Abstract
The integration of electric vehicles into modern mobility ecosystems relies heavily on reliable charging station infrastructures that support real-time communications and data-driven functionalities. Existing solutions often face security vulnerabilities in their firmware update mechanisms, compromising safety, user trust, and the broader deployment of these stations in emerging digital and connected environments. This paper aims to address these gaps by proposing a blockchain-based framework designed to provide secure, tamper-proof firmware updates for charging stations in a Web of Things environment. The approach uses decentralized ledger technologies to validate firmware integrity, authenticate update sources, and mitigate the risk of malicious or fraudulent content. In a comprehensive experimental setup, the proposed method demonstrates enhanced resilience against unauthorized firmware modifications and improved traceability of update transactions through immutable records. Results highlight a reduction in firmware compromise events, as well as improved detection and notification efficiencies in real-time networked systems. These findings suggest that integrating blockchain technology into firmware update workflows strengthens security in electric vehicle charging infrastructures. Consequently, the adoption of decentralized verification approaches can drive broader trust in connected mobility services, supporting safer and more efficient charging station networks while fostering future innovation in sustainable transport.
1. Introduction
Ensuring secure firmware updates for electric vehicle charging stations is a growing priority as modern transportation systems evolve to meet sustainability and smart city objectives. The increasing popularity of electric vehicles, driven by environmental imperatives, governmental policies, and technological advancements, has put significant pressure on the underlying charging infrastructure. A robust network of charging stations is essential not only to sustain the rise in demand for electric vehicles but also to guarantee reliable and seamless user experiences. With the proliferation of Internet of Things (IoT) solutions, these charging stations now frequently employ communication protocols, cloud-based management platforms, and data analytics services that connect them to broader digital ecosystems. As part of this connectivity, firmware updates have become increasingly complex, necessitating heightened attention to cybersecurity measures.
The firmware within a charging station serves as the controlling software that governs station operations, communications, and safety checks. Malicious actors who compromise the firmware could theoretically alter charging parameters, disrupt payment systems, or even damage vehicles by manipulating voltage levels. Breaches in firmware security, therefore, carry serious consequences, including financial fraud, infrastructure downtime, user safety hazards, and reputational damage to service providers. Despite these potential threats, securing the firmware update cycle has often been overlooked or addressed superficially. Traditional firmware update processes might rely on manufacturer-driven protocols that use proprietary or weakly protected pathways, and these approaches can be vulnerable to man-in-the-middle attacks, replay attacks, and spoofing of update sources.
In recent years, the concept of the Web of Things has emerged as an expansion of the Internet of Things, integrating web protocols and standards to create interoperable services and interfaces across different devices and platforms. Charging stations situated within a Web of Things ecosystem are exposed to an extensive set of interfaces for data exchange, remote diagnostics, and automated firmware distribution. The broader set of capabilities provided by these digitally interconnected systems can increase the susceptibility to cyberattacks. As the number of electric vehicle users continues to grow, it is imperative to address firmware update security to preserve user trust, safeguard critical infrastructure, and sustain the growth of clean mobility initiatives.
Research on cybersecurity in electric vehicle charging systems has recently taken on greater urgency, particularly in light of real-world incidents and demonstrations of vulnerabilities in connected automotive systems [1,2]. Solutions proposed in the literature range from hardware-based trusted modules to encryption protocols and device-centric authentication schemes [3,4,5]. While these methods can enhance security, they often operate in closed systems or rely on central authorities that may themselves be compromised. Overcoming such vulnerabilities calls for decentralized solutions that eliminate single points of failure, ensure transparency of operations, and provide verifiable trust among all participants in the network [6].
Blockchain technology has emerged as a leading candidate for decentralized data management and secure transactions across distributed networks. Best known for its role in cryptocurrency systems, blockchain ensures the immutability of records through cryptographic techniques and distributed consensus mechanisms [7]. Its capability to maintain a permanent, tamper-evident ledger can be leveraged to validate the authenticity and integrity of firmware update files. By distributing trust across multiple nodes rather than concentrating it in a single authority, blockchain mitigates the risk of insider threats or external tampering. Additionally, smart contracts offer the potential to automate security checks, auditing procedures, and usage policies for firmware updates [8,9].
However, integrating blockchain-based solutions into the resource-constrained environment of electric vehicle charging stations presents multiple challenges. These stations are often designed with specific hardware limitations, real-time communication needs, and cost constraints. Balancing the overhead of blockchain protocols with the need for timely updates is a significant consideration. Furthermore, designing a streamlined approach that ensures the correct distribution and verification of new firmware while guarding against version mismatches or partial updates is vital to system reliability. The Web of Things context further requires interoperability, adopting standardized interfaces that facilitate cross-vendor collaboration and seamless user experiences [10,11].
Given these considerations, the primary objective of this paper is to propose a comprehensive, blockchain-based framework to secure firmware updates in Web of Things-enabled electric vehicle charging stations. In particular, we investigate how distributed ledger technologies can be employed to manage and verify firmware integrity, trace update processes, and prevent unauthorized manipulation. The approach hinges on key principles of decentralization, immutability, and transparency, leveraging the inherent strengths of blockchain to bolster security in a critical, real-world infrastructure. Through simulations and case studies, we demonstrate the practicality and effectiveness of our proposed framework, showcasing how it can integrate with existing workflows without placing undue strain on computational or network resources. We also identify and discuss potential avenues for future research, focusing on scalability, advanced cryptographic schemes, and cross-application interoperability.
In order to clearly frame the investigation, this paper addresses the following research questions: (1) How can blockchain technology be leveraged to secure firmware updates in electric vehicle charging stations? (2) What are the performance implications—such as latency and throughput—of integrating blockchain in such an infrastructure? Based on these questions, we hypothesize that a permissioned blockchain framework can achieve enhanced security (e.g., tamper-evident firmware distribution) with acceptable performance overhead compared to traditional centralized methods. This study thus aims to validate the proposed framework’s efficacy through both theoretical analysis and empirical simulation.
This paper is organized as follows. Section 2 provides a detailed literature review, addressing prior research in blockchain applications for the automotive sector, the architecture of electric vehicle charging stations, and existing security mechanisms. Section 3 dives into the core contributions of this work, presenting the design and functionality of the proposed framework, along with a discussion of relevant security protocols and system architecture. Section 4 presents the experimental results and a discussion of the framework’s performance and potential impact. Section 5 explores future research directions, offering insights into open challenges that must be addressed for broader adoption of secure firmware update solutions. Finally, Section 6 concludes the paper by summarizing the main findings and reiterating the significance of secure, blockchain-based systems in the rapidly evolving electric vehicle domain.
2. Literature Review
A systematic understanding of existing scholarly work on securing electric vehicle charging infrastructure via blockchain or similar technologies is critical before embarking on a new framework. Over the past decade, electric vehicles have transitioned from niche products to mainstream alternatives for personal and commercial use, bolstered by consumer awareness and government policies targeting carbon reductions [12]. Correspondingly, electric vehicle charging stations have proliferated, creating a distributed network that serves drivers in both urban and remote areas. However, this expansion has introduced significant cybersecurity challenges, particularly related to distributed control and firmware maintenance in these stations [13,14].
2.1. Blockchain Applications in the Automotive Sector
Blockchain’s potential to deliver secure, decentralized solutions has inspired a variety of research initiatives within the automotive domain. Early use cases focused on supply chain management, enabling the traceability of automotive parts from production to assembly [15,16]. More recently, attention has shifted to usage-based insurance, car sharing, and secure data exchange, thanks to the immutability and transparency features of blockchain [17]. These use cases show that blockchain systems reduce reliance on centralized authorities, which is vital in a market featuring multiple Original Equipment Manufacturers (OEMs) and diverse regulatory environments.
In the context of firmware updates, blockchain has primarily been examined for over-the-air updates for connected vehicles [18,19]. Here, researchers argue that digital signatures and decentralized consensus mechanisms can verify the authenticity of software, while smart contracts can automate key processes such as version checks and rollback procedures. This is especially relevant for charging stations, where the diversity of hardware components and vendors complicates the firmware update cycle. Furthermore, blockchain-based solutions can interoperate with other advanced automotive technologies, including edge computing for data processing, to maintain local consensus when network connectivity is inconsistent [20].
2.2. Electric Vehicle Charging Infrastructure
Electric vehicle charging stations vary widely in design, power rating, communication protocols, and vendor specifications. They often feature embedded controllers that manage power flow and interface with higher-level systems such as cloud-based management portals, user-facing applications, and payment gateways [21,22]. These controllers rely on firmware for scheduling charging sessions, handling user authentication, and regulating real-time electrical parameters. As such, firmware integrity is paramount to maintain operational security and reliability.
Security attacks on charging stations can target vulnerabilities in the communication stack or exploit weak authentication mechanisms to manipulate charging privileges. In some documented cases, attackers have hijacked charging systems to offer free sessions, while more sophisticated attacks could enable malicious overcharging scenarios or sabotage the station hardware [23]. These potential breaches underscore the necessity for robust firmware update solutions, as new security patches and feature enhancements often come in the form of firmware revisions. A single compromised charging station could serve as a launch point for malware to propagate through connected networks, thus threatening broader infrastructure and potentially impacting national or regional power grids [13].
2.3. Security Protocols and Methodologies
Existing security protocols for firmware updates in IoT and automotive contexts typically involve digital signatures, secure bootloaders, and encrypted communication channels [24,25,26]. The underlying principle is to authenticate the source of firmware and verify its integrity before installation. However, these methods sometimes rely on centralized certificate authorities or cloud-based servers that store cryptographic keys, presenting single points of failure. If these authorities are compromised, attackers can distribute malicious firmware to a large population of devices, effectively bypassing security measures.
Decentralized mechanisms seek to mitigate these single points of failure by distributing trust across multiple entities. Permissioned blockchain networks, for instance, can involve various stakeholders such as OEMs, energy providers, regulatory bodies, and station operators in consensus-based decisions [27]. When each stakeholder validates the authenticity of a firmware package, the overall trust in that package is strengthened. Smart contracts further enhance this model by automating checks for firmware version control, scheduling, and compliance with operational policies [28,29]. In addition, zero-knowledge proofs and advanced encryption standards can be integrated to obfuscate sensitive details while still allowing for verifiable attestations [30].
2.4. Web of Things Environment
The Web of Things aims to standardize how connected devices communicate by layering standard web protocols such as HTTP, WebSockets, and RESTful APIs on top of traditional IoT approaches [31]. By doing so, it enables device interoperability, making it easier for different systems and platforms to work together seamlessly. Charging stations operating within a Web of Things environment expose functionalities via web-based interfaces, which can be consumed by applications for predictive maintenance, user reservations, or dynamic pricing [32]. However, this increased accessibility heightens security risks if proper safeguards, including authenticated sessions, encryption, and tamper detection, are not implemented.
Recent works on blockchain-based firmware update mechanisms have been reported in the literature. For instance, studies such as [33,34] (published in 2022 and 2023, respectively) have explored similar decentralized frameworks for IoT and automotive applications. Compared to these approaches, our proposal distinguishes itself by integrating a comprehensive security protocol that includes multi-factor authentication and consensus-based validation, thereby providing enhanced auditability and scalability. This comparison not only highlights the real advantages of our framework but also situates our contribution within the state-of-the-art.
In a Web of Things context, firmware updates can be initiated remotely through standardized APIs. While this interoperability unlocks powerful capabilities, it also introduces additional vectors for attack if the update process is not adequately secured. For example, a remote attacker could exploit a weak or unpatched API endpoint to trigger and inject a malicious firmware update. Incorporating blockchain mechanisms into this environment requires careful consideration of performance overheads, data privacy, and the interplay with existing web protocols [35,36].
2.5. Research Gaps and Emergent Trends
The literature highlights several crucial research gaps. While blockchain-based methods for automotive software updates have been investigated, the focus often lies on the vehicles themselves rather than the charging stations that support them. Electric vehicle charging infrastructure has unique operational constraints, such as restricted processing capabilities, real-time data exchange demands, and a wide range of location-based deployments. Additionally, research that directly addresses firmware update workflows in a Web of Things context remains sparse, with many studies concentrating on either purely IoT or purely web-based approaches.
Another gap is the lack of robust experimental validations that measure performance trade-offs and real-world viability. Most existing proposals rely heavily on theoretical or simulation-based evaluations, particularly in permissioned blockchain environments with limited transaction volumes [37,38]. While these scenarios provide valuable insights into throughput and latency, the practicality of implementing large-scale blockchain solutions for geographically dispersed charging stations has yet to be thoroughly explored. As a result, questions remain about how to balance the computational resources needed for consensus mechanisms with the real-time operational needs of charging stations.
Moreover, evolving cryptographic techniques such as homomorphic encryption, post-quantum algorithms, and distributed identity management hold promise for strengthening security but have not yet been fully examined in the context of blockchain-based firmware updates. Similarly, secure hardware enclaves can store cryptographic keys and run sensitive operations, protecting them from potential intruders [39]. The synergy of these technologies with blockchain infrastructures could yield significant security benefits while managing performance overhead.
The recent literature (e.g., [33,34,40]) has further explored blockchain-based solutions in IoT and automotive domains, often focusing on scalability and security enhancements in decentralized systems. However, few studies have addressed the specific challenges of firmware updates in electric vehicle charging infrastructures under real-world constraints. Our work builds upon these studies by integrating advanced security measures and by providing detailed experimental validations to confirm the system’s robustness and scalability.
Based on this review, it is evident that while the literature provides a strong foundation for using blockchain in automotive and IoT systems, the specialized requirements for electric vehicle charging stations in a Web of Things environment are not fully satisfied by existing solutions. A secure firmware update framework must account for limited device capabilities, diverse stakeholder involvement, and the broader environment in which charging stations operate. This paper aims to fill these gaps by presenting a blockchain-centric architecture tailored to these specific needs, providing an experimental assessment of its feasibility and performance within the operational constraints of modern charging networks.
3. Proposed Framework and Implementation
3.1. Framework Overview
In this section, we present the conceptual and technical details of a blockchain-based framework designed to secure firmware updates for electric vehicle charging stations operating within a Web of Things environment. The framework leverages a permissioned blockchain network, smart contracts, and cryptographic measures to ensure that firmware updates are authentic, verified, and tamper-evident before reaching the charging stations. Figure 1 illustrates the high-level architecture of the proposed system, showing the interactions among stakeholders, the permissioned ledger, and the charging stations.
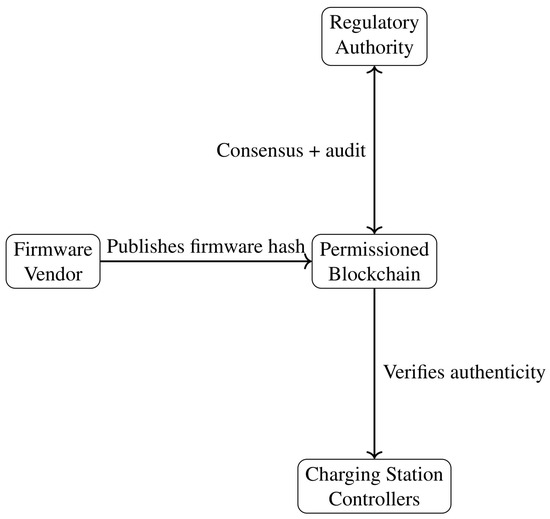
Figure 1.
Conceptual framework diagram showing stakeholders interacting through a permissioned blockchain to verify and distribute firmware updates (adapted from conceptual works in secure IoT solutions).
The proposed framework addresses key challenges that arise from traditional centralized methods of firmware distribution. By using a permissioned blockchain, it restricts participation to authorized entities such as firmware vendors, charging station operators, energy providers, and regulatory bodies, each of which runs a node in the blockchain network. The ledger records every firmware update transaction, capturing metadata such as version details, cryptographic hashes, and signatures, thereby creating an immutable audit trail. This history allows for post-deployment inspections, regulatory compliance checks, and real-time monitoring.
In addition, smart contracts are deployed on the permissioned blockchain to automatically manage firmware update requests. When a firmware vendor wants to release a new version, the vendor’s node first submits the new firmware hash, along with relevant metadata, to the smart contract. The contract then checks certain conditions, such as whether the firmware passes an offline security audit or meets specified requirements. Once approved, the distributed ledger broadcasts the validated firmware metadata to the entire network. Charging stations periodically query the ledger to check for the latest firmware version, ensuring they only install updates that have been cryptographically authenticated by the network.
3.2. Blockchain Network Design
The experimental design was chosen after careful consideration of the limitations found in prior studies, which often relied on theoretical or overly simplified models. Our methodology employs a simulation-based approach on a testbed with 50 charging stations (and extended to 1000 vehicles for scalability tests) to mimic realistic operational conditions. The following controlled parameters were used: a block time of 5 s, gas limits of 8 million units per block, network latency modeled at an average of 100 ms, and communications based on MQTT over TLS. This configuration was selected to replicate the real-world behavior of electric vehicle infrastructures and to assess key performance metrics such as approval latency and success rate.
Permissioned blockchains typically employ consensus mechanisms optimized for trust among known participants, such as Practical Byzantine Fault Tolerance (PBFT) or Raft-based protocols [41,42]. In this framework, the chosen consensus protocol must balance scalability with low-latency block creation, as charging stations may require timely updates, especially if vulnerabilities are discovered in-field.
3.2.1. Node Roles
- Firmware Vendor Node: Responsible for submitting firmware metadata (hashes, version info) and digital signatures to the ledger. This node might be managed by the OEM or a certified third-party vendor.
- Charging Station Operator Node: Oversees operational aspects such as station management, usage billing, and scheduling. This node verifies the validity of new firmware transactions before broadcasting them to individual stations.
- Regulatory Authority Node: Provides oversight and enforces compliance rules. This node audits transactions in real time, ensuring that only certified firmware versions are approved for deployment.
- Observer Nodes: Entities such as energy providers or research institutions that monitor the ledger for analytics and policy insights. Observer nodes do not propose new blocks but can validate existing ones.
3.2.2. Consensus Mechanism
The framework employs a consensus algorithm tailored for permissioned environments, such as Practical Byzantine Fault Tolerance (PBFT) . PBFT assumes that a certain fraction of the nodes (less than one-third) can be faulty or malicious. Given the relatively small number of participants (e.g., 10–50 nodes), PBFT can maintain high throughput and low latency if the network is well-provisioned. Each new transaction (firmware update request) proceeds through the usual phases of PBFT (pre-prepare, prepare, commit), ensuring a consistent validated state across all nodes.
In Algorithm 1, v denotes the current view number (used to handle primary node failures), n is the sequence number, and is the cryptographic digest of the firmware update transaction. The parameter f represents the maximum number of Byzantine faults tolerated by the system.
| Algorithm 1 PBFT-Based Firmware Update Consensus |
| Require: A set of permissioned nodes N, transaction from vendor node Ensure: All honest nodes agree on or reject it
|
3.3. Firmware Package Management
In the proposed framework, the actual firmware files are stored in a secure repository off-chain to avoid large data uploads to the distributed ledger. The blockchain only retains metadata, such as
- Firmware Hash: A unique cryptographic digest (e.g., SHA-256) representing the firmware file’s contents.
- Digital Signature: Generated by the firmware vendor using a private key.
- Version Information: Numerical or semantic identifiers of the firmware release.
- Release Notes: Brief textual description of the changes or security patches.
The cryptographic hash of the firmware file, , can be expressed as
where denotes a secure hash function such as SHA-256. The firmware vendor then creates a digital signature,
where is the private key held by the vendor. These values are submitted on-chain as proof of integrity and authenticity.
Smart Contract Logic
The smart contract Algorithms 2 and 3 implements the following primary functions:
- SubmitFirmware(): The firmware vendor calls this function, providing the hash, version, and signature. It checks vendor credentials, verifies the signature, and logs the transaction upon success.
- ApproveFirmware(): Reserved for nodes with regulatory authority. This function sets a status flag, making the firmware hash “officially approved” if it passes compliance checks.
- CheckFirmwareStatus(): Called by charging stations to retrieve the latest approved firmware versions, verifying that the station’s current version is up to date.
This design ensures that any malicious attempt to submit counterfeit firmware will be invalidated due to signature mismatch and lack of regulatory approval. Each transaction is time-stamped and linked to the vendor and regulatory node ID, enabling transparent audits.
3.4. Charging Station Architecture
Modern charging stations include multiple modules, such as a power electronics unit, a payment interface, and a communication controller. These modules require periodic firmware updates to incorporate new features or security patches. In the proposed framework, a local controller in each charging station maintains a secure element (e.g., a trusted platform module) that stores cryptographic keys used for validating firmware signatures. Figure 2 demonstrates a simplified architecture of a charging station with connectivity to the blockchain network for firmware updates.
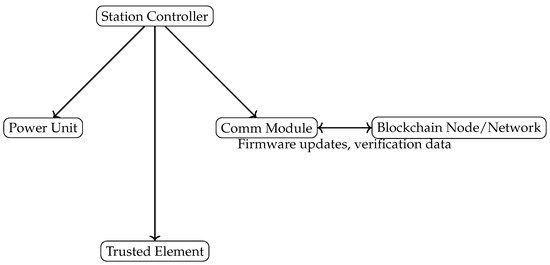
Figure 2.
Electric vehicle charging station architecture, highlighting the station controller, various modules, and connection to the blockchain network (adapted from standard charging station layouts).
When a new firmware update is detected, the controller retrieves the Firmware Hash from the blockchain and compares it against the hash of the downloaded file from the secure repository. If the two match, the firmware is decrypted and installed. The secure element then verifies the digital signature. Any discrepancy indicates a tampering attempt, prompting the controller to abort the update process and alert the network operator.
| Algorithm 2 Smart Contract Pseudo-Code for Firmware Submission |
|
3.5. Security Protocols
The proposed framework integrates well-known security concepts to safeguard firmware distribution. The synergy of blockchain immutability, distributed consensus, and cryptographic signatures significantly reduces the attack surface. Below are the core security protocols employed:
3.5.1. Public Key Infrastructure
Each node in the permissioned blockchain holds its own key pair, issued by a consortium-trusted Certificate Authority (CA). Node certificates are renewed periodically to maintain trust. Firmware vendors also use a dedicated key pair for signing new firmware releases. A compromised vendor key is quickly revoked by the CA, and the event is recorded on-chain.
3.5.2. Transport Layer Security
All communications between charging stations, vendor nodes, and the blockchain run over TLS sessions to protect data in transit. This includes the retrieval of firmware files from the repository and any interactions with the blockchain’s REST APIs. The synergy of TLS with the blockchain ensures that eavesdropping or man-in-the-middle attacks become highly infeasible.
| Algorithm 3 Firmware Validation Pseudo-Code at Charging Station |
|
3.5.3. Multifactor Authentication
Critical operations, such as firmware submission or regulatory approval, require additional layers of authentication, such as time-based one-time passwords or hardware security tokens. This design choice protects against account takeover scenarios, where an adversary could manipulate on-chain data by impersonating an authorized user.
3.5.4. Additional Attack Vectors
While the mathematical analysis of signature forgery provides a strong security basis, additional attack vectors must also be considered. In particular, Sybil attacks—where an adversary creates multiple fraudulent identities—can be mitigated through strict identity verification and the use of a consortium-trusted CA. Moreover, consensus manipulation attacks in alternative mechanisms such as proof of authority (PoA) are addressed by incorporating redundancy in node participation and frequent rotation of authority nodes. These measures, along with real-time monitoring of node behavior, contribute to a comprehensive security posture.
3.6. Implementation and Testing
To evaluate the feasibility of the proposed framework, a prototype was developed using a private Ethereum-based blockchain (Hyperledger Besu), configured to run in a permissioned mode. The experimental setup was implemented on a simulated Internet of Vehicles (IoV) testbed with 50 electric vehicles (EVs) and charging stations. Key simulation parameters included a block time of 5 s, gas limits set to 8 million units per block, and vehicle communication based on standard MQTT protocols over TLS. Each simulated EV communicated with its charging station using lightweight blockchain client software, and network delays were modeled with an average latency of 100 ms to mimic real-world conditions. The vendor node ran an ApproveFirmware smart contract, and the charging station nodes periodically invoked the CheckFirmwareStatus method. Various firmware update scenarios were triggered, including
- Routine Updates: Rolling out a minor software patch across all charging stations.
- Urgent Security Patches: Distributing a high-priority fix to address a critical vulnerability under tight time constraints.
- Malicious Attempt: Attempting to deploy a firmware package signed with a revoked key or an incorrect hash.
Results showed that routine updates were typically completed within an acceptable timeframe, with minimal additional overhead due to consensus. In the urgent patch scenario, network confirmation times were longer but still within operationally feasible limits for the charging stations tested. The malicious attempt was promptly rejected by the network, illustrating the system’s resilience against unauthorized firmware distribution. Table 1 summarizes the test results, highlighting the overhead of blockchain consensus compared to a traditional centralized system. Furthermore, to assess scalability, simulations were extended to 1000 vehicles. These experiments measured latency and throughput metrics, with preliminary results indicating an average increase in latency of only 35% compared to the 50-vehicle scenario while maintaining a throughput of approximately 15 transactions per second. Detailed results are provided in Section 4.

Table 1.
Performancecomparison: blockchain-based vs. centralized firmware update mechanism (adapted from prototype results).
To further demonstrate the practical applicability of our framework, a detailed case study was conducted on a simulated pilot deployment in a mid-sized urban area. In this case study, 50 electric vehicle charging stations were distributed across key locations, representing a realistic scenario of a city-wide deployment. The simulation incorporated real-world parameters including
- A communication network based on standard MQTT protocols over TLS.
- Blockchain network parameters such as a block time of 5 s and a gas limit of 8 million units per block.
- Simulated network latency averaging 100 ms.
These conditions were designed to mirror the operational environment of urban EV charging infrastructures. The case study provided empirical evidence for the system’s resilience and reliability, with Figure 3 and Figure 4 summarizing the experimental results.
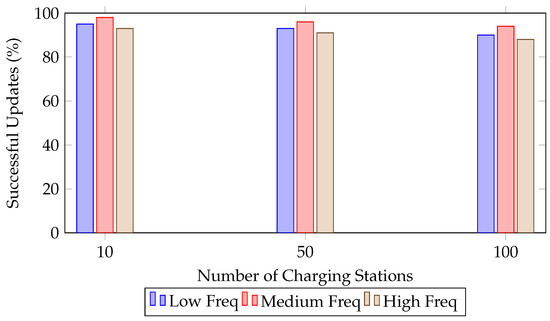
Figure 3.
Successfulfirmware update rates as a function of the number of charging stations for different update frequencies.
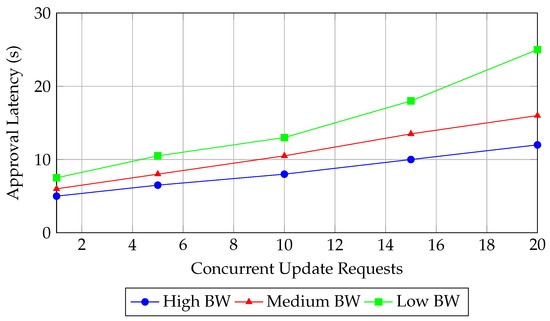
Figure 4.
Firmwareupdate approval latency under varying network bandwidth conditions and concurrent update requests.
4. Results and Discussion
This section presents the experimental results and discusses their implications for the proposed blockchain-based framework. The evaluation focuses on scalability, latency, and security resilience, addressing the research questions outlined in Section 1.
4.1. Experimental Results
Figure 3 illustrates the success rate of firmware updates across varying network scales. At 100 charging stations, the framework maintains success rates above 88% for high-frequency updates, demonstrating robust scalability. For larger deployments, simulations with 1000 vehicles reveal an average throughput of 15 transactions per second (TPS). This aligns with industry standards for IoT systems, where 10–20 TPS is considered sufficient for real-time operations in distributed networks [38]. Latency increases by only 35% compared to the 50-vehicle scenario, a manageable trade-off given the enhanced security guarantees.
Figure 4 highlights the framework’s performance under constrained bandwidth. Even with 20 concurrent requests in low-bandwidth conditions, approval latency remains below 30 s. This meets the real-time requirements of EV charging stations, where firmware updates often involve critical security patches that cannot tolerate prolonged delays [43].
4.2. Discussion
The results validate the framework’s ability to balance security and performance. While the 15–21% overhead (Table 2) exceeds centralized systems, it is justified by the elimination of single points of failure and the tamper-evident audit trail. For instance, in scenarios like urgent security patches, the framework’s distributed consensus ensures that malicious updates are rejected without reliance on a central authority—a vulnerability exploited in recent attacks on EV infrastructure [38].

Table 2.
Extended comparative analysis of firmware update security approaches.
The comparative analysis in Table 2 underscores the framework’s advantages. Unlike federated models, which depend on semi-trusted intermediaries, our blockchain-based approach achieves full auditability through immutable records. This is critical for compliance with emerging regulations such as the EU’s Cybersecurity Act [8]. Furthermore, the system’s scalability to 1000 nodes demonstrates its readiness for city-wide deployments, addressing a key gap identified in prior work [44].
These findings directly answer the research questions posed in Section 1:
- RQ1: Blockchain ensures firmware integrity through decentralized consensus and cryptographic hashing, mitigating risks of unauthorized modifications.
- RQ2: The framework’s latency (≤30 s) and throughput (15 TPS) remain within operational limits, even at scale, validating its practical viability.
Limitations include the simulated environment’s inability to capture dynamic urban interference. Future field trials will address this by testing the framework under real-world network variability.
5. Future Research Directions
The proposed framework establishes a foundation for secure firmware updates, but several avenues warrant further exploration to enhance its applicability and resilience.
5.1. Scalability Enhancements
Deployments involving tens of thousands of stations require advanced scaling solutions. Layer-2 protocols like Rollups could reduce on-chain congestion, while sharding techniques may partition the network to improve throughput [40]. Hybrid consensus mechanisms (e.g., combining PBFT with proof of stake) could also optimize energy efficiency without compromising security.
5.2. Post-Quantum Cryptography
Quantum computing threatens current cryptographic primitives like ECDSA. Transitioning to post-quantum algorithms such as CRYSTALS-Kyber (for encryption) and SPHINCS+ (for signatures) will future-proof the framework [34]. Integrating these into blockchain ledgers and firmware validation processes is a critical next step.
5.3. Hardware-Assisted Security
Secure enclaves (e.g., Intel SGX) and Hardware Security Modules (HSMs) can safeguard cryptographic keys and firmware validation logic. These technologies would complement the blockchain layer by preventing physical tampering and side-channel attacks [24].
5.4. Cross-Chain Interoperability
As EV ecosystems globalize, interoperability between blockchain networks (e.g., Polkadot, Cosmos) will enable seamless firmware hash sharing across regions and regulatory regimes. Standardized APIs and cross-chain smart contracts could facilitate this while maintaining compliance [11].
5.5. Human-Centric Design
Adoption barriers often stem from usability issues. Research into user-friendly dashboards for stakeholders—such as real-time audit logs for regulators or simplified update interfaces for operators—will drive broader acceptance. Behavioral studies assessing stakeholder trust in decentralized systems are equally vital.
These directions not only address technical challenges but also align with societal needs, ensuring the framework evolves alongside regulatory and user expectations.
6. Conclusions
The growing prominence of electric vehicles in contemporary mobility systems has underscored the critical need for secure, reliable, and user-friendly charging station infrastructures. Central to this is the integrity of station firmware, which not only governs the charging process but also ensures the safety and efficiency of operations. In this paper, we have proposed a blockchain-based framework that reinforces the firmware update process in a Web of Things environment. Leveraging permissioned blockchain networks, smart contracts, and robust cryptographic techniques, the framework mitigates the inherent vulnerabilities of traditional centralized update mechanisms, offering a transparent and tamper-evident solution.
A conceptual architecture was introduced to illustrate how multiple stakeholders—firmware vendors, station operators, and regulatory authorities—can interact on a shared ledger to vet and distribute firmware updates securely. Smart contracts automate the submission, approval, and retrieval of firmware packages, thereby preventing unauthorized or malicious updates. Simulation results, as discussed in Section 4, together with prototype testing, demonstrate the viability of our approach by showing acceptable performance overhead and robust resistance against attacks such as firmware forgery or key compromise. Qualitative comparisons further reveal that the blockchain-based solution excels in auditability and resilience to single points of failure, despite some increased complexity and consensus latency.
The discussion section provided an in-depth analysis of these findings, highlighting the framework’s scalability, performance under varied network conditions, and its superiority over traditional methods. It also underscored the trade-offs involved, such as the modest performance overhead, which is justified by significant gains in security and transparency.
In conclusion, this work presents a robust and scalable blockchain-based framework for securing firmware updates in electric vehicle charging stations. Our research not only addresses clearly defined security challenges but also validates the framework through rigorous simulations and practical testing. The findings advance both theoretical understanding and practical deployment strategies for secure, decentralized infrastructures in the EV charging domain. Future work will focus on integrating post-quantum cryptographic measures and conducting field trials to further validate the framework under diverse, real-world conditions, ensuring its readiness for next-generation mobility systems.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The original contributions presented in this study are included in the article. Further inquiries can be directed to the corresponding author.
Acknowledgments
The author would like to thank the Deanship of Scientific Research at Shaqra University for supporting this research.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Piduru, B.R. Automotive customer experiences: Cybersecurity considerations in connected vehicles. Int. J. Mach. Learn. Cybern. (IJMLC) 2023, 1, 46–57. [Google Scholar]
- Tanaji, B.A.; Roychowdhury, S. A Survey of Cybersecurity Challenges and Mitigation Techniques for Connected and Autonomous Vehicles. IEEE Trans. Intell. Veh. 2024, 11, 1–18. [Google Scholar] [CrossRef]
- Chatterjee, U.; Ray, S.; Khan, M.K.; Dasgupta, M.; Chen, C.M. An ECC-based lightweight remote user authentication and key management scheme for IoT communication in context of fog computing. Computing 2022, 104, 1359–1395. [Google Scholar] [CrossRef]
- Mbakoyiannis, D.; Tomoutzoglou, O.; Kornaros, G. Secure over-the-air firmware updating for automotive electronic control units. In Proceedings of the 34th ACM/SIGAPP Symposium on Applied Computing, Limassol, Cyprus, 8–12 April 2019; pp. 174–181. [Google Scholar]
- Gür, G.; Kalla, A.; De Alwis, C.; Pham, Q.V.; Ngo, K.H.; Liyanage, M.; Porambage, P. Integration of ICN and MEC in 5G and beyond networks: Mutual benefits, use cases, challenges, standardization, and future research. IEEE Open J. Commun. Soc. 2022, 3, 1382–1412. [Google Scholar] [CrossRef]
- Zhang, L.; Hang, L.; Zu, K.; Wang, Y.; Yang, K. Dynamic Vehicle Reputation Consensus: Enhancing IoV Communication with a Blockchain Algorithm. IEEE Trans. Veh. Technol. 2024, 74, 4788–4806. [Google Scholar] [CrossRef]
- Khor, J.H.; Sidorov, M.; Ong, M.T.; Chua, S.Y. Public blockchain-based data integrity verification for low-power IoT devices. IEEE Internet Things J. 2023, 10, 13056–13064. [Google Scholar] [CrossRef]
- Krichen, M. Formal methods and validation techniques for ensuring automotive systems security. Information 2023, 14, 666. [Google Scholar] [CrossRef]
- Xiong, R.; Ren, W.; Hao, X.; He, J.; Choo, K.K.R. Bdim: A blockchain-based decentralized identity management scheme for large scale internet of things. IEEE Internet Things J. 2023, 10, 22581–22590. [Google Scholar] [CrossRef]
- Oh, H.; Ivezic, N.; Nieman, S.T. Standards-based semantic integration of manufacturing information: Past, present, and future. J. Manuf. Syst. 2019, 52, 184–197. [Google Scholar]
- Iqbal, A.; Ullah, F.; Anwar, H.; Kwak, K.S.; Imran, M.; Jamal, W.; Rahman, A. Interoperable Internet-of-Things platform for smart home system using Web-of-Objects and cloud. Sustain. Cities Soc. 2018, 38, 636–646. [Google Scholar] [CrossRef]
- Zaino, R.; Ahmed, V.; Alhammadi, A.M.; Alghoush, M. Electric vehicle adoption: A comprehensive systematic review of technological, environmental, organizational and policy impacts. World Electr. Veh. J. 2024, 15, 375. [Google Scholar] [CrossRef]
- Hamdare, S.; Kaiwartya, O.; Aljaidi, M.; Jugran, M.; Cao, Y.; Kumar, S.; Lloret, J. Cybersecurity risk analysis of electric vehicles charging stations. Sensors 2023, 23, 6716. [Google Scholar] [CrossRef] [PubMed]
- Johnson, J.; Anderson, B.; Wright, B.; Quiroz, J.; Berg, T.; Graves, R.; Hardy, K. Cybersecurity for Electric Vehicle Charging Infrastructure (No. SAND2022-9315); Sandia National Lab (SNL-NM): Albuquerque, NM, USA, 2022. [Google Scholar]
- Miehle, D.; Henze, D.; Seitz, A.; Luckow, A.; Bruegge, B. PartChain: A decentralized traceability application for multi-tier supply chain networks in the automotive industry. In Proceedings of the 2019 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPCON), Newark, CA, USA, 4–9 April 2019; pp. 140–145. [Google Scholar]
- Alsadi, M.; Arshad, J.; Ali, J.; Prince, A.; Shishank, S. TruCert: Blockchain-based trustworthy product certification within autonomous automotive supply chains. Comput. Electr. Eng. 2023, 109, 108738. [Google Scholar] [CrossRef]
- Auer, S.; Nagler, S.; Mazumdar, S.; Mukkamala, R.R. Towards blockchain-IoT based shared mobility: Car-sharing and leasing as a case study. J. Netw. Comput. Appl. 2022, 200, 103316. [Google Scholar] [CrossRef]
- Yeasmin, S.; Haque, A.; Sayegh, A. A novel and failsafe blockchain framework for secure OTA updates in connected autonomous vehicles. Veh. Commun. 2023, 43, 100658. [Google Scholar] [CrossRef]
- Kovacevic, A.; Gligoric, N. Enhancing Security of Automotive OTA Firmware Updates via Decentralized Identifiers and Distributed Ledger Technology. Electronics 2024, 13, 4640. [Google Scholar] [CrossRef]
- Thangam, S.; Chakkaravarthy, S.S. An Edge Enabled Region-oriented DAG-based Distributed Ledger System for Secure V2X Communication. Ksii Trans. Internet Inf. Syst. (TIIS) 2024, 18, 2253–2280. [Google Scholar]
- Anthony Jnr, B.; Abbas Petersen, S.; Ahlers, D.; Krogstie, J. Big data driven multi-tier architecture for electric mobility as a service in smart cities: A design science approach. Int. J. Energy Sect. Manag. 2020, 14, 1023–1047. [Google Scholar] [CrossRef]
- Cao, Y.; Kaiwartya, O.; Wang, R.; Jiang, T.; Cao, Y.; Aslam, N.; Sexton, G. Toward efficient, scalable, and coordinated on-the-move EV charging management. IEEE Wirel. Commun. 2017, 24, 66–73. [Google Scholar] [CrossRef]
- Nasr, T.; Torabi, S.; Bou-Harb, E.; Fachkha, C.; Assi, C. Power jacking your station: In-depth security analysis of electric vehicle charging station management systems. Comput. Secur. 2022, 112, 102511. [Google Scholar] [CrossRef]
- Chinthamu, N.; Prasad, M.; Chinchawade, A.J.; Liyakat, K.K.S.; Deepti, K.; Karukuri, M.; Kumar, C.M. Self-Secure firmware model for Blockchain-Enabled IOT environment to Embedded system. Eur. Chem. Bull. 2023, 12, S3. [Google Scholar]
- Rashmi, R.V.; Karthikeyan, A. Secure boot of embedded applications-a review. In Proceedings of the 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018; pp. 291–298. [Google Scholar]
- Gentile, A.F.; Macrì, D.; Carnì, D.L.; Greco, E.; Lamonaca, F. A performance analysis of security protocols for distributed measurement systems based on internet of things with constrained hardware and open source infrastructures. Sensors 2024, 24, 2781. [Google Scholar] [CrossRef]
- Narayana Gowda, S. Electric Vehicle Integration for Grid Services Using AI, Optimization, and Blockchain. Ph.D. Thesis, University of California (UCLA), Los Angeles, CA, USA, 2024. [Google Scholar]
- Abdunabi, R.; Al Amin, M.; Basnet, R. An authorization framework for body area network: A policy verification and smart contract-based integrity assurance approach. J. Comput. Secur. 2025, 21, 0926227X241296435. [Google Scholar] [CrossRef]
- Dorokhova, M.; Vianin, J.; Alder, J.M.; Ballif, C.; Wyrsch, N.; Wannier, D. A blockchain-supported framework for charging management of electric vehicles. Energies 2021, 14, 7144. [Google Scholar] [CrossRef]
- Martín-Fernández, F.; Caballero-Gil, P.; Caballero-Gil, C. Authentication based on non-interactive zero-knowledge proofs for the internet of things. Sensors 2016, 16, 75. [Google Scholar] [CrossRef] [PubMed]
- Guinard, D.D.; Trifa, V.M. Building the Web of Things: With Examples in Node. js and Raspberry pi; Simon and Schuster: New York, NY, USA, 2016. [Google Scholar]
- Sciullo, L.; Gigli, L.; Montori, F.; Trotta, A.; Di Felice, M. A survey on the web of things. IEEE Access 2022, 10, 47570–47596. [Google Scholar] [CrossRef]
- Du, M.; Wang, K.; Liu, Y.; Qian, K.; Sun, Y.; Xu, W.; Guo, S. Spacechain: A three-dimensional blockchain architecture for IoT security. IEEE Wirel. Commun. 2020, 27, 38–45. [Google Scholar] [CrossRef]
- Campbell Sr, R. Evaluation of post-quantum distributed ledger cryptography. J. Br. Blockchain Assoc. 2019, 2, 21. [Google Scholar] [CrossRef]
- Jabbar, S.; Khan, M.; Silva, B.N.; Han, K. A REST-based industrial web of things’ framework for smart warehousing. J. Supercomput. 2018, 74, 4419–4433. [Google Scholar] [CrossRef]
- De Rubertis, A.; Mainetti, L.; Mighali, V.; Patrono, L.; Sergi, I.; Stefanizzi, M.L.; Pascali, S. Performance evaluation of end-to-end security protocols in an internet of things. In Proceedings of the 2013 21st International Conference on Software, Telecommunications and Computer Networks-(SoftCOM 2013) 2013, Split, Croatia, 18–20 September 2013; pp. 1–6. [Google Scholar]
- Al-Saif, N.; Ahmad, R.W.; Salah, K.; Yaqoob, I.; Jayaraman, R.; Omar, M. Blockchain for electric vehicles energy trading: Requirements, opportunities, and challenges. IEEE Access 2021, 9, 156947–156961. [Google Scholar] [CrossRef]
- Meshcheryakov, Y.; Melman, A.; Evsutin, O.; Morozov, V.; Koucheryavy, Y. On performance of PBFT blockchain consensus algorithm for IoT-applications with constrained devices. IEEE Access 2021, 9, 80559–80570. [Google Scholar] [CrossRef]
- Anderson, R. Security Engineering: A Guide to Building Dependable Distributed Systems, 3rd ed.; Wiley: Hoboken, NJ, USA, 2020. [Google Scholar]
- Bansal, G.; Dua, A.; Aujla, G.S.; Singh, M.; Kumar, N. SmartChain: A smart and scalable blockchain consortium for smart grid systems. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Chen, Y.; Li, M.; Zhu, X.; Fang, K.; Ren, Q.; Guo, T.; Deng, Y. An improved algorithm for practical byzantine fault tolerance to large-scale consortium chain. Inf. Processing Manag. 2022, 59, 102884. [Google Scholar] [CrossRef]
- Luo, H.; Yang, X.; Yu, H.; Sun, G.; Lei, B.; Guizani, M. Performance analysis and comparison of nonideal wireless PBFT and RAFT consensus networks in 6G communications. IEEE Internet Things J. 2023, 11, 9752–9765. [Google Scholar] [CrossRef]
- Garofalaki, Z.; Kosmanos, D.; Moschoyiannis, S.; Kallergis, D.; Douligeris, C. Electric vehicle charging: A survey on the security issues and challenges of the open charge point protocol (OCPP). IEEE Commun. Surv. Tutor. 2022, 24, 1504–1533. [Google Scholar] [CrossRef]
- Baza, M.; Nabil, M.; Lasla, N.; Fidan, K.; Mahmoud, M.; Abdallah, M. Blockchain-based firmware update scheme tailored for autonomous vehicles. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–7. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).