A Review of AI-Based Cyber-Attack Detection and Mitigation in Microgrids
Abstract
:1. Introduction
- We conducted a systematic search across several scholarly databases, including Google Scholar, IEEE, MDPI, Elsevier, and Springer, using a combination of keywords and focused search terms associated with our area of study. We focused on peer-reviewed books, journals, conference proceedings, and industry white papers to cover a broad spectrum of perspectives and findings, as shown in Figure 3.
- The existing techniques are divided into two main categories, i.e., cyber attack detection and mitigation. The system under study, attack type, data acquisition, and training method of AI-based techniques are summarized in tables for each category.
- A case study is presented on the use case of AI-based technique in the microgrid.
2. Types of Cyber-Attacks in Microgrids
2.1. False Data Injection Cyber-Attack
2.2. Denial-of-Service Cyber-Attack
2.3. Man-in-the-Middle Cyber-Attack
3. AI-Based Cyber-Attack Detection
4. AI-Based Cyber-Attack Mitigation
5. Learning-Based Cyber Attack Detection and Mitigation
6. Case Study
7. Discussion
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Nassif, A.B.; Ericson, S.; Abbey, C.; Jeffers, R.; Hotchkiss, E.; Bahramirad, S. Valuing Resilience Benefits of Microgrids for an Interconnected Island Distribution System. Electronics 2022, 11, 4206. [Google Scholar] [CrossRef]
- Aghmadi, A.; Hussein, H.; Polara, K.H.; Mohammed, O. A Comprehensive Review of Architecture, Communication, and Cybersecurity in Networked Microgrid Systems. Inventions 2023, 8, 84. [Google Scholar] [CrossRef]
- de la Cruz, J.; Wu, Y.; Candelo-Becerra, J.E.; Vásquez, J.C.; Guerrero, J.M. A review of networked microgrid protection: Architectures, challenges, solutions, and future trends. CSEE J. Power Energy Syst. 2023. [Google Scholar] [CrossRef]
- Bazmohammadi, N.; Madary, A.; Vasquez, J.C.; Mohammadi, H.B.; Khan, B.; Wu, Y.; Guerrero, J.M. Microgrid digital twins: Concepts, applications, and future trends. IEEE Access 2021, 10, 2284–2302. [Google Scholar] [CrossRef]
- Espina, E.; Llanos, J.; Burgos-Mellado, C.; Cardenas-Dobson, R.; Martinez-Gomez, M.; Saez, D. Distributed control strategies for microgrids: An overview. IEEE Access 2020, 8, 193412–193448. [Google Scholar] [CrossRef]
- Nasirian, V.; Moayedi, S.; Davoudi, A.; Lewis, F.L. Distributed cooperative control of DC microgrids. IEEE Trans. Power Electron. 2014, 30, 2288–2303. [Google Scholar] [CrossRef]
- Morstyn, T.; Hredzak, B.; Agelidis, V.G. Distributed cooperative control of microgrid storage. IEEE Trans. Power Syst. 2014, 30, 2780–2789. [Google Scholar] [CrossRef]
- Mustafa, A.; Poudel, B.; Bidram, A.; Modares, H. Detection and mitigation of data manipulation attacks in AC microgrids. IEEE Trans. Smart Grid 2019, 11, 2588–2603. [Google Scholar] [CrossRef]
- Beg, O.A.; Nguyen, L.V.; Johnson, T.T.; Davoudi, A. Signal temporal logic-based attack detection in DC microgrids. IEEE Trans. Smart Grid 2018, 10, 3585–3595. [Google Scholar] [CrossRef]
- Khan, A.A.; Beg, O.A. Cyber Vulnerabilities of Modern Power Systems. In Power Systems Cybersecurity: Methods, Concepts, and Best Practices; Haes Alhelou, H., Hatziargyriou, N., Dong, Z.Y., Eds.; Springer International Publishing: Cham, Switzerland, 2023; pp. 47–66. [Google Scholar] [CrossRef]
- Bhusal, N.; Abdelmalak, M.; Kamruzzaman, M.; Benidris, M. Power system resilience: Current practices, challenges, and future directions. IEEE Access 2020, 8, 18064–18086. [Google Scholar] [CrossRef]
- Ribas Monteiro, L.F.; Rodrigues, Y.R.; Zambroni de Souza, A. Cybersecurity in Cyber–Physical Power Systems. Energies 2023, 16, 4556. [Google Scholar] [CrossRef]
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Reza Ahrabi, R. Cyber-security of smart microgrids: A survey. Energies 2020, 14, 27. [Google Scholar] [CrossRef]
- Tan, S.; Wu, Y.; Xie, P.; Guerrero, J.M.; Vasquez, J.C.; Abusorrah, A. New challenges in the design of microgrid systems: Communication networks, cyberattacks, and resilience. IEEE Electrif. Mag. 2020, 8, 98–106. [Google Scholar] [CrossRef]
- Tan, S.; Xie, P.; Guerrero, J.M.; Vasquez, J.C. False data injection cyber-attacks detection for multiple DC microgrid clusters. Appl. Energy 2022, 310, 118425. [Google Scholar] [CrossRef]
- Venkatachary, S.K.; Prasad, J.; Samikannu, R. Cybersecurity and cyber terrorism-in energy sector—A review. J. Cyber Secur. Technol. 2018, 2, 111–130. [Google Scholar] [CrossRef]
- Suprabhath Koduru, S.; Machina, V.S.P.; Madichetty, S. Cyber Attacks in Cyber-Physical Microgrid Systems: A Comprehensive Review. Energies 2023, 16, 4573. [Google Scholar] [CrossRef]
- Krause, T.; Ernst, R.; Klaer, B.; Hacker, I.; Henze, M. Cybersecurity in power grids: Challenges and opportunities. Sensors 2021, 21, 6225. [Google Scholar] [CrossRef]
- MITRE ATT&CK Matrix for Enterprise. Available online: https://attack.mitre.org/ (accessed on 10 November 2023).
- Ramotsoela, D.T.; Hancke, G.P.; Abu-Mahfouz, A.M. Practical Challenges of Attack Detection in Microgrids Using Machine Learning. J. Sens. Actuator Netw. 2023, 12, 7. [Google Scholar] [CrossRef]
- Karanfil, M.; Rebbah, D.E.; Debbabi, M.; Kassouf, M.; Ghafouri, M.; Youssef, E.N.S.; Hanna, A. Detection of Microgrid Cyberattacks Using Network and System Management. IEEE Trans. Smart Grid 2023, 14, 2390–2405. [Google Scholar] [CrossRef]
- Pinto, S.J.; Siano, P.; Parente, M. Review of Cybersecurity Analysis in Smart Distribution Systems and Future Directions for Using Unsupervised Learning Methods for Cyber Detection. Energies 2023, 16, 1651. [Google Scholar] [CrossRef]
- Ortega-Fernandez, I.; Liberati, F. A Review of Denial of Service Attack and Mitigation in the Smart Grid Using Reinforcement Learning. Energies 2023, 16, 635. [Google Scholar] [CrossRef]
- Kim, Y.; Hakak, S.; Ghorbani, A. Smart grid security: Attacks and defence techniques. IET Smart Grid 2023, 6, 103–123. [Google Scholar] [CrossRef]
- Sahoo, S.; Blaabjerg, F.; Dragicevic, T. (Eds.) Cyber Security for Microgrids; IEEE: New York, NY, USA, 2022. [Google Scholar] [CrossRef]
- Leng, M.; Sahoo, S.; Blaabjerg, F.; Molinas, M. Projections of Cyberattacks on Stability of DC Microgrids—Modeling Principles and Solution. IEEE Trans. Power Electron. 2022, 37, 11774–11786. [Google Scholar] [CrossRef]
- Jamali, M.; Sadabadi, M.S.; Davari, M.; Sahoo, S.; Blaabjerg, F. Resilient Cooperative Secondary Control of Islanded AC Microgrids Utilizing Inverter-Based Resources Against State-Dependent False Data Injection Attacks. IEEE Trans. Power Electron. 2023, 1–12. [Google Scholar] [CrossRef]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Trivedi, R.; Khadem, S. Implementation of artificial intelligence techniques in microgrid control environment: Current progress and future scopes. Energy AI 2022, 8, 100147. [Google Scholar] [CrossRef]
- Nair, D.R.; Nair, M.G.; Thakur, T. A smart microgrid system with artificial intelligence for power-sharing and power quality improvement. Energies 2022, 15, 5409. [Google Scholar] [CrossRef]
- Wu, T.; Wang, J. Artificial intelligence for operation and control: The case of microgrids. Electr. J. 2021, 34, 106890. [Google Scholar] [CrossRef]
- Lv, L.; Wu, Z.; Zhang, L.; Gupta, B.B.; Tian, Z. An Edge-AI Based Forecasting Approach for Improving Smart Microgrid Efficiency. IEEE Trans. Ind. Inform. 2022, 18, 7946–7954. [Google Scholar] [CrossRef]
- Zhao, S.; Blaabjerg, F.; Wang, H. An Overview of Artificial Intelligence Applications for Power Electronics. IEEE Trans. Power Electron. 2021, 36, 4633–4658. [Google Scholar] [CrossRef]
- Dewangan, F.; Abdelaziz, A.Y.; Biswal, M. Load Forecasting Models in Smart Grid Using Smart Meter Information: A Review. Energies 2023, 16, 1404. [Google Scholar] [CrossRef]
- Poti, K.D.; Naidoo, R.M.; Mbungu, N.T.; Bansal, R.C. Intelligent solar photovoltaic power forecasting. Energy Rep. 2023, 9, 343–352. [Google Scholar] [CrossRef]
- Yang, Y.; Guo, L.; Li, X.; Li, J.; Liu, W.; He, H. A data-driven detection strategy of false data in cooperative DC microgrids. In Proceedings of the IECON 2021—47th Annual Conference of the IEEE Industrial Electronics Society, Toronto, ON, Canada, 13–16 October 2021; pp. 1–6. [Google Scholar]
- Banda, M.K.; Koduru, S.S.; Machina, V.S.P.; Madichetty, S. A Deep Learning Based Cyber Attack Detection and Mitigation Scheme in Synchronous Buck Converter. In Proceedings of the 2022 IEEE International Conference on Power Electronics, Drives and Energy Systems (PEDES), Jaipur, India, 14–17 December 2022; pp. 1–6. [Google Scholar]
- Suprabhath, K.; Prasad, M.V.S.; Chetty, S.; Mishra, S. A deep learning based cyber attack detection scheme in DC microgrid systems. CPSS Trans. Power Electron. Appl. 2023, 8, 2. [Google Scholar] [CrossRef]
- Siniosoglou, I.; Radoglou-Grammatikis, P.; Efstathopoulos, G.; Fouliras, P.; Sarigiannidis, P. A unified deep learning anomaly detection and classification approach for smart grid environments. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1137–1151. [Google Scholar] [CrossRef]
- Panthi, M. Anomaly detection in smart grids using machine learning techniques. In Proceedings of the 2020 First International Conference on Power, Control and Computing Technologies (ICPC2T), Raipur, India, 3–5 January 2020; pp. 220–222. [Google Scholar]
- Glauner, P. Big Data-Driven Detection of False Data Injection Attacks in Smart Meters. IEEE Access 2021, 9, 144313–144326. [Google Scholar]
- Basati, A.; Guerrero, J.M.; Vasquez, J.C.; Bazmohammadi, N.; Golestan, S. A Data-Driven Framework for FDI Attack Detection and Mitigation in DC Microgrids. Energies 2022, 15, 8539. [Google Scholar] [CrossRef]
- Abazari, A.; Zadsar, M.; Ghafouri, M.; Atallah, R.; Assi, C. A data mining/anfis and adaptive control for detection and mitigation of attacks on dc mgs. IEEE Trans. Smart Grid 2022, 14, 2406–2422. [Google Scholar] [CrossRef]
- Khan, A.A.; Beg, O.A.; Jin, Y.F.; Ahmed, S. An Explainable Intelligent Framework for Anomaly Mitigation in Cyber-Physical Inverter-based Systems. IEEE Access 2023, 11, 65382–65394. [Google Scholar] [CrossRef]
- Tian, E.; Wu, Z.; Xie, X. Codesign of FDI Attacks Detection, Isolation, and Mitigation for Complex Microgrid Systems: An HBF-NN-Based Approach. IEEE Trans. Neural Netw. Learn. Syst. 2022. [Google Scholar] [CrossRef]
- Habibi, M.R.; Sahoo, S.; Rivera, S.; Dragičević, T.; Blaabjerg, F. Decentralized coordinated cyberattack detection and mitigation strategy in DC microgrids based on artificial neural networks. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 4629–4638. [Google Scholar] [CrossRef]
- Zhang, N.; Sun, Q.; Yang, L.; Li, Y. Event-Triggered Distributed Hybrid Control Scheme for the Integrated Energy System. IEEE Trans. Ind. Inform. 2022, 18, 835–846. [Google Scholar] [CrossRef]
- Yang, L.; Li, X.; Sun, M.; Sun, C. Hybrid Policy-Based Reinforcement Learning of Adaptive Energy Management for the Energy Transmission-Constrained Island Group. IEEE Trans. Ind. Inform. 2023, 19, 10751–10762. [Google Scholar] [CrossRef]
- AlSkaif, T.; Crespo-Vazquez, J.L.; Sekuloski, M.; van Leeuwen, G.; Catalão, J.P.S. Blockchain-Based Fully Peer-to-Peer Energy Trading Strategies for Residential Energy Systems. IEEE Trans. Ind. Inform. 2022, 18, 231–241. [Google Scholar] [CrossRef]
- Cui, S.; Wang, Y.W.; Shi, Y.; Xiao, J.W. A new and fair peer-to-peer energy sharing framework for energy buildings. IEEE Trans. Smart Grid 2020, 11, 3817–3826. [Google Scholar] [CrossRef]
- Lopez-Garcia, T.B.; Coronado-Mendoza, A.; Domínguez-Navarro, J.A. Artificial neural networks in microgrids: A review. Eng. Appl. Artif. Intell. 2020, 95, 103894. [Google Scholar] [CrossRef]
- Singh, N.K.; Mahajan, V. Analysis and evaluation of cyber-attack impact on critical power system infrastructure. Smart Sci. 2021, 9, 1–13. [Google Scholar] [CrossRef]
- Pour, M.M.; Anzalchi, A.; Sarwat, A. A review on cyber security issues and mitigation methods in smart grid systems. In Proceedings of the SoutheastCon 2017, Concord, NC, USA, 30 March–2 April 2017; pp. 1–4. [Google Scholar]
- Reda, H.T.; Anwar, A.; Mahmood, A. Comprehensive survey and taxonomies of false data injection attacks in smart grids: Attack models, targets, and impacts. Renew. Sustain. Energy Rev. 2022, 163, 112423. [Google Scholar] [CrossRef]
- Olowu, T.O.; Dharmasena, S.; Hernandez, A.; Sarwat, A. Impact analysis of cyber attacks on smart grid: A review and case study. In New Research Directions in Solar Energy Technologies; Springer: Berlin/Heidelberg, Germany, 2021; pp. 31–51. [Google Scholar]
- Liang, G.; Zhao, J.; Luo, F.; Weller, S.R.; Dong, Z.Y. A review of false data injection attacks against modern power systems. IEEE Trans. Smart Grid 2016, 8, 1630–1638. [Google Scholar] [CrossRef]
- Khan, A.A.; Beg, O.A.; Alamaniotis, M.; Ahmed, S. Intelligent anomaly identification in cyber-physical inverter-based systems. Electric Power Syst. Res. 2021, 193, 107024. [Google Scholar] [CrossRef]
- Peng, C.; Sun, H.; Yang, M.; Wang, Y.L. A survey on security communication and control for smart grids under malicious cyber attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1554–1569. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, B.; Wu, H. Smart grid cyber-physical attack and defense: A review. IEEE Access 2021, 9, 29641–29659. [Google Scholar] [CrossRef]
- Huseinović, A.; Mrdović, S.; Bicakci, K.; Uludag, S. A survey of denial-of-service attacks and solutions in the smart grid. IEEE Access 2020, 8, 177447–177470. [Google Scholar] [CrossRef]
- Li, F.; Yan, X.; Xie, Y.; Sang, Z.; Yuan, X. A review of cyber-attack methods in cyber-physical power system. In Proceedings of the 2019 IEEE 8th International Conference on Advanced Power System Automation and Protection (APAP), Xi’an, China, 21–24 October 2019; pp. 1335–1339. [Google Scholar]
- Wlazlo, P.; Sahu, A.; Mao, Z.; Huang, H.; Goulart, A.; Davis, K.; Zonouz, S. Man-in-the-middle attacks and defence in a power system cyber-physical testbed. IET Cyber-Phys. Syst. Theory Appl. 2021, 6, 164–177. [Google Scholar] [CrossRef]
- Das, A.K.; Zeadally, S. Data security in the smart grid environment. In Pathways to a Smarter Power System; Elsevier: Amsterdam, The Netherlands, 2019; pp. 371–395. [Google Scholar]
- Zhang, Z.; Ning, H.; Shi, F.; Farha, F.; Xu, Y.; Xu, J.; Zhang, F.; Choo, K.K.R. Artificial intelligence in cyber security: Research advances, challenges, and opportunities. Artif. Intell. Rev. 2022, 55, 1029–1053. [Google Scholar] [CrossRef]
- Zhang, Y.; Liu, J.; Shen, W. A Review of Ensemble Learning Algorithms Used in Remote Sensing Applications. Appl. Sci. 2022, 12, 8654. [Google Scholar] [CrossRef]
- Mienye, I.D.; Sun, Y. A Survey of Ensemble Learning: Concepts, Algorithms, Applications, and Prospects. IEEE Access 2022, 10, 99129–99149. [Google Scholar] [CrossRef]
- Harrou, F.; Taghezouit, B.; Khadraoui, S.; Dairi, A.; Sun, Y.; Hadj Arab, A. Ensemble Learning Techniques-Based Monitoring Charts for Fault Detection in Photovoltaic Systems. Energies 2022, 15, 6716. [Google Scholar] [CrossRef]
- Arman, A.; Krishnan, V.V.G.; Srivastava, A.; Wu, Y.; Sindhu, S. Cyber physical security analytics for transactive energy systems using ensemble machine learning. In Proceedings of the 2018 North American Power Symposium (NAPS), Fargo, ND, USA, 9–11 September 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Goyel, H.; Swarup, K.S. Data Integrity Attack Detection Using Ensemble-Based Learning for Cyber–Physical Power Systems. IEEE Trans. Smart Grid 2023, 14, 1198–1209. [Google Scholar] [CrossRef]
- Liu, S.; You, S.; Yin, H.; Lin, Z.; Liu, Y.; Yao, W.; Sundaresh, L. Model-Free Data Authentication for Cyber Security in Power Systems. IEEE Trans. Smart Grid 2020, 11, 4565–4568. [Google Scholar] [CrossRef]
- Toker, O.; Khalghani, M.R. Cyber Anomaly Detection Design for Microgrids using an Artificial Intelligent-Based Method. In Proceedings of the 2022 North American Power Symposium (NAPS), Salt Lake City, UT, USA, 9–11 October 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Dehghani, M.; Niknam, T.; Ghiasi, M.; Bayati, N.; Savaghebi, M. Cyber-Attack Detection in DC Microgrids Based on Deep Machine Learning and Wavelet Singular Values Approach. Electronics 2021, 10, 1914. [Google Scholar] [CrossRef]
- Dehghani, M.; Kavousi-Fard, A.; Dabbaghjamanesh, M.; Avatefipour, O. Deep learning based method for false data injection attack detection in AC smart islands. IET Gener. Transm. Distrib. 2020, 14, 5756–5765. [Google Scholar] [CrossRef]
- Mao, J. Data-Driven Cyberattack Detection for Microgrids. Master’s Thesis, KTH School of Electrical Engineering and Computer Science, Stockholm, Sweden, 2022. [Google Scholar]
- Reda, H.T.; Anwar, A.; Mahmood, A.; Chilamkurti, N. Data-driven approach for state prediction and detection of false data injection attacks in smart grid. J. Mod. Power Syst. Clean Energy 2022, 11, 455–467. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. Detection of false data injection cyber-attacks in DC microgrids based on recurrent neural networks. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 9, 5294–5310. [Google Scholar] [CrossRef]
- Kwon, S.; Yoo, H.; Shon, T. IEEE 1815.1-based power system security with bidirectional RNN-based network anomalous attack detection for cyber-physical system. IEEE Access 2020, 8, 77572–77586. [Google Scholar] [CrossRef]
- Qiu, W.; Tang, Q.; Wang, Y.; Zhan, L.; Liu, Y.; Yao, W. Multi-view convolutional neural network for data spoofing cyber-attack detection in distribution synchrophasors. IEEE Trans. Smart Grid 2020, 11, 3457–3468. [Google Scholar] [CrossRef]
- Naderi, E.; Asrari, A. Toward detecting cyberattacks targeting modern power grids: A deep learning framework. In Proceedings of the 2022 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 6–9 June 2022; pp. 357–363. [Google Scholar]
- He, Q.; Shah, P.; Zhao, X. Resilient operation of DC microgrid against FDI attack: A GRU based framework. Int. J. Electr. Power Energy Syst. 2023, 145, 108586. [Google Scholar] [CrossRef]
- Wan, Y.; Dragičević, T. Data-driven cyber-attack detection of intelligent attacks in islanded dc microgrids. IEEE Trans. Power Electron. 2022, 70, 4293–4299. [Google Scholar] [CrossRef]
- Sourav, S.; Biswas, P.P.; Chen, B.; Mashima, D. Detecting Hidden Attackers in Photovoltaic Systems Using Machine Learning. In Proceedings of the 2022 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Singapore, 25–28 October 2022; pp. 360–366. [Google Scholar]
- Li, F.; Xie, R.; Yang, B.; Guo, L.; Ma, P.; Shi, J.; Ye, J.; Song, W. Detection and identification of cyber and physical attacks on distribution power grids with pvs: An online high-dimensional data-driven approach. IEEE J. Emerg. Sel. Top. Power Electron. 2019, 10, 1282–1291. [Google Scholar] [CrossRef] [PubMed]
- Hakim, M.S.S.; Karegar, H.K. Detection of False Data Injection Attacks Using Cross Wavelet Transform and Machine Learning. In Proceedings of the 2021 11th Smart Grid Conference (SGC), Tabriz, Iran, 7–9 December 2021; pp. 1–5. [Google Scholar]
- Qiu, W.; Tang, Q.; Zhu, K.; Yao, W.; Ma, J.; Liu, Y. Cyber spoofing detection for grid distributed synchrophasor using dynamic dual-kernel SVM. IEEE Trans. Smart Grid 2020, 12, 2732–2735. [Google Scholar] [CrossRef]
- Ahmed, S.; Lee, Y.; Hyun, S.H.; Koo, I. Unsupervised machine learning-based detection of covert data integrity assault in smart grid networks utilizing isolation forest. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2765–2777. [Google Scholar] [CrossRef]
- Zhang, Y.; Yan, J. Domain-adversarial transfer learning for robust intrusion detection in the smart grid. In Proceedings of the 2019 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Beijing, China, 21–23 October 2019; pp. 1–6. [Google Scholar]
- EL-Ebiary, A.H.; Mokhtar, M.; Mansour, A.M.; Awad, F.H.; Marei, M.I.; Attia, M.A. Distributed Mitigation Layers for Voltages and Currents Cyber-Attacks on DC Microgrids Interfacing Converters. Energies 2022, 15, 9426. [Google Scholar] [CrossRef]
- Naderi, E.; Asrari, A. Detection of False Data Injection Cyberattacks: Experimental Validation on a Lab-scale Microgrid. In Proceedings of the 2022 IEEE Green Energy and Smart System Systems (IGESSC), Long Beach, CA, USA, 7–8 November 2022; pp. 1–6. [Google Scholar]
- Canaan, B.; Colicchio, B.; Abdeslam, D.O. Experimental HIl implementation of RNN for detecting cyber physical attacks in AC microgrids. In Proceedings of the 2022 International Symposium on Power Electronics, Electrical Drives, Automation and Motion (SPEEDAM), Sorrento, Italy, 22–24 June 2022; pp. 958–963. [Google Scholar]
- Mohiuddin, S.M.; Qi, J.; Fung, S.; Huang, Y.; Tang, Y. Deep learning based multi-label attack detection for distributed control of AC microgrids. In Proceedings of the 2021 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aachen, Germany, 25–28 October 2021; pp. 233–238. [Google Scholar]
- Canaan, B.; Colicchio, B.; Abdeslam, D.O.; Idoumghar, L. LSTM Networks for Cyber-physical Attack Diagnoses in Microgrids. In Proceedings of the 2023 IEEE 32nd International Symposium on Industrial Electronics (ISIE), Helsinki, Finland, 19–21 June 2023; pp. 1–6. [Google Scholar]
- Jadidi, S.; Badihi, H.; Zhang, Y. Design of an intelligent hybrid diagnosis scheme for cyber-physical PV systems at the microgrid level. Int. J. Electr. Power Energy Syst. 2023, 150, 109062. [Google Scholar] [CrossRef]
- Warraich, Z.; Morsi, W. Early detection of cyber–physical attacks on fast charging stations using machine learning considering vehicle-to-grid operation in microgrids. Sustain. Energy Grids Netw. 2023, 34, 101027. [Google Scholar] [CrossRef]
- Chen, Y.; Qi, D.; Dong, H.; Li, C.; Li, Z.; Zhang, J. A FDI attack-resilient distributed secondary control strategy for islanded microgrids. IEEE Trans. Smart Grid 2020, 12, 1929–1938. [Google Scholar] [CrossRef]
- Ye, J.; Giani, A.; Elasser, A.; Mazumder, S.K.; Farnell, C.; Mantooth, H.A.; Kim, T.; Liu, J.; Chen, B.; Seo, G.S.; et al. A review of cyber–physical security for photovoltaic systems. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 10, 4879–4901. [Google Scholar] [CrossRef]
- Gaggero, G.B.; Girdinio, P.; Marchese, M. Advancements and research trends in microgrids cybersecurity. Appl. Sci. 2021, 11, 7363. [Google Scholar] [CrossRef]
- Rana, M.M.; Li, L.; Su, S.W. Cyber attack protection and control of microgrids. IEEE/CAA J. Autom. Sin. 2017, 5, 602–609. [Google Scholar] [CrossRef]
- Sahoo, S.; Yang, Y.; Blaabjerg, F. Resilient synchronization strategy for AC microgrids under cyber attacks. IEEE Trans. Power Electron. 2020, 36, 73–77. [Google Scholar] [CrossRef]
- Sahoo, S.; Dragičević, T.; Blaabjerg, F. Multilayer resilience paradigm against cyber attacks in DC microgrids. IEEE Trans. Power Electron. 2020, 36, 2522–2532. [Google Scholar] [CrossRef]
- Zhang, J.; Sahoo, S.; Peng, J.C.H.; Blaabjerg, F. Mitigating concurrent false data injection attacks in cooperative dc microgrids. IEEE Trans. Power Electron. 2021, 36, 9637–9647. [Google Scholar] [CrossRef]
- Mishra, S.; Anderson, K.; Miller, B.; Boyer, K.; Warren, A. Microgrid resilience: A holistic approach for assessing threats, identifying vulnerabilities, and designing corresponding mitigation strategies. Appl. Energy 2020, 264, 114726. [Google Scholar] [CrossRef]
- Naderi, E.; Asrari, A. Experimental Validation of a Remedial Action via Hardware-in-the-loop System Against Cyberattacks Targeting a Lab-scale PV/Wind Microgrid. IEEE Trans. Smart Grid 2023, 14, 4060–4072. [Google Scholar] [CrossRef]
- Danilczyk, W.; Sun, Y.; He, H. ANGEL: An intelligent digital twin framework for microgrid security. In Proceedings of the 2019 North American Power Symposium (NAPS), Wichita, KS, USA, 13–15 October 2019; pp. 1–6. [Google Scholar]
- Zeng, H.; Zhao, Y.; Wang, T.; Zhang, J. Defense Strategy against False Data Injection Attacks in Ship DC Microgrids. J. Mar. Sci. Eng. 2022, 10, 1930. [Google Scholar] [CrossRef]
- Habibi, M.R.; Dragicevic, T.; Blaabjerg, F. Secure control of dc microgrids under cyber-attacks based on recurrent neural networks. In Proceedings of the 2020 IEEE 11th International Symposium on Power Electronics for Distributed Generation Systems (PEDG), Dubrovnik, Croatia, 28 September–1 October 2020; pp. 517–521. [Google Scholar]
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. False data injection cyber-attacks mitigation in parallel DC/DC converters based on artificial neural networks. IEEE Trans. Circuits Syst. II Express Briefs 2020, 68, 717–721. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Blaabjerg, F.; Dragičević, T. Secure control of DC microgrids for instant detection and mitigation of cyber-attacks based on artificial intelligence. IEEE Syst. J. 2021, 16, 2580–2591. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Blaabjerg, F.; Dragičević, T. Secure MPC/ANN-based false data injection cyber-attack detection and mitigation in DC microgrids. IEEE Syst. J. 2021, 16, 1487–1498. [Google Scholar] [CrossRef]
- Abianeh, A.J.; Wan, Y.; Ferdowsi, F.; Mijatovic, N.; Dragičević, T. Vulnerability identification and remediation of fdi attacks in islanded dc microgrids using multiagent reinforcement learning. IEEE Trans. Power Electron. 2021, 37, 6359–6370. [Google Scholar] [CrossRef]
- Basati, A.; Bazmohammadi, N.; Guerrero, J.M.; Vasquez, J.C. Real-time estimation in cyber attack detection and mitigation framework for dc microgrids. In Proceedings of the 2023 23rd International Scientific Conference on Electric Power Engineering (EPE), Brno, Czech Republic, 24–26 May 2023; pp. 1–6. [Google Scholar]
- Ye, Z.; Yang, H.; Zheng, M. Using modified prediction interval-based machine learning model to mitigate data attack in microgrid. Int. J. Electr. Power Energy Syst. 2021, 129, 106847. [Google Scholar] [CrossRef]
- Heidary, J.; Oshnoei, S.; Gheisarnejad, M.; Khalghani, M.R.; Khooban, M.H. Shipboard Microgrid Frequency Control Based on Machine Learning Under Hybrid Cyberattacks. IEEE Trans. Power Electron. 2023. [Google Scholar] [CrossRef]
- Alhelou, H.H.; Hatziargyriou, N.; Dong, Z.Y. Power Systems Cybersecurity: Methods, Concepts, and Best Practices; Springer Nature: Berlin/Heidelberg, Germany, 2023. [Google Scholar]
- Xia, Y.; Xu, Y.; Mondal, S.; Gupta, A.K. A Transfer Learning-Based Method for Cyber-Attack Tolerance in Distributed Control of Microgrids. IEEE Trans. Smart Grid 2023. [Google Scholar] [CrossRef]
- Zhao, L.; Zhang, X.; Chen, Y.; Peng, X.; Cao, Y. An Improved Load Forecasting Method Based on the Transfer Learning Structure under Cyber-Threat Condition. Comput. Intell. Neurosci. 2022, 2022, 1696663. [Google Scholar] [CrossRef] [PubMed]
- Kavousi-Fard, A.; Su, W.; Jin, T. A machine-learning-based cyber attack detection model for wireless sensor networks in microgrids. IEEE Trans. Ind. Inform. 2020, 17, 650–658. [Google Scholar] [CrossRef]
- Cui, H.; Dong, X.; Deng, H.; Dehghani, M.; Alsubhi, K.; Aljahdali, H.M.A. Cyber attack detection process in sensor of DC micro-grids under electric vehicle based on Hilbert–Huang transform and deep learning. IEEE Sensors J. 2020, 21, 15885–15894. [Google Scholar] [CrossRef]
- Javed, A.R.; Ahmed, W.; Pandya, S.; Maddikunta, P.K.R.; Alazab, M.; Gadekallu, T.R. A survey of explainable artificial intelligence for smart cities. Electronics 2023, 12, 1020. [Google Scholar] [CrossRef]
- Machlev, R.; Heistrene, L.; Perl, M.; Levy, K.; Belikov, J.; Mannor, S.; Levron, Y. Explainable Artificial Intelligence (XAI) techniques for energy and power systems: Review, challenges and opportunities. Energy AI 2022, 9, 100169. [Google Scholar] [CrossRef]
- Ajayi, O. Explainable AI (XAI) for Fault Detection and Classification in Microgrids Using a Real-Time Simulation Framework. Master’s Thesis, The Pennsylvania State University, State College, PA, USA, 2023. [Google Scholar]
- Larriva-Novo, X.; Sánchez-Zas, C.; Villagrá, V.A.; Marín-Lopez, A.; Berrocal, J. Leveraging Explainable Artificial Intelligence in Real-Time Cyberattack Identification: Intrusion Detection System Approach. Appl. Sci. 2023, 13, 8587. [Google Scholar] [CrossRef]
- Zhang, C.; Ma, Y. Ensemble Machine Learning: Methods and Applications; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Wu, T.; Xue, W.; Wang, H.; Chung, C.; Wang, G.; Peng, J.; Yang, Q. Extreme learning machine-based state reconstruction for automatic attack filtering in cyber physical power system. IEEE Trans. Ind. Inform. 2020, 17, 1892–1904. [Google Scholar] [CrossRef]
- Huang, B.; Wang, J. Applications of physics-informed neural networks in power systems—A review. IEEE Trans. Power Syst. 2022, 38, 572–588. [Google Scholar] [CrossRef]
- She, B.; Li, F.; Cui, H.; Shuai, H.; Oboreh-Snapps, O.; Bo, R.; Praisuwanna, N.; Wang, J.; Tolbert, L.M. Inverter PQ Control with Trajectory Tracking Capability for Microgrids Based on Physics-informed Reinforcement Learning. IEEE Trans. Smart Grid 2023. [Google Scholar] [CrossRef]
- Wang, L.; Zhang, S.; Zhou, Y.; Fan, C.; Zhang, P.; Shamash, Y.A. Physics-Informed, Safety and Stability Certified Neural Control for Uncertain Networked Microgrids. IEEE Trans. Smart Grid 2023. [Google Scholar] [CrossRef]
- Wang, Y.; Qiu, D.; Sun, M.; Strbac, G.; Gao, Z. Secure energy management of multi-energy microgrid: A physical-informed safe reinforcement learning approach. Appl. Energy 2023, 335, 120759. [Google Scholar] [CrossRef]
- Zhang, H.; Yue, D.; Dou, C.; Hancke, G.P. Resilient optimal defensive strategy of micro-grids system via distributed deep reinforcement learning approach against fdi attack. IEEE Trans. Neural Netw. Learn. Syst. 2022. [Google Scholar] [CrossRef] [PubMed]
- Chatzivasileiadis, S.; Venzke, A.; Stiasny, J.; Misyris, G. Machine learning in power systems: Is it time to trust it? IEEE Power Energy Mag. 2022, 20, 32–41. [Google Scholar] [CrossRef]
- Simonovich, L. Leveraging Security Analytics To Mitigate the Risk of Cyberattacks on Oil & Gas Infrastructure. In Proceedings of the World Petroleum Congress, WPC, Moscow, Russia, 15–19 June 2014; p. D021S019R003. [Google Scholar]
- SiemensEnergy. Industrial Cybersecurity EOS.iiTM Monitoring and Detection Platform. Available online: https://assets.siemens-energy.com/siemens/assets/api/uuid:c7ac7495-74a5-482f-81c7-fac6b45e5689/EOS.ii-Whitepaper-21-09-14.pdf (accessed on 10 November 2023).
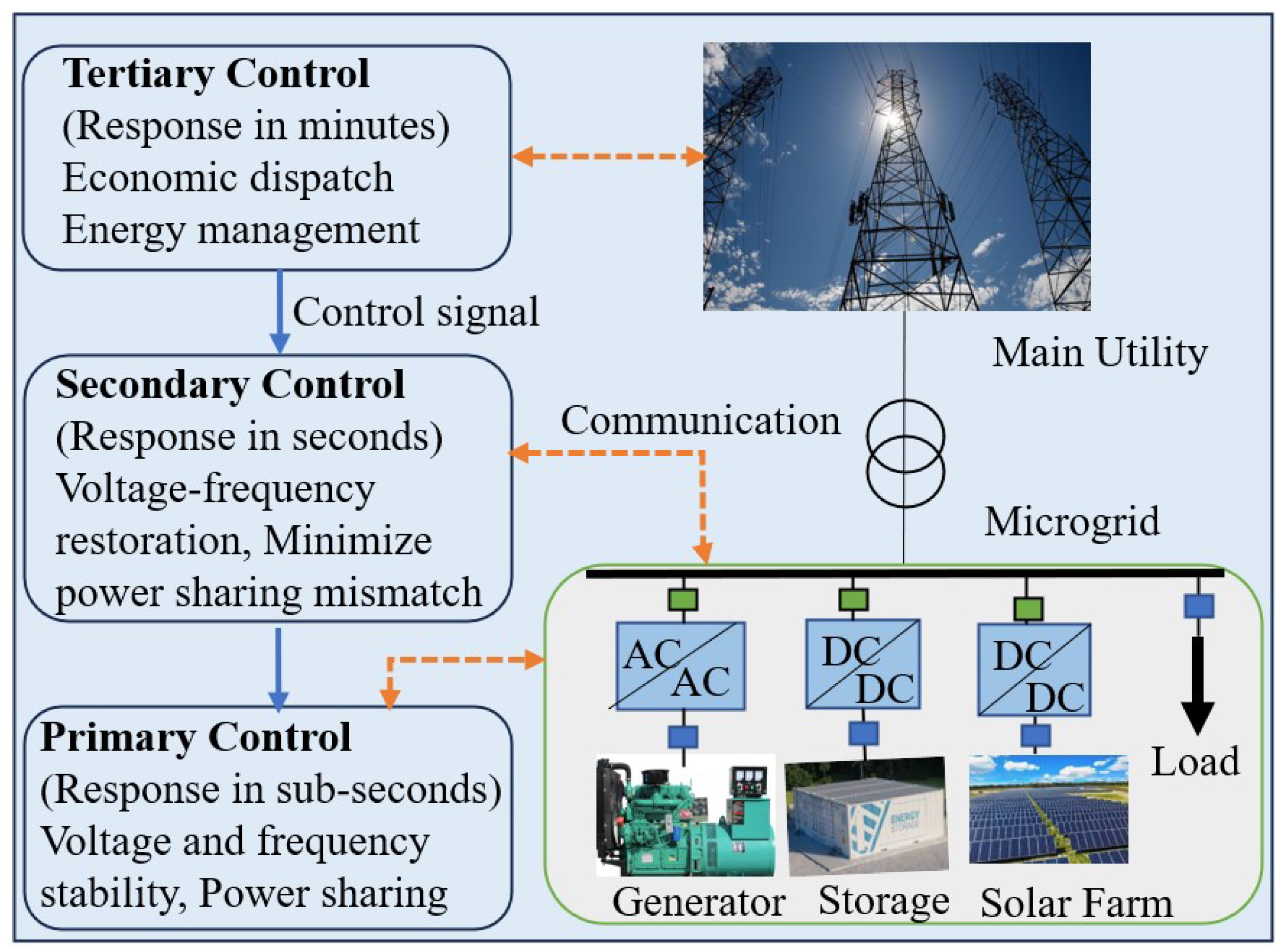


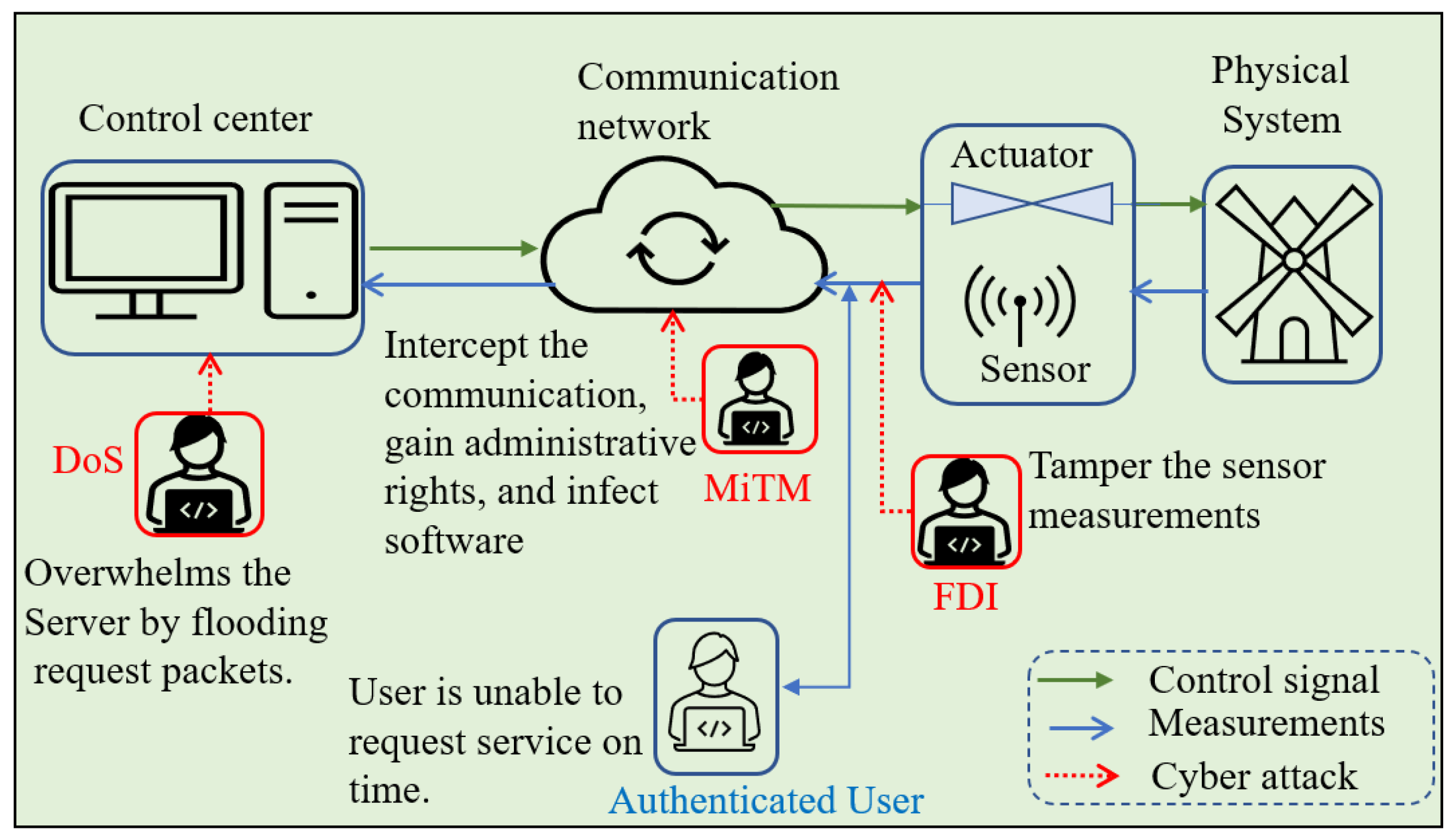


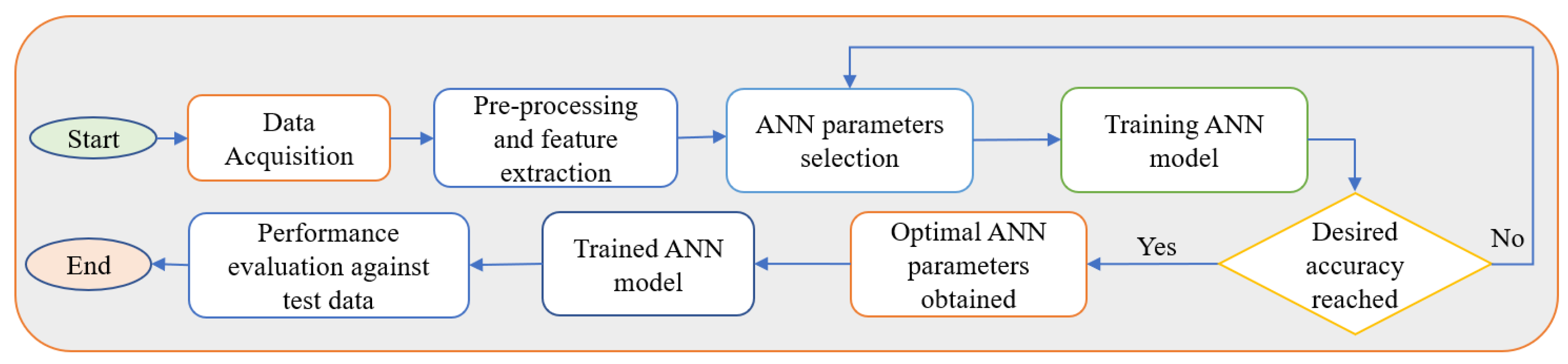
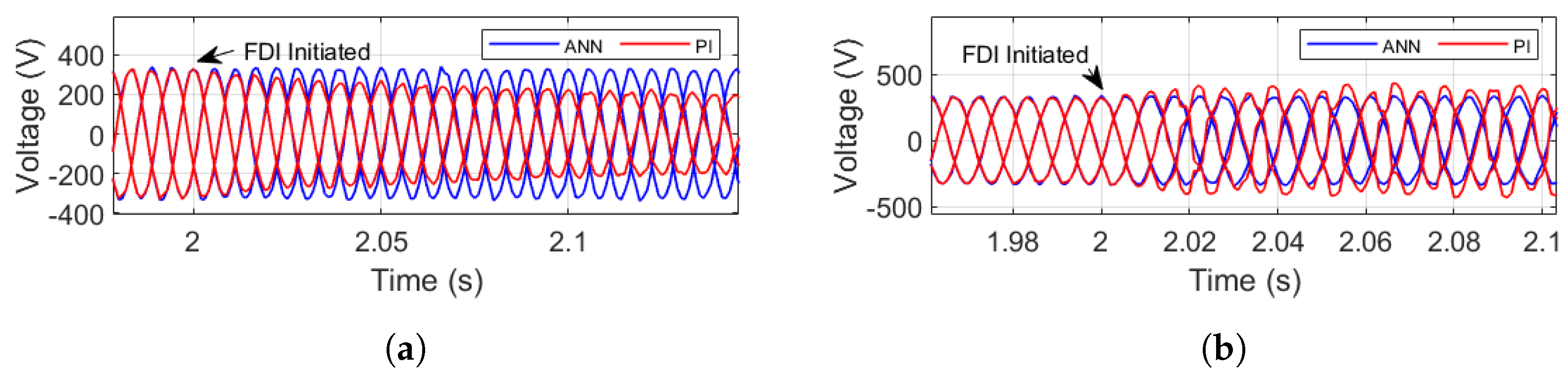
| Location | Target | Type | Impact |
|---|---|---|---|
| North America (2003) | Network failures in control room operating system | Denial of service | Blackout across multiple regions |
| Korea Hydro and Nuclear Power (2014) | Unauthorized access to critical information | Potential loss of confidential information and designs | Compromised security and safety of plant and personnel |
| Ukraine (2015) | BackEnergy malware in control room computers | Denial of service, False data injection | Blackout across multiple substations |
| Kyiv (2016) | Industroyer malware targeting industrial control systems | Denial of service, Issuing false control commands | Power outage to at least one-fifth of Kyiv |
| Middle East petrochemical plant (2017) | Safety system of the plant | Potential denial of services and life loss | Plant shut down |
| System | Attack | Algorithm | Data | Performance Metric |
|---|---|---|---|---|
| Islanded AC | FDI (control signals, communication networks) | Wavelet transform with deep learning using deep auto-encoder | MATLAB simulations, Unsupervised | Accuracy, >97% [73] |
| FDI into load frequency control | Auto-encoder neural network | Using datasets on TensorFlow and Keras software framework, Unsupervised | Not given, [71] | |
| DoS and FDI into control and measurement signals | Feed-forward ANN, NB, SVM | MATLAB/real-time simulation, Supervised | MAPE 1 0.6% (FDI), 0.1% (DoS), [57] | |
| DoS, FDI, and time delay on communication and measurements | LSTM, CNN | Simulation-based data, Supervised | Accuracy nearly 100%, [74] | |
| Islanded DC | FDI into voltage and current measurements | Linear regression | Simulation-based, Supervised | Not given, [36] |
| FDI into output voltage sensor of DC converter | Deep learning | Simulation-based, Supervised using back propagation | Not given, [37] | |
| FDI into DC bus voltage sensor | Deep learning | Matlab simulation, Supervised | Not given, [38] | |
| FDI into voltage sensor | Deep learning auto-encoder with grey wolf optimization | Simulation-based, Unsupervised | Precision 95%, [72] | |
| RL 3-based intelligent FDI into measurements and control signals | Pattern recognition network, type of feed-forward ANN | Simulation-based, Supervised | Accuracy 98.5%, [81] | |
| FDI into measurements and communications | NARX ANN | MATLAB/real-time simulations, Supervised | MAPE 1 0.064% (voltages), 0.36% (currents), [76] | |
| FDI into sensor, communication network, and measurements | Gated recurrent unit neural network | MATLAB simulation, Supervised | RMSE 2 0.028036, [80] | |
| Networked | FDI,MiTM, and DoS on network communication | Deep learning | Real data (from smart grid, substation, power plant), Supervised | Accuracy 96.50%, [39] |
| FDI into measurements | NB, RF, Regression | Simulation-based, Supervised | F-score (0.08,095,0.81) for (NB, RF, Regression, respectively), [40] | |
| FDI on substation measurements and sensors | Ensemble learning technique, minimum voting for critical class | Simulation-based, Supervised | Accuracy 98.8%, [69] | |
| FDI into wide area communication networks and measurements | Deep recurrent ANN | Simulation-based, Supervised | MSE 4 2.15 × 10, [75] | |
| FDI and DoS sensor measurements and PV control operation modes | LR, kNN, GBT, RF, MLP | (Real smart home electricity consumption data, real solar power, and MATPOWER simulations), Supervised-based data. | Accuracy 95%, [82] | |
| FDI and time delay on PV control center | Auto-regressive (AR), data driven approach | Simulation-based, Supervised | Not given, [83] | |
| FDI into substation measurements, sensors, and control commands | domain-adversarial training based on neural networks (DANN) | Datasets obtained from experimental hardware testbed, Transfer learning | Accuracy 80%, [87] |
| System | Attack | Algorithm | Data | Performance Metric |
|---|---|---|---|---|
| Islanded DC | FDI into currents and voltage measurements | Feed-forward ANN | Real-time Typhoon simulation, supervised | Accuracy >90%, [88] |
| FDI into communication network | RNN | MATLAB real-time simulation, Supervised | Not given, [89] | |
| Islanded AC | FDI into communication layer and replay attacks | NARX ANN | MATLAB real-time simulation, Supervised | Not given, [90] |
| FDI into output voltage and power measurements | Deep learning using rectified linear unit | MATLAB simulation, Supervised | Accuracy 91%, [91] | |
| FDI into measurements | LSTM | MATLAB simulation, Supervised | Not given, [92] | |
| Networked | FDI into substation measurements and sensors | Cross wavelet transform with SVM classifier | Simulation-based, Supervised | Accuracy 95.53%, [84] |
| Network traffic attacks (FDI, malware behavior (Dos), Disabling reassembly) | Bidirectional RNN | Normal dataset from operating IEEE 1815.1-based Korean substation and simulations based attacked dataset, Supervised | Accuracy 98%, [77] | |
| FDI (measurement source data spoofing) | Ensemble empirical mode decomposition using back propagation neural network | Real data from universal grid analyzers in US locations, Supervised | Accuracy 96%, [70] | |
| FDI (spoofing synchrophasor measurements) | Dynamic dual kernel SVM | distributed Synchrophasor data from FNET/GridEye, (Supervised, particle swarm optimization) | Accuracy 94.26%, [85] | |
| FDI (spoofing synchrophasor measurements) | Multi-view convolutional neural networks (CNN) | Distributed synchrophasor data from 11 locations in the frequency measurements network FNET/GridEye, Supervised | Accuracy 91.46%, [78] | |
| FDI into sensor and measurements | Isolation forest based technique | MATPOWER based simulations, Unsupervised | Accuracy 94%, [86] | |
| FDI, DoS, Distributed DoS on communication networks and sensors | Deep Learning(LSTM,RNN) | MATLAB-based simulation, Supervised | Accuracy 95%, [79] | |
| FDI into PV related measurements | ANFIS | MATLAB simulation, Supervised | RMSE 0.11, [93] | |
| DOS, communication layer | Decision Tree classifier | MATLAB simulation, supervised | Accuracy 98%, [94] |
| System | Control | Attack | Algorithm | Data | Performance Metric |
|---|---|---|---|---|---|
| Islanded DC | Distributed secondary control | FDI into cyber layer | ANFIS | MATLAB simulation, Supervised | Accuracy 99.40%, [42] |
| Adaptive model predictive control (APMC) | FDI into voltage and current sensors | ANFIS | MATLAB simulation, Unsupervised | RMSE 0.000846, MAE 0.001543, [43] | |
| Decentralized cooperative control | FDI into cyber layer (current measurements) | Feed-forward ANN | MATLAB real-time simulation, Supervised | Not given, [46] | |
| Supervisory control | FDI into secondary control voltage and current measurements | Feed-forward ANN | MATLAB simulation, Supervised | Not given, [105] | |
| Distributed cooperative secondary control | FDI into cyber layer measurements | Feed-forward ANN | MATLAB real-time simulation, Supervised | Not given, [107] | |
| Droop control | FDI into output voltage measurements | Deep learning Gated recurrent unit | MATLAB Simulation, Supervised | RMSE <0.05, [80] | |
| Distributed cooperative secondary control | FDI into cyber layer voltage and current measurements | Feed-forward ANN | MATLAB simulation, Supervised | MSE 5 × 10, [108] | |
| Distributed cooperative secondary control | FDI into cyber layer current and voltage measurements | NARX ANN | MATLAB simulation, Supervised | Not given, [106] | |
| Model predictive control | FDI into cyber layer currents and voltages | Feed-forward ANN | MATLAB simulation, Supervised | MSE 2.9 × 10, [109] | |
| Distributed cooperative secondary control | FDI into cyber layer currents and voltages | Multiagent deep reinforcement learning | MATLAB and dSpace MicroLabBox, Supervised | Not given, [110] | |
| Synchronous buck converter primary control | FDI into output voltage sensor | Back-propagation ANN | MATLAB simulation, Supervised | RMSE 0.000283, [37] | |
| Islanded AC | Distributed cooperative secondary control | FDI into measurements and communication network | NARX ANN | MATLAB real-time simulation, Supervised | MAPE 0.01%, [44] |
| Load frequency control with electric vehicles | FDI into measurements and communication network | Hyper basis function neural network | MATLAB simulation, Supervised | RMSE 0.0015, [45] | |
| Distributed cooperative secondary control | FDI into measurements and communication network | Feed-forward ANN | MATLAB real-time simulation, Supervised | Not given, [57] | |
| IEEE distribution networks and islanded microgrid with supervisory control | FDI (Low-frequency source oscillations) | Ensemble learner | Digisilent, Supervised | True positive rate (TPR) >90% False positive rate (FPR) < 3%, [111] | |
| Islanded AC | Central supervisory control | FDI into smart metering devices and central controller unit | Modified prediction interval-based LSTM | Residential microgrid data, Supervised | Accuracy 97%, [112] |
| Secondary control for frequency regulation | DoS and FDI into measurements | Adaptive reinforcement learning | MATLAB real-time simulation, Supervised | MAE 1.2 × 10, [113] |
| Learning Method | Attack | Algorithm | Data | Performance Metric |
|---|---|---|---|---|
| Transfer Learning | FDI, DoS | RSD-based transfer learning | MATLAB/Simulink based simulation | RMSE 3.332 × 10−3, [115] |
| FDI | Deep transfer learning | Raw power fluctuations data from neighboring cities | MAPE 2.87%, RMSE 0.042, [116] | |
| FDI | Lower and Upper Bound Estimator (LUBE) combined with Optimization | Smart meters on the customer side | Confusion matrix CR 91.64% FR 8.63%, [117] | |
| FDI | Deep learning using Krill Herd Optimization algorithm | Distinctive datasets generated via bootstrap | Accuracy 93.76%, [118] | |
| Explainable Learning | FDI | XAI framework using python libraries | Accuracy, recall and precision, [121] | |
| FDI | Explainable AI using SHAP | UNSW-NB15 | True Positive Ration (TPR) and False Positive Ration (FPR), [122] | |
| Physics-based Learning | FDI | DRL | microgrid simulations | Average security level [129] |
| Parameter | Value | Parameter | Value |
|---|---|---|---|
| (0.23 + j318 µ) | 300 V | ||
| (0.35 + j1847 µ) | 1.35 mh | ||
| (0.23 + j318 µ) | 50 µF | ||
| Simulator | OP5600 from OPAL-RT | Processor | 4 Cores, 3.0 GHz |
| Software | RT-LAB 2019 | FPGA | Xilinx® Artix®-7 from OPAL-RT |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Beg, O.A.; Khan, A.A.; Rehman, W.U.; Hassan, A. A Review of AI-Based Cyber-Attack Detection and Mitigation in Microgrids. Energies 2023, 16, 7644. https://doi.org/10.3390/en16227644
Beg OA, Khan AA, Rehman WU, Hassan A. A Review of AI-Based Cyber-Attack Detection and Mitigation in Microgrids. Energies. 2023; 16(22):7644. https://doi.org/10.3390/en16227644
Chicago/Turabian StyleBeg, Omar A., Asad Ali Khan, Waqas Ur Rehman, and Ali Hassan. 2023. "A Review of AI-Based Cyber-Attack Detection and Mitigation in Microgrids" Energies 16, no. 22: 7644. https://doi.org/10.3390/en16227644
APA StyleBeg, O. A., Khan, A. A., Rehman, W. U., & Hassan, A. (2023). A Review of AI-Based Cyber-Attack Detection and Mitigation in Microgrids. Energies, 16(22), 7644. https://doi.org/10.3390/en16227644








