Reliability Enhancement of Edge Computing Paradigm Using Agreement
Abstract
:1. Introduction
2. Related Works
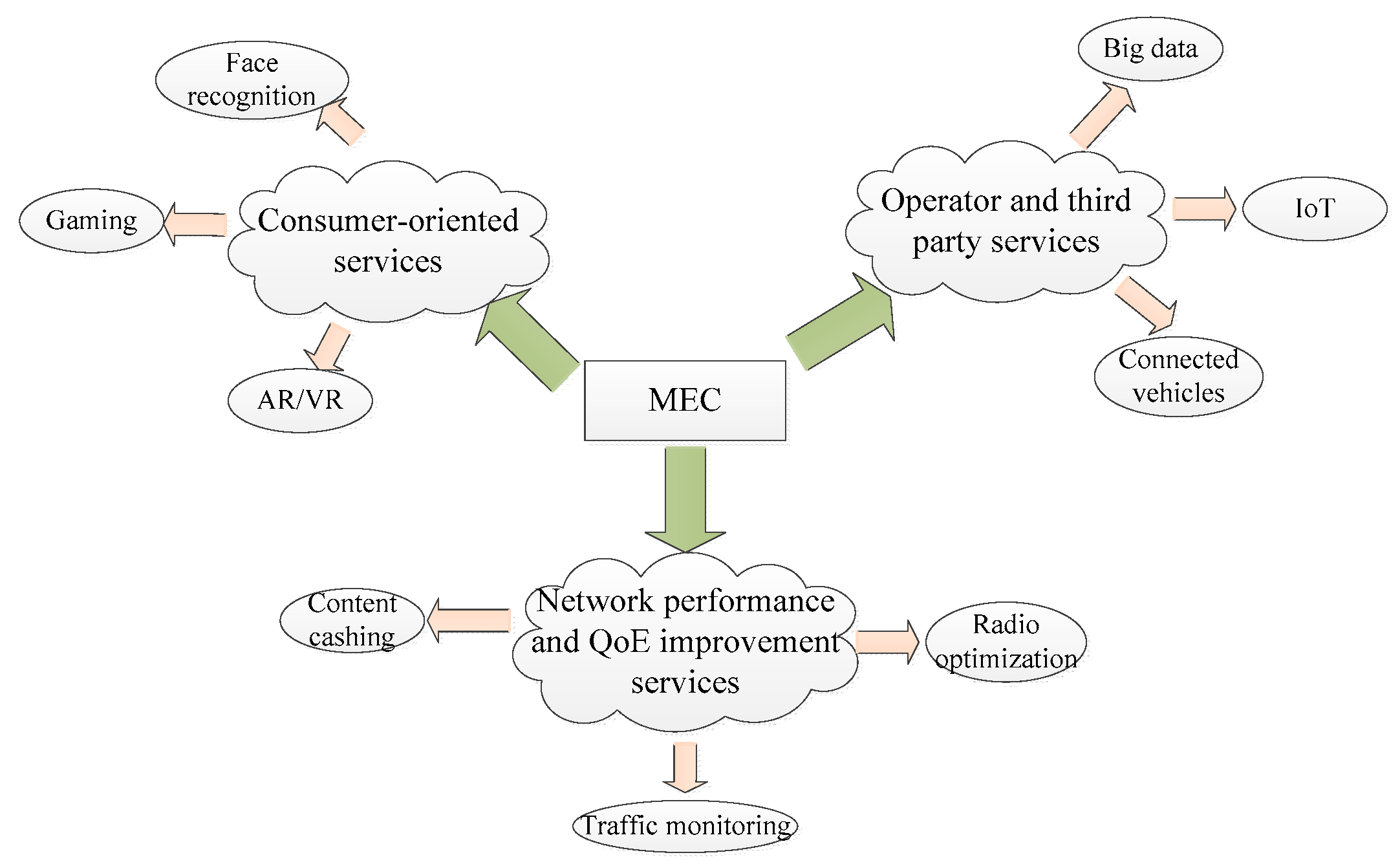
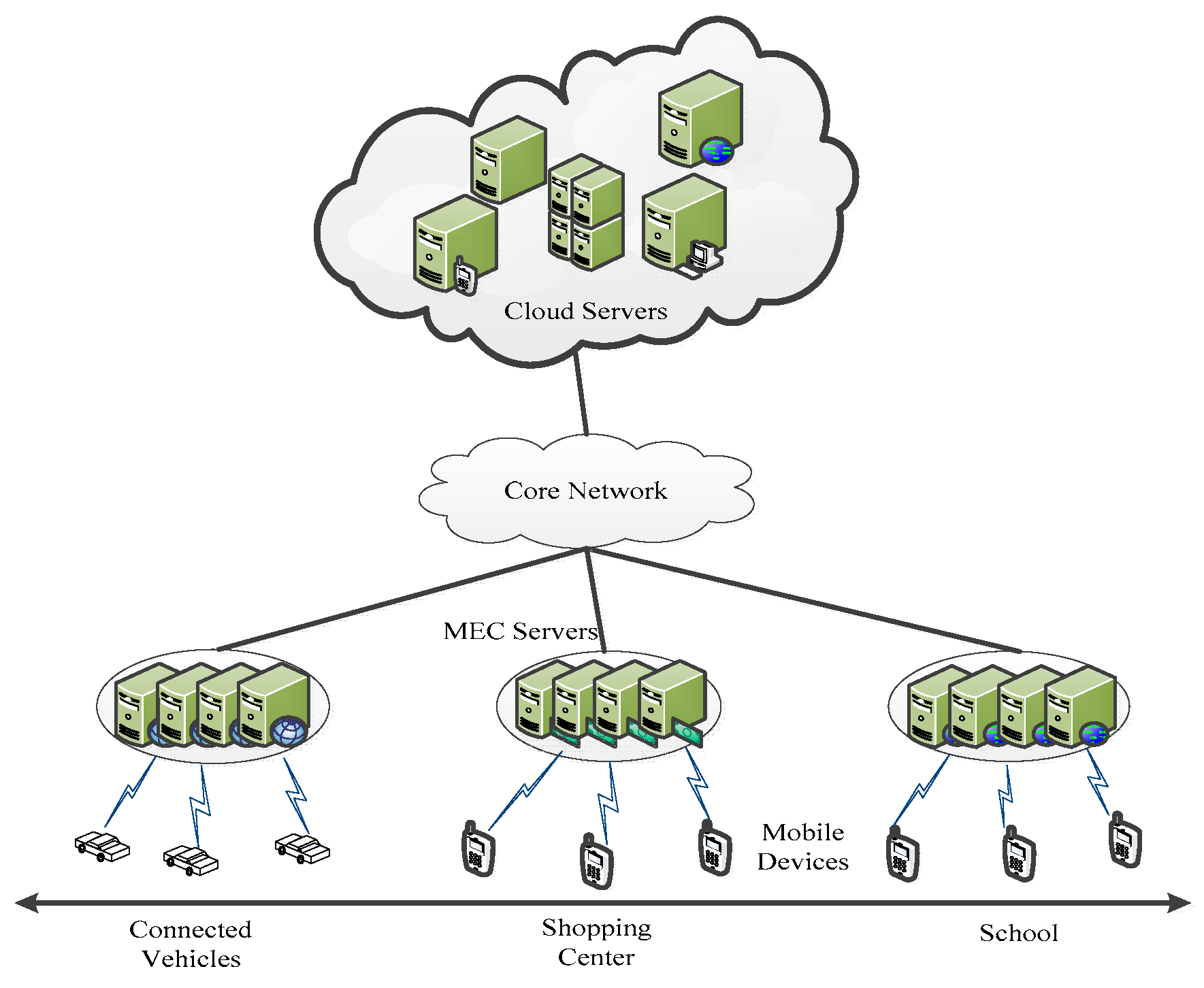
2.1. The Network Structure
- (1)
- Optimization of mobile resources by hosting compute intensive application at the edge network.
- (2)
- Optimization of the large data before sending to the cloud.
- (3)
- Enabling cloud services within the close proximity of mobile subscribers.
- (4)
- Providing context-aware services with the help of radio access network (RAN) information.
2.2. Agreement Problems
| Consensus: | All fault-free MEC nodes agree on a common value. |
| Validity: | If the initial value of each fault-free MEC node ni is vi then all fault-free MEC nodes shall agree on the value vi. |
| Consistency: | Each fault-free cloud node agrees on a set of common values V = [v1, v2, …, vn]. |
| Validity: | If the initial value of fault-free cloud node i is vi, then the i-th value in the common vector V should be vi. |
2.3. Failure Types
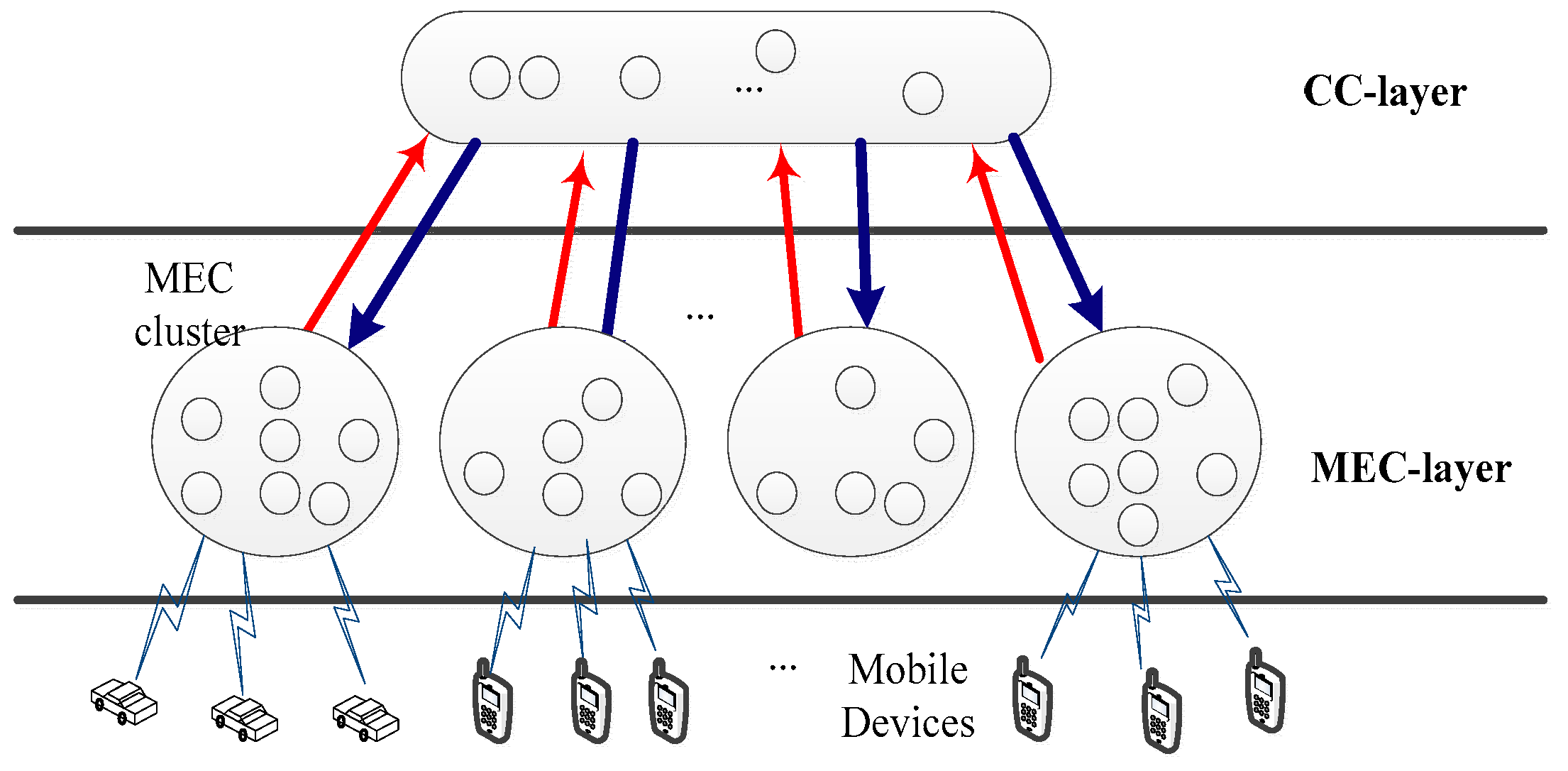
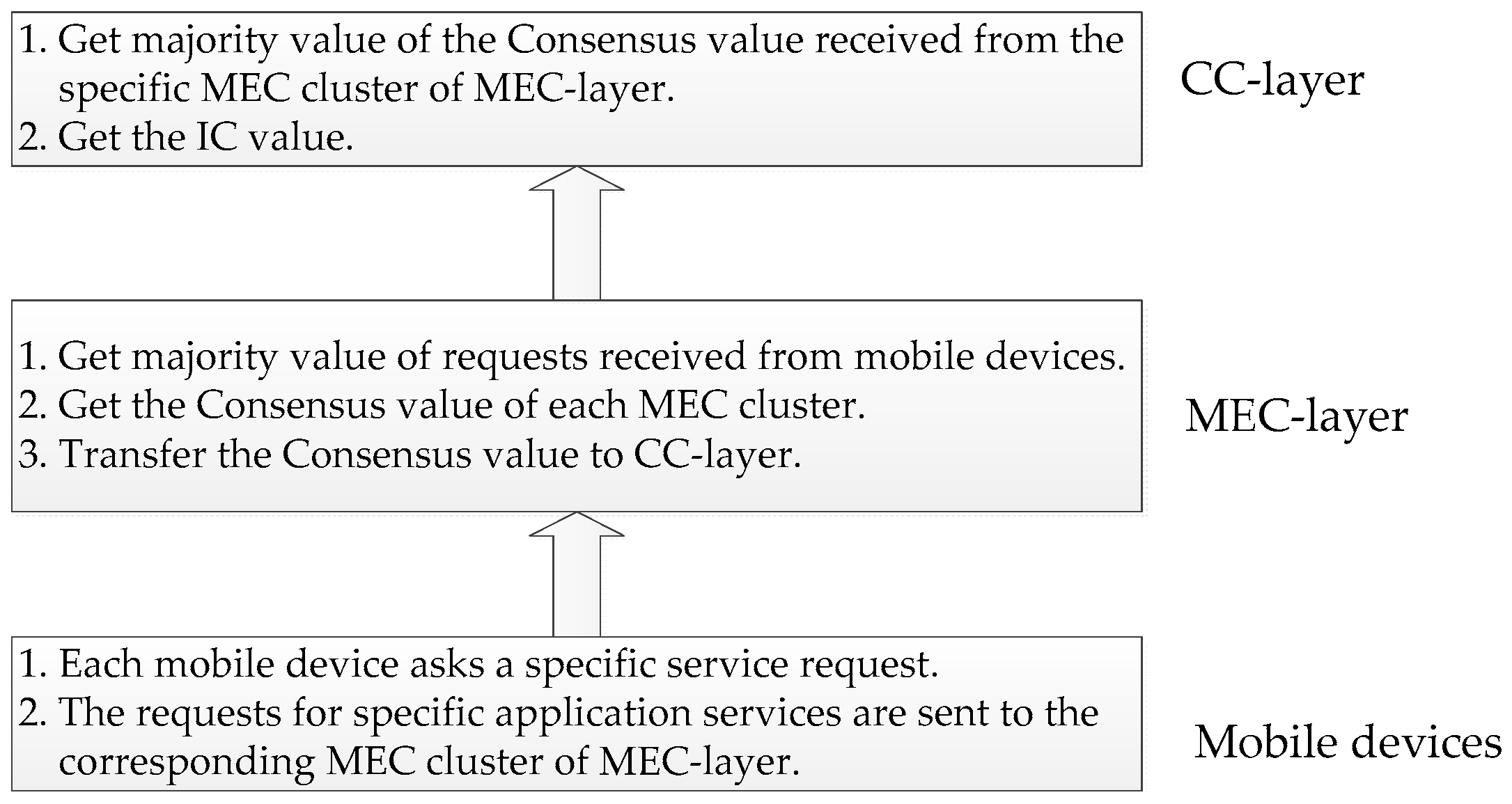
3. The Proposed Protocol
- (Constraint of MEC-layer): nEj > ⌊(nEj − 1)/3⌋ + 2fmEj where nEj is the number of MEC nodes and fmEj is the total number of allowable malicious faulty MEC nodes in MEC cluster Ej of the MEC-layer. This constraint specifies the number of MEC nodes required in MEC cluster Ej.
- (Constraint of CC-layer): The (Constraint of CC-layer) is similar to the (Constraint of MEC-layer) in that nC > ⌊(nC − 1)/3⌋ + 2fmC where nC is the number of cloud nodes and fmC is the total number of allowable malicious faulty cloud nodes in the CC-layer.
- trans(req, Ej): transfer the request of a specific application service to MEC cluster Ej.
- recv(req, Ej): receive the requests sent from UEs in the MEC cluster Ej.
- majority(recv(req, Ej)): take the majority of the received requests from UEs.
- recv(cv, Ej): receive the Consensus values transferred from nodes in the MEC cluster Ej.
- majority(recv(cv, Ej)): take the majority of the received Consensus values from nodes in the MEC cluster Ej.
- trans(cv, Ej): transfer the Consensus value of MEC cluster Ej to CC-layer.
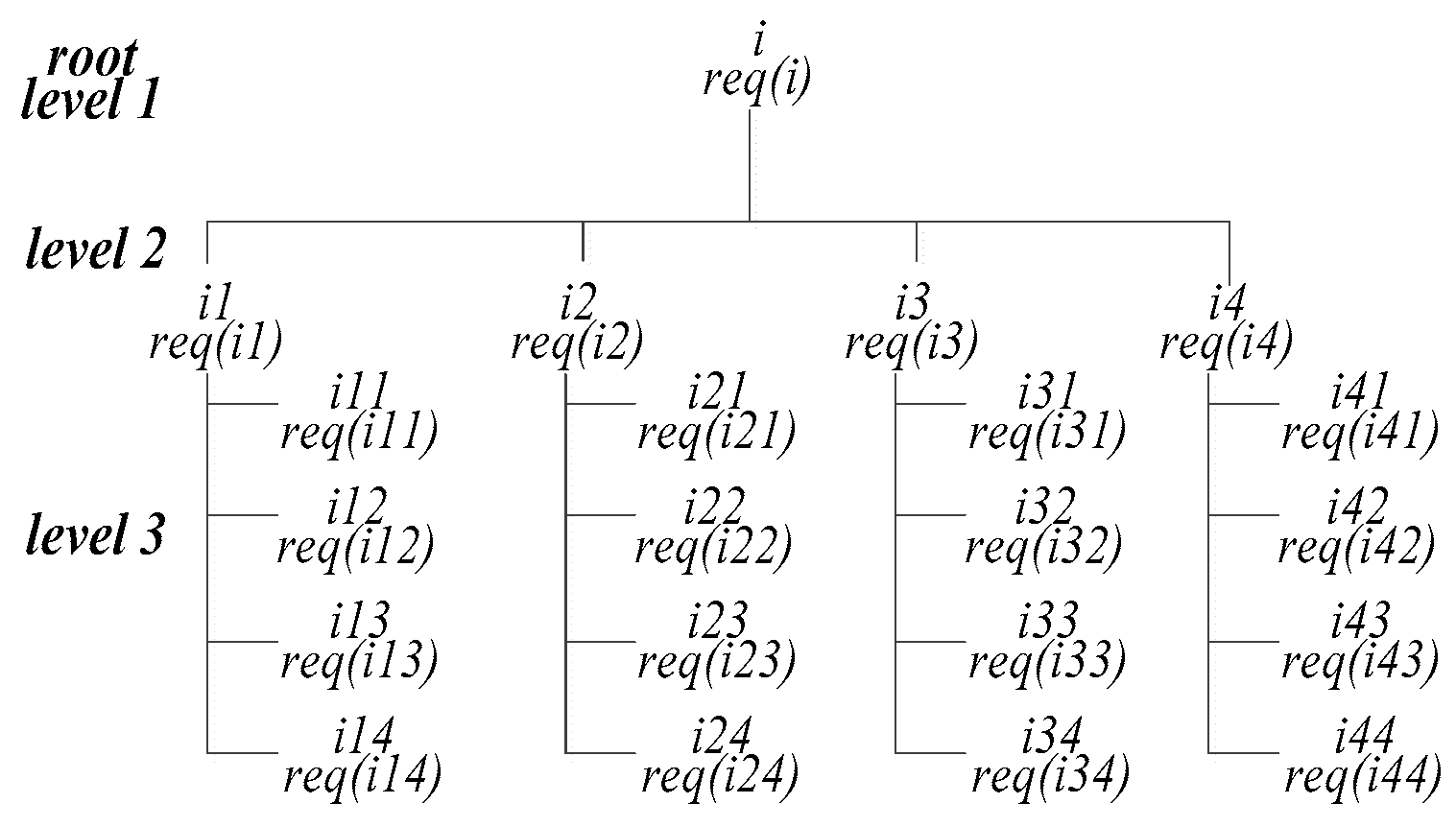
- send(i, <vs>, nA): node i sends the initial value vs to all nA nodes in the same cluster.
- rvst(i, nA, <vs, >, rg-tree(root)): node i receives and stores the nA <vs, > sent from nA nodes of same cluster in the corresponding root of its rg-tree.
- send(i, <val, r − 1>, nA): node i sends the values at level r − 1 in its rg-tree to other nA nodes in same cluster.
- rvst(i, nA, <val, r − 1>, re-tree(r)): node i receives and stores the nA <val, r − 1> sent from nA nodes of same cluster in the corresponding vertices at level r of its rg-tree.
- retree(i, rg-tree): delete the vertices in node i’s rg-tree with repeated node names.
- vote_value(new_rg-tree): compute the function value at the root of the new_rg-tree.
- tree_maj(α): take the majority value of new_rg-tree.
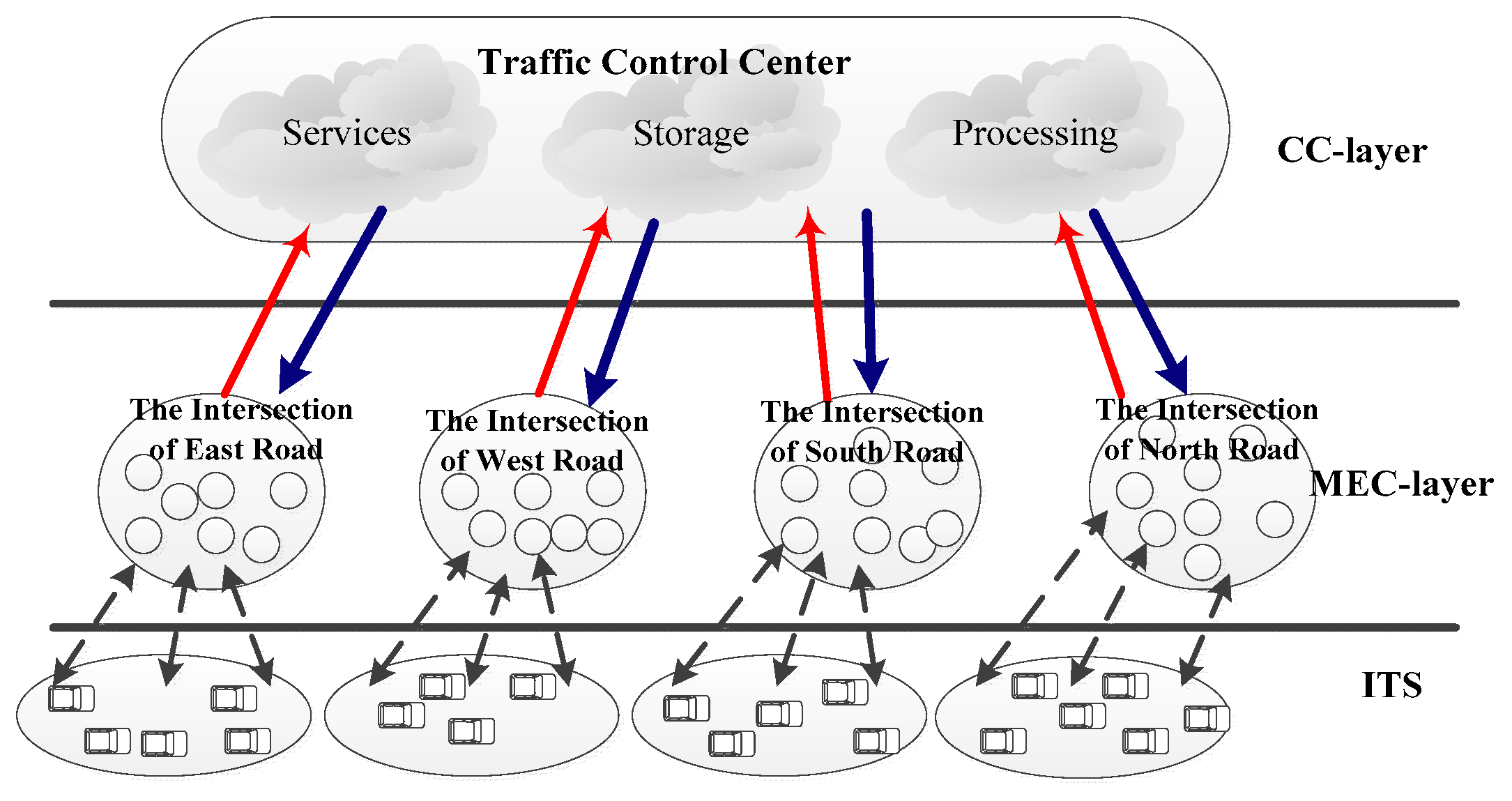
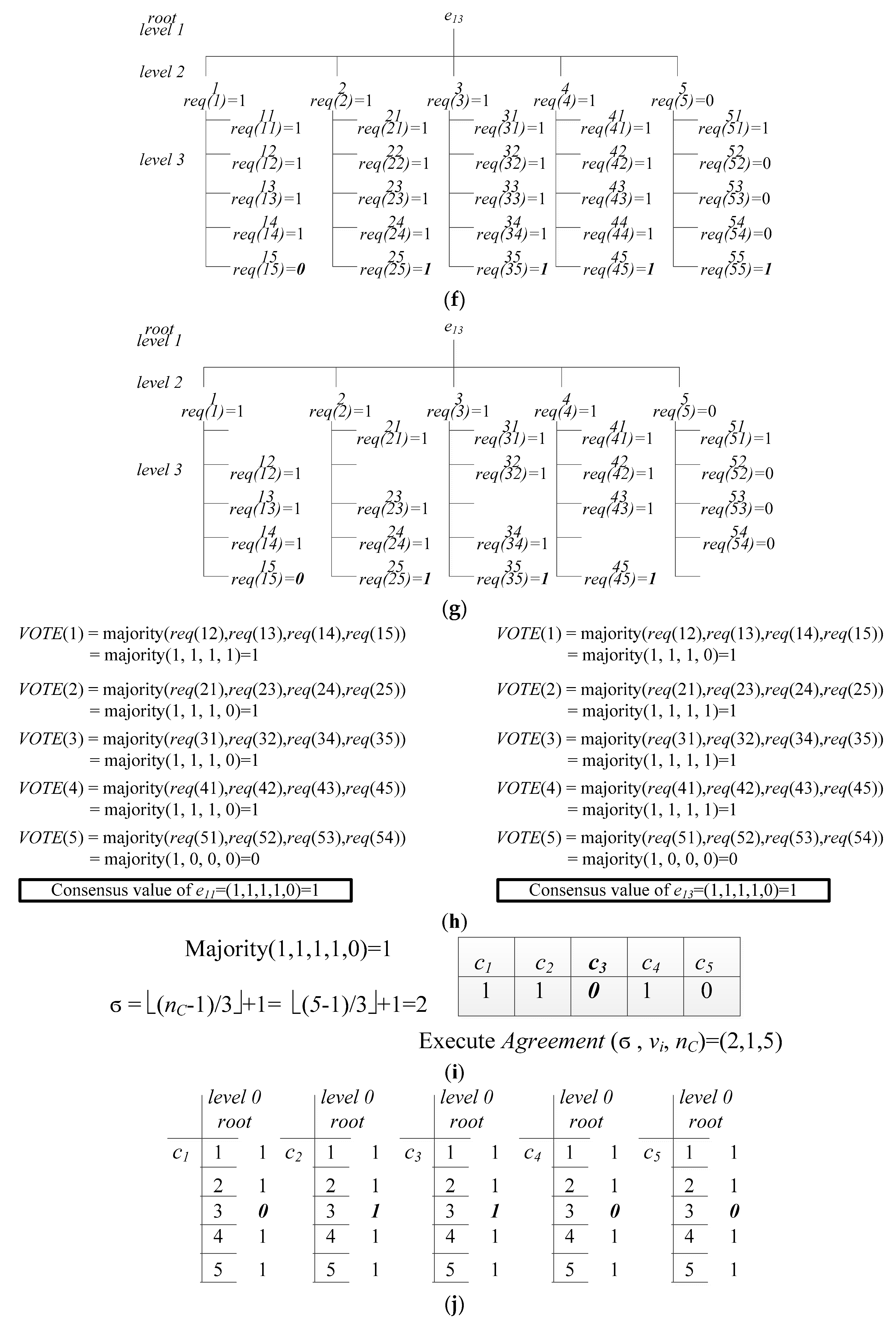
4. An Example of the Execution of MECAA
5. The Complexity of MECAA
- (1)
- MEC-layer: Because message passing is required only in the Request Gathering Step, the Request Gathering Step is time consuming. Dolev and Reischuk pointed out that ⌊(n–1)/3⌋ + 1 rounds are the minimum number of rounds to send sufficient messages to achieve agreement in an n-node fallible distributed system [21]. However, in the fallible MEC-layer, the MEC nodes maybe in malicious fault. In addition, each node in the fallible MEC-layer must exchange messages with other nodes. Therefore, a constraint on the minimum number of rounds can be applied to the study. In other words, in the MEC-layer, there are nEj nodes in the MEC cluster Ej; MECAA needs ⌊(nEj − 1)/3⌋ + 1 rounds to exchange messages. In an E-clusters MEC-layer, the nodes in each MEC cluster execute MECAA simultaneously, where E is the total number of clusters in the MEC-layer of MIoT. Therefore, the required rounds for executing MECAA by each node in all MEC clusters depend on the number of nodes in the MEC cluster.
- (2)
- CC-layer: As in the discussion of the number of message exchanges required in the MEC-layer. In the CC-layer, the research of Dolev and Reischuk can still be applied [21]. In the CC-layer, there are nC nodes; MECAA needs ⌊(nC − 1)/3⌋ + 1 rounds to exchange messages.
- (1)
- MEC-layer: Fischer and Lynch indicate the lower bound for agreement problem for node faults as f ≤ ⌊(n − 1)/3⌋, where f is the total number of allowable malicious faulty nodes and n is the total number of nodes in a distributed computing system [17]. Therefore, f ≤ ⌊(n − 1)/3⌋ in the study of Fischer and Lynch [17] can be applied to fmEj ≤ ⌊(nEj − 1)/3⌋ in the MEC-layer, where fmEj is the total number of allowable malicious faulty MEC nodes in MEC cluster Ej and nEj is the number of nodes in MEC cluster Ej. Then, TFE = where E is the total number of MEC clusters in the MEC-layer of MIoT, and TFE is the total number of allowable faulty nodes in the MEC-layer.
- (2)
- CC-layer: The research results of Fischer and Lynch [17] can also be applied to the CC-layer. Therefore, fmC is the total number of allowable faulty nodes in the CC-layer, and fmC ≤ ⌊(nC − 1)/3⌋ where nC is the number of cloud nodes.
6. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Botta, A.; De Donato, W.; Persico, V.; Pescapé, A. On the Integration of Cloud Computing and Internet of Things. In Proceedings of the 2014 International Conference on Future Internet of Things and Cloud (FiCloud), Barcelona, Spain, 27–29 August 2014; pp. 23–30. [Google Scholar]
- Dastjerdi, A.V.; Buyya, R. Fog Computing: Helping the Internet of Things Realize Its Potential. Computer 2016, 49, 112–116. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile Edge Computing, Fog et al.: A Survey and Analysis of Security Threats and Challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Puthal, D.; Sahoo, B.P.S.; Mishra, S.; Swain, S. Cloud Computing Features, Issues, and Challenges: A Big Picture. In Proceedings of the 2015 International Conference on Computational Intelligence and Networks (CINE), Bhubaneshwar, India, 12–13 January 2015; pp. 116–123. [Google Scholar]
- Kumar, P.; Gupta, S.K. Abstract Model of Fault Tolerance Algorithm in Cloud Computing Communication Networks. Int. J. Comput. Sci. Eng. 2011, 3, 3283. [Google Scholar]
- Wang, S.C.; Wang, S.S.; Yan, K.Q. New Anatomy of Trustworthy Mobile Cloud Computing. Inf. Technol. Control 2016, 45, 349–357. [Google Scholar] [CrossRef]
- Khalid, O.; Khan, M.U.S.; Khan, S.U.; Zomaya, A.Y. Omnisuggest: A Ubiquitous Cloud-Based Context-Aware Recommendation System for Mobile Social Networks. IEEE Trans. Serv. Comput. 2014, 7, 401–414. [Google Scholar] [CrossRef]
- Mach, P.; Zdenek, B. Mobile Edge Computing: A Survey on Architecture and Computation Offloading. IEEE Commun. Surv. Tutor. 2017, 19, 1628–1656. [Google Scholar] [CrossRef]
- Dinh, H.T.; Lee, C.; Niyato, D.; Wang, P. A Survey of Mobile Cloud Computing: Architecture, Applications, and Approaches. Wirel. Commun. Mob. Comput. 2013, 13, 1587–1611. [Google Scholar] [CrossRef]
- Mauch, V.; Kunze, M.; Hillenbrand, M. High Performance Cloud Computing. Future Gener. Comput. Syst. 2013, 29, 1408–1416. [Google Scholar] [CrossRef]
- Ficco, M.; Esposito, C.; Xiang, Y.; Palmieri, F. Pseudo-Dynamic Testing of Realistic Edge-Fog Cloud Ecosystems. IEEE Commun. Mag. 2017, 55, 98–104. [Google Scholar] [CrossRef]
- Jin, J.; Gubbi, J.; Marusic, S.; Palaniswami, M. An Information Framework for Creating a Smart City through International of Things. IEEE Internet Things J. 2014, 1, 112–121. [Google Scholar] [CrossRef]
- Whitmore, A.; Agarwal, A.; Da Xu, L. The Internet of Things-A Survey of Topics and Trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Li, X.; Chen, X.; Xie, Y. Agreement of Networks of Discrete-Time Agents with Mixed Dynamics and Time Delays. Math. Probl. Eng. 2015. [Google Scholar] [CrossRef]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine general Problem. ACM Trans. Progr. Lang. Syst. 1982, 4, 382–401. [Google Scholar] [CrossRef]
- Meyer, F.J.; Pradhan, D.K. Consensus with Dual Failure Modes. IEEE Trans. Parallel Distrib. Syst. 1991, 2, 214–222. [Google Scholar] [CrossRef]
- Fischer, M.J.; Lynch, N.A. A Lower Bound for the Time to Assure Interactive Consistency. Inf. Process. Lett. 1981, 14, 183–186. [Google Scholar] [CrossRef]
- Wang, S.C.; Wang, S.S.; Yan, K.Q. Reaching Optimal Interactive Consistency in a Fallible Cloud Computing Environment. J. Inf. Sci. Eng. 2018, 34, 205–223. [Google Scholar]
- Bar-Noy, A.; Dolev, D.; Dwork, C.; Strong, H.R. Shifting Gears: Changing Algorithms on the Fly to Expedite Byzantine Agreement. Inf. Comput. 1992, 97, 205–233. [Google Scholar] [CrossRef]
- Agrawal, S.; Daudjee, K. A Performance Comparison of Algorithms for Byzantine Agreement in Distributed Systems. In Proceedings of the 12th European Dependable Computing Conference (EDCC), Gothenburg, Sweden, 5–9 September 2016; pp. 249–260. [Google Scholar]
- Dolev, D.; Reischuk, R. Bounds on Information Exchange for Byzantine Agreement. J. ACM 1985, 32, 191–204. [Google Scholar] [CrossRef]


| MEC Agreement Algorithm (MECAA) | |
| Main | |
| |
| Procedure Consensus (for the MEC node eij in the MEC cluster Ej of MEC-layer, 1 ≤ i ≤ nEj where nEj is the number of MEC nodes in MEC cluster Ej of MEC-layer and nEj > 3) | |
| |
| Procedure Interactive Consistency (for the cloud node ci in the CC-layer, 1 ≤ j ≤ nC, where nC is the number of cloud nodes in the CC-layer and nC > 3) | |
| |
| Agreement(σ, vs, nA) (σ is the required rounds, vs is the initial value and nA is the number of nodes participating in the agreement) | |
| Request Gathering Step: | |
| If r = 1 then: |
|
| For 2 < r ≤ σ, do: |
|
| Request Deciding Step: | |
| Step 1: | Reorganize each rg-tree by deleting the vertices with repeated node names. |
| Step 2: | Using function VOTE with the root i of each node’s rg-tree and obtaining the common value VOTE(i). |
| VOTE(α)= | If the α is a leaf, then outputs the value α. If the majority value does not exist, then output the default value φ. |
| MECAP MECAA /* MEC Agreement Algorithm*/ | |
| { for i = 1 to NUE /* NUE is the total number of UEs */ trans(req, Ej); end for j = 1 to NE /* NE is the total number of MEC clusters in MEC-layer */ Consensus(nEj, Ej) Interactive Consistency(nC, Ej) end } Consensus(nEj, Ej) { for i = 1 to nEj recv(req, Ej); vi = majority(recv(req, Ej)); σ = ⌊(nEj − 1)/3⌋ + 1; cv = Agreement(σ, vi, nEj); trans(cv, Ej); end } Interactive Consistency(nC, Ej) { for j = 1 to nC recv(cv, Ej); vj = najority(recv(cv, Ej)); σ = ⌊(nC − 1)/3⌋ + 1; IC = Agreement(σ, vj, nC); end } | Agreement(σ, vs, nA) /* σ is the required rounds, vs is the initial value and nA is the number of nodes participating in the agreement */ { int VOTE[nA]; /* Request Gathering Step */ for i = 1 to nA do send(i, <vs>, nA); rvst(i, nA, <vs>, rg-tree(root)); end for r = 2 to σ do for i=1 to nA do send(i, <val, r − 1>, nA); rvst(i, nA, <val, r − 1>, re-tree(r)); end /* Request Deciding Step */ for i = 1 to nA do new_rg-tree = retree(i, rg-tree); VOTE(i) = vote_value(new_rg-tree); end return(VOTE); } vote_value(α) { if (α is a leaf) return(α); else if (tree_maj(α) = m) /* m is 0 or 1/ return(m); else return(φ); |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, S.-C.; Hsiung, W.-S.; Hsieh, C.-F.; Tsai, Y.-T. Reliability Enhancement of Edge Computing Paradigm Using Agreement. Symmetry 2019, 11, 167. https://doi.org/10.3390/sym11020167
Wang S-C, Hsiung W-S, Hsieh C-F, Tsai Y-T. Reliability Enhancement of Edge Computing Paradigm Using Agreement. Symmetry. 2019; 11(2):167. https://doi.org/10.3390/sym11020167
Chicago/Turabian StyleWang, Shu-Ching, Wei-Shu Hsiung, Chia-Fen Hsieh, and Yao-Te Tsai. 2019. "Reliability Enhancement of Edge Computing Paradigm Using Agreement" Symmetry 11, no. 2: 167. https://doi.org/10.3390/sym11020167
APA StyleWang, S.-C., Hsiung, W.-S., Hsieh, C.-F., & Tsai, Y.-T. (2019). Reliability Enhancement of Edge Computing Paradigm Using Agreement. Symmetry, 11(2), 167. https://doi.org/10.3390/sym11020167





