Automated Runtime Verification of Security for E-Commerce Smart Contracts
Abstract
1. Introduction
1.1. Problem Analysis
1.2. Our Contributions
1.3. Structure of the Paper
2. Related Works
2.1. Security Verification of Smart Contracts
2.2. Model Learning
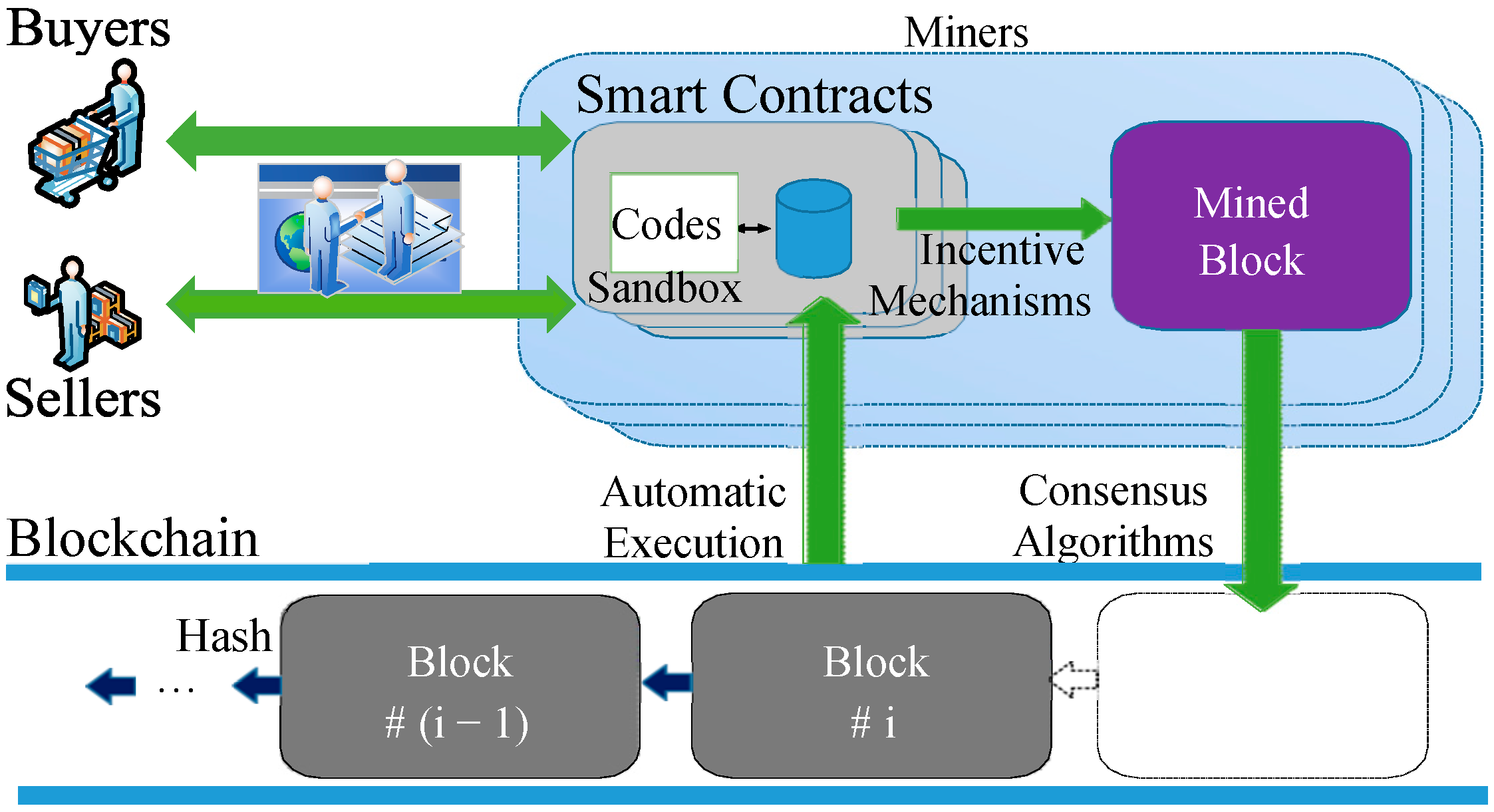
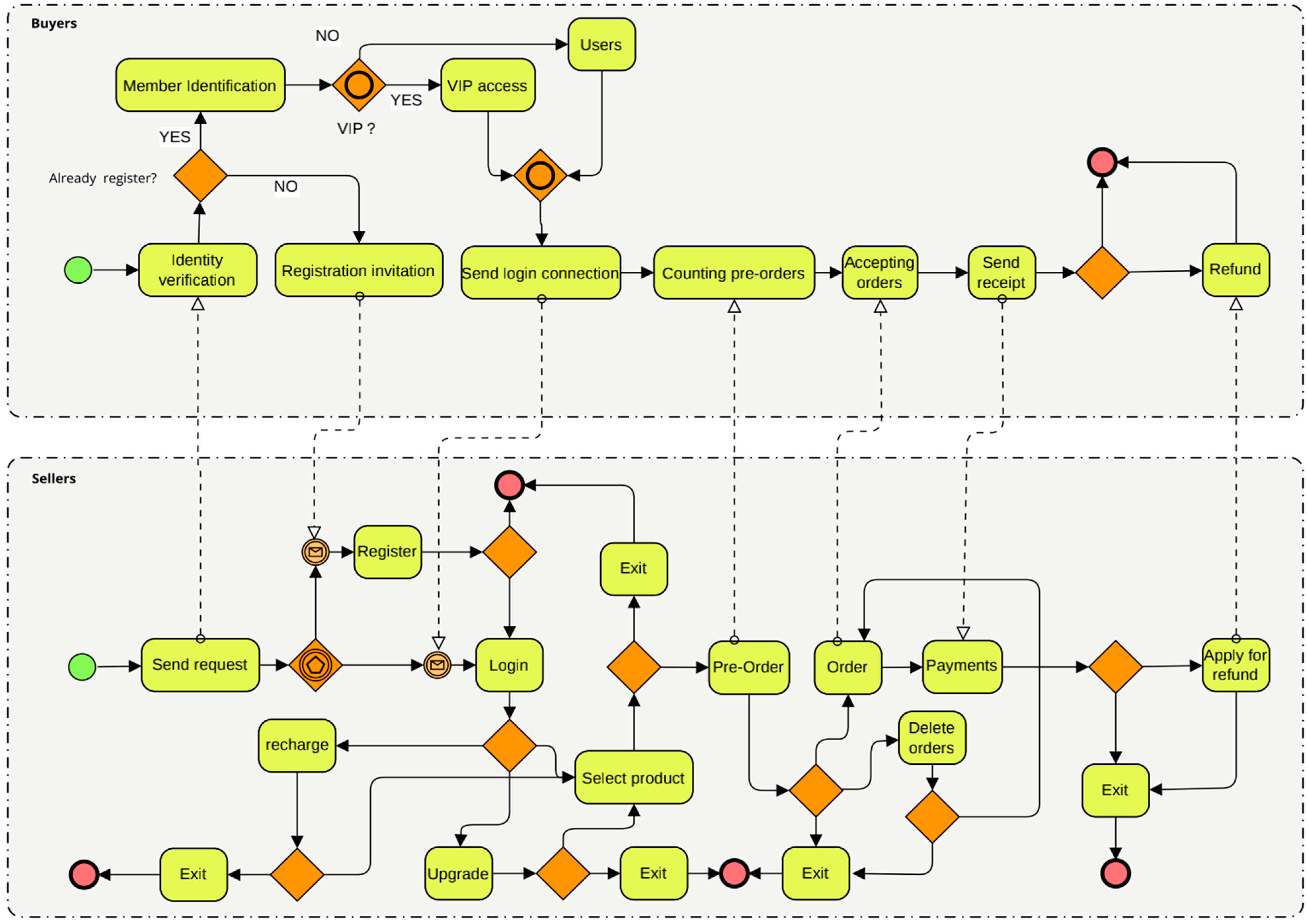
3. Runtime Model of E-Commerce Smart Contract
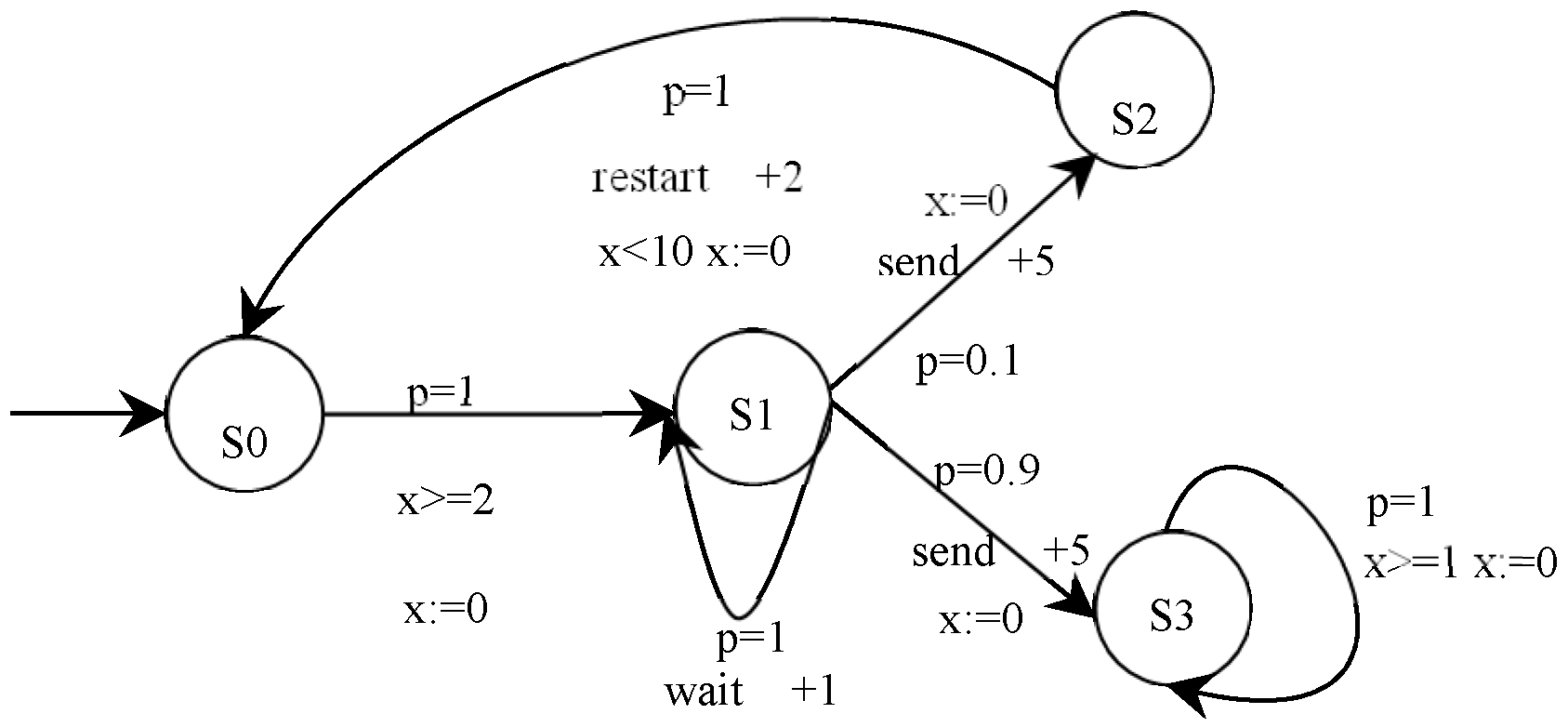
3.1. Clocks, Guards, and Probability
3.2. Priced Probabilistic Timed Automata for an E-Commerce Smart Contract
4. Passive Learning P2TA for Runtime E-Commerce Smart Contracts
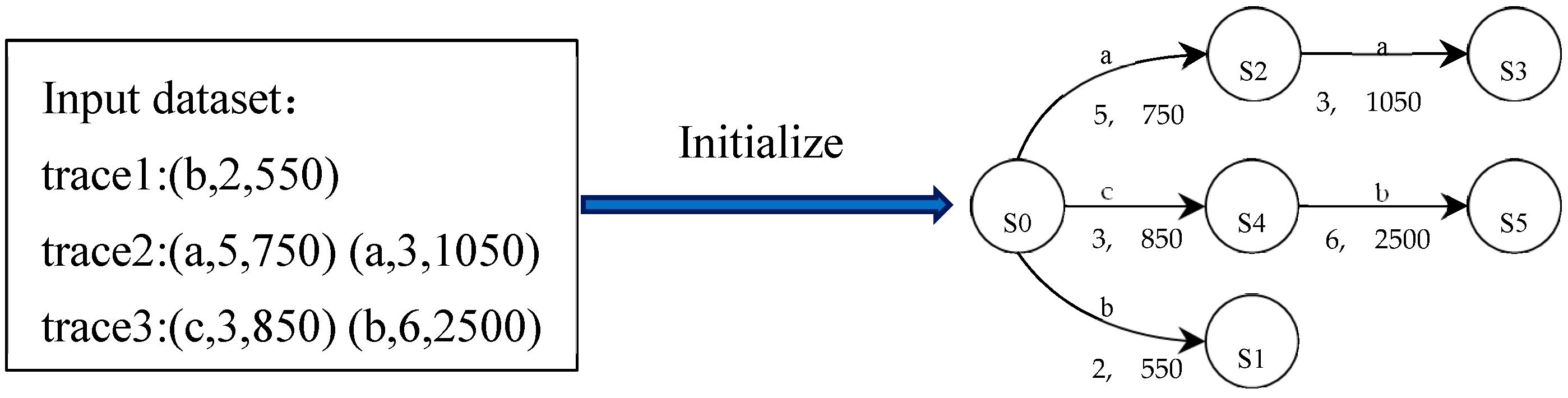
4.1. Automaton Initializing
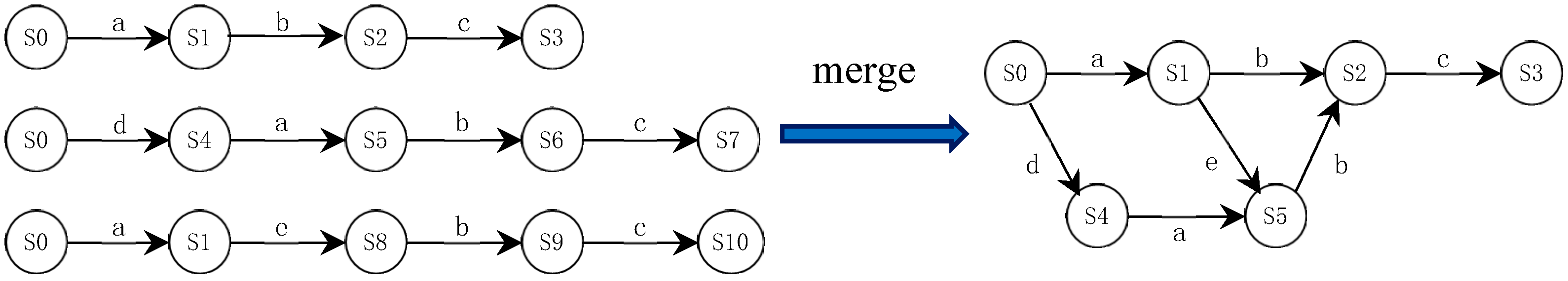
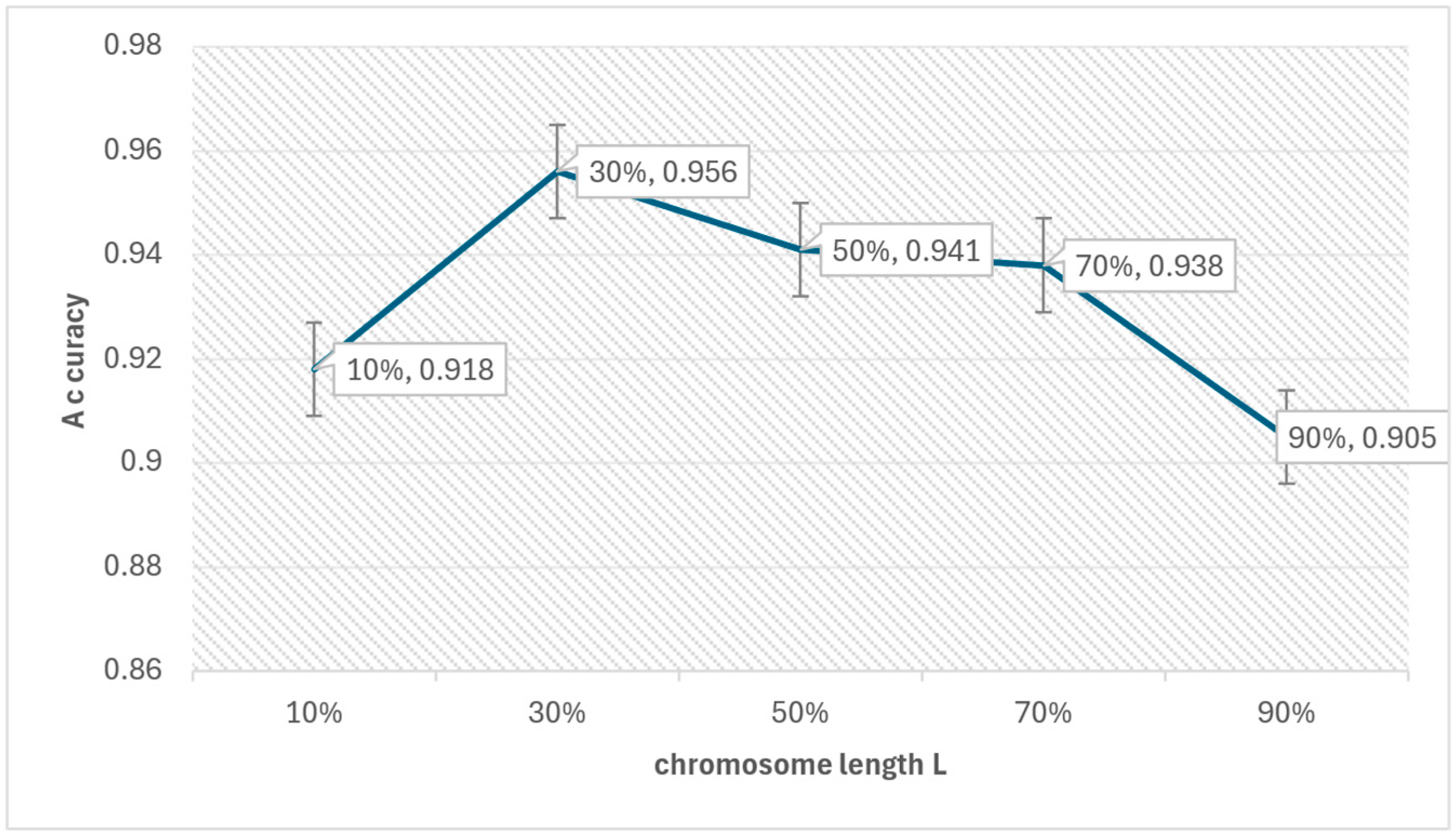
4.2. Genetic Algorithm-Based State Merging
| Algorithm 1: State merging based on GA |
| Input: An augmented prefix tree A, Reduction Table RT |
| Output: A P2TA merge(A) such that L(A) ⊆ L(merge(A)) and |merge(A)| < |A| |
| 1: Creating some chromosomes from RT(the number is p, length is L) |
| 2: i = 0, Score ≠ 0 |
| 3: While (!(i >= I) and !(Score==0) ) |
| 4: Fitness evaluate: |
| 5: for each chromosome from Population do |
| 6: Merging all valid merges from chromosome in A => a part hypothesis PH |
| 7: if Si and Sj will be merged do |
| 8: for all t ∈ Ein(Sj) do |
| 9: Replace t = (S, act, g, h, p, Sj) with (S, act, g, h, p, Si) |
| 10: for all t ∈ Eout(Sj) do |
| 11: Replace t = (Sj, act, g, h, p, S) with (Si, act, g, h, p, S) |
| 12: Delete Sj |
| 13: Merging the remaining valid merges by EDSM in PH => a final hypothesis FH |
| 14: |
| 15: Crossover, Mutation, Selection |
| 16: New generation |
| 17: i++ |
| 18: A is the P2TA corresponding to the chromosome with the lowest fitness score |
| 19: return merge(A) |
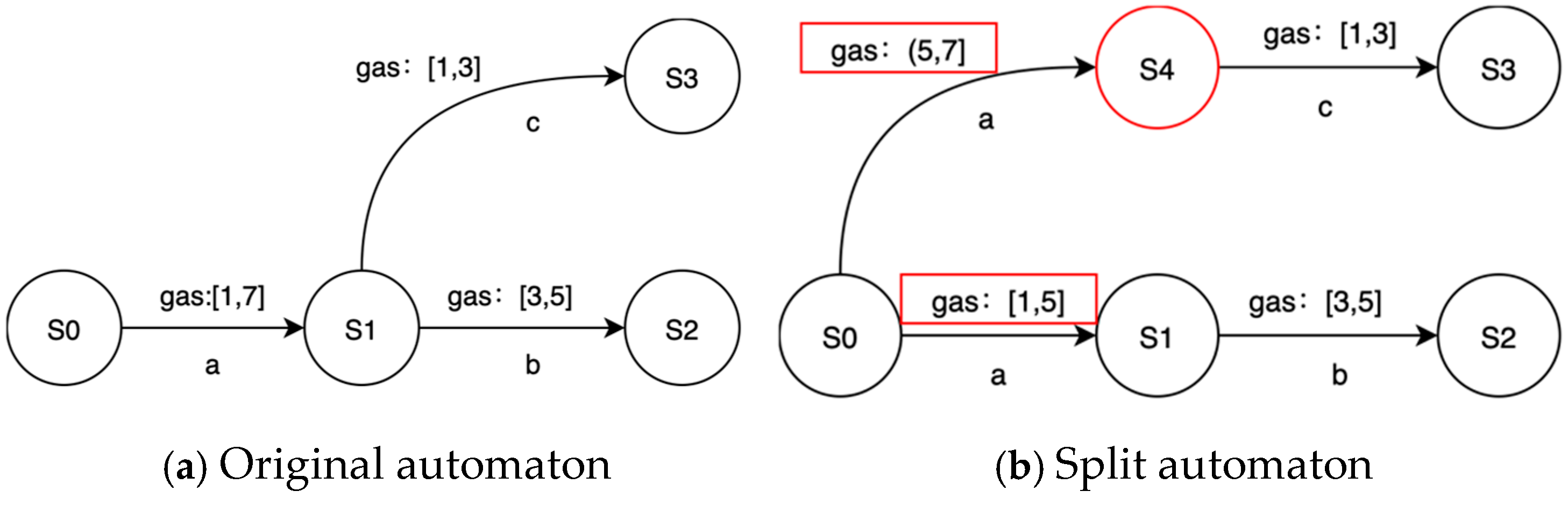
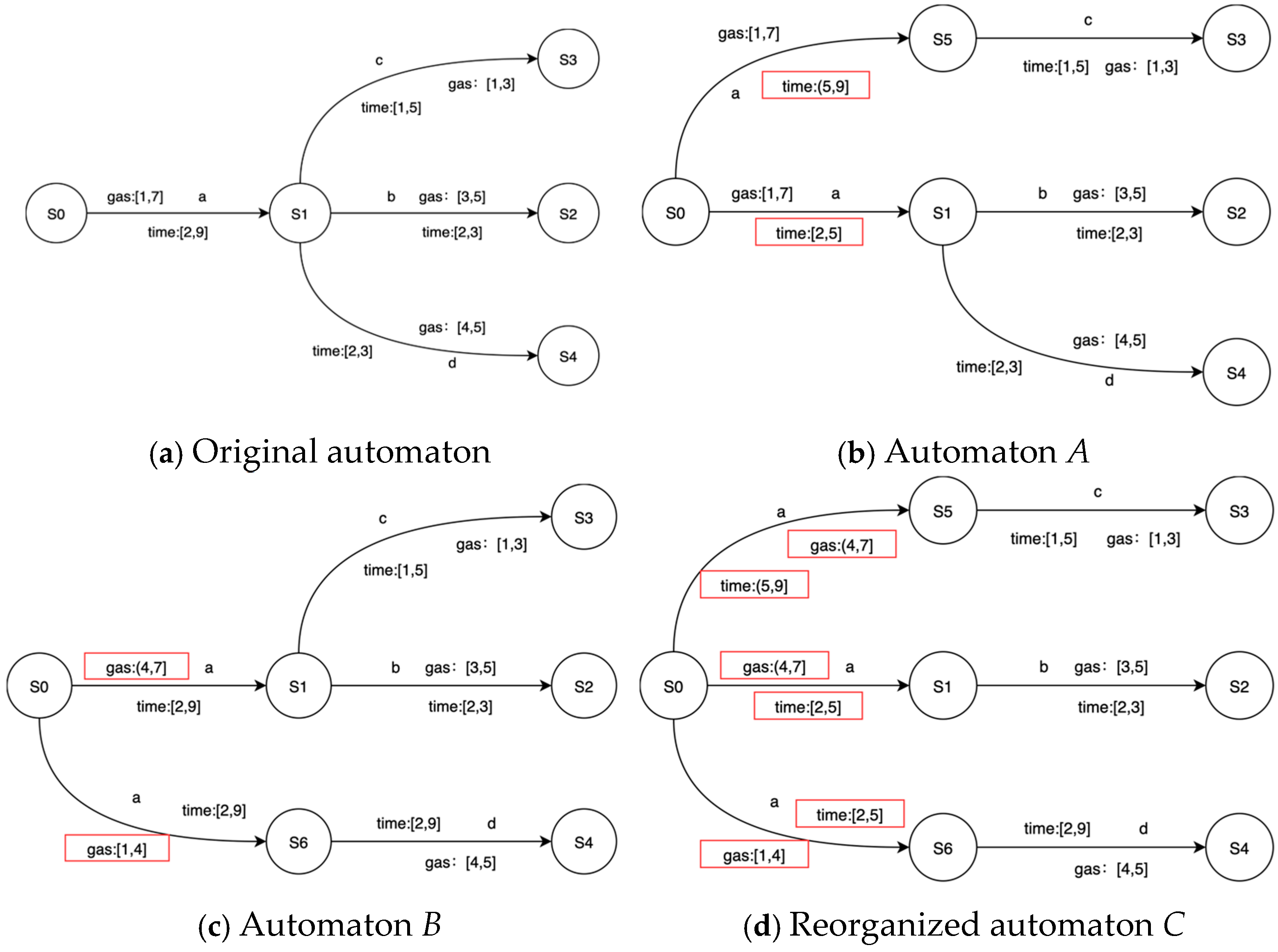
4.3. Splitting and Reorganizing
- Number Extraction: Select a guard [min, max] from the edge to be split. During the initialization of the automaton, in order to obtain a more generalized automaton, we extend the discrete data in a runtime trajectory with a continuous interval. In order to ensure the accuracy of splitting and reduce the interference of irrelevant data, we need to extract all the discrete data that actually exists in the runtime trajectory from the guards. Note that the time and gas consumption need to be handled separately.
- Sorting: Sort all the extracted numbers for subsequent analysis.
- Kernel Density Estimation: Use the kernel density estimation method to estimate the probability density function of the data.
- Finding Density Saddle Points: Search multiple density saddle points on the density curve. These saddle points will divide the data into multiple parts.
- Determining the Boundary Value: The value corresponding to each saddle point is taken as the boundary value, and the data are divided into multiple parts. Each part forms a new guard interval.
- Validate: Kernel density estimation often results in multiple saddle points. A single saddle point will divide the discrete data into two parts. The number of saddle points selected depends primarily on the output number of the node to be split, but the actual situation may not require such a large number of nodes. After determining the number of saddle points to be selected, we can obtain the value of t.
| Algorithm 2: Automaton reorganizing |
| Input: P2TA A and B |
| Output: P2TA A |
| 1: Let A and B be the result of the transition T = (S1, a, g, h, p, S2) edge splitting |
| 2: Let S3 is a new state in A and S4 is a new state in B |
| 3: edge |
| 4: |
| 5: edge |
| 6: |
| 7: Reorganizing operation: |
| 8: add Bt1 to edge in A, |
| 9: At2 = (S1, a, g1,h1, p, S2) |
| 10: let state S is a child node of states S2 and S4 with action b |
| 11: replace (S2, b, g, h, p, S) with (S4, a, g, h, p, S) |
| 12: delete B |
| 13: end for |
| 14: A = Probability_Update(A) |
| 15: Return A |
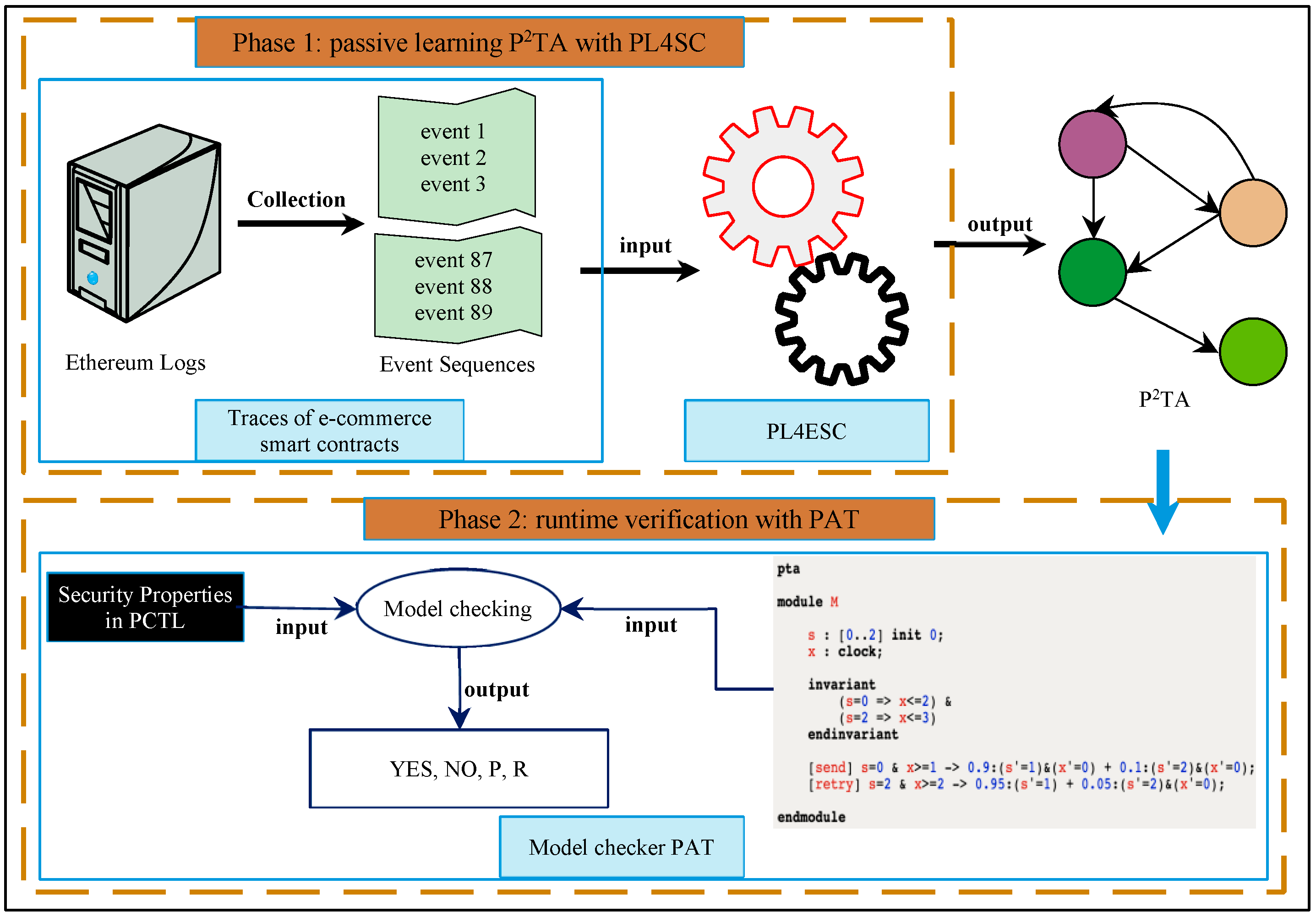
5. Automated Runtime Verification of E-Commerce Smart Contracts
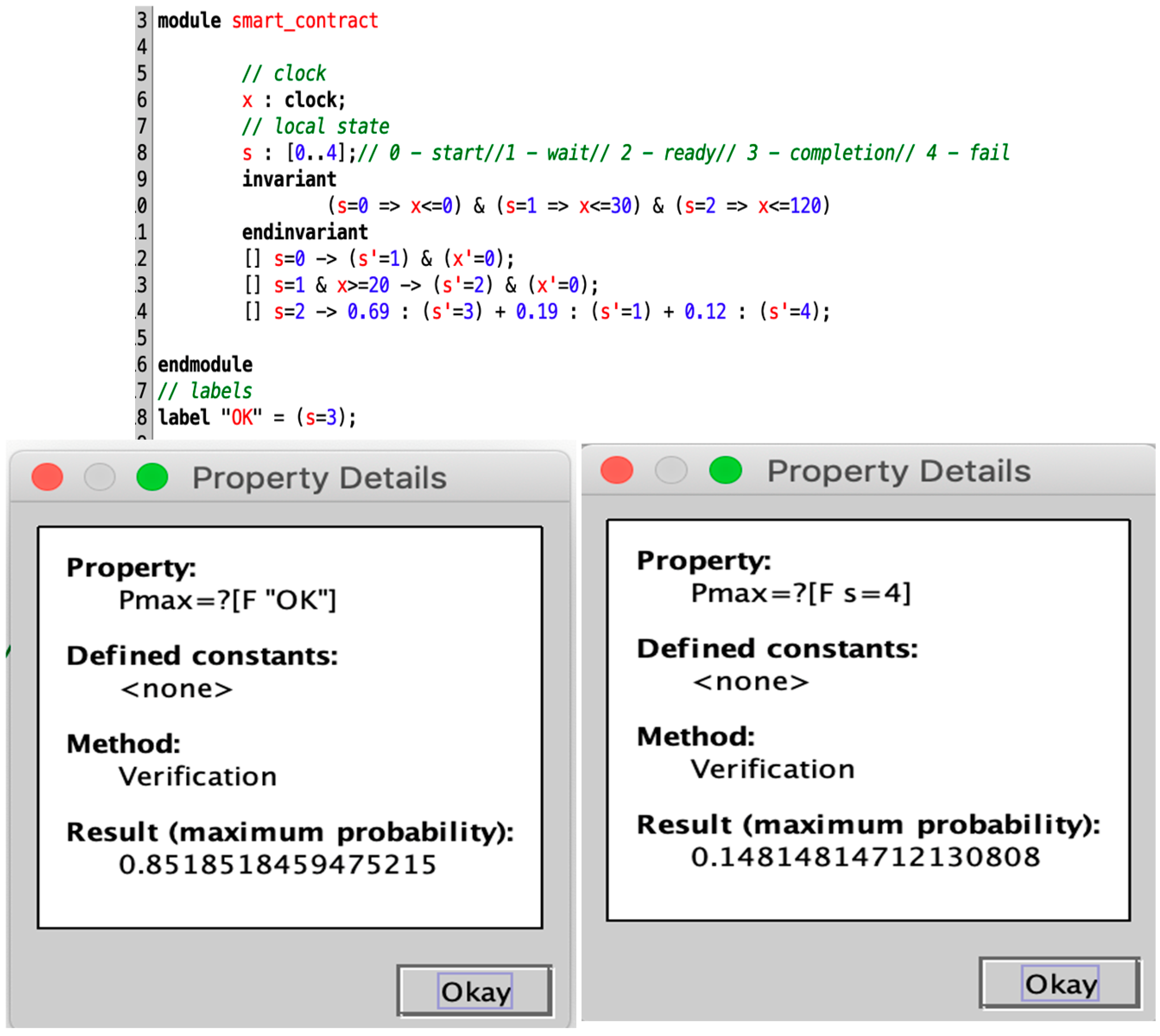
6. Case Study
6.1. Experimental Setup
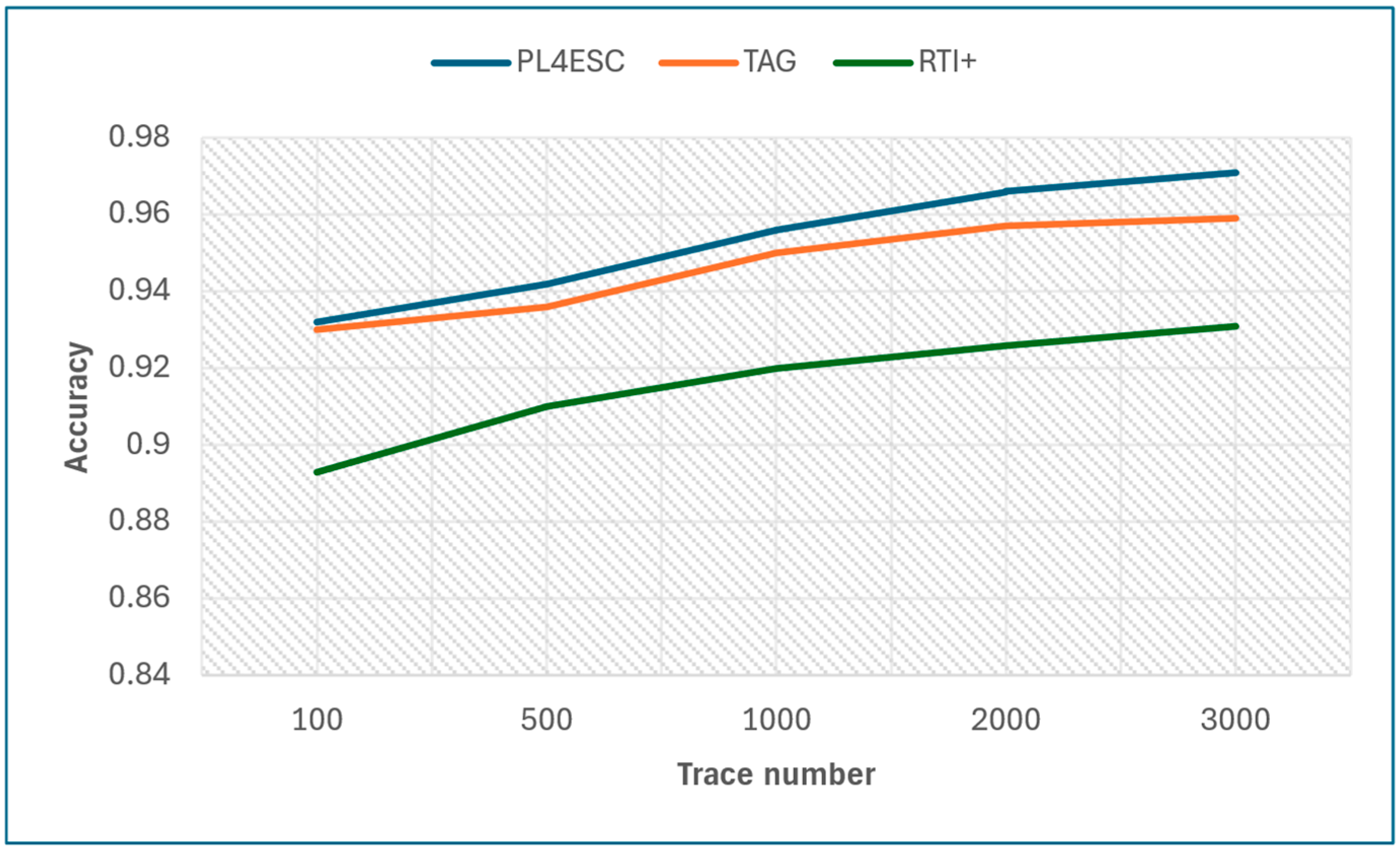
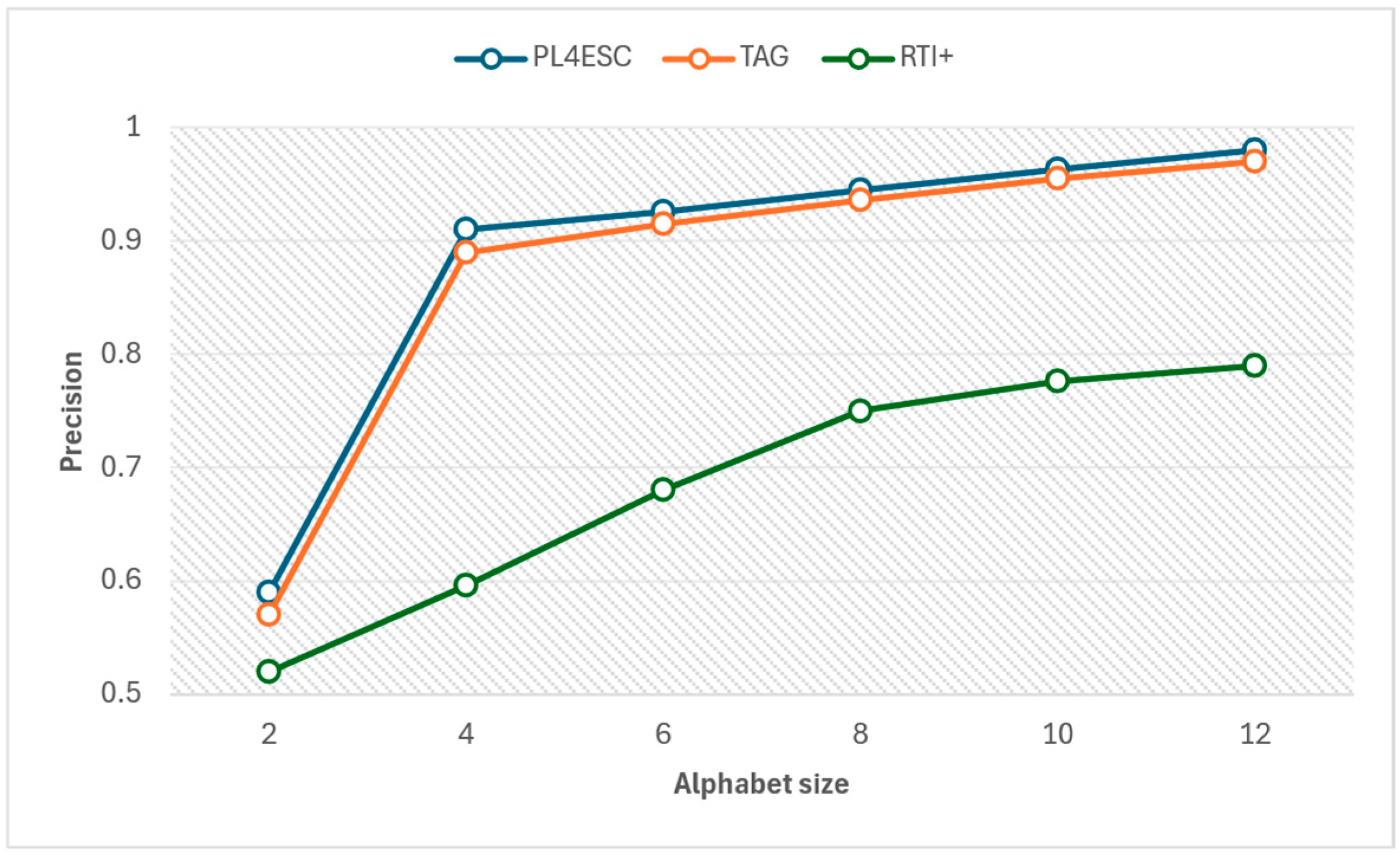
6.2. Experimental Results and Analysis
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Huang, J.; Xu, B.; Yan, X. Selling mode choice and blockchain adoption in an e-commerce platform with information disclosure. Electron. Commer. Res. Appl. 2023, 62, 101331. [Google Scholar]
- Cui, Y.; Gaur, V.; Liu, J. Supply chain transparency and blockchain design. Manag. Sci. 2024, 70, 3245–3263. [Google Scholar] [CrossRef]
- Sun, L.; Hua, G.; Teunter, R.H.; Cheng, T.; Shen, Z.M. The effects of tokenization on ride-hailing blockchain platforms. Prod. Oper. Manag. 2023; early view. [Google Scholar] [CrossRef]
- Merlec, M.M.; In, H.P. DataMesh+: A Blockchain-Powered Peer-to-Peer Data Exchange Model for Self-Sovereign Data Marketplaces. Sensors 2024, 24, 1896. [Google Scholar] [CrossRef]
- Merlec, M.M.; In, H.P. Blockchain-Based Decentralized Storage Systems for Sustainable Data Self-Sovereignty: A Comparative Study. Sustainability 2024, 16, 7671. [Google Scholar] [CrossRef]
- Li, G.; Fan, Z.P.; Zhao, Q.; Sun, M. Blockchain Technology Application in an E-commerce Supply Chain: Privacy Protection and Sales Mode Selection. IEEE Trans. Eng. Manag. 2024, 71, 8060–8074. [Google Scholar] [CrossRef]
- Delmolino, K.; Arnett, M.; Kosba, A.; Miller, A.; Shi, E. Step by step towards creating a safe smart contract: Lessons and insights from a cryptocurrency lab. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 26 February 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 79–94. [Google Scholar]
- Liu, Y.; Wang, C.; Ma, Y. DL4SC: A novel deep learning-based vulnerability detection framework for smart contracts. Autom. Softw. Eng. 2024, 31, 24. [Google Scholar]
- Amani, S.; Bégel, M.; Bortin, M.; Staples, M. Towards verifying ethereum smart contract bytecode in Isabelle/HOL. In Proceedings of the 7th ACM SIGPLAN International Conference on Certified Programs and Proofs, Los Angeles, CA, USA, 8–9 January 2018; pp. 66–77. [Google Scholar]
- He, J.; Balunović, M.; Ambroladze, N.; Tsankov, P.; Vechev, M. Learning to fuzz from symbolic execution with application to smart contracts. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 531–548. [Google Scholar]
- Osterland, T.; Rose, T. Model checking smart contracts for Ethereum. Pervasive Mob. Comput. 2020, 63, 101129. [Google Scholar]
- Falcone, Y.; Krstić, S.; Reger, G.; Traytel, D. A taxonomy for classifying runtime verification tools. Int. J. Softw. Tools Technol. Transf. 2021, 23, 255–284. [Google Scholar]
- Abdellatif, T.; Brousmiche, K.L. Formal verification of smart contracts based on users and blockchain behaviors models. In Proceedings of the 9th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 26–28 February 2018; pp. 1–5. [Google Scholar]
- Tolmach, P.; Li, Y.; Lin, S.W.; Liu, Y. Formal analysis of composable DeFi protocols. In Proceedings of the International Workshop on Financial Cryptography and Data Security, Virtual Event, 5 March 2021; pp. 149–161. [Google Scholar]
- Mao, H.; Chen, Y.; Jaeger, M.; Nielsen, T.D.; Larsen, K.G.; Nielsen, B. Learning probabilistic automata for model checking. In Proceedings of the 8th International Conference on Quantitative Evaluation of Systems, Aachen, Germany, 5–8 September 2011; pp. 111–120. [Google Scholar]
- Feldman, Y.M.Y.; Sagiv, M.; Shoham, S.; Wilcox, J.R. Learning the boundary of inductive invariants. Proc. ACM Program. Lang. 2021, 5, 1–30. [Google Scholar]
- Vaandrager, F. Model learning. Commun. ACM 2017, 60, 86–95. [Google Scholar] [CrossRef]
- Fiterău-Broştean, P.; Janssen, R.; Vaandrager, F. Combining model learning and model checking to analyze TCP implementations. In Proceedings of the 28th International Conference on Computer Aided Verification, Toronto, ON, Canada, 17–23 July 2016; pp. 454–471. [Google Scholar]
- Tijssen, M.; Poll, E.; de Ruiter, J. Automatic Modeling of SSH Implementations with State Machine Learning Algorithms. Bachelor’s Thesis, Radboud University, Nijmegen, The Netherlands, 2014. [Google Scholar]
- Lin, Q.; Zhang, Y.; Verwer, S.; Wang, J. MOHA: A multi-mode hybrid automaton model for learning car-following behaviors. IEEE Trans. Intell. Transp. Syst. 2018, 20, 790–796. [Google Scholar]
- Lorenzoli, D.; Mariani, L.; Pezzè, M. Automatic generation of software behavioral models. In Proceedings of the 30th International Conference on Software Engineering, Leipzig, Germany, 10–18 May 2008; pp. 501–510. [Google Scholar]
- Dong, G.; Wang, J.; Sun, J.; Zhang, Y.; Wang, X.; Dai, T.; Dong, J.S.; Wang, X. Towards interpreting recurrent neural networks through probabilistic abstraction. In Proceedings of the 35th IEEE/ACM International Conference on Automated Software Engineering (ASE), Melbourne, Australia, 21–25 December 2020; pp. 499–510. [Google Scholar]
- Lucas, S.M.; Reynolds, T.J. Learning deterministic finite automata with a smart state labeling evolutionary algorithm. IEEE Trans. Pattern Anal. Mach. Intell. 2005, 27, 1063–1074. [Google Scholar] [PubMed]
- Li, Y.; Chen, Y.F.; Zhang, L.; Liu, D. A novel learning algorithm for Büchi automata based on family of DFAs and classification trees. Inf. Comput. 2021, 281, 104678. [Google Scholar]
- Ndukwu, U. Generating counterexamples for quantitative safety specifications in probabilistic B. J. Log. Algebr. Program. 2012, 81, 26–45. [Google Scholar] [CrossRef]
- Cornanguer, L.; Largouët, C.; Rozé, L.; Termier, A. TAG: Learning Timed Automata from Logs. In Proceedings of the 36th AAAI Conference on Artificial Intelligence (AAAI’22), Virtually, 22 February–1 March 2022; pp. 1–9. [Google Scholar]
- Verwer, S.; Weerdt, M.; Witteveen, C. A likelihood-ratio test for identifying probabilistic deterministic real-time automata from positive data. In International Colloquium on Grammatical Inference; Springer: Berlin/Heidelberg, Germany, 2010; pp. 203–216. [Google Scholar]
- Liu, Y.; Sun, J.; Dong, J.S. PAT 3: An extensible architecture for building multi-domain model checkers. In Proceedings of the 22nd Annual International Symposium on Software Reliability Engineering, Hiroshima, Japan, 29 November–2 December 2011; pp. 190–199. [Google Scholar]
- Tolmach, P.; Li, Y.; Lin, S.W.; Liu, Y.; Li, Z. A survey of smart contract formal specification and verification. ACM Comput. Surv. 2021, 54, 1–38. [Google Scholar]
- Tsankov, P.; Dan, A.; Drachsler-Cohen, D.; Gervais, A.; Buenzli, F.; Vechev, M. Securify: Practical security analysis of smart contracts. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 67–82. [Google Scholar]
- Kalra, S.; Goel, S.; Dhawan, M.; Sharma, S. Zeus: Analyzing safety of smart contracts. In Proceedings of the Network and Distributed System Security Symposium, San Diego, CA, USA, 18–21 February 2018; Internet Society: Reston, VA, USA, 2018; pp. 1–12. [Google Scholar]
- Antonino, P.; Roscoe, A.W. Solidifier: Bounded model checking solidity using lazy contract deployment and precise memory modelling. In Proceedings of the 36th Annual ACM Symposium on Applied Computing (SAC’21), Virtual, 22–26 March 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 1788–1797. [Google Scholar] [CrossRef]
- Hajdu, Á.; Jovanović, D. solc-verify: A modular verifier for solidity smart contracts. In Proceedings of the 11th Working Conference on Verified Software: Theories, Tools, and Experiments, New York, NY, USA, 13–14 July 2019; pp. 161–179. [Google Scholar]
- Mossberg, M.; Manzano, F.; Hennenfent, E.; Groce, A.; Grieco, G.; Feist, J.; Brunson, T.; Dinaburg, A. Manticore: A user-friendly symbolic execution framework for binaries and smart contracts. In Proceedings of the 34th IEEE/ACM International Conference on Automated Software Engineering (ASE), San Diego, CA, USA, 11–15 November 2019; pp. 1186–1189. [Google Scholar]
- Nehai, Z.; Piriou, P.Y.; Daumas, F. Model-checking of smart contracts. In Proceedings of the IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 980–987. [Google Scholar]
- Zupan, N.; Kasinathan, P.; Cuellar, J.; Sauer, M. Secure smart contract generation based on petri nets. In Blockchain Technology for Industry 4.0; Springer: Singapore, 2020; pp. 73–98. [Google Scholar]
- Azzopardi, S.; Ellul, J.; Pace, G.J. Monitoring smart contracts: Contractlarva and open challenges beyond. In Proceedings of the 18th International Conference on Runtime Verification, Limassol, Cyprus, 10–13 November 2018; pp. 113–137. [Google Scholar]
- Abraham, M.; Jevitha, K.P. Runtime verification and vulnerability testing of smart contracts. In Proceedings of the International Conference on Advances in Computing and Data Sciences, Singapore, 12–13 April 2019; pp. 333–342. [Google Scholar]
- Azzopardi, S.; Colombo, C.; Pace, G. Model-based static and runtime verification for ethereum smart contracts. In Proceedings of the 9th International Conference on Model-Driven Engineering and Software Development, Vienna, Austria, 25–27 February 2021; pp. 323–348. [Google Scholar]
- Ali, S.; Sun, H.; Zhao, Y. Model learning: A survey of foundations, tools and applications. Front. Comput. Sci. 2021, 15, 1–22. [Google Scholar]
- Angluin, D. Learning regular sets from queries and counterexamples. Inf. Comput. 1987, 75, 87–106. [Google Scholar]
- Shahbaz, M.; Groz, R. Inferring mealy machines. In International Symposium on Formal Methods; Springer: Berlin/Heidelberg, Germany, 2009; pp. 207–222. [Google Scholar]
- Jonsson, B. Learning of automata models extended with data. In Proceedings of the International School on Formal Methods for the Design of Computer, Communication and Software Systems, Bertinoro, Italy, 13–18 June 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 327–349. [Google Scholar]
- Cassel, S.; Howar, F.; Jonsson, B.; Steffen, B. Learning extended finite state machines. In Proceedings of the 12th International Conference on Software Engineering and Formal Methods (SFFM 2014), Grenoble, France, 1–5 September 2014; pp. 250–264. [Google Scholar]
- An, J.; Chen, M.; Zhan, B.; Zhan, N.; Zhang, M. Learning One-Clock Timed Automata. In Tools and Algorithms for the Construction and Analysis of Systems. TACAS 2020; Biere, A., Parker, D., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; Volume 12078, pp. 444–462. [Google Scholar]
- Dupont, P. Regular grammatical inference from positive and negative samples by genetic search: The GIG method. In International Colloquium on Grammatical Inference; Springer: Berlin/Heidelberg, Germany, 1994; pp. 236–245. [Google Scholar]
- Lang, K.J.; Pearlmutter, B.A.; Price, R.A. Results of the abbadingo one DFA learning competition and a new evidence-driven state merging algorithm. In Grammatical Inference; Springer: Berlin/Heidelberg, Germany, 1998; pp. 1–12. [Google Scholar]
- Lang, K. Evidence Driven State Merging with Search; Rapport technique TR98–139; NECI: Mansfield, MA, USA, 1998; Volume 31. [Google Scholar]
- Giantamidis, G.; Tripakis, S.; Basagiannis, S. Learning Moore machines from input–output traces. Int. J. Softw. Tools Technol. Transf. 2021, 23, 1–29. [Google Scholar]
- Walkinshaw, N.; Taylor, R.; Derrick, J. Inferring extended finite state machine models from software executions. Empir. Softw. Eng. 2016, 21, 811–853. [Google Scholar]
- Matos Pedro, A.; Crocker, P.A.; Sousa, S.M. Learning stochastic timed automata from sample executions. In Proceedings of the 5th International Conference on Leveraging Applications of Formal Methods, Verification and Validation: Technologies for Mastering Change-Volume Part I (ISoLA’12), Heraclion, Greece, 15–18 October 2012; pp. 508–523. [Google Scholar]
- Mao, H.; Chen, Y.; Jaeger, M.; Nielsen, T.D.; Larsen, K.G.; Nielsen, B. Learning deterministic probabilistic automata from a model checking perspective. Mach. Learn. 2016, 105, 255–299. [Google Scholar]
- Pastore, F.; Micucci, D.; Mariani, L. Timed k-tail: Automatic inference of timed automata. In Proceedings of the IEEE International Conference on Software Testing, Verification and Validation (ICST), Tokyo, Japan, 13–17 March 2017; pp. 401–411. [Google Scholar]
- Biermann, A.W.; Feldman, J.A. On the synthesis of finite-state machines from samples of their behavior. IEEE Trans. Comput. 1972, 100, 592–597. [Google Scholar]
- Jurdziński, M.; Kwiatkowska, M.; Norman, G.; Trivedi, A. Concavely-priced probabilistic timed automata. In CONCUR 2009-Concurrency Theory: 20th International Conference, CONCUR 2009, Bologna, Italy, 1–4 September 2009. Proceedings; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5710. [Google Scholar]
- Coste, F.; Nicolas, J. Regular inference as a graph coloring problem. In Proceedings of the Workshop on Grammatical Inference, Automata Induction, and Language Acquisition (ICML’97), Nashville, TN, USA, 12 July 1997; pp. 9–17. [Google Scholar]
- Guillaumier, K.; Abela, J. Learning DFAs by Evolving Short Sequences of Merges. In Proceedings of the 15th International Conference on Grammatical Inference (ICGI’20), Online, 23–27 August 2021; PMLR: London, UK, 2021; pp. 217–236. [Google Scholar]
- Zhou, Y.; Han, T.; Chen, T.; Zhou, S. Probabilistic analysis of QoS-aware service composition with explicit environment models. IET Softw. 2020, 14, 59–71. [Google Scholar]
- Lòpez-Pintado, O.; García-Bañuelos, L.; Dumas, M.; Weber, I.; Ponomarev, A. Caterpillar: A business process execution engine on the Ethereum blockchain. Softw. Pract. Exp. 2019, 49, 1162–1193. [Google Scholar]



| Learned Models | Learning Process | |
|---|---|---|
| PL4ESC | P2TA (priced probabilistic timed automata) | (1) K-future state merging based on the Genetic algorithm (2) Edge splitting (3) Automata reorganizing |
| TAG | TA (timed automata) | (1) K-future-based state merging (2) Edge splitting |
| RTI+ | PDRTA (probabilistic deterministic real-time automata) | Likelihood-ratio test-based state merging |
| Factor | Details of Data |
|---|---|
| Alphabet size | 2, 4, 6, 8, 10, 12 |
| Trace number | 100, 500, 1000, 2000, 3000 |
| Trace Number | 100 | 500 | 1000 | 2000 | 3000 | |
|---|---|---|---|---|---|---|
| Method | ||||||
| PL4ESC | 0.932 | 0.942 | 0.956 | 0.966 | 0.971 | |
| PL4ESC without AR | 0.929 | 0.937 | 0.948 | 0.952 | 0.955 | |
| PL4ESC without GA | 0.927 | 0.934 | 0.942 | 0.948 | 0.952 | |
| Trace Number | 100 | 500 | 1000 | 2000 | 3000 | |
|---|---|---|---|---|---|---|
| Method | ||||||
| PL4ESC | 0.932 | 0.942 | 0.956 | 0.966 | 0.971 | |
| TAG | 0.93 | 0.936 | 0.95 | 0.957 | 0.959 | |
| RTI+ | 0.893 | 0.91 | 0.92 | 0.926 | 0.931 | |
| Alphabet Size | 2 | 4 | 6 | 8 | 10 | 12 | |
|---|---|---|---|---|---|---|---|
| Method | |||||||
| PL4ESC | 0.59 | 0.91 | 0.926 | 0.945 | 0.963 | 0.98 | |
| TAG | 0.57 | 0.89 | 0.915 | 0.936 | 0.955 | 0.97 | |
| RTI+ | 0.52 | 0.596 | 0.68 | 0.75 | 0.776 | 0.79 | |
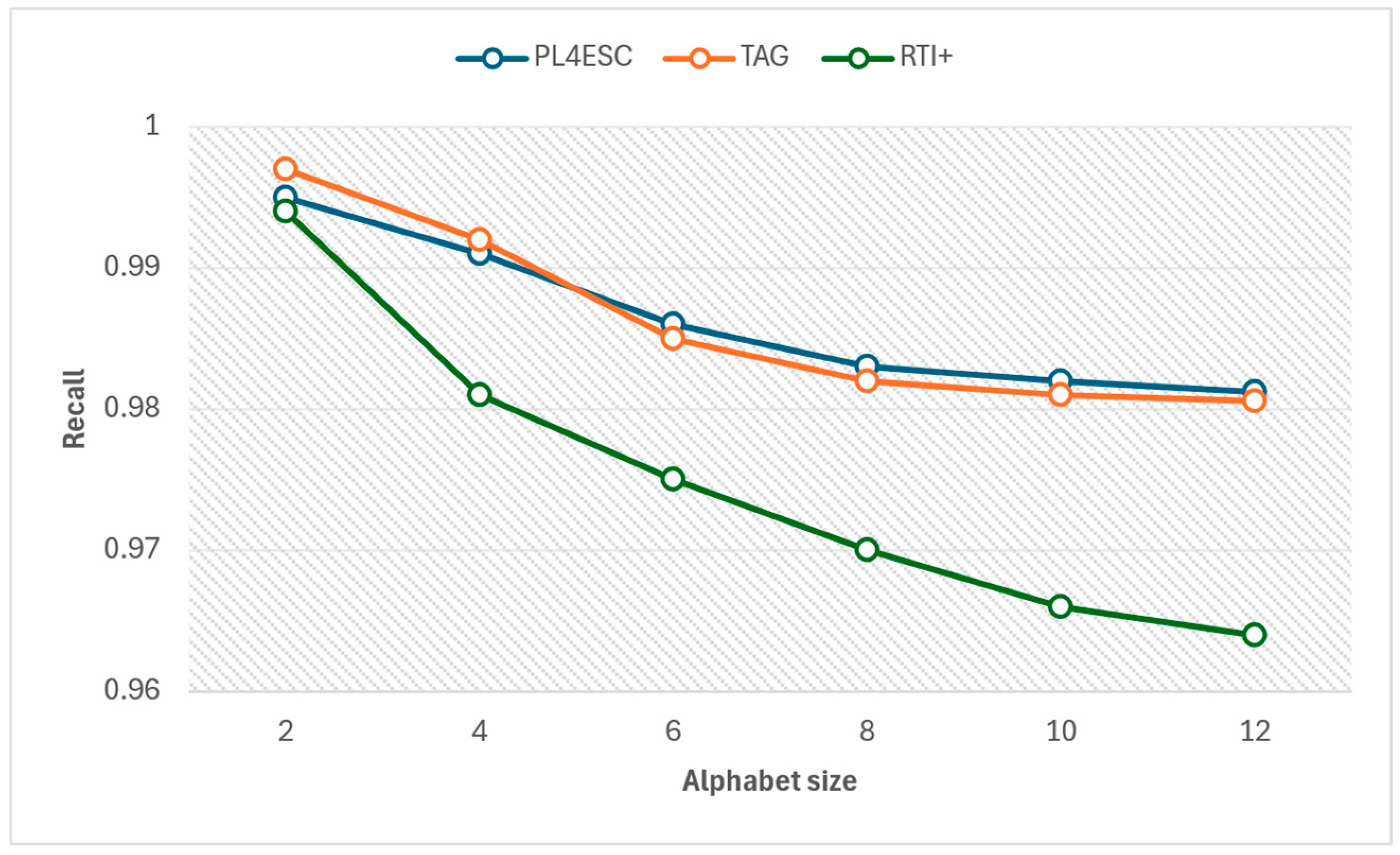
| Alphabet Size | 2 | 4 | 6 | 8 | 10 | 12 | |
|---|---|---|---|---|---|---|---|
| Method | |||||||
| PL4ESC | 0.995 | 0.991 | 0.986 | 0.983 | 0.982 | 0.9812 | |
| TAG | 0.997 | 0.992 | 0.985 | 0.982 | 0.981 | 0.9806 | |
| RTI+ | 0.994 | 0.981 | 0.975 | 0.97 | 0.968 | 0.964 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Y.; Zhang, S.; Ma, Y. Automated Runtime Verification of Security for E-Commerce Smart Contracts. J. Theor. Appl. Electron. Commer. Res. 2025, 20, 73. https://doi.org/10.3390/jtaer20020073
Liu Y, Zhang S, Ma Y. Automated Runtime Verification of Security for E-Commerce Smart Contracts. Journal of Theoretical and Applied Electronic Commerce Research. 2025; 20(2):73. https://doi.org/10.3390/jtaer20020073
Chicago/Turabian StyleLiu, Yang, Shengjie Zhang, and Yan Ma. 2025. "Automated Runtime Verification of Security for E-Commerce Smart Contracts" Journal of Theoretical and Applied Electronic Commerce Research 20, no. 2: 73. https://doi.org/10.3390/jtaer20020073
APA StyleLiu, Y., Zhang, S., & Ma, Y. (2025). Automated Runtime Verification of Security for E-Commerce Smart Contracts. Journal of Theoretical and Applied Electronic Commerce Research, 20(2), 73. https://doi.org/10.3390/jtaer20020073




