Threat Landscape and Integrated Cybersecurity Framework for V2V and Autonomous Electric Vehicles
Abstract
1. Introduction
2. Background Study
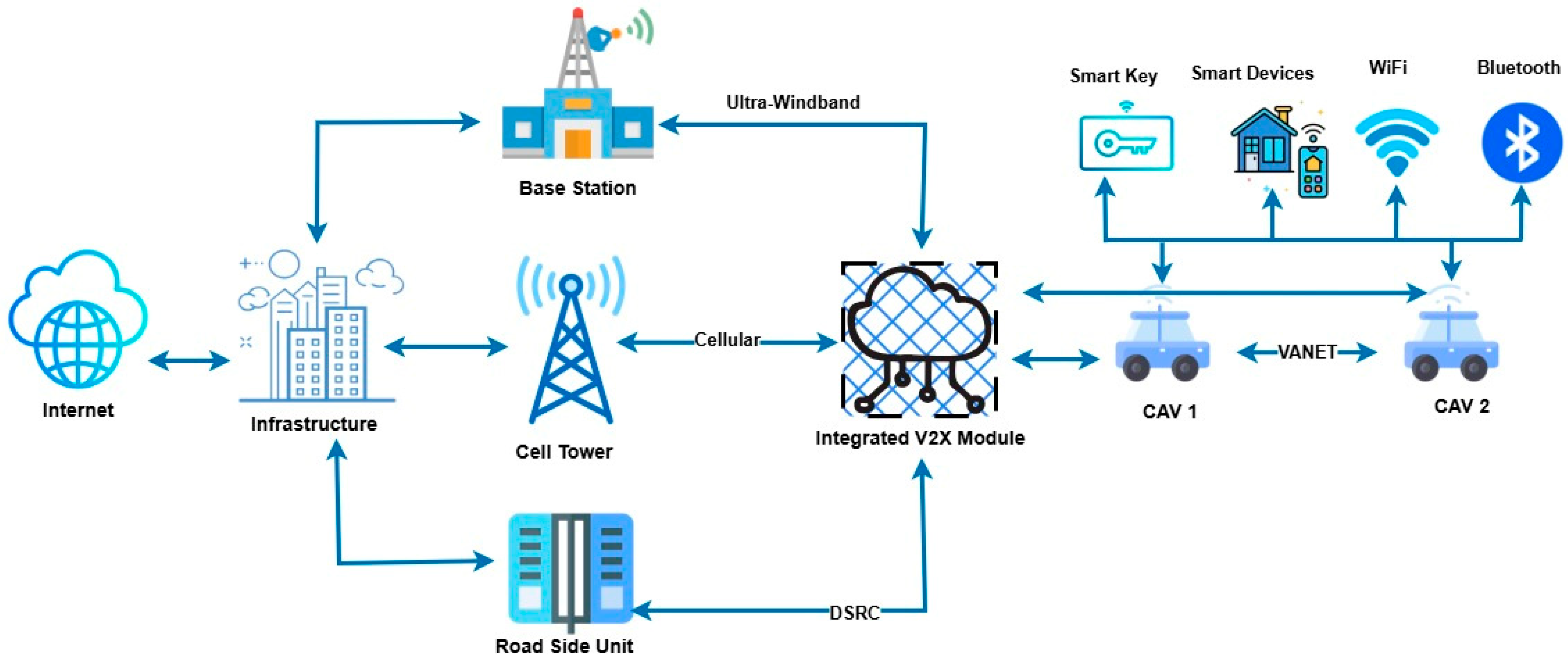
2.1. Technological Foundations of CAVs
2.2. Overview of the Cybersecurity Attacks CAVS
2.3. Electronic Control Unit Manipulation
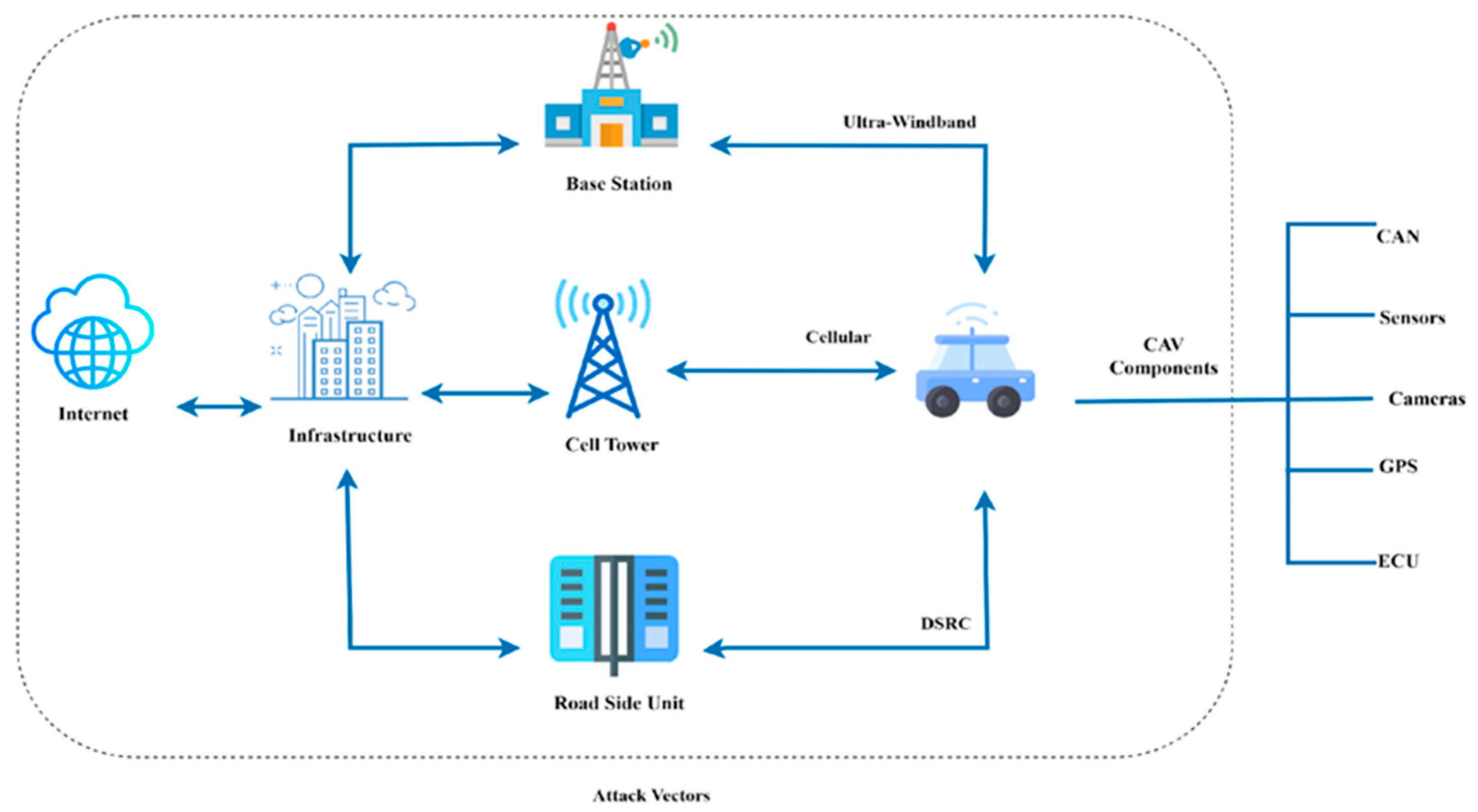
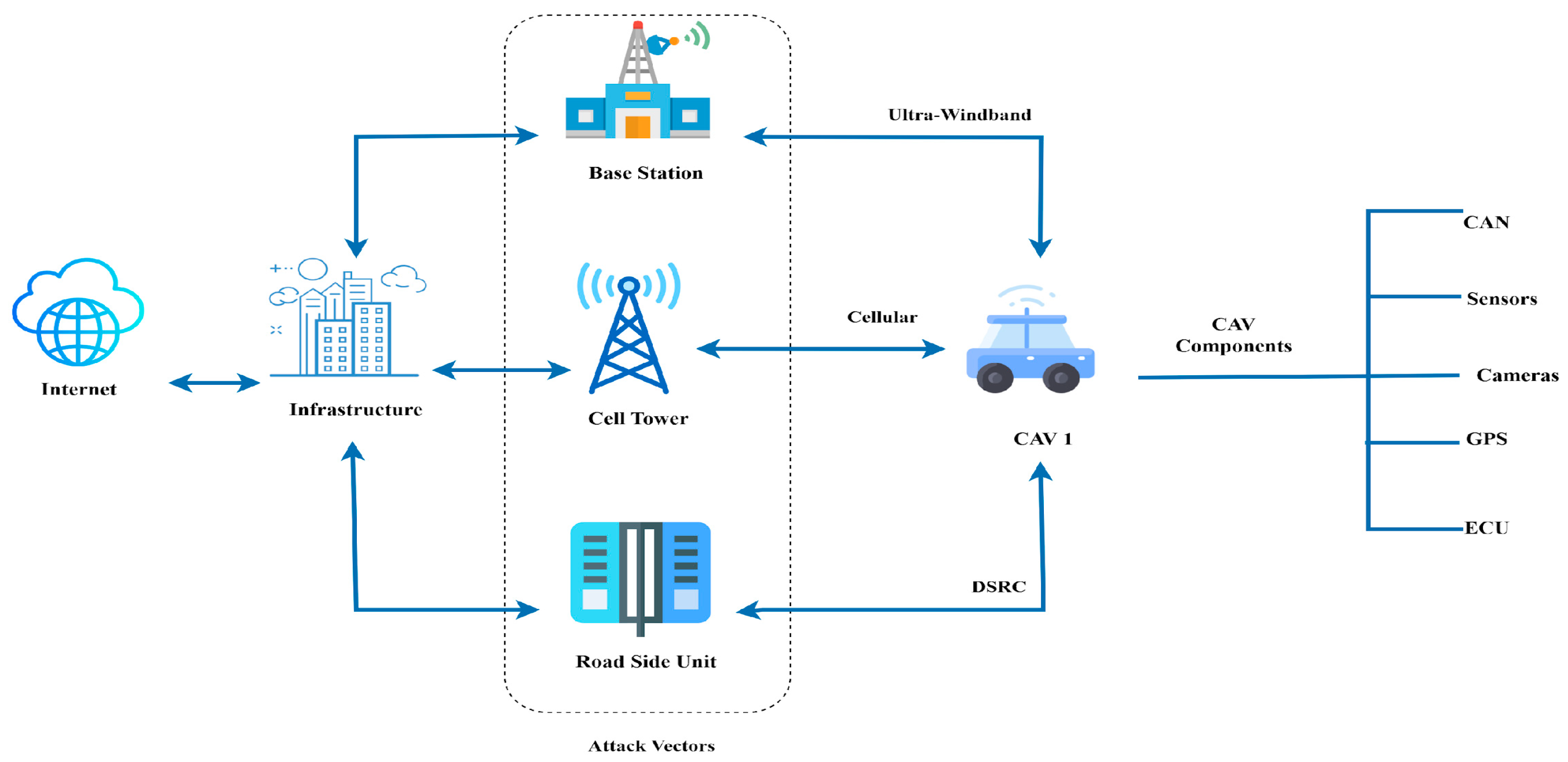
2.4. Cybersecurity Attacks on the Infrastructure of Connected and Autonomous Vehicles
2.5. Cybersecurity Threats to CAV Communication Protocols
3. Materials and Methods
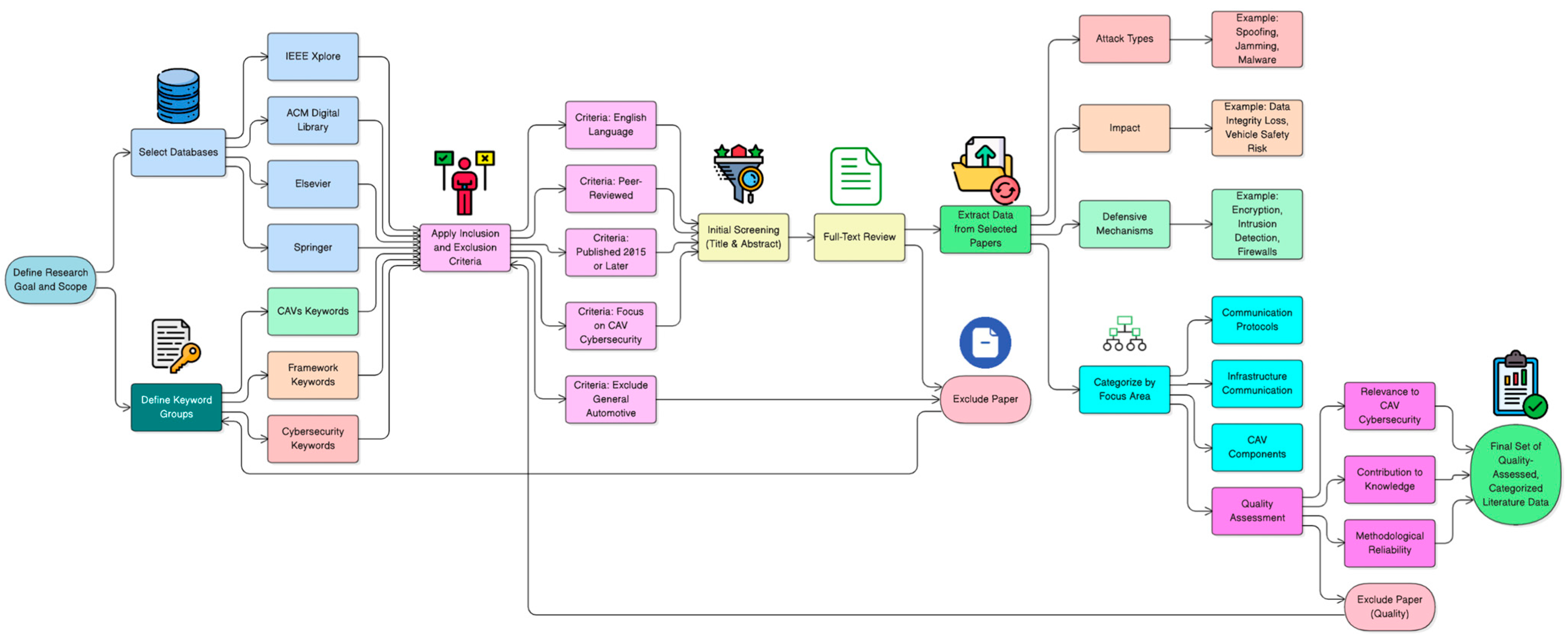
3.1. Literature Review Strategy
3.2. Data Extraction from Selected Papers
- Attack Types: Particular cybersecurity risks have been identified for CAV infrastructure, communication protocols, and components.
- Impact: The seriousness of each attack and its possible effects on data integrity and vehicle safety.
- Defensive Mechanisms: Current or suggested strategies to neutralize recognized threats.
3.3. Quality Assessment
- Relevance: Checks how much the paper discusses in the review conducted is based on cybersecurity in relation to CAVs.
- Contribution to Knowledge: Whether the study offers theoretical frameworks, empirical data, or fresh viewpoints on cybersecurity threats.
- Methodological Reliability: Evaluation of the employed methodology, such as attack simulations, vulnerability assessments, or empirical analysis.
4. Framework of Security Protocols and Standards in V2V Communication
4.1. Threat Assessment
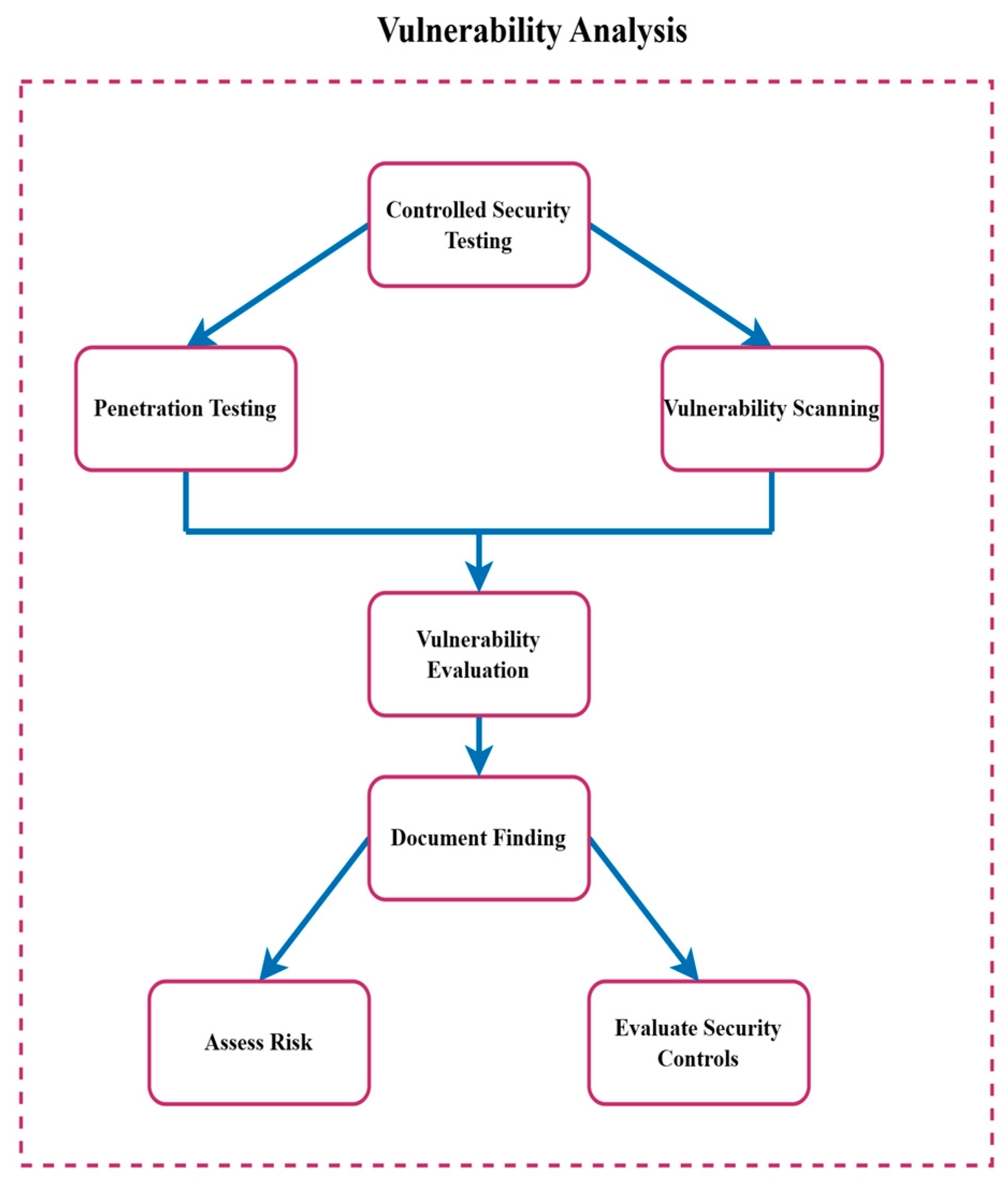
4.2. Attacks Analysis Framework
- Option 1: Perform dispersion testing to identify any known vulnerabilities. Dispersion testers also attempt to exploit the system to uncover unknown attacks and gaps, including issues in authentication mechanisms, encryption protocols, and message integrity verification [38].
- Option 2: Regular vulnerability scanning must be conducted using dedicated tools, which scan the entire system plus assets to detect any known vulnerabilities. Vulnerability analysis performed includes:
- i.
- Controlled security testing and vulnerability scanning are the two primary methods used in controlled security testing, which is the first step in the process [40]. To reduce the threats to real systems, this stage makes sure that the testing is carried out in a secure and regulated setting.
- ii.
- Figure 8 shows dispersion testing, which involves simulating cyber-attacks on the system to identify potential threats.
- iii.
- Vulnerability scanning automated technology is used in bikes with penetration testing to find any known threats in systems.
- iv.
- Vulnerability evaluation involves validating and ranking the results to determine which vulnerabilities are the most dangerous.
- v.
- Document findings; every vulnerability that has been found is included, along with information on its seriousness and its effects.
- vi.
- Risk assessment based on collected findings to determine the risk level of each vulnerability. Prioritizing which issues require instant attention and which can wait is made easier by this assessment.
- vii.
- Security controls evaluation of current security measures in addressing the vulnerabilities found is assessed.
- viii.
- Continuous improvement analysis used the recorded findings and evaluation outcomes. This helps maintain strong security over time, which entails upgrading testing procedures, enhancing tools, and consistently checking for new threats.
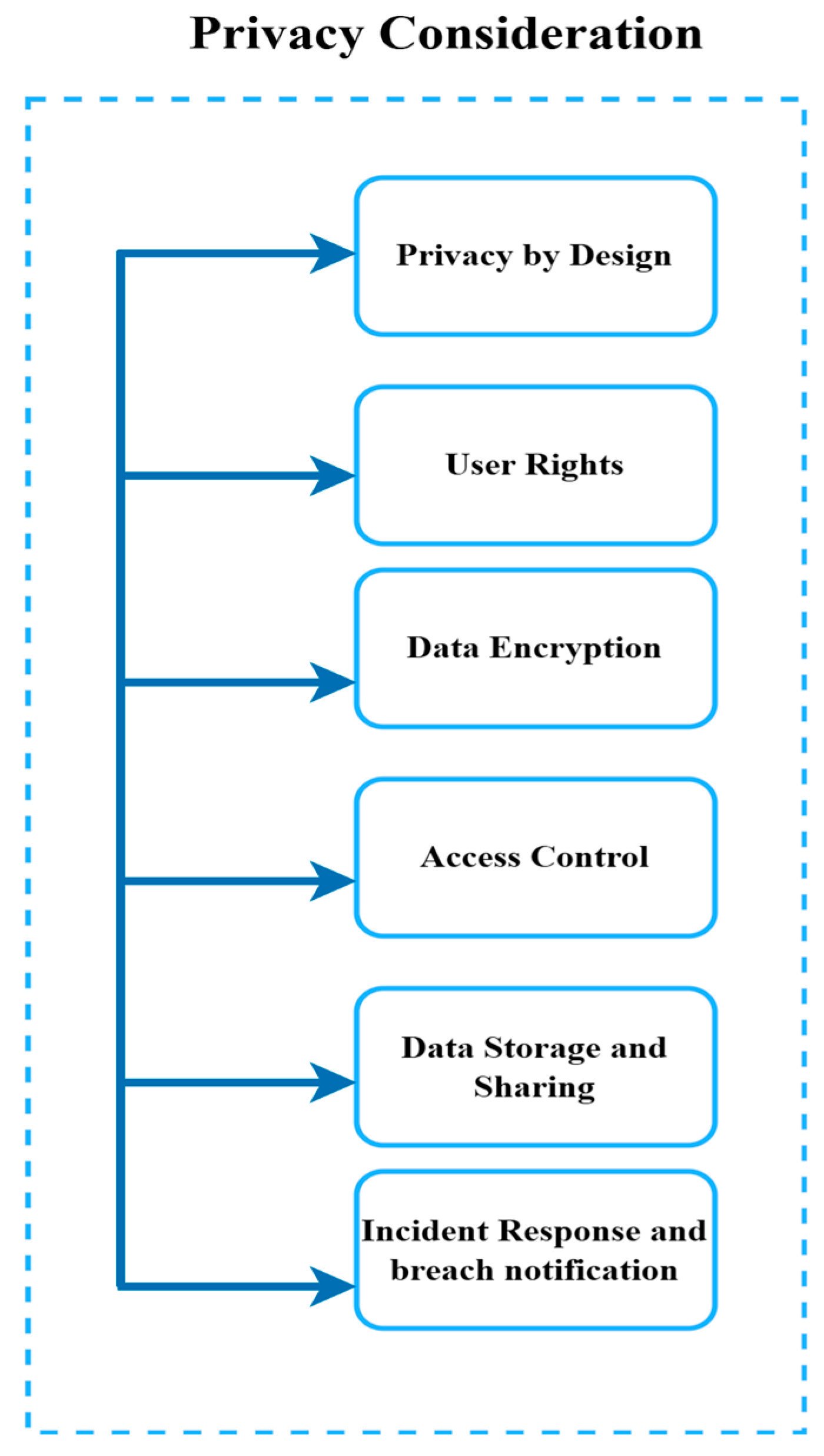
4.3. Privacy Considerations
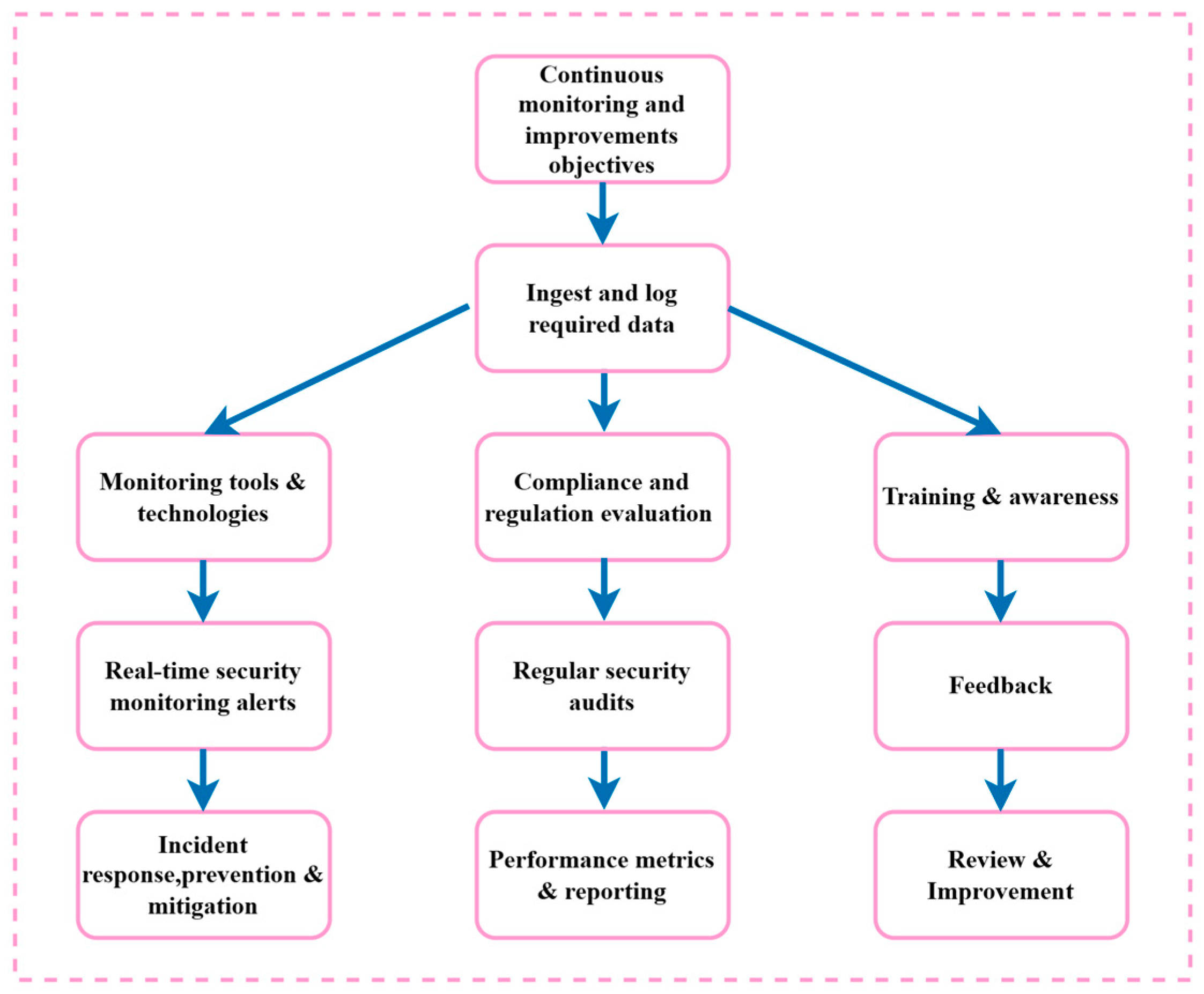
5. Continuous Monitoring, Compliance and Regulations
- i.
- EDR tool installed on endpoints to rapidly detect and respond to cyber-attacks, thereby ensuring no endpoint becomes compromised [47].
- ii.
- Compliance and regulations are evaluated regularly to ensure that the defined standards and techniques are followed exactly as they are defined.
- iii.
- Ensure regulatory compliance verifies that V2V technology complies with applicable regulations and standards, such as ISO/SAE 21434 for automotive cybersecurity or regional regulatory requirements.
- iv.
- Adhering to industry best practices helps V2V security practices utilize industry-recognized frameworks and guidelines, such as the NIST Cybersecurity Framework or those specific to the Automotive Industry.
- v.
- Participate in information sharing and engage with industry consortia, government agencies, and cybersecurity communities to share threat intelligence and best practices for enhancing the security of V2V technology.
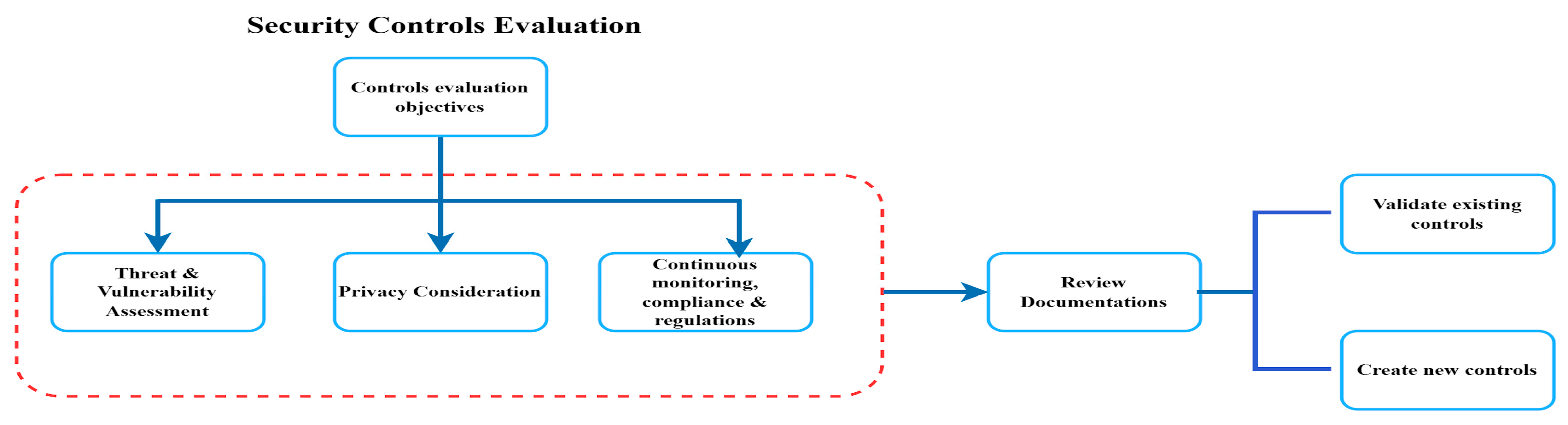
Security Controls Evaluation
- i.
- New security controls are created based on the requirements, or existing ones are evaluated.
- ii.
- Threat assessments are performed, evaluated, and documented according to the objectives.
- iii.
- Privacy considerations are assessed and documented according to the objectives;
- iv.
- Continuous monitoring, compliance, and regulations are performed, evaluated, and documented according to the objectives.
- v.
- A detailed evaluation and documentation review is conducted.
- vi.
- Based on the findings, new control protocols are created.
6. Comparative Analysis and Discussion
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Chattopadhyay, A.; Lam, K.-Y.; Tavva, Y. Autonomous Vehicle: Security by Design. IEEE Trans. Intell. Transp. Syst. 2021, 22, 7015–7029. [Google Scholar] [CrossRef]
- Sun, X.; Yu, F.R.; Zhang, P. A Survey on Cyber-Security of Connected and Autonomous Vehicles (CAVs). IEEE Trans. Intell. Transp. Syst. 2022, 23, 6240–6259. [Google Scholar] [CrossRef]
- Parkinson, S.; Ward, P.; Wilson, K.; Miller, J. Cyber Threats Facing Autonomous and Connected Vehicles: Future Challenges. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2898–2915. [Google Scholar] [CrossRef]
- Chowdhury, I.; Hasan, R. Security Analysis of Connected Autonomous Vehicles (CAVs): Challenges, Issues, Defenses, and Open Problems. In Proceedings of the IEEE World Forum Public Safety Technology (WFPST), Herndon, VA, USA, 14–15 May 2024. [Google Scholar] [CrossRef]
- Shahid, M.A.; Jaekel, A.; Ezeife, C.; Al-Ajmi, Q.; Saini, I. Review of Potential Security Attacks in VANET. In Proceedings of the 2018 Majan International Conference (MIC), Muscat, Oman, 9–20 March 2018. [Google Scholar] [CrossRef]
- Mun, H.; Seo, M.; Lee, D.H. Secure Privacy-Preserving V2V Communication in 5G-V2X Supporting Network Slicing. IEEE Trans. Intell. Transp. Syst. 2022, 23, 14439–14455. [Google Scholar] [CrossRef]
- Kim, M.; Oh, I.; Yim, K.; Sahlabadi, M.; Shukur, Z. Security of 6G Enabled Vehicle-to-Everything Communication in Emerging Federated Learning and Blockchain Technologies. IEEE Access 2023, 12, 33972–34001. [Google Scholar] [CrossRef]
- Hankins, A.; Das, T.; Sengupta, S.; Feil-Seifer, D. Eyes on the Road: A Survey on Cyber Attacks and Defense Solutions for Vehicular Ad-Hoc Networks. In Proceedings of the IEEE 13th Annual Computing and Communication Workshop Conference (CCWC), Las Vegas, NV, USA, 8–11 March 2023. [Google Scholar] [CrossRef]
- Sui, A.; Muehl, G. Security for Autonomous Vehicle Networks. In Proceedings of the 2020 IEEE 3rd International Conference on Electronic Information and Communication Technology (ICEICT), Shenzhen, China, 13–15 November 2020. [Google Scholar] [CrossRef]
- Khan, S.K.; Shiwakoti, N.; Stasinopoulos, P.; Chen, Y. Cyber-Attacks in the Next-Generation Cars, Mitigation Techniques, Anticipated Readiness and Future Directions. Accid. Anal. Prev. 2020, 148, 105837. [Google Scholar] [CrossRef]
- Girdhar, M.; Hong, J.; Moore, J. Cybersecurity of Autonomous Vehicles: A Systematic Literature Review of Adversarial Attacks and Defense Models. IEEE Open J. Veh. Technol. 2023, 4, 417–437. [Google Scholar] [CrossRef]
- Rathore, R.S.; Hewage, C.; Kaiwartya, O.; Lloret, J. In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors 2022, 22, 6679. [Google Scholar] [CrossRef] [PubMed]
- Li, Z.; Pei, Q.; Markwood, I.; Liu, Y.; Pan, M.; Li, H. Location Privacy Violation via GPS-Agnostic Smart Phone Car Tracking. IEEE Trans. Veh. Technol. 2018, 67, 5042–5053. [Google Scholar] [CrossRef]
- Larson, U.E.; Nilsson, D.K.; Jonsson, E. An approach to specification-based attack detection for in-vehicle networks. In Proceedings of the 2008 IEEE Intelligent Vehicles Symposium, Eindhoven, The Netherlands, 4–6 June 2008. [Google Scholar] [CrossRef]
- Yan, C.; Xu, W.; Liu, J. Can You Trust Autonomous Vehicles: Contactless Attacks Against Sensors of Self-Driving Vehicle. Def Con 2016, 24, 109. [Google Scholar]
- Xu, W.; Yan, C.; Jia, W.; Ji, X.; Liu, J. Analyzing and Enhancing the Security of Ultrasonic Sensors for Autonomous Vehicles. IEEE Internet Things J. 2018, 5, 5015–5029. [Google Scholar] [CrossRef]
- Stotelaar, B.G. Practical Cyber-Attacks on Autonomous Vehicles. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2015. [Google Scholar]
- Petit, J.; Bas, S.; Feiri, M.; Kargl, F. Remote Attacks on Automated Vehicles Sensors: Experiments on Camera and Lidar. Black Hat Eur. 2015, 11, 995. [Google Scholar]
- Arachchige, K.G.; Murtaza, M.; Cheng, C.-T.; Albahlal, B.M.; Lee, C.-C. Blockchain-Enabled Mitigation Strategies for Distributed Denial of Service Attacks in IoT Sensor Networks: An Experimental Approach. Comput. Mater. Contin. 2024, 81, 3679–3705. [Google Scholar] [CrossRef]
- Shao, X.; Dong, C.; Dong, L. Research on Detection and Evaluation Technology of Cybersecurity in Intelligent and Connected Vehicle. In Proceedings of the 2019 International Conference on Artificial Intelligence and Advanced Manufacturing (AIAM), Dublin, Ireland, 16–18 October 2019; pp. 413–416. [Google Scholar]
- Mudhivarthi, B.R.; Thakur, P.; Singh, G. Aspects of Cyber Security in Autonomous and Connected Vehicles. Appl. Sci. 2023, 13, 3014. [Google Scholar] [CrossRef]
- Purohit, K.C.; Dimri, S.C.; Jasola, S. Mitigation and Performance Analysis of Routing Protocols Under Black-Hole Attack in Vehicular Ad-hoc Network (VANET). Wireless Pers. Commun. 2017, 97, 5099–5114. [Google Scholar] [CrossRef]
- Shin, H.; Kim, D.; Kwon, Y.; Kim, Y. Illusion and Dazzle: Adversarial Optical Channel Exploits Against Lidars for Automotive Applications. In Cryptographic Hardware and Embedded Systems—CHES; Springer: New York, NY, USA, 2017; pp. 445–467. [Google Scholar]
- Ahangar, M.N.; Ahmed, Q.Z.; Khan, F.A.; Hafeez, M. A Survey of Autonomous Vehicles: Enabling Communication Technologies and Challenges. Sensors 2021, 21, 706. [Google Scholar] [CrossRef]
- Parekh, D.; Poddar, N.; Rajpurkar, A.; Chahal, M.; Kumar, N.; Joshi, G.P.; Cho, W. A Review on Autonomous Vehicles: Progress, Methods and Challenges. Electronics 2022, 11, 2162. [Google Scholar] [CrossRef]
- Ma, Y.; Wang, Z.; Yang, H.; Yang, L. Artificial Intelligence Applications in the Development of Autonomous Vehicles: A Survey. IEEE/CAA J. Autom. Sin. 2020, 7, 315–329. [Google Scholar] [CrossRef]
- Schwarting, W.; Alonso-Mora, J.; Rus, D. Planning and Decision-Making for Autonomous Vehicles. Annu. Rev. Control Robot. Auton. Syst. 2018, 1, 187–210. [Google Scholar] [CrossRef]
- Joo, J.; Park, M.C.; Han, D.S.; Pejovic, V. Deep Learning-Based Channel Prediction in Realistic Vehicular Communications. IEEE Access 2019, 7, 27846–27858. [Google Scholar] [CrossRef]
- Zahedi, F.; Farzaneh, N. An Evolutionary Game Theory–Based Security Model in Vehicular Ad Hoc Networks. Int. J. Commun. Syst. 2020, 33, e4290. [Google Scholar] [CrossRef]
- Tesei, A.; Luise, M.; Pagano, P.; Ferreira, J. Secure Multi-Access Edge Computing Assisted Maneuver Control for Autonomous Vehicles. In Proceedings of the 2021 IEEE 93rd Vehicular Technology Conference (VTC2021-Spring), Helsinki, Finland, 25–28 April 2021; pp. 1–6. [Google Scholar]
- Huang, J.L.; Yeh, L.Y.; Chien, H.Y. ABAKA: An Anonymous Batch Authenticated and Key Agreement Scheme for Value-Added Services in Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2011, 60, 248–262. [Google Scholar] [CrossRef]
- Palanca, A.; Evenchick, E.; Maggi, F.; Zanero, S. A Stealth, Selective, Link-Layer Denial-of-Service Attack Against Automotive Networks; Springer International Publishing: Cham, Switzerland, 2017; pp. 185–206. [Google Scholar] [CrossRef]
- Murvay, P.-S.; Groza, B. Security Shortcomings and Countermeasures for the SAE J1939 Commercial Vehicle Bus Protocol. IEEE Trans. Veh. Technol. 2018, 67, 4325–4339. [Google Scholar] [CrossRef]
- Huang, J.; Fang, D.; Qian, Y.; Hu, R.Q. Recent advances and challenges in security and privacy for V2X communications. IEEE Open J. Veh. Technol. 2020, 1, 244–266. [Google Scholar] [CrossRef]
- Dash, S.; Azad, C. Cyber Security and Threat Analysis in Autonomous Vehicles. In Autonomous Vehicles; Wiley: Hoboken, NJ, USA, 2022; Volume 1, pp. 161–180. [Google Scholar] [CrossRef]
- Xu, H.; Dong, M.; Ota, K.; Wu, J.; Li, J. Toward Software Defined Dynamic Defense as a Service for 5G-Enabled Vehicular Networks. In Proceedings of the 2019 International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Atlanta, GA, USA, 14–17 July 2019; pp. 880–887. [Google Scholar] [CrossRef]
- Ucar, S.; Ergen, S.C.; Ozkasap, O. IEEE 802.11p and Visible Light Hybrid Communication Based Secure Autonomous Platoon. IEEE Trans. Veh. Technol. 2018, 67, 8667–8681. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Zhang, Y. Privacy-Preserved Pseudonym Scheme for Fog Computing Supported Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2018, 19, 2627–2637. [Google Scholar] [CrossRef]
- Chen, C.-M.; Xiang, B.; Liu, Y.; Wang, K.-H. A Secure Authentication Protocol for Internet of Vehicles. IEEE Access 2019, 7, 12047–12057. [Google Scholar] [CrossRef]
- Lee, S.; Park, Y.; Lim, H.; Shon, T. Study on Analysis of Security Vulnerabilities and Countermeasures in ISO/IEC 15118 Based Electric Vehicle Charging Technology. International Conference on IT Convergence and Security, ICITCS, Beijing, China, 28–30 October 2014. [Google Scholar] [CrossRef]
- Dosovitskiy, A.; Ros, G.; Codevilla, F.; Lopez, A.; Koltun, V. CARLA: An Open Urban Driving Simulator. arXiv 2017. [Google Scholar] [CrossRef]
- Habib, M.A.; Ahmad, M.; Jabbar, S.; Khalid, S.; Chaudhry, J.; Saleem, K.; Rodrigues, J.J.P.C.; Khalil, M.S. ; Ahmad, M.; Jabbar, S.; Khalid, S.; Chaudhry, J.; Saleem, K.; Rodrigues, J.J.P.C.; Khalil, M.S. Security and Privacy-Based Access Control Model for Internet of Connected Vehicles. Future Gener. Comput. Syst. 2019, 97, 687–696. [Google Scholar] [CrossRef]
- Barletta, V.S.; Caivano, D.; Vincentiis, M.D.; Ragone, A.; Scalera, M.; Martín, M.Á.S. V-SOC4AS: A Vehicle-SOC for Improving Automotive Security. Algorithms 2023, 16, 112. [Google Scholar] [CrossRef]
- González-Granadillo, G.; González-Zarzosa, S.; Diaz, R. Security Information and Event Management (SIEM): Analysis, Trends, and Usage in Critical Infrastructures. Sensors 2021, 21, 4759. [Google Scholar] [CrossRef]
- Deshpande, D.S.; Tathe, A.A.; Lahe, A.; Rathi, B.; Parkhade, G. Endpoint Detection and Response System: Emerging Cyber Security Technology. In Proceedings of the International Conference on Intelligent Systems and Networks: ICISN, Hanoi, Vietnam, 21–22 March 2024; Springer Nature: Gateway East, Singapore, 2024; pp. 202–213. [Google Scholar]
- Implementing SIEM and SOAR Platforms: Practitioner Guidance. Australian Cyber Security Centre. 2025. Available online: https://www.cyber.gov.au/sites/default/files/2025-05/implementing_siem_and_soar_platforms_-_practitioner_guidance.pdf (accessed on 15 May 2025).
- Lord, N. What is Endpoint Detection and Response? A Definition of Endpoint Detection & Response. Data Insider Report. 2019. Available online: https://digitalguardian.com/blog/what-endpoint-detection-and-response-definition-endpoint-detection-response (accessed on 25 May 2024).
- Yang, T.; Sun, R.; Rathore, R.S.; Baig, I. Enhancing Cybersecurity and Privacy Protection for Cloud Computing-Assisted Vehicular Network of Autonomous Electric Vehicles: Applications of Machine Learning. World Electr. Veh. J. 2025, 16, 14. [Google Scholar] [CrossRef]
- Cappello, M.; Καππέλλο, Μ. A Comprehensive Analysis of EDR (Endpoint Detection & Response), EPP (Endpoint Protection Platform), and Antivirus Security Technologies. Master’s Thesis, University of Piraeus, Pireas, Greece, 2024. Available online: https://dione.lib.unipi.gr/xmlui/handle/unipi/16751 (accessed on 20 February 2025).
- Almehrezi, F.R.; Yeun, C.Y.; Yoo, P.D.; Damiani, E.; Al Hammadi, Y.; Yeun, H. An Emerging Security Framework for Connected Autonomous Vehicles. In Proceedings of the 2020 7th International Conference on Behavioural and Social Computing (BESC), Bournemouth, UK, 5–7 November 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Australian Government Department of Home Affairs. Policy 3: Security Planning and Risk Management. Available online: https://www.protectivesecurity.gov.au/pspf-annual-release (accessed on 29 October 2024).
- Chika, P.E.; Ibrahim, H.A.; Dwivedi, A. Lightweight Cryptography for Internet of Things: A Review. EAI Endorsed Trans. Internet Things 2024, 10, 1. [Google Scholar] [CrossRef]
- Vrščaj, D.; Nyholm, S.; Verbong, G.P.J. Is tomorrow’s car appealing today? Ethical issues and user attitudes beyond automation. AI Soc. 2020, 35, 1033–1046. [Google Scholar] [CrossRef]
- Murtaza, M.; Cheng, C.-T.; Fard, M.; Zeleznikow, J. The importance of transparency in naming conventions, designs, and operations of safety features: From modern ADAS to fully autonomous driving functions. AI Soc. 2022, 38, 983–993. [Google Scholar] [CrossRef]
- Murtaza, M.; Cheng, C.-T.; Fard, M.; Zeleznikow, J. Preparing Drivers for the Future: Evaluating the Effects of Training on Drivers’ Performance in an Autonomous Vehicle Landscape. Transp. Res. Part F Traffic Psychol. Behav. 2023, 98, 280–296. [Google Scholar] [CrossRef]
- Murtaza, M.; Cheng, C.-T.; Fard, M.; Zeleznikow, J. Assessing Training Methods for Advanced Driver Assistance Systems and Autonomous Vehicle Functions: Impact on User Mental Models and Performance. Appl. Sci. 2024, 14, 2348. [Google Scholar] [CrossRef]
- Murtaza, M.; Cheng, C.-T.; Fard, M.; Zeleznikow, J. Transforming Driver Education: A Comparative Analysis of LLM-Augmented Training and Conventional Instruction for Autonomous Vehicle Technologies. Int. J. Artif. Intell. Educ. 2024, 35, 736–773. [Google Scholar] [CrossRef]
- Murtaza, M.; Cheng, C.T.; Albahlal, B.M.; Muslam, M.M.A.; Raza, M.S. The impact of LLM chatbots on learning outcomes in advanced driver assistance systems education. Sci. Rep. 2025, 15, 7260. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, Y.; Gong, X. Enhancing Vehicular Communication Security: A Two-Factor Authentication Protocol for V2V Communications in IoV. J. Inf. Secur. Appl. 2025, 92, 104114. [Google Scholar] [CrossRef]
- Bashir, E.; Hernando-Gallego, F.; Martín, D.; Shoushtari, F. Secure Cooperative Dual-RIS-Aided V2V Communication: An Evolutionary Transformer–GRU Framework for Secrecy Rate Maximization in Vehicular Networks. World Electr. Veh. J. 2025, 16, 396. [Google Scholar] [CrossRef]
- Ahmed, S.F.; Alam, M.S.B.; Hoque, M.; Lameesa, A.; Afrin, S.; Farah, T.; Muyeen, S.M. Industrial Internet of Things enabled technologies, challenges, and future directions. Comput. Electr. Eng. 2023, 110, 108847. [Google Scholar] [CrossRef]
- Berti, N.; Katiraee, N.; Zuin, S.; Aldrighetti, R.; Persona, A.; Battini, D. The Challenges of Driverless Mobile Vehicles in Shared Workspace in the Industry 5.0 Era. IEEE Access 2025, 13, 27228–27237. [Google Scholar] [CrossRef]
- Awouda, A.; Traini, E.; Bruno, G.; Chiabert, P. IoT-Based Framework for Digital Twins in the Industry 5.0 Era. Sensors 2024, 24, 594. [Google Scholar] [CrossRef] [PubMed]



| Attack Type | Description | Impact | Countermeasures |
|---|---|---|---|
| Spoofing [15] | The attacker copies a real device to gain unauthorized access or disrupt communication | Lead to identity theft, unauthorized access, and system compromise | Authentication, encryption, and monitoring of anomalous behavior |
| Meaconing [15] | Retransmitting legitimate signals to mislead the target system into inappropriate actions | Systems will process false data, leading to incorrect decisions | Secure communication protocols |
| Jamming [16] | Troublesome communication by flooding the communication channel with noise | Disables the quality of communication, leading to a loss of service | Use of frequency hopping, signal modulation |
| Replay [17] | Capturing valid communication to trick the system into suffering the repeated data | Compromise authentication or authorization mechanisms | Timestamping, usage nonce values, and sequence numbers to detect repeated data |
| Denial-of-Service [18,19] | Overloading a system’s resources or network to prevent legitimate users from accessing the system or services | Causes downtime, performance degradation, or total unavailability of services | Rate limiting, network firewalls, traffic analysis, and redundancy to distribute the load |
| Disruptive [20] | Attacks that cause disturbances in the operation of a system | System reliability, availability, and performance affected | Monitoring for abnormal behaviors and recovery measures |
| Relay [21] | Interrupting messages between two deceive | Breach of confidential data | Encryption and secure key exchange protocols can be used |
| Time Synchronization [22] | Interrupts the synchronization of time-sensitive operations in V2V communication | Falsify vehicles communication | Strong anomaly detection systems |
| Routing [22] | Serious risks to the communication infrastructure | Flaws in routing protocols | Monitoring for abnormal behaviors and recovery measures |
| Blinding [23] | Systems or sensors manipulated by attackers | Disables system performance, often rendering it blind | Robust sensor design and anomaly detection in systems |
| Ref. | Survey | Area Covered |
|---|---|---|
| [24] | Autonomous vehicles challenges | AV data gathering using sensors |
| [25] | Autonomous vehicle’s progress, and challenges | Focuses on the current state of research |
| [26] | Artificial intelligence applications in the development of autonomous vehicles: A survey | AI in supporting primary applications in AVs in decision-making |
| [27] | Decision-making for autonomous vehicles | Trends and challenges in autonomous vehicles |
| [28] | Vehicular communication systems | Intensive road safety and traffic efficiency |
| [29] | Proposed security models | Enhanced study on common attacks and attack defenses |
| [30] | Smart car sensors and applications | Consider an intelligent autonomous vehicle control system |
| [31] | Anonymous batch authenticated and key agreement (ABAKA) scheme | Personalized for autonomous vehicles to authenticate multiple requests |
| Group | Keywords |
|---|---|
| CAVs | “Autonomous Vehicle(s)”, “CAV(s)”, “V2V technology”, “connected and autonomous vehicle(s)”, “smart car(s)”, “vehicle-to-vehicle technology” |
| Framework | “CAV security framework(s)”, “autonomous vehicle security framework(s)”, “V2V cybersecurity framework(s)”, “cybersecurity framework(s)”, “cybersecurity frameworks for autonomous vehicle(s)”, “framework” |
| Cybersecurity | “cyber-attack(s)”, “cyber security”, “hacker(s)”, “attack(s)”, “cyber safety” |
| Abbreviations | Explanation |
|---|---|
| CAVs | Connected Autonomous Vehicles |
| AI | Artificial Intelligence |
| CRF | Cyber Security Regulatory Framework |
| DSRC | Dedicated short-range Communication |
| ITS | Intelligence Transport System |
| V2X | Vehicle-to-Everything |
| ECU | Electronic Control Unit |
| UWB | Ultra-Wideband |
| Ref. | Problem Focused | Key Contribution | Limitation | Proposed Framework |
|---|---|---|---|---|
| [50] | CAV security | Proposed an emerging framework for CAVs | Limited integration across V2V, V2X, and EVs | Offers holistic protection across all subsystems |
| [51,52] | Lightweight cryptography | Surveyed cryptographic techniques for IoT | Lacks specific adaptation to V2V/EVs | Adapts lightweight crypto for EV-specific needs |
| [51,53,54] | Technology standardization, Ethics and user trust | Explores ethical concerns in automation and outlines policy frameworks | Not focused on technical cybersecurity | Integrates security with regulatory/ethical alignment |
| [55,56,57,58] | Human training and performance | Enhances AV user understanding via training | Focus on human factors, not system-level threats | Complements technical cybersecurity with user education |
| [59,60] | V2V authentication | Proposed a dual-factor AKE protocol using biometrics and PUF | Focused on V2V only; lacks broader system integration | Integrates strong AKE within a monitored multi-layered architecture |
| [61,62] | Industrial IoT in Industry 5.0 | Describes IIoT and scalability challenges | No direct application to transportation systems | Bridges Industry 5.0 principles with vehicular networks |
| [63] | IoT-Digital Twins (Industry 5.0) | Outlines IoT-based frameworks for digital twins | Focus on manufacturing, not CAVs | Applies principles to EV infrastructure and firmware updates |
| Proposed Study | V2V, V2X, EVs (integrated) | AI-driven, cryptographic, lightweight, regulatory-aligned cybersecurity framework | Not yet empirically validated; implementation remains future work | Comprehensive, scalable, and adaptive to evolving cyber threats |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the World Electric Vehicle Association. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Arachchige, K.G.; Alkaabi, G.; Murtaza, M.; Haq, Q.E.U.; Abualkishik, A.Z.; Lee, C.-C. Threat Landscape and Integrated Cybersecurity Framework for V2V and Autonomous Electric Vehicles. World Electr. Veh. J. 2025, 16, 469. https://doi.org/10.3390/wevj16080469
Arachchige KG, Alkaabi G, Murtaza M, Haq QEU, Abualkishik AZ, Lee C-C. Threat Landscape and Integrated Cybersecurity Framework for V2V and Autonomous Electric Vehicles. World Electric Vehicle Journal. 2025; 16(8):469. https://doi.org/10.3390/wevj16080469
Chicago/Turabian StyleArachchige, Kithmini Godewatte, Ghanem Alkaabi, Mohsin Murtaza, Qazi Emad Ul Haq, Abedallah Zaid Abualkishik, and Cheng-Chi Lee. 2025. "Threat Landscape and Integrated Cybersecurity Framework for V2V and Autonomous Electric Vehicles" World Electric Vehicle Journal 16, no. 8: 469. https://doi.org/10.3390/wevj16080469
APA StyleArachchige, K. G., Alkaabi, G., Murtaza, M., Haq, Q. E. U., Abualkishik, A. Z., & Lee, C.-C. (2025). Threat Landscape and Integrated Cybersecurity Framework for V2V and Autonomous Electric Vehicles. World Electric Vehicle Journal, 16(8), 469. https://doi.org/10.3390/wevj16080469







