Cyber Threats to Smart Grids: Review, Taxonomy, Potential Solutions, and Future Directions
Abstract
:1. Introduction
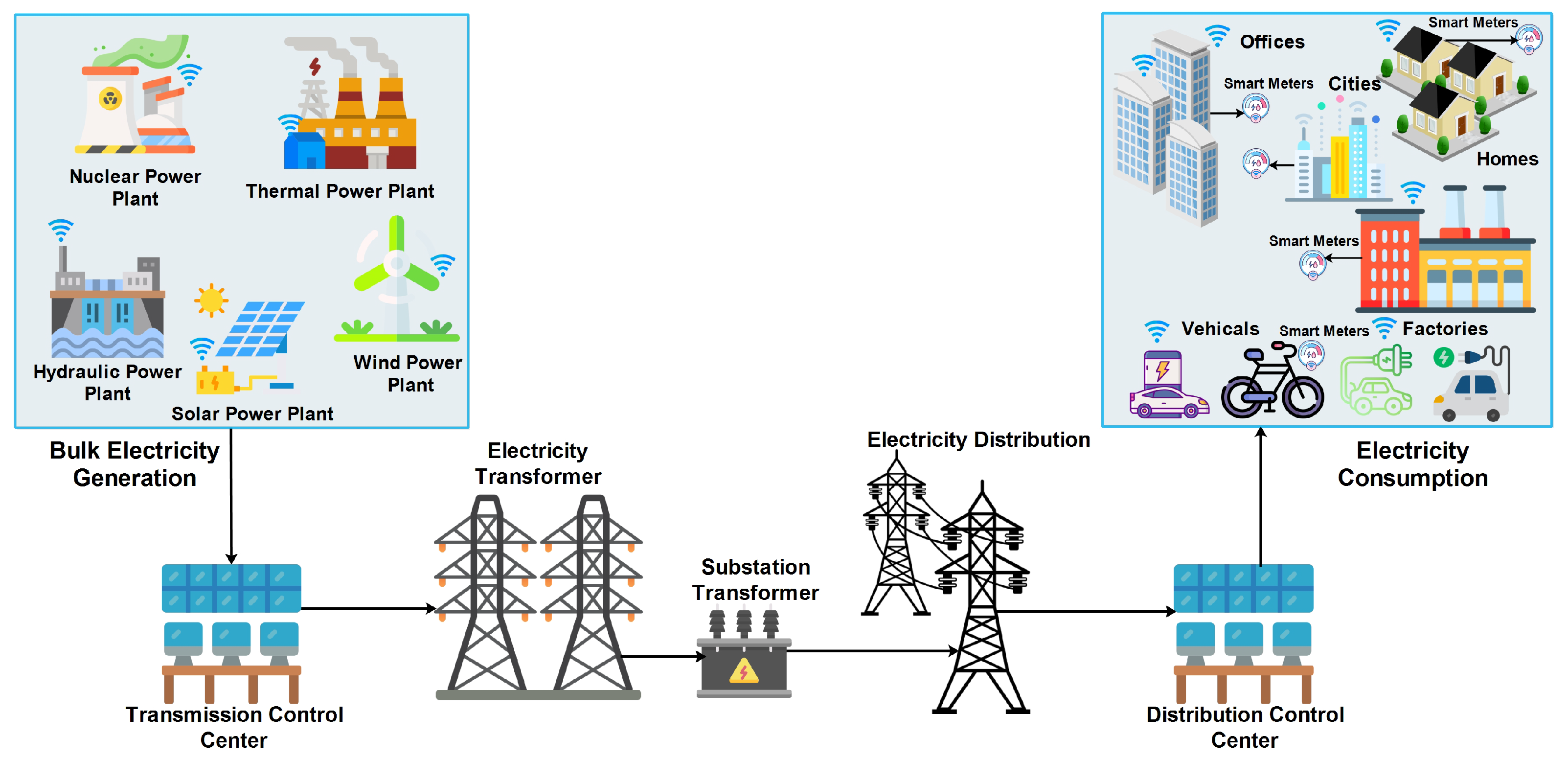
1.1. Overview of Smart Grid Infrastructure
- SmartGrid.gov: like the Internet, the Smart Grid will consist of controls, computers, automation, and new technologies and equipment working together, but in this case, these technologies will work with the electrical grid to respond digitally to our quickly changing electric demand [11].
- National Institute of Standards and Technology (U.S. Department of Commerce): The smart grid is a planned nationwide network that uses information technology to deliver electricity efficiently, reliably, and securely. It has been called “electricity with a brain”, “the energy internet”, and “the electronet”. A more comprehensive definition we use at NIST is a modernized grid that enables bidirectional flows of energy and uses two-way communication and control capabilities that will lead to an array of new functionalities and applications [12].
- Grid 2030: Grid 2030 is a fully automated power delivery network that monitors and controls every customer and node, ensuring a two-way flow of electricity and information between the power plant and the appliance, and all points in between. Its distributed intelligence, coupled with broadband communications and automated control systems, enables real-time market transactions and seamless interfaces among people, buildings, industrial plants, generation facilities, and the electric network [13].
- The Office of Electricity: An automated, widely distributed energy delivery network, the Smart Grid will be characterized by a two-way flow of electricity and information and be capable of monitoring everything from power plants to customer preferences to individual appliances. It incorporates into the grid the benefits of distributed computing and communications to deliver real-time information and enable the near-instantaneous balance of supply and demand at the device level [14].
- Internet Technology (IT) and Operational Technology (OT): IT provides conditions for the two-way interaction and sharing of information flow in the smart grid. Due to the openness of the protocol, the information collected from different components of the power grid can be circulated conveniently. The advanced technologies such as wireless communication, satellite communication, and laser communication provide diverse and accurate information acquisition and transmission services for the smart grid.To realize the high integration of the industrialization process and information construction, the smart grid needs the help of OT. OT and IT are two different concepts, and this difference is reflected in the operation, technology, and management of the system [15]. The core idea of OT is to effectively transform the long-term accumulated manual experience into an applicable knowledge system for computers and other equipment, and build the automatic operation and management process of the power grid [16].
- Supervisory Control and Data Acquisition (SCADA): SCADA is widely used in the power system to realize the monitoring and control of field equipment [17]. In this system, the remote terminal unit (RTU) and feeder terminal unit (FTU) provide strong support for data acquisition, control, regulation, feedback, alarm, and other operations. With the continuous development of the computer industry, SCADA began to combine new technologies such as expert systems, artificial intelligence, deep learning, and knowledge inference to improve the linkage ability of all parts of the power grid [18]. However, the growth of remote accessibility between systems has compromised the security of SCADA [19].
- Cyber-Physical Systems (CPS): Realizing the deep convergence of physical space and cyberspace is the ultimate goal of CPS. During the construction of the power grid, physical space contains a variety of infrastructure related to power systems, such as power generation equipment, substation equipment, transmission equipment, and electrical equipment. Ning et al. [20] pointed out that arithmetic logic unit (ALU) with computing function, various devices used for storage, gateways/routes used for data transmission belongs to things that appear together in cyberspace. They can transform things in traditional physical space to make them have the ability of perception, computing, and communication [21].
- Internet of Things (IoT): Using sensor network, radio frequency identification technology (RFID), intelligent embedding technology, and other means, it is possible to take the network as the carrier to build a things-centered information interaction network, that is, IoT. Compared with CPS, IoT aims to realize the ubiquitous connection between physical space and cyberspace, to realize the intelligent management of things. Since power generation, transmission, and final power consumption require the cooperation and linkage of different components in the power grid, the effective management of each component is an important measure to achieve intelligence. In the process of construction and the improvement of the smart grid, the data sharing and management mechanisms of the system also need to solved in terms of perception, transmission, and application, so that they can be realized by relying on the three layers including the sensing, network, and application layer architecture of the IoT.
- Fog/edge computing: With the development of micro miniaturization, low power consumption, intelligence, high integration, and networking of sensors, fog computing and edge computing have become important technologies that can be applied in the construction of distributed smart grids [22]. At present, the transformation of the smart grid is developing towards decentralization and distribution. Compared with the current highly centralized power system, this scheme has the advantage of, in case of failure or other accidents, being able to theoretically reduce the scope and scale of influence.
- Internet of Energy (IoE): The goal of IoE is to transform the electricity-related infrastructure of existing energy producers and suppliers, making them digital, automated, and intelligent. Such transformation is a necessary basis for building a smart grid [23]. The development of IoE relies on IoT, which can help accelerate the transformation of traditional power grids to smart grids. The purpose of IoE construction is to make energy production more environmentally friendly [24], energy utilization more efficient, energy consumption reduced, and energy cost more economical.
1.2. Research Method
1.3. Our Contribution
1.4. Organization of Paper
2. Vulnerabilities of Smart Grids
2.1. Vulnerabilities in Physical Components
- Inadequate physical access control systems, e.g., inadequate camera surveillance, and inadequate surveillance at unmanned sites;
- Inadequate physical security for DERs at remote locations;
- Internal redundancy constraints within the substation;
- Inadequate monitoring of long lines;
- Obsolete components and long replacement times for damaged equipment;
- Inadequate filtering of electromagnetic pulses near the smart grid system;
- Poor physical environment of grid operation.
2.2. Vulnerabilities in IT/OT
- Vulnerabilities in Hardware and SoftwareSmart grids consist of a large number of different smart hardware and software, especially networked devices. Any vulnerability in this hardware and software can lead to corresponding cyberattacks [28]. These devices include:
- Field devices I/O, such as pump, sensor, fan, valve;
- Control level, such as HMI, RTU;
- Process level, such as HMI, SCADA server;
- Operation workstation, various servers, such as DNS servers, file servers, mail servers;
- Network devices, such as routers, IT&OT DMZ;
- Enterprise IT, such as ERP, Mail, CRM, security operation center (log Management, SIEM, Analytics).
The reported vulnerabilities in National Vulnerability Database (NVD), Vulnerability Database (VULDB) [29], and CVE Details [30] demonstrate the increasing vulnerabilities in the hardware/software of smart grid and general software [31]. The CVE and CVSS show the long-term trend of increasing vulnerabilities on smart grid devices and combined software [30,32]. The vulnerability of these smart grid devices with intelligent operation and networking capabilities is growing rapidly, not only because of more vulnerabilities in the new devices but because of evolving smart grid systems, newer smart grid operating environments, and expanding applications and services. - Vulnerabilities in data communicationsVarious modern communication technologies are used in different areas of the smart grid, such as IEC 61850, IEC 60870-5-104, DNP3, PRP/HSR, Modbus, Synchrophasor, DLMS/COSEM, AMI, TASE.2/ICCP, NTP, and also the protocols used in IT parts, as well as other new communication technologies and protocols. These communication technologies and protocols themselves contain various traditional and new vulnerabilities [33]. These vulnerabilities also facilitate various communication and network-based attacks [26,34].
2.3. Vulnerabilities in Data Management
2.4. Vulnerabilities in Services and Applications
- Lack of patching policy and regular updates, e.g., unpatched software and systems;
- Common mode failures;
- Improper asset management;
- Improper maintenance documentation;
- Use of outdated operating system versions;
- Inadequate AAA: authentication (to identify), authorization (to grant permission), and accounting (to log an audit trail);
- Poor grid isolation from the Internet;
- Lack of intrusion detection systems for OT;
- Inadequate malware detection and defense for OT;
- Unreliable technology provider for those OT devices;
- Inadequate compatibility with legacy systems and legacy devices.
2.5. Vulnerabilities in Running Environment
- Staff incompetence, e.g., lack of professional skills, unreliable and dishonest behavior, etc.;
- Weak controls on legal, social, and ethical aspects;
- Weak relationships between managers;
- Inadequately controlled outsourcing;
- Non-compliance with national and international regulations;
- Political, war, or regional conflicts;
- Terrorism;
- Government corruption;
- Pandemics.
2.6. Vulnerabilities in Evolving and Complex Smart Grids
- Identify and detect as many and as complete vulnerabilities as possible at all levels of the system, as any undiscovered vulnerability can lead to potential security risks. The security of the smart grid is determined by the weakest part, not by the strongest part.
- Repair or remove system vulnerabilities as soon as possible. Once vulnerabilities exist and are discovered, hidden threats must be eliminated as quickly as possible. Many cyberattacks exploit zero-day vulnerabilities.
- Vulnerability aggregation. The final vulnerability of the system is not simply a collection of vulnerabilities. It is necessary to clarify the physical, logical, and functional dependencies between them and figure out their aggregation rules. This enables a complete understanding of the system vulnerability of smart grids.
- Automated discovery and analysis of system vulnerabilities are necessary. The smart grid system contains various vulnerabilities, and it is difficult to find all vulnerabilities manually with exhaustive methods and analyze them in time. Automated methods need to be developed to support vulnerability detection, analysis, and management.
- Vulnerability analysis and attack matching. All cyberattacks exploit one or more vulnerabilities in a system. A clear map of vulnerabilities and attacks is very helpful in defending and protecting system security.
- It is necessary to create a systematic plan with countermeasures to address the vulnerabilities. A single point of failure or weak point of failure is always a challenge to a smart grid.
3. Global Review of Cyberattacks to Smart Grids
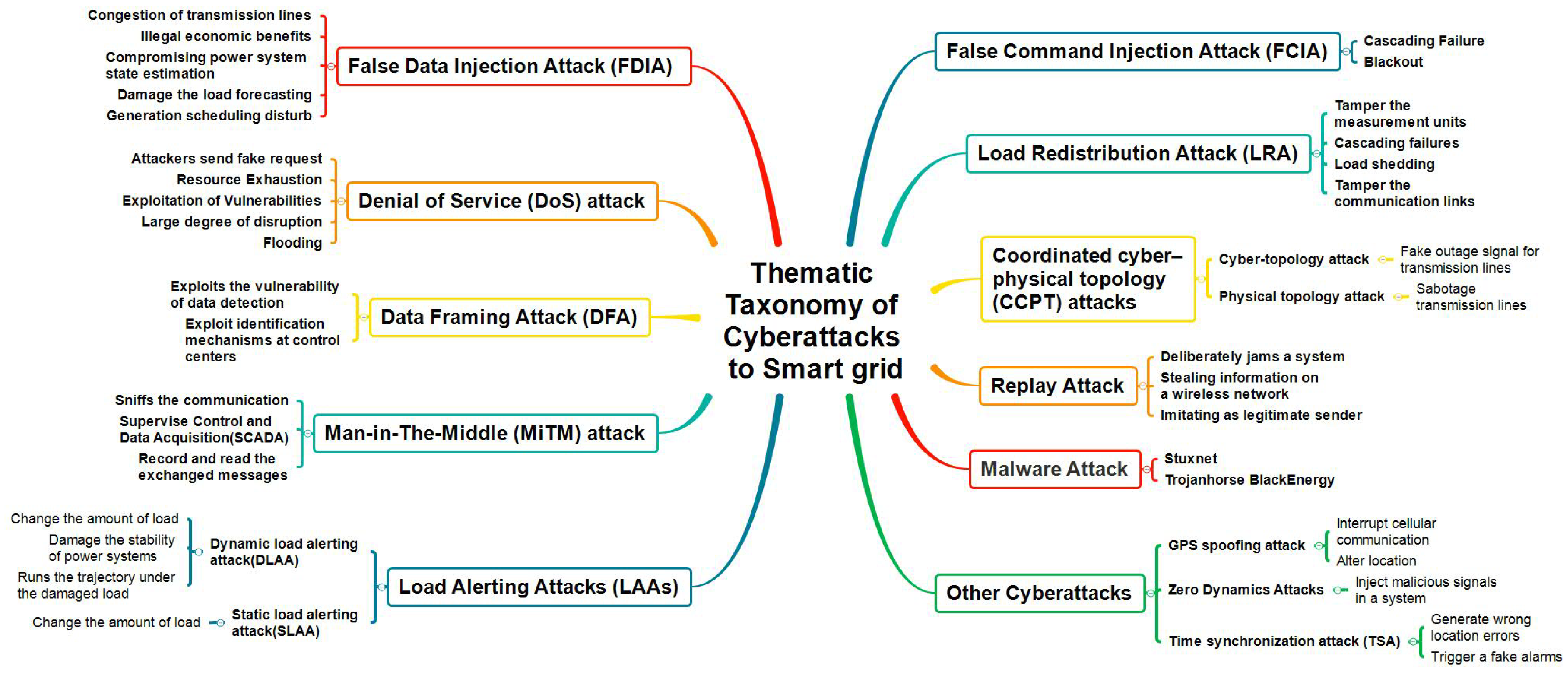
4. Thematic Taxonomy of Cyberattacks to Smart Grid
4.1. False Data Injection Attack
4.2. Denial-of-Service Attack
4.3. Data Framing Attacks
4.4. Man-in-the-Middle (MITM) Attack
4.5. Load Altering Attack
4.6. Malicious Command Injection Attack
4.7. Load Redistribution Attacks
4.8. Coordinated Cyber Physical Topology Attacks
4.9. Replay Attack
4.10. Malware Attacks
4.11. Other Cyberattacks
5. Potential Solutions for Cybersecurity in Smart Grid
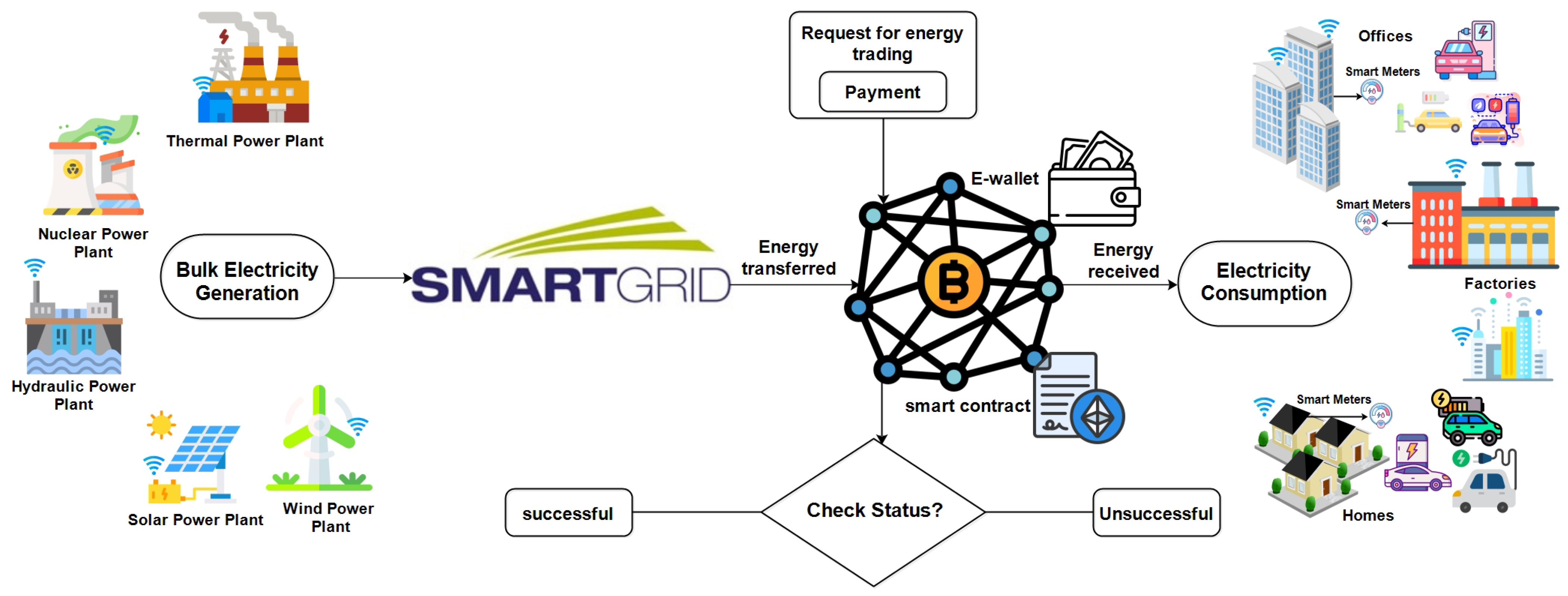
5.1. Blockchain Based Cybersecurity Techniques in Smart Grid
| Reference | Objective | Type of Attack | Solution | Consensus Algorithm | Blockchain Tool | Smart Contract Tool | Performance Evaluation |
|---|---|---|---|---|---|---|---|
| [129] | To propose a data analytics scheme, to identify malicious behavior in the SG system. | FDIA and SM failure | ARIMA and blockchain-based schemes to classify attacked/non-attacked, and reward to utility provider to deal with malicious activity. | - | Ethereum | Remix IDE | Prediction accuracy, latency, and data storage cost |
| [130] | Aim to control the smart meter attacks, protect them from unauthorized access and DDoS attacks. | DDoS | A decentralized architecture based on the blockchain in a distributed and trustworthy manner to deal with DDoS attacks. | - | Ethereum | Truffle framework | Flexibility, security and cost effectiveness |
| [79] | Aim to detect the network attacks and fraudulent transactions in smart grids. | Network attacks and fraudulent transactions | A blockchain-based scheme to achieve privacy with short signature, hash function for the exchange of energy between nodes and RNN for attack detection. | PBFT | - | - | Accuracy, detection rate and false alarm rate |
| [132] | Developed the blockchain-based decentralized mechanism against cyberattacks. | Coordinated replay attacks | Decentralized mechanism that relies on Bayesian inference with Ethereum-based blockchain. | PoA | Geth-based | Solidity | Computational performance and accuracy |
| [137] | To build the mechanism against PMU as it is susceptible to cyber-attacks due to their reliance on the GPS. | FDIAs | Consensus-based approach to improve the self-defensive capabilities of smart grids against cyberattacks. | - | - | - | Successful attack capability and probabilities |
| [133] | Detect the manipulation of meters’ measurements that causes flawed decisions to be made in energy systems | FDIAs | Implementation of transparent public Blockchain-based SG data security | - | - | - | Accuracy, RMSE, MAE, and F1 score |
| [134] | Aim to solve the anonymity and privacy problem of consumers | SPoF and lack of trust | Implementation of garlic routing and consortium blockchain for privacy preservation during energy transfer in SGs. | PoA | - | - | Computational cost and path selection probability |
| [138] | To detect the identity-based security loop holes in the smart grid | Data manipulation and identity theft attacks | Blockchain-based identification and authentication technique to prevent identity theft and masquerading. | - | Hyperledger | - | Validation of the node in log(n) |
| [135] | Mitigate the cheating attack initiated by energy sellers, i.e., an energy seller refuses to transfer the energy to customer who already paid money. | Malicious energy purchasers | Blockchain-based energy trading scheme to assure the verifiable fairness of energy transfer. | PBFT | Ethereum, Ethereum-Wallet and Geth | - | Computational cost |
| [136] | Goal to design the secure SGs against FDI attacks | FDI attack | Blockchain based incentive method to reward operators for uploading authentic data and penalize if data is missing or malicious. | Round robin | Hyperledger Fabric | Go language | Anomaly detection rate |
5.2. Artificial Intelligence Based Cybersecurity Techniques in Smart Grids
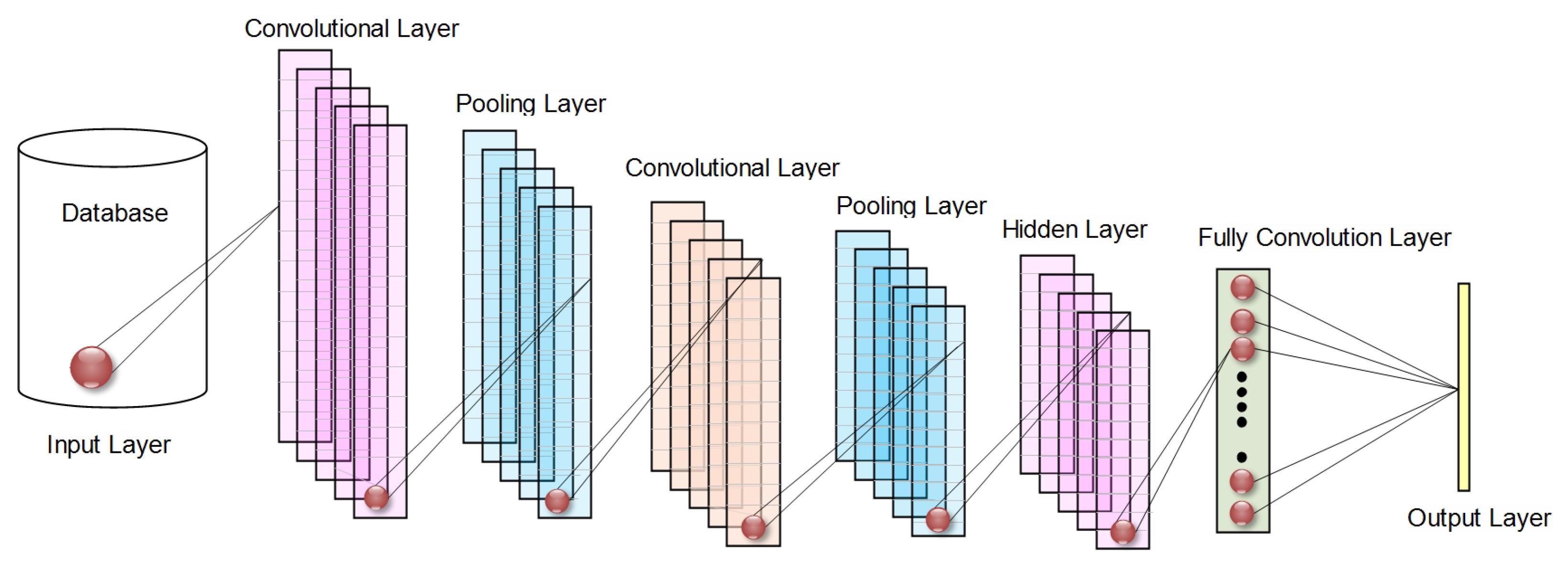
5.2.1. Deep Learning Based Cybersecurity Techniques in Smart Grids
| Reference | Type of Attack | Solution | DL Training Models | Dataset Generator | Implementation Tools | Performance Evaluation |
|---|---|---|---|---|---|---|
| [69] | FDIA | A two-level learner-based scheme with Kalman filter and recurrent neural network (KFRNN) is presented. | RNN | IEEE 14 Bus and IEEE 57 Bus | Matpower | MRSE, accuracy, F1 score, detection probability, false alarm rate |
| [140] | FDIA | A scheme based on the CNN and WT is proposed to detect attacks on the information received by the facility scheduler. Furthermore, hybrid neural network is presented to detect attacks on the output control signals. | WT, CNN and ANN | IEEE 30-bus | MATLAB | Identified as attacked, identified as normal, and detection accuracy |
| [141] | Inject, capture, replay, modify, drop, and delay attacks | Proposed and implemented the two-step deep learning model for cyberattack detection. | LSTM, RNN and GRU | IEEE 9-bus system | Testbed implementation | TPR, FNR, TNR, FPR, recall, precision, and F1-score |
| [142] | Energy theft | A combined CNN is used to detect abnormal behavior of the metering data. In addition, Paillier algorithm is deployed to protect the energy privacy. | CNN | Energy theft dataset from SGCC | Python, Numpy, Pandas, Keras and TensorFlow | Accuracy score |
| [143] | Malware, FDI and DR | An intrusion detection system with bidirectional RNN is presented for an IEEE 1815.1-based power system using CPS. | Bi-RNN | IEEE 1815.1 | TensorFlow | - |
| [144] | Anomalies (i.e.,electricity measurements) | Presented the DL-based MENSA (anoMaly dEtection aNd claSsificAtion) for anomalies and cyberattacks. | GAN and DBN | Four datasets from the SPEAR project | Tshark, REST API, MTU, CICFlowMeter, and Suricata | Average accuracy, TPR, FPR and F1 score |
| [145] | FDI attacks | A simplified neural network is presented to detect FDI attacks targeting transmission line overflows. | NN | IEEE 118-bus system | MATPOWER 7.0 | Accuracy, DR, precision, F1 score, FPR, ROC, and AUC |
| [146] | False readings in AMI | A general ensemble-based DL detector to enables the system operator to detect false readings in real time. | FFN, CNN, GRU, and LSTM | Smart Project Dataset | Python3, Numpy, Keras, Scikit-learn and Matplotlib | Accuracy, DR, FA, and HD |
| [147] | Electricity theft detection | DNN-based electricity theft detection method using time-domain features is presented. | DNN | SGCC dataset | - | TPR, Precision, F1 score, MCC, Accuracy and AUC ROC curve |
5.2.2. Machine Learning-Based Cybersecurity Techniques in Smart Grids
| Reference | Type of Attack | Solution | Feature Selection | ML Training Models | Dataset Generator | Implementation Tools | Performance Evaluation |
|---|---|---|---|---|---|---|---|
| [149] | FDIA | A data-driven ML-based scheme to detect stealthy FDIA on state estimation. | RFC | LR, DT, NB, NN, SVM, LOF, ISOF and EE | IEEE 14-bus system | MATPOWER | F1-Score, Accuracy, Precision, Sensitivity, FPR, Specificity, ROC AUC |
| [150] | FDIA | Analyze the historical data by concept drift and focus on the distribution change. The dimensionality reduction and statistical hypothesis testing are implemented. | PCA | KNN | IEEE 14-bus system | MATPOWER, MATLAB 2017 and Python 3 | F-measure and FPR |
| [151] | Stealthy cyber-attack (SCA) | KPCA technique is applied to transform the data into a lower-dimensional space. The data transformed by KPCA become the input for the ERT to detect SCA attacks. | KPCA | ERT | IEEE 57 and 118-bus systems | Matpower | Accuracy, ROC curves, and ROC AUC |
| [63] | DoS | A multi-class classification algorithm employed for anomaly detection in smart grid. | - | SVM and DT | IEEE 39-bus system | Testbed-based implementation | - |
| [152] | Pulse, ramp, relay-trip, and replay attack | Anomaly detection (AD) with supervised ML and model-based mitigation. With physics and signal entropy-based feature extraction increased the robustness and detection accuracy of ML model. | PCA | KNN and DT | 2-area of 4-machine | Testbed-based implementation | Accuracy |
| [153] | FDIA | A CPADS (cyber–physical anomaly detection system) developed with PMU measurements, network packet properties and ML algorithms. | Rules-based | VMD and DT | IEEE 39-bus system | Testbed-based implementation | Accuracy, AR, AP, and AF |
| [154] | FDIA | A novel FDIA detection model based on ensemble learning with optimal feature extraction and a FLGB ensemble classifier is employed. | JMIM | Ensemble classifier | Public Google power system cyber-attack dataset | - | Accuracy, FPR, ROC curve, and AUC |
| [155] | FDIA | A classifier is developed by aggregating a series of extreme learning machines (ELMs) to detect anomalies caused by FDIAs. | - | GRD, LHS and ensemble ELM | IEEE 14-bus and IEEE 57-bus | MATLAB R2014a | Classification accuracy |
6. Emerging Technologies and Future Research Directions
- Communication infrastructure in smart grid security: The network and communication model should be strengthened through advanced security measures which should be imposed during data collection and interchange phase. Furthermore, the vendors should follow the standards to make use of distribution devices in the communication phase to avoid interoperability issues. Consequently, the providers/vendors can build their protocols as open-source so that other vendors should anticipate in existing code and follow the same standard while manufacturing their own security tools. Being open-source, bug fixes and security vulnerability checks can also be easily verified and corrected as the community is taking part in the development and testing process. As a result of this collaboration, the security product will support the implementation of security tools by default in the communication network of the smart grid, which will ultimately enforce the standard security policies available on all devices that are participating in the grid communication network.
- High-level security algorithms to detect attacks: For implementing more enhanced security mechanisms, extra effort is required to target higher-level algorithms or data structures. As a result, the current state estimator algorithms cannot identify improper/defective data using the existing detection techniques available in the FDIAs, therefore high-level security data structures and algorithms are needed. For instance, apart from the existing bad data detection steps, if the SCADA system consists of other security modules, which are solely used to diagnose the false positive rates with the help of new regulation, it would better harden the security breaches by the attackers. Consequently, the additional work is required to enrich the impact analysis of FDIA on the distribution and use side, respectively. Apart from transmission systems, the distribution end can also be affected by showing false meter readings and fake topology information. Similarly, the meters installed at user premises that are used to transmit user consumption measures can also be hacked and manipulated. As a result, the load management and demand side management security measures should keenly be focused in the future.
- Federated learning in smart grids: Currently, federated learning (FL) is appealing as a privacy-preserving paradigm as it trained the AI models in a collaborative manner by inviting underlying devices. The privacy of each device is protected by localizing the training of model in comparison with ML where raw data are sent to the main server [158]. FL applications for the smart grid include electric load forecasting, energy demand prediction, and data privacy of a large power system. In addition, federated learning has been successfully implemented in various fields, i.e., health care, smart cities, transportation, finance, visual object detection, next-word prediction, and so on. Similarly, in [159] authors applied FL to share the private energy data of users in smart grid to achieve privacy and efficient communication. However, FL surface is also facing challenges and is prone to cybersecurity attacks mentioned by various researchers [160,161]. Before the implementation of FL into smart grid, it is necessary to consider robust security measures in the future.
- Blockchain technology for securing smart grids: As blockchain technology is still immature, case-by-case analysis of regulatory frameworks in terms of security is necessary. The electricity flowing through the wires to the home is similar as it passes by a burning coal or a solar array. Therefore, authenticating and tracing the energy source is a huge challenge. The embedded security features in blockchain technology can be emerged with the smart grids to enforce efficient and secure power transmission and management. As blockchain technology implements security using public/private key encryption methods with key access, everyone who tries to breach the system would encounter authentication through a secure credentials system in order to access system’s operational resources over the network. Consequently, the blockchain technology is an essential approach to make power grid safe if the access key codes are kept secure and safe. Overall, in order to prevent malicious attacks and make hacking more difficult for intruders, secure and efficient smart cities must be used as backbone. Furthermore, blockchain features such as the immutability and decentralization of data lead to permanent storage; hence, one must be careful when implementing smart contracts, as any malfunction or misconduct can be observed within the system [162].
- Big data integration in smart grids: The big data (BD) collected from smart grids is key information that could be extensively beneficial for different smart grid applications, such as load profiling and demand response. However, a security vulnerability in decision-making techniques may cause the unauthorized gain of full access to a customer’s data. On the other hand, a secure approach for decision making can provide enormous satisfaction to all the stakeholders, i.e., utility providers and consumers. The prospective research in big data is diverse when used in smart grids. Big data supports various solutions to the directional flow of data/information and analyzing and processing that information. Similarly, with the big data solutions, demand-side management has become a crucial activity for managing the stockholders in power systems. As a result, the learned behaviors of consumer actions and power consumption can enormously help to demand response activities on the customers’ end, which is also known as consumer behavior predictions.
- Smart grid security with AI and 5G: Major changes have been posted on smart grids through the latest technologies introduced by AI and 5G. Indeed, 5G and B5G (Beyond5G) technology would be a powerful tool to govern high-speed and reliable communication to perform real-time grid monitoring via Internet of things (IoT). However, with the advent of this technology, new challenges are ahead [163]. AI and Machine learning algorithms are promising options to intelligently operate the network with reliability, network efficiency, robustness goals, and can obtain the Quality of Service (QoS) demands as expected. Enriched historical data are required to train model in order to ensure the model’s accuracy and mitigate the over/under fitting issues of AI model in smart grid. Furthermore, it should provide the guarantee of controlling the decisions of AI models to align with the cybersecurity constraints of power systems.
- Cyber resilience of smart grid SoS: The entire smart grid network is considered as a system of systems (SoS) that integrates the legacies, new systems, and produces new goals beyond the distinct systematic competencies. Any breakdown occurred in the smart grid subsystem will have an impact on the entire smart grid system of systems. The implementation of a secure smart grid system of systems is now essential and a high research priority. To address this challenge, in the future extended Bayesian model can be developed, and utilize the analysis techniques, i.e., information theory, to improve the overall smart grid resilience system. Furthermore, the time-dependent dynamic Bayesian model can be integrated to observe the system performance and uniformity of the model with the passage of time [164].
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AAA | Authentication, Authorization, and Accounting |
| ANN | Artificial Neural Network |
| AUC | Area Under Curve |
| AMI | Advanced Metering Infrastructure |
| API | Application Programming Interface |
| ABOD | Angle-based Outlier Detector |
| ARP | Address Resolution Protocol |
| CPS | Cyber–Physical System |
| CVE | Common Vulnerabilities and Exposures |
| CVSS | Common Vulnerability Scoring System |
| CNN | Convolutional Neural Network |
| CIA | Confidentiality, Integrity, and Availability |
| COSEM | Companion Specification for Energy Metering |
| CRM | Customer Relationship Management |
| DNN | Deep Neural Network |
| DMZ | DeMilitarized Zone |
| DBN | Deep Belief Networks |
| DER | Distributed Energy Resources |
| DR | Detection rate |
| FA | False Alarm |
| DNP3 | Distributed Network Protocol 3 |
| DLMS | Device Language Message Specification |
| DWT | Discrete wavelet transform |
| DT | Decision Tree |
| DBSCAN | Density-Based Spatial Clustering of Applications with Noise |
| ERT | Extremely Randomized Trees |
| EE | Elliptic Envelope |
| ERP | Enterprise Resource Planning |
| FTP | File Transfer Protocol |
| FFN | Feed-Forward Neural Network |
| FNR | False Negative Rate |
| FPR | False Positive Rate |
| FLGB | Focal-Loss-lightgbm |
| GRU | Gated Recurrent Unit Network |
| GAN | Generative Adversarial Networks |
| GRD | Gaussian Random Distribution |
| HD | Highest difference |
| HBOS | Histogram-base Outlier Detection |
| HTTPS | Hyper Text Transfer Protocol over SecureSocket Layer |
| HMI | Human Machine Interface |
| IDE | Integrated Dynamic Environment |
| IF | Isolation Forest |
| ICCP | Inter Control Center Protocol |
| ICMP | Internet Control Message Protocol |
| IEC | International Electrotechnical Commission |
| IED | Intelligent Electronic Device |
| KNN | K-Nearest Neighbor |
| KPCA | Kernel Principal Component Analysis |
| JMIM | Joint Mutual Information Maximization |
| LSTM | Long Short-Term Memory Network |
| LR | Logistic Regression |
| LOF | Local Outlier Factor |
| LHS | Latin Hypercube Sampling |
| LSCP | Locally Selective Combination |
| MAE | Mean Absolute Error |
| MRSE | Mean Relative Square Error |
| MTU | Master Terminal Unit |
| MCC | Matthews Correlation Coefficient |
| NB | Naive Bayes |
| NN | Neural Network |
| NTP | Network Time Protocol |
| NVD | National Vulnerability Database |
| OT | Operational Technology |
| PoA | Proof-of-Authority |
| PBFT | Practical Byzantine Fault Tolerance |
| PCA | Principal Component Analysis |
| RNN | Recurrent Neural Networks |
| RMSE | Root Mean Square Error |
| RNN | Recurrent Neural Networks |
| REST | Representational State Transfer |
| ROC | Receiver Operator Characteristic |
| RFC | Random forest classifier |
| RTU | Remote Terminal Unit |
| SGCC | State Grid Corporation of China |
| SPEAR | Secure and PrivatE smArt gRid |
| SCADA | Supervisory Control And Data Acquisition |
| SIEM | Security Information and Event Management |
| SVM | Support Vector Machine |
| TP | True Positive |
| TNR | True Negative Rate |
| TASE.2 | Telecontrol Application Service Element 2 |
| VMD | Variational Mode Decomposition |
| VULDB | Vulnerability Database |
References
- GlobalNewswire. The $39.9 Billion Worldwide Substation Automation Industry Is Expected to Reach $54.2 Billion by 2026. Available online: https://www.globenewswire.com/news-release/2021/06/04/2241918/28124/en/The-39-9-Billion-Worldwide-Substation-Automation-Industry-is-Expected-to-Reach-54-2-Billion-by-2026.html (accessed on 22 January 2022).
- Nations, U. What Is Renewable Energy? Available online: https://www.un.org/en/climatechange/what-is-renewable-energy (accessed on 1 August 2022).
- Solaun, K.; Cerdá, E. Climate change impacts on renewable energy generation. A review of quantitative projections. Renew. Sustain. Energy Rev. 2019, 116, 109415. [Google Scholar] [CrossRef]
- Abrahamsen, F.E.; Ai, Y.; Cheffena, M. Communication Technologies for Smart Grid: A Comprehensive Survey. Sensors 2021, 21, 8087. [Google Scholar] [CrossRef] [PubMed]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Otuoze, A.O.; Mustafa, M.W.; Larik, R.M. Smart grids security challenges: Classification by sources of threats. J. Electr. Syst. Inf. Technol. 2018, 5, 468–483. [Google Scholar] [CrossRef]
- NISTIR. Guidelines for Smart Grid Cybersecurity. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2014/NIST.IR.7628r1.pdf (accessed on 22 January 2022).
- Tufail, S.; Parvez, I.; Batool, S.; Sarwat, A. A Survey on Cybersecurity Challenges, Detection, and Mitigation Techniques for the Smart Grid. Energies 2021, 14, 5894. [Google Scholar] [CrossRef]
- Rawat, D.B.; Bajracharya, C. Cyber security for smart grid systems: Status, challenges and perspectives. In Proceedings of the SoutheastCon 2015, Fort Lauderdale, FL, USA, 9–12 April 2015. [Google Scholar] [CrossRef]
- Mrabet, Z.E.; Kaabouch, N.; Ghazi, H.E.; Ghazi, H.E. Cyber-security in smart grid: Survey and challenges. Comput. Electr. Eng. 2018, 67, 469–482. [Google Scholar] [CrossRef]
- SmartGrid.gov. The Smart Grid. Available online: https://www.smartgrid.gov/the_smart_grid/smart_grid.html (accessed on 22 January 2022).
- NIST. National Vulnerability Database. Available online: https://nvd.nist.gov/ (accessed on 5 August 2022).
- U.S.D. of Energy. “GRID 2030” A National Vision Forelectricity’s Second 100 Years. Available online: https://www.energy.gov/sites/default/files/oeprod/DocumentsandMedia/Electric_Vision_Document.pdf (accessed on 22 January 2022).
- Office of Electricity. The Smart Grid: An Introduction. Available online: https://www.energy.gov/oe/downloads/smart-grid-introduction-0 (accessed on 22 January 2022).
- Hahn, A. Operational Technology and Information Technology in Industrial Control Systems. In Advances in Information Security; Springer International Publishing: Cham, Switzerland, 2016; pp. 51–68. [Google Scholar] [CrossRef]
- Zhang, Z.; Yin, R.; Ning, H. Internet of Brain, Thought, Thinking, and Creation. Chin. J. Electron. 2022, 31, 1–18. [Google Scholar]
- Gaushell, D.J.; Darlington, H.T. Supervisory control and data acquisition. Proc. IEEE 1987, 75, 1645–1658. [Google Scholar] [CrossRef]
- Zhang, Z.; Ning, H.; Shi, F.; Farha, F.; Xu, Y.; Xu, J.; Zhang, F.; Choo, K.K.R. Artificial intelligence in cyber security: Research advances, challenges, and opportunities. Artif. Intell. Rev. 55 2021, 55, 1029–1053. [Google Scholar] [CrossRef]
- Upadhyay, D.; Sampalli, S. SCADA (Supervisory Control and Data Acquisition) systems: Vulnerability assessment and security recommendations. Comput. Secur. 2020, 89, 101666. [Google Scholar] [CrossRef]
- Ning, H.; Zhang, Z.; Daneshmand, M. PhiNet of Things: Things Connected by Physical Space From the Natural View. IEEE Internet Things J. 2021, 8, 8680–8692. [Google Scholar] [CrossRef]
- Ning, H.; Ye, X.; Bouras, M.A.; Wei, D.; Daneshmand, M. General Cyberspace: Cyberspace and Cyber-Enabled Spaces. IEEE Internet Things J. 2018, 5, 1843–1856. [Google Scholar] [CrossRef]
- Huang, Y.; Lu, Y.; Wang, F.; Fan, X.; Liu, J.; Leung, V.C. An Edge Computing Framework for Real-Time Monitoring in Smart Grid. In Proceedings of the 2018 IEEE International Conference on Industrial Internet (ICII), Seattle, WA, USA, 21–23 October 2018. [Google Scholar] [CrossRef]
- Bui, N.; Castellani, A.; Casari, P.; Zorzi, M. The internet of energy: A web-enabled smart grid system. IEEE Netw. 2012, 26, 39–45. [Google Scholar] [CrossRef]
- Kafle, Y.R.; Mahmud, K.; Morsalin, S.; Town, G.E. Towards an internet of energy. In Proceedings of the 2016 IEEE International Conference on Power System Technology (POWERCON), Wollongong, NSW, Australia, 28 September–1 October 2016. [Google Scholar] [CrossRef]
- Piggin, R. Industrial systems: Cyber-security’s new battlefront. Eng. Technol. 2014, 9, 70–74. [Google Scholar] [CrossRef]
- Anand, P.; Singh, Y.; Selwal, A.; Singh, P.K.; Felseghi, R.A.; Raboaca, M.S. IoVT: Internet of Vulnerable Things? Threat Architecture, Attack Surfaces, and Vulnerabilities in Internet of Things and Its Applications towards Smart Grids. Energies 2020, 13, 4813. [Google Scholar] [CrossRef]
- Xie, J.; Stefanov, A.; Liu, C.C. Physical and Cybersecurity in a Smart Grid Environment. In Advances in Energy Systems: The Large-Scale Renewable Energy Integration Challenge; Wiley: Hoboken, NJ, USA, 2019; pp. 85–109. [Google Scholar] [CrossRef]
- Mathas, C.M.; Vassilakis, C.; Kolokotronis, N.; Zarakovitis, C.C.; Kourtis, M.A. On the Design of IoT Security: Analysis of Software Vulnerabilities for Smart Grids. Energies 2021, 14, 2818. [Google Scholar] [CrossRef]
- Vuldb. Vulnerability Database. Available online: https://vuldb.com/ (accessed on 5 August 2022).
- Details, C. Common Vulnerabilities and Exposures. Available online: https://www.cvedetails.com/ (accessed on 5 August 2022).
- O’Driscoll, A. Cyber Security Vulnerability Statistics and Facts of 2022. Available online: https://www.comparitech.com/blog/information-security/cybersecurity-vulnerability-statistics/ (accessed on 22 January 2022).
- First Common Vulnerability Scoring System SIG. Available online: https://www.first.org/cvss/ (accessed on 5 August 2022).
- Lázaro, J.; Astarloa, A.; Rodríguez, M.; Bidarte, U.; Jiménez, J. A Survey on Vulnerabilities and Countermeasures in the Communications of the Smart Grid. Electronics 2021, 10, 1881. [Google Scholar] [CrossRef]
- Xu, Y.; Yang, Y.; Li, T.; Ju, J.; Wang, Q. Review on cyber vulnerabilities of communication protocols in industrial control systems. In Proceedings of the 2017 IEEE Conference on Energy Internet and Energy System Integration (EI2), Beijing, China, 26–28 November 2017. [Google Scholar] [CrossRef]
- ENISA. Smart Grid Security—Annex II. Security Aspects of the Smart Grid. Available online: https://www.enisa.europa.eu/topics/critical-information-infrastructures-and-services/smart-grids/smart-grids-and-smart-metering/ENISAAnnexII-SecurityAspectsofSmartGrid.pdf (accessed on 5 August 2022).
- ENISA. ENISA Smart Grid Security Recommendations. Available online: https://www.enisa.europa.eu/publications/ENISA-smart-grid-security-recommendations. (accessed on 5 August 2022).
- Krause, T.; Ernst, R.; Klaer, B.; Hacker, I.; Henze, M. Cybersecurity in Power Grids: Challenges and Opportunities. Sensors 2021, 21, 6225. [Google Scholar] [CrossRef]
- Alonso, M.; Turanzas, J.; Amaris, H.; Ledo, A.T. Cyber-Physical Vulnerability Assessment in Smart Grids Based on Multilayer Complex Networks. Sensors 2021, 21, 5826. [Google Scholar] [CrossRef]
- Borenius, S.; Gopalakrishnan, P.; Tjernberg, L.B.; Kantola, R. Expert-Guided Security Risk Assessment of Evolving Power Grids. Energies 2022, 15, 3237. [Google Scholar] [CrossRef]
- Cartwright, J. Europe’s Power Grids Readied against Cyber Attack. Available online: https://ec.europa.eu/research-and-innovation/en/horizon-magazine/europes-power-grids-readied-against-cyber-attack (accessed on 22 January 2022).
- Wikipedia. Stuxnet. Available online: https://en.wikipedia.org/wiki/Stuxnet#:~:text=Stuxnet%20reportedly%20ruined%20almost%20one,1%2C000%20machines%20to%20physically%20degrade (accessed on 22 January 2022).
- NERC. September 2011 Southwest Blackout Event. Available online: https://www.nerc.com/pa/rrm/ea/Pages/September-2011-Southwest-Blackout-Event.aspx#:~:text=OntheafternoonofSeptember,,andBajaCalifornia,Mexico (accessed on 22 January 2022).
- Ju-min Park, M.C. South Korea Blames North Korea for December Hack on Nuclear Operator. Available online: https://www.reuters.com/article/us-nuclear-southkorea-northkorea-idUSKBN0MD0GR20150317 (accessed on 22 January 2022).
- Khan, R.; Maynard, P.; McLaughlin, K.; Laverty, D.; Sezer, S. Threat analysis of blackenergy malware for synchrophasor based real-time control and monitoring in smart grid. In Proceedings of the 4th International Symposium for ICS & SCADA Cyber Security Research 2016, Belfast, UK, 23–25 August 2016; pp. 53–63. [Google Scholar]
- Wei, L.; Gao, D.; Luo, C. False Data Injection Attacks Detection with Deep Belief Networks in Smart Grid. In Proceedings of the 2018 Chinese Automation Congress (CAC), Xi’an, China, 30 November–2 December 2018. [Google Scholar] [CrossRef]
- Androjna, A.; Twrdy, E. Cyber threats to maritime critical infrastructure. In Cyber Terrorism and Extremism as Threat to Critical Infrastructure Protection; Ministry of Defence Republic of Slovenia: Ljubljana, Slovenia, 2020. [Google Scholar]
- Detwiler, B. Ukraine Cybersecurity Conference Highlighted New Threats a Week before the Petya Ransomware Attack. Available online: https://www.techrepublic.com/article/ukraine-cybersecurity-conference-highlighted-new-threats-a-week-before-the-petya-ransomware-attack/ (accessed on 22 January 2022).
- News, C.H. Hackers Hit French Firm Ingerop Stealing 65 GB Data Relating to Nuclear Power Plants. Available online: https://cyware.com/news/hackers-hit-french-firm-ingerop-stealing-65-gb-data-relating-to-nuclear-power-plants-f193b9ba/ (accessed on 22 January 2022).
- Harper, C. First Ever DoS Cyber-Attack on a US Power Grid Detailed In Startling Report. Available online: https://hothardware.com/news/dos-us-power-grid (accessed on 22 January 2022).
- News, B. Ransomware Hits Johannesburg Electricity Supply. Available online: https://www.bbc.com/news/technology-49125853 (accessed on 22 January 2022).
- Winder, D. Bitcoin Hackers Charged as Nuclear Power Plant Security Compromised. Available online: https://www.forbes.com/sites/daveywinder/2019/08/23/bitcoin-hackers-charged-as-nuclear-power-plant-security-compromised/?sh=407f199e2735 (accessed on 22 January 2022).
- He, S.; Zhou, Y.; Lv, X.; Chen, W. Detection Method for Tolerable False Data Injection Attack Based on Deep Learning Framework. In Proceedings of the 2020 Chinese Automation Congress (CAC), Shanghai, China, 6–8 November 2020; pp. 6717–6721. [Google Scholar]
- Toulas, B. Energias de Portugal (EDP) Fell Victim to the “Ragnar Locker” Ransomware. Available online: https://www.technadu.com/energias-de-portugal-edp-fell-victim-to-ragnar-locker-ransomware/98913/ (accessed on 22 January 2022).
- BleepingComputer. Power Company Enel Group Suffers Snake Ransomware Attack. Available online: https://www.bleepingcomputer.com/news/security/power-company-enel-group-suffers-snake-ransomware-attack/ (accessed on 22 January 2022).
- BleepingComputer. Netwalker Ransomware Hits Pakistan’s Largest Private Power Utility. Available online: https://www.bleepingcomputer.com/news/security/netwalker-ransomware-hits-pakistans-largest-private-power-utility/ (accessed on 22 January 2022).
- Esposito, D.; Gimon, E. The Texas Big Freeze: How Much Were Markets to Blame for Widespread Outages? Available online: https://www.utilitydive.com/news/the-texas-big-freeze-how-much-were-markets-to-blame-for-widespread-outages/601158/ (accessed on 22 January 2022).
- IronNet. Industroyer2 Malware Targeting Ukrainian Energy Company. Available online: https://www.ironnet.com/blog/industroyer2-malware-targeting-ukrainian-energy-company (accessed on 22 January 2022).
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 1–33. [Google Scholar] [CrossRef]
- Wang, Q.; Tai, W.; Tang, Y.; Ni, M. A review on false data injection attack toward cyber-physical power system. Acta Autom. Sin. 2019, 45, 7283. [Google Scholar]
- Che, L.; Liu, X.; Li, Z.; Wen, Y. False Data Injection Attacks Induced Sequential Outages in Power Systems. IEEE Trans. Power Syst. 2019, 34, 1513–1523. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z.; Liu, X.; Li, Z. Masking Transmission Line Outages via False Data Injection Attacks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1592–1602. [Google Scholar] [CrossRef]
- Tan, R.; Nguyen, H.H.; Foo, E.Y.S.; Dong, X.; Yau, D.K.Y.; Kalbarczyk, Z.; Iyer, R.K.; Gooi, H.B. Optimal False Data Injection Attack against Automatic Generation Control in Power Grids. In Proceedings of the 2016 ACM/IEEE 7th International Conference on Cyber-Physical Systems (ICCPS), Vienna, Austria, 11–14 April 2016. [Google Scholar] [CrossRef]
- Wang, S.; Bi, S.; Zhang, Y.J.A. Locational Detection of the False Data Injection Attack in a Smart Grid: A Multilabel Classification Approach. IEEE Internet Things J. 2020, 7, 8218–8227. [Google Scholar] [CrossRef]
- Prasanna Srinivasan, V.; Balasubadra, K.; Saravanan, K.; Arjun, V.S.; Malarkodi, S. Multi Label Deep Learning classification approach for False Data Injection Attacks in Smart Grid. KSII Trans. Internet Inf. Syst. 2021, 15, 2168–2187. [Google Scholar]
- Singh, S.K.; Khanna, K.; Bose, R.; Panigrahi, B.K.; Joshi, A. Joint-Transformation-Based Detection of False Data Injection Attacks in Smart Grid. IEEE Trans. Ind. Inform. 2018, 14, 89–97. [Google Scholar] [CrossRef]
- Huang, K.; Xiang, Z.; Deng, W.; Yang, C.; Wang, Z. False Data Injection Attacks Detection in Smart Grid: A Structural Sparse Matrix Separation Method. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2545–2558. [Google Scholar] [CrossRef]
- Tang, B.; Yan, J.; Kay, S.; He, H. Detection of false data injection attacks in smart grid under colored Gaussian noise. In Proceedings of the 2016 IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA, 17–19 October 2016. [Google Scholar] [CrossRef]
- Zhang, G.; Li, J.; Bamisile, O.; Cai, D.; Hu, W.; Huang, Q. Spatio-Temporal Correlation-Based False Data Injection Attack Detection Using Deep Convolutional Neural Network. IEEE Trans. Smart Grid 2022, 13, 750–761. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, Z.; Ma, J.; Jin, Q. KFRNN: An Effective False Data Injection Attack Detection in Smart Grid Based on Kalman Filter and Recurrent Neural Network. IEEE Internet Things J. 2021, 9, 6893–6904. [Google Scholar] [CrossRef]
- Dehghani, M.; Ghiasi, M.; Niknam, T.; Kavousi-Fard, A.; Shasadeghi, M.; Ghadimi, N.; Taghizadeh-Hesary, F. Blockchain-Based Securing of Data Exchange in a Power Transmission System Considering Congestion Management and Social Welfare. Sustainability 2020, 13, 90. [Google Scholar] [CrossRef]
- Yi, P.; Zhu, T.; Zhang, Q.; Wu, Y.; Li, J. A denial of service attack in advanced metering infrastructure network. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014. [Google Scholar] [CrossRef]
- Guo, Y.; Ten, C.W.; Hu, S.; Weaver, W.W. Modeling distributed denial of service attack in advanced metering infrastructure. In Proceedings of the 2015 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 18–20 February 2015. [Google Scholar] [CrossRef]
- Taft, J. Assessment of Existing Synchrophasor Networks. Available online: https://www.naspi.org/sites/default/files/reference_documents/pnnl_27557_assess_existing_synchrophasor_net.pdf (accessed on 22 January 2022).
- Attia, M.; Senouci, S.M.; Sedjelmaci, H.; Aglzim, E.H.; Chrenko, D. An efficient Intrusion Detection System against cyber-physical attacks in the smart grid. Comput. Electr. Eng. 2018, 68, 499–512. [Google Scholar] [CrossRef]
- Wang, K.; Du, M.; Maharjan, S.; Sun, Y. Strategic Honeypot Game Model for Distributed Denial of Service Attacks in the Smart Grid. IEEE Trans. Smart Grid 2017, 8, 2474–2482. [Google Scholar] [CrossRef]
- Zhe, W.; Wei, C.; Chunlin, L. DoS attack detection model of smart grid based on machine learning method. In Proceedings of the 2020 IEEE International Conference on Power, Intelligent Computing and Systems (ICPICS), Shenyang, China, 28–30 July 2020. [Google Scholar] [CrossRef]
- Hasnat, M.A.; Rahnamay-Naeini, M. A Data-Driven Dynamic State Estimation for Smart Grids under DoS Attack using State Correlations. In Proceedings of the 2019 North American Power Symposium (NAPS), Wichita, KS, USA, 13–15 October 2019. [Google Scholar] [CrossRef]
- Mahmood, H.; Mahmood, D.; Shaheen, Q.; Akhtar, R.; Changda, W. S-DPS: An SDN-Based DDoS Protection System for Smart Grids. Secur. Commun. Netw. 2021, 2021, 6629098. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Maglaras, L. DeepCoin: A Novel Deep Learning and Blockchain-Based Energy Exchange Framework for Smart Grids. IEEE Trans. Eng. Manag. 2020, 67, 1285–1297. [Google Scholar] [CrossRef]
- Radoglou-Grammatikis, P.I.; Sarigiannidis, P.G. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. IEEE Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Kim, J.; Tong, L.; Thomas, R.J. Data Framing Attack on State Estimation. IEEE J. Sel. Areas Commun. 2014, 32, 1460–1470. [Google Scholar] [CrossRef]
- Wang, J.; Hui, L.C.K.; Yiu, S.M. Data Framing Attacks against Nonlinear State Estimation in Smart Grid. In Proceedings of the 2015 IEEE Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015. [Google Scholar] [CrossRef]
- Jiao, W.; Li, V.O.K. Support Vector Machine Detection of Data Framing Attack in Smart Grid. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018. [Google Scholar] [CrossRef]
- Drias, Z.; Serhrouchni, A.; Vogel, O. Taxonomy of attacks on industrial control protocols. In Proceedings of the 2015 International Conference on Protocol Engineering (ICPE) and International Conference on New Technologies of Distributed Systems (NTDS), Paris, France, 22–24 July 2015. [Google Scholar] [CrossRef]
- Kayastha, N.; Niyato, D.; Hossain, E.; Han, Z. Smart grid sensor data collection, communication, and networking: A tutorial. Wirel. Commun. Mob. Comput. 2012, 14, 1055–1087. [Google Scholar] [CrossRef]
- Crane, C. 80 Eye-Opening Cyber Security Statistics for 2019. Available online: https://www.thesslstore.com/blog/80-eye-opening-cyber-security-statistics-for-2019/ (accessed on 22 January 2022).
- Deb, D.; Chakraborty, S.R.; Lagineni, M.; Singh, K. Security Analysis of MITM Attack on SCADA Network. In Communications in Computer and Information Science; Springer: Singapore, 2020; pp. 501–512. [Google Scholar] [CrossRef]
- Swales, A. Open modbus/tcp specification. Schneider Electr. 1999, 29, 3–19. [Google Scholar]
- Konstantinou, C.; Sazos, M.; Maniatakos, M. FLEP-SGS2: A Flexible and Low-cost Evaluation Platform for Smart Grid Systems Security. In Proceedings of the 2019 IEEE Power & Energy Society Innovative Smart Grid Technologies Conference (ISGT), Washington, DC, USA, 18–21 February 2019. [Google Scholar] [CrossRef]
- Kulkarni, S.; Rahul, R.K.; Shreyas, R.; Nagasundari, S.; Honnavalli, P.B. MITM Intrusion Analysis for Advanced Metering Infrastructure Communication in a Smart Grid Environment. In Communications in Computer and Information Science; Springer International Publishing: Cham, Switzerland, 2020; pp. 256–267. [Google Scholar] [CrossRef]
- Varmaziari, H.; Dehghani, M. Cyber Attack Detection in PMU Networks Exploiting the Combination of Machine Learning and State Estimation-Based Methods. In Proceedings of the 2021 11th Smart Grid Conference (SGC), Tabriz, Iran, 7–9 December 2021. [Google Scholar] [CrossRef]
- Aruna Gawade, N.S. MITM Attack Prevention Using PUF Authentication in Smart Grid. Int. J. Adv. Sci. Technol. 2020, 29, 12321–12331. [Google Scholar]
- Wlazlo, P.; Sahu, A.; Mao, Z.; Huang, H.; Goulart, A.E.; Davis, K.R.; Zonouz, S.A. Man-in-The-Middle Attacks and Defense in a Power System Cyber-Physical Testbed. arXiv 2021, arXiv:2102.11455. [Google Scholar]
- Mohsenian-Rad, A.H.; Leon-Garcia, A. Distributed Internet-Based Load Altering Attacks against Smart Power Grids. IEEE Trans. Smart Grid 2011, 2, 667–674. [Google Scholar] [CrossRef]
- Amini, S.; Pasqualetti, F.; Mohsenian-Rad, H. Dynamic Load Altering Attacks Against Power System Stability: Attack Models and Protection Schemes. IEEE Trans. Smart Grid 2018, 9, 2862–2872. [Google Scholar] [CrossRef]
- Amini, S.; Pasqualetti, F.; Abbaszadeh, M.; Mohsenian-Rad, H. Hierarchical Location Identification of Destabilizing Faults and Attacks in Power Systems: A Frequency-Domain Approach. IEEE Trans. Smart Grid 2019, 10, 2036–2045. [Google Scholar] [CrossRef]
- Gobmaier, T. Measuring Devices for Frequency Measurement. Available online: https://www.mainsfrequency.com/meter.htm (accessed on 5 March 2022).
- Zhao, C.; Topcu, U.; Low, S.H. Optimal Load Control via Frequency Measurement and Neighborhood Area Communication. IEEE Trans. Power Syst. 2013, 28, 3576–3587. [Google Scholar] [CrossRef]
- Huang, B.; Cardenas, A.A.; Baldick, R. Not Everything is Dark and Gloomy: Power Grid Protections Against IoT Demand Attacks. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; USENIX Association: Santa Clara, CA, USA, 2019; pp. 1115–1132. [Google Scholar]
- Su, Q.; Li, S.; Gao, Y.; Huang, X.; Li, J. Observer-based detection and reconstruction of dynamic load altering attack in smart grid. J. Frankl. Inst. 2021, 358, 4013–4027. [Google Scholar] [CrossRef]
- Ma, Q.; Xu, Z.; Wang, W.; Lin, L.; Ren, T.; Yang, S.; Li, J. Dynamic load-altering attack detection based on adaptive fading Kalman filter in power systems. Glob. Energy Interconnect. 2021, 4, 184–192. [Google Scholar] [CrossRef]
- Chen, C.; Cui, M.; Fang, X.; Ren, B.; Chen, Y. Load altering attack-tolerant defense strategy for load frequency control system. Appl. Energy 2020, 280, 116015. [Google Scholar] [CrossRef]
- Chakrabarty, S.; Sikdar, B. Detection of Malicious Command Injection Attacks on Phase Shifter Control in Power Systems. IEEE Trans. Power Syst. 2021, 36, 271–280. [Google Scholar] [CrossRef]
- Lin, H.; Kalbarczyk, Z.; Iyer, R.K. Impact of Malicious SCADA Commands on Power Grids’ Dynamic Responses. In Proceedings of the 2018 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aalborg, Denmark, 29–31 October 2018. [Google Scholar] [CrossRef]
- Chakrabarty, S.; Sikdar, B. Detection of Hidden Transformer Tap Change Command Attacks in Transmission Networks. IEEE Trans. Smart Grid 2020, 11, 5161–5173. [Google Scholar] [CrossRef]
- Wang, H.; Li, J.; Zhang, T.; Ying, H.; Han, J.; Ji, X. Malicious Code Detection on Smart Meters -A Side-Channel Based Approach. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019. [Google Scholar] [CrossRef]
- Yuan, Y.; Li, Z.; Ren, K. Quantitative Analysis of Load Redistribution Attacks in Power Systems. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1731–1738. [Google Scholar] [CrossRef]
- Pinceti, A.; Sankar, L.; Kosut, O. Detection and Localization of Load Redistribution Attacks on Large-Scale Systems. J. Mod. Power Syst. Clean Energy 2021, 10, 361–370. [Google Scholar] [CrossRef]
- Pinceti, A.; Sankar, L.; Kosut, O. Load Redistribution Attack Detection using Machine Learning: A Data-Driven Approach. In Proceedings of the 2018 IEEE Power & Energy Society General Meeting (PESGM), Portland, OR, USA, 5–10 August 2018. [Google Scholar] [CrossRef]
- Chu, Z.; Kosut, O.; Sankar, L. Detecting load redistribution attacks via support vector models. IET Smart Grid 2020, 3, 551–560. [Google Scholar] [CrossRef]
- PJM. Load Forecast Development Process. Available online: https://www.pjm.com/planning/resource-adequacy-planning/load-forecast-dev-process.aspx (accessed on 5 February 2022).
- Zhang, J.; Sankar, L. Implementation of unobservable state-preserving topology attacks. In Proceedings of the 2015 North American Power Symposium (NAPS), Charlotte, NC, USA, 4–6 October 2015. [Google Scholar] [CrossRef]
- Zhang, J.; Sankar, L. Physical System Consequences of Unobservable State-and-Topology Cyber-Physical Attacks. IEEE Trans. Smart Grid 2016, 7, 2016–2025. [Google Scholar] [CrossRef]
- Kim, J.; Tong, L. On Topology Attack of a Smart Grid: Undetectable Attacks and Countermeasures. IEEE J. Sel. Areas Commun. 2013, 31, 1294–1305. [Google Scholar] [CrossRef]
- Li, Z.; Shahidehpour, M.; Alabdulwahab, A.; Abusorrah, A. Bilevel Model for Analyzing Coordinated Cyber-Physical Attacks on Power Systems. IEEE Trans. Smart Grid 2016, 7, 2260–2272. [Google Scholar] [CrossRef]
- Knapp, E.D.; Samani, R. Applied Cyber Security and the Smart Grid: Implementing Security Controls into the Modern Power Infrastructure; Elsevier: Amsterdam, The Netherlands, 2013. [Google Scholar] [CrossRef]
- Mo, Y.; Weerakkody, S.; Sinopoli, B. Physical authentication of control systems: Designing watermarked control inputs to detect counterfeit sensor outputs. IEEE Control Syst. Mag. 2015, 35, 93–109. [Google Scholar] [CrossRef]
- Mo, Y.; Chabukswar, R.; Sinopoli, B. Detecting Integrity Attacks on SCADA Systems. IEEE Trans. Control. Syst. Technol. 2014, 22, 1396–1407. [Google Scholar] [CrossRef]
- Irita, T.; Namerikawa, T. Detection of replay attack on smart grid with code signal and bargaining game. In Proceedings of the 2017 American Control Conference (ACC), Seattle, WA, USA, 24–26 May 2017. [Google Scholar] [CrossRef]
- Ma, M.; Zhou, P.; Du, D.; Peng, C.; Fei, M.; AlBuflasa, H.M. Detecting Replay Attacks in Power Systems: A Data-Driven Approach. In Communications in Computer and Information Science; Springer: Singapore, 2017; pp. 450–457. [Google Scholar] [CrossRef]
- Abdelwahab, A.; Lucia, W.; Youssef, A. Set-Theoretic Control for Active Detection of Replay Attacks with Applications to Smart Grid. In Proceedings of the 2020 IEEE Conference on Control Technology and Applications (CCTA), Montreal, QC, Canada, 24–26 August 2020. [Google Scholar] [CrossRef]
- Hossain-McKenzie, S.; Chavez, A.; Jacobs, N.; Jones, C.B.; Summers, A.; Wright, B. Proactive Intrusion Detection and Mitigation System: Case Study on Packet Replay Attacks in Distributed Energy Resource Systems. In Proceedings of the 2021 IEEE Power and Energy Conference at Illinois (PECI), Urbana, IL, USA, 1–2 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- kaspersky. BlackEnergy APT Attacks in Ukraine. Available online: https://www.kaspersky.com/resource-center/threats/blackenergy (accessed on 5 February 2022).
- Denning, D.E. Stuxnet: What Has Changed? Future Internet 2012, 4, 672–687. [Google Scholar] [CrossRef]
- Zhang, Z.; Gong, S.; Dimitrovski, A.D.; Li, H. Time Synchronization Attack in Smart Grid: Impact and Analysis. IEEE Trans. Smart Grid 2013, 4, 87–98. [Google Scholar] [CrossRef]
- Park, G.; Shim, H.; Lee, C.; Eun, Y.; Johansson, K.H. When adversary encounters uncertain cyber-physical systems: Robust zero-dynamics attack with disclosure resources. In Proceedings of the 2016 IEEE 55th Conference on Decision and Control (CDC), Las Vegas, NV, USA, 12–14 December 2016. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, J.; Liu, J. Attack Identification and Correction for PMU GPS Spoofing in Unbalanced Distribution Systems. IEEE Trans. Smart Grid 2020, 11, 762–773. [Google Scholar] [CrossRef]
- Li, Y.; Yang, S. GPS Spoofing attack detection in smart grids based on improved CapsNet. China Commun. 2021, 18, 174–186. [Google Scholar] [CrossRef]
- Kumari, A.; Patel, M.M.; Shukla, A.; Tanwar, S.; Kumar, N.; Rodrigues, J.J.P.C. ArMor: A Data Analytics Scheme to identify malicious behaviors on Blockchain-based Smart Grid System. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020. [Google Scholar] [CrossRef]
- Houda, Z.A.E.; Hafid, A.; Khoukhi, L. Blockchain Meets AMI: Towards Secure Advanced Metering Infrastructures. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020. [Google Scholar] [CrossRef]
- Bari, A.; Jiang, J.; Saad, W.; Jaekel, A. Challenges in the Smart Grid Applications: An Overview. Int. J. Distrib. Sens. Netw. 2014, 10, 974682. [Google Scholar] [CrossRef]
- Ramanan, P.; Li, D.; Gebraeel, N. Blockchain-Based Decentralized Replay Attack Detection for Large-Scale Power Systems. IEEE Trans. Syst. Man Cybern. Syst. 2022, 52, 4727–4739. [Google Scholar] [CrossRef]
- Samy, S.; Banawan, K.; Azab, M.; Rizk, M. Smart Blockchain-based Control-data Protection Framework for Trustworthy Smart Grid Operations. In Proceedings of the 2021 IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 27–30 October 2021; pp. 0963–0969. [Google Scholar]
- Samuel, O.; Javaid, N. GarliChain: A privacy preserving system for smart grid consumers using blockchain. Int. J. Energy Res. 2021, 1–17. [Google Scholar] [CrossRef]
- Li, M.; Hu, D.; Lal, C.; Conti, M.; Zhang, Z. Blockchain-Enabled Secure Energy Trading With Verifiable Fairness in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2020, 16, 6564–6574. [Google Scholar] [CrossRef]
- Reijsbergen, D.; Maw, A.; Dinh, T.T.A.; Li, W.T.; Yuen, C. Securing Smart Grids Through an Incentive Mechanism for Blockchain-Based Data Sharing. In Proceedings of the Twelveth ACM Conference on Data and Application Security and Privacy, Baltimore, MD, USA, 24–27 April 2022. [Google Scholar] [CrossRef]
- Liang, G.; Weller, S.R.; Luo, F.; Zhao, J.; Dong, Z.Y. Distributed Blockchain-Based Data Protection Framework for Modern Power Systems Against Cyber Attacks. IEEE Trans. Smart Grid 2019, 10, 3162–3173. [Google Scholar] [CrossRef]
- Dehalwar, V.; Kolhe, M.L.; Deoli, S.; Jhariya, M.K. Blockchain-based trust management and authentication of devices in smart grid. Clean. Eng. Technol. 2022, 8, 100481. [Google Scholar] [CrossRef]
- Poggio, T.; Mhaskar, H.; Rosasco, L.; Miranda, B.; Liao, Q. Why and when can deep-but not shallow-networks avoid the curse of dimensionality: A review. Int. J. Autom. Comput. 2017, 14, 503–519. [Google Scholar] [CrossRef]
- Sawas, A.M.; Khani, H.; Farag, H.E.Z. On the Resiliency of Power and Gas Integration Resources Against Cyber Attacks. IEEE Trans. Ind. Inform. 2021, 17, 3099–3110. [Google Scholar] [CrossRef]
- Albarakati, A.; Robillard, C.; Karanfil, M.; Kassouf, M.; Debbabi, M.; Youssef, A.; Ghafouri, M.; Hadjidj, R. Security Monitoring of IEC 61850 Substations Using IEC 62351-7 Network and System Management. IEEE Trans. Ind. Inform. 2022, 18, 1641–1653. [Google Scholar] [CrossRef]
- Yao, D.; Wen, M.; Liang, X.; Fu, Z.; Zhang, K.; Yang, B. Energy Theft Detection With Energy Privacy Preservation in the Smart Grid. IEEE Internet Things J. 2019, 6, 7659–7669. [Google Scholar] [CrossRef]
- Kwon, S.; Yoo, H.; Shon, T. IEEE 1815.1-Based Power System Security With Bidirectional RNN-Based Network Anomalous Attack Detection for Cyber-Physical System. IEEE Access 2020, 8, 77572–77586. [Google Scholar] [CrossRef]
- Siniosoglou, I.; Radoglou-Grammatikis, P.; Efstathopoulos, G.; Fouliras, P.; Sarigiannidis, P. A Unified Deep Learning Anomaly Detection and Classification Approach for Smart Grid Environments. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1137–1151. [Google Scholar] [CrossRef]
- He, Z.; Khazaei, J.; Moazeni, F.; Freihaut, J.D. Detection of false data injection attacks leading to line congestions using Neural networks. Sustain. Cities Soc. 2022, 82, 103861. [Google Scholar] [CrossRef]
- Abdulaal, M.J.; Ibrahem, M.I.; Mahmoud, M.M.E.A.; Khalid, J.; Aljohani, A.J.; Milyani, A.H.; Abusorrah, A.M. Real-Time Detection of False Readings in Smart Grid AMI Using Deep and Ensemble Learning. IEEE Access 2022, 10, 47541–47556. [Google Scholar] [CrossRef]
- Lepolesa, L.J.; Achari, S.; Cheng, L. Electricity Theft Detection in Smart Grids Based on Deep Neural Network. IEEE Access 2022, 10, 39638–39655. [Google Scholar] [CrossRef]
- Khan, S.; Aslam, S.; Mustafa, I.; Aslam, S. Short-Term Electricity Price Forecasting by Employing Ensemble Empirical Mode Decomposition and Extreme Learning Machine. Forecasting 2021, 3, 28. [Google Scholar] [CrossRef]
- Ashrafuzzaman, M.; Das, S.; Chakhchoukh, Y.; Shiva, S.; Sheldon, F.T. Detecting stealthy false data injection attacks in the smart grid using ensemble-based machine learning. Comput. Secur. 2020, 97, 101994. [Google Scholar] [CrossRef]
- Mohammadpourfard, M.; Weng, Y.; Pechenizkiy, M.; Tajdinian, M.; Mohammadi-Ivatloo, B. Ensuring cybersecurity of smart grid against data integrity attacks under concept drift. Int. J. Electr. Power Energy Syst. 2020, 119, 105947. [Google Scholar] [CrossRef]
- Acosta, M.R.C.; Ahmed, S.; Garcia, C.E.; Koo, I. Extremely Randomized Trees-Based Scheme for Stealthy Cyber-Attack Detection in Smart Grid Networks. IEEE Access 2020, 8, 19921–19933. [Google Scholar] [CrossRef]
- Ravikumar, G.; Govindarasu, M. Anomaly Detection and Mitigation for Wide-Area Damping Control using Machine Learning. IEEE Trans. Smart Grid 2020. [Google Scholar] [CrossRef]
- Singh, V.K.; Govindarasu, M. A Cyber-Physical Anomaly Detection for Wide-Area Protection Using Machine Learning. IEEE Trans. Smart Grid 2021, 12, 3514–3526. [Google Scholar] [CrossRef]
- Cao, J.; Wang, D.; Qu, Z.; Cui, M.; Xu, P.; Xue, K.; Hu, K. A Novel False Data Injection Attack Detection Model of the Cyber-Physical Power System. IEEE Access 2020, 8, 95109–95125. [Google Scholar] [CrossRef]
- Wu, T.; Xue, W.; Wang, H.; Chung, C.Y.; Wang, G.; Peng, J.; Yang, Q. Extreme Learning Machine-Based State Reconstruction for Automatic Attack Filtering in Cyber Physical Power System. IEEE Trans. Ind. Inform. 2021, 17, 1892–1904. [Google Scholar] [CrossRef]
- Aflaki, A.; Gitizadeh, M.; Razavi-Far, R.; Palade, V.; Ghasemi, A.A. A Hybrid Framework for Detecting and Eliminating Cyber-Attacks in Power Grids. Energies 2021, 14, 5823. [Google Scholar] [CrossRef]
- Parizad, A.; Hatziadoniu, C. Cyber-Attack Detection Using Principal Component Analysis and Noisy Clustering Algorithms: A Collaborative Machine Learning-Based Framework. IEEE Trans. Smart Grid 2022. [Google Scholar] [CrossRef]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A.y. Communication-Efficient Learning of Deep Networks from Decentralized Data. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, Fort Lauderdale, FL, USA, 20–22 April 2017; Singh, A., Zhu, J., Eds.; Proceedings of Machine Learning Research. PMLR: Fort Lauderdale, FL, USA, 2017; Volume 54, pp. 1273–1282. [Google Scholar]
- Su, Z.; Wang, Y.; Luan, T.H.; Zhang, N.; Li, F.; Chen, T.; Cao, H. Secure and Efficient Federated Learning for Smart Grid with Edge-Cloud Collaboration. IEEE Trans. Ind. Inform. 2022, 18, 1333–1344. [Google Scholar] [CrossRef]
- Qammar, A.; Ding, J.; Ning, H. Federated learning attack surface: Taxonomy, cyber defences, challenges, and future directions. Artif. Intell. Rev. 2021, 55, 3569–3606. [Google Scholar] [CrossRef]
- Li, Z.; Sharma, V.; Mohanty, S.P. Preserving Data Privacy via Federated Learning: Challenges and Solutions. IEEE Consum. Electron. Mag. 2020, 9, 8–16. [Google Scholar] [CrossRef]
- Aklilu, Y.T.; Ding, J. Survey on Blockchain for Smart Grid Management, Control, and Operation. Energies 2022, 15, 193. [Google Scholar] [CrossRef]
- Borgaonkar, R.; Tøndel, I.A.; Degefa, M.Z.; Jaatun, M.G. Improving smart grid security through 5G enabled IoT and edge computing. Concurr. Comput. Pract. Exp. 2021, 33, e6466. [Google Scholar] [CrossRef]
- Hossain, N.U.I.; Nagahi, M.; Jaradat, R.; Shah, C.; Buchanan, R.; Hamilton, M. Modeling and assessing cyber resilience of smart grid using Bayesian network-based approach: A system of systems problem. J. Comput. Des. Eng. 2020, 7, 352–366. [Google Scholar] [CrossRef]


| Power Application Stage | Related Hardware |
|---|---|
| Production | Traditional: generators, utility boilers, gas turbines, steam turbines, water turbines, etc. Intelligent: remote control module, cloud service control module, unit adjustment module, field equipment management module, etc. |
| Transmission | Traditional: boosters, substations, grids, high voltage switches, voltage transformers, arresters, etc. Intelligent: status monitoring device of substation equipment, airborne inspection components, etc. |
| Distribution | Traditional: distribution transformers, incoming cabinets, metering cabinets, outgoing cabinets, isolation cabinets, etc. Intelligent: temperature and humidity sensor, current detector, leakage detector, etc. |
| Consumption | Traditional: mechanical meters, induction meters, electronic meters, etc. Intelligent: remote control module, microprocessor, operation panel, A/D converter, etc. |
| Time | Location | Attack Target(s) | Attack Method(s) | Attack Range | Impact and Consequence | Reference |
|---|---|---|---|---|---|---|
| 2010 | Iran | Disrupt the nuclear centrifuges | Stuxnet virus | - | Nearly one-fifth of Iran’s nuclear centrifuges were destroyed. The worm infected over 200,000 computers and damaged 1000 devices by targeting industrial control systems. | [40,41] |
| September 2011 | Arizona, Southern California | affected nearly 2.7 million customers | - | - | This problem causes huge variance between the demand and power supply resulted in a noticeable frequency drop, tripping, and blackout. | [42] |
| December 2014 | Korea | goal | Malicious Code “kimsuky” | Korea Hydro and Nuclear Power plant | Sent 5986 phishing emails containing malicious codes to 3571 employees of the nuclear plant operator. | [43] |
| December 2015 | Part of Kiev (the capital of Ukraine) and western Ukraine | Transformer substations | BlackEnergy malware | 30 seats | About 1.4 million residents had power outages in their homes, disrupting phone calls from power companies that prevented residents from contracting them properly. | [44] |
| January 2016 | Israel | National power supply system | Malware | - | The government had to suspend the operation of a large number of computers in Israel’s power facilities. | [45] |
| June 2017 | Ukraine | Chernobyl nuclear power plant | Petya blackmail virus | Unknown | Several national power facilities were infected, resulting in abnormal operations. | [46,47] |
| June 2018 | France | French company Ingerop | Malicious software | Sensitive data of Fessenheim nuclear power plant | Hackers stole more than 65 GB of sensitive data. These data included nuclear power plant plans and the personal information of thousands of staff. | [48] |
| March 2019 | United States (U.S.) | U.S. power grid | Denial of service (DoS) attack | The Western U.S. | The accident did not cause power failure, and the machine failure time was less than 5 min. | [49] |
| August 2019 | South Africa (Johan-nesburg) | City Power company | Blackmail software | All databases, applications, web apps, and official websites of the company | The attack prevented users from buying electricity, recharging, processing invoices, and accessing the official website of City Power. | [50] |
| August 2019 | Ukraine (Yuzh-noukrainsk) | NPP | Intranet connection to extranet | All sensitive data inside the nuclear power plant | The accident was classified as leakage of state secrets. | [51] |
| April 2020 | Portugal | Energias de Portugal | Blackmail software (Ragnar Locker) | Confidential information within the company | The attacker claimed to have acquired 10TB of sensitive data, including bills, contracts, transactions, customer, and partner sensitive contents. | [52,53] |
| June 2020 | Europe | Enel Group | Snake blackmail software | Internal IT network | The internal IT network was temporarily blocked, resulting in a temporary interruption of customer service activities. | [54] |
| June 2020 | Brazil | Light S.A (Power company) | Sodinokibi blackmail software | Confidential information within the company | The attacker extorted USD 14 million in ransom, and only the attacker’s private key could decrypt the file. | [52] |
| September 2020 | Palestine | K-Electric (Power supplier) | Netwalker blackmail software | Unencrypted files | An unknown amount of stolen data, power billing, and online service interruption. | [55] |
| February 2021 | Texas | - | - | Texas energy market failures | February’s “Big Freeze” winter storm vulnerable to Texas energy market failures. | [56] |
| April 2022 | Ukrainian | Energy company | Industroyer2 malware | - | Industroyer2 directly connects with electrical utility equipment to send commands to the substation devices that regulate the flow of electricity. | [57] |
| Reference | Key Method | Explanation |
|---|---|---|
| [63,64] | Deep learning | Authors proposed the deep-learning-based locational detection (DLLD) framework to detect the location of FDIAs in real time. The DLLD framework is combined with regular bad data detector (BDD) and convolutional neural network (CNN) to eliminate low-quality data and to record the inconsistency in electricity flow due to FDIAs, respectively. Similarly, a false data detector (FDD) concatenates with CNN to detect fake information and co-occurrence dependency of electric flow. From both research and experimental results, this method performs efficiently under attack conditions. |
| [65] | Kullback–Leibler distance | A joint transformation scheme is implemented to detect the FDIAs in real time. The presented method is assembled on the dynamics of measurement variations. Furthermore, Kullback–Leibler distance is used to determine the variance between probability distributions resulting from measurement variations. For validation purpose, the method is evaluated by IEEE 14-bus system under attack and provided great detection probability. |
| [66] | Sparse matrix separation | In sparse matrix separation, in-depth analysis is performed based on the attack properties to detect FDIAs, as it can block the transmission lines and infringes financial benefits with stealth. Through the sparse matrix mechanism, the compromised matrix and normal measurement matrix are detected and recovered from the corrupted measurement matrix. |
| [67] | Colored Gaussian noise | With the implementation of colored Gaussian noise, the detection of FDIAs is made possible and tested on independent component analysis (ICA), which relates to the unobservable FDIAs scheme. Furthermore, the performance of the attack detector is evaluated on the IEEE 30-bus power system, benchmarked to traditional Gaussian noise detector. |
| [68] | Spatio-temporal correlations | A Spatio-temporal detection method is to detect and evaluate the false data injection attacks. The temporal and spatial correlation are examined through cubature Kalman filter and Gaussian process regression, respectively. Both are applied to record the dynamic properties of state vector. After that, deep CNN is trained to investigate the system is under FDIAs or not. Consequently, performance shows 99.84%-100% accuracy. |
| [69] | Kalman filter | With the combination of Kalman filter and recurrent neural network (KFRNN), an effective scheme is presented to detect FDIAs in smart grid. At the first stage, Kalman filter and RNN are applied for state prediction to fit linear and nonlinear data features, respectively. The second stage used the fully connected layer and back propagation (BP) to adaptively concatenate the outcomes of two base learners. Moreover, dynamic threshold is measured to identify the occurrence of FDIAs with the fitting Weibull distribution of the sum of square errors (SSEs) within the observed and the predicted measurements. |
| [70] | Blockchain | As information is switched between independent system operation (ISO) and under-operating agents, an FDIA is generated to check the security level. Attack results in loss of network stability and economic loss to the operator. For this purpose, a blockchain-based secure architecture is developed to switch data between ISO and under-operating agents. Finally, the achieved results prove the effectiveness of blockchain in order to improve the social welfare for power system users. |
| Reference | Key Method | Explanation |
|---|---|---|
| [75] | Deployment of honeypots | Honeypots are specially formulated devices that imitate the intended target of malicious attacks. The deployment of honeypots is suggested as a part of smart grid systems. Moreover, honeypots are implemented to detect, deflect, and analyze attacks. As advanced metering infrastructure (AMI) is an important component of smart grid, vulnerable to DoS attack. Authors presented the honeypots as decoy system in AMI to collect the attack details. The interaction between attacker and defender are investigated with optimum schemes at both sides. |
| [76] | Machine Learning | Machine learning (ML) based models in smart grid are used to detect DoS attacks. ML algorithms are principally used to identify DoS attacks or abnormal behavior. In first phase, it collects network data. Secondly, it selects features and employs principal component analysis (PCA). Finally, an ML algorithm is implemented. |
| [77] | Data-driven | The dynamic states of components subjected to DoS attacks are predicted using a data-driven scheme based on relationships between the state of the attacked modules and the rest of the components of a system before the DoS attack. It is possible to determine the time-series data for PMUs under DoS attack using interrelations among the PMU time-series, even when the attack size is quite large. |
| [78] | Software defined Networking (SDN) | A software-defined networking (SDN) approach is implemented with light-weight entropy-based method to detect low rate and high-rate DDoS attack. Through the adaptive threshold scheme, the highest detection rate is achieved. |
| [79] | Deep Learning and Blockchain | In order to achieve consensus in energy network a practical Byzantine fault tolerance (PBFT) algorithm is employed within blockchain framework. Furthermore, to detect DDoS TCP (transmission control protocol) and DDoS UDP (user datagram protocol) attack, a deep learning algorithm recurrent neural network (RNN) is implemented. |
| [80] | Intrusion Detection and Prevention System (IDPS) | IDPS guarantees confidentiality, integrity and availability (CIA). IDS aims to analyze the security events and identify malicious activities. In smart grids, IDPS can be applied on entire SG or AMI, SCADA, subsation and synchrophasor. |
| Reference | Key Method | Explanation |
|---|---|---|
| [91] | Machine Learning | Extensive research is performed on the detection of MiTM attack in smart grid. Firstly, input observer is designed for power grid system and database with several normal and malicious features are generated. Secondly, machine learning technique is implemented on the phasor measurement unit (PMU) information. ML-based algorithms such as support vector machine (SVM) and K-nearest neighbor (KNN) are employed to classify normal and attacked classes. Furthermore, type of attack such as MiTM and DoS attacks are also recognized successfully. |
| [92] | PUF Authentication | A light-weight physical unclonable functions (PUF) authentication technique is used for the prevention of MiTM attack in smart grid. The proposed PUF authentication technique is applied on the smart meter and share the keys of the enrolment phase with each other. Unique keys are shared as a digital footprint with PUF scheme. Through keys, nodes are able to share information in encrypted form. Hence, the evaluated results show that the MiTM attack on smart meters is not possible in PUF authentication. |
| [93] | Multiple alerts from intrusion detection systems | MiTM attack lead towards the false data injection (FDI), false command injection (FCI) and replay attacks in smart grid. At earlier stage on DNP3-based MiTM attacks on a SCADA system in smart grid. Then, at the second stage, the MiTM attack is detected with IDS alarm alerts by considering the network metrics, including retransmission rate, round trip time (RTT) and processing time. It is significantly necessary to observe the network metrics to identify the signature of stealthy MiTM attack. Consequently, the effectiveness of MiTM attack is reduced. |
| Reference | Key Method | Explanation |
|---|---|---|
| [100] | Observer-based detection | The power system is subjected to attack under the DLAA as two vulnerable loads are proposed to examine the effectiveness of attacks on the system. After that, a robust observer mode is designed to detect load frequency with residual signal generation. Consequently, evaluation done through three generators and six buses of the power system to show the feasibility of detection. |
| [101] | Adaptive Fading Kalman Filter (AFKF) | In order to detect DLAA, a smart grid model is proven, then adaptive fading Kalman filter (AFKF) is established to predict the state of smart grid. Gaussian noise of the smart grid is removed through AFKF to achieve accurate state modification curve. Furthermore, Euclidean distance ratio, which is a detection algorithm, is presented based on the AFKF. Hence, amplifying the invisible DLAA by Euclidean distance ratio enhances the DLAA detection acuteness, particularly in terms of weak DLAAs. |
| [102] | Model-free defense framework | A unique defense strategy based on the model-free technique is presented for load frequency control (LFC) system. The defender has an objective to learn diverse LAAs and achieved learned evidence for attack attenuation as an active defense (AD). Moreover, a model-free passive defense (PD) proposed where the defender tolerates a load-altering attack through improving the system redundancies. As a result, both AD and PD techniques work effectively and are evaluated on IEEE benchmark systems. |
| Reference | Key Method | Explanation |
|---|---|---|
| [106] | Long Short-Term Memory (LSTM) network-based | For the detection of malicious code from smart meters, a long short-term memory (LSTM) network-based technique is proposed on the side channel of power utilization of CPU or MCU. The evaluation done on the real-case smart meters and achieved results shows the efficiency with an accuracy of 92%. |
| [105] | Light-weight index Algorithm | A light-weight algorithm is proposed that has the capability to detect the occurrence of stealthy malicious tap modified commands. The algorithm is developed on the intuition bases in which attacks related to false data and commands only affect the measurement and estimation of particularly designated variables instead of all of them. The algorithm relies on the branch current to the voltages of end nodes of the tap modifying transformers. |
| [103] | Beat bad data detection | A detection algorithm is capable of detecting the existence of anomalous phase shifts in the response of cyberattacks. The algorithm is established on detection features and particularly includes the four indices based on branch ratio and injection currents to terminals. Moreover, reference values are counted at the phase shift selection with the evaluation of discrete indices. |
| Reference | Key Method | Explanation |
|---|---|---|
| [108] | Nearest neighbor-based detection scheme | To detect the load redistribution attack, nearest neighbor-based detection method is proposed and scaled from a small to a large system with promising constant detection performance. A sensitive analysis as well as broad testing is conducted on the LR attack with unsystematic anomalies load changes. Furthermore, through the statistical method, the attack is localized, and the probability of each load under attack is uncovered. |
| [109,110] | Machine learning Based | Three types of machine learning algorithms such as nearest neighbor, support vector machines (SVM), and replicator neural networks are employed as anomalies detectors to detect cyberattacks that malevolently redistribute loads by transforming the measurements. These anomaly detection algorithms are tested with realistic historic datasets collected from PJM zonal data mapped [111]. Results presented that among the three, the nearest neighbor algorithm worked efficiently and reduced the computational cost. Similarly, LR attacks are detected via multi-output support vector regression (SVR) which worked as a load predictor and later applied the SVM. |
| Reference | Key Method | Explanation |
|---|---|---|
| [119] | Bargaining game | Replay attacks apparently threaten the smart grid system and need to be detected early. A Kalman filter is utilized to state the fault diagnosis matrix and then noise and control signal are included to present the properties of replay attack detection. Furthermore, based on the bargaining game method, noise is added to the control input with the knowledge of control performance and detection accuracy. At the end, through simulation, the efficiency of the proposed method is validated. |
| [120] | Support vector machine (SVM) | A data-driven approach is presented in which learning from classifier a labelled dataset is used, i.e., power state, to detect replay attack states from useful normal states. The support vector machine (SVM) is implemented as an ML classifier. To evaluate the effectiveness of the approach, IEEE bus systems are utilized and high detection accuracy is achieved. |
| [121] | Watermarking Technique | A novel improved watermarking technique is proposed to detect active replay attacks to smart grids. The suggested scheme makes use of the set-theoretic model predictive control framework to create a control input that can be securely and steadily connected to the utility grid for an a priori known number of steps, as and when they are needed. Results indicate that the watermarking technique efficiently detects the replay attack. |
| [122] | Proactive Intrusion Detection and Mitigation System (PIDMS) | PIDMS analyzes the both cyber and physical data streams in parallel in order to detect intrusion and implement the proactive response. Furthermore, PIDMS comprises ML algorithms and network IDS. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ding, J.; Qammar, A.; Zhang, Z.; Karim, A.; Ning, H. Cyber Threats to Smart Grids: Review, Taxonomy, Potential Solutions, and Future Directions. Energies 2022, 15, 6799. https://doi.org/10.3390/en15186799
Ding J, Qammar A, Zhang Z, Karim A, Ning H. Cyber Threats to Smart Grids: Review, Taxonomy, Potential Solutions, and Future Directions. Energies. 2022; 15(18):6799. https://doi.org/10.3390/en15186799
Chicago/Turabian StyleDing, Jianguo, Attia Qammar, Zhimin Zhang, Ahmad Karim, and Huansheng Ning. 2022. "Cyber Threats to Smart Grids: Review, Taxonomy, Potential Solutions, and Future Directions" Energies 15, no. 18: 6799. https://doi.org/10.3390/en15186799
APA StyleDing, J., Qammar, A., Zhang, Z., Karim, A., & Ning, H. (2022). Cyber Threats to Smart Grids: Review, Taxonomy, Potential Solutions, and Future Directions. Energies, 15(18), 6799. https://doi.org/10.3390/en15186799









