An Image Encryption Method Based on a Two-Dimensional Cross-Coupled Chaotic System
Abstract
1. Introduction
- (1)
- A new 2D cross-coupled chaotic system is proposed, capable of generating multiple chaotic maps. Specifically, a hyperchaotic system was developed by combining Chebyshev mapping, the Fuch map, sine mapping, and cosine mapping.
- (2)
- The analysis of bifurcation diagrams, phase diagrams, Lyapunov exponents, and permutation entropy reveals that the proposed system exhibits a larger key space, enhanced ergodicity, and increased unpredictability, leading to more complex chaotic dynamics.
- (3)
- An efficient image encryption scheme is introduced, which utilizes a chaotic matrix in conjunction with a Zigzag transformation for effective permutation and forward and reverse random multidirectional diffusion operations with symmetrical significance. The chaotic matrix-based permutation disrupts pixel positions by simultaneously scrambling both rows and columns in a random order. The symmetric forward and backward random multi-directional diffusion is achieved by conducting two rounds of random diffusion in multiple directions.
- (4)
- A comprehensive evaluation of the encryption algorithm’s performance is conducted, covering aspects such as key space, histogram analysis, variance, entropy, and correlation coefficient.
2. Definition of 2D-CFCM
3. Chaotic Property Evaluation of 2D-CFCM
3.1. Phase Diagram
3.2. Bifurcation Diagram
3.3. Lyapunov Exponent
3.4. Complexity
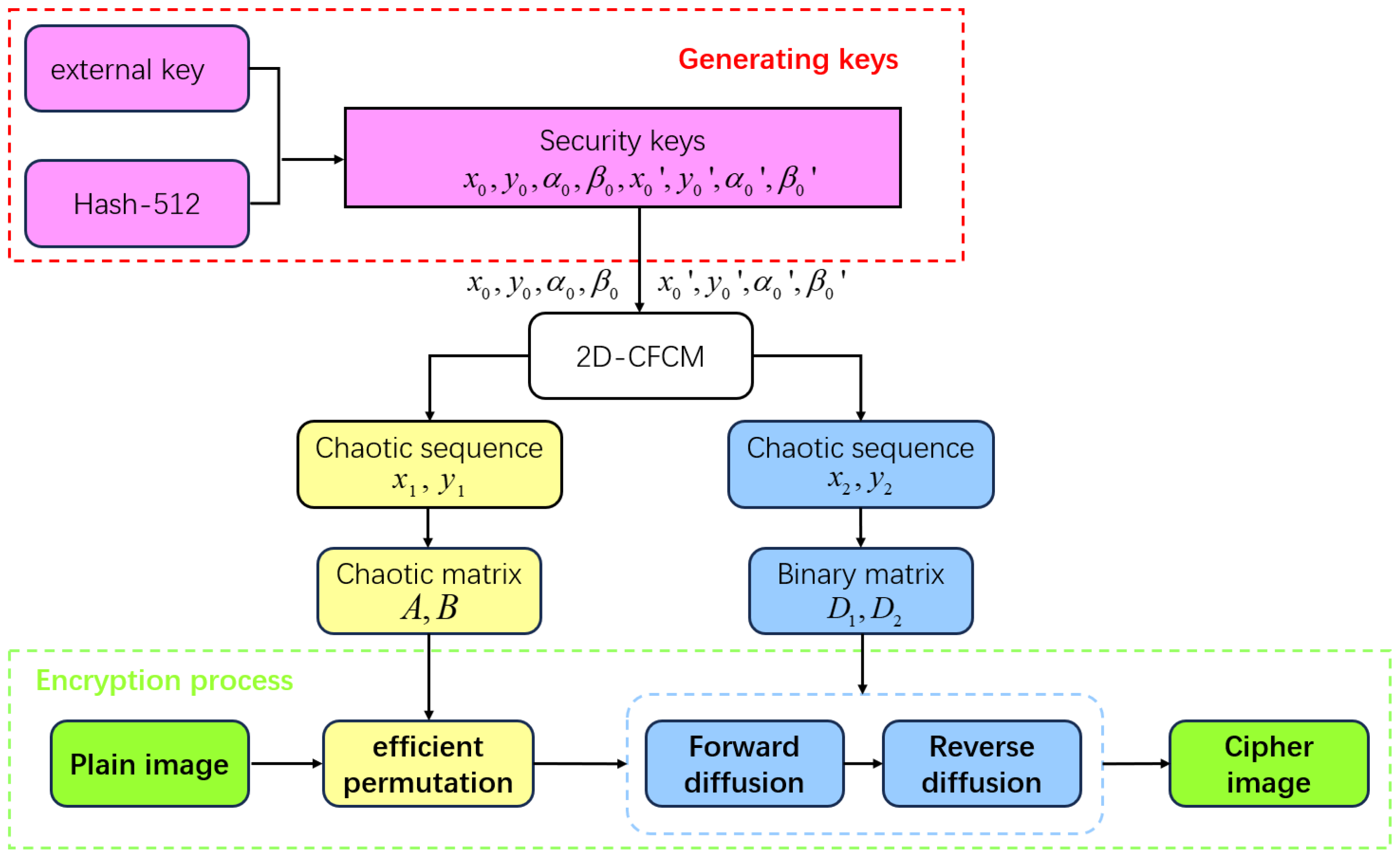
4. Image Encryption Method
4.1. Generating Keys
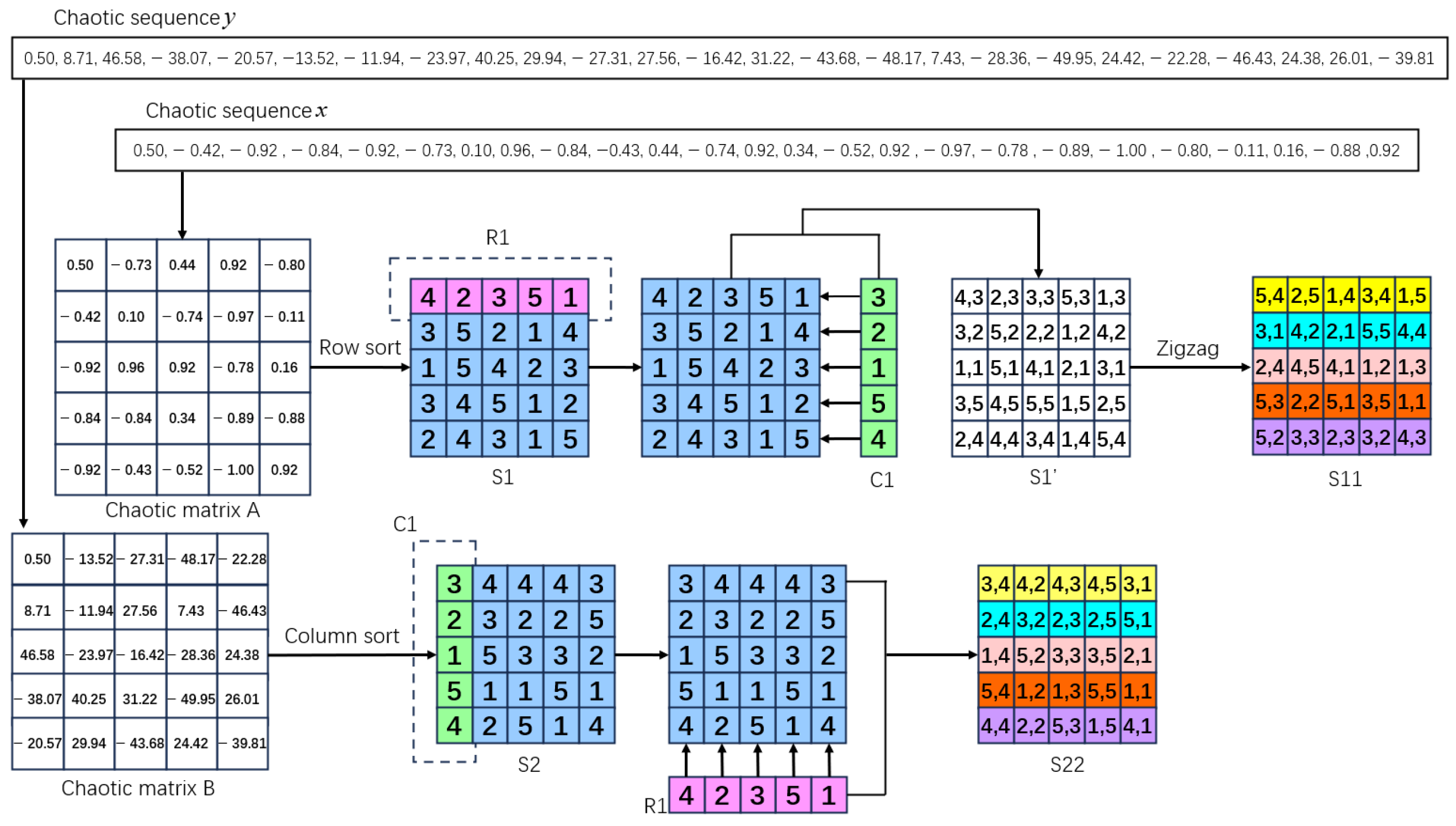
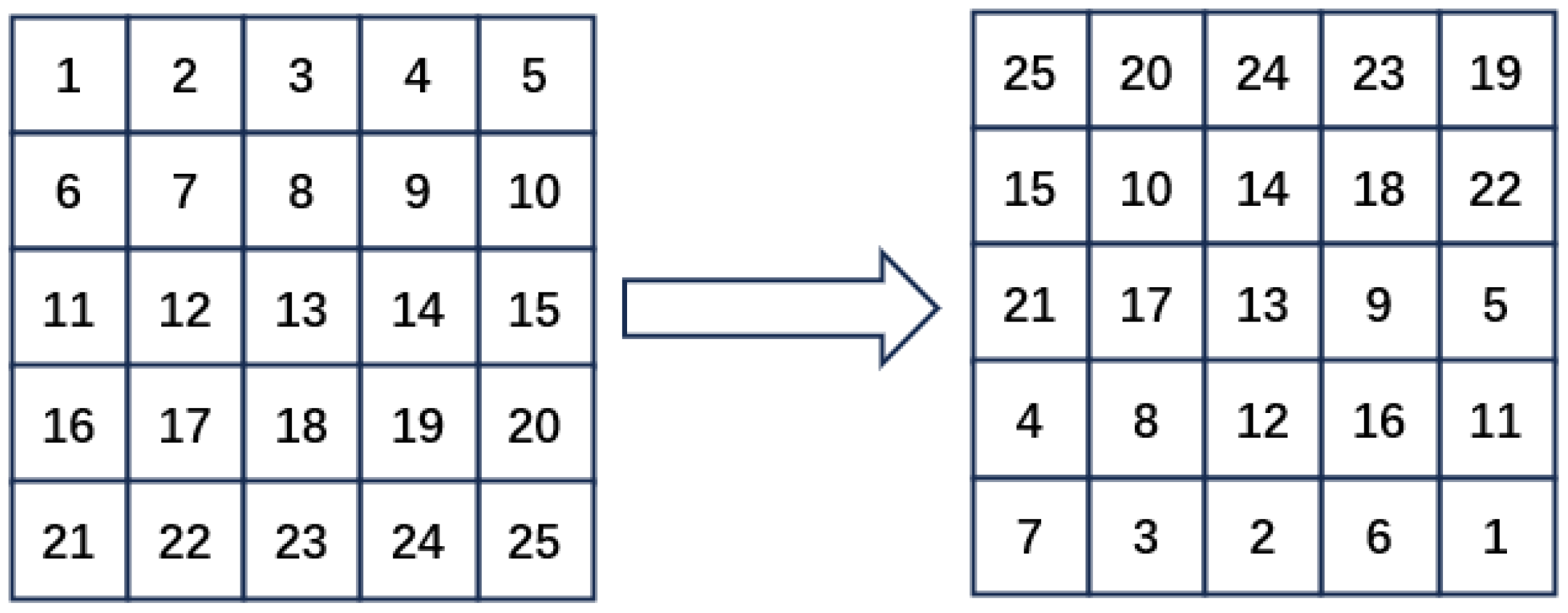
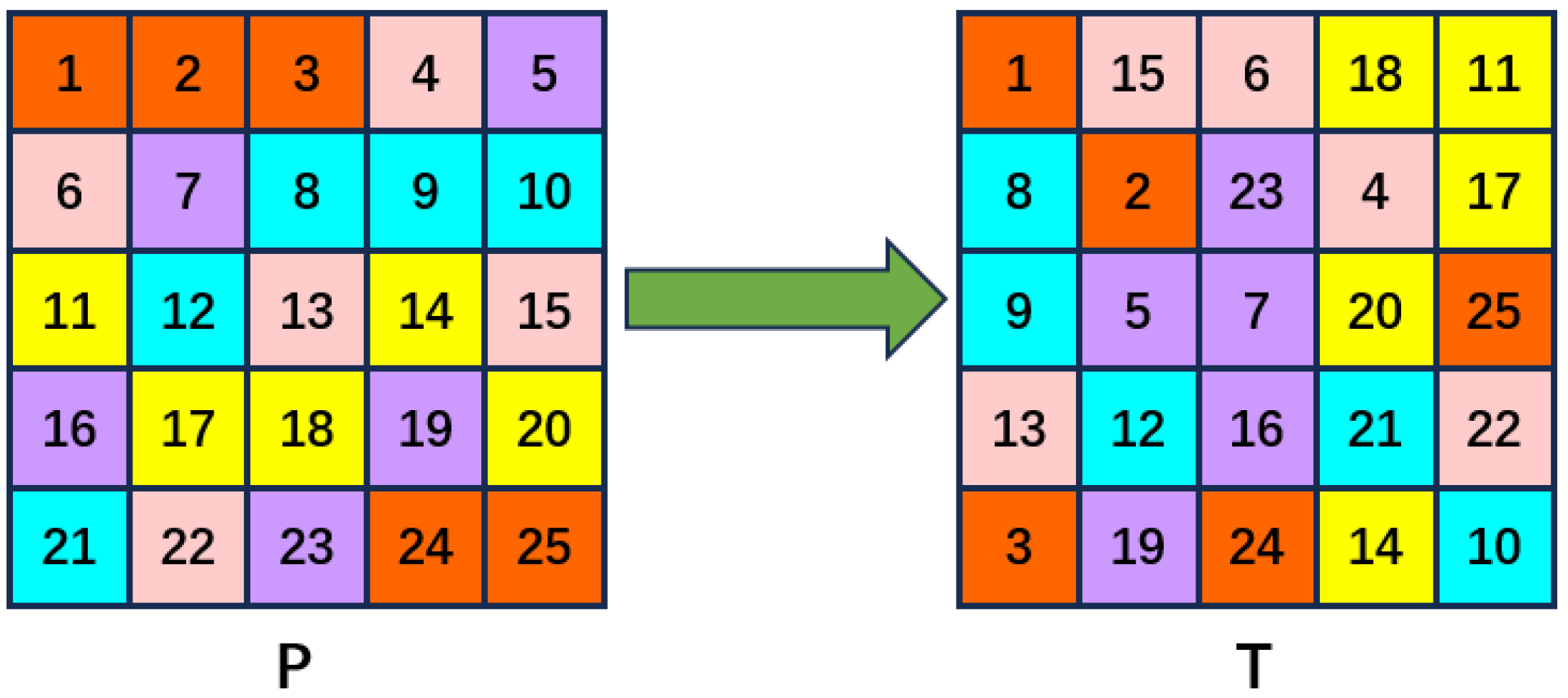
4.2. Chaotic Efficient Permutation
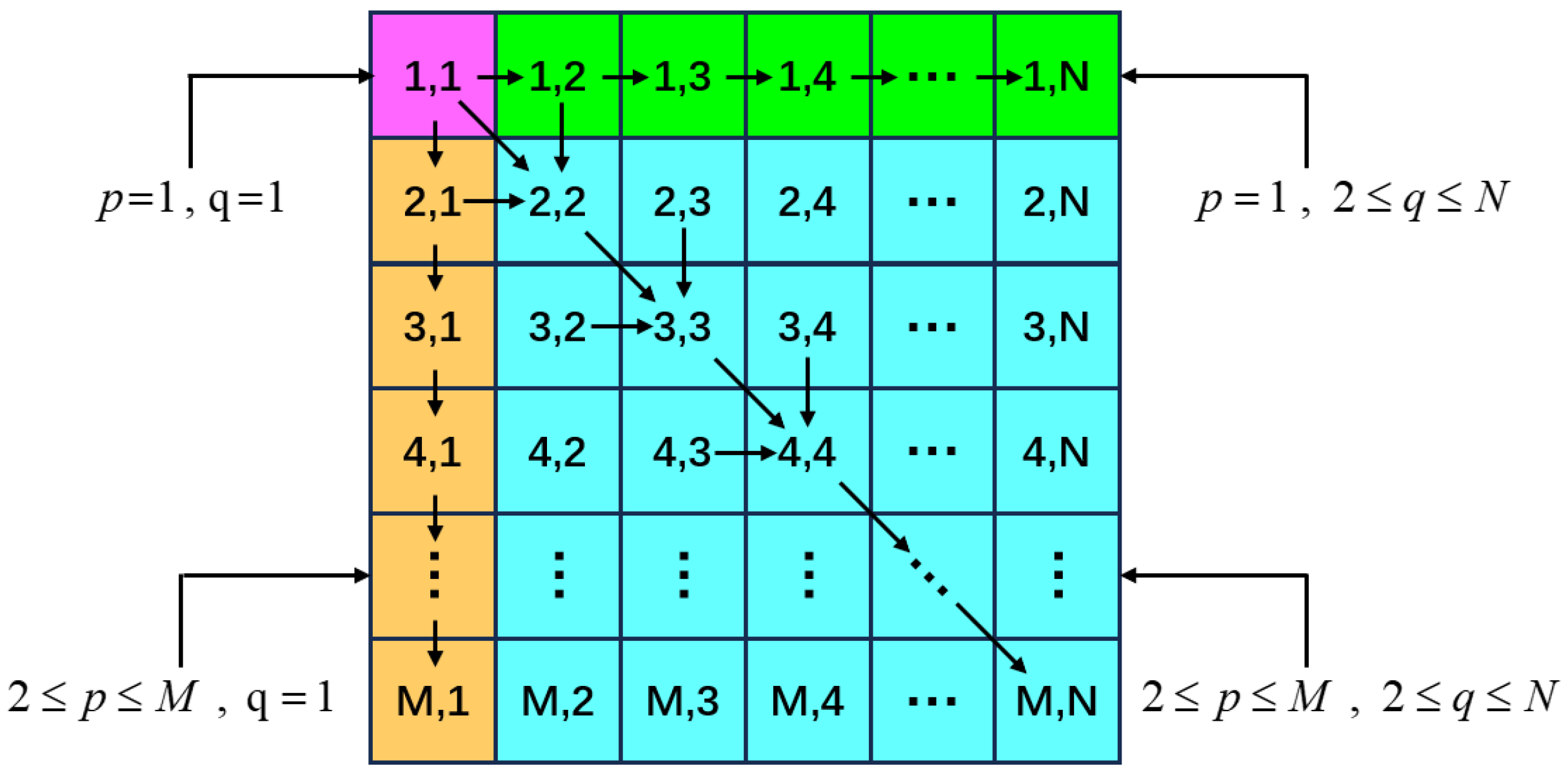
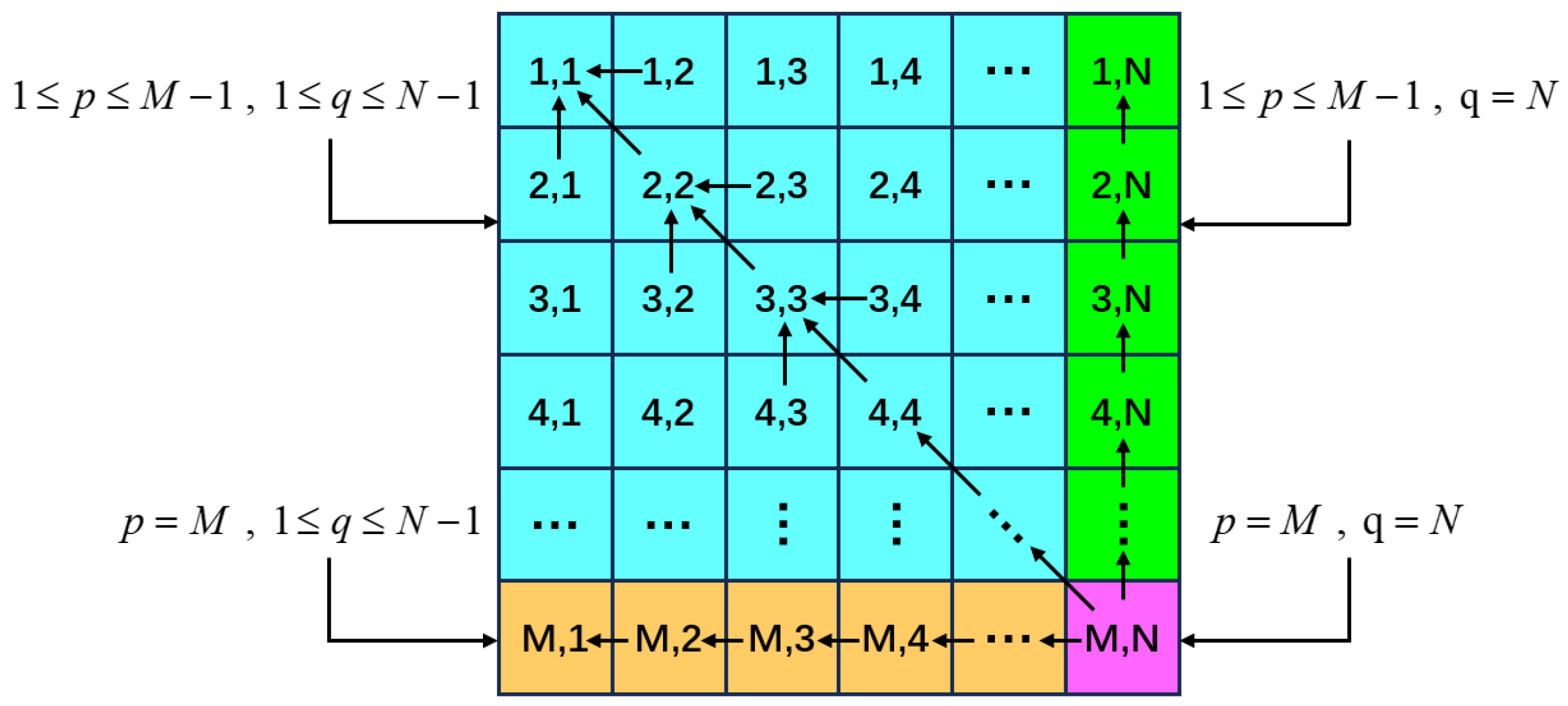
4.3. Forward and Reverse Random Multidirectional Diffusion
5. Simulation Results and Performance Analysis
5.1. Key Space Analysis
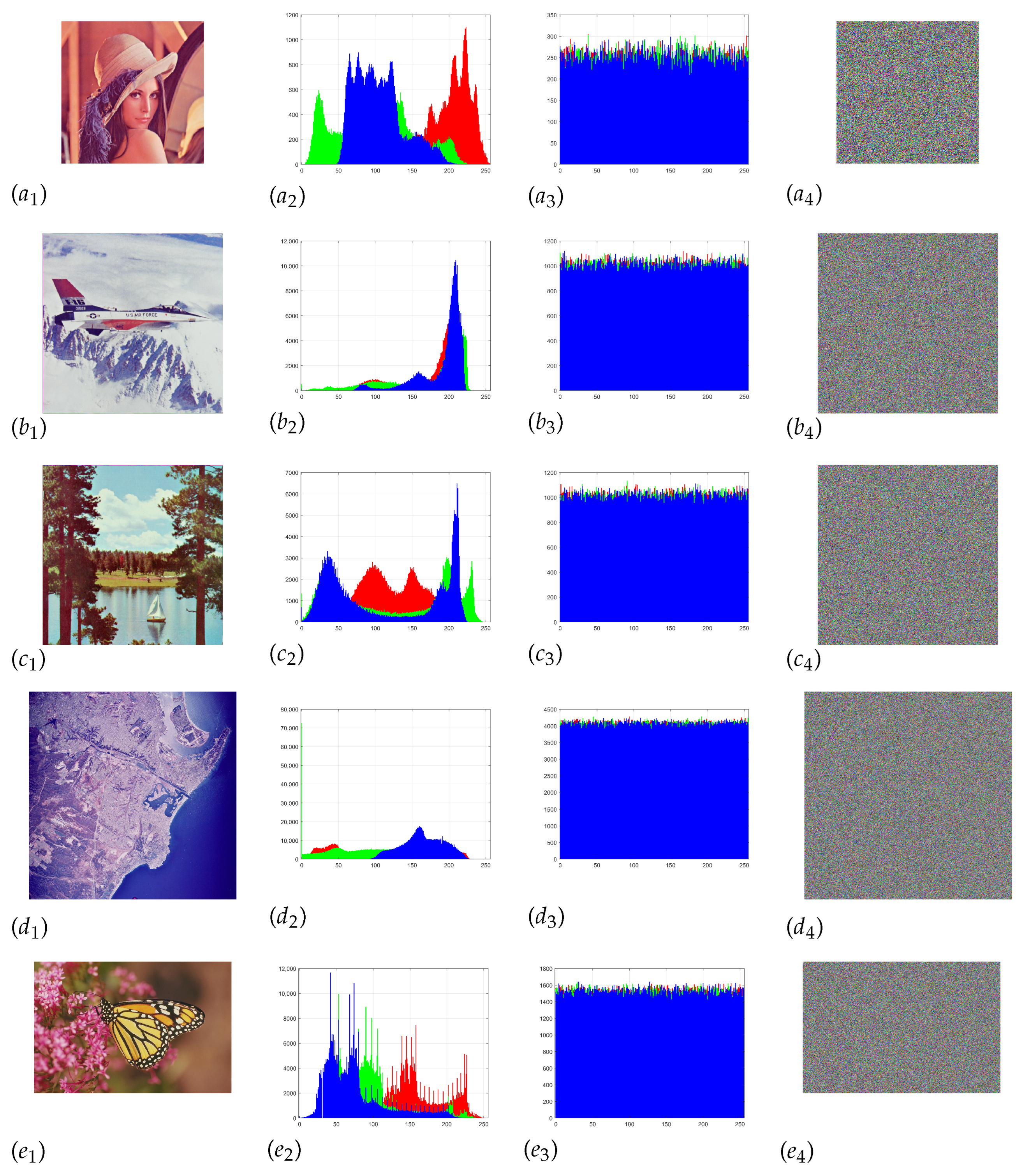
5.2. Histogram Analysis
5.3. Variance and Chi-Square Analysis
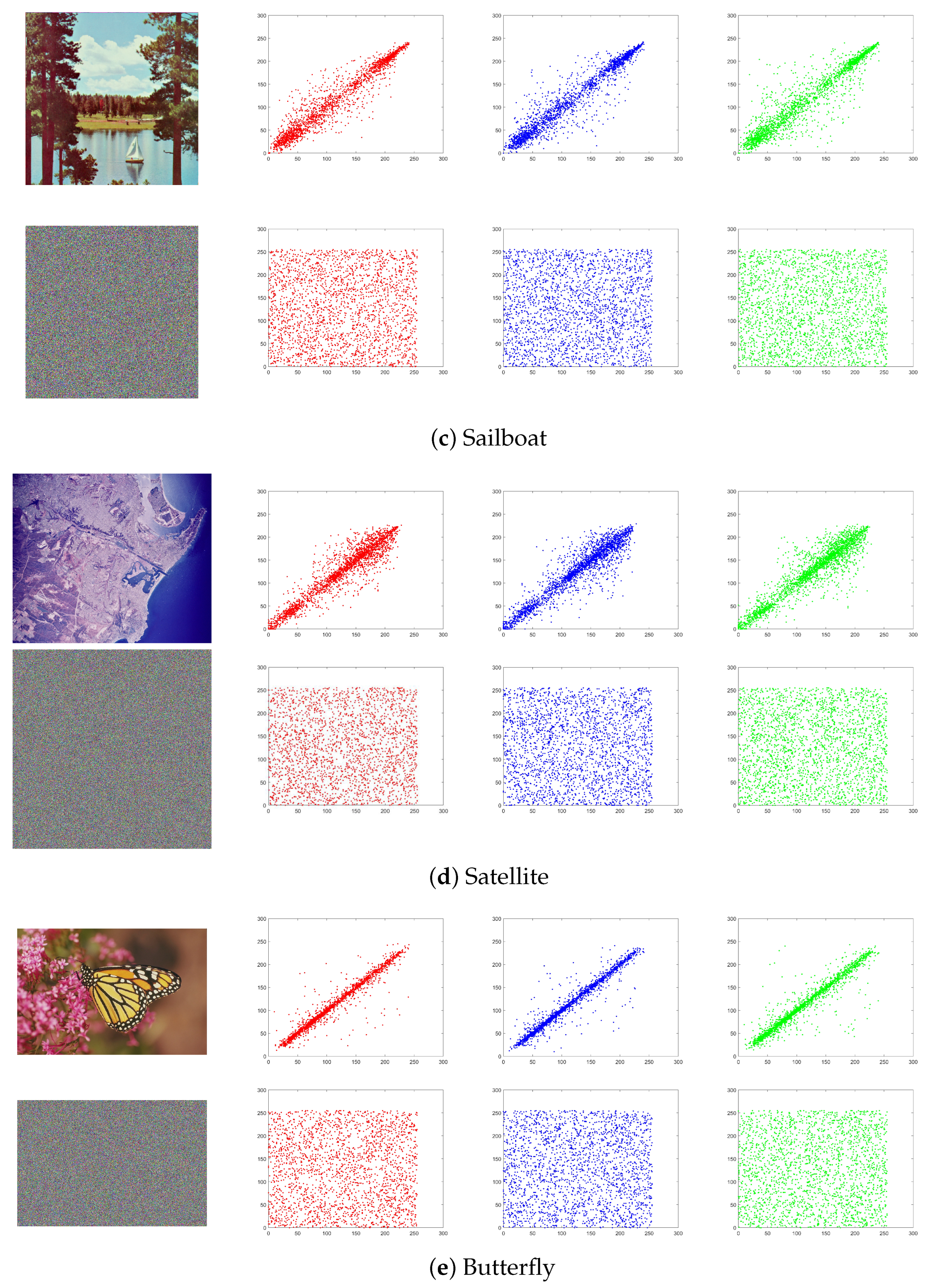
5.4. Correlation Analysis
5.5. Information Entropy Analysis
5.6. Differential Attack Analysis
6. Conclusions and Outlook
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Khan, M.; Jamal, S.S.; Hazzazi, M.M. An efficient image encryption scheme based on double affine substitution box and chaotic system. Integration 2021, 81, 108–122. [Google Scholar] [CrossRef]
- Wang, X.; Chen, S.; Zhang, Y. A chaotic image encryption algorithm based on random dynamic mixing. Opt. Laser Technol. 2021, 138, 106837. [Google Scholar] [CrossRef]
- Zhou, S.; Wang, X.; Zhang, Y. Novel image encryption scheme based on chaotic signals with finite-precision error. Inf. Sci. 2023, 621, 782–798. [Google Scholar] [CrossRef]
- Golalipour, K. A novel permutation-diffusion technique for image encryption based on the imperialist competitive algorithm. Multimed. Tools Appl. 2023, 82, 725–746. [Google Scholar] [CrossRef]
- Coppersmith, D. The Data Encryption Standard (DES) and its strength against attacks. IBM J. Res. Dev. 1994, 38, 243–250. [Google Scholar] [CrossRef]
- Toughi, S.; Fathi, M.H.; Sekhavat, Y.A. An image encryption scheme based on elliptic curve pseudo random and advanced encryption system. Signal Process. 2017, 141, 217–227. [Google Scholar] [CrossRef]
- Gong, L.; Qiu, K.; Deng, C. An optical image compression and encryption scheme based on compressive sensing and RSA algorithm. Opt. Lasers Eng. 2019, 121, 169–180. [Google Scholar] [CrossRef]
- Wu, X.; Kurths, J.; Kan, H. A robust and lossless DNA encryption scheme for color images. Multimed. Tools Appl. 2018, 77, 12349–12376. [Google Scholar] [CrossRef]
- Mahmud, M.; Lee, M.; Choi, J.Y. Evolutionary-based image encryption using RNA codons truth table. Opt. Laser Technol. 2020, 121, 105818. [Google Scholar] [CrossRef]
- Cun, Q.; Tong, X.; Wang, Z. A new chaotic image encryption algorithm based on dynamic DNA coding and RNA computing. Vis. Comput. 2023, 39, 6589–6608. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, K.; Zhang, J. Integrating fractional-order Hopfield neural network with differentiated encryption: Achieving high-performance privacy protection for medical images. Fractal Fract. 2025, 9, 426. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, S.; Su, D. Dynamic analysis and implementation of FPGA for a new 4D fractional-order memristive Hopfield neural network. Fractal Fract. 2025, 9, 115. [Google Scholar] [CrossRef]
- Darani, A.Y.; Yengejeh, Y.K.; Pakmanesh, H. Image encryption algorithm based on a new 3D chaotic system using cellular automata. Chaos Solit. Fractals 2024, 179, 114396. [Google Scholar] [CrossRef]
- Zhang, D.; Liao, X.; Yang, B. A fast and efficient approach to color-image encryption based on compressive sensing and fractional Fourier transform. Multimed. Tools Appl. 2018, 77, 2191–2208. [Google Scholar] [CrossRef]
- Gan, Z.; Xiong, B.; Pang, Z. A visually secure image encryption scheme using newly designed 1D sinusoidal chaotic map and P-tensor product compressive sensing. Nonlinear Dyn. 2024, 112, 2979–3001. [Google Scholar] [CrossRef]
- Wang, C.; Song, L. An image encryption scheme based on chaotic system and compressed sensing for multiple application scenarios. Inf. Sci. 2023, 642, 119166. [Google Scholar] [CrossRef]
- Zhang, Z.; Tang, J.; Ni, H. Image adaptive encryption algorithm using a novel 2D chaotic system. Nonlinear Dyn. 2023, 111, 10629–10652. [Google Scholar] [CrossRef]
- Luo, Y.; Lin, J.; Liu, J. A robust image encryption algorithm based on Chua’s circuit and compressive sensing. Signal Process. 2019, 161, 227–247. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Chen, Y. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Luo, J.; Xu, X.; Ding, Y. Application of a memristor-based oscillator to weak signal detection. Eur. Phys. J. Plus 2018, 133, 239. [Google Scholar] [CrossRef]
- Yang, F.; Mou, J.; Ma, C. Dynamic analysis of an improper fractional-order laser chaotic system and its image encryption application. Opt. Lasers Eng. 2020, 129, 106031. [Google Scholar] [CrossRef]
- Lu, T.; Anwar, W.; Tang, X. Distributional chaoticity of C0-semigroup on a Frechet space. Symmetry 2019, 11, 345. [Google Scholar] [CrossRef]
- Mohamadi, H.E.; Lahlou, L.; Kara, N. A versatile chaotic cryptosystem with a novel substitution-permutation scheme for internet-of-drones photography. Nonlinear Dyn. 2024, 112, 4977–5012. [Google Scholar] [CrossRef]
- Akraam, M.; Rashid, T.; Zafar, S. A novel and secure image encryption scheme based on two-dimensional logistic and Arnold cat map. Clust. Comput. 2024, 27, 2029–2048. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.M. 2D sine logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Zhu, H.; Zhao, Y.; Song, Y. 2D logistic-modulated-sine-coupling-logistic chaotic map for image encryption. IEEE Access 2019, 7, 14081–14098. [Google Scholar] [CrossRef]
- Feng, W.; Qin, Z.; Zhang, J. Cryptanalysis and improvement of the image encryption scheme based on Feistel network and dynamic DNA encoding. IEEE Access 2021, 9, 145459–145470. [Google Scholar] [CrossRef]
- Feng, W.; He, Y.; Li, H. Cryptanalysis and improvement of the image encryption scheme based on 2D logistic-adjusted-sine map. IEEE Access 2019, 7, 12584–12597. [Google Scholar] [CrossRef]
- Wang, X.; Guan, N. 2D sine-logistic-tent-coupling map for image encryption. J. Ambient Intell. Humaniz. Comput. 2023, 14, 13399–13419. [Google Scholar] [CrossRef]
- Yang, Z.; Cao, Y.; Ji, Y. Securing color image by using bit-level modified integer nonlinear coupled chaos model in Fresnel diffraction domains. Opt. Lasers Eng. 2022, 152, 106969. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Yi, S. Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Inf. Sci. 2021, 546, 1063–1083. [Google Scholar] [CrossRef]
- Huang, X.; Dong, Y.; Zhu, H. Visually asymmetric image encryption algorithm based on SHA-3 and compressive sensing by embedding encrypted image. Alex. Eng. J. 2022, 61, 7637–7647. [Google Scholar] [CrossRef]
- Hua, Z.; Yi, S.; Zhou, Y. Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process. 2018, 144, 134–144. [Google Scholar] [CrossRef]
- Herbadji, D.; Derouiche, N.; Belmeguenai, A. A new colour image encryption approach using a combination of two 1D chaotic map. Int. J. Electron. Secur. Digit. Forensics 2020, 12, 337–356. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, J.Y.; Zhang, L.Y. Performance of the 2D coupled map lattice model and its application in image encryption. Complexity 2022, 2022, 5193618. [Google Scholar] [CrossRef]
- Zhang, Z.; Tang, J.; Zhang, F. Color image encryption using 2D sine-cosine coupling map. IEEE Access 2022, 10, 67669–67685. [Google Scholar] [CrossRef]
- Xuejing, K.; Zihui, G. A new color image encryption scheme based on DNA encoding and spatiotemporal chaotic system. Signal Process. 2020, 80, 115670. [Google Scholar] [CrossRef]
- Rezaei, B.; Ghanbari, H.; Enayatifar, R. An image encryption approach using tuned Henon chaotic map and evolutionary algorithm. Nonlinear Dyn. 2023, 111, 9629–9647. [Google Scholar] [CrossRef]
- Li, L.; Luo, Y.; Qiu, S. Image encryption using chaotic map and cellular automata. Multimed. Tools Appl. 2022, 81, 40755–40773. [Google Scholar] [CrossRef]
- Demirtaş, M. A new RGB color image encryption scheme based on cross-channel pixel and bit scrambling using chaos. Optik 2022, 265, 169430. [Google Scholar] [CrossRef]
- Zhang, Y.Q.; He, Y.; Li, P. A new color image encryption scheme based on 2DNLCML system and genetic operations. Opt. Lasers Eng. 2020, 128, 106040. [Google Scholar] [CrossRef]
- Erkan, U.; Toktas, A.; Enginoğlu, S. An image encryption scheme based on chaotic logarithmic map and key generation using deep CNN. Multimed. Tools Appl. 2022, 81, 7365–7391. [Google Scholar] [CrossRef]
- Li, L. A novel chaotic map application in image encryption algorithm. Expert Syst. Appl. 2024, 252, 124316. [Google Scholar] [CrossRef]
- Zhang, X.; Zhao, Z.; Wang, J. Chaotic image encryption based on circular substitution box and key stream buffer. Signal Process. 2014, 29, 902–913. [Google Scholar] [CrossRef]
- Dong, Y.; Zhao, G.; Ma, Y. A novel image encryption scheme based on pseudo-random coupled map lattices with hybrid elementary cellular automata. Inf. Sci. 2022, 593, 121–154. [Google Scholar] [CrossRef]
- Ahmad, I.; Shin, S. A novel hybrid image encryption compression scheme by combining chaos theory and number theory. Signal Process. 2021, 98, 116418. [Google Scholar] [CrossRef]
- Yildirim, M. Optical color image encryption scheme with a novel DNA encoding algorithm based on a chaotic circuit. Chaos Solit. Fractals 2022, 155, 111631. [Google Scholar] [CrossRef]
- Liu, X.; Tong, X.; Wang, Z. Uniform non-degeneracy discrete chaotic system and its application in image encryption. Nonlinear Dyn. 2022, 108, 653–682. [Google Scholar] [CrossRef]

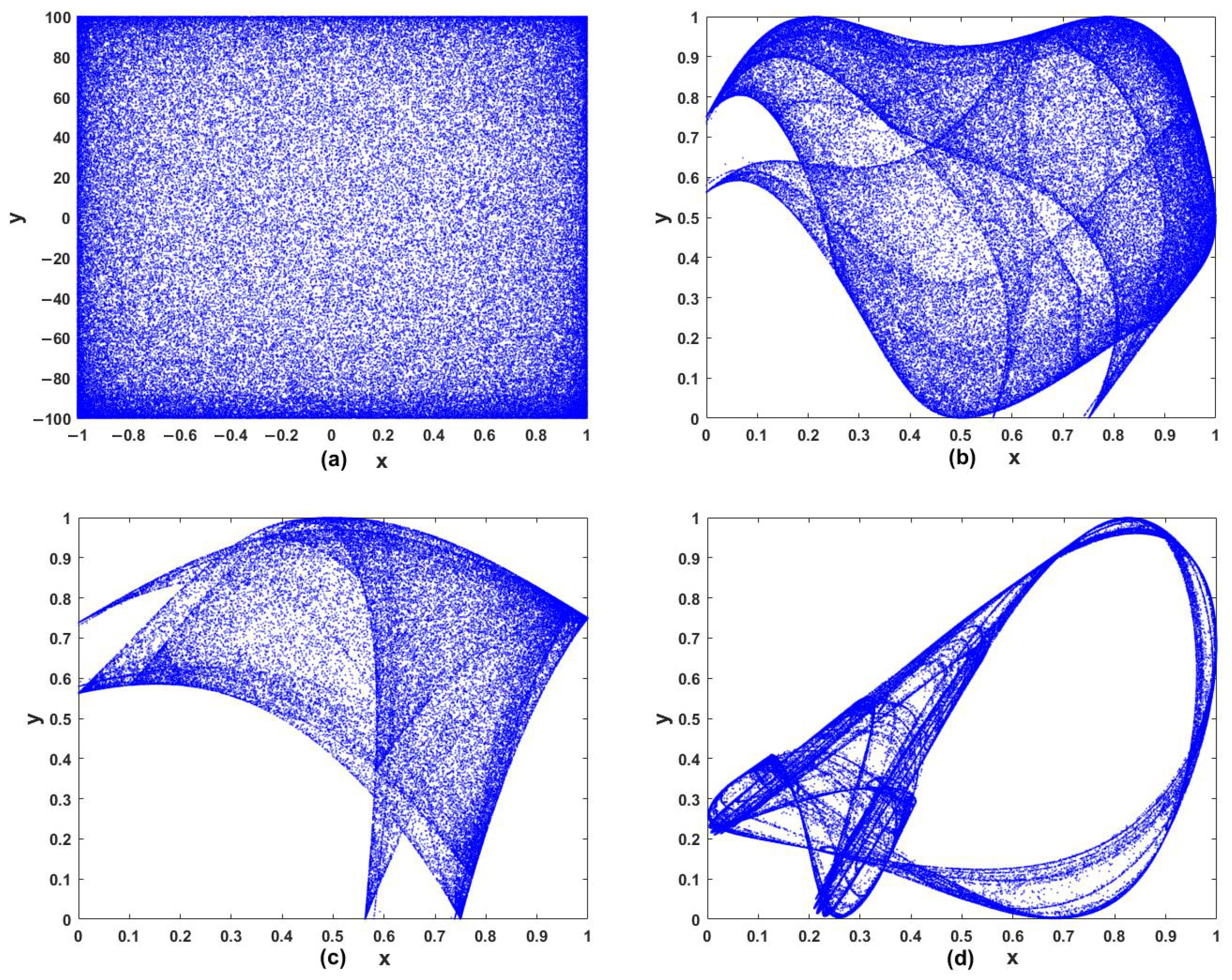



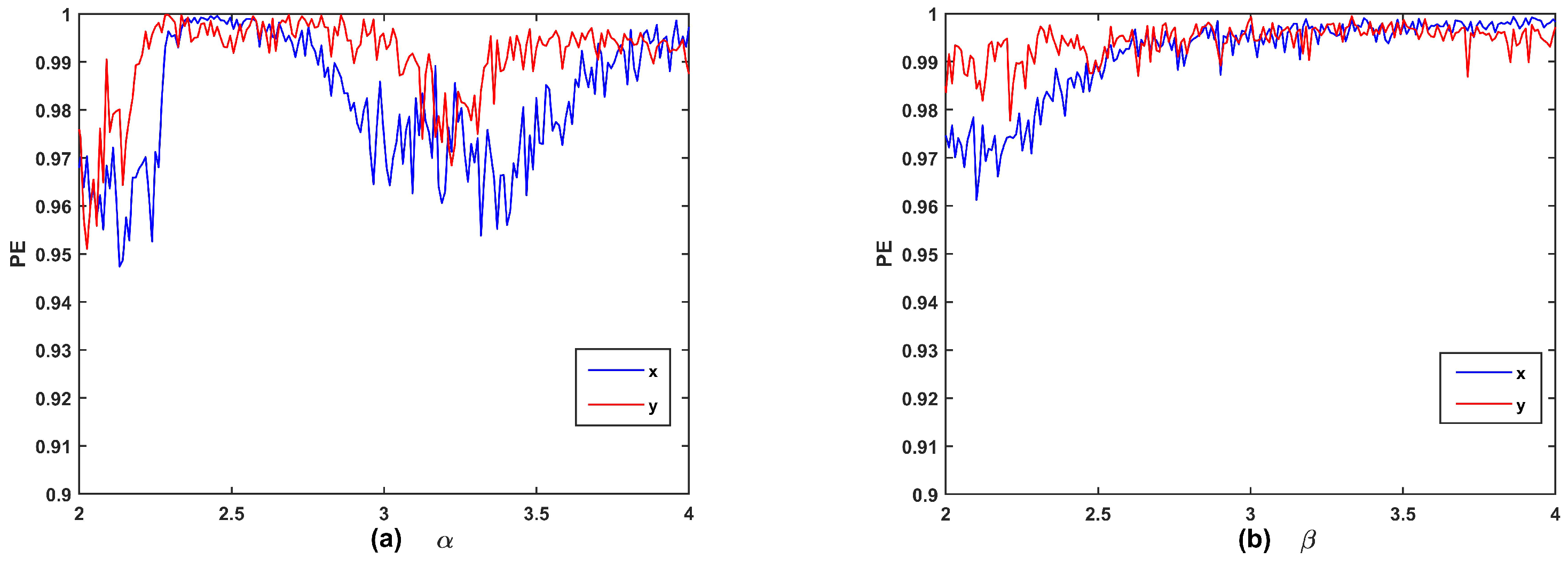



| Scheme | Key Space | Scheme | Key Space | Scheme | Key Space |
|---|---|---|---|---|---|
| Ref. [36] | Ref. [37] | Ref. [38] | |||
| Ref. [39] | Ref. [40] | Ref. [41] | |||
| Ref. [42] | Ref. [43] | Proposed | > |
| Images | P/E | Size | Variance | Chi-Square |
|---|---|---|---|---|
| Lena | Plain | 256 256 | 1.9329 | 6.4430 |
| Encrypted | 256 256 | 666.9725 | 221.4557 | |
| Aircraft | Plain | 512 512 | 2.7718 | 2.3098 |
| Encrypted | 512 512 | 2714.8 | 225.3457 | |
| Sailboat | Plain | 512 512 | 2.6723 | 2.2269 |
| Encrypted | 512 512 | 2955.1 | 245.2995 | |
| Satellite | Plain | 1024 1024 | 6.8016 | 1.4170 |
| Encrypted | 1024 1024 | 11,434 | 237.2786 | |
| Butterfly | Plain | 768 512 | 1.4687 | 8.1595 |
| Encrypted | 768 512 | 4145.3 | 229.3971 |
| Images | Channels | Plaintext Image | Ciphertext Image | ||||
|---|---|---|---|---|---|---|---|
| H | V | D | H | V | D | ||
| Lena | R | 0.9403 | 0.9742 | 0.9255 | 0.0127 | −0.0252 | 0.0022 |
| G | 0.9500 | 0.9669 | 0.9279 | −0.0238 | 0.0003 | 0.0066 | |
| B | 0.9431 | 0.9634 | 0.9203 | −0.0080 | −0.0130 | −0.0020 | |
| Aircraft | R | 0.9686 | 0.9733 | 0.9447 | −0.0107 | 0.0033 | 0.0008 |
| G | 0.9646 | 0.9722 | 0.9458 | 0.0392 | −0.0076 | 0.0086 | |
| B | 0.9591 | 0.9570 | 0.9274 | −0.0369 | 0.0096 | −0.0092 | |
| Sailboat | R | 0.9632 | 0.9594 | 0.9483 | −0.0113 | 0.0069 | 0.0001 |
| G | 0.9716 | 0.9689 | 0.9586 | 0.0295 | −0.0111 | −0.0093 | |
| B | 0.9748 | 0.9719 | 0.9560 | −0.0006 | −0.0015 | 0.0044 | |
| Satellite | R | 0.9560 | 0.9192 | 0.9027 | 0.0004 | −0.0102 | 0.0248 |
| G | 0.9208 | 0.9242 | 0.9038 | −0.0001 | −0.0005 | 0.0256 | |
| B | 0.8902 | 0.9128 | 0.8902 | −0.0228 | 0.0034 | 0.0017 | |
| Butterfly | R | 0.9721 | 0.9612 | 0.9535 | 0.0207 | −0.0263 | 0.0023 |
| G | 0.9411 | 0.9478 | 0.9091 | 0.0061 | 0.0193 | −0.0093 | |
| B | 0.9590 | 0.9470 | 0.9455 | −0.0062 | 0.0030 | 0.0311 | |
| Images | Size | Plaintext Image | Ciphertext Image | ||||
|---|---|---|---|---|---|---|---|
| R | G | B | R | G | B | ||
| Lena | 256 × 256 × 3 | 7.2353 | 7.5683 | 6.9176 | 7.9974 | 7.9976 | 7.9972 |
| Aircraft | 512 × 512 × 3 | 6.7178 | 6.799 | 6.2138 | 7.9994 | 7.9993 | 7.9994 |
| Sailboat | 512 × 512 × 3 | 7.3124 | 7.6461 | 7.2137 | 7.9993 | 7.9994 | 7.9993 |
| Satellite | 1024 × 1024 × 3 | 7.7229 | 7.5289 | 6.8318 | 7.9998 | 7.9998 | 7.9998 |
| Butterfly | 768 × 512 × 3 | 7.4042 | 7.0843 | 6.9801 | 7.9996 | 7.9995 | 7.9996 |
| Ref. [34] | 512 × 512 × 3 | – | – | – | 7.9971 | 7.9975 | 7.9974 |
| Ref. [36] | 512 × 512 × 3 | – | – | – | 7.9912 | 7.9913 | 7.9914 |
| Ref. [38] | 512 × 512 × 3 | – | – | – | 7.9974 | 7.9974 | 7.9974 |
| Images | NPCR(%) | UACI(%) | ||||
|---|---|---|---|---|---|---|
| R | G | B | R | G | B | |
| Lena | 99.6156 | 99.5965 | 99.5978 | 33.4829 | 33.4759 | 33.4573 |
| Aircraft | 99.6046 | 99.6107 | 99.6116 | 33.3912 | 33.4616 | 33.4250 |
| Sailboat | 99.5964 | 99.6064 | 99.6075 | 33.4997 | 33.4976 | 33.4578 |
| Satellite | 99.6076 | 99.5987 | 99.5989 | 33.4419 | 33.5068 | 33.5038 |
| Butterfly | 99.5921 | 99.6242 | 99.6056 | 33.4480 | 33.4497 | 33.4656 |
| Ref. [46] | 99.5461 | 99.7066 | 99.6070 | 35.9229 | 36.6366 | 36.2376 |
| Ref. [47] | 99.5925 | 99.6294 | 99.6140 | 33.4226 | 33.4344 | 33.4698 |
| Ref. [48] | 99.6048 | 99.6010 | 99.5987 | 33.4481 | 33.4886 | 33.5094 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.; Lu, T.; Yan, B. An Image Encryption Method Based on a Two-Dimensional Cross-Coupled Chaotic System. Symmetry 2025, 17, 1221. https://doi.org/10.3390/sym17081221
Chen C, Lu T, Yan B. An Image Encryption Method Based on a Two-Dimensional Cross-Coupled Chaotic System. Symmetry. 2025; 17(8):1221. https://doi.org/10.3390/sym17081221
Chicago/Turabian StyleChen, Caiwen, Tianxiu Lu, and Boxu Yan. 2025. "An Image Encryption Method Based on a Two-Dimensional Cross-Coupled Chaotic System" Symmetry 17, no. 8: 1221. https://doi.org/10.3390/sym17081221
APA StyleChen, C., Lu, T., & Yan, B. (2025). An Image Encryption Method Based on a Two-Dimensional Cross-Coupled Chaotic System. Symmetry, 17(8), 1221. https://doi.org/10.3390/sym17081221






