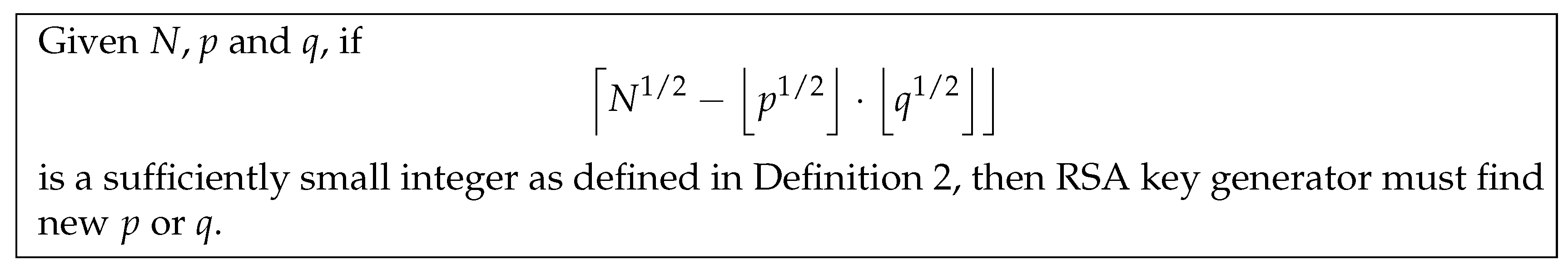1. Introduction
One of the earliest asymmetric key cryptosystems is the Rivest–Shamir–Adleman (RSA) cryptosystem, introduced by Rivest, Shamir and Adleman in 1978 [
1]. Its simple and easy-to-understand mathematical design makes it compelling to be used in the early ages of digital cyberspace technology. Since then, it is considered as the most widely known asymmetric key cryptosystem. In its key generation algorithm, an RSA modulus,
is computed where
p and
q, called RSA primes are two distinct primes such that
. From the values of
p and
q, another parameter called RSA public exponent,
e is obtained which satisfies
and
where
. An RSA private exponent,
d that satisfies
then is computed. One of the security strength of RSA is integer factorization problem and it is embedded in the RSA modulus since
p and
q are very large
bit primes (typically,
). The problem is deemed infeasible to be solved by current computing machines and the best algorithm to solve the problem, called general number field sieve (GNFS) [
2] is still running in sub-exponential time.
Past attacks on RSA by Pollard in 1974 [
3] have shown that primes with particular structures are vulnerable to be factored in polynomial time, which is easily computed by any modern computers. In his attacks, Pollard showed that if
or
are constituted of small primes, then there is a factoring algorithm to factor
in polynomial time. Another method in attacking RSA assumes that several bits of
p and
q are known by the adversary and this weakens the hardness of factoring
N. Particularly, ref. [
4] showed that
least significant bits (LSBs) of the RSA primes are sufficient to factor
N in polynomial time. Random reconstruction algorithm by Heninger and Shacham also showed that it can efficiently recover all of the RSA keys given 0.57 fraction of the random bits of each
p and
q [
5]. Later, Maitra et al. [
6] provided a combinatorial model of Heninger’s work and was able to reconstruct the LSBs of RSA primes using modified brute-force by shortening the total search space.
The LSBs discussed in the prior attacks of RSA are commonly gathered by side-channel attack. It is one of the prominent methods to collect the physical outputs or side-effects of cryptographic devices during the computing processes [
7]. The outputs or side-effects include but are not limited to the computational time and power of decryption [
8,
9], emission heat and electromagnetic radiation of the devices [
10], cache behavior [
11] and sound of processor during computations [
12].
About This Paper
The results in this paper are the extensions from our papers in [
13] and [
14]. In this paper, we assume that certain LSBs of the RSA primes are known. We show that only a small amount of LSBs are required in our attack to factor
N in polynomial time given that the RSA primes satisfy specified structures. We also show the abundance of primes that can satisfy the structures and no proper checking mechanism has been done in any standard RSA libraries to hinder the usage of such primes. This shows the risks inherent in the existing method to generate RSA keys may produces RSA modulus that falls under our attack.
2. Preliminaries
In this section, we provide some helpful lemmas which results are applied to make our attack successful.
Lemma 1. Let and be an even number. If then .
Proof. Let
be an integer where
. Then
Since
then
. This terminates the proof. □
Suppose is a valid RSA modulus where and . Let , we can see that is unknown if p and q are secret values. Using the result from Lemma 1, we find the lower and upper bounds of in the following lemma.
Lemma 2. Let and be an even number such that . Suppose where . If and then .
Proof. To prove the lower bound, first we need to show that
. Observe that
Since
will always be positive value, it implies that
. Then
Thus,
. To prove the upper bound, since
and
. Then, based on Lemma 1,
If
and
then
If
, then Equation (
1) becomes
This terminates the proof. □
By obtaining the lower and upper bounds of in Lemma 2, we have gathered a result that can be useful in our attack later. Throughout this paper, we focus on the RSA primes in the forms of and . Therefore, we define LSBs in the next definition based on these forms.
Definition 1 (Least Significant Bits (LSBs) of Primes)
. Let . Suppose and are primes. Suppose there exist unknown and such thatandThen we define and to be k-many LSBs of p and q respectively where satisfiesand To identify primes that satisfy Equations (
3) and (
4), we observe the binary representations of
and
. Their LSBs must have
k many consecutive 0’s to satisfy
and
. Particularly, let
be the binary representation of
a and
be the binary representation of
b where
. Observe
The random reconstruction algorithm [
5], which was improved by [
6], is one of the efficient algorithms used to find the LSBs of RSA primes. Thus, it can be utilized to find the values of
and
that satisfy Equations (
5) and (
6).
3. Our Attack
Before we proceed to show how N can be factored in polynomial time using previous results, we define the term ‘sufficiently small’ that is used to justify our attack.
Definition 2. We define sufficiently small value in this paper to be a value smaller than the largest feasible value of the lowest security level to be brute forced by current computing machine.
Remark 1. The latest recommendation for key management by NIST [15] stated that the lowest security level is 112-bit. This implies that the largest feasible value of this security level to be brute forced by current computing machine is . Based on Definition 2, a value lower than is considered sufficiently small. This value can be changed in the future, depends on the future advancements of computing technology. Now we are ready to show how RSA modulus can be factored in polynomial time by using this next theorem.
Theorem 1. Let and be an even number such that . Suppose is a valid RSA modulus. Let and where and such that . If is a sufficiently small value as defined in Definition 2 and k many LSBs of p and q are known then N can be factored in polynomial time.
Proof. From Lemma 2 we can see that
. Thus,
Suppose
and
are known LSBs of
p and
q respectively. The LSB values may be obtained from side-channel attacks described previously in
Section 1. Since
, then the difference between the upper and lower bounds of Equation (
9) is
which is the size for set of integers to find
. If
is sufficiently small as defined in Definition 2, then we can find
in polynomial time. By computing
, we find
. Then
Observe that from
and
, then we can have
. Thus, we obtain the full integer
without modular reduction. Since the values of
and
are known, we can find the roots of the following quadratic equation
We find that
and
. Since
and
are known, we can can obtain
Thus we can factor
N by calculating
□
The next remark justifies our selection criteria on parameter m.
Remark 2. Let be the set of possible value of . From Equation (9), we know that will yield a set of numbers between and . If is an even integer, then will be an integer and causes to be a finite set. However, if m is a positive odd integer, then will be a real value and causes to be an infinite set. The latter consequence will make our method to be infeasible since there are infinite possible values of to be tried on. Therefore, m must be an even integer equals or greater than 2. The following is an example to illustrate the result from Theorem 1.
Example 1. We use RSA-2048 modulus in this example. Specifically, we are givenSuppose from side-channel attack described previously, we know the 12 LSBs of p and q. Particularly,andwhereandThen we set Then we calculateand solve the equation We find that neither nor are integers. This means and are not our final solutions. It also means at this point. To find the correct σ, we have to iterate the computation of Equations (13) and (14) using iterations of increasing values of i. This search can be done in polynomial time as i should be less than as stated in Lemma 2. In this case, we find the correct σ when . That is, we computeandUsing values of σ and z, we solve the equationThe solutions of Equation (15) are used to computeandHence, N has been successfully factored in polynomial time. Remark 3. From Example 1, we show that as small as 12-bits of LSBs are required to successfully execute our attack. Hence, this put our method in advantage since it does not necessarily depend on side-channel attack [7] to gather the LSBs. Instead, by using our method, an adversary can use brute-force approach to find the correct LSBs since the required LSBs can be very small. 4. Numbers of Primes with Vulnerable Specialized Structures Against Random Reconstruction Algorithm
From Equations (
7) and (8) we can see that
until
must be another binary representation of a squared number. The same case also applies on
until
In the next Theorem, we count the number of squared numbers with
bit.
Theorem 2. If n is any large positive integer and k is a small positive integer then there are at least squared numbers between and .
Proof. Let
for
be the set of all squared numbers between
and
. Particularly,
Then
To find the least number of
i, the amount of squared numbers between
and
, we compute the difference between the upper bound and the lower bound of Equation (
16) in integer form. That is,
If
n is any large positive integer and
k is a small positive integer then
This terminates the proof. □
Theorem 3. Let and be an even number such that . Suppose be a valid RSA modulus. Let and where and such that . Let be an integer where is the smallest squared number with n-bit size. If is a sufficiently small value as defined in Definition 2 and k many LSBs of p and q are known, then there are at mostcandidates of p and q with size of n-bit such that and satisfy Theorem 1. Proof. Let
be an integer where
is the smallest squared number with
-bit. Let
be the prime-counting function between
and
. Then
From Theorem 2, we know there are approximately
squared numbers with
-bit size where
is a large integer suitably used in RSA. Thus,
for the consecutive squared numbers are as follows:
The summation of Equation (
17) can be represented in the sum of arithmetic progression formula where the number of
i terms is multiplied by the sum of the first and last number in the progression and dividing by 2. That is,
This terminates the proof. □
Result from Theorem 3 shows there is a significant amount of primes that satisfy Theorem 1.
5. Comparative Analysis
Here we compare our results with the existing attacks with known bits of primes. The authors of [
16] introduced partial key exposure attacks with assumption that certain bits of primes can be known by the adversary. They showed that
bits of
p or
q are sufficient to factor
N using integer programming technique. Later, ref. [
17] reduced this value to
using LLL algorithm. The attack from Herrmann and May later on required the known bits to be arranged in random blocks [
18].
Heninger and Shacham’s attack is motivated by the so-called cold boot attack which targets the memory in electronic chips to reconstruct the bits of the private keys given that the bits are from random positions [
5]. They successfully conducted the attack if
random bits of the primes are known. It should be noted here their fraction value is much lower if they consider the random bits of RSA private exponent,
d (
and
in the case of CRT-RSA). Using a similar method, ref. [
6] proved that if the total LSBs from both
p and
q known is at least 50% of the total length of
N, then
N can be factored using lattice-based method. Our method, unlike existing methods, utilize
k-many LSBs of the primes where
k is less than the value of
which is sufficiently small as defined in Definition 2, as shown in Theorem 1.
The summaries of all the attacks are compiled in
Table 1.
From
Table 1, we can see that our method required less LSBs for the attack to be successful when compared to [
5,
6]. That is, the attack required less computational time and space to be executed. It is easy to see that if
and
, then
. This is a substantial improvement from previous works.
We would like to point out the trade-off of our attack, namely the characteristics as mentioned in Theorem 1. Nevertheless, our analysis shows that if
and
are bounded to
where
k is stated as in Definition 2, the side-channel attack can be conducted in reasonable time in order to identify whether the primes in physical devices fall under the category as mentioned. This results in our research to be of importance for real-world implementation of the RSA cryptosystem. Moreover, we have shown in
Section 4 that the number of primes satisfying our conditions are exponentially many. This shows the importance of our attack.
6. Countermeasure of the Attack
Although the attack seems to target a niche set of primes, there is no immediate noticeable detection that can be implemented to overcome the attack. This means the prevention from utilizing the weak primes must be applied in the RSA key generator with the full knowledge of the secret parameters,
p and
q. The countermeasure is depicted in
Figure 1.
Since the computation is minimal, the prevention of the attack can be applied in the real-world RSA implementation.
Example 2. For a toy example of this countermeasure method, we revisit the values in Example 1. Given from Example 1, we computeSince 2811 is definitely sufficiently small based on Definition 2, an RSA key generator must find new p and q. Letbe the the new p and q. Then,be the new RSA modulus, N. We computewhich is larger than . Hence N is safe from our attack. 7. Conclusions
We have shown an attack on RSA modulus, where and for and are k LSBs of p and q respectively. Our attack can be mounted successfully in polynomial time if the LSBs of the primes are known and satisfy the conditions. We also show that there is a significant number of primes with respect to their sizes that are vulnerable to our attack. This imposes a great threat to the RSA users who might not realize that their RSA primes may fall under these vulnerable primes. However, our suggestion on how to detect the vulnerable primes during the key generation process may help to overcome this problem so that the RSA cryptosystem can still be applied.
Author Contributions
Conceptualization, A.H.A.G., M.R.K.A. and M.A.A.; methodology, formal analysis, investigation, writing—original draft preparation, A.H.A.G.; writing—review and editing, A.H.A.G., M.R.K.A. and M.A.A.; supervision and funding acquisition, M.R.K.A. All authors have read and agreed to the published version of the manuscript.
Funding
The research was supported by Ministry of Education of Malaysia with Fundamental Research Grant Scheme (FRGS/1/2019/STG06/UPM/02/08).
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| LSB | Least significant bits |
| MSB | Most significant bits |
| RRA | random reconstruction algorithm |
| RSA | Rivest–Shamir–Adleman |
References
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Buhler, J.P.; Lenstra, H.W.; Pomerance, C. Factoring integers with the number field sieve. In The Development of the Number Field Sieve; Springer: Berlin/Heidelberg, Germany, 1993; pp. 50–94. [Google Scholar]
- Pollard, J.M. Theorems on factorization and primality testing. Math. Proc. Camb. Philos. Soc. 1974, 76, 521–528. [Google Scholar] [CrossRef]
- Boneh, D.; Durfee, G.; Frankel, Y. An attack on RSA given a small fraction of the private key bits. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 1998; pp. 25–34. [Google Scholar]
- Heninger, N.; Shacham, H. Reconstructing RSA private keys from random key bits. In Advances in Cryptology-CRYPTO 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 1–17. [Google Scholar]
- Maitra, S.; Sarkar, S.; Gupta, S.S. Factoring RSA modulus using prime reconstruction from random known bits. In International Conference on Cryptology in Africa; Springer: Berlin/Heidelberg, Germany, 2010; pp. 82–99. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B.; Rohatgi, P. Introduction to differential power analysis. J. Cryptogr. Eng. 2011, 1, 5–27. [Google Scholar] [CrossRef]
- Kocher, P.C. Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1996; pp. 104–113. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Martinasek, Z.; Zeman, V.; Trasy, K. Simple electromagnetic analysis in cryptography. Int. J. Adv. Telecommun. Electrotech. Signals Syst. 2012, 1, 13–19. [Google Scholar] [CrossRef]
- Cho, J.; Kim, T.; Kim, S.; Im, M.; Kim, T.; Shin, Y. Real-Time Detection for Cache Side Channel Attack using Performance Counter Monitor. Appl. Sci. 2020, 10, 984. [Google Scholar] [CrossRef]
- Genkin, D.; Shamir, A.; Tromer, E. RSA key extraction via low-bandwidth acoustic cryptanalysis. In Annual Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2014; pp. 444–461. [Google Scholar]
- Ghafar, A.H.A.; Ariffin, M.R.K.; Asbullah, M.A. Extending Pollard Class of Factorable RSA Modulus. In Proceedings of the 6th International Cryptology and Information Security Conference 2018 (CRYPTOLOGY2018), Port Dickson, Negeri Sembilan, Malaysia, 9–11 July 2018; p. 103. [Google Scholar]
- Ghafar, A.; Ariffin, M.; Asbullah, M. A New Attack on Special-Structured RSA Primes. Malays. J. Math. Sci. 2019, 13, 111–125. [Google Scholar]
- Barker, E.; Dang, Q. Recommendation for Key Management, Part 1: General; NIST Special Publication 800-57 Part 1, Revision 4; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2016. [Google Scholar]
- Rivest, R.L.; Shamir, A. Efficient factoring based on partial information. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1985; pp. 31–34. [Google Scholar]
- Coppersmith, D. Finding a small root of a bivariate integer equation; factoring with high bits known. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1996; pp. 178–189. [Google Scholar]
- Herrmann, M.; May, A. Solving linear equations modulo divisors: On factoring given any bits. In International Conference on the Theory and Application of Cryptology and Information Security; Springer: Berlin/Heidelberg, Germany, 2008; pp. 406–424. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).