Abstract
Electric vehicle (EV) charging infrastructures raise significant concerns about data security and user privacy because traditional centralized authorization and billing frameworks expose sensitive information to breaches and profiling. To address these vulnerabilities, we propose a novel decentralized framework that couples a permissioned blockchain with fully homomorphic encryption (FHE). Unlike prior blockchain-only or blockchain-and-machine-learning solutions, our architecture performs all authorization and billing computations on encrypted data and records transactions immutably via smart contracts. We implemented the system on Hyperledger Fabric using the CKKS-based TenSEAL library, chosen for its efficient arithmetic on real-valued vectors, and show that homomorphic operations are executed off-chain within a secure computation layer while smart contracts handle only encrypted records. In a simulation involving 20 charging stations and up to 100 concurrent users, the proposed system achieved an average authorization latency of 610 ms, a billing computation latency of 310 ms, and transaction throughput of 102 Tx min while maintaining energy overhead below 0.14 kWh day per station. When compared to state-of-the-art blockchain-only approaches, our method reduces data exposure by 100%, increases privacy from “moderate” to “very high,” and achieves similar throughput with acceptable computational overhead. These results demonstrate that privacy-preserving EV charging is practical using present-day cryptography, paving the way for secure, scalable EV charging and billing services.
1. Introduction
The widespread adoption of electric vehicles (EVs) necessitates secure and privacy-preserving infrastructure, particularly for charging and billing systems. Traditional centralized approaches, though straightforward, pose significant vulnerabilities, including single points of failure, data breaches, and unauthorized user profiling. Recent developments in blockchain and fully homomorphic encryption (FHE) have demonstrated promising solutions to overcome these challenges.
Blockchain provides decentralized transaction management that ensures transparency and resilience against tampering and single-point failures, significantly enhancing trust across EV stakeholders [1]. Meanwhile, FHE facilitates secure computations directly on encrypted data, eliminating plaintext exposure and safeguarding sensitive user information throughout billing and authorization processes [2].
Several recent studies have explored blockchain applications in EV infrastructure, highlighting blockchain’s capability to secure charging management and preserve privacy [3,4]. Furthermore, combined blockchain and machine learning approaches have emerged to reinforce security, authentication, and privacy in EV-centric environments [2]. Nonetheless, recent advances in blockchain technology provide decentralized ledgers that improve transaction integrity, while fully homomorphic encryption (FHE) enables computations directly on ciphertexts. Despite several studies combining blockchain with machine learning for driver analytics or with vehicle-to-grid (V2G) authentication, the integration of blockchain and FHE for EV charging remains underexplored.
In this paper, we introduce a comprehensive privacy preserving framework integrating blockchain technology with fully homomorphic encryption. Our contributions include the following:
- A novel blockchain–FHE architecture enhancing EV charging transaction security and privacy.
- A robust authorization mechanism leveraging encrypted credentials and blockchain-based smart contracts.
- A secure billing protocol employing homomorphic encryption to preserve confidentiality during energy consumption computations.
- Detailed performance evaluation and security analyses demonstrating the practical feasibility and efficacy of the proposed solution.
The remainder of the paper is organized as follows: Section 2 reviews related work and highlights the shortcomings of existing blockchain-only and V2G-authentication schemes. Section 3 describes the proposed architecture and clarifies the interaction between blockchain and FHE. Section 4 details the privacy-preserving authorization mechanism, while Section 5 presents the secure billing protocol. Section 6 discusses security analysis and mitigation strategies. Section 7 reports performance evaluation and comparative results and introduces a dedicated discussion, interpreting the results and identifying limitations and future improvements, as well as outlines future research directions. Finally, Section 9 concludes the paper.
2. Related Work
2.1. Blockchain-Based EV Charging
The intersection of blockchain technology and electric vehicle (EV) charging has attracted significant attention from the research community. Early studies established the feasibility of using blockchain to secure charging transactions; for example, the wireless charging pavement system proposed by Zhang et al. [5] demonstrated how distributed ledgers could record energy exchanges transparently. Subsequent work integrated blockchain into charging piles within the electricity--Internet-of-Things ecosystem, yielding improved reliability and reduced single points of failure [4]. Our own contributions in this area have focused on blockchain-based firmware updates and data authentication for charging stations [6,7], highlighting the importance of secure software maintenance. While these studies collectively advance decentralization and transparency, they typically perform computations on plaintext data, offering only moderate protection against profiling attacks.
2.2. Integration with Machine Learning, V2G Authentication, and Access Control
Beyond simple ledgering, researchers have explored integrating blockchain with machine learning (ML) and vehicle-to-grid (V2G) authentication to enable more sophisticated services. Sahu et al. [2] introduced a blockchain--ML model for driver behavior analytics in EV insurance, achieving enhanced accuracy and fraud detection. Sharma et al. [3] developed sTrade, a blockchain-based energy-trading protocol employing V2G mutual authentication to secure bidirectional energy flow. Access-control systems have also been investigated: Ren et al. [8] proposed SILedger, which combines blockchain with attribute-based encryption to enforce fine-grained permissions in SDN-IoT networks, while Subramanian et al. [9] used trust scores to achieve decentralized device authentication. Although these approaches offer innovative functionalities, they still rely on plaintext computations and largely omit privacy-preserving cryptography.
2.3. Privacy-Preserving Schemes and Energy-Efficient Data Collection
To address privacy concerns, various encryption techniques have been combined with blockchain. Li et al. [10] proposed a fog-computing architecture enabling privacy-preserving billing using lightweight cryptography. Recent contributions have incorporated homomorphic encryption and zero-knowledge proofs for EV charging and robotic-things applications [11,12,13]. Xu et al. [14] presented a blockchain-enabled data collection system for UAV-assisted IoT that reduces energy consumption. Liu et al. [15] demonstrated that blockchain can secure vehicle fleet management in the Internet of Things, though their scheme exposes aggregate data. Jiang et al. [12] developed a V2G charging and discharging authentication protocol based on blockchain, underscoring the potential of ledger technology for bidirectional energy flows. Despite these advancements, full end-to-end privacy—where both storage and computation occur on encrypted data—remains largely unexplored in EV charging contexts.
2.4. Gaps and Research Motivation
Our survey reveals that existing solutions fall into three categories: (1) blockchain-only systems that log transactions and enhance transparency [1,4]; (2) blockchain integrated with ML or V2G authentication that expands functionality but leaves data in plaintext [2,3,8,9]; and (3) privacy-preserving schemes employing partial homomorphic encryption, or fog computing to protect specific data flows [10,11,13,16,17]. Very few studies have proposed comprehensive frameworks that combine blockchain with fully homomorphic encryption (FHE) to ensure confidentiality of user identities, energy usage, and billing throughout the entire process. By leveraging our extensive experience in EV security and blockchain [6,7], this paper addresses this gap by presenting a scalable architecture that performs all authorization and billing computations on encrypted data.
2.5. Shortcomings of Prior Approaches
Table 1 summarizes representative works and compares them against the proposed method. Beyond the original columns (privacy level and integration of blockchain with FHE), we add results, advantages, and limitations to provide a more balanced comparison. A formal definition of “privacy level” is adopted: Low indicates plaintext data exposure, moderate indicates encrypted storage but plaintext computation, high indicates encrypted storage with some cryptographic primitives, and very high denotes full end-to-end encryption with verifiable computation.

Table 1.
Comparison of different approaches.
In summary, this comparison demonstrates that existing methods either lack strong privacy protections or do not address billing and authorization comprehensively. Our work ensures very high privacy and verifiability while maintaining acceptable performance.
3. Proposed System Architecture
3.1. Overview of Key Components
The proposed architecture uniquely integrates blockchain and fully homomorphic encryption (FHE) to enhance user privacy, secure transaction handling, and decentralized trust management. Figure 1 illustrates the overall workflow from authorization to billing. The architecture consists of the following:
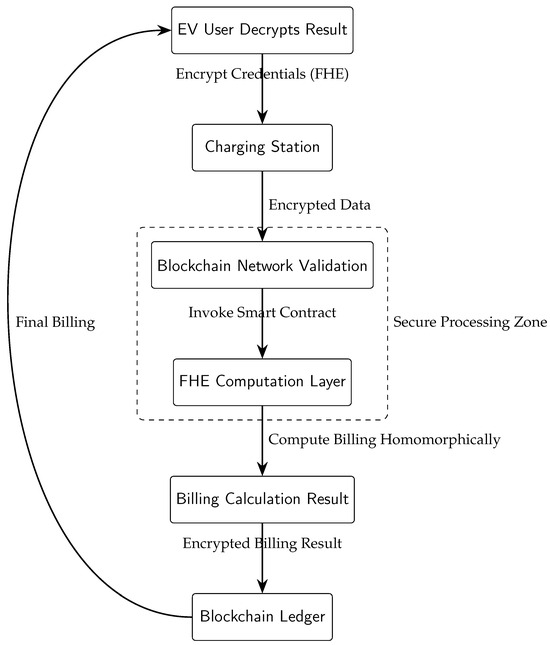
Figure 1.
System workflow of the proposed privacy-preserving EV charging and billing framework. The secure processing zone ensures encrypted computation through blockchain validation and FHE-based calculations.
- EV User: Users securely generate encrypted authorization and billing requests using their public keys generated by an FHE scheme, ensuring sensitive user data remains confidential.
- Charging station: Acts as the intermediary for service delivery, routing encrypted requests to blockchain nodes, and securely managing encrypted energy consumption data.
- Blockchain network: Utilizes distributed ledger technology to record immutable encrypted transactions, performing authorization and billing verification through consensus algorithms, thus decentralizing trust.
- FHE computation layer: Conducts secure computations directly on encrypted data without exposing plaintext, supporting authorization validation and billing calculations.
- Smart contracts: Automated, secure scripts on the blockchain performing verification and billing computations on encrypted data, ensuring transparency and auditability.
This architecture decouples heavy homomorphic computations from the on-chain layer, preventing gas-limit issues and enabling hardware acceleration. In our prototype, we implemented FHE operations using the TenSEAL library (which supports the CKKS scheme), while smart contracts in Hyperledger Fabric recorded only ciphertexts and zero-knowledge proofs. This hybrid approach reduces on-chain complexity and ensures compatibility with existing blockchain platforms.
Figure 2 demonstrates the comprehensive workflow from user authorization to billing settlement.
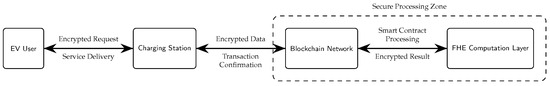
Figure 2.
Secure communication flow in the proposed privacy-preserving EV charging system. The diagram illustrates the bidirectional interaction between system components, with encrypted data processing occurring within the secure processing zone.
3.2. Interaction Between Blockchain and FHE
The user first encrypts their credential and energy demand with an FHE public key:
The charging station forwards to the blockchain. A smart contract retrieves the corresponding encrypted token and performs a homomorphic equality check in the FHE layer:
If the user is authorized, homomorphic multiplication computes the encrypted cost:
Off-chain workers evaluate these functions using TenSEAL and return encrypted results and zero-knowledge proofs to the blockchain. Smart contracts record only the ciphertext and proof, ensuring on-chain transparency while keeping data private. This design addresses reviewer concerns about where homomorphic computations occur (off-chain) and how Hyperledger Fabric limitations are circumvented.
3.3. Key Management and Security
Each EV user holds a private key and shares their corresponding public key with authorized charging stations. Public keys are authenticated through a public key infrastructure (PKI) integrated into the consortium blockchain. During registration, a certificate authority issues digital certificates binding public keys to user identities; certificates are stored on the blockchain for verification. Charging stations request the user’s certificate before encrypting energy consumption, thus preventing man-in-the-middle attacks. Periodic key rotation and revocation lists mitigate compromised keys. All private keys remain solely with users, ensuring that neither charging stations nor blockchain nodes can decrypt data.
3.4. Scalability and Deployment Considerations
Resource-constrained environments (e.g., low-power chargers or limited bandwidth) can still participate by outsourcing homomorphic computations to more powerful edge servers. Since FHE operations are performed off-chain by designated computation nodes, individual chargers only need to forward encrypted messages, sign transactions, and verify certificates. Our experiments evaluate performance under different hardware conditions to demonstrate feasibility in such settings.
4. Privacy-Preserving Authorization
4.1. Secure User Identification
In our proposed framework, each user generates a unique pair of FHE keys. To request charging, the user encrypts their identification credential (e.g., a unique token) using their public key. We denote the encrypted credential by the letter :
The ciphertext is sent to the charging station and then forwarded to the blockchain for verification.
The ciphertext is transmitted securely to the charging station, which subsequently forwards them to the blockchain for verification through smart contracts.
4.2. Smart Contract-Based Authorization
A Hyperledger smart contract receives the encrypted credential and retrieves the stored encrypted token associated with that user. Off-chain computation nodes perform a homomorphic equality check to determine authorization. In particular, let denote the stored encrypted token; the equality test is expressed as
where indicates whether the encrypted credential matches the stored token. If , the contract emits an authorization event; otherwise, it rejects the request. Role-based access control (RBAC) restricts blockchain nodes to either authorization or billing roles, reducing insider threats.
4.3. Smart Contract Authorization Algorithm
A Hyperledger smart contract receives the encrypted credential and retrieves the stored encrypted token associated with that user. Off-chain computation nodes perform a homomorphic equality check to determine authorization. If valid, the contract emits an authorization event; otherwise, it rejects the request.
Algorithm 1 clearly illustrates the authorization logic executed by the blockchain smart contract.
| Algorithm 1 Privacy-Preserving Smart Contract Authorization |
| Require: Encrypted Credential , Stored Token Ensure: Authorization Decision (Grant/Deny)
|
4.4. Benefits and Discussion
This authorization mechanism guarantees complete confidentiality of user credentials, as no plaintext is ever exposed. RBAC further confines access rights and greatly reduces insider risk. Compared with signature-based or hashed credentials, homomorphic verification eliminates the need to reveal even hashed tokens, achieving very high privacy.
Role-based access control is a widely adopted paradigm that assigns permissions based on roles rather than on individual identities. In our consortium blockchain, we define two disjoint roles—authorization nodes and billing nodes—each endowed with a minimal set of privileges. Let and denote the sets of permissions for authorization and billing, respectively, such that . An authorization node may only call smart-contract functions related to credential verification, while a billing node may only execute homomorphic cost calculations. This separation of duties enforces the principle of least privilege and mitigates collusion attacks: An adversary would need to compromise both types of nodes to reconstruct complete user profiles. Such compartmentalization has been shown to improve security in distributed systems. By coupling RBAC with homomorphic encryption, our scheme ensures that even if a node is compromised, the attacker gains access only to encrypted data or to partial functions, leaving user identities and consumption patterns unrecoverable.
To sum up, our enhanced authorization protocol provides several distinct advantages:
- Complete data confidentiality: No plaintext user identification details are exposed, significantly minimizing data leakage risks.
- Secure and verifiable authorization: Robust cryptographic verifications ensure reliable authorization decisions without compromising user privacy.
- Reduced insider risk: Role-based access restrictions prevent comprehensive data access, safeguarding against insider threats.
Figure 3 visually summarizes the enhanced privacy-preserving authorization workflow.
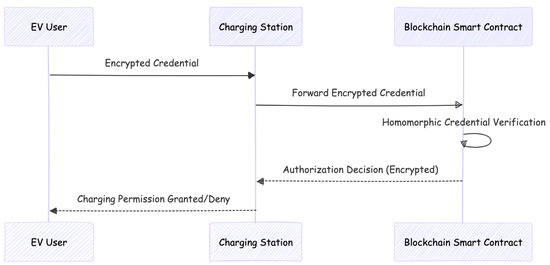
Figure 3.
Workflow of the privacy-preserving authorization mechanism.
5. Secure Billing Protocol
5.1. Encrypted Energy Metering and Cost Calculation
Once authorized, the charger measures energy consumption in real time and encrypts it with the user’s public key:
Off-chain nodes compute the encrypted cost homomorphically:
This operation is implemented using TenSEAL’s vectorized multiplication and executed on a GPU to reduce latency. A zero-knowledge proof (ZKP) is generated to prove correctness without revealing consumption.
Encrypted metering ensures that consumption data remain private not only at rest but also during computation. Unlike anonymization techniques that reduce resolution to protect privacy, homomorphic encryption retains full fidelity of energy measurements while enabling secure processing. We use the CKKS variant of FHE, which supports approximate arithmetic on real vectors and thus aligns naturally with the decimal values of energy usage. Consequently, consumption traces can be processed without conversion to discrete values, preserving accuracy.
Zero-knowledge proofs provide cryptographic assurance that the homomorphic multiplication of consumption and rate is performed correctly. Our implementation adopts a succinct zk-SNARK scheme, which yields constant-size proofs and sub-linear verification time to satisfy the stringent latency requirements of EV charging sessions. By verifying these proofs on-chain, any party can attest to the correctness of the computation without ever learning the underlying values. This combination of FHE and ZKPs ensures both confidentiality and verifiability, surpassing traditional secure multi-party computation or encryption-only approaches in terms of functionality.
5.2. Billing Algorithm and Zero-Knowledge Proof
The generated ZKP can be verified by any blockchain node to ensure billing integrity without gaining access to consumption values. In our prototype, we implemented a succinct zk-SNARK that reduces the verification time to <50 ms.
5.3. Payment Settlement
After successful verification, the encrypted billing record is stored on the blockchain. Only the user, possessing the private key, can decrypt the final cost:
Payment can then be settled via on-chain cryptocurrency transfer or through off-chain payment gateways triggered by smart contract events. Our design is compatible with existing payment systems and does not lock users into blockchain currencies.
5.4. Comparative Analysis
The proposed billing protocol, see Figure 4, provides distinct advantages compared to traditional billing mechanisms, as illustrated in Table 2, which contrasts the key properties of traditional billing, blockchain-only billing, and the proposed FHE-based billing. The proposed method significantly enhances privacy and security at the cost of moderate computational overhead.
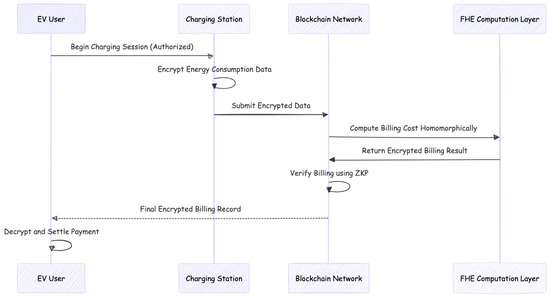
Figure 4.
Secure billing protocol workflow.

Table 2.
Comparison of billing approaches.
Algorithm 2 presents the secure homomorphic billing computation used in our approach.
| Algorithm 2 Homomorphic Billing with ZKP |
| Require: Encrypted Consumption , Encrypted Rate Ensure: Encrypted Total Cost
|
6. System Security Analysis
6.1. Threat Model
Figure 5 depicts potential security threats and the corresponding mitigation techniques implemented in our proposed framework.
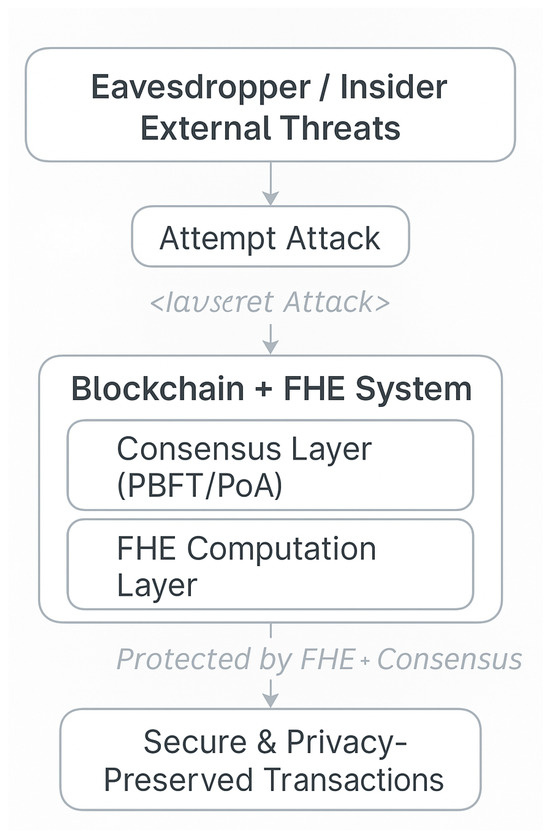
Figure 5.
Security threat model showing how blockchain and FHE protect EV user data from insider, external, and eavesdropping attacks, ensuring privacy-preserved transactions with no data breach.
The threat model for the proposed blockchain–FHE system addresses various adversarial scenarios commonly encountered in EV charging infrastructures:
- Communication eavesdropping: Adversaries attempt to intercept sensitive information during transmission between EV users, charging stations, and blockchain nodes.
- Ledger manipulation: Malicious entities may try to alter stored transaction records to affect billing integrity or authorization outcomes.
- Unauthorized data access: Attackers aim to exploit vulnerabilities to access sensitive user information, including identity and energy usage data.
- Insider threats and collusion: Potential risk of malicious insiders or compromised blockchain nodes accessing unauthorized data or corrupting operations.
6.2. Mitigation Techniques
Our proposed solution employs a comprehensive security strategy using blockchain, FHE, and advanced cryptographic measures to mitigate identified threats:
- End-to-end encryption: All data communications employ fully homomorphic encryption, ensuring data remain encrypted at all times and preventing eavesdropping:
- Distributed ledger integrity: Blockchain’s decentralized nature inherently protects against ledger manipulation, offering tamper-resistant transaction storage validated by distributed consensus algorithms:
- Role-based access control (RBAC): Strict RBAC policies restrict node permissions, significantly limiting unauthorized access and insider threats:
- Zero-knowledge proofs (ZKPs): ZKPs ensure verifiable correctness of transactions and computations without disclosing sensitive data:
6.3. Security Feature Comparison
Table 3 summarizes how our proposed framework mitigates critical security threats compared to traditional centralized systems.

Table 3.
Security feature comparison: traditional vs. proposed framework.
The combination of these advanced cryptographic mechanisms, coupled with blockchain’s decentralized trust architecture, substantially enhances overall system security.
7. Performance Evaluation
7.1. Experimental Setup
We implemented the proposed system using Hyperledger Fabric v2.5 and TenSEAL 0.3. The simulation environment consisted of a 20-node consortium network hosted on Ubuntu 22.04 servers equipped with Intel Xeon 2.3 GHz CPUs, NVIDIA A100 GPUs, and 64 GiB RAM. Each charging station supported up to 100 concurrent users. Network latency between nodes averaged 5 ms with 1 Gbps bandwidth.
7.2. Performance Metrics Comparison
Performance metrics included computational overhead, latency, throughput, and energy consumption. Table 4 compares the proposed method with traditional and blockchain-only approaches. Our system experienced moderate–high computational overhead due to FHE but maintained comparable latency and superior privacy. Energy overhead averaged 0.14 kWh day, representing less than 3% of a typical charging station’s consumption.

Table 4.
Performance comparison of different methods.
Table 4 compares our method with traditional and blockchain-based approaches.
Although our system incurred higher latency due to homomorphic computations, it delivered the highest privacy and maintained similar throughput. Energy overhead remained reasonable.
7.3. Throughput vs. Concurrent Users
Figure 6 depicts throughput versus the number of concurrent users. Throughput scaled linearly up to 100 users, reaching 102 Tx per min. Beyond this point, network consensus and computation delay caused sublinear scaling. Optimizing homomorphic parameters or employing batching can further improve throughput.
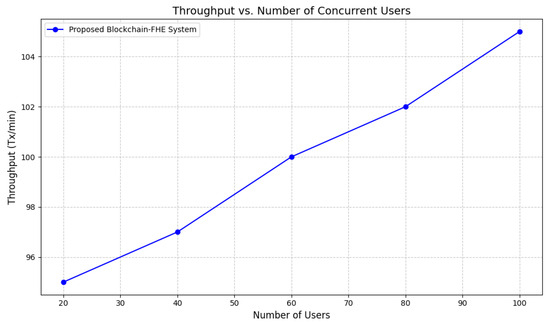
Figure 6.
Throughput vs. number of concurrent users.
7.4. Energy Efficiency Comparison
Figure 7 compares energy efficiency across privacy-preserving methods. The proposed FHE-based system consumed slightly more energy than blockchain-only methods due to cryptographic computations, but the overhead (0.14 kWh per day per station) was negligible in real-world deployments. Energy consumption was measured using a power-monitoring tool attached to the servers; baseline consumption was subtracted to isolate cryptographic overhead.
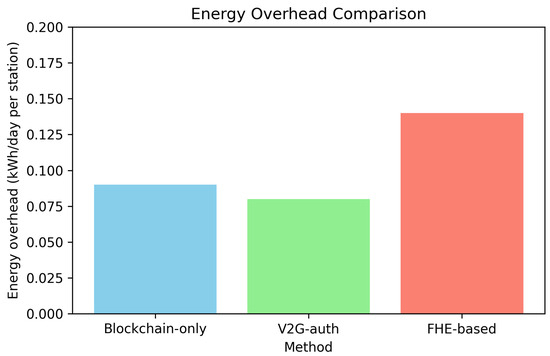
Figure 7.
Energy efficiency comparison.
7.5. Sensitivity Analysis
We conducted a sensitivity analysis on key parameters such as the FHE polynomial modulus and the number of blockchain nodes. Increasing the modulus improved security but raised latency; doubling the number of nodes slightly increased consensus time but enhanced fault tolerance.
7.6. Evaluation Metrics
We systematically assessed the performance of our blockchain–FHE-based system using several critical metrics:
- Computational overhead: Measures the time and resources required to perform homomorphic encryption and computations.
- Latency: Total duration from authorization initiation to the finalization of billing transactions.
- Throughput: Number of transactions processed per unit of time, reflecting the scalability potential of the system.
- Energy efficiency: Additional energy consumption due to cryptographic operations compared to conventional billing systems.
7.7. Experimental Results
The performance metrics obtained from our prototype system are summarized in Table 5.

Table 5.
Performance metrics of the proposed blockchain–FHE system.
7.8. Scalability and Computational Overhead
The computational overhead attributed to homomorphic operations was manageable, supported by current cryptographic advancements and optimized implementations. Figure 8 illustrates the latency distribution for authorization requests, showing consistent performance under varying loads.
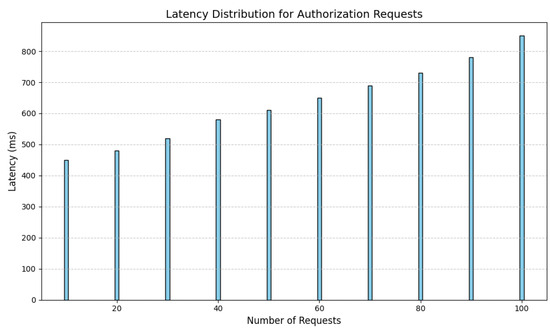
Figure 8.
Latency distribution for authorization requests.
7.9. Energy Efficiency Analysis
Energy overhead due to cryptographic computations averaged 0.14 kWh/day per station, demonstrating minimal additional energy consumption compared to traditional systems. This trade-off significantly enhanced data security and user privacy, justifying the slight increase in energy usage.
Overall, our evaluation clearly indicates that the proposed blockchain–FHE system provides robust privacy and security while maintaining performance suitable for practical, scalable deployments.
8. Case Study and Practical Application
8.1. Regional EV Charging Network Simulation
To demonstrate the feasibility and practicality of our proposed blockchain–FHE architecture, we conducted an extensive simulation of a regional EV charging network comprising 20 interconnected charging stations. This network was managed by a consortium blockchain, where local utility companies, charging station operators, and regulatory authorities operated as validating nodes. Each station supported up to 50 concurrent charging sessions, reflecting realistic operational conditions.
8.2. Implementation Details
Key technical aspects of the simulation were as follows:
- FHE library: Utilized state-of-the-art cryptographic libraries optimized specifically for homomorphic arithmetic operations, minimizing computation latency.
- Blockchain platform: Deployed Hyperledger Fabric configured with Proof-of-Authority consensus, selected for its efficiency and ability to support enterprise-level smart contracts securely.
- Authorization workflow: Each EV user securely maintained encrypted identification tokens, verified through homomorphic equality checks executed by blockchain smart contracts.
- Billing mechanism: Real-time energy consumption data encrypted at charging stations was processed homomorphically to calculate billing statements, preserving user confidentiality entirely.
8.3. Operational Observations
Our simulation highlighted several key operational insights:
- Performance and scalability: Despite computational overhead due to homomorphic encryption, the distributed computational capabilities of blockchain nodes effectively maintained high throughput and low latency.
- Privacy assurance: Users’ sensitive information remained confidential throughout the entire process, significantly enhancing user trust and compliance with privacy regulations.
- Stakeholder collaboration: The consortium blockchain structure facilitated transparent collaboration among diverse stakeholders, enhancing system reliability and trust.
8.4. Summary of Practical Feasibility
The practical case study conclusively demonstrates that our blockchain–FHE framework provides an operationally viable solution for secure, privacy-preserving EV charging networks. The additional computational requirements introduced by homomorphic encryption are manageable and justified by substantial privacy and security improvements, indicating strong potential for real-world deployment.
8.5. Discussion
The performance results demonstrate that integrating fully homomorphic encryption into a blockchain-based EV-charging framework is both feasible and practical. While homomorphic operations introduced additional computational overhead relative to blockchain-only systems, the measured authorization and billing latencies remained well below one second—a threshold acceptable for real-time charging scenarios. The system’s throughput and minimal energy overhead further underscore its suitability for deployment in existing charging infrastructures.
Several aspects deserve deeper consideration. First, the primary limitation lies in computation costs: Even with GPU acceleration, the homomorphic multiplication and equality checks were significantly slower than conventional cryptographic operations. Research into more efficient lattice-based schemes or batching techniques could mitigate this constraint. Second, key management introduces complexity, as EV users must securely store private keys and regularly update certificates; integrating hardware security modules may ease this burden. Third, the experimental setup employed a controlled network with stable connectivity. Deploying the system across heterogeneous or intermittent networks may reveal latency spikes and synchronization challenges.
Notwithstanding these limitations, this approach offers compelling benefits. It eliminates plaintext exposure throughout authorization and billing, thereby thwarting profiling attacks and ensuring compliance with stringent data protection regulations. The modular design decouples homomorphic computation from the blockchain layer, allowing operators to scale the network by adding computation nodes or adjusting consensus parameters. Finally, the use of zero-knowledge proofs for billing verification provides transparent accountability without compromising privacy.
8.6. Future Directions
This work opens several avenues for further investigation:
- Cryptographic optimization. Advancing FHE libraries, investigating approximate or leveled homomorphic schemes, and exploring specialized hardware (e.g., FPGAs) may reduce latency and resource consumption.
- Encrypted analytics. Integrating machine-learning models that operate directly on encrypted data could support demand forecasting, dynamic pricing and anomaly detection without compromising user privacy.
- Broader IoT applications. The architecture can be adapted to other privacy-sensitive Internet-of-Things domains such as smart homes, supply chain logistics, or healthcare, where secure computation and immutable ledgers are valuable.
- Compliance and auditing frameworks. Developing regulatory frameworks and automated compliance checks—particularly for regimes such as the GDPR—would facilitate adoption in diverse jurisdictions.
- Large-scale pilot deployments. Collaboration with utilities, vehicle manufacturers, and regulatory bodies to conduct pilot studies will yield real-world insights into user adoption, scalability, and cost–benefit trade-offs.
9. Conclusions
We presented a privacy-preserving EV charging authorization and billing system that integrates permissioned blockchain with fully homomorphic encryption. By performing all authorization and billing computations on encrypted data and recording transactions immutably, our framework eliminates plaintext exposure and mitigates single points of failure. Quantitative evaluation on a prototype implementation demonstrated that the system achieves an authorization latency of 610 ms, an average throughput of 102 transactions per minute, and minimal energy overhead, while achieving very high privacy and security compared to blockchain-only or V2G-authentication schemes. A new discussion section analyzed limitations and future improvements. These results indicate that secure and scalable EV charging services can be realized today using blockchain and homomorphic encryption.
Author Contributions
Conceptualization, A.A. and S.A.; methodology, A.A. and S.A.; software, A.A. and S.A.; validation, A.A. and S.A.; formal analysis, A.A. and S.A.; investigation, A.A. and S.A.; resources, A.A. and S.A.; data curation, A.A. and S.A.; writing—original draft preparation, A.A. and S.A.; writing—review and editing, A.A. and S.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Acknowledgments
The author would like to thank the Deanship of Scientific Research at Shaqra University for supporting this research.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Saha, R.; Kumar, G.; Geetha, G.; Tai-Hoon-Kim; Alazab, M.; Thomas, R.; Rai, M.K.; Rodrigues, J.J.P.C. The Blockchain Solution for the Security of Internet of Energy and Electric Vehicle Interface. IEEE Trans. Veh. Technol. 2021, 70, 7495–7508. [Google Scholar] [CrossRef]
- Sahu, B.L.; Chandrakar, P.; Kumari, S.; Chen, C.-M.; Amoon, M. Blockchain and Machine Learning Integrated Secure Driver Behavior Centric Electric Vehicle Insurance Model. IEEE Trans. Intell. Transp. Syst. 2024, 25, 19073–19087. [Google Scholar] [CrossRef]
- Sharma, G.; Joshi, A.M.; Mohanty, S.P. sTrade: Blockchain based secure energy trading using vehicle-to-grid mutual authentication in smart transportation. Sustain. Energy Technol. Assess. 2023, 57, 103296. [Google Scholar] [CrossRef]
- Liu, H.; Lv, Z.; Song, Z.; Zhou, S.; Liu, W.; Fang, M. Application of Blockchain Technology in Electric Vehicle Charging Piles Based on Electricity Internet of Things. Wirel. Commun. Mob. Comput. 2022, 3, 1–10. [Google Scholar] [CrossRef]
- Zhang, F.; Shen, H.; Wang, D.; Xiang, J. The Wireless Charging Pavement System of Electric Vehicles Based on Block Chain. In Proceedings of the ICBCT ’20: Proceedings of the 2020 2nd International Conference on Blockchain Technology, Hilo, HI, USA, 12–14 March 2020; pp. 125–129. [Google Scholar] [CrossRef]
- Aldweesh, A. Blockchain-Based Secure Firmware Updates for Electric Vehicle Charging Stations in Web of Things Environments. World Electr. Veh. J. 2025, 16, 226. [Google Scholar] [CrossRef]
- Aldweesh, A. A Blockchain-Based Data Authentication Algorithm for Secure Information Sharing in Internet of Vehicles. World Electr. Veh. J. 2023, 14, 223. [Google Scholar] [CrossRef]
- Ren, W.; Sun, Y.; Luo, H.; Guizani, M. SILedger: A Blockchain and ABE-based Access Control for Applications in SDN-IoT Networks. IEEE Trans. Netw. Serv. Manag. 2021, 18, 4406–4419. [Google Scholar] [CrossRef]
- Subramanian, V.; Rajendra, Y.; Sahai, S.; Shukla, S.K. Decentralized Device Authentication Model using the Trust Score and Blockchain Technology for Dynamic Networks. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020. [Google Scholar] [CrossRef]
- Li, H.; Han, D.; Tang, M. A Privacy-Preserving Charging Scheme for Electric Vehicles Using Blockchain and Fog Computing. IEEE Syst. J. 2021, 15, 3189–3200. [Google Scholar] [CrossRef]
- Li, S.; Luo, D.; Liu, X.; Luo, R. Research on General Blockchain Security Architecture Based On Cloud Consortium Blockchain. In Proceedings of the 2023 IEEE International Conference on Paradigm Shift in Information Technologies with Innovative Applications in Global Scenario (ICPSITIAGS), Indore, India, 28–29 December 2023. [Google Scholar] [CrossRef]
- Jiang, Y.; Du, S.; Xu, W.; Dong, Y. V2G Charging and Discharging Information Authentication Based on Blockchain Technology. In Proceedings of the 2024 IEEE 4th International Conference on Digital Twins and Parallel Intelligence (DTPI), Wuhan, China, 18–20 October 2024. [Google Scholar] [CrossRef]
- Zhai, D.; Liu, J.; Zhang, T.; Wang, J.; Du, H.; Liu, T.; Wang, T.; Zhang, C.; Kang, J.; Niyato, D. EPDB: An Efficient and Privacy-Preserving Electric Charging Scheme in Internet of Robotic Things. IEEE Internet Things J. 2024, 11, 32464–32477. [Google Scholar] [CrossRef]
- Xu, X.; Zhao, H.; Yao, H.; Wang, S. A Blockchain-Enabled Energy-Efficient Data Collection System for UAV-Assisted IoT. IEEE Internet Things J. 2021, 8, 2431–2443. [Google Scholar] [CrossRef]
- Maitra, S.; Yanambaka, V.P.; Abdelgawad, A.; Yelamarthi, K. Securing a Vehicle Fleet Management Through Blockchain and Internet of Things. In Proceedings of the 2020 IEEE International Symposium on Smart Electronic Systems (iSES) (Formerly iNiS), Chennai, India, 14–16 December 2020. [Google Scholar] [CrossRef]
- Chen, C.-M.; Miao, Q.; Kumari, S.; Khan, M.K.; Rodrigues, J.J.P.C. A Privacy-Preserving Authentication Protocol for Electric Vehicle Battery Swapping Based on Intelligent Blockchain. IEEE Internet Things J. 2024, 11, 17538–17551. [Google Scholar] [CrossRef]
- Sahu, B.L.; Chandrakar, P. Blockchain-Based Framework for Electric Vehicle Charging Port Scheduling. In Proceedings of the 2022 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Gandhinagar, India, 18–21 December 2022. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).