A Novel Method for Performance Improvement of Chaos-Based Substitution Boxes
Abstract
1. Introduction
2. Chaos-Based S-Box Structures
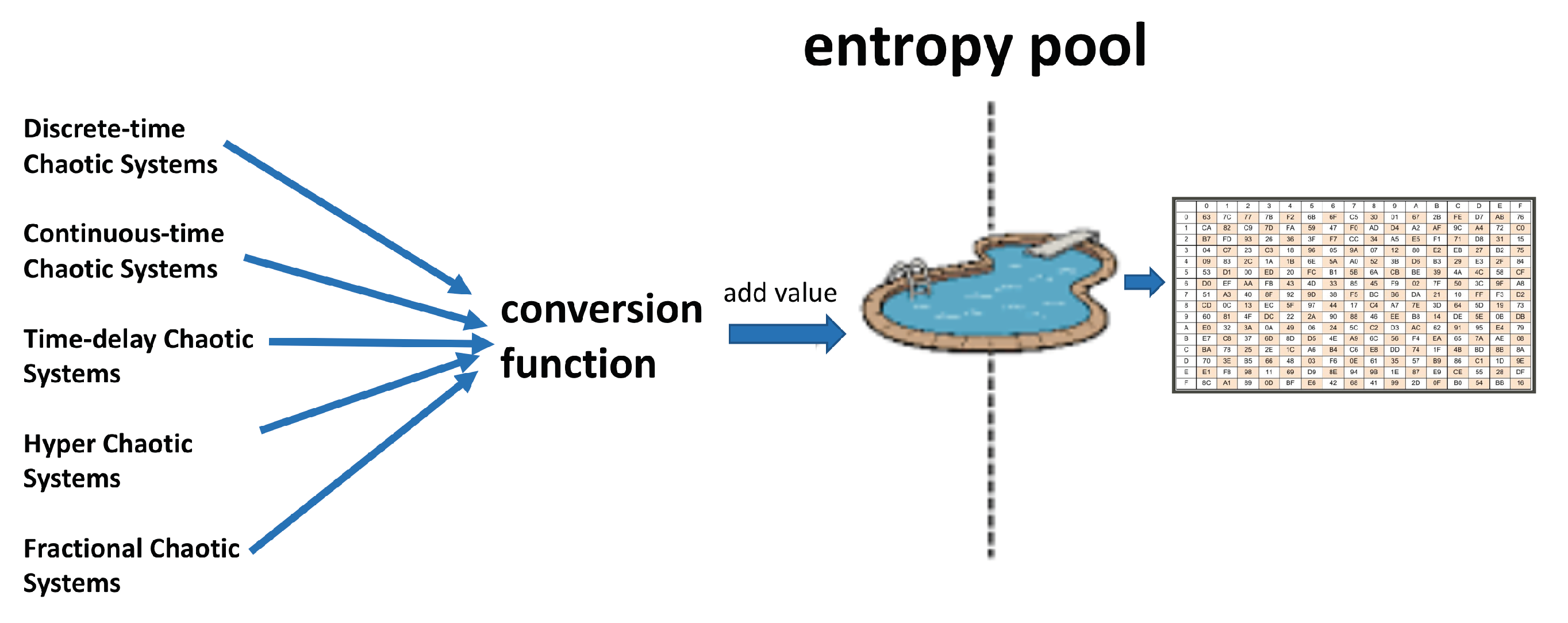
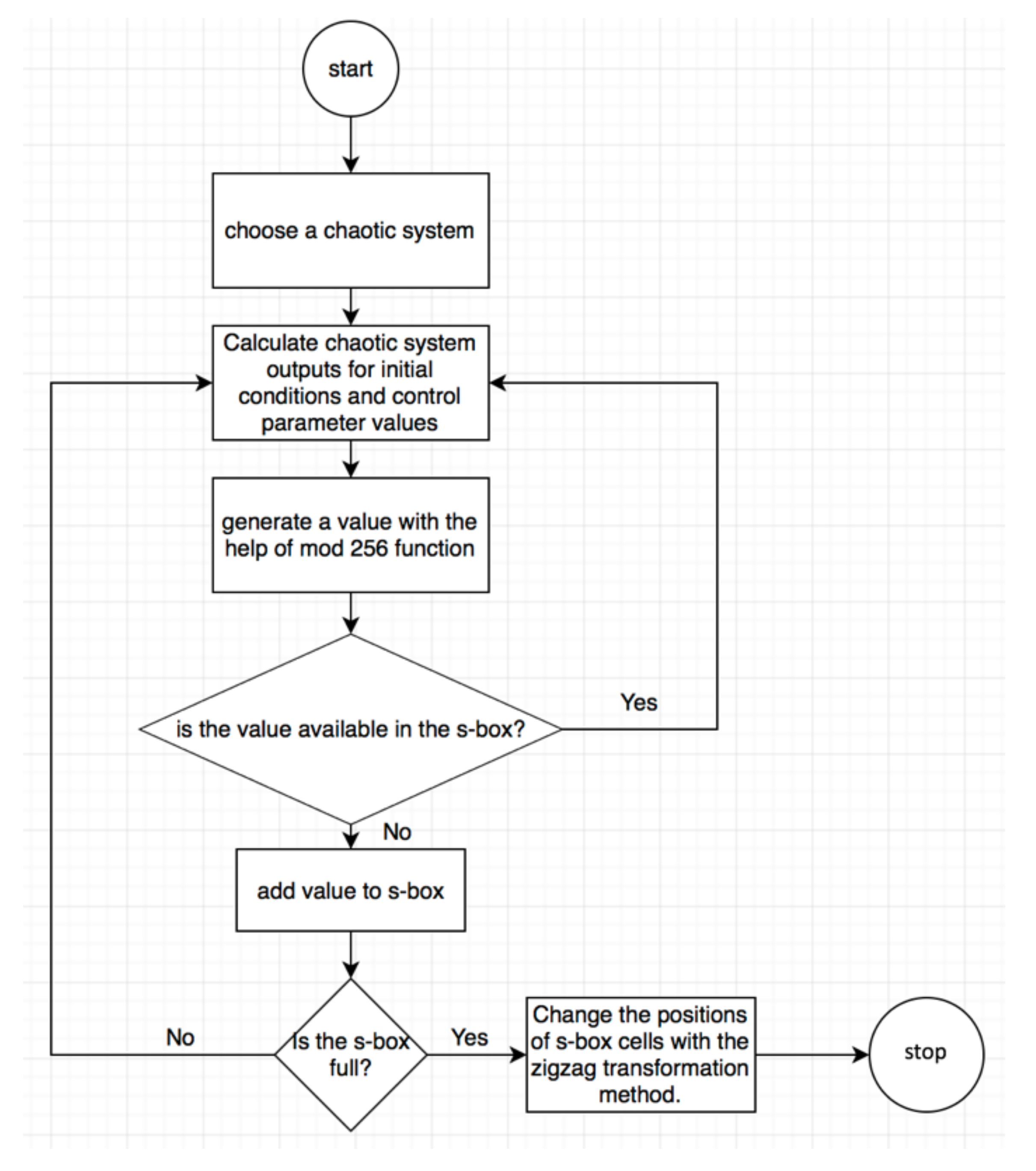
3. Detail of Proposed Method
- Step 1.
- A discrete or continuous time chaotic system is chosen.
- Step 2.
- The initial condition and control parameter values in which the chaotic system can exhibit rich random features are determined.
- Step 3.
- State variable(s) of the chaotic system are calculated. Preferably, the first 1000 values can be ignored to eliminate the effects of transient response.
- Step 4.
- The status variable value, which is the fractional value, is converted to a decimal value between 0–255 by applying mod 256.
- Step 5.
- If the decimal value is not included in the s-box, it is added, otherwise a new state variable value is calculated, which continues until the table is full.
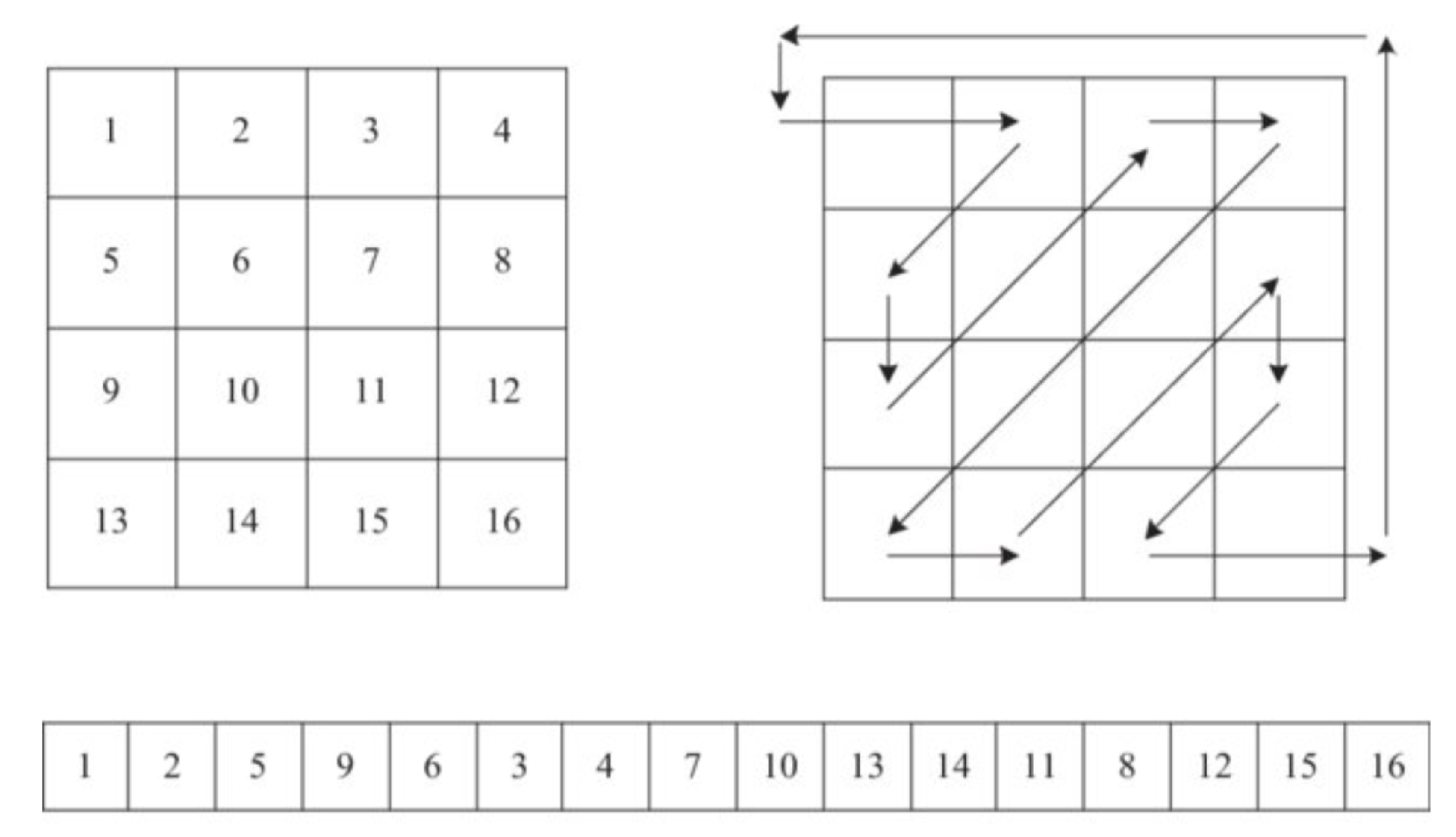
- Step 6.
- The positions of s-box cells are shuffled using zigzag transformation.
4. Performance Analysis of Proposed Method
5. Conclusions
- It has been shown that s-box performance criteria can be improved using a postprocessing algorithm.
- The proposed postprocessing algorithm for performance improvements has a simple and elegant structure.
- Speed, computational complexity, and user friendliness are strong features of the proposed method.
- Considering these advantages, it can be said that the proposed postprocessing algorithm is a more convenient method for performance improvement compared to the optimization algorithms described in the literature to date.
- The proposed method can give successful results, regardless of the chaotic system type and class.
- Only the s-box generator should not be considered as the output of the study. It has been shown that new designs can be developed that can be used as a counter measurement to prevent side channel attacks.
- Many different postprocessing algorithms can be developed to achieve performance improvements. An example is the displacement of s-box rows or columns.
- In this study, postprocessing was applied to only one s-box generator. The success of the proposed method on different s-box generators should be evaluated.
- The postprocessing technique gives successful results for the nonlinearity criteria of 103 and below. However, the question of how performance improvements can be achieved for designs with better nonlinearity measurements should be investigated.
- The fact that the performance improvement is independent of the chaotic system type and class reveals that the proposed method can produce successful outputs from different entropy sources. Performance improvements will be investigated for s-box structures that will be designed in the future using different entropy sources.
- The practical applicability of chaos-based s-box structures in the field of information security should be investigated.
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Li, C.; Zhang, Y.; Yong, E. When an attacker meets a cipher-image in 2018: A year in review. J. Inf. Sec. Appl. 2019, 48, 1–9. [Google Scholar] [CrossRef]
- Özkaynak, F. Brief Review on Application of Nonlinear Dynamics in Image Encryption. Nonlinear Dyn. 2018, 92, 305–313. [Google Scholar] [CrossRef]
- Cho, J.; Kim, T.; Kim, S.; Im, M.; Kim, T.; Shin, Y. Real-Time Detection for Cache Side Channel Attack using Performance Counter Monitor. Appl. Sci. 2020, 10, 984. [Google Scholar] [CrossRef]
- Açıkkapı, M.S.; Özkaynak, F.; Özer, A.B. Side-channel Analysis of Chaos-based Substitution Box Structures. IEEE Access 2019, 79030–79043. [Google Scholar] [CrossRef]
- Nyberg, K. Differentially uniform mappings for cryptography. In Workshop on the Theory and Application of of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1994; Volume 765, pp. 55–64. [Google Scholar]
- Daemen, J.; Rijmen, V. AES proposal: Rijndael. In Proceedings of the 1st Advanced Encryption Conference, Ventura, CA, USA, 20–22 August 1998; pp. 1–45. [Google Scholar]
- Özkaynak, F. Construction of Robust Substitution Boxes Based on Chaotic Systems. Neural Comp. Appl. 2019, 31, 3317–3326. [Google Scholar] [CrossRef]
- Strogatz, S. Nonlinear Dynamics and Chaos: With Applications to Physics, Biology, Chemistry, and Engineering (Studies in Nonlinearity); Westview Press: Boulder, CO, USA, 2001. [Google Scholar]
- Kocarev, L.; Lian, S. Chaos Based Cryptography Theory Algorithms and Applications; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Zhu, C.; Wang, G.; Sun, K. Cryptanalysis and Improvement on an Image Encryption Algorithm Design Using a Novel Chaos Based S-Box. Symmetry 2018, 10, 399. [Google Scholar] [CrossRef]
- Zhang, X.; Wang, X. Multiple-Image Encryption Algorithm Based on the 3D Permutation Model and Chaotic System. Symmetry 2018, 10, 660. [Google Scholar] [CrossRef]
- Ding, L.; Liu, C.; Zhang, Y.; Ding, Q. A New Lightweight Stream Cipher Based on Chaos. Symmetry 2019, 11, 853. [Google Scholar] [CrossRef]
- Demir, K.; Ergün, S. An Analysis of Deterministic Chaos as an Entropy Source for Random Number Generators. Entropy 2018, 20, 957. [Google Scholar] [CrossRef]
- Özkaynak, F. An Analysis and Generation Toolbox for Chaotic Substitution Boxes: A Case Study Based on Chaotic Labyrinth Rene Thomas System. Iran. J. Sci. Tech. Trans. Elect. Eng. 2020, 44, 89–98. [Google Scholar] [CrossRef]
- Cusick, T.; Stanica, P. Cryptographic Boolean Functions and Applications; Elsevier: Amsterdam, The Netherlands, 2009. [Google Scholar]
- Wu, C.; Feng, D. Boolean Functions and Their Applications in Cryptography; Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Ahmad, M. Random search based efficient chaotic substitution box design for image encryption. Int. J. Rough Sets Data Anal. 2018, 5, 131–147. [Google Scholar] [CrossRef]
- Hussain, I.; Anees, A.; Al-Maadeed, T.A.; Mustafa, M.T. Construction of S-Box Based on Chaotic Map and Algebraic Structures. Symmetry 2019, 11, 351. [Google Scholar] [CrossRef]
- Zahid, A.H.; Arshad, M.J. An Innovative Design of Substitution-Boxes Using Cubic Polynomial Mapping. Symmetry 2019, 11, 437. [Google Scholar] [CrossRef]
- Zhu, S.; Wang, G.; Zhu, C. A Secure and Fast Image Encryption Scheme Based on Double Chaotic S-Boxes. Entropy 2019, 21, 790. [Google Scholar] [CrossRef]
- Liu, H.; Zhao, B.; Huang, L. Quantum Image Encryption Scheme Using Arnold Transform and S-box Scrambling. Entropy 2019, 21, 343. [Google Scholar] [CrossRef]
- Lai, Q.; Akgul, A.; Li, C.; Xu, G.; Çavuşoğlu, Ü. A New Chaotic System with Multiple Attractors: Dynamic Analysis, Circuit Realization and S-Box Design. Entropy 2018, 20, 12. [Google Scholar] [CrossRef]
- Lu, Q.; Zhu, C.; Wang, G. A Novel S-Box Design Algorithm Based on a New Compound Chaotic System. Entropy 2019, 21, 1004. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, Y.; Wang, X. A Novel Method for Constructing the S-Box Based on Spatiotemporal Chaotic Dynamics. Appl. Sci. 2018, 8, 2650. [Google Scholar] [CrossRef]
- Wang, X.; Akgul, A.; Cavusoglu, U.; Pham, V.-T.; Vo Hoang, D.; Nguyen, X.Q. A Chaotic System with Infinite Equilibria and Its S-Box Constructing Application. Appl. Sci. 2018, 8, 2132. [Google Scholar] [CrossRef]
- Wang, X.; Çavuşoğlu, Ü.; Kacar, S.; Akgul, A.; Pham, V.-T.; Jafari, S.; Alsaadi, F.E.; Nguyen, X.Q. S-Box Based Image Encryption Application Using a Chaotic System without Equilibrium. Appl. Sci. 2019, 9, 781. [Google Scholar] [CrossRef]
- Al Solami, E.; Ahmad, M.; Volos, C.; Doja, M.N.; Beg, M.M.S. A New Hyperchaotic System-Based Design for Efficient Bijective Substitution-Boxes. Entropy 2018, 20, 525. [Google Scholar] [CrossRef]
- Islam, F.; Liu, G. Designing S-box based on 4D-4 wing hyperchaotic system. 3D Res. 2017, 8, 9. [Google Scholar] [CrossRef]
- Özkaynak, F.; Yavuz, S. Designing chaotic S-boxes based on time-delay chaotic system. Nonlinear Dyn. 2013, 74, 551–557. [Google Scholar] [CrossRef]
- Khan, M.; Shah, T.; Batool, S.I. Construction of S-box based on chaotic Boolean functions and its application in image encryption. Neural Comp. Appl. 2016, 27, 677–685. [Google Scholar] [CrossRef]
- Özkaynak, F.; Çelik, V.; Özer, A.B. A New S-Box Construction Method Based on the Fractional Order Chaotic Chen System. Signal Image Video Proc. 2017, 11, 659–664. [Google Scholar] [CrossRef]
- Zahid, A.H.; Arshad, M.J.; Ahmad, M. A Novel Construction of Efficient Substitution-Boxes Using Cubic Fractional Transformation. Entropy 2019, 21, 245. [Google Scholar] [CrossRef]
- Tanyıldızı, E.; Özkaynak, F. A New Chaotic S-Box Generation Method Using Parameter Optimization of One Dimensional Chaotic Maps. IEEE Access 2019, 117829–117838. [Google Scholar] [CrossRef]
- Anees, A.; Hussain, I. A Novel Method to Identify Initial Values of Chaotic Maps in Cybersecurity. Symmetry 2019, 11, 140. [Google Scholar] [CrossRef]
- Özkaynak, F. On the Effect of Chaotic System in Performance Characteristics of Chaos Based S-box Designs. Phys. A Stat. Mech. Appl. 2020, 124072. [Google Scholar] [CrossRef]
- Stoyanova, B.; Ivanova, T. CHAOSA: Chaotic map based random number generator on Arduino platform. AIP Conf. Proc. 2019, 2172, 090001. [Google Scholar] [CrossRef]
- Zhu, S.; Zhu, C.; Wang, W. A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256. Entropy 2018, 20, 716. [Google Scholar] [CrossRef]
- Yang, C.-H.; Chien, Y.-S. FPGA Implementation and Design of a Hybrid Chaos-AES Color Image Encryption Algorithm. Symmetry 2020, 12, 189. [Google Scholar] [CrossRef]
- Available online: http://www.kriptarium.com/symmetry.html (accessed on 3 November 2019).
- Shang, Y. Hybrid consensus for averager-copier-voter networks with non-rational agents. Chaos Solitons Fractals 2018, 110, 244–251. [Google Scholar] [CrossRef]
- Shang, Y. Consensus of hybrid multi-agent systems with malicious nodes. IEEE Trans. Circuits Syst. II Express Briefs 2019. [Google Scholar] [CrossRef]
| ChaoticSboxGenerate() begin sbox=[0:255] for(k=0;k<256;I++) sbox[k]=-1 end for xOld= Random_Selection [0,1] for(i=0;I<1000;I++) xNew=4*xOld*(1-xOld) xOld=xNex end for j=0; while (j<sbox.lenght) value=(xNex*100000000)%256 if(!contain(sbox,value)) sbox[j]=value j++; end if xNew=r*xOld*(1-xOld) xOld=xNex end while return ZigZagTransform(sbox) end contain(array, value) begin for(int i=0;i<array.length;i++) if(array[i]==value) return true end if end for return false end |
| Performance Criteria for Original S-box | Performance Criteria for Improved S-box | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Name. | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR |
| L.map_1 | 100.75 | 0.4971 | 102.71 | 0.4992 | 12 | 105 | 0.5046 | 103.64 | 0.5009 | 10 |
| L.map_2 | 102.5 | 0.5051 | 104.86 | 0.5012 | 12 | 103 | 0.5056 | 102.93 | 0.5004 | 12 |
| L.map_3 | 102.75 | 0.502 | 103.21 | 0.5022 | 12 | 104.5 | 0.5027 | 102.93 | 0.4983 | 12 |
| L.map_4 | 103.5 | 0.4985 | 104.29 | 0.4981 | 10 | 104.75 | 0.5049 | 103.71 | 0.4979 | 10 |
| L.map_5 | 101.75 | 0.4998 | 103.21 | 0.4996 | 10 | 104.5 | 0.4983 | 103.64 | 0.5011 | 12 |
| L.map_6 | 103.25 | 0.4976 | 103.64 | 0.4968 | 10 | 103.75 | 0.4973 | 103.29 | 0.5013 | 12 |
| L.map_7 | 102 | 0.5051 | 103.07 | 0.5017 | 12 | 104.25 | 0.491 | 103.64 | 0.501 | 12 |
| L.map_8 | 101.25 | 0.5056 | 103.29 | 0.503 | 12 | 103.75 | 0.4934 | 103.86 | 0.4962 | 12 |
| L.map_9 | 103.75 | 0.5059 | 102.64 | 0.4997 | 10 | 104.5 | 0.4907 | 103.86 | 0.4978 | 10 |
| L.map_10 | 103 | 0.5015 | 104.71 | 0.5023 | 12 | 104.5 | 0.498 | 103.5 | 0.5018 | 10 |
| L.map_11 | 103.5 | 0.5012 | 103.36 | 0.4999 | 10 | 104 | 0.4998 | 104.14 | 0.5018 | 12 |
| L.map_12 | 103.25 | 0.5049 | 103.64 | 0.4948 | 10 | 103.5 | 0.5 | 102.36 | 0.4978 | 12 |
| L.map_13 | 102.25 | 0.5042 | 103.64 | 0.503 | 12 | 103.25 | 0.5022 | 104.07 | 0.4963 | 10 |
| L.map_14 | 102 | 0.512 | 103.36 | 0.4969 | 12 | 103 | 0.4971 | 102.86 | 0.5007 | 12 |
| L.map_15 | 102.75 | 0.5007 | 103.86 | 0.5001 | 10 | 103.25 | 0.5088 | 104 | 0.5005 | 12 |
| L.map_16 | 101 | 0.5039 | 103.07 | 0.4976 | 10 | 103.5 | 0.5005 | 102.86 | 0.4974 | 12 |
| L.map_17 | 102.5 | 0.5134 | 102.86 | 0.5 | 10 | 103.5 | 0.5056 | 104.29 | 0.4978 | 10 |
| L.map_18 | 103.5 | 0.499 | 103.64 | 0.4941 | 12 | 103.75 | 0.5161 | 103.64 | 0.4957 | 10 |
| L.map_19 | 102.75 | 0.5073 | 102.93 | 0.5037 | 12 | 103.75 | 0.5002 | 102.5 | 0.5018 | 10 |
| L.map_20 | 103.25 | 0.491 | 103 | 0.4951 | 10 | 104 | 0.5042 | 103,5 | 0.4993 | 10 |
| L.map_21 | 102.5 | 0.5078 | 102.86 | 0.4985 | 10 | 103.75 | 0.5154 | 103.64 | 0.5013 | 14 |
| L.map_22 | 102.75 | 0.4966 | 103.71 | 0.4997 | 10 | 103.75 | 0.5066 | 103 | 0.4973 | 12 |
| L.map_23 | 102.25 | 0.5012 | 103.5 | 0.5015 | 12 | 103.25 | 0.5044 | 103.36 | 0.5022 | 12 |
| L.map_24 | 102.5 | 0.5068 | 104.36 | 0.4986 | 12 | 104.25 | 0.511 | 104.21 | 0.5006 | 10 |
| L.map_25 | 103.25 | 0.5012 | 103.29 | 0.4992 | 12 | 104.24 | 0.5071 | 104.71 | 0.5027 | 10 |
| Performance Criteria for Original S-box | Performance Criteria for Improved S-box | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Name. | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR |
| S.map_1 | 101.75 | 0.5122 | 104.07 | 0.4985 | 14 | 103.5 | 0.4924 | 103.64 | 0.4911 | 12 |
| S.map _2 | 103 | 0.5046 | 102.86 | 0.4964 | 12 | 104.5 | 0.5027 | 103.64 | 0.4977 | 10 |
| S.map _3 | 102.25 | 0.4988 | 102.5 | 0.498 | 12 | 104.25 | 0.4978 | 103.93 | 0.5017 | 12 |
| S.map _4 | 103 | 0.5063 | 103.79 | 0.5029 | 12 | 104.5 | 0.5034 | 103.43 | 0.5013 | 12 |
| S.map _5 | 103.25 | 0.4973 | 103.57 | 0.4978 | 12 | 104.5 | 0.51 | 103.93 | 0.5006 | 12 |
| S.map _6 | 102.5 | 0.51 | 104 | 0.4967 | 12 | 103 | 0.511 | 103.64 | 0.4921 | 10 |
| S.map _7 | 103.5 | 0.501 | 102.79 | 0.4991 | 12 | 103.75 | 0.5093 | 103.5 | 0.504 | 10 |
| S.map _8 | 102.5 | 0.5002 | 104.07 | 0.5005 | 12 | 105 | 0.5083 | 103.79 | 0.5029 | 10 |
| S.map _9 | 103.75 | 0.5002 | 103.57 | 0.495 | 12 | 104 | 0.5103 | 103 | 0.4988 | 12 |
| S.map _10 | 101.5 | 0.4973 | 103.57 | 0.4981 | 10 | 103.25 | 0.4934 | 104 | 0.499 | 12 |
| S.map _11 | 103.75 | 0.4934 | 104.29 | 0.4999 | 12 | 104.5 | 0.5083 | 104.5 | 0.4952 | 12 |
| S.map _12 | 102 | 0.5054 | 103 | 0.4963 | 12 | 103 | 0.5103 | 103.43 | 0.4963 | 12 |
| S.map _13 | 102.5 | 0.4993 | 104.29 | 0.4967 | 14 | 103.75 | 0.4971 | 103 | 0.501 | 12 |
| S.map _14 | 101.5 | 0.5007 | 103.64 | 0.501 | 10 | 102.5 | 0.5056 | 104.14 | 0.5003 | 10 |
| S.map _15 | 102 | 0.499 | 103.71 | 0.5003 | 12 | 102.75 | 0.498 | 103.71 | 0.4957 | 12 |
| S.map _16 | 103 | 0.5002 | 104.07 | 0.5026 | 12 | 130.25 | 0.5166 | 103 | 0.4925 | 12 |
| S.map _17 | 101.75 | 0.4973 | 102.86 | 0.4995 | 12 | 102 | 0.4961 | 103.43 | 0.4998 | 10 |
| S.map _18 | 103 | 0.5022 | 103.07 | 0.4972 | 10 | 103.5 | 0.4988 | 103.14 | 0.499 | 10 |
| S.map _19 | 102.75 | 0.4978 | 103.43 | 0.4998 | 10 | 104.75 | 0.4976 | 103.07 | 0.5005 | 12 |
| S.map _20 | 103.25 | 0.4973 | 103.21 | 0.4959 | 12 | 104.75 | 0.501 | 103.86 | 0.5013 | 12 |
| S.map _21 | 102.25 | 0.4934 | 103.21 | 0.4978 | 10 | 104.5 | 0.4998 | 104.14 | 0.5029 | 12 |
| S.map _22 | 103.25 | 0.5017 | 102.86 | 0.4987 | 12 | 105 | 0.5029 | 105.07 | 0.5017 | 10 |
| S.map _23 | 103 | 0.5012 | 103.57 | 0.5014 | 12 | 103.75 | 0.5107 | 104.36 | 0.4997 | 12 |
| S.map _24 | 103 | 0.5078 | 103.71 | 0.4994 | 10 | 103.75 | 0.5059 | 104 | 0.5007 | 10 |
| S.map _25 | 102.75 | 0.5044 | 103.14 | 0.5009 | 10 | 103.25 | 0.5005 | 103.29 | 0.5021 | 12 |
| Performance Criteria for Original S-box | Performance Criteria for Improved S-box | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Name. | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR |
| C.map_1 | 102.25 | 0.5098 | 102.93 | 0.495 | 12 | 104.25 | 0.5015 | 102.79 | 0.5031 | 10 |
| C.map_2 | 103.5 | 0.5027 | 103.29 | 0.501 | 10 | 105.5 | 0.5042 | 103.64 | 0.5055 | 10 |
| C.map_3 | 102.75 | 0.5029 | 104.14 | 0.4902 | 12 | 105.75 | 0.5005 | 103.07 | 0.495 | 10 |
| C.map_4 | 103.5 | 0.4915 | 103.43 | 0.4973 | 10 | 104.25 | 0.5005 | 102.86 | 0.4974 | 10 |
| C.map_5 | 102 | 0.5115 | 103.57 | 0.4965 | 12 | 102.5 | 0.5007 | 104.07 | 0.501 | 12 |
| C.map_6 | 103.25 | 0.5105 | 102.93 | 0.5022 | 12 | 104.5 | 0.4917 | 103.29 | 0.4988 | 10 |
| C.map_7 | 102.25 | 0.498 | 102.93 | 0.5024 | 12 | 104.25 | 0.502 | 103.64 | 0.4983 | 12 |
| C.map_8 | 100.75 | 0.4998 | 104.07 | 0.4961 | 12 | 105 | 0.4954 | 103.71 | 0.5026 | 12 |
| C.map_9 | 102 | 0.498 | 103.07 | 0.5009 | 12 | 102.75 | 0.5066 | 103.86 | 0.4977 | 10 |
| C.map_10 | 103.25 | 0.4978 | 103.36 | 0.5017 | 12 | 103.5 | 0.5037 | 103 | 0.4986 | 14 |
| C.map_11 | 103 | 0.4946 | 103 | 0.5034 | 14 | 104.25 | 0.5007 | 103.5 | 0.5004 | 12 |
| C.map_12 | 103.5 | 0.4944 | 103.29 | 0.5019 | 12 | 105.25 | 0.4976 | 103.43 | 0.4946 | 10 |
| C.map_13 | 103.5 | 0.4932 | 102.71 | 0.502 | 10 | 104 | 0.5 | 103.36 | 0.4957 | 12 |
| C.map_14 | 103.25 | 0.5061 | 103.21 | 0.4982 | 10 | 105.5 | 0.5039 | 103.29 | 0.4995 | 10 |
| C.map_15 | 102 | 0.4951 | 104.63 | 0.5052 | 10 | 104.25 | 0.5029 | 103.93 | 0.5015 | 10 |
| C.map_16 | 102.25 | 0.4968 | 104 | 0.4957 | 10 | 104 | 0.5037 | 104.86 | 0.5044 | 10 |
| C.map_17 | 102.75 | 0.4939 | 104.07 | 0.5012 | 10 | 104.5 | 0.4924 | 103.79 | 0.4971 | 12 |
| C.map_18 | 102.75 | 0.5083 | 102 | 0.4979 | 10 | 103 | 0.5015 | 104.21 | 0.4983 | 10 |
| C.map_19 | 103 | 0.51 | 103 | 0.5017 | 10 | 104.25 | 0.4978 | 103.71 | 0.4976 | 10 |
| C.map_20 | 101.5 | 0.5078 | 103 | 0.5011 | 12 | 103.25 | 0.5034 | 102.5 | 0.5025 | 14 |
| C.map_21 | 101.75 | 0.501 | 102.43 | 0.4977 | 10 | 102.25 | 0.4993 | 104 | 0.4992 | 10 |
| C.map_22 | 102 | 0.5027 | 103 | 0.4925 | 10 | 102.25 | 0.5112 | 103.71 | 0.5014 | 10 |
| C.map_23 | 103 | 0.4976 | 103.14 | 0.5002 | 10 | 103.75 | 0.4937 | 102.57 | 0.4995 | 14 |
| C.map_24 | 102.75 | 0.4917 | 104.57 | 0.4983 | 10 | 103.75 | 0.4956 | 104.79 | 0.5004 | 12 |
| C.map_25 | 101.75 | 0.5171 | 102.86 | 0.5014 | 12 | 104.75 | 0.5073 | 102.79 | 0.4966 | 10 |
| Performance Criteria for Original S-box | Performance Criteria for Improved S-box | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Name. | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR |
| Lorenz_1 | 101.5 | 0.4902 | 103.64 | 0.4988 | 10 | 103.75 | 0.4973 | 103.21 | 0.5041 | 12 |
| Lorenz _2 | 103.25 | 0.5044 | 103.29 | 0.5063 | 12 | 105 | 0.5037 | 102.79 | 0.4989 | 12 |
| Lorenz _3 | 101.75 | 0.5063 | 103.36 | 0.4911 | 12 | 103 | 0.4998 | 103 | 0.4985 | 12 |
| Lorenz _4 | 102.75 | 0.5042 | 103.5 | 0.5005 | 12 | 104.25 | 0.5027 | 103.21 | 0.5013 | 10 |
| Lorenz _5 | 103.75 | 0.5095 | 104.86 | 0.4928 | 12 | 104.25 | 0.5024 | 103 | 0.5039 | 12 |
| Lorenz _6 | 103.5 | 0.4944 | 103.79 | 0.5015 | 12 | 105.5 | 0.4937 | 104 | 0.4991 | 10 |
| Lorenz _7 | 102.5 | 0.5027 | 103.21 | 0.4959 | 12 | 106.25 | 0.4929 | 104.07 | 0.499 | 14 |
| Lorenz _8 | 102.25 | 0.4978 | 103.14 | 0.5002 | 14 | 103.25 | 0.4912 | 103.21 | 0.5029 | 12 |
| Lorenz _9 | 102.25 | 0.4954 | 104.21 | 0.5 | 12 | 105.5 | 0.499 | 103.07 | 0.4957 | 12 |
| Lorenz _10 | 103.25 | 0.5029 | 103.36 | 0.4959 | 12 | 103.75 | 0.5068 | 103.43 | 0.5028 | 12 |
| Lorenz _11 | 101.5 | 0.5002 | 104.07 | 0.5018 | 10 | 103.75 | 0.4961 | 103.07 | 0.5036 | 12 |
| Lorenz _12 | 101.25 | 0.5085 | 103.71 | 0.4981 | 10 | 103 | 0.5015 | 103.29 | 5033 | 12 |
| Lorenz _13 | 101 | 0.5029 | 103.64 | 0.4989 | 10 | 105 | 0.5039 | 103.21 | 0.4993 | 12 |
| Lorenz _14 | 102.75 | 0.4934 | 103.93 | 0.4938 | 12 | 104.5 | 0.4988 | 103.5 | 0.4992 | 12 |
| Lorenz _15 | 103.25 | 0.4995 | 103 | 0.4996 | 10 | 103.5 | 0.4985 | 103.29 | 0.5045 | 10 |
| Lorenz _16 | 103 | 0.4961 | 103.07 | 0.4987 | 14 | 103.25 | 0.5071 | 104.07 | 0.5008 | 12 |
| Lorenz _17 | 103.75 | 0.5093 | 103.57 | 0.5015 | 12 | 104.25 | 0.4917 | 103.86 | 0.4958 | 14 |
| Lorenz _18 | 102.75 | 0.5068 | 103.07 | 0.4994 | 10 | 103.25 | 0.4939 | 103.29 | 0.499 | 12 |
| Lorenz _19 | 101.25 | 0.4998 | 102.79 | 0.5029 | 12 | 103 | 0.491 | 104.79 | 0.5029 | 10 |
| Lorenz _20 | 103.25 | 0.5098 | 102.79 | 0.5015 | 10 | 104.25 | 0.499 | 103.57 | 0.4973 | 10 |
| Lorenz _21 | 103.5 | 0.4973 | 103.21 | 0.4959 | 12 | 103.75 | 0.4971 | 102.71 | 0.4985 | 12 |
| Lorenz _22 | 103.25 | 0.5046 | 103.21 | 0.4964 | 12 | 104.24 | 0.4988 | 103.29 | 0.4986 | 12 |
| Lorenz _23 | 102.75 | 0.5017 | 103 | 0.504 | 12 | 103.75 | 0.5007 | 103.86 | 0.4991 | 12 |
| Lorenz _24 | 103.5 | 0.5005 | 103.14 | 0.5007 | 10 | 103.75 | 0.4978 | 102.43 | 0.4964 | 12 |
| Lorenz _25 | 102.75 | 0.5017 | 104.14 | 0.5003 | 12 | 105.5 | 0.4993 | 103.71 | 0.4993 | 12 |
| Performance Criteria for Original S-box | Performance Criteria for Improved S-box | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Name. | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR |
| Thomas_1 | 101.75 | 0.5046 | 103.86 | 0.5018 | 10 | 103.5 | 0.4966 | 103.86 | 0.4997 | 10 |
| Thomas _2 | 103.25 | 0.4993 | 103.29 | 0.4995 | 10 | 104.5 | 0.4932 | 103.07 | 0.4971 | 12 |
| Thomas _3 | 102.5 | 0.5039 | 104.43 | 0.4937 | 12 | 104 | 0.5002 | 103.5 | 0.5022 | 12 |
| Thomas _4 | 103.5 | 0.5132 | 104.07 | 0.4962 | 12 | 104 | 0.5032 | 102.93 | 0.4957 | 12 |
| Thomas _5 | 102.5 | 0.5037 | 103.64 | 0.4982 | 12 | 104 | 0.5022 | 103.86 | 0.5033 | 14 |
| Thomas _6 | 103.25 | 0.51 | 103.29 | 0.499 | 12 | 104.25 | 0.5015 | 103.36 | 0.4952 | 10 |
| Thomas _7 | 103.25 | 0.4944 | 103.36 | 0.4967 | 12 | 104.25 | 0.5034 | 104.14 | 0.5047 | 10 |
| Thomas _8 | 103 | 0.5054 | 102.93 | 0.502 | 12 | 104.75 | 0.5137 | 103.57 | 0.502 | 12 |
| Thomas _9 | 103.25 | 0.4893 | 103.43 | 0.4962 | 12 | 105.25 | 0.5088 | 103.64 | 0.5017 | 12 |
| Thomas _10 | 102 | 0.4963 | 104.07 | 0.4939 | 12 | 105.5 | 0.5095 | 103.71 | 0.4992 | 10 |
| Thomas _11 | 103 | 0.5071 | 102.79 | 0.4975 | 10 | 104 | 0.502 | 103.29 | 0.496 | 10 |
| Thomas _12 | 102 | 0.4976 | 104.71 | 0.4963 | 12 | 103 | 0.5149 | 103.43 | 0.5031 | 12 |
| Thomas _13 | 102.25 | 0.5037 | 103.14 | 0.4941 | 10 | 103.5 | 0.5083 | 103.5 | 0.4999 | 10 |
| Thomas _14 | 102.75 | 0.5 | 103.36 | 0.5001 | 10 | 103 | 0.4971 | 103.14 | 0.5008 | 12 |
| Thomas _15 | 103.25 | 0.5117 | 102.29 | 0.4978 | 10 | 104 | 0.5063 | 104.07 | 0.4951 | 12 |
| Thomas _16 | 103 | 0.5017 | 102.64 | 0.502 | 10 | 104 | 0.5105 | 103.86 | 0.5037 | 12 |
| Thomas _17 | 101 | 0.4961 | 103.07 | 0.501 | 12 | 104.25 | 0.4897 | 103.86 | 0.498 | 10 |
| Thomas _18 | 102.5 | 0.5056 | 103.86 | 0.4994 | 10 | 103.5 | 0.5078 | 103.57 | 0.5047 | 10 |
| Thomas _19 | 103.5 | 0.4995 | 103.14 | 0.5017 | 10 | 103.75 | 0.4924 | 103.21 | 0.4967 | 14 |
| Thomas _20 | 103 | 0.5078 | 103.5 | 0.4971 | 10 | 104.5 | 0.5012 | 104.07 | 0.5006 | 12 |
| Thomas _21 | 103.25 | 0.5095 | 104 | 0.4996 | 12 | 104 | 0.5049 | 103 | 0.4983 | 10 |
| Thomas _22 | 103 | 0.5027 | 104.14 | 0.5009 | 10 | 103.75 | 0.4998 | 104.21 | 0.5017 | 10 |
| Thomas _23 | 102.5 | 0.5088 | 104 | 0.5021 | 12 | 104 | 0.5056 | 104.57 | 0.4983 | 10 |
| Thomas _24 | 102.5 | 0.5051 | 104.14 | 0.4969 | 12 | 104.5 | 0.4998 | 103.5 | 0.498 | 10 |
| Thomas _25 | 103.25 | 0.4983 | 102.86 | 0.5059 | 12 | 103.5 | 0.4951 | 103.79 | 0.5001 | 10 |
| Performance Criteria for Original S-box | Performance Criteria for Improved S-box | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Name. | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR | Average Nonlinearity | SAC | BIC-Non. | BIC-SAC | XOR |
| Chua_1 | 103.75 | 0.4922 | 103.64 | 0.4988 | 14 | 104.25 | 0.5051 | 103.64 | 0.4999 | 10 |
| Chua _2 | 103.75 | 0.4995 | 103.29 | 0.494 | 12 | 104.75 | 0.5078 | 104.21 | 0.4943 | 12 |
| Chua _3 | 102.25 | 0.4939 | 103.79 | 0.506 | 12 | 105.5 | 0.5063 | 102.86 | 0.5001 | 12 |
| Chua _4 | 103.25 | 0.5032 | 104.57 | 0.5054 | 10 | 105 | 0.51 | 103.21 | 0.5046 | 10 |
| Chua _5 | 103.5 | 0.4954 | 103 | 0.5028 | 12 | 103.75 | 0.4956 | 103.5 | 0.4948 | 10 |
| Chua _6 | 103.5 | 0.5034 | 103.29 | 0.502 | 12 | 104.25 | 0.5027 | 104 | 0.4973 | 10 |
| Chua _7 | 103 | 0.5027 | 103.57 | 0.5024 | 12 | 103.75 | 0.5051 | 103.21 | 0.4995 | 12 |
| Chua _8 | 102.5 | 0.5029 | 104.29 | 0.5015 | 10 | 104 | 0.5068 | 103.21 | 0.4994 | 10 |
| Chua _9 | 102.75 | 0.5059 | 103.29 | 0.5011 | 10 | 105.25 | 0.5034 | 103.5 | 0.5009 | 12 |
| Chua _10 | 103 | 0.4956 | 103.43 | 0.4958 | 12 | 104.5 | 0.5027 | 103.57 | 0.4986 | 12 |
| Chua _11 | 102.75 | 0.5022 | 103.36 | 0.4971 | 12 | 104.25 | 0.4968 | 103.79 | 0.498 | 12 |
| Chua _12 | 103.75 | 0.5039 | 103.43 | 0.4999 | 10 | 104.75 | 0.4976 | 104.07 | 0.5018 | 12 |
| Chua _13 | 101.75 | 0.498 | 104.07 | 0.4981 | 12 | 104.75 | 0.4985 | 103.57 | 0.4993 | 12 |
| Chua _14 | 102 | 0.5 | 103.64 | 0.4994 | 12 | 103.5 | 0.5024 | 104.29 | 0.502 | 12 |
| Chua _15 | 102.5 | 0.5049 | 104 | 0.4994 | 10 | 103.5 | 0.5029 | 103.36 | 0.5037 | 12 |
| Chua _16 | 103 | 0.4939 | 103.29 | 0.4993 | 14 | 104.25 | 0.5081 | 102.71 | 0.5006 | 10 |
| Chua _17 | 103 | 0.5044 | 103.86 | 0.502 | 12 | 105.5 | 0.4998 | 103.57 | 0.4979 | 12 |
| Chua _18 | 103 | 0.4922 | 103.64 | 0.5012 | 12 | 103.5 | 0.4983 | 102.29 | 0.4979 | 12 |
| Chua _19 | 102.75 | 0.5034 | 104.57 | 0.4998 | 12 | 104.25 | 0.5 | 103.57 | 0.4931 | 10 |
| Chua _20 | 103.25 | 0.5056 | 103.79 | 0.4992 | 12 | 103.5 | 0.4922 | 102.5 | 0.4976 | 12 |
| Chua _21 | 102.25 | 0.5007 | 103.14 | 0.5065 | 12 | 103.5 | 0.4956 | 103.07 | 0.4956 | 14 |
| Chua _22 | 103.25 | 0.4917 | 103.36 | 0.4985 | 10 | 105 | 0.5088 | 103.5 | 0.4937 | 12 |
| Chua _23 | 101.25 | 0.4995 | 103.36 | 0.493 | 12 | 103.75 | 0.4915 | 103.29 | 0.4992 | 12 |
| Chua _24 | 103 | 0.5103 | 102.79 | 0.4929 | 14 | 104.5 | 0.5007 | 103.64 | 0.5042 | 10 |
| Chua _25 | 102.75 | 0.499 | 103.57 | 0.4985 | 12 | 103.25 | 0.5034 | 103 | 0.5013 | 12 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Artuğer, F.; Özkaynak, F. A Novel Method for Performance Improvement of Chaos-Based Substitution Boxes. Symmetry 2020, 12, 571. https://doi.org/10.3390/sym12040571
Artuğer F, Özkaynak F. A Novel Method for Performance Improvement of Chaos-Based Substitution Boxes. Symmetry. 2020; 12(4):571. https://doi.org/10.3390/sym12040571
Chicago/Turabian StyleArtuğer, Fırat, and Fatih Özkaynak. 2020. "A Novel Method for Performance Improvement of Chaos-Based Substitution Boxes" Symmetry 12, no. 4: 571. https://doi.org/10.3390/sym12040571
APA StyleArtuğer, F., & Özkaynak, F. (2020). A Novel Method for Performance Improvement of Chaos-Based Substitution Boxes. Symmetry, 12(4), 571. https://doi.org/10.3390/sym12040571





