Abstract
The integration of Internet of things (IoT) and cloud computing technology has made our life more convenient in recent years. Cooperating with cloud computing, Internet of things can provide more efficient and practical services. People can accept IoT services via cloud servers anytime and anywhere in the IoT-based cloud computing environment. However, plenty of possible network attacks threaten the security of users and cloud servers. To implement effective access control and secure communication in the IoT-based cloud computing environment, identity authentication is essential. In 2016, He et al. put forward an anonymous authentication scheme, which is based on asymmetric cryptography. It is claimed that their scheme is capable of withstanding all kinds of known attacks and has good performance. However, their scheme has serious security weaknesses according to our cryptanalysis. The scheme is vulnerable to insider attack and DoS attack. For overcoming these weaknesses, we present an improved authentication and key agreement scheme for IoT-based cloud computing environment. The automated security verification (ProVerif), BAN-logic verification, and informal security analysis were performed. The results show that our proposed scheme is secure and can effectively resist all kinds of known attacks. Furthermore, compared with the original scheme in terms of security features and performance, our proposed scheme is feasible.
1. Introduction
Internet of things (IoT) takes advantage of massive sensors, intelligent terminals, global positioning system, and other technologies to establish connections between people and things whenever and wherever, and realize intelligent control and management [1]. For example, users can use smartphones to remotely control lamps, TVs, and refrigerators at home through the Internet of things. Internet of things makes people’s lives more convenient, and also makes the social economy develop faster. However, limited by the low power and computation ability of embedded devices, applying the IoT in the real applications is still a critical issue. To settle the matter, researchers apply cloud computing to the Internet of things.
Cloud computing makes plentiful computing and storage resources accessible to all of the servers and users through the Internet. A cloud server has more resources and more powerful computation ability. Cooperating with the cloud server, IoT devices can provide a better quality of services for users [2]. In a typical scenario of the IoT-based cloud computing environment as shown in Figure 1, IoT devices and sensors submit the IoT-releated data they collected to a cloud server via a wired/wireless network. Users can access the cloud servers to get the IoT-releated data from anywhere at any time. Furthermore, Users can send commands to the IoT devices through the cloud server for productive remote control. The IoT-based cloud computing environment combines the advantages of IoT and cloud computing, making the Internet of things more efficient and practical.
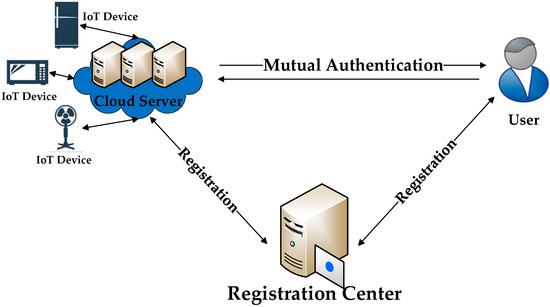
Figure 1.
Proposed model of an IoT-based cloud computing environment.
As the cloud servers provide IoT services for users over an insecure public channel, the communications between users and cloud servers must be confidential [3]. It is essential to authenticate each other in an IoT-based cloud computing environment. Only authorized users can access the cloud server to obtain the services of IoT devices. Figure 1 shows the assumed architecture for an IoT-based cloud computing environment. As a trusted third party, the registration center (RC) provides registration services for users and cloud servers. After that, users and cloud servers establish secure communication through mutual authentication.
Authentication and key agreement protocols are playing a crucial part in the security of an IoT-based cloud computing environment. Since the first authentication scheme was put forward by Lamport in 1980 [4], the research on the authentication protocol has not stopped. Numerous schemes were proposed based on different cryptography technologies. Generally, the scheme using symmetric key cryptography [5,6,7,8,9,10,11,12,13,14] has better performance while it cannot achieve forward security. For the scheme using asymmetric cryptography [15,16,17,18,19,20,21,22,23], the balance between security and performance is a crucial problem.
In 2016, He et al. presented an anonymous authentication protocol [24], which is based on asymmetric cryptography. They declared that their scheme is capable of withstanding various known attacks and has good performance. However, we found that their scheme is vulnerable to DoS attack and insider attack under our proposed adversary model.
Contributions
The main contributions of this article include: (1) we propose a new adversary model in Section 2.3. (2) In Section 4, we show that He et al.’s scheme is unable to defend against insider attack and DoS attack under our proposed adversary model. (3) In Section 5, we present an improved authentication and key agreement scheme for the IoT-based cloud computing environment. The proposed scheme modifies the registration and authentication phases, uses ‘fuzzy verifier’, and adds the validation in the side of cloud servers, so as to effectively resist insider attack and DoS attack. (4) It is proven that our proposed scheme is secure via an automated security verification tool ProVerif [25] in Section 6.1. Meanwhile, we present the proofs of BAN logic [26] verification in Section 6.2. Furthermore, informal security analysis is put forward in Section 6.3. (5) In Section 7, we compare the proposed scheme with He et al.’s scheme in terms of security features and performance.
2. Preliminaries
2.1. Bilinear Pairing
Let be a cyclic additive group with a large prime order and a cyclic multiplicative group of the same order . Let and be generators of and separately. A bilinear pairing is a map and satisfies the following properties:
(1) Bilinear: Give for all .
(2) Non-degenerate: There exists such that .
(3) Computable: There exists an efficient algorithm to calculate for all in polynomial time.
2.2. Related Mathematical Problems
The mathematical problems for designing authentication protocols are as follows.
2.2.1. Discrete Logarithm Problem
Given , where , it is relatively easy to calculate given τ and P ( and g), while it is relatively hard to determine given X and P (x and g).
2.2.2. Computational Diffie–Hellman Problem
For , given , it is hard to find .
2.3. Adversary Model
The adversary model makes clear assumptions about the adversary’s ability in advance. The adversary model of remote authentication protocol always follows the classic Dolev–Yao model [27]. Recently, Side-channel technology [28] enables attackers to extract information from smart cards, and the ability of the adversary is enhanced. In this paper, we improve the adversary models in literature [29] and literature [30], and propose a more rigorous (but practical) multi-factor authentication protocol adversary model (see Table 1).

Table 1.
The capabilities of adversaries.
In real life, when someone finds the lost smart card and the owner cannot be found, usually, the person who finds the smart card will give it to the insider to find the owner. Therefore, it is possible for insiders to obtain users’ smart cards. Meanwhile, the insiders have the opportunity to obtain the user’s registration information. Thus, is realistic.
3. Review of He et al.’s Scheme
This section briefly reviews the authentication scheme proposed by He et al. There are the following phases in their scheme. Table 2 shows the notations used herein.

Table 2.
Notations.
3.1. Setup Phase
RC selects and chooses his private keys . Then, it calculates , , as public keys. Furthermore, RC selects seven secure hash functions and publishes all public parameters.
3.2. User Registration Phase
- 1.
- chooses , and a random number freely. Then, computers . Finally, sends the registration message towards RC.
- 2.
- RC selects freely and computes , , , , . Then, RC transmits towards .
- 3.
- writes into .
3.3. Cloud Server Registration Phase
- 1.
- transmits to RC.
- 2.
- RC calculates and responses to via a private channel.
- 3.
- receives and stores safely.
3.4. Login and Authentication Phase
- 1.
- inserts to a reader, and inputs and . verifies the equality check for . If it holds true, ensures that and are correct. Then, randomly generates a number and calculates , . Finally, transmits a login request towards .
- 2.
- receives and calculates . Then, randomly chooses a number and calculates , . Finally, responds towards .
- 3.
- receives and checks the equality for . If , terminates the session. Otherwise, calculates , , , the session key and . Finally, transmits towards cloud server .
- 4.
- receives and recovers , , via computing . Furthermore, calculates , and checks the equality for . If it holds true, gets the session key .
3.5. Password Modification Phase
- 1.
- inputs , . checks the equality .
- 2.
- If , rejects the modification request. Otherwise, inputs . chooses a new random number , calculates , . Finally, SC replaces with and the new password is .
4. Cryptanalysis of He et al.’s Scheme
4.1. Insider Attack
In our proposed adversary model, an insider adversary is able to acquire the user’s registration information and smart card. Suppose an insider adversary acquires the registration information of . Furthermore, gets ’s smart card and extracts the values , , and . Using this information, can launch the following attacks through the following procedure.
4.1.1. Offline Password Guessing
Suppose an insider being an adversary knows the registration information of . Furthermore, gets ’s smart card and extracts the values , , and . Using this information, is able to launch an offline password guessing attack through following these steps:
- 1.
- guesses a candidate password .
- 2.
- calculates .
- 3.
- checks whether holds. If not, repeats Steps 1–3 until he acquires a true password. Otherwise, has already succeeded in getting the true password. The attack is finished.
The computational overhead of this offline password attack is , where is the running time of one-way hash function, and and are the spaces of user identity and password, respectively. According to [31,32], we have . According to experiment data in [33], we have . The adversary can obtain the true password in seven days. If using a high-performance cloud computing platform, the attack can be completed in a few hours.
4.1.2. User Impersonation
- 1.
- randomly generates a number and calculates , . Afterwards, transmits the request to server .
- 2.
- Upon receiving from , computes , , where and were obtained before. Subsequently, calculates , and gets the session key . Finally, sends to .The information generated by is legal. The cloud server considers as the user .
4.2. Possible DoS Attack
In the authentication phase, doesn’t validate the login request information until formula is validated. Even if the adversary sends illegal information, the cloud server still responds and completes the relevant calculations. This results in unnecessary communication costs and time costs and leads a possible DoS attack.
5. Our Improved Scheme
For overcoming the weaknesses above, we put forward an enhanced authentication and key agreement protocol. Figure 2 depicts our proposed scheme.
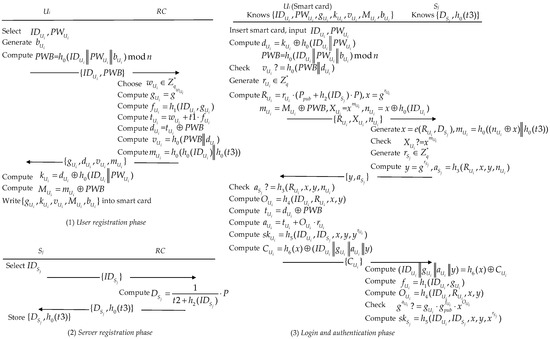
Figure 2.
The conceptual architecture of our proposed protocol.
5.1. Setup Phase
RC selects and chooses his private keys . Then, RC calculates , , as public keys. Furthermore, RC selects seven secure hash functions . Finally, RC publishes all public parameters .
5.2. User Registration Phase
- 1.
- chooses , and a number freely. Then, computers . Note that is an integer that determines the capacity of . Then, it transmits the registration message towards RC.
- 2.
- RC selects freely and computes , , , , , . Then, RC responses to via a private secure channel.
- 3.
- receives and computes , . Finally, writes into .
5.3. Cloud Server Registration Phase
- 1.
- sends to RC.
- 2.
- Upon reception of , RC calculates and sends to via a private channel.
- 3.
- stores in secret.
5.4. Login and Authentication Phase
- 1.
- inserts to the reader and inputs and . calculates , and verifies the equality check for . If , rejects the login request. Otherwise, it randomly chooses and calculates , , , , . Finally, transmits login request towards .
- 2.
- receives and calculates , . Then, verifies the equality check . If , terminates the session. Otherwise, randomly selects and calculates , . Finally, transmits towards .
- 3.
- Upon reception of from , verifies the equality check . If , terminates the session. Otherwise, calculates , , , the session key and . Finally, transmits towards .
- 4.
- receives and recovers , and via computing . Furthermore, calculates , and checks the equality for . If it holds true, gets the session key .
5.5. Password Modification Phase
- 1.
- inputs , . computes , and checks the equality .
- 2.
- If , rejects the request. Otherwise, inputs . randomly generates and calculates , . Finally, replaces with .
6. Security Analysis
6.1. Security Verification Using ProVerif
ProVerif [25] is one of the most widely used automated security verification tools. The security validation of ProVerif works on applied π calculus, and ProVerif can verify the authentication and confidentiality of authentication protocol. We elaborate the design process and results of security validation using ProVerif in this section.
First, we define two channels for communication between participants, an insecure channel Pch and a secure channel SEch.
(*--Channels--*)
free SEch:channel [private]. (* Secure Channel *)
free Pch:channel. (*Insecure Channel *)
Then, public and private parameters and constructors are defined as follows:
(*----------------Variable and constants---------------------*)
const P: bitstring.
const g: bitstring.
const q: bitstring.
const n: bitstring.
free Uid: bitstring. (* User ID *)
free PWi: bitstring [private]. (* Password of user *)
free bUi:bitstring. (* Random number of user in registration phase *)
free Sid: bitstring. (* Server ID *)
free t1, t2, t3: bitstring [private]. (* Private key of RC *)
free Ppub: bitstring. (* Ppub = t2. P *)
free gpub: bitstring. (* gpub = Exp (g, t1) *)
(*----------------Constructor---------------------*)
fun CONCAT (bitstring, bitstring): bitstring. (* CONCAT operation *)
fun Div1 (bitstring): bitstring. (* Division operation and get the first part *)
fun Div2 (bitstring): bitstring. (* Division operation and get the second part *)
fun h0 (bitstring): bitstring. (* Hash operation h0 *)
fun h1 (bitstring,bitstring): bitstring. (* Hash operation h1 *)
fun h2 (bitstring): bitstring. (* Hash operation h2 *)
fun h3 (bitstring,bitstring,bitstring,bitstring):bitstring. (* Hash operation h3 *)
fun h4 (bitstring,bitstring,bitstring,bitstring):bitstring. (* Hash operation h4 *)
fun h5 (bitstring,bitstring,bitstring,bitstring,bitstring): bitstring. (* Hash operation h5 *)
fun h6 (bitstring): bitstring. (* Hash operation h6 *)
fun Xor (bitstring, bitstring): bitstring. (* XOR operation *)
fun Smul (bitstring, bitstring): bitstring. (* Scalar multiplication operation *)
fun Padd (bitstring, bitstring): bitstring. (* Point addition operation *)
fun BPL (bitstring, bitstring): bitstring. (* Bilinear paring operation *)
fun Exp (bitstring, bitstring): bitstring. (* Exponentiation operation *)
fun Mod (bitstring, bitstring): bitstring. (* Mod operation *)
fun Mul (bitstring, bitstring): bitstring. (* multiplication operation *)
fun Add (bitstring, bitstring): bitstring. (* Addition operation *)
fun Inverse (bitstring): bitstring. (* inverse operation *)
The following four events are specified to check authentication between the user and server:
(*----------------Events---------------------*)
event beginUserUi (bitstring).
event endUserUi (bitstring).
event beginServerSj (bitstring).
event endServerSj (bitstring).
The processes UserUi, ServerSj, and RC represent , and RC, respectively.
(*----------------Processes---------------------*)
(*----------------User Ui---------------------*)
let UserUi =
(* Registration Phase *)
let PWB = Mod (h0 (CONCAT (CONCAT (Uid, PWi), bUi)), n) in
out (SEch, (Uid, PWB));
in (SEch, (gUi: bitstring, dUi:bitstring, vUi:bitstring, mUi:bitstring));
let kUi = Xor (dUi, h0(CONCAT (Uid, PWi))) in
let MUi = Xor (mUi, PWB) in
(*Login and Authentication Phase *)
event beginUserUi (Uid);
let PWB = Mod (h0 (CONCAT (CONCAT (Uid, PWi), bUi)), n) in
let dUi = Xor (kUi, h0 (CONCAT (Uid, PWi))) in
let vUi’ = h0 (CONCAT (PWB, dUi)) in
if vUi’ = vUi then
new rUi:bitstring;
let RUi = Smul (rUi, Padd (Ppub, Smul (h2 (Sid), P))) in
let x = Exp (g, rUi) in
let mUi = Xor (MUi, PWB) in
let XUi = Exp (x, mUi) in
let nUi = Xor (x, h0 (Uid)) in
out (Pch, (RUi, XUi, nUi));
in (Pch, (y:bitstring, aSj:bitstring ));
let aSj’ = h3 (RUi, x, y, nUi) in
if (aSj = aSj’) then
let oUi = h4 (Uid,RUi, x, y) in
let tUi = Xor (dUi, PWB) in
let aUi = Add (tUi, Mul (oUi, rUi)) in
let SKij = h5 (Uid,Sid, x, y, Exp (y, rUi)) in
let CUi = Xor (h6 (x), CONCAT (CONCAT (CONCAT (Uid, gUi), aUi), y)) in
out (Pch, CUi);
event endUserUi (Uid)
else
0.
(*----------------Server Sj---------------------*)
let ServerSj =
(* Registration Phase *)
out (SEch, Sid);
in (SEch, (DSj: bitstring, ht3: bitstring));
(* Login and Authentication Phase *)
event beginServerSj (Sid);
in (Pch, (RUi: bitstring, XUi:bitstring, nUi:bitstring));
let x = BPL (RUi, DSj) in
let mUi = h0 (CONCAT (Xor (nUi, x), ht3)) in
let XUi’ = Exp (x, mUi) in
if XUi’ = XUi then
new rSj: bitstring;
let y = Exp (g, rSj) in
let aSj = h3 (RUi, x, y, nUi) in
out (Pch, (y, aSj));
in (Pch, CUi:bitstring);
let aUi = Div2 (Div1 (Xor (h6 (x), CUi))) in
let gUi = Div2 (Div1 (Div1 (Xor (h6 (x), CUi)))) in
let Uid = Div1 (Div1 (Div1 (Xor (h6 (x), CUi)))) in
let fUi = h1 (Uid, gUi) in
let oUi = h4 (Uid, RUi, x, y) in
let gaUi = Exp (g, aUi) in
let gaUi’ = Mul (Mul (gUi, Exp (gpub, fUi)), Exp (x,oUi)) in
if gaUi = gaUi’ then
let SKij = h5 (Uid, Sid, x, y, Exp (x, rSj)) in
event endServerSj (Sid)
else
0.
(*----------------Registration Centre RC---------------------*)
let RC =
(* Registration with User *)
in (SEch, (Uid: bitstring, PWB: bitstring));
new wUi: bitstring;
let gUi = Exp (g, wUi) in
let fUi = h1 (Uid, gUi) in
let tUi = Add (wUi, Mul (t1, fUi)) in
let dUi = Xor (tUi, PWB) in
let vUi = Mod (h0 (CONCAT (PWB, dUi)), n) in
let mUi = h0 (CONCAT (h0 (Uid), h0(t3))) in
out (SEch, (gUi, dUi, vUi, mUi));
(*Registration with Servers*)
in (SEch, Sid: bitstring);
let DSj = Inverse (Add (t2, h2(Sid))) in
let ht3 = h0(t3) in
out (SEch, (DSj, ht3));
0.
We simulate our proposed protocol as unbounded parallel execution of the three processes mentioned:
process
((! UserUi) | (! RC) | (! ServerSj))
The following queries are used to test mutual authentication and session key security of the improved protocol.
(*-------------Queries-----------------*)
free SKij: bitstring [private].
query attacker (SKij).
query id: bitstring; inj-event (endUserUi (id)) = = > inj-event (beginUserUi (id)).
query id: bitstring; inj-event (endServerSj (id)) = = > inj-event (beginServerSj (id)).
At last, we get the simulation result:

According to RESULT 2 and RESULT 3, mutual authentication between and succeeded. Furthermore, RESULT 1 indicates that no adversary is capable of exposing the session key.
6.2. Formal Security Analysis Using BAN-Logic
Burrows–Abadi–Needham logic [26] is a modal logic based on belief, which is proposed by Burrows et al. We use BAN-logic to prove that user and server have succeeded in session key agreement. Table 3 is the BAN-logic notations and the basic BAN-logic rules are shown in Table 4.

Table 3.
BAN logic notations.

Table 4.
Basic BAN-logic rules.
6.2.1. Idealized Form
Message 1:
Message 2:
Message 3:
6.2.2. Verification Purposes
Purpose 1: .
Purpose 2: .
Purpose 3: .
Purpose 4: .
6.2.3. Assumptions about Initial State
Assumption 1: .
Assumption 2: .
Assumption 3: .
Assumption 4: .
Assumption 5:
Assumption 6: .
Assumption 7:
6.2.4. Proofs
- 1.
- According to Message 2, we get the following: .
- 2.
- According to Assumption 3 and the message-meaning rule, we get the following: .
- 3.
- Based on Assumption 1 and the freshness–conjuncatenation rule, we can prove: .
- 4.
- From Step 2, Step 3, and the nonce-verification rule, we obtain the following: .
- 5.
- According to Step 4 and believe rule, .
- 6.
- According to Step 5, Assumption 3 and , we prove that: (Purpose 2).
- 7.
- Based on Step 6, Assumption 6, and jurisdiction rule, we prove that: (Purpose 1).
- 8.
- From Message 3, we get: .
- 9.
- Based on Assumption 4 and the message-meaning rule, we obtain the following: .
- 10.
- From Assumption 2 and the freshness-conjuncatenation rule, we can obtain: .
- 11.
- Based on Step 9, Step 10, and the nonce-verification rule, we obtain the following: .
- 12.
- According to Assumption 5, Step 11, , and the believe rule, we obtain the following: .
- 13.
- According to Step 12, Assumption 4, and , we prove that: (Purpose 4).
- 14.
- According to Step 13, Assumption 7, and jurisdiction rule, we prove that: (Purpose 3).
From Purposes 1–4, and believe that the session key has been established between them successfully.
6.3. Informal Security Analysis
6.3.1. Anonymity and Untraceability
In authentication phase, the adversary can intercept the login request information from users and the response information from cloud servers. The constructions of , and are related to , , , . Obviously, under the protection of shared secret and hash function, the adversary is unable to obtain . On the other hand, the generation of is affected by random number , so the parameters , and generated by in each session changes. Even if an adversary intercepts and other information, he can’t judge whether two sessions come from the same user, and can’t track the user’s access behavior effectively.
6.3.2. Forward Secrecy
Suppose the adversary captured the private keys and intercepts propagated in the public channel. The adversary can calculate through the private key, but he can’t calculate and in polynomial time, so the adversary is unable to capture session key .
6.3.3. Two-Factor Security
It is obviously less difficult for adversary to break through the user’s password than for smart cards. In the proposed scheme, the process of verification is a fuzzy verification process, . Even if guessed by the adversary has passed the verification of the smart card, it still needs to go through the online login authentication process to determine whether it is correct. Specifically, an adversary needs to log in online times to get the correct password, about times, the cloud server can easily resist this attack.
6.3.4. Session Key Agreement
In the proposed scheme, and reach a session key for future communication after the login and authentication phase is completed, .
6.3.5. Resistance of Other Attacks
Insider attack: In our proposed adversary model, an insider can acquire user’s registration information and smart card parameter . Since PWB is generated by modulo operation, the insider adversary cannot directly acquire via offline password guessing. On the other hand, when the insider adversary wants to authenticate with the cloud server as , he cannot compute . Therefore, no effective attack can be launched.
Cloud Server Spoofing Attack: If the adversary wants to complete authentication with user as cloud server , he needs to generate legal response information; however, only when the adversary gets can he generate legal login request information. Therefore, the attack is unfeasible.
Replay attack: In the improved scheme, the change of random number and will affect the login request information and cloud server response information. As a result, the replay attack cannot be launched.
DoS attack: Different from He et al.’s scheme, verifies ’s login request before subsequent operations in the improved scheme . Only legitimate users could generate legitimate login information, so the improved scheme is capable of withstanding DoS attack.
According to the above analysis, we know that an insider adversary cannot guess the user’s password offline and impersonate a user, even if he obtains the user’s smart card and registration information. As a result, offline password guessing attack, stolen smart card attack, and user impersonation attack are unfeasible.
7. The Comparisons of Security and Performance
We compare the proposed protocol with [24] in terms of security features. The comparisons are demonstrated in Table 5.

Table 5.
Comparison of security features.
We compare the proposed protocol with [24] in terms of time complexity. Since RC is usually regarded as a powerful device, our efficiency analysis focuses on users and servers. For the sake of convenience, we define to represent time of bilinear paring operation, point scalar multiplication operation, point addition operation, exponentiation operation, and hash function respectively.
The XOR operation, concatenate operation, the modular multiplication, and modular operation are neglected while comparing with the related operation mentioned above. Based on the experiments conducted on a Quad-core 2.45G processor with 2 GB memory and an I5-4460S 2.90GHz processor with 4 GB memory in [24], we get the running time of above operations in Table 6.

Table 6.
The running time of related operations based on [24].
All participants register with RC only once, and users do not change their passwords frequently. Therefore, the computation cost of registration phase and password modification phase is not discussed. Table 7 summarizes the results of efficiency comparison.

Table 7.
Comparison of computation cost.
8. Conclusions
Numerous research efforts on authentication and key agreement scheme can be witnessed in recent years. In 2016, He et al. proposed an anonymous authentication protocol using asymmetric cryptography, which is looking promising. However, we discovered vulnerabilities of their scheme under our proposed adversary model. Furthermore, we propose an improved authentication and key agreement scheme for IoT-based cloud computing environment, and provide ProVerif tool verification and formal security analysis via BAN-logic. The comparisons of security and performance show that the computational cost of our proposed scheme is slightly higher but is much safer than the original scheme.
Author Contributions
Y.Y. and L.H. proposed the adversary model and designed the scheme; J.C. performed the security analysis. All authors have read and agreed to the published version of the manuscript.
Funding
This research is funded by: National Key R&D Plan of China under Grant No. 2017YFA0604500, and by National Sci-Tech Support Plan of China under Grant No. 2014BAH02F00, and by National Natural Science Foundation of China under Grant No. 61701190, and by Youth Science Foundation of Jilin Province of China under Grant No. 20160520011JH & 20180520021JH, and by Youth Sci-Tech Innovation Leader and Team Project of Jilin Province of China under Grant No. 20170519017JH, and by Key Technology Innovation Cooperation Project of Government and University for the whole Industry Demonstration under Grant No. SXGJSF2017-4, and by Key scientific and technological R&D Plan of Jilin Province of China under Grant No. 20180201103GX, Project of Jilin Province Development and Reform Commission No. 2019FGWTZC001.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yang, H.; Kumara, S.; Bukkapatnam, S.T.S.; Tsung, F. The internet of things for smart manufacturing: A review. IISE Trans. 2019, 51, 1190–1216. [Google Scholar] [CrossRef]
- Dang, L.M.; Piran, M.; Han, D.; Min, K.; Moon, H. A Survey on Internet of Things and Cloud Computing for Healthcare. Electronics 2019, 8, 768. [Google Scholar] [CrossRef]
- Grobauer, B.; Walloschek, T.; Stocker, E. Understanding cloud computing vulnerabilities. IEEE Secur. Priv. 2010, 9, 50–57. [Google Scholar] [CrossRef]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Wang, B.; Ma, M. A smart card based efficient and secured multi-server authentication scheme. Wirel. Pers. Commun. 2013, 68, 361–378. [Google Scholar] [CrossRef]
- Sahoo, J.; Das, A.K.; Goswami, A. An efficient approach for mining association rules from high utility itemsets. Expert Syst. Appl. 2015, 42, 5754–5778. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Yang, X.; Yang, Y. Robust biometrics based authentication and key agreement scheme for multi-server environments using smart cards. PLoS ONE 2015, 10, e0126323. [Google Scholar] [CrossRef]
- Zhou, L.; Li, X.; Yeh, K.H.; Su, C.; Chiu, W. Lightweight IoT-based authentication scheme in cloud computing circumstance. Future Gener. Comput. Syst. 2019, 91, 244–251. [Google Scholar] [CrossRef]
- Li, X.; Wen, Q.; Li, W.; Zhang, H.; Jin, Z. A biometric-based password authentication with key exchange scheme using mobile device for multi-server environment. Appl. Math. Inf. Sci. 2015, 9, 1123. [Google Scholar]
- Amin, R.; Islam, S.K.H.; Gope, P.; Choo, K.K.R.; Tapas, N. Anonymity preserving and lightweight multi-medical server authentication protocol for telecare medical information system. IEEE J. Biomed. Health Inform. 2018, 23, 1749–1759. [Google Scholar] [CrossRef]
- Lwamo, N.M.R.; Zhu, L.; Xu, C.; Sharif, K.; Liu, X.; Zhang, C. SUAA: A Secure User Authentication Scheme with Anonymity for the Single & Multi-server Environments. Inf. Sci. 2019, 477, 369–385. [Google Scholar]
- Cui, J.; Zhang, X.; Cao, N.; Zhang, D.; Ding, J.; Li, G. An improved authentication protocol–based dynamic identity for multi-server environments. Int. J. Distrib. Sens. Netw. 2018, 14, 1550147718777654. [Google Scholar] [CrossRef]
- Renuka, K.; Kumar, S.; Kumari, S.; Chen, C.M. Cryptanalysis and Improvement of a Privacy-Preserving Three-Factor Authentication Protocol for Wireless Sensor Networks. Sensors 2019, 19, 4625. [Google Scholar] [CrossRef] [PubMed]
- Amin, R.; Islam, S.K.H.; Kumar, N.; Choo, K.K.R. An untraceable and anonymous password authentication protocol for heterogeneous wireless sensor networks. J. Netw. Comput. Appl. 2018, 104, 133–144. [Google Scholar] [CrossRef]
- Mohit, P.; Amin, R.; Karati, A.; Biswas, G.P.; Khan, M.K. A standard mutual authentication protocol for cloud computing based health care system. J. Med. Syst. 2017, 41, 50. [Google Scholar] [CrossRef]
- Xu, G.; Qiu, S.; Ahmad, H.; Xu, G.; Guo, Y.; Zhang, M.; Xu, H. A multi-server two-factor authentication scheme with un-traceability using elliptic curve cryptography. Sensors 2018, 18, 2394. [Google Scholar] [CrossRef]
- Chandrakar, P.; Om, H. A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC. Comput. Commun. 2017, 110, 26–34. [Google Scholar] [CrossRef]
- Ying, B.; Nayak, A. Lightweight remote user authentication protocol for multi-server 5G networks using self-certified public key cryptography. J. Netw. Comput. Appl. 2019, 131, 66–74. [Google Scholar] [CrossRef]
- Hou, J.L.; Yeh, K.H. Novel authentication schemes for IoT based healthcare systems. Int. J. Distrib. Sens. Netw. 2015, 11, 183659. [Google Scholar] [CrossRef]
- Tomar, A.; Dhar, J. An ECC Based Secure Authentication and Key Exchange Scheme in Multi-server Environment. Wirel. Pers. Commun. 2019, 107, 351–372. [Google Scholar] [CrossRef]
- Qi, M.; Chen, J. Anonymous biometrics-based authentication with key agreement scheme for multi-server environment using ECC. Multimed. Tools Appl. 2019, 78, 27553–27568. [Google Scholar] [CrossRef]
- Tseng, Y.M.; Huang, S.S.; Tsai, T.T.; Ke, J.H. List-free ID-based mutual authentication and key agreement protocol for multiserver architectures. IEEE Trans. Emerg. Top. Comput. 2015, 4, 102–112. [Google Scholar] [CrossRef]
- Wang, H.; Guo, D.; Zhang, H.; Wen, Q. Robust Multiple Servers Architecture Based Authentication Scheme Preserving Anonymity. Sensors 2019, 19, 3144. [Google Scholar] [CrossRef] [PubMed]
- He, D.; Zeadally, S.; Kumar, N.; Wu, W. Efficient and anonymous mobile user authentication protocol using self-certified public key cryptography for multi-server architectures. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2052–2064. [Google Scholar] [CrossRef]
- Blanchet, B.; Smyth, B.; Cheval, V.; Sylvestre, M. ProVerif 2.00: Automatic Cryptographic Protocol Verifier, User Manual and Tutorial. 2018. Available online: https://prosecco.gforge.inria.fr/personal/bblanche/proverif (accessed on 9 January 2020).
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. Lond. A Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Veyrat-Charvillon, N.; Standaert, F.X. Generic side-channel distinguishers: Improvements and limitations. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 354–372. [Google Scholar]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2014, 12, 428–442. [Google Scholar] [CrossRef]
- Huang, X.; Xiang, Y.; Chonka, A.; Zhou, J.; Deng, R.H. A generic framework for three-factor authentication: Preserving security and privacy in distributed systems. IEEE Trans. Parallel Distrib. Syst. 2010, 22, 1390–1397. [Google Scholar] [CrossRef]
- Das, M.L.; Saxena, A.; Gulati, V.P. A dynamic ID-based remote user authentication scheme. IEEE Trans. Consum. Electron. 2004, 50, 629–631. [Google Scholar] [CrossRef]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Wang, D.; Gu, Q.; Cheng, H.; Wang, P. The request for better measurement: A comparative evaluation of two-factor authentication schemes. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016; ACM: New York, NY, USA, 2016; pp. 475–486. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).