A Blockchain-Based Anti-Counterfeit and Traceable NBA Digital Trading Card Management System
Abstract
:1. Introduction
1.1. Background
1.2. Related Works
- (1)
- Distribution and member access—Distributed computing storage with the same rights and obligations for each node. The identity of members who join the block is controlled to ensure information security.
- (2)
- Integrity and non-tampering—The information data related to digital trading cards are signed by the ECDSA after the hash calculation before the transmission process, and the receiver verifies the signature and then stores it on the chain to solve the data security problem.
- (3)
- Transparency—The source, issuance, purchase, and ownership information of digital trading cards are stored on the chain, and the information on the chain is open and transparent to enhance trust among users and protect collectors’ rights. The proxy encryption ensures collectors’ secure and transparent access to digital trading cards.
- (4)
- Traceability—The history of the digital trading card information is traceable with time stamps and signature mechanisms, and all the information is non-repudiation.
- (5)
- Timeliness—The sale and sharing of digital trading cards is managed reasonably, and digital content is not permanently appropriated by imposing time limits on access certificates.
- (6)
- Resist attacks—Using timestamps, asymmetric encryption, and blockchain technology, our system can resist replay attacks, man-in-the-middle attacks, and witch attacks to build a secure digital trading card management platform.
2. Preliminary
2.1. Hyperledger Fabric
2.2. Smart Contract
2.3. Elliptic Curve Digital Signature Algorithm (ECDSA)
2.4. Proxy Re-Encryption
- (a)
- Definition of system parameters: Let a large prime number and multiplicative group generate , where and are public parameters.
- (b)
- Key generation: Licensee Alice chooses positive integers , at random as his keys. Then, the decryption key is sent to the licensee Bob via a secure transmission channel.
- (c)
- Authorized person encrypts plaintext: Set random number and calculate and to obtain ciphertext .
- (d)
- Re-encryption key generation: If Bob is authorized by Alice’s message, then Alice needs to send ciphertext and proxy key to the proxy.
- (e)
- Re-encryption process: After receiving and proxy key , the agent re-encrypts the ciphertext to and sends the re-encrypted ciphertext to Bob.
- (f)
- Licensee decrypts the ciphertext: Licensee Bob computes using the decryption key and obtains the plaintext using .
3. Proposed Scheme
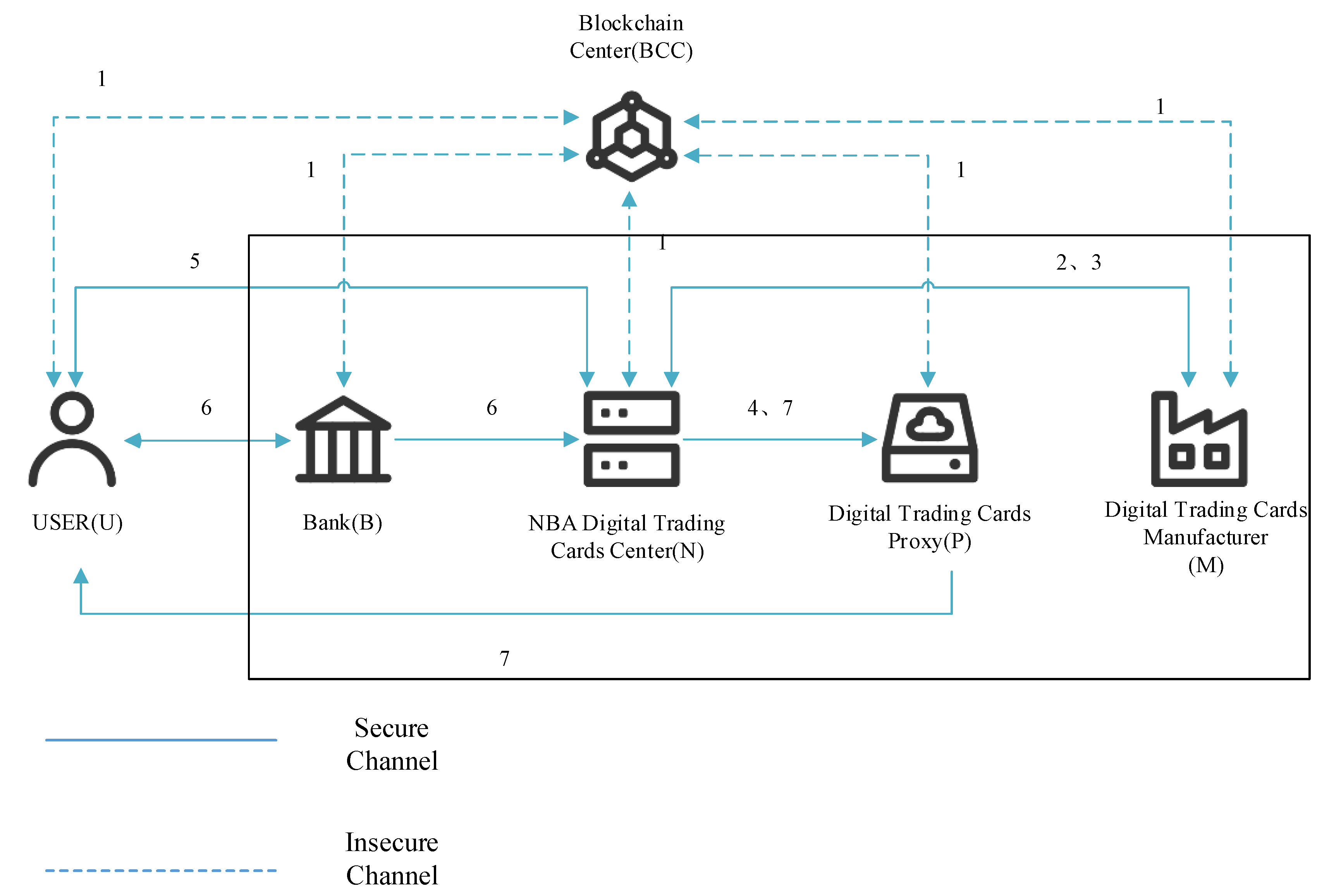
3.1. System Architecture
- (1)
- Blockchain Center (BCC): The Blockchain Center registers each role in the system architecture and issues identity certificates as well as public and private keys to each role.
- (2)
- NBA Digital Trading Cards Center (N): N is the NBA’s cloud platform, responsible for the provision of video information and authorization of video manufacturing, review and issuance of digital trading cards, and review of user requests to determine whether to allow access to digital content resources.
- (3)
- Digital Trading Cards Manufacturer (M): A digital trading card manufacturer must obtain authorization from the NBA Center, as well as genuine video, and manufacture digital content related to digital trading cards.
- (4)
- Digital Trading Cards Proxy (P): The Digital Trading Cards Proxy is the NBA’s agent, which is the cloud platform for storing digital trading cards. After the user’s identity is verified, the proxy is actually responsible for authorizing the user in the cloud (sending re-encrypted ciphertext).
- (5)
- User (U): Users are collectors of digital trading cards. When a user wants to access the NBA’s digital trading cards, the user should pay a fee to the NBA.
- (6)
- Bank (B): The bank issues a payment certificate to the user.
- Step 1
- Registration Phase—This step is the registration phase for each role in the system; all users, digital trading card manufacturers, NBA digital trading card centers, digital trading card agents, and banks need to register with the blockchain center to obtain the public and private keys provided by the blockchain center.
- Step 2
- Manufacturing Authorization Phase—When a digital trading card manufacturer wants to manufacture a digital trading card for sale, they need to obtain an authorization code from the NBA digital trading card center for the manufacture and an authentic NBA game video.
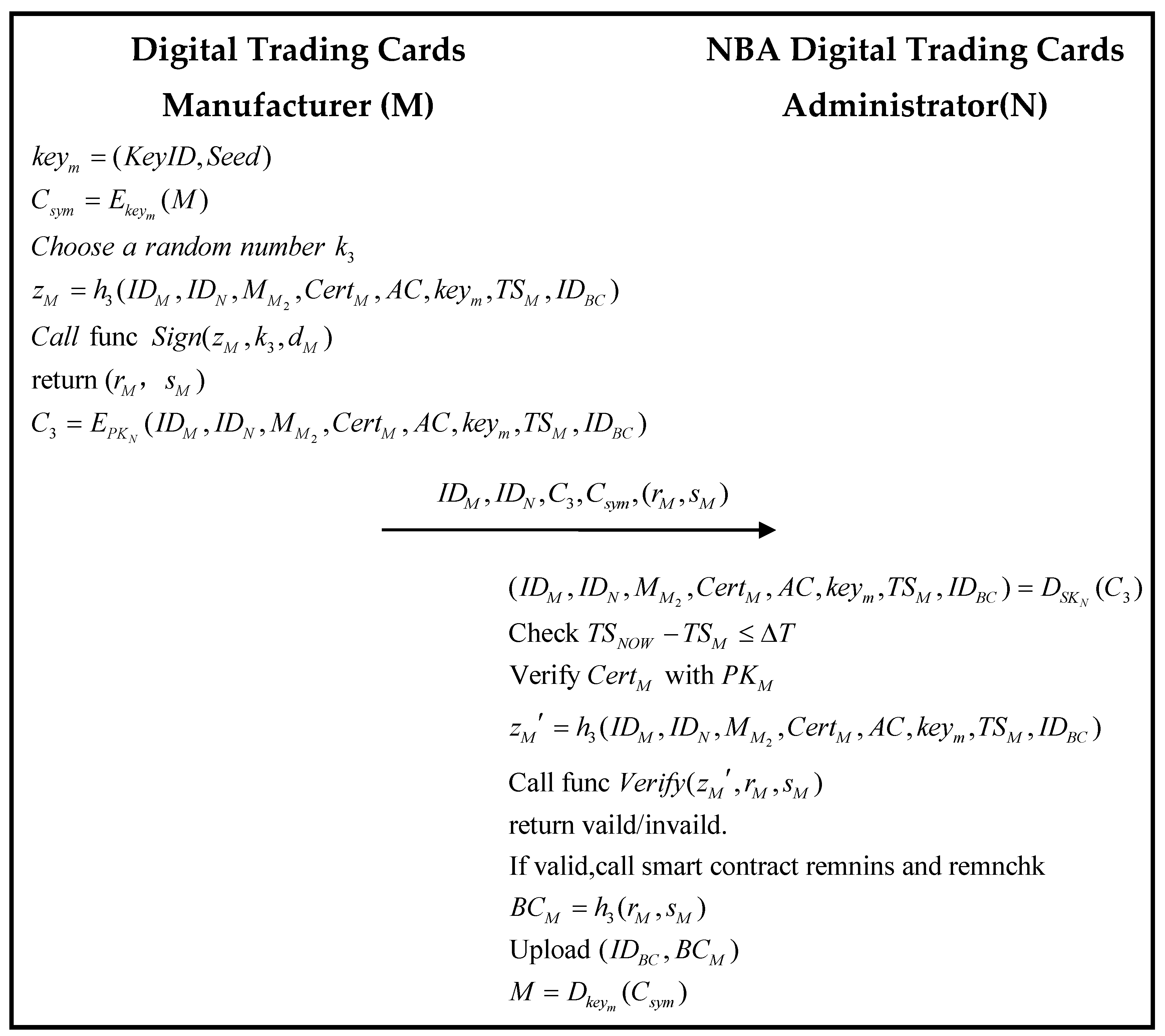
- Step 3
- Review Phase—After the manufacturer has obtained the authorization from the NBA Center, it will enter the review phase after completing the authorization phase. The digital trading card manufacturer will send the processed digital content and information related to the digital content to the NBA digital trading card center so that the NBA digital trading card center conducts a review of the content.
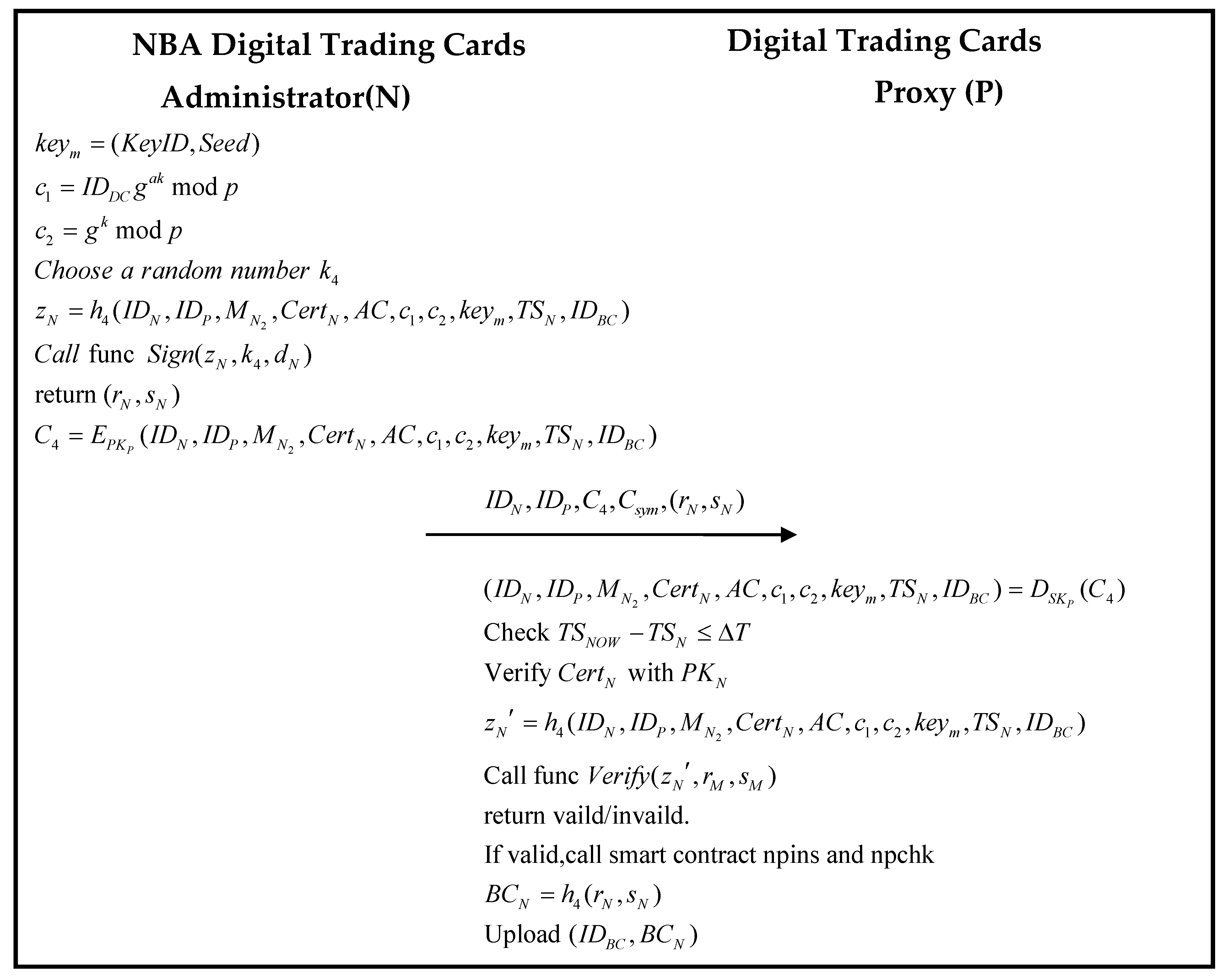
- Step 4
- Issue Phase—After the NBA digital trading card center completes the review of the digital trading card, the video content is classified, and the number of sales is approved. The NBA digital trading card center uploads the classification and number of sales of the digital trading card to the blockchain center and sends the content encrypted (by key encryption) to the digital trading card agent for storage.
- Step 5
- Identity Verification and Invoicing Phase—When a user submits a transaction request to the NBA digital trading card center, the NBA digital trading card center generates an invoice and transaction ID for the user after reviewing the user’s identity.
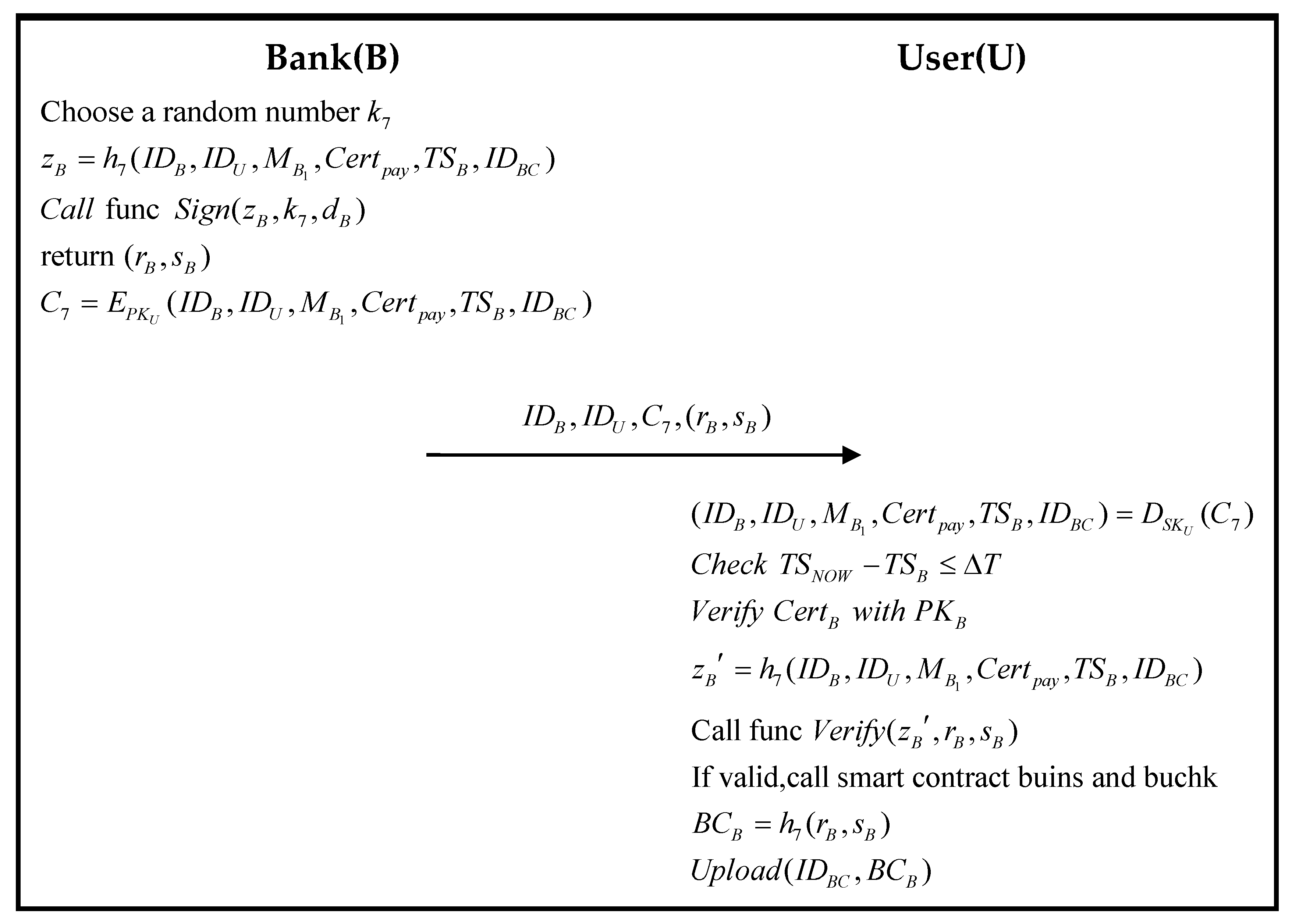
- Step 6
- Payment Phase—The user makes the payment through the bank. After the payment, the user requests the bank to issue a payment certificate for the transaction to authenticate the payment.
- Step 7
- Browse and Access phase—The NBA digital trading card center verifies the user’s identity and payment certificate, and upon successful verification, the NBA digital trading card center transfers the re-encryption key to the proxy and the time-limited decryption key to the user. The proxy’s re-encryption key generates a re-agent ciphertext, which the proxy transfers to the user, who uses the key to automatically decrypt the protected digital trading card and browse the digital trading card.
3.2. Smart Contract Initialization
| Algorithm 1. The structure of the smart contract scheme | |
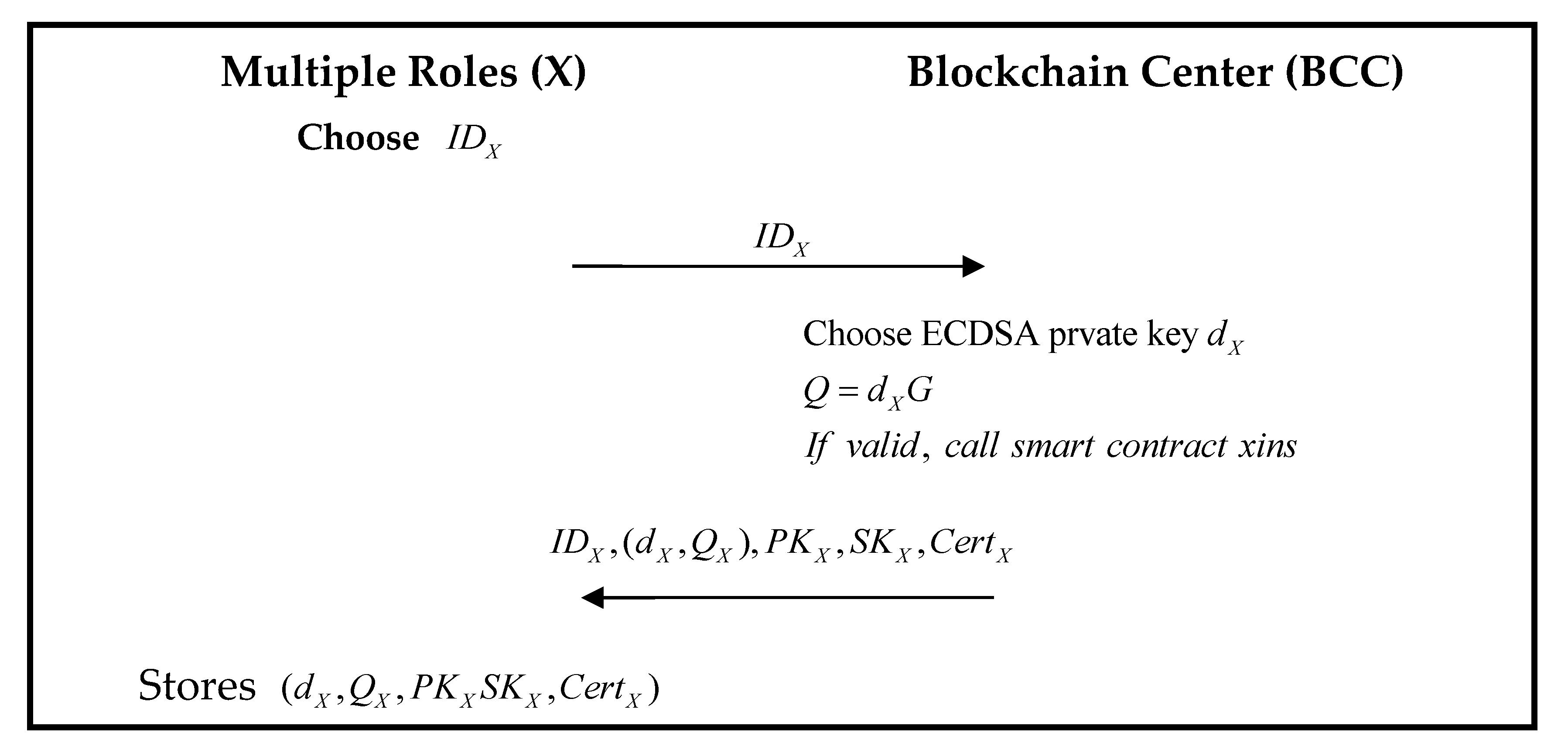
3.3. Registration Phase
| Algorithm 2. The scheme of the smart contract xins. |
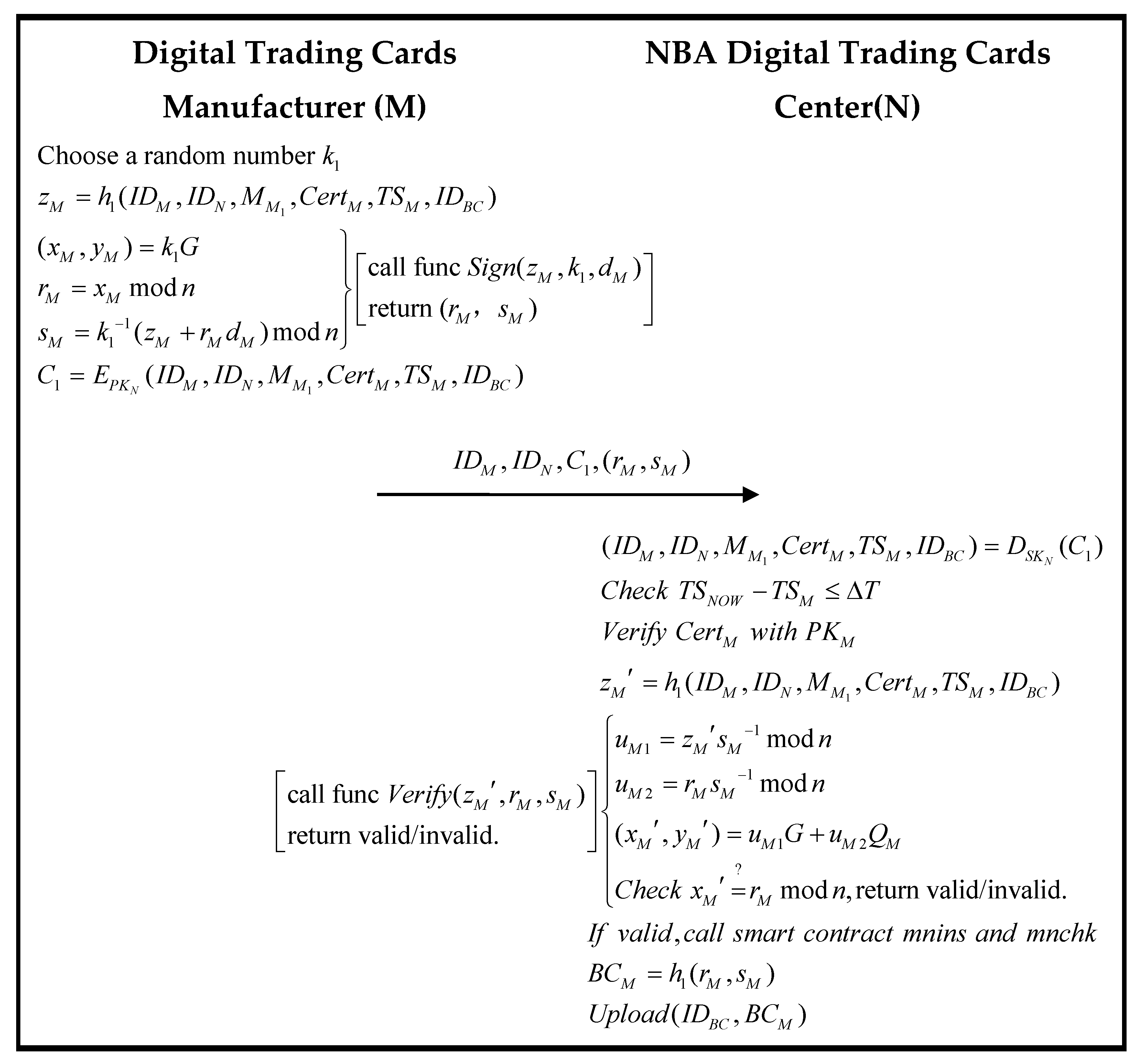
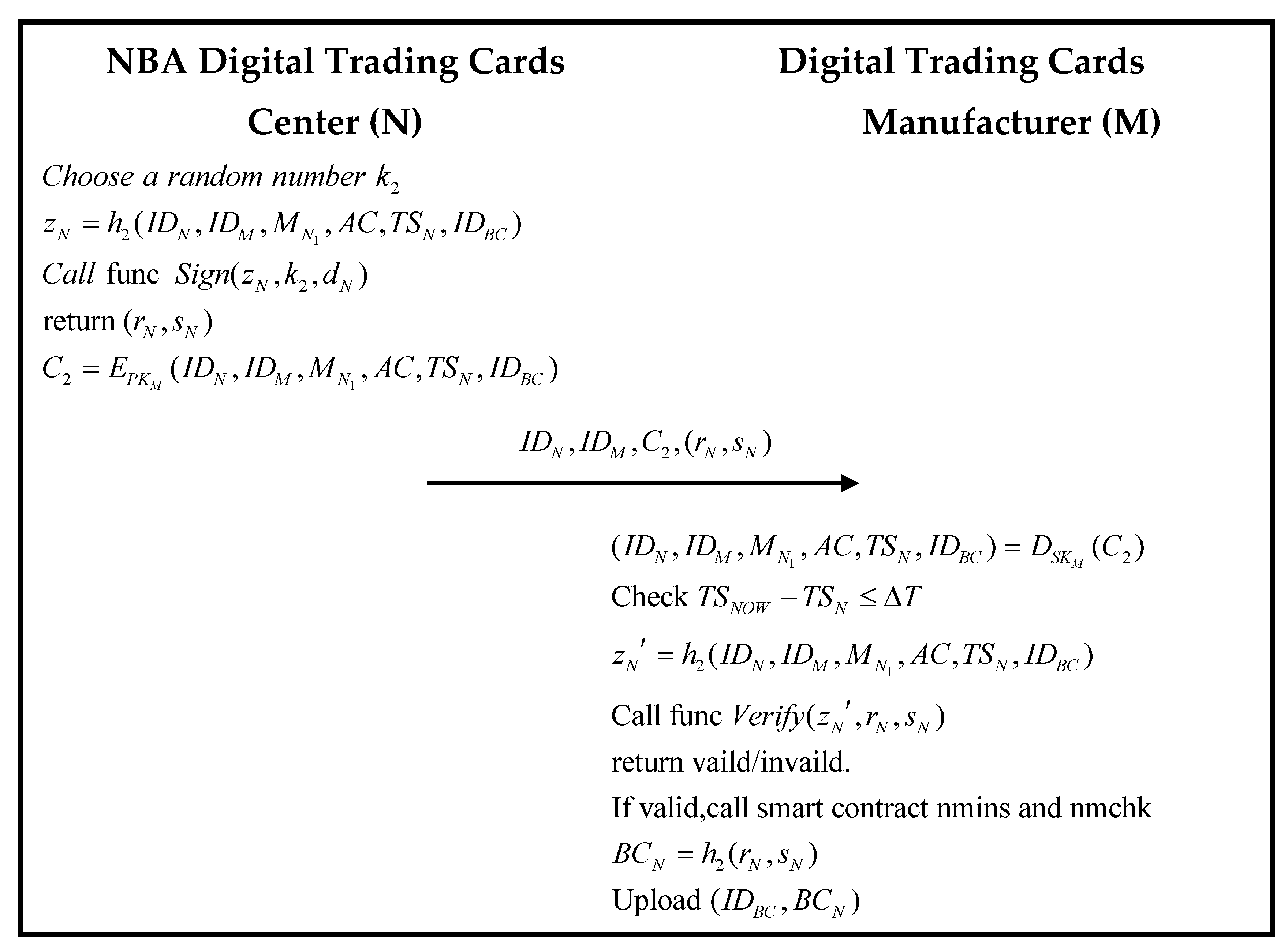
3.4. Manufacturing Authorization Phase
| Algorithm 3. The scheme of the smart contracts mnins and mnchk | |
| Algorithm 4. Chaincode Sign and Verify scheme | |
| Algorithm 5. The scheme of the smart contracts nmins and nmchk | |
3.5. Review Phase
| Algorithm 6. The scheme of the smart contracts remnins and remnchk | |
3.6. Issue Phase
| Algorithm 7. The scheme of the smart contracts npins and npchk | |
3.7. Identity Verification and Invoicing Phase
| Algorithm 8. The scheme of the smart contracts unins and unchk | |
| Algorithm 9. The scheme of the smart contracts nuins and nuchk | |
3.8. Payment Phase
| Algorithm 10. The scheme of the smart contracts buins and buchk | |
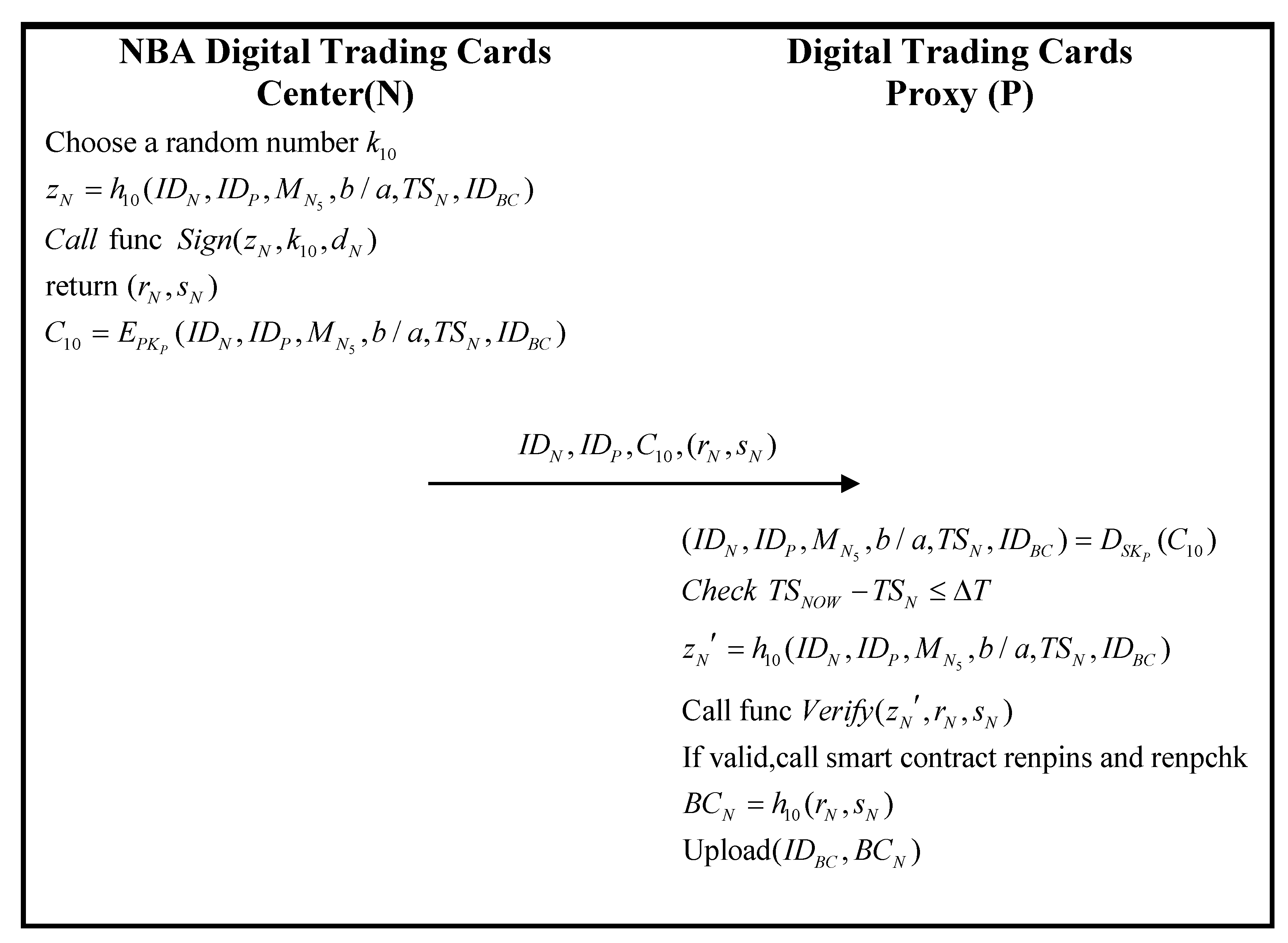
3.9. Browse and Access Phase
| Algorithm 11. The scheme of the smart contracts reunins and reunchk | |
| Algorithm 12. The scheme of the smart contracts renuins and renuchk | |
| Algorithm 13. The scheme of the smart contracts renpins and renpchk | |
| Algorithm 14. The scheme of the smart contracts repuins and repuchk | |
4. Security Analysis
4.1. Dispersive and Membership Access Control
4.2. Data Integrity and Unforgeable Data
4.3. Transparency
4.4. Traceability
4.5. Timeless
4.6. Replay Attacks
4.7. Man-in-the-Middle Attack
4.8. Sybil Attack
5. Discussion
5.1. Computation Cost
5.2. Communication Cost
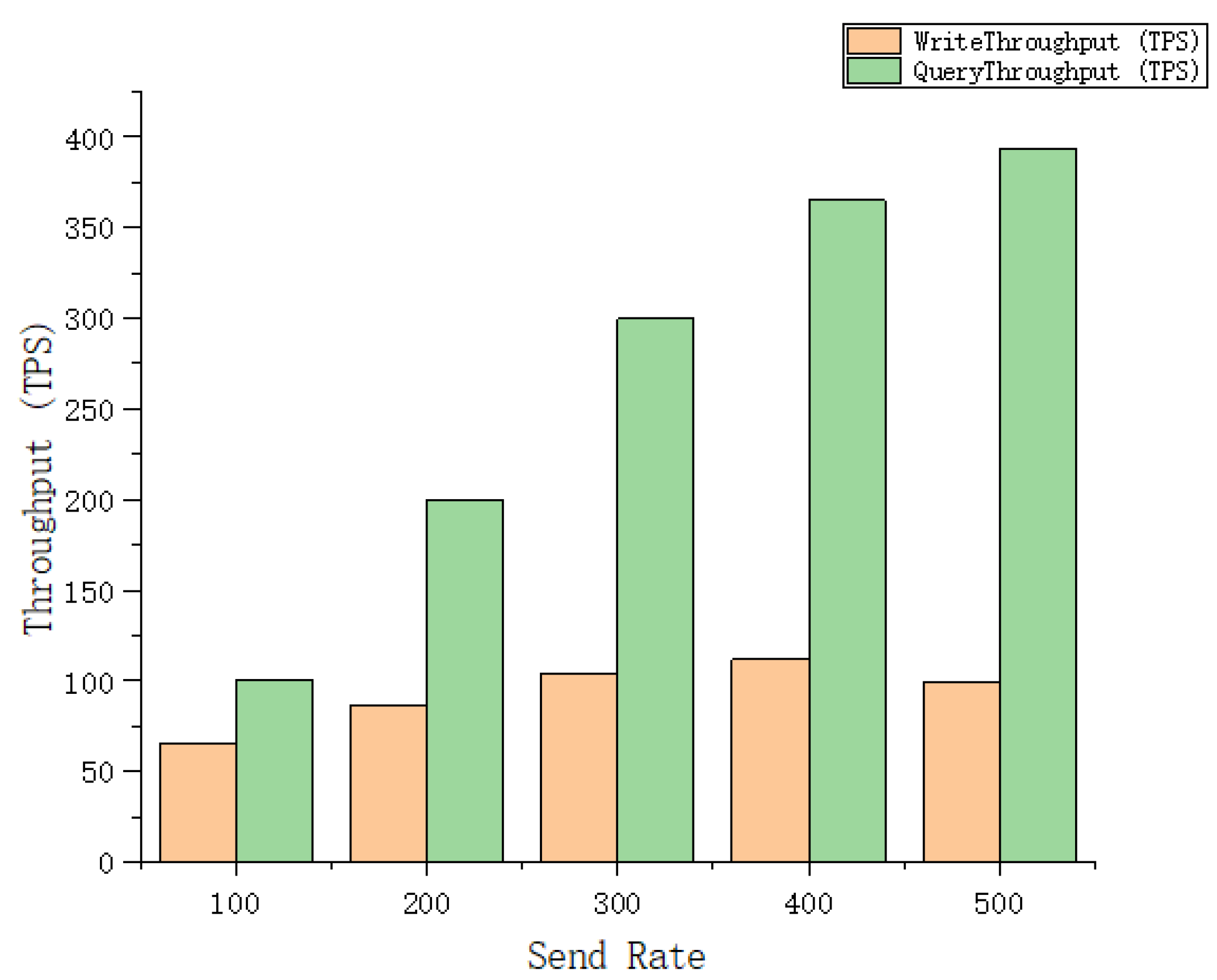
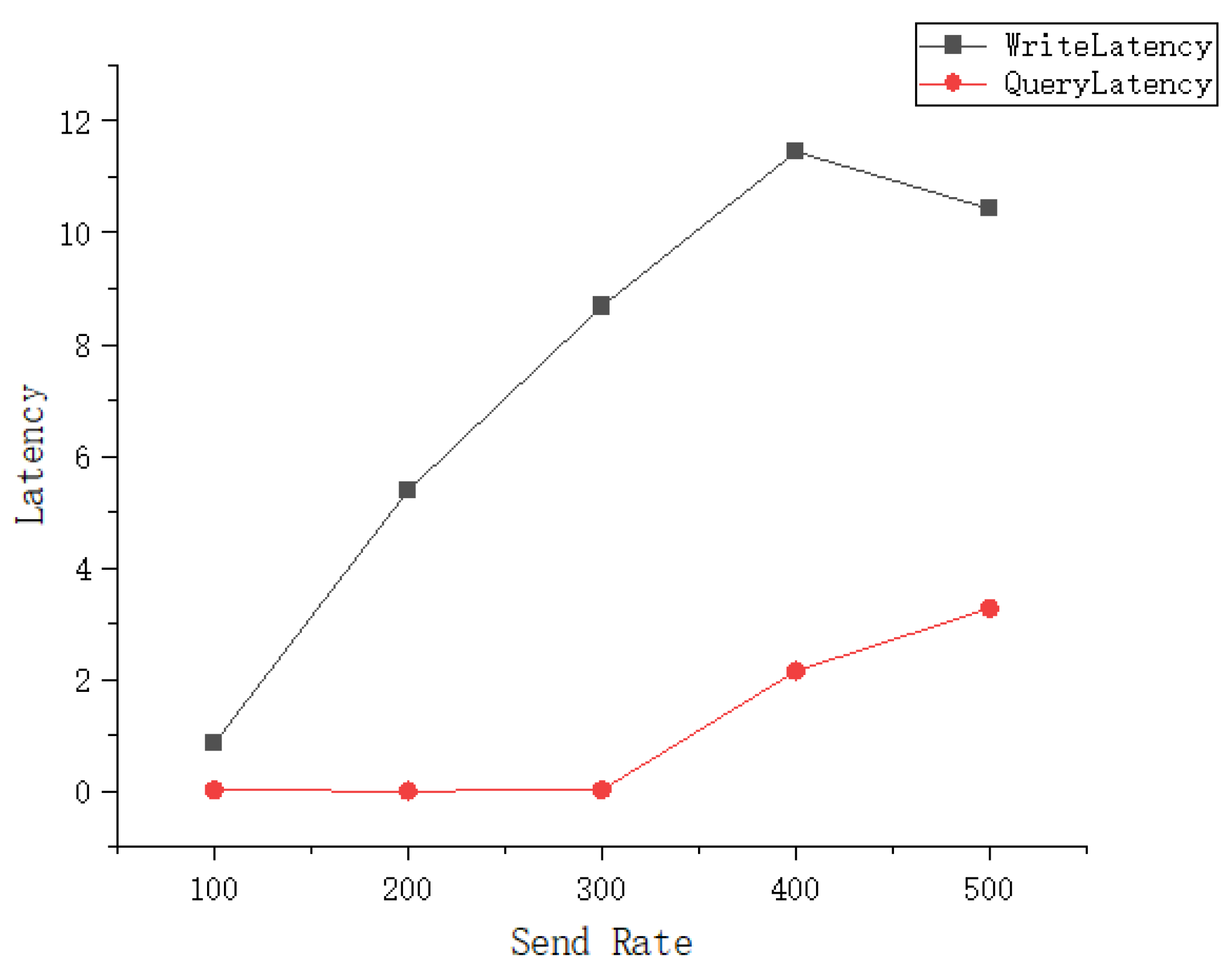
5.3. Performance Analysis-Deploying System Based on Blockchain
5.4. Function Comparison
6. Conclusions
- (1)
- Hyperledger Fabric technology is used for the management of anti-counterfeit traceability of digital trading cards.
- (2)
- The ECDSA signature algorithm can be used to ensure data integrity.
- (3)
- Proxy re-encryption is used for secure and trusted digital content authorization.
- (4)
- Smart contracts are designed for the ins and outs of digital transaction cards.
- (5)
- An analysis of the computational and communication costs.
- (6)
- Collectors can verify the ownership of NBA digital trading cards via blockchain.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Notations
| A k-bit prime number | |
| Finite group q | |
| The elliptic curve defined on finite group | |
| A generating point based on the elliptic curve | |
| A name representing an identity | |
| The -th generated a random number on the elliptic curve | |
| N generated digital cards to generate authorization codes | |
| The -th ECDSA/elliptic curve signature value of user X | |
| Private/public key of | |
| Private/public key in proxy re-encryption | |
| The -th message sent by role | |
| An index value of blockchain message | |
| Blockchain messages for | |
| X’s timestamp/current timestamp | |
| X’s public key/private key that was issued by | |
| Encrypt/decrypt the message using X’s public key/private key | |
| Encrypt/decrypt the digital content using symmetric keys | |
| An identity of digital content | |
| Asymmetric key containing KeyID and Seed | |
| A digital certificate conforms to the X.509 standard | |
| Certification issued by the bank for the user’s purchase | |
| The hash value of X | |
| The -th hash function | |
| The ciphertext obtained by symmetric encryption | |
| . | Verify whether is equal to |
References
- Trading Card—Wikipedia. Available online: https://en.wikipedia.org/wiki/Trading_card (accessed on 22 July 2022).
- Sports Trading Card Market Size and Forecast. Available online: https://www.verifiedmarketresearch.com/product/sports-trading-card-market/ (accessed on 22 July 2022).
- Ebay’s 2021 “State of Trading Cards” Report Spotlights Collecting Trends and Industry Predictions. Available online: https://www.ebayinc.com/stories/news/ebays-2021-state-of-trading-cards-report-spotlights-collecting-trends-and-industry-predictions/ (accessed on 22 July 2022).
- Operation Bullpen. Available online: https://archives.fbi.gov/archives/news/stories/2005/july/operation-bullpen-overview (accessed on 22 July 2022).
- Rovell: A Look Inside the Scandal Rocking the Sports Memorabilia World. Available online: https://www.actionnetwork.com/general/darren-rovell-card-memorabilia-fraud-national-sports-collector-convention (accessed on 22 July 2022).
- PSA-Wikipedia. Available online: https://en.wikipedia.org/wiki/PSA (accessed on 22 July 2022).
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://klausnordby.com/bitcoin/Bitcoin_Whitepaper_Document_HD.pdf (accessed on 22 July 2022).
- Ante, L. The non-fungible token (NFT) market and its relationship with Bitcoin and Ethereum. FinTech 2022, 1, 216–224. [Google Scholar] [CrossRef]
- Chen, C.-L.; Lin, C.-Y.; Chiang, M.-L.; Deng, Y.-Y.; Chen, P.; Chiu, Y.-J. A traceable online will system based on blockchain and smart contract technology. Symmetry 2021, 13, 466. [Google Scholar] [CrossRef]
- Chen, C.-L.; Deng, Y.-Y.; Tsau, W.-J.; Li, C.-T.; Lee, C.-C.; Wu, C.-M. A traceable online insurance claims system based on blockchain and smart contract technology. Sustainability 2021, 13, 9386. [Google Scholar] [CrossRef]
- Chen, C.; Lim, Z.; Liao, H.; Deng, Y.; Chen, P. A traceable and verifiable tobacco products logistics system with GPS and RFID technologies. Appl. Sci. 2021, 11, 4939. [Google Scholar] [CrossRef]
- Deepa, N.; Pham, Q.; Nguyen, D.; Bhattacharya, S.; Prabadevi, B.; Gadekallu, T.; Maddikunta, P.; Fang, F.; Pathirana, P. A survey on blockchain for big data: Approaches, opportunities, and future directions. Future Gener. Comput. Syst. 2022, 131, 209–226. [Google Scholar] [CrossRef]
- Stamatellis, C.; Papadopoulos, P.; Pitropakis, N.; Katsikas, S.; Buchanan, W.J. A Privacy-Preserving Healthcare Framework Using Hyperledger Fabric. Sensors 2020, 20, 6587. [Google Scholar] [CrossRef]
- Chen, C.; Wang, T.; Tsaur, W.; Weng, W.; Deng, Y.; Cui, J. Based on Consortium Blockchain to Design a Credit Verifiable Cross University Course Learning System. Secur. Commun. Netw. 2021, 2021, 8241801. [Google Scholar] [CrossRef]
- Chen, C.-L.; Deng, Y.-Y.; Li, C.-T.; Zhu, S.; Chiu, Y.-J.; Chen, P.-Z. An IoT-Based Traceable Drug Anti-Counterfeiting Management System. IEEE Access 2020, 8, 224532–224548. [Google Scholar] [CrossRef]
- Zhao, S.; O’Mahony, D. Bmcprotector: A blockchain and smart contract based application for music copyright protection. In Proceedings of the 2018 International Conference on Blockchain Technology and Application, Xi’an, China, 10–12 December 2018; pp. 1–5. [Google Scholar]
- Jing, N.; Liu, Q.; Sugumaran, V. A blockchain-based code copyright management system. Inf. Process. Manag. 2021, 58, 102518. [Google Scholar] [CrossRef]
- Wang, Y.-C.; Chen, C.-L.; Deng, Y.-Y. Authorization Mechanism Based on Blockchain Technology for Protecting Museum-Digital Property Rights. Appl. Sci. 2021, 11, 1085. [Google Scholar] [CrossRef]
- Wang, N.; Xu, H.; Xu, F.; Cheng, L. The algorithmic composition for music copyright protection under deep learning and blockchain. Appl. Soft Comput. 2021, 112, 107763. [Google Scholar] [CrossRef]
- NBA Top Shot Mints A Unicorn: How an Ethereum Competitor Cashed in on The NFT Craze. Available online: https://www.forbes.com/sites/brettknight/2021/03/30/nba-top-shot-dapper-labs-nft-funding/?sh=2b0b234a67ae (accessed on 22 July 2022).
- Ma, Z.; Jiang, M.; Gao, H.; Wang, Z. Blockchain for digital rights management. Future Gener. Comput. Syst. 2018, 89, 746–764. [Google Scholar] [CrossRef]
- Ma, Z.; Wang, L.; Wang, X.; Wang, Z.; Zhen, W. Blockchain-enabled decentralized trust management and secure usage control of IoT big data. IEEE Internet Things J. 2019, 7, 4000–4015. [Google Scholar]
- Guo, J.; Li, C.; Zhang, G.; Sun, Y.; Bie, R. Blockchain-enabled digital rights management for multimedia resources of online education. Multimed. Tools Appl. 2020, 79, 9735–9755. [Google Scholar] [CrossRef]
- Khan, U.; An, Z.; Imran, A. A blockchain Ethereum technology-enabled digital content: Development of trading and sharing economy data. IEEE Access 2022, 8, 217045–217056. [Google Scholar] [CrossRef]
- Li, M.; Zeng, L.; Zhao, L.; Yang, R.; An, D.; Fan, H. Blockchain-watermarking for compressive sensed images. IEEE Access 2021, 9, 56457–56467. [Google Scholar] [CrossRef]
- Heo, G.; Yang, D.; Doh, I.; Chae, K. Efficient and secure blockchain system for digital content trading. IEEE Access 2021, 9, 77438–77450. [Google Scholar] [CrossRef]
- Polge, J.; Robert, J.; Le Traon, Y. Permissioned blockchain frameworks in the industry: A comparison. ICT Express 2020, 7, 229–233. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Gai, R.; Du, X.; Ma, S.; Chen, N.; Gao, S. A summary of the research on the foundation and application of blockchain technology. J. Phys. Conf. Ser. 2020, 1693, 012025. [Google Scholar] [CrossRef]
- Nasir, Q.; Qasse, I.A.; Abu Talib, M.; Nassif, A. Performance analysis of hyper ledger fabric platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef]
- Chen, C.-L.; Yang, J.; Tsaur, W.-J.; Weng, W.; Wu, C.-M.; Wei, X. Enterprise Data Sharing with Privacy-Preserved Based on Hyperledger Fabric Blockchain in IIOT’s Application. Sensors 2022, 22, 1146. [Google Scholar] [CrossRef] [PubMed]
- Szabo, N. The Idea of Smart Contracts. Nick Szabo’s Papers and Concise Tutorials. 1997, 6, p. 199. Available online: http://www.fon.hum.uva.nl/rob/Courses/InformationInSpeech/CDROM/Literature/LOTwinterschool2006/szabo.best.vwh.net/smart_contracts_idea.html (accessed on 22 July 2022).
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin, Germany, 1998; pp. 127–144. [Google Scholar]
- Malladi, S.; Alves-Foss, J.; Heckendorn, R.B. On Preventing Replay Attacks on Security Protocols. 2002. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.15.6492&rep=rep1&type=pdf (accessed on 22 July 2022).



| Authors | Year | Objective | Technologies | Merits | Demerits |
|---|---|---|---|---|---|
| Ma et al. [21] | 2018 | Blockchain-based scheme for digital rights management | Ethereum, Smart Contract | Detailed implementation of DRM on a blockchain platform, transparency data format standardization | Timeless Not applicable |
| Ma et al. [22] | 2019 | Permissioned blockchain-based decentralized trust management and secure usage control scheme of IoT big data | Ethereum, Smart Contract | Detailed implementation of DRM on a blockchain platform | No security analysis and no specific comparison with other methods |
| Guo et al. [23] | 2020 | Combination of the public and private blockchains-enabled digital rights management system | Smart Contract, Blockchain | With a detailed functional module design and system architecture design | No security analysis, and comparison with other methods |
| Khan et al. [24] | 2020 | Content protection and transaction method using blockchain Ethereum technology | Ethereum, Smart Contract | There is a detailed implementation process An encryption algorithm is implemented for the content | No safety analysis, and comparison with other methods |
| Li et al. [25] | 2021 | Blockchain-watermarking scheme to protect the privacy | Watermarking, compressed sensing, BlockChain, IPFS | The low computational cost of the encryption process, simultaneous encryption, and compression, robustness of ciphertext | No detailed chain code implementation process |
| Heo et al. [26] | 2021 | Using SBBC’s blockchain digital content trading system | Fingerprinting, BlockChain, SBBC, Consensus, algorithm. | Solves the problem of illegal digital content copying and leakage Addresses blockchain network overload and storage space limitations | Only part of the blockchain algorithm has been designed, and there are restrictions on the environment of use |
| Phase | Party | Message | Hash Value | Verification | |
|---|---|---|---|---|---|
| Sender | Receiver | ||||
| Manufacturing | M | N | |||
| Authorization | N | M | |||
| Review | M | N | |||
| Issued | N | P | |||
| Verify User Id | U | N | |||
| and Invoice | N | U | |||
| Payment | B | U | |||
| Browse | U | N | |||
| Request | N | U | |||
| and | N | P | |||
| Access | P | U | |||
| Phase | Party | Verification | |
|---|---|---|---|
| Sender | Receiver | ||
| Manufacturing | M | N | |
| Authorization | N | M | |
| Review | M | N | |
| Issued | N | P | |
| Verify User Id | U | N | |
| and Invoice | N | U | |
| Payment | B | U | |
| Browse | U | N | |
| Request | N | U | |
| and | N | P | |
| Access | P | U | |
| Phase | Party | Encryption | Decryption | |
|---|---|---|---|---|
| Sender | Receiver | |||
| Manufacturing | M | N | ||
| Authorization | N | M | ||
| Review | M | N | ||
| Issued | N | P | ||
| Verify User Id | U | N | ||
| and Invoice | N | U | ||
| Payment | B | U | ||
| Browse | U | N | ||
| Request | N | U | ||
| and | N | P | ||
| Access | P | U | ||
| Phase | 1st Role | 2nd Role | 3rd Role |
|---|---|---|---|
| Manufacturing Authorization | Digital Trading Cards Manufacturer | NBA Digital Trading Cards Center | N/A |
| Review | Digital Trading Cards Manufacturer | NBA Digital Trading Cards Center | N/A |
| Issued | NBA Digital Trading Cards Center | Digital Trading CardsProxy | N/A |
| Verify User Id and Invoice | User | NBA Digital Trading Cards Center | N/A |
| Payment | Bank | User | N/A |
| Browse Request and Access | User | NBA Digital Trading Cards Center | Digital Trading CardsProxy |
| Phase | Message Length | 3.5G (14 Mbps) | 4G (100 Mbps) | 5G (20 Gbps) |
|---|---|---|---|---|
| Manufacturing Authorization | 2688 bits | 0.192 ms | 0.027 ms | 0.134 μs |
| Review | 1856 bits | 0.133 ms | 0.019 ms | 0.093 μs |
| Issued | 1362 bits | 0.097 ms | 0.014 ms | 0.068 μs |
| Verify User Id and Invoice | 2688 bits | 0.192 ms | 0.027 ms | 0.134 μs |
| Payment | 1344 bits | 0.096 ms | 0.014 ms | 0.065 μs |
| Browse and Access | 5076 bits | 0.384 ms | 0.054 ms | 0.268 μs |
| Authors | Year | Objectives | 1 | 2 | 3 | 4 | 5 | 6 |
|---|---|---|---|---|---|---|---|---|
| Ma et al. [21] | 2018 | Blockchain-based scheme for digital rights management | Y | Y | Y | Y | Y | N |
| Ma et al. [22] | 2019 | Permissioned blockchain-based decentralized trust management and secure usage control scheme of IoT big data | Y | N | N | Y | N | N |
| Guo et al. [23] | 2020 | Combination of the public and private blockchains-enabled digital rights management system | Y | N | N | Y | N | N |
| Khan et al. [24] | 2020 | Content protection and transaction method using blockchain Ethereum technology | Y | N | N | Y | N | N |
| Li et al. [25] | 2021 | Blockchain-watermarking scheme to protect the privacy | Y | Y | N | Y | N | N |
| Heo et al. [26] | 2021 | Using SBBC’s blockchain digital content trading system | Y | N | N | Y | N | N |
| Ours | 2022 | Blockchain-based digital trading card management platform | Y | Y | Y | Y | Y | Y |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.-L.; Fang, C.-C.; Zhou, M.; Tsaur, W.-J.; Sun, H.; Zhan, W.; Deng, Y.-Y. A Blockchain-Based Anti-Counterfeit and Traceable NBA Digital Trading Card Management System. Symmetry 2022, 14, 1827. https://doi.org/10.3390/sym14091827
Chen C-L, Fang C-C, Zhou M, Tsaur W-J, Sun H, Zhan W, Deng Y-Y. A Blockchain-Based Anti-Counterfeit and Traceable NBA Digital Trading Card Management System. Symmetry. 2022; 14(9):1827. https://doi.org/10.3390/sym14091827
Chicago/Turabian StyleChen, Chin-Ling, Cheng-Chen Fang, Ming Zhou, Woei-Jiunn Tsaur, Hongyu Sun, Wanbing Zhan, and Yong-Yuan Deng. 2022. "A Blockchain-Based Anti-Counterfeit and Traceable NBA Digital Trading Card Management System" Symmetry 14, no. 9: 1827. https://doi.org/10.3390/sym14091827
APA StyleChen, C.-L., Fang, C.-C., Zhou, M., Tsaur, W.-J., Sun, H., Zhan, W., & Deng, Y.-Y. (2022). A Blockchain-Based Anti-Counterfeit and Traceable NBA Digital Trading Card Management System. Symmetry, 14(9), 1827. https://doi.org/10.3390/sym14091827








