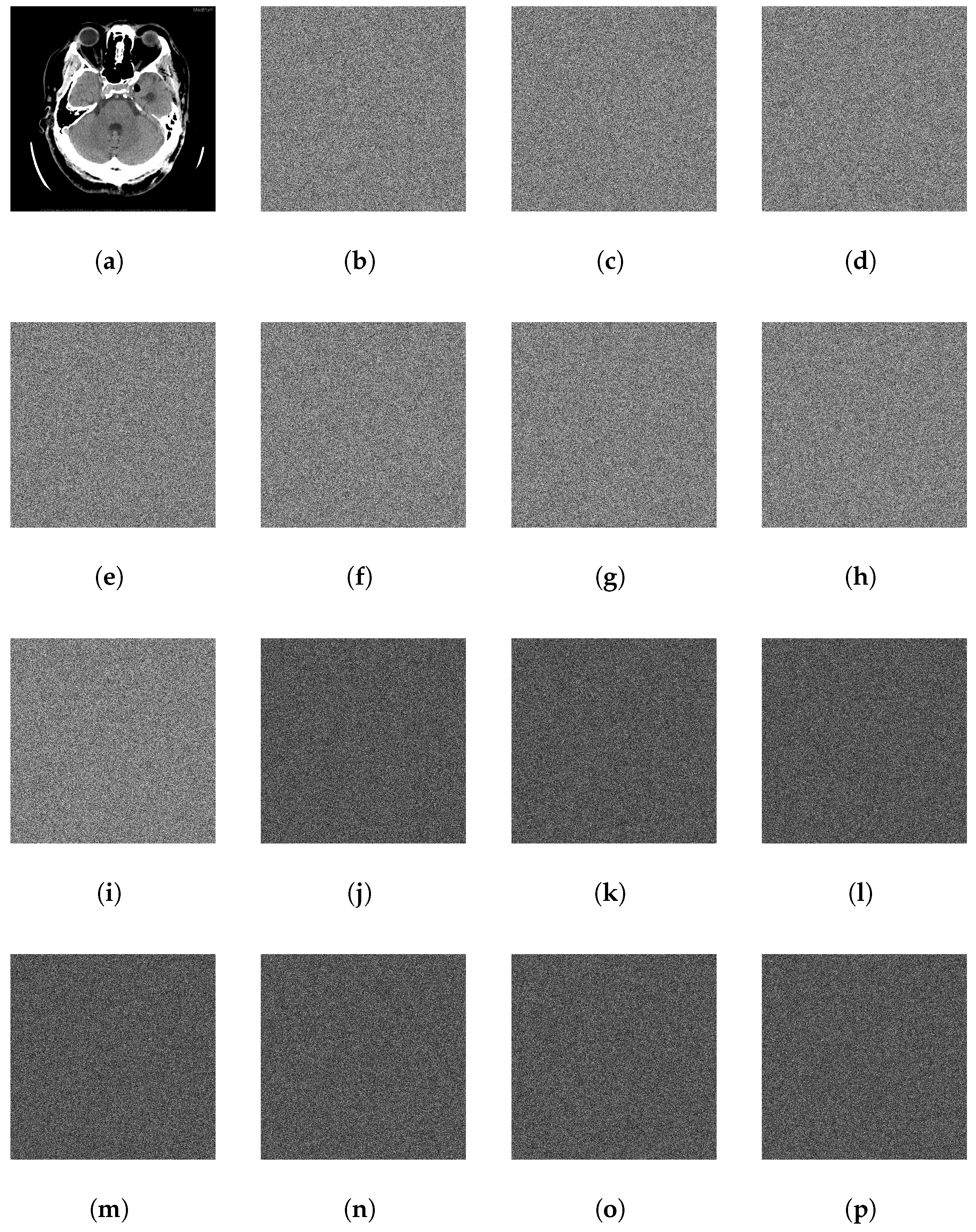
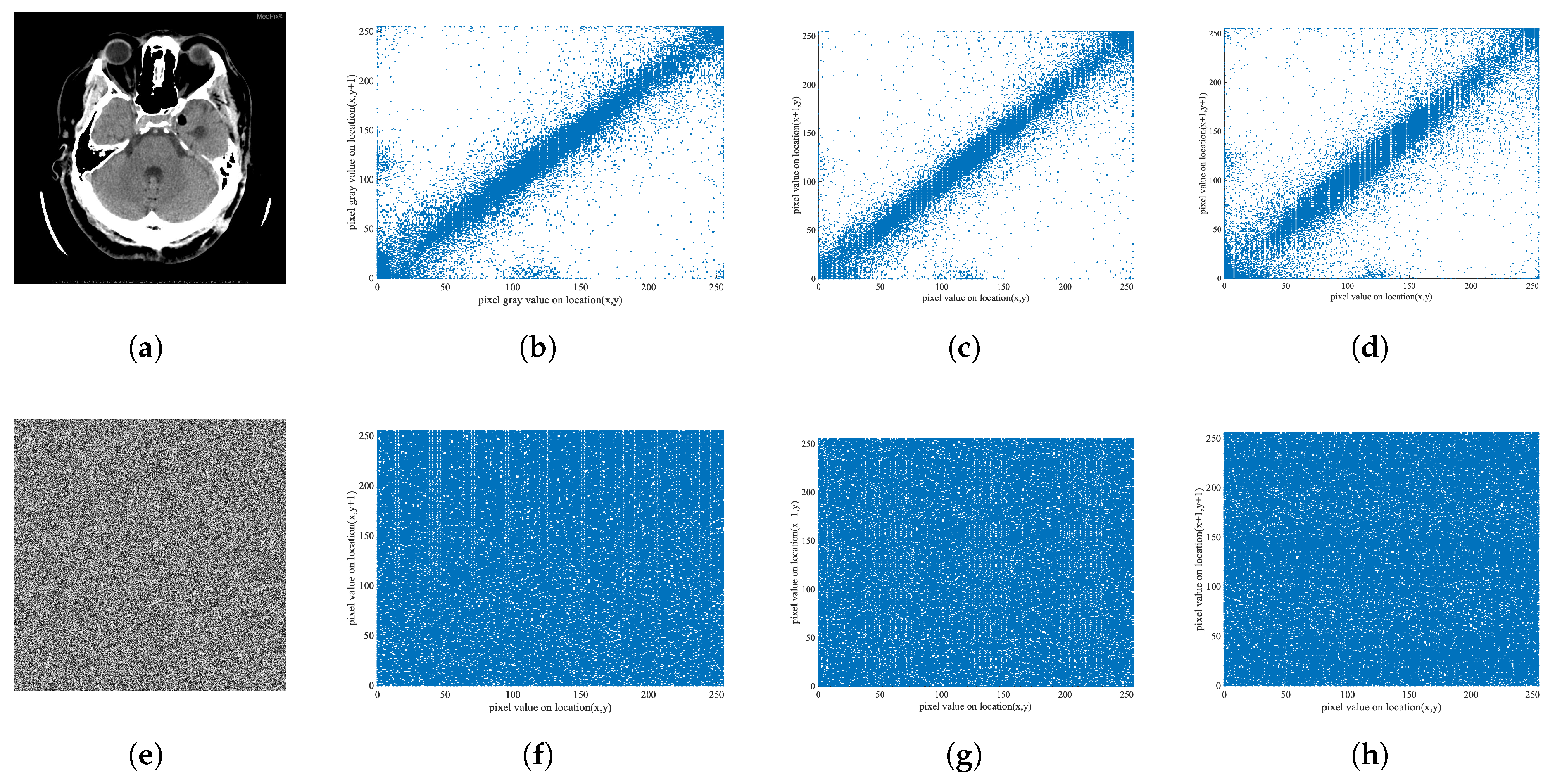
Simulation results demonstrate that the proposed method achieves near-ideal entropy (e.g., 7.9992), low pixel correlation (e.g., 0.0043), strong robustness (NPCR: 99.62%, UACI: 33.45%), and fast processing time (e.g., 0.0964 s encryption for 256 × 256 images). The algorithm exhibits strong resistance to statistical and differential attacks and shows stable performance across medical and natural image datasets, validating its general applicability.
In conclusion, the proposed method offers a lightweight, high-security solution for medical image protection, with potential applications in telemedicine, image archiving, and privacy-preserving diagnostics. Future work will explore hardware acceleration, adaptation to 3-D or multi-modal medical images, and integration with compression–encryption and federated learning frameworks.