1. Introduction
With the popularization of various types of intelligent terminals and the development of image processing technology, the digitization of image works has become a mainstream trend, especially in the fields of e-commerce, social media, and other areas play an important role; however, the characteristics of digitized images which are easy to be downloaded, copied, and modified, and the ensuing problem of copyright infringement of images has also become increasingly prominent [
1,
2]. The cost of copyright infringement of digital works, especially image works, is extremely low, but it is difficult for authors to obtain evidence for the defense of such intellectual property rights, and the cost of litigation to defend their rights is high, which ultimately leads to the overall inefficiency of copyright protection, and the competitiveness of the network business entities and even their business reputation will be affected [
3].
In the network environment, existing technologies such as digital watermarks can no longer adequately protect the rights of copyright holders due to their easy elimination, destruction, and tampering characteristics [
4]. In the existing blockchain technology, the traditional hash algorithm has low accuracy for the infringement detection of images after noise addition and rotation operation, and the encryption algorithm and the method of calling the contract to obtain the key are complicated, which is not suitable for the safe storage of image information in the big data environment [
5]. The originality detection methods in blockchain technology are mostly based on content or manually designed feature extraction methods, which have the following shortcomings. First, content-based originality detection methods only capture single features and local information of an image, ignoring the global structure of the image. As a result, only the local information of an image can be compared during originality detection, while the similarity of the global structure cannot be taken into account, which in turn causes poor originality detection. Second, feature extraction methods based on manual design usually need to select and design parameters based on experts’ a priori knowledge, which often requires manual intervention and adjustment, and it is difficult to fully utilize the rich semantic information in the image, which affects the accuracy of the algorithm in image originality detection [
6,
7].
Based on the discovery of these problems,
Section 2 of this paper improves the traditional hash algorithm and proposes a system model for image copyright protection and management based on blockchain and perceptual hash. It introduces the information transmission process among blockchain, users and InterPlanetary File System (IPFS). Meanwhile, it improves the blockchain storage structure to enhance query efficiency. To ensure the security of image data, it applies chaotic encryption to the images to be uploaded to the blockchain and provides the corresponding decryption algorithm.
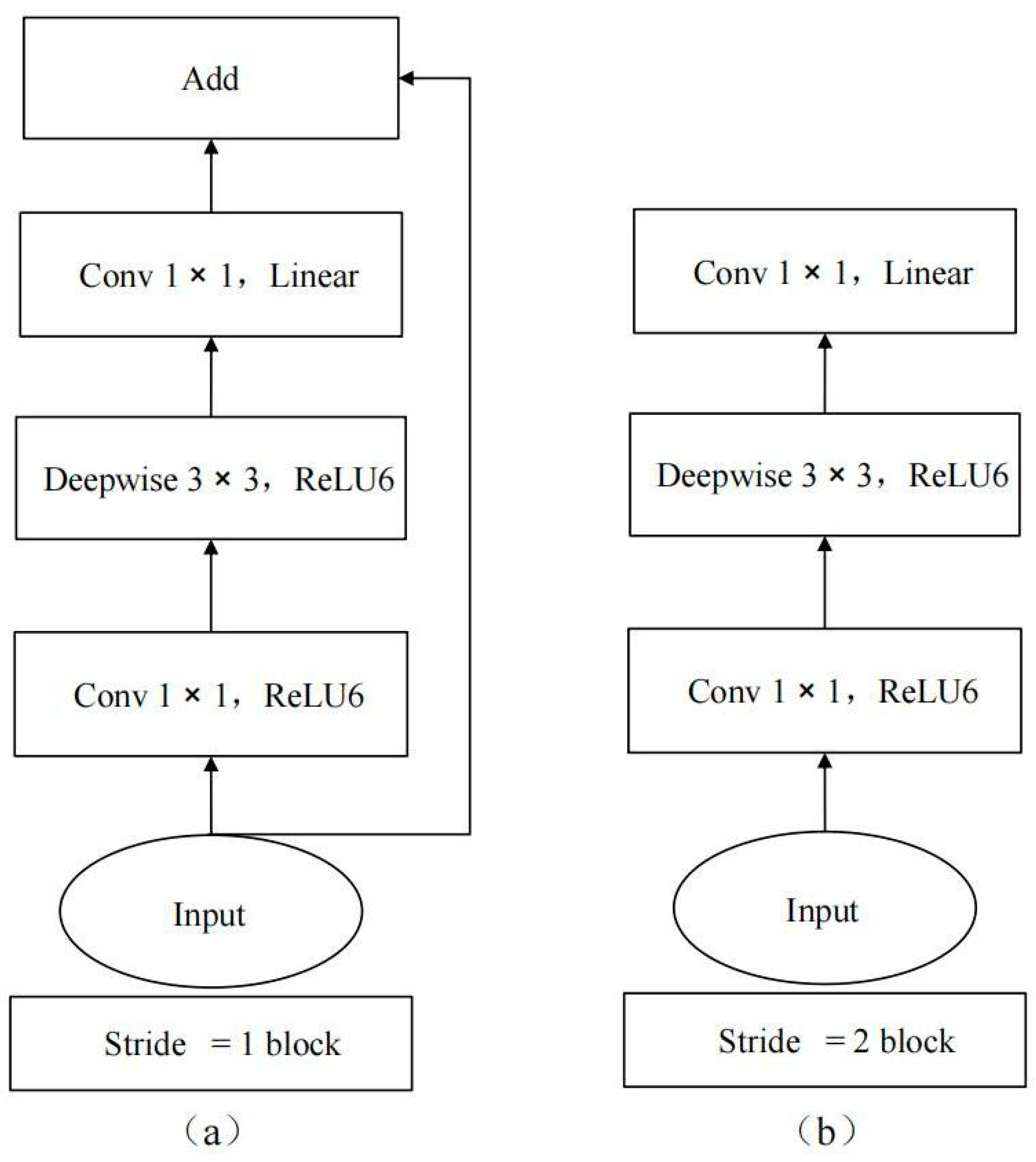
Section 3 proposes an innovative solution for originality detection of images using the MobileNetV2 model, and introduces the MobileNetV2 model, the detection principle and process. This solution effectively integrates deep learning technology with blockchain technology, overcoming the inherent technical barriers of blockchain.
Section 4 combines the image copyright protection and management method based on blockchain and perceptual hash proposed in the previous chapter with the MobileNetV2 image originality detection model based on deep learning, and it provides an overall introduction to the core technology of this paper, namely the digital image copyright protection and management method based on artificial intelligence and blockchain technology. This chapter details the detection process of images under the fusion scheme and verifies the feasibility and effectiveness of the scheme through experiments. It also presents the improved perceptual hash and MobileNetV2 classification model and mathematical model and analyzes the scalability of the system.
Section 5 compares the existing blockchain technology and artificial intelligence technology with this fusion scheme in terms of technical architecture, function, performance, and applicability, and rigorously explains the innovation and feasibility of this scheme.
Section 6 discusses the limitations and applications of this scheme from aspects such as energy consumption and transaction costs, storage limitations, algorithm optimization, and data privacy.
Section 7 concludes this scheme.
4. Image Copyright Registration Protection and Management Method Based on Blockchain and Deep Learning
The existing digital copyright registration methods usually adopt the method of storing the hash value (also called data fingerprint) of the digital content to be registered on the blockchain and storing the original data in the database for the authentication [
39]. However, for image data, conventional data fingerprinting methods cannot achieve good originality detection, and the definition of uniqueness is particularly precise and strict. Users usually pay attention to the content of the image rather than the specific details of the image, so it cannot be purely applied to the copyright registration of the image, and it needs to be based on the image visual content features for originality detection [
40]. The aforementioned has improved the hash algorithm in the current blockchain technology, and in order to ensure the accuracy of image similarity detection to the greatest extent, it is necessary to break the technical barriers of the blockchain, combined with deep learning technology, and carry out a secondary comparison of the images that have been detected by the upper and lower chains [
41].
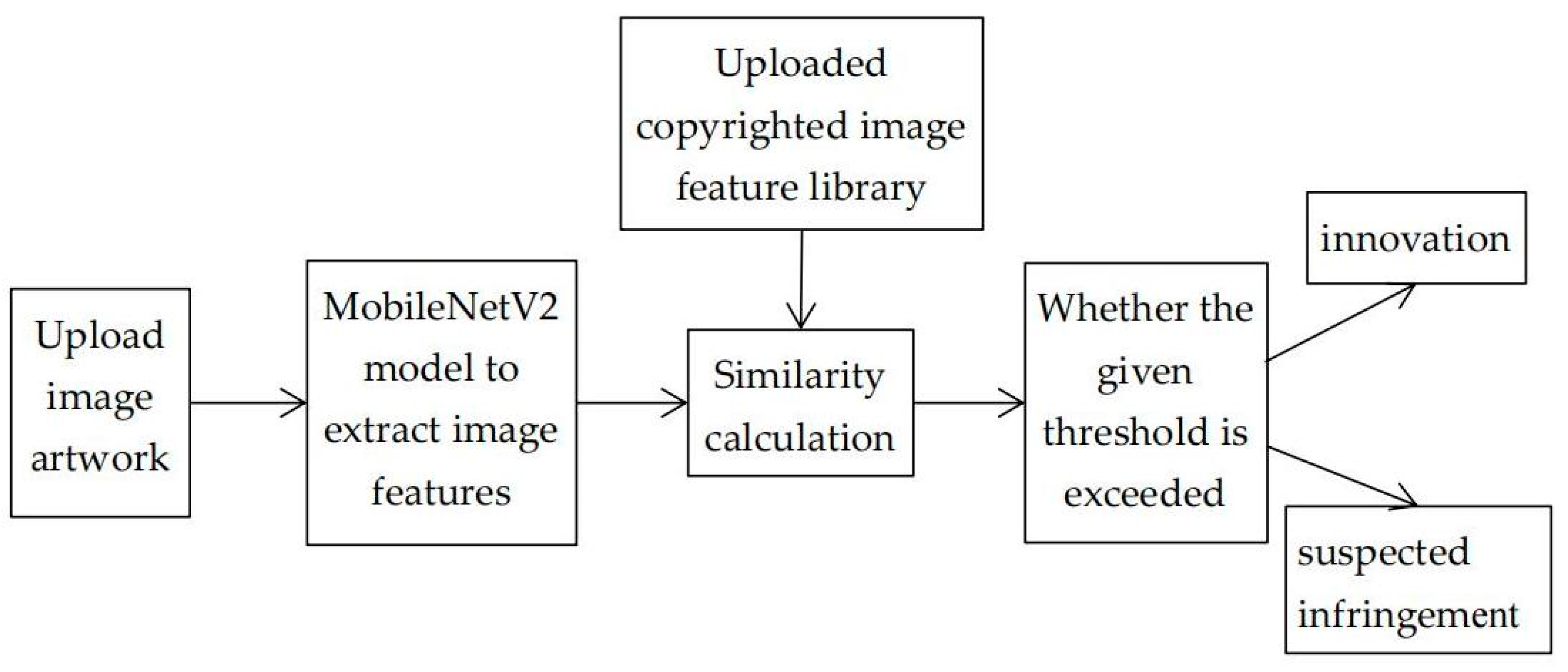
In the previous chapters, this paper improves the traditional hash algorithm based on the advantages and disadvantages of the perceived hash algorithm as the on-chain query detection method of the image copyright registration protection and management method system model based on the blockchain and deep learning. But, the image will be queried off-chain before it enters the chain query by this system, and after passing the up and down chain query detection, it will be detected by using the MobileNetV2 convolutional. After passing the upstream and downstream query detection, the MobileNetV2 convolutional neural network is utilized to carry out the secondary detection of the uploaded image to be uploaded as the last layer of guarantee for the detection of image copyright infringement. This method of combining blockchain and artificial intelligence technology for image copyright registration protection and management can not only make up for the defects of poor robustness of blockchain’s traditional detection, but also use triple detection to achieve a more accurate degree of detection of the uploaded image to be uploaded, and improve the query efficiency of the originality detection through multi-dimensional search, and utilize the on-chain storage to ensure that image fingerprints cannot be tampered with [
42,
43].
4.1. Image Copyright Registration Process
Image copyright registration protection and management method based on blockchain, and deep learning firstly accepts the user’s registration application [
44] through the copyright registration organization. After verifying the user’s identity, the copyright registration organization conducts a double query for detecting the originality of the image to be registered, which includes an off-chain query and an on-chain query. The off-chain query is conducted by the copyright registration institution accepting the application using the image fingerprint and the off-chain query summary. When the off-chain query passes, i.e., no similar image is found, the image fingerprint generated by the improved hash algorithm and the on-chain query summary are used to conduct a blockchain query to determine the originality detection results. When both off-chain and on-chain detection passes, the MobileNetV2 model is used to extract image features and the library of copyrighted image features that have been uploaded for similarity calculation and finally determine the detection results.
When an image has passed the triple originality detection, the copyright registration organization stores the off-chain query digest of the image together with other image copyright data in a local database [
45]. It adopts the fuzzy commitment-based storage of the off-chain query digest to improve the security when querying, and to ensure the tamperability of the image fingerprints [
46]. The blockchain registration system stores the on-chain query summaries of the images that have passed the originality detection together with the user identification information (e.g., user address) in the blockchain with the structure of the MKD tree to ensure the tamperability of the on-chain query summaries and improve the efficiency of the on-chain query. At the same time, it supports the user that has registered the copyright to conduct the query based on the identification [
47].
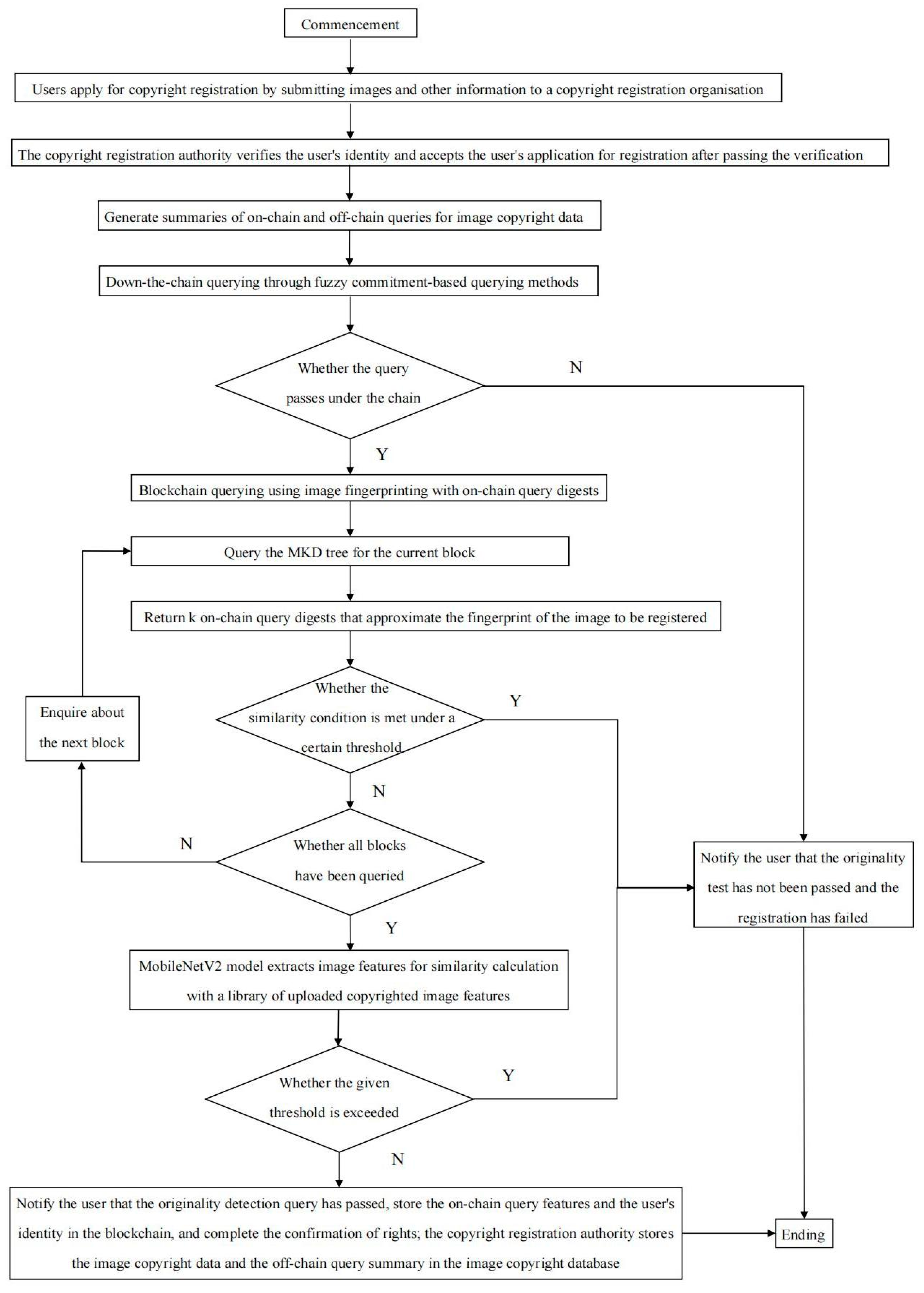
As shown in
Figure 7, the specific steps of the image copyright registration method based on blockchain and deep learning are as follows:
First, (image copyright registration user) sends an application for image copyright registration to (image copyright registration organization) and submits identity information and the image to be registered .
Secondly, verifies the identity of after receiving the copyright registration application, obtains the image to be registered at , and then performs a triple originality detection query, including the off-chain query, the on-chain query, and the MobileNetV2 convolutional neural network query.
Once again, returns a notification that failed the originality test and registered a failure, and the query is closed.
Finally, encrypts and uploads the user identification of the copyright registration and the on-chain query feature of the image to the copyright blockchain, and stores them in the MKD tree structure to complete the copyright confirmation. It uses and the fuzzy commitment function to generate the off-chain query digest , and stores the confirmed image files and other copyright information together with the off-chain query digest in the image copyright database.
4.2. Experimental Results and Analysis
In this subsection, we will conduct experiments on the image copyright registration protection and management method based on blockchain and deep learning designed in this paper to verify the effectiveness and feasibility of the improved image infringement detection scheme by fusing perceptual hash and the MobileNetV2 model. By comparing the experimental data, the performance of the scheme is evaluated in terms of detection precision, recall rate, F1 score, and other indicators, and compared with the traditional method.
4.2.1. Experimental Environment
The hardware environment for this system experiment is CPU: Intel Xeon E5-2680 v4 @ 2.40 GHz; GPU: NVIDIA Tesla V100 32 GB (GPU driver version: CUDA 11.2, cuDNN 8.1.0); RAM: 128 GB DDR4; Storage: 1 TB SSD; Software environment is OS: Ubuntu 20.04 LTS; Deep Learning framework: TensorFlow 2.5.0, Keras 2.4.3; Programming language: Python 3.8; Other tools: OpenClow 2.5.0, Keras 2.4.3; Other tools: Python 3.8 Ubuntu 20.04 LTS; Deep Learning framework: TensorFlow 2.5.0, Keras 2.4.3; Programming language: Python 3.8; Other tools: OpenCV 4.5.2, NumPy 1.19.5, Pandas 1.2.4, Matplotlib 3.3.4; Python dependency library version: scikon, cuDNN 8.1.0; Storage: 1TB SSD. Dependent library versions are: scikit-learn = 0.24.2 (for evaluation metrics calculation), scipy = 1.6.2 (for DCT calculation), seaborn = 0.11.1 (for visualization).
Two datasets are constructed for the experimental data: the COCO dataset, where 100,000 images are randomly selected as the training set and 10,000 as the validation set. For the infringement dataset, 1000 images from the COCO test set are tampered with to generate infringement samples (positive samples), and 1000 untampered images from the COCO validation set are randomly selected as non-infringement samples (negative samples). The tampering methods in the positive samples include light tampering: random cropping (retaining 80% of the region), brightness adjustment (±20%), and adding Gaussian noise (σ = 0.05); and heavy tampering: interpolation reduction after scaling to 50%, local blurring (5×5 Gaussian kernel), and superimposed text watermark. The infringement dataset was divided into a training set, validation set, and test set by 8:1:1.
The image needs to be preprocessed before the experiment starts: image normalization is performed by scaling to 224 × 224 (bilinear interpolation) and grayscaling (OpenCV cv2.COLOR_BGR2GRAY). By using scipy.fftpack.dct to calculate the frequency domain for DCT conversion, the original 8 × 8 low-frequency sampling matrix is extended to 16 × 16 (covering more medium and high-frequency information), the mean value of the extended matrix is calculated, and a 256-bit hash is generated (1 means ≥ the mean value, 0 means < the mean value) to binarize the image, completing the improvement of perceptual hash generation. Normalize the pixel values to [−1, 1] as MobileNetV2 input for processing.
4.2.2. Model Training and Process Implementation
Load ImageNet on MobileNetV2 model configuration for pre-training weights and fine-tune it. The first 150 layers were frozen and only the last two convolutional blocks and the fully connected layer were trained using Adam optimization (initial learning rate 1 × 10
−4, decaying to 0.5 of the original value every 10 epochs) [
48], with a loss function of weighted cross-entropy (infringement samples weight = 2 to mitigate category imbalance) [
49] The Epochs 50 early stopping strategy is used in the training details, and the validation set loss terminates when it does not decrease for five consecutive times [
50]. Optimization for perceptual hash thresholding mainly uses the Hamming distance for hash similarity computation. The threshold selection on the optimal Hamming distance threshold is determined by the validation set (e.g., distance ≤ 5 is judged as similar).
Triple detection is performed on the images of the dataset according to the process of
Figure 7.
Off-chain detection: Calculate the improved perception hash of the image to be uploaded and compare it with all the hashes in the database. If there is a record with Hamming distance ≤ threshold, it is labeled as “suspected infringement”, otherwise it goes to the next stage.
On-chain detection (simulation): Assuming that all hash values are stored on the chain, use smart contracts to simulate hash matching (simulated by local databases in actual tests).
MobileNetV2 model detection: Input image is reasoned by the model and the probability of infringement is output. Set the classification threshold (e.g., 0.5), and above the threshold it is judged as infringement.
4.2.3. Rationale and Proof of Mathematical Models
DCT frequency domain transformation is to convert the image grayscale matrix
to the frequency domain matrix
after DCT, as shown in Equation (6), where
is the image size and
indicates the frequency domain coefficients, DCT concentrates the image energy in the low-frequency region, which is suitable for extracting the main features of the image [
51]. Then, the original 8 × 8 low-frequency region is extended to 16 × 16 to cover more medium and high-frequency components and enhance the contour detail-capturing ability [
52].
where
is the size of the image (assumed to be
),
is the gray value of the image at position
, and
is the frequency domain coefficient.
In the binarized hash generation of the image should first calculate the matrix mean value based on Equation (7) and then generate the hash bits [
53] by Equation (8).
where
is the mean of the frequency domain matrix,
is the frequency domain coefficients, and
is the generated hash bits.
A collision proof is also required, i.e., if the two images are hashed with a Hamming distance
(threshold), then their similarity probability is
where
is the single-bit matching probability,
is the threshold for the Hamming distance, the experiment measured the misjudgment rate
at
, which meets the practical application requirements [
54].
For the weighted cross-entropy loss, balancing positive and negative samples, the loss function is
where
is the weighted cross-entropy loss,
is the total number of samples, and
is the true label (0 or 1) of the sample
, and
is the model’s predictive probability for sample
.
mitigates the problem of sparse infringement samples.
In terms of completeness of fusion detection, let the detection rate of the sensed hash be
, and the detection rate of MobileNetV2 be
, then the total detection rate of the system is
where
is the leakage rate of the sensed hash,
is the leakage rate of MobileNetV2, and
denotes the probability that at least one method detects the target. Experimentally measured
,
, then
0.98 are close to the theoretical optimum.
4.2.4. Performance Analysis of Digital Image Copyright Infringement Detection
In this paper, a baseline method is used to compare traditional perceptual hashing (using 8 × 8 DCT 64-bit low-frequency hashing), MobileNetV2 alone (direct output of infringement probability, no hash prescreening), and other hashing methods (including aHash, dHash). Evaluation metrics include classification metrics: Accuracy, Recall, F1 score, and AUC. Efficiency metrics: single image detection time (off-chain + on-chain + model). Robustness metrics: detection sensitivity to different degrees of tampering.
Additionally, the experiment was analyzed for significance using a paired t-test (α = 0.05) comparing the F1 scores of the fusion scheme with the baseline method, and the results obtained were with traditional perceptual hashing: p = 1.2 − 8 (significant) and with MobileNetV2 alone: p = 0.003 (significant).
4.2.5. Experimental Conclusions and Discussion
In terms of detection accuracy, the improved fusion scheme of perceptual hashing with MobileNetV2 achieves 93% accuracy and 89% recall on the test set, which significantly outperforms traditional perceptual hashing (72% accuracy) and MobileNetV2 alone (86% accuracy). The F1 score of the fusion scheme is 0.91, indicating a good balance between accuracy and recall. The AUC of the fusion scheme is 0.95, which is close to the perfect classifier (AUC = 1), indicating that the model performs well under different thresholds.
In terms of robustness, the improved perceptual hash achieves a detection success rate of 85% under mild tampering (e.g., brightness adjustment, local blurring), and maintains a success rate of 70% under heavy tampering (e.g., scaling + noise), which is significantly better than that of the traditional perceptual hash (45%). The MobileNetV2 model performs well under complex tampering (e.g., adding watermarks), with a detection success rate of 84%.
In terms of detection efficiency, the total detection time of the single image detection fusion scheme is 120 ms, of which 40 ms are accounted for off-chain detection, 15 ms for on-chain detection, and 65 ms for model inference. Although the detection time of the fusion scheme is slightly higher than that of MobileNetV2 alone (95 ms), it reduces the number of model calls by 75% through the off-chain prescreening, which significantly reduces the overall system load and is suitable for high concurrency scenarios.
In summary, the image copyright registration protection and management method based on blockchain and deep learning proposed in this paper can quickly screen out suspected infringing images by improving the perceptual hash for off-chain detection and reducing the subsequent computational load, and on-chain detection utilizes the tamperability of the blockchain to ensure the authenticity and traceability of the hash value, and the MobileNetV2 model provides a high-precision final determination to make up for the hashing method’s deficiencies. The triple detection mechanism can effectively defend against counterattacks (such as targeted modification of local features to bypass a single detection).
4.2.6. System Scalability Analysis
In terms of computational complexity, the computational complexity of the improved perceptual hash generation DCT transform is , where is the image size. For a 224 × 224 image, the single DCT computation time is about 10 ms (CPU). Extending the 8 × 8 low-frequency region to 16 × 16 increases the computation, but the computation time can be reduced to less than 2 ms by GPU acceleration (e.g., CUDA implementation). In addition, the complexity of the binarization operation is , which can be optimized by the SIMD (Single Instruction Multiple Data Stream) instruction set.
For distributed processing, images can be processed in chunks and hashes can be computed in parallel using multi-core CPUs or GPU clusters. Also, we used Local Sensitive Hashing (LSH) or Bloom Filter to reduce the Hamming distance query complexity from to .
In terms of inference efficiency, MobileNetV2 has a single image inference time of 65 ms (Tesla V100) and a theoretical throughput of 15 images/s (single GPU). The throughput can be increased to 100 images/s (batch size = 64) by dynamically adjusting the batch size. At the same time, it can be scaled horizontally by deploying a multi-instance model using TensorFlow Serving or TorchServe, which distributes requests through load balancing. Multi-GPU parallelism can also be used, with a theoretical throughput of up to 400 sheets/s on four GPU nodes.
5. Innovativeness and Feasibility
The problem of infringement regarding image copyright in e-commerce activities has always been a difficult issue in the field of e-commerce protection. The traditional centralized copyright management method has many defects in solving the digital infringement problem due to its cumbersome process, high cost, difficulty in managing data, and long period of confirming rights. In the following, the image copyright registration protection and management method based on blockchain and deep learning proposed in this paper will be summarized through the technical architecture aspect, functionality aspect, performance aspect, and applicability aspect:
Typical representatives of AI copyright systems in the technical architecture of existing systems are YouTube’s Content ID, and Google’s Vision API, whose technical features are based on deep learning models (e.g., CNN) for content recognition, relying on centralized servers for data processing and storage, but lacking the ability to robustly detect tampered images. The typical representatives of existing blockchain copyright systems are KodakOne and Po.et. Their technical features are using blockchain to store copyright information (e.g., hashes, timestamps) and relying on smart contracts to realize copyright transactions and authorization, but they lack efficient content detection capabilities and usually need to manually upload copyright information.
The triple detection mechanism proposed in this paper improves perceptual hashing to quickly screen suspected infringing images through off-chain detection, utilizes blockchain to store the hash value to ensure that the data cannot be tampered with through on-chain detection, and provides high-precision infringement determination through MobileNetV2 model detection. Combines the advantages of traditional image processing (perceptual hashing) and deep learning (MobileNetV2). Ensure data credibility and traceability through blockchain, support large-scale data processing, and efficient query. From the experimental data above, it can be seen that the improved perceptual hashing significantly improves the tamper resistance, and the system combines the complementary nature of hashing and modeling to perform optimally in complex tampering scenarios. Therefore, the triple detection mechanism covers the whole process from fast screening to high-precision determination, while the improved perceptual hash enhances the detection ability of tampered images, and the blockchain storage ensures the data’s non-tamperability and traceability.
The functions of existing AI copyright systems are embodied in content identification, infringement detection, and copyright management, but they have limited ability to detect tampered images, rely on centralized servers, have single-point-of-failure risks, and lack protection of user privacy. The functions of existing blockchain copyright systems, on the other hand, are only embodied in copyright registration, transaction, and authorization, lack efficient content detection capabilities, usually require manual uploading of copyright information, have high storage costs, are difficult to support large-scale data, and the automatic execution of smart contracts may conflict with the traditional legal framework.
The image copyright registration protection and management method based on blockchain and deep learning proposed in this paper, on the other hand, realizes efficient and accurate infringement detection through a triple detection mechanism. Blockchain is utilized to store the hash value to ensure the non-tampering of copyright information. User privacy is protected through chaotic encryption technology while supporting large-scale data processing and efficient queries.
The detection accuracy of existing AI copyright systems is high for untampered images (over 90%) but low for tampered images (50–70%). The detection time for a single image is about 100 ms (GPU dependent). Although centralized storage costs are low, there is a risk of data leakage. Existing blockchain copyright systems lack efficient content detection capabilities and usually rely on the manual uploading of copyright information. High latency of on-chain operations (~10 min/block for Bitcoin). High on-chain storage cost (about 1200 USD/GB/year for Ether main chain).
The image copyright registration protection and management method based on blockchain and deep learning proposed in this paper has a detection accuracy of 93% for untampered images and 70–85% for tampered images. The triple detection mechanism significantly improves the detection accuracy and robustness. The detection time of a single image is 120 ms (40 ms for off-chain detection, 15 ms for on-chain detection, and 65 ms for model inference). It will support high concurrency scenarios through distributed architecture and GPU acceleration. Using IPFS + Filecoin hybrid storage, the cost is 2.5 USD/GB/year, significantly lower than pure on-chain storage. Truly high precision, high efficiency, and low cost.
The applicable scenarios of existing AI copyright systems are mostly content distribution platforms (e.g., YouTube, Spotify). It has limited ability to detect tampered images and relies on centralized servers, with the risk of a single point of failure. The applicable scenarios of existing blockchain copyright systems, on the other hand, are copyright registration and trading platforms (e.g., KodakOne, Po.et). Lack of efficient content detection capability. High storage cost, difficult to support large-scale data.
The triple detection system proposed in this paper is applicable to a wide range of scenarios, including digital content distribution platforms (e.g., music, video, and image libraries), social media infringement monitoring, and copyright registration and trading platforms. It is multifunctional, widely applicable, and scalable. It supports functions such as infringement detection, copyright registration, privacy protection, etc. It is applicable to a wide range of scenarios, has high versatility, and supports large-scale data processing through distributed architecture and storage optimization.
In summary, the triple detection mechanism created by the blockchain and deep learning-based image copyright registration protection and management method that integrates traditional perceptual hashing, deep learning and blockchain can effectively fill the capability gaps of existing schemes. Experimental data show that the F1 score (0.91) and tamper detection success rate (80%) are significantly better than the existing scheme, the distributed architecture supports ten million image processing, and the scalability is better than the centralized scheme. Blockchain deposit improves legal validity, and the MD5 chaotic encryption algorithm reduces the possibility of users stealing copyright information and ensures that image fingerprints are not tampered with. The triple detection mechanism can effectively counter sample attacks, and the improved hash maintains a 70% detection success rate even under heavy tampering. The whole process integrates blockchain and deep learning technology, which not only effectively solves the natural barriers of blockchain technology in the detection of image infringement and improves the accuracy of image originality detection, but also provides a new idea and new power for technology integration in the era of science and technology.
6. Practical Implications and Delimitations
In this paper, corresponding solutions are proposed for the current problems of digital image copyright protection applications based on blockchain and artificial intelligence technologies. However, the current research work still has the following aspects of improvement:
6.1. Blockchain Energy Consumption and Transaction Cost Management
On the issue of energy consumption, the high energy consumption of GPU clusters may lead to higher operating costs, especially when processing large-scale data. The energy consumption problem of blockchain nodes has not been fully solved, especially since the PoW consensus mechanism consumes ≈ 1000 kWh for a single transaction, which is not suitable for high-frequency infringement detection. In this regard, PoS (Ethernet 2.0 single transaction energy consumption ≈ 0.01 kWh) or PBFT can be used, which can effectively reduce energy consumption by 99% and is suitable for this system.
In terms of transaction costs, on-chain operations (e.g., hash storage, smart contract invocations) consume Gas, with the cost formula:
This can be optimized by using batch on-chain, off-chain calculation, and dynamic pricing. Packaging multiple hashes into a single transaction submission (e.g., ZK-Rollups), storing only the final detection results on-chain instead of intermediate data, and selecting low Gas Price time slots to submit transactions. As shown in
Table 6, the average daily transaction cost can be reduced from 50 USD (for a single submission) to less than 5 USD by batch processing and off-chain computation.
6.2. Blockchain Storage Limitations and Implications for Copyright Registration
Each node of the blockchain needs to store the complete historical data, resulting in a linear increase in storage costs with the amount of data, and a higher pressure on the storage of the whole node. If the infringement detection system processes 100,000 images per day, the annual on-chain storage demand is about: 105 × 256 bits/day × 365 ≈ 11.7 TB/year, and the on-chain storage cost (about 1200 USD/GB/year on the Ethernet main chain) is about 14,000 USD. At the same time, the number of transactions per second (TPS) of the blockchain is limited (e.g., Ethernet mainchain ≈ 15 TPS), and it may be congested at high concurrency. In this regard, a layered storage approach can be used, where only the hash digest (Merkle Root) is stored on the chain, and the full amount of data are stored in IPFS or Filecoin, ensuring tamperability through content addressing (CID). Meanwhile, a sharded blockchain (e.g., Zilliqa) is used to decentralize data to multiple sub-chains to improve parallel processing capabilities. Old data are periodically migrated to cold storage (e.g., AWS Glacier) to reduce the main chain load. As can be seen in
Table 7, the IPFS + blockchain hybrid solution strikes a balance between cost and reliability and is suitable for copyright registration scenarios.
6.3. Computational Resource Requirements and Algorithm Optimization
In terms of hardware, MobileNetV2 model inference relies on high-performance GPUs (e.g., Tesla V100), which require expensive hardware support for large-scale deployment. Although the DCT computation of perceptual hashing can be accomplished by CPU, GPU acceleration can significantly improve efficiency and further increase the hardware cost. In this regard, model compression techniques (e.g., quantization, pruning) can be used to reduce the computational requirements.
Deep learning hashing methods (e.g., DeepHash) can be introduced for perceptual hash improvement to enhance the discriminative ability of hash features. Further, you can explore multi-scale hash fusion to enhance sensitivity to local tampering. For model optimization you can use lightweight models (e.g., EfficientNet) instead of MobileNetV2 to reduce the computational cost. You can also introduce self-supervised learning to reduce the dependence on labeled data.
6.4. Data Privacy and Legal Issues
The GDPR requires that the processing of personal data be transparent and lawful, and ensures the rights of data subjects (e.g., access, deletion, correction). The CCPA gives California residents the right to control their personal data, including the right to object to the sale of data. Transparency in blockchain can lead to the disclosure of sensitive information, especially in copyright registration scenarios where users may be reluctant to disclose image hashes. The system may involve personal data (e.g., face, geolocation) when processing images uploaded by users, and needs to ensure that the data are anonymized or that the user gives explicit consent. This can be performed by using ZKP technologies (e.g., zk-SNARKs) to protect the privacy of user-uploaded content, ensuring that the data on the chain is not visible but verifiable, and providing a clear privacy policy that specifies the scope and purpose of data use. You can explore homomorphic encryption techniques to support direct computation on encrypted data. A federated learning framework can also be introduced to localize data processing and avoid uploading sensitive data to a central server. You can mprove global model performance through model aggregation while protecting user privacy.
In addition, different countries and regions have strict restrictions on cross-border data transfers (e.g., the EU’s GDPR, China’s Data Security Law), so if the system is deployed in more than one country, it is necessary to ensure that the data storage and processing complies with local regulations. To this end, a localized deployment strategy can be adopted to ensure that data are stored in the user’s country or region. One can use blockchain sharding technology to decentralize data storage in nodes in different geographic regions.
The current legal validity of blockchain deposits has not been fully clarified in different countries. If the blockchain deposit certificate is not legally recognized, the credibility of the system will be greatly reduced. Therefore, the legal recognition of blockchain depositary certificates should be promoted (e.g., China’s Blockchain Information Service Administrative Regulations). One can ntroduce a third-party notary to enhance the credibility of the depository. Also note that the automatic execution of smart contracts may conflict with traditional legal frameworks, and design flexible smart contracts that allow for manual intervention and adjustment. One can cooperate with legal organizations to ensure that smart contracts comply with local legal requirements.
In the area of copyright, cooperation with legal organizations should be made to ensure that the results of the system’s testing meet legal standards of evidence. One can introduce a multi-party verification mechanism (e.g., manual review) to enhance the credibility of the results and introduce a contextual analysis module to determine whether it constitutes fair use in combination with the usage scenario. One can provide a manual complaint channel to allow users to submit proof of fair use, and prevent systematic misjudgment or omission, which may lead to legal disputes. In addition, as copyright laws differ from country to country, the system needs to adapt to multinational legal frameworks and cooperate with multinational legal organizations to establish unified copyright protection standards. One can provide multi-language and multi-legal framework support to ensure the applicability of the system globally.
In addition, the system needs to provide transparent reports on system operations to facilitate review by regulators. One can establish a cooperative relationship with regulators to ensure that system design and operation comply with regulatory requirements. One can design data access control mechanisms to ensure that only authorized personnel have access to sensitive data during regulatory audits and provide anonymized versions of data to meet audit requirements while protecting privacy.
7. Summary
The research focuses on the chaos of image copyright infringement in the e-commerce field and proposes a method for image copyright registration, protection and management based on artificial intelligence and blockchain technology. It queries and determines the originality of images through visual content, supports originality detection queries and user copyright information queries, and improves the efficiency of blockchain image copyright registration. For digital images that meet the registration requirements, the copyright data of the images is stored on the blockchain for rights confirmation. This design can be roughly divided into two parts: improve the hash algorithm and add chaotic encryption sequence for blockchain technology to optimize the aforementioned deficiencies of the current blockchain technology, and design an originality detection system for deep learning technology to make up for the natural technical barriers of blockchain technology. Finally, the two are combined with being used for the overall process of image detection, and a block storage structure based on the MKD tree is proposed to ensure the tamperability of image fingerprints using on-chain storage. The specific program is as follows:
(1) A blockchain-based image copyright management method is designed. Improvements are made to the problem of poor robustness of traditional image-aware hashing, and the spatial sampling rate in the frequency domain is improved to enhance the accuracy of originality detection. The chaotic encryption sequence is utilized to protect the uplinked image data so that the copyright data stored on it will not be maliciously tampered with, and at the same time to ensure that the stored data are safe, trustworthy, and traceable.
(2) Design a deep learning-based MobileNet V2 image originality detection method as a detection barrier after the uploaded image interacts with the blockchain. The images after passing the off-chain detection and on-chain detection are extracted the feature values through the MobileNet V2 model and compared according to the similarity between the features of the uploaded images and the confirmed images, aiming to determine the image copyright infringement in an all-round and highly accurate way.
(3) A blockchain-based image copyright registration protection method is proposed. Using image multidimensional data with fuzzy commitment to generate on-chain and off-chain query summaries to ensure the safe storage of image off-chain summaries, firstly completing the off-chain query within the organization during originality detection, and at the same time using the approximate query of on-chain summaries to determine the originality of the image to be registered. A block storage structure based on the MKD tree is proposed to ensure the tamperability of image fingerprints using on-chain storage.