Machine Learning for Physical Layer in 5G and beyond Wireless Networks: A Survey
Abstract
:1. Introduction
| Key Performance Indicator (KPIs) | 4G-LTE | 5G | 6G |
|---|---|---|---|
| Deployment year | 2000 | 2020 | Yet to be implemented |
| Core architecture | Internet | Internet | Internet |
| Core networking | Internet | Internet | Internet |
| Multiplexing bandwidth | OFDMA/SC-FDMA | BDMA/FBMC | OMA/NOMA |
| (1.4 Mhz–20 Mhz) | (60 GHz) | (up to 3 THz) | |
| Per device peak data rate | 1 Gbps | 10 Gbps | 1 Tbps |
| Switching | Packet switching | Packet switching | Packet switching |
| Forward error correction | Turbo codes | LDPC codes | LDPC codes |
| E2E latency | 100 ms | 10 ms | 1 ms |
| Maximum spectral efficiency | 15 bps/Hz | 30 bps/Hz | 100 bps/Hz |
| Mobility support | Up to 350 km/h | Up to 500 km/h | Up to 1000 km/h |
| Satellite integration | No | No | Fully supported |
| AI supported | No | Partially supported | Fully supported |
| Autonomous vehicle supported | No | Partially supported | Fully supported |
| XR supported | No | Partially supported | Fully supported |
| Haptic communication | No | Partially supported | Fully supported |
| Visible light communication (VLC) | No | No | Yes |
| Maximum frequency | 6 GHz | 90 GHz | 10 THz |
| Architecture | MIMO | Massive MIMO | Intelligent surface |
| Service Level | Video | AR, VR | Tactile |
| Connectivity density | 105 Devices/km | 106 Devices/km | 107 Devices/km |
| Area traffic capacity | 0.1 Mb/s/m | 10 Mb/s/m | 1 Gb/s/m |
| Network energy efficiency | 1× | 10–100× of 4G | 10–100× of 5G |
| Spectrum efficiency | 1× | 3× of 4G | 5–10× of 5G |
| Reliability | 99.99 | 99.999 | 99.99999 |
Contribution
2. 5G Technology
2.1. 5G Network Architecture
| 5G Network Technologies | Key Aspect | References |
|---|---|---|
| Centralized architecture C-RAN (Cloud-RAN) | 1. RAN as a Service (RAAS) capabilities. | [29,30,31,32,33,34,35,36], |
| 2. Boosts the network performance and highly favorable in low latency. | ||
| 3. Offers to reuse infrastructure, pool resources, support multiple technologies, decrease energy usage, create a heterogeneous and self-organizing structure, and reduce the costs associated with CAPEX and OPEX. | ||
| 4. Also allows other network operations in a data center environment. | ||
| Multi-access edge computing (MEC) | 1. Support for ultra-low latency, interoperability, virtualization, high bandwidth, augmented reality, strengthens security and compliance. | [37,38,39,40,41,42,43,44,45] |
| 2. Optimized local content distribution and data caching. | ||
| Network functionvirtualization (NFV) | 1. Supports longer life cycles for network hardware. | [46,47,48,49,50,51,52,53,54] |
| 2. Reduced space needed for network hardware, power consumption, maintenance, and hardware costs. | ||
| 3. Ease in network upgrades. | ||
| Network Slicing (NS) | 1. Improve performance. | [55,56,57,58,59,60,61] |
| 2. Protecting sensitive data. | ||
| 3. CAPEX and OPEX can also be reduced. | ||
| 4. Offers various services based on the requirements. | ||
| 5. Effective and efficient utilization of resources | ||
| 6. Improves operational efficiency. | ||
| 7. Overcomes all the drawbacks of DiffServ. | ||
| Beamforming (BF) | 1. Improves the spectral efficiency. | [62,63,64,65,66,67,68,69] |
| 2. Boosts cell range and capacity. | ||
| 3. mmWave offers a large bandwidth. | ||
| 4. Support for higher path loss and blockage scenarios. | ||
| Enhanced Common Public Radio Interface (eCPRI) | 1. Supports carrier aggregation, downlink CoMP, MIMO, uplink L1 Comp. | [70,71,72,73,74,75,76,77] |
| 2. Reduces jitter and latency for high priority traffic. | ||
| 3. Ease in troubleshooting at the lower layers. | ||
| 4. Reduced bandwidth is required. | ||
| 5. Software upgradable interfaces. | ||
| 6. Ethernet can carry eCPRI traffic. | ||
| 7. Saves electricity. | ||
| 5G Spectrum and Frequency | 1. Multiple frequency ranges. | [78,79,80,81,82,83,84,85] |
| 2. Supports higher frequencies, wide-area, outside-in coverage, deep indoor coverage, reliability, spectral efficiency, and the M2M type of communication. | ||
| 3. Supports very high throughput services for eMBB, and industrial IoT. | ||
| 4. Provides a balance between throughput, coverage, quality, and latency. |
- Increased spectrum, bits, and reliability:For proper working and operation, the sub-6 GHz spectrum must deliver increased bits, a large spectrum, and increased reliability [93]. Fifth-generation networks are a standalone approach to provide services for the latest technological applications, such as wireless brain–computer interactions, abbreviated as BCI [94,95]; extended reality services, abbreviated as XR [96]; connected robotics and autonomous systems, abbreviated as CRAS [97]; distributed ledger technologies, abbreviated as DLT [98]; and much more. This is possible only by exploring more spectrum resources and achieving higher reliability ratios at high-frequency bands.
- Using volumetric spectral efficiency and metamaterials:5G demands the use of volumetric spectrum efficiency and energy efficiency, abbreviated as SEE, with bps/Hz/m/Joules units. Along similar lines, 6G requires the support of XR, CRAS, DLT, BCI devices, and flying vehicles, which would not be possible without aerial bandwidths. Furthermore, the 3D evolutionary architecture of 6G requires active surfaces, smart, or intelligent coverings to transmit signals instead of deploying a conventional base system [99].
- Moving from a centralized to distributed data approach:Due to the continuous transformation of data from large, big, and centralized to a small and distributed approach, 5G must furnish its infrastructure to provide services for current centralized and future distributed data. This is one of the most crucial trends of 5G required for ML, and small data analytics [100].
- Implementing wearable devices:5G creates a space for smart body implementation, wearable devices, and integrated handsets. All these devices operate through human sensory inputs [101].
- Focusing self-sustaining networks:The technologies upheld by 5G and beyond demand intuitive networks instead of self-organizing networks, supported by previous cellular generations. These self-sustaining networks bring instantaneous sources, network operations, and optimization traits. Furthermore, the network can perform and explore dynamic environmental conditions, states, and key performance indicators [102]. Thus, beyond 5G networks (B5G) create artificial learning, quantum computing (QC), and quantum machine learning (QML) skill sets [103].
- Enhancing communication premises:From 1G to 4G, the primary purpose of these generations is to serve wireless communication, but 5G has slightly different premises. 3CLS stands for communication, computing, control, localization, and sense, which is potentially given by 6G, allowing it to become a multi-purpose generation. The design of 5G must evolve in a way to achieve all the 3CLS services and bring something valuable for real-time applications [104].
| 5G Network Architecture | Key Aspect | References |
|---|---|---|
| IIoT MEC based Architecture | 1. Supports industrial IoT (IIoT), smart energy, wearables, environment monitoring, gaming, AR/VR, autonomous vehicles, healthcare and remote surgery, smart city/home. | [105,106,107,108,109,110,111,112] |
| TelcoFog Architecture | 1. Providing unified cloud and fog resources for deploying NFV, MEC, and IoT services. | [113,114,115,116,117,118,119,120] |
| 2. Distributed and programmable fog technologies. | ||
| 3. Supports HVAC service. | ||
| 4. Secure, highly distributed. | ||
| 5G IoT Architecture | 1. Supports nano-chip, millimeter wave, heterogeneous networks, device-to-device communication, 5G-IoT, machine-type communication, wireless network function virtualization, wireless software defined networks, advanced spectrum sharing and interference management, mobile edge computing, mobile cloud computing, data analytics and big data. | [121,122,123,124,125,126,127,128] |
| Blockchain-Based Architecture | 1. Cost-effective, scalable, secure, and handles various vehicular network issues in a smart city. | [129,130,131,132,133,134,135,136] |
| 2. Provides ledger and smart contract (chaincode) services to applications. | ||
| 3. Provides a decentralized and distributed network. | ||
| 4. Provides protection for the entire data life cycle. | ||
| 5. Prevents internal and privacy attacks. | ||
| 6. Distributed, reliable, and efficient authentication and traceability. | ||
| 7. Empowered data-driven networks. | ||
| 8. Supports several use cases; i.e., smart healthcare, smart city, smart transportation, smart grid, and UAVs. |
2.2. Next-Generation Wireless Networks (NGWN)
| 4G-LTE | 5G | 6G | |
|---|---|---|---|
| FeMBB, ERLLC, | |||
| Use cases | MBB | eMBB, URLLC, mMTC | umMTC, LDHMC, ELPC |
| Telemedicine | Autonomous vehicles, | ||
| Mobile TV/Pay, high-definition video, voice, mobile internet | VR/AR/360 video, | tactile/haptic internet, | |
| Applications | IoT, V2X, UHD videos, | space travel, holography, | |
| wearable devices, smart-city | Internet of Bio-Nano-Things | ||
| Slicing, cloud, | Virtual, software, | ||
| Network characteristics | Flat and all-IP | software, virtual | intelligent, cloud, slicing |
3. Physical Layer in 5G
| Domain | Key Aspect | Related Work |
|---|---|---|
| 1. Power delay profile. | [157,158,159,160,161,162,163,164] | |
| mmWave channel | 2. Doppler effect. | |
| characterization | 3. Multi-path and propagation. | |
| 4. LOS and N-LOS communication. | ||
| 1. Angle of arrival. | ||
| Adaptive beamforming. | 2. Antenna training. | [165,166,167,168,169,170,171] |
| 3. Adaptive beamforming. | ||
| 1. Overlapping sector. | ||
| Switched Beam | 2. Cost effective. | [172,173,174,175,176,177,178,179] |
| 3. Sectorized antenna model. | ||
| 1. MIMO small cell combination. | [180,181,182,183,184,185,186] | |
| 2. Inexpensive low-power component. | ||
| Massive MIMO systems | 3. High number of antennas per BS. | |
| 4. Coherent superposition of waveforms. | ||
| 1. Active and passive SI cancellation. | ||
| 2. Improved spectral efficiency. | ||
| Full duplex radio technology | 3. Decreased self interference (SI) and pathloss. | [187,188,189,190,191,192,193,194] |
| 4. Decreased crosstalk between Tx and Rx. | ||
| 5. Improved feedback and latency |
3.1. Signaling Techniques for 5G
| N | N | SCS f = 2 × 15 kHz | Supported Data (PDSCH, (PUSCH) | Supported Sync Blocks (PSS, PBCH) | Cyclic Prefix Type | Cyclic Prefix Length (s) | OFDM and Useful Symbol Length (s) | |
|---|---|---|---|---|---|---|---|---|
| 0 | 14 | 1 | 15 | Yes | Yes | Normal | 4.69 | 71.35/66.67 |
| 1 | 14 | 2 | 30 | Yes | Yes | Normal | 2.34 | 35.68/33.33 |
| 2 | 14 | 4 | 60 | Yes | No | Normal/Extd | 1.17 | 17.84/16.67 |
| 3 | 14 | 8 | 120 | Yes | Yes | Normal | 0.57 | 8.92/8.33 |
| 4 | 14 | 16 | 240 | No | Yes | Normal | 0.29 | 4.46/4.17 |
| Waveform | Filter Granularity | Time Orthogonality | Frequency Orthogonality | Spectral Efficiency | uRLLC | PAPR | Reference |
|---|---|---|---|---|---|---|---|
| UFMC | Subband | Orthogonal | Quasi-orthogonal | High | Better | High | [232] |
| OFDM | Whole Band | Orthogonal | Orthogonal | Medium | Better | High | [233] |
| F-OFDM | Subband | Non-orthogonal | Quasi-orthogonal | Medium | Better | Medium | [234] |
| GFDM | Subcarrier | Non-orthogonal | Non-orthogonal | Medium | Better | Low | [235] |
| FBMC | Subcarrier | Orthogonal | Orthogonal | High | Bad | Medium | [236] |
3.2. Massive MIMO and Beamforming
| Approach | Methodology | Advantages | Future Work | Related Work |
|---|---|---|---|---|
| Decreasing bit error rate | Approximate message passing algorithm for uplink detection | Efficient uplink detection and trade-off between complexity and performance | Large mMIMO | [265] |
| Training-based blind channel estimation | BER count | Complex algorithm | [266] | |
| Spectrum sensing | Direct localization algorithm based on source and location | Minimizes execution time and enhances spectrum accuracy | Higher computational complexity | [267] |
| Match filter pre-coding techniques for performance analysis of SE and BS antennas | Improves throughput and spectral efficiency | Enhanced channel information is required for the pilot signal | [268] | |
| Receiver design | Multi-user MIMO pre-coding schemes | Flexibility in system design | Limited to LOS environment only | [269] |
| TDD realization based on zero forcing and max ratio combining schemes for uplink M-MIMO system | Spectral efficiency improvement and design condition depends upon number of antennas and pilot reuse factor | Limited for small number of antennas | [270] | |
| Virtual uniform linear array and uniform cylindrical array | Better performance close to that in i.i.d. fading rayleigh channels | Propagation delay should be included | [271] | |
| Channel modeling | Gauss–Markov Rayleigh fading channel model in time-selective channels | Aggregate-rate achieved optimum results | Interference effect is not considered | [272] |
| Designed mMIMO correlated channel using MATLAB for pilot contamination | Achieves better performance by increasing more antennas at BS | Correlated channels reduce the overall performance | [273] | |
| Scheduling algorithm based on the downlink mMIMO system along with zero forcing (ZF) beamforming approach | Better results in terms of error performance, sum rate, throughput, and fairness | Need to test on more realistic model and for multi-antenna users | [274] |
3.3. Physical Layer Issues
- Near end crosstalk (NEXT):In NEXT, the aggressor signal performs couples with the victim signal in the opposite direction.
- Far end crosstalk (FEXT):In FEXT, both the victim and aggressor signal travel in the same direction [288].
4. Security and Privacy in 5G
| Standard Body | Work Groups | Focused Area | Breakthrough |
|---|---|---|---|
| Security architecture, security aspects, | TS 33.102,TR 33.899, | ||
| fraud information gathering system, | TS 22.031,TS 23.031, | ||
| cryptographic algorithm requirements, | TS 33.105,TR 33.901, | ||
| 3GPP | TSG SA WG3 | lawful interception requirements, | TS 33.106, TS 33.126, |
| security assurance specification, | TS 33.511,TS 33.326, | ||
| generic authentication architecture, | TS 33.220,TR 33.918, | ||
| network domain security. | TS 33.210,TR 33.810. | ||
| Security requirements and risks, | Report 1.4,Report 1.5, | ||
| security architecture and enablers, | Report 2.1,Report 2.3, | ||
| 5GPPP | Security WG | access control, slicing and MEC security, | Report 3.1,Report 3.2, |
| privacy and trust in 5G, | Report 5.2,Report 5.3, | ||
| security architecture and solutions, | Report 6.2,Report 6.3, | ||
| policy management and orchestration. | Report 6.4. | ||
| i2nsf | Network security function, | RFC8192,RFC8329, | |
| ipsecme | IPsec, | RFC9061,RFC8983, | |
| sacm | automation and continuous monitoring, | RFC8598,RFC8784, | |
| IETF | secdispatch | security dispatch, | RFC7632,RFC8248,RFC8412, |
| secevent | security events, | RFC8936,RFC8935,RFC8417, | |
| tls | transport layer security, | RFC8996,RFC8744,RFC8773, | |
| opsec | operational security. | RFC9099,RFC8704,RFC7707. | |
| Security consideration for 5G, | White paper V-1.0, | ||
| NGMN alliances | sustainable trust, | White paper V-1.0, | |
| NGMN | 5G end-to-end architecture framework, | White paper V-4.31, | |
| NGMN 5G security group | 5G security recommendations, | White paper V-1.0, | |
| 5G security network slicing. | White paper V-1.0. | ||
| Authentication mechanisms, | ETSI TR 103 692, | ||
| quantum cryptography, | ETSI TR 103 823, | ||
| Internet of Things, | ETSI TS 103 701, | ||
| ETSI | Cyber security | security threats analysis, | ETSI TR 103 743, |
| access control, | ETSI TS 103 532, | ||
| infrastructure cybersecurity. | ETSI TR 103 741. | ||
| Security assurance, | Recommendation X.1404, | ||
| security threats, | Recommendation X.1408. | ||
| security framework and requirements, | Recommendation X.1145, | ||
| ITU | SG-17 | secure protection guidelines, | Recommendation X.1146, |
| risk identification, | Recommendation X.1451, | ||
| guidelines for security services. | Recommendation X.1452. |
| Security Threat/Attacks | Targeted Network Elements | SDN | NFV | Cloud | Links | Privacy | References |
|---|---|---|---|---|---|---|---|
| Boundary attacks | Subscriber location | ✕ | ✕ | ✕ | ✕ | √ | [315] |
| Configuration attacks | Virtual switches and routers | √ | √ | ✕ | ✕ | ✕ | [316] |
| DoS attack | Centralized elements | √ | √ | √ | ✕ | ✕ | [317] |
| Hijacking attacks | SDN controller and hypervisor | √ | √ | ✕ | ✕ | ✕ | [318] |
| IMSI catching attacks | Subscriber Identity | ✕ | ✕ | ✕ | √ | √ | [319] |
| MITM attack | SDN communication | √ | ✕ | ✕ | √ | √ | [320] |
| Penetration attacks | Virtual resources and clouds | √ | ✕ | √ | ✕ | ✕ | [321] |
| IP spoofing | Control channels | ✕ | ✕ | ✕ | √ | ✕ | [322] |
| Resource attacks | Shared cloud resources | ✕ | √ | √ | ✕ | ✕ | [323] |
| Saturation attacks | SDN controller and switches | √ | ✕ | ✕ | ✕ | ✕ | [324] |
| Scanning attacks | Open air interfaces | ✕ | ✕ | ✕ | √ | √ | [325] |
| Encryption keys attack | Unencrypted channels | ✕ | ✕ | ✕ | √ | ✕ | [326] |
| Semantic-info attacks | Subscriber location | ✕ | ✕ | ✕ | √ | √ | [327] |
| Signaling storms attack | 5G core network elements | ✕ | ✕ | √ | √ | ✕ | [328] |
| TCP level attacks | SDN communication | √ | ✕ | ✕ | √ | ✕ | [329] |
| Timing attacks | Subscriber location | ✕ | ✕ | √ | ✕ | √ | [330] |
| User identity attack | User information databases | ✕ | ✕ | √ | ✕ | √ | [331] |
- Shared information:For each message in the physical layer, security has a confidential shield—unauthorized users cannot share and access information. However, in the case of PHY-SI, the medium is served to transfer both public and private information at once. Public and confidential information waveforms are superimposed at the transmitting antenna and follow the channel path.
- Secrecy rate:In physical-layer security, only a single secrecy rate is used to perform the protection of signals, and the design of the system is maintained to maximize this rate. However, in PHY-SI, a Pareto transmit scheme is used to optimize the capacity of the secrecy rate, and each service has a different transmitting rate. These transmitting rates then combine to form a secrecy platform.
- Security issues:PHY-SI suffers more interference as compared to physical layer security. Any unauthorized users can view public messages, and it is easy for them to create security breaches. Therefore, both confidential and public messages are accessed by insiders. To avoid such issues, encoding techniques should be restructured and modified. In this way, the superimposition of both messages results in their transmission without facing any interference issue.
- Coding schemes:PHY-SI performs a superposition coding technique at the transmission side; on the other end, the receiving side performs interference cancellation to obtain desired outcomes. Depending on the service type, PHY-SI uses different codebook formats for transmitting waveforms.
5. Challenges and Future Directions
- Business model and economic challenges for 5G network:Before 5G technology, telecommunication operators were providing services using integrated services (IntServ) and differentiated services (DiffServ) models, while 5G technology introduces eMBB, URLLC, and mMTC. Therefore, 5G is expected to meet the requirements (bandwidth and latency) of various vertical applications and services accordingly. Hence, the future network should be capable of new business models based on heterogeneously oriented services and provide the services in all use case scenarios. Business models for the network could be business to business (B2B), business to consumers (B2C), and business to business to consumer (B2B2C) [353]. Furthermore, we need to conduct detailed and comprehensive research to find out the real-time problems for all 5G use cases and embedded ML-based optimized solutions for the upcoming era.
- Collaboration of OTT and ISP for 5G service management:The quality of experience in vertical heterogeneous networks is one of the significant challenges. This can be achieved using QoE monitoring and QoE management theories. A collaboration between over-the-top providers (OTT) and internet service providers (ISP) needs to be established for QoE/QoS monitoring and measurement factors. Researchers have already proposed monitoring probes (passive) with OTT applications at UE to exchange information for desired QoS [354]. We need to find ML-based standardized interfaces, ML-based optimized level frequency, and ML-based tradeoffs between QoE and latency in network operations. This will have a high impact, and optimized ML-based algorithms can enhance network performance. Besides these issues, the scalability and effectiveness of QoE also need to be addressed.
- RAN virtualization in 5G network:RAN slicing, an integral part of virtualized 5G systems, is yet to be addressed because it is in the nascent phase. Docker and VM-based solutions do not address radio resource problems to an acceptable degree in terms of shared and multiple RATs in 5G networks. Hence, another challenge for RAN virtualization is RAN as a service (RaaS), where beyond physical infrastructure, radio resource sharing is crucial [355]. Furthermore, ML-based solutions are greatly needed for mobility management and the scheduling of radio resources as virtualized control functions to be implemented. The optimized RaaS will improve network performance and cost-effectiveness for the complex environment. At the same time, ML is needed to address system integration, achieving widespread adoption, technology support difficulties, and security risks.
- End-to-end slice orchestration and management:With the introduction of SDN and NFV in 5G networks, it is necessary to change the deployment, operation, and management of networks and find intelligent methods for how resources are to be orchestrated [356]. Recently, many projects have shown promise in this context; i.e., AT&T’s ECOMP project, OSM project, ETSI MANO framework, and ONAP project implementation. However, several challenges remain with these advancements, such as moving towards a concrete network slice from a high-level service description. Scalability and resilience are core services supporting multi-vendor case scenarios and entertaining upcoming 5G network elements. We need to find a way to manage all underlying slices and the E2E orchestration of all available resources while keeping the fact in view that all network slices must meet their service; e.g., services and experience level agreements (ELAs/SLAs).
- Mobility management in 5G networks:Fifth-generation networks will face mobility management issues due to the numbers of smart devices increasing exponentially, heterogeneous networks, ultra-dense small cell networks, fast-moving vehicles, and concerns about the truthfulness of information in vehicle-to-vehicle communications [357]. While due to the fixed position of devices in an industrial area, there is no need for mobility management, as they do not need to relocate, a number of researchers have proposed frameworks/solutions to handle mobility management in 5G networks. Automated driving services have different criteria than mobile broadband management; i.e., high-speed trains (e.g., 600 km/h) may trigger multiple handovers for railway communication [358]. Maintaining high priority for real-time services and seamless mobility support is crucial, so the requirements for automated driving services are different. Therefore, ML-based optimized and efficient methodologies are required that depend upon use cases, maintain service-aware QoE/QoS control in 5G systems, and enable users to maneuver between all SDN controllers in a 5G heterogeneous environment.
- Network sharing and slicing in 5G:Software-based platforms have the potential to make support for multi-tenancy more accessible using SDN/NFV based infrastructure in 5G systems. Therefore, multiple services and applications may be entertained successfully. This network sharing paradigm allows many virtual network functions to be set up on a similar 5G NFV platform and introduces various management challenges [359]. Vast amounts of research are required correlated to the isolation between slices, inter-domain services slicing, network functions placement within a slice, dynamic slice creation, and understanding the slicing concept’s performance in 5G networks. Besides other issues, QoS/QoE performance must also be ensured on every slice, neglecting network congestion and other slices’ performance levels.
- Security and privacy challenges in 5G networks:Providing various services, multiple network slices, and resource sharing for different verticals can introduce different levels of security concerns and privacy policy requirements in 5G networks [360]. Hence, complicated research challenges are raised and addressed considering the impact of one slice on another, efficient coordination mechanisms, and the impact of entire network systems, particularly in multi-domain infrastructures. Intelligent ML-based algorithms can meet these challenges and ensure network performance.
- Network reconstruction:Fifth-generation technology is envisioned to increase capacity, the density of connections, and energy efficiency with reliability while decreasing latency. At the network edge, 5G can also transmit touch-perception-type real-time communication; i.e., robotics and haptics equipment. In this respect, wide-ranging changes are required in network architecture, including the core and radio access network (RAN). Fifth-generation heterogeneous wireless networks are required to reconstruct RAN and CN architecture to support E2E to achieve an end-to-end latency of 1 ms in network slicing with the help of optimized ML-based methodologies. The cooperation of multiple RATs and macrocells with ultra-dense small cells in complex heterogeneous networks may confront these slicing demands [361].
- Fifth-generation technologies collaboration:Future 5G architecture demands the coexistence and cooperation of all conventional and recent technologies—i.e., broadband transmission, LTE/LTE-A systems, C-RAN, mmWave, massive MIMO, SDN, NFV, network slicing, and mobile cloud engineering (MCE)—to support all use cases of 5G [362]. On the other hand, ML will participate alone with one on one technology or manage the whole system intelligently. Besides combining the benefits of emerging technologies, there are still many crucial challenges to achieving the desired collaborative performance. Low-cost internet and the maximum digital transmission capacity of a channel are concerns for broadband transmission. Virtualization, BBU cooperation and clustering, and high fronthaul capacities are needed in C-RAN. In mmWave, the higher path loss due to higher carrier frequency and mMIMO, reciprocity error, signal-to-interference ratio (SIR), and channel coherence time requires an optimized solution. With ML, it is also necessary to choose the SDN solution; inter-operability, budget constraints, and security are primary concerns. The key challenges that need to be addressed using advanced ML-based algorithms are orchestration and integration in hybrid networks, slice isolation mechanism, security, and privacy.
- Backhaul 5G wireless network architecture design:It is a pivotal challenge to deploy a new backhaul network architecture design and security-aware protocols for heterogeneous ultra-dense small cell network use cases. The massive wireless network traffic caused congestion and later collapsed the backhaul network [363]. Motivations behind the backhaul wireless network architecture design are ML-based mobility within small cell networks and the optimization of the cell load distribution. Besides this, ML-based admission and congestion control algorithms are also required for quality of service and experience, mainly focused on the backhaul network.
- 11.
- Flash network traffic:The potential of large-scale events causing significant changes in network traffic patterns, either accidentally or maliciously, increases as the network capacity and the number of UEs grows. While maintaining an acceptable level of performance, the 5G system must prevent significant fluctuations in traffic utilization and be adaptable to them when they do occur. ML-based algorithms are capable of learning the environments and suggesting optimized outputs in these situations.
- 12.
- Security of radio interfaces:In existing internet generations, keys for radio interface encryption are obtained in the home core network and then sent to the visiting radio network using signaling channels such as SS7 or Diameter. When sent between network nodes, the exposed cipher key is an example of a GSM network. The connection between operators’ signaling systems should be adequately secured using ML so that the radio interface session keys can be transferred via SS7 and Diameter, and such exposure is prevented.
- 13.
- User plane integrity:There was no explicit user data plane or cryptographic integrity protection until the second-generation internet; in addition, the third and fourth generation have protection, but still not for user plane data. The transport layer, application layer, or bearer layer integrity with encryption is used if data integrity is required. There is also a risk of a man-in-the-middle attack, and session hijacking is also possible. In addition, the 5G network will not add integrity protection to user plane data but at the transport or application layer with the help of ML-based algorithms.
- 14.
- Mandated security in the network:There are service-driven restrictions in the security architecture, and generally, there are measures in place to minimize the effects of these restrictions, and these measures are often not mandatory in current cellular specifications. Reducing the security dependency on the access network and on the security provided on intranet interfaces is possible, but this dependency is unlikely to be eliminated entirely. The security measures using ML must be embedded in architectural design, and otherwise, the system will not work at all—this approach is the best solution to implement mandatory security.
- 15.
- Roaming security:While roaming from one network to another, updates on the security parameters of the user are greatly required, particularly in the 5G densification scenario. Ingress/egress firewall security policies, subscriber-level security, and personal firewalls are used to protect from security and privacy attacks, but the challenge is to provide these services to different subscribers in multiple locations. Hence, ML also provides an intelligent information-sharing mechanism for roaming security using network slices to address these challenges.
- 16.
- Signaling storms:Low-cost M2M devices have several limitations such as computational capabilities, energy support, and memory capabilities. At the same time, these low-cost devices can be compromised and allow DoS and DDoS attacks against the radio access network. Unexpected non-malicious events may also cause the devices to behave abnormally and produce “flash crowd” situations, leading to the exhaustion of radio resources. Hence, ML is required to provide an overload control (currently relying on MME) mechanism to prevent all devices from attempting to access the network, as well as to initiate the “START” and “STOP” and select UEs to target the overload procedures.
- 17.
- DoS and DDoS attacks:Fifth-generation networks are expected to support a number of network devices, while DOS and DDOS attacks will become a real threat designed to exhaust the physical and logical resources of the target. In this regard, network infrastructure and devices DOS attacks are common categories. Using these attacks, the attackers drain the network, logical, and physical resources of 5G users and devices accordingly. These challenges can be minimized by introducing ML-based approaches. Intelligent ML-based approaches can predict an attack using ongoing traffic and offer optimized network management. Network control elements can be hidden and revamp the unencrypted control channels.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| 5G | Fifth-generation |
| AIPN | All IP network |
| AI | Artificial intelligence |
| BBU | Base band unit |
| BS | Base stations |
| CN | Core network |
| CoMP | Coordinated multipoint |
| CRKG | Channel reciprocity-based key generation |
| CSI | Channel state information |
| DDoS | Distributed denial of service |
| DPC | Dirty paper coding |
| E-HARQ | Early hybrid automatic repeat request |
| ELAs/SLAs | Services and experience level agreements |
| EON | Elastic optical networks |
| GFDM | Generalized frequency division multiplexing |
| HetNet | Heterogeneous network |
| IntServ | Integrated services |
| IoT | Internet of Things |
| ISP | Internet service providers |
| KPIs | Key performance indicators |
| KQIs | Key quality indicators |
| LALP | Large-scale antenna linear processing |
| LDP | Low-density parity-check codes |
| LPF | Low pass filter |
| LSFD | Large-scale fading decoding |
| MCF | Multi-core fiber |
| MDAF | Management data analytic function |
| MIMO | Multiple-input and multiple-output |
| ML | Machine learning |
| MMTC | Machine-type communications |
| MRT | Maximum-ratio transmission |
| MRC | Maximum-ratio combining |
| NGMN | Next-generation mobile networks |
| NR | New radio |
| NSA | Non-standalone |
| NWDAF | Network data analytics function |
| OTFS | Orthogonal time–frequency spread |
| OTT | Over-the-top providers |
| PAPR | Peak-to-average power |
| PC | Polar codes |
| PCA | Principal component analysis |
| PHY-SI | Physical layer service integration |
| QoE | Quality of experience |
| QoS | Quality of service |
| RaaS | RAN as a service |
| RAN | Radio access networks |
| RLC | Radio link control |
| RRM | Radio resource management |
| RRU | Remote radio unit |
| RSS | Received signal strength |
| SDR | Software-defined radio |
| SE | Spectral efficiency |
| SNR | Signal-to-noise ratio |
| uRLLC | Ultra-reliable low latency communication |
| V2X | Vehicle to everything |
| WWWW | Worldwide Wireless Web |
References
- Al-samman, A.M.; Azmi, M.H.; Abd Rahman, T. A survey of millimeter wave (mm-Wave) communications for 5G: Channel measurement below and above 6 GHz. In Proceedings of the International Conference of Reliable Information and Communication Technology, Kuala Lumpur, Malaysia, 23–24 June 2018; pp. 451–463. [Google Scholar]
- Da Silva, M.M.; Guerreiro, J. On the 5G and Beyond. Appl. Sci. 2020, 10, 7091. [Google Scholar] [CrossRef]
- Patra, S.K.; Sundaray, B.K.; Mahapatra, D.M. Are university teachers ready to use and adopt e-learning system? An empirical substantiation during COVID–19 pandemic. In Quality Assurance in Education; Emerald Publishing Limited: Bentley, UK, 2021. [Google Scholar]
- Awwad, A. The impact of Over The Top service providers on the Global Mobile Telecom Industry: A quantified analysis and recommendations for recovery. arXiv 2021, arXiv:2105.10265. [Google Scholar]
- Gökarslan, K.; Sandal, Y.S.; Tugcu, T. Towards a URLLC-Aware Programmable Data Path with P4 for Industrial 5G Networks. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Lehr, W.; Queder, F.; Haucap, J. 5G: A new future for Mobile Network Operators, or not? Telecommun. Policy 2021, 45, 102086. [Google Scholar] [CrossRef]
- Rahman, M.T.; Bakibillah, A.S.M.; Parthiban, R.; Bakaul, M. Review of advanced techniques for multi-gigabit visible light communication. IET Optoelectron. 2020, 14, 359–373. [Google Scholar] [CrossRef]
- Guevara, L.; Auat Cheein, F. The role of 5G technologies: Challenges in smart cities and intelligent transportation systems. Sustainability 2020, 12, 6469. [Google Scholar] [CrossRef]
- Amin, R. Introduction of 5G as a Next-generation Mobile Network. ABC Res. Alert 2020, 8, 129–138. [Google Scholar] [CrossRef]
- Al-Absi, M.A.; Al-Absi, A.A.; Sain, M.; Lee, H.J. A State of the Art: Future Possibility of 5G with IoT and Other Challenges. Smart Healthcare Analytics in IoT Enabled Environment; Pattnaik, P., Mohanty, S., Mohanty, S., Eds.; Springer, Cham: Switzerland, 2020; pp. 35–65. [Google Scholar]
- Jagannath, J.; Polosky, N.; Jagannath, A.; Restuccia, F.; Melodia, T. Machine learning for wireless communications in the Internet of Things: A comprehensive survey. Ad Hoc Netw. 2019, 93, 101913. [Google Scholar] [CrossRef] [Green Version]
- Zikria, Y.B.; Afzal, M.K.; Kim, S.W.; Marin, A.; Guizani, M. Deep learning for intelligent IoT: Opportunities, challenges and solutions. Comput. Commun. 2020, 164, 50–53. [Google Scholar] [CrossRef]
- Qiu, J.; Wu, Q.; Ding, G.; Xu, Y.; Feng, S. A survey of machine learning for big data processing. EURASIP J. Adv. Signal Process. 2016, 2016, 1–16. [Google Scholar]
- Hou, T.; Feng, G.; Qin, S.; Jiang, W. Proactive content caching by exploiting transfer learning for mobile edge computing. Int. J. Commun. Syst. 2018, 31, e3706. [Google Scholar] [CrossRef]
- Wang, S.; Chen, M.; Liu, X.; Yin, C.; Cui, S.; Poor, H.V. A Machine Learning Approach for Task and Resource Allocation in Mobile-Edge Computing-Based Networks. IEEE Internet Things J. 2020, 8, 1358–1372. [Google Scholar] [CrossRef]
- Qin, M.; Yang, Q.; Cheng, N.; Zhou, H.; Rao, R.R.; Shen, X. Machine learning aided context-aware self-healing management for ultra dense networks with QoS provisions. IEEE Trans. Veh. Technol. 2018, 67, 12339–12351. [Google Scholar] [CrossRef]
- Akhtar, T.; Tselios, C.; Politis, I. Radio resource management: Approaches and implementations from 4G to 5G and beyond. Wirel. Netw. 2021, 27, 693–734. [Google Scholar] [CrossRef]
- Du, Z.; Deng, Y.; Guo, W.; Nallanathan, A.; Wu, Q. Green Deep Reinforcement Learning for Radio Resource Management: Architecture, Algorithm Compression, and Challenges. IEEE Veh. Technol. Mag. 2020, 16, 29–39. [Google Scholar] [CrossRef]
- Elsayed, M. Machine Learning-Enabled Radio Resource Management for Next-Generation Wireless Networks. Ph.D. Thesis, Université d’Ottawa/University of Ottawa, Ottawa, ON, Canada, 2021. [Google Scholar]
- Fourati, H.; Maaloul, R.; Chaari, L. A survey of 5G network systems: Challenges and machine learning approaches. Int. J. Mach. Learn. Cybern. 2021, 12, 385–431. [Google Scholar] [CrossRef]
- Ari, A.A.A.; Gueroui, A.; Titouna, C.; Thiare, O.; Aliouat, Z. Resource allocation scheme for 5G C-RAN: A Swarm Intelligence based approach. Comput. Netw. 2019, 165, 106957. [Google Scholar] [CrossRef]
- Valanarasu, M.R.; Christy, A. Comprehensive survey of wireless cognitive and 5G networks. J. Ubiquitous Comput. Commun. Technol. (UCCT) 2019, 1, 23–32. [Google Scholar]
- Amjad, M.; Musavian, L.; Rehmani, M.H. Effective capacity in wireless networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 3007–3038. [Google Scholar] [CrossRef] [Green Version]
- Shaik, N.; Malik, P.K. A comprehensive survey 5G wireless communication systems: Open issues, research challenges, channel estimation, multi carrier modulation and 5G applications. Multimed. Tools Appl. 2021, 80, 28789–28827. [Google Scholar] [CrossRef]
- Lin, X.; Lee, N. 5G and Beyond: Fundamentals and Standards; Springer Nature: Cham, Switzerland, 2021. [Google Scholar]
- Lei, W.; Soong, A.C.; Jianghua, L.; Yong, W.; Classon, B.; Xiao, W.; Mazzarese, D.; Yang, Z.; Saboorian, T. 5G system architecture. In 5G System Design; Springer: Berlin/Heidelberg, Germany, 2021; pp. 297–339. [Google Scholar]
- Penttinen, J.T. 5G Second Phase Explained: The 3GPP Release 16 Enhancements; John Wiley & Sons: Hoboken, NJ, USA, 2021. [Google Scholar]
- Pedersen, K.; Kolding, T. Overview of 3GPP New Radio Industrial IoT Solutions. In Wireless Networks and Industrial IoT; Springer: Berlin/Heidelberg, Germany, 2021; pp. 3–20. [Google Scholar]
- Lassoued, N.; Boujnah, N.; Bouallegue, R. Reducing Power Consumption in C-RAN Using Switch On/Off of MC-RRH Sectors and Small Cells. IEEE Access 2021, 9, 75668–75682. [Google Scholar] [CrossRef]
- Nakayama, Y.; Hisano, D.; Maruta, K. Adaptive C-RAN Architecture with Moving Nodes Toward Beyond the 5G Era. IEEE Netw. 2020, 34, 249–255. [Google Scholar] [CrossRef]
- Askri, A.; Zhang, C.; Othman, G.R.B. Distributed Learning Assisted Fronthaul Compression for Multi-Antenna C-RAN. IEEE Access 2021, 9, 113997–114007. [Google Scholar] [CrossRef]
- Wey, J.S.; Luo, Y.; Pfeiffer, T. 5G wireless transport in a PON context: An overview. IEEE Commun. Stand. Mag. 2020, 4, 50–56. [Google Scholar] [CrossRef]
- Thangappan, T.; Therese, B. Overview of Fronthaul Technologies and the DBA Algorithms in XGPON-Based FH Technology in CRAN Architecture in 5G Network. In Futuristic Communication and Network Technologies; Springer: Berlin/Heidelberg, Germany, 2022; pp. 271–280. [Google Scholar]
- Borges, R.M.; de Souza Lopes, C.H.; Lima, E.S.; de Oliveira, M.A.; Cunha, M.S.B.; Alexandre, L.C.; da Silva, L.G.; Pereira, L.A.M.; Spadoti, D.H.; Romero, M.A.; et al. Integrating Optical and Wireless Techniques towards Novel Fronthaul and Access Architectures in a 5G NR Framework. Appl. Sci. 2021, 11, 5048. [Google Scholar] [CrossRef]
- Iovanna, P.; Cavaliere, F.; Stracca, S.; Giorgi, L.; Ubaldi, F. 5G Xhaul and service convergence: Transmission, switching and automation enabling technologies. J. Light. Technol. 2020, 38, 2799–2806. [Google Scholar] [CrossRef]
- Pateromichelakis, E.; Gebert, J.; Mach, T.; Belschner, J.; Guo, W.; Kuruvatti, N.P.; Venkatasubramanian, V.; Kilinc, C. Service-tailored user-plane design framework and architecture considerations in 5G radio access networks. IEEE Access 2017, 5, 17089–17105. [Google Scholar] [CrossRef]
- Filali, A.; Abouaomar, A.; Cherkaoui, S.; Kobbane, A.; Guizani, M. Multi-access edge computing: A survey. IEEE Access 2020, 8, 197017–197046. [Google Scholar] [CrossRef]
- Taleb, T.; Samdanis, K.; Mada, B.; Flinck, H.; Dutta, S.; Sabella, D. On multi-access edge computing: A survey of the emerging 5G network edge cloud architecture and orchestration. IEEE Commun. Surv. Tutor. 2017, 19, 1657–1681. [Google Scholar] [CrossRef] [Green Version]
- Pham, Q.V.; Fang, F.; Ha, V.N.; Piran, M.J.; Le, M.; Le, L.B.; Hwang, W.J.; Ding, Z. A survey of multi-access edge computing in 5G and beyond: Fundamentals, technology integration, and state-of-the-art. IEEE Access 2020, 8, 116974–117017. [Google Scholar] [CrossRef]
- Liu, Y.; Peng, M.; Shou, G.; Chen, Y.; Chen, S. Toward edge intelligence: Multiaccess edge computing for 5G and Internet of Things. IEEE Internet Things J. 2020, 7, 6722–6747. [Google Scholar] [CrossRef]
- Singh, S.P.; Nayyar, A.; Kumar, R.; Sharma, A. Fog computing: From architecture to edge computing and big data processing. J. Supercomput. 2019, 75, 2070–2105. [Google Scholar] [CrossRef]
- Tufail, A.; Namoun, A.; Alrehaili, A.; Ali, A. A Survey on 5G Enabled Multi-Access Edge Computing for Smart Cities: Issues and Future Prospects. Int. J. Comput. Sci. Netw. Secur. 2021, 21, 107–118. [Google Scholar]
- Hsieh, H.C.; Chen, J.L.; Benslimane, A. 5G virtualized multi-access edge computing platform for IoT applications. J. Netw. Comput. Appl. 2018, 115, 94–102. [Google Scholar] [CrossRef]
- Khan, W.Z.; Ahmed, E.; Hakak, S.; Yaqoob, I.; Ahmed, A. Edge computing: A survey. Future Gener. Comput. Syst. 2019, 97, 219–235. [Google Scholar] [CrossRef]
- Ryu, J.W.; Pham, Q.V.; Luan, H.N.; Hwang, W.J.; Kim, J.D.; Lee, J.T. Multi-access edge computing empowered heterogeneous networks: A novel architecture and potential works. Symmetry 2019, 11, 842. [Google Scholar] [CrossRef] [Green Version]
- Kumar, M.S. Analysis of network function virtualization and software defined virtualization. JOIV Int. J. Informatics Vis. 2017, 1, 122–126. [Google Scholar] [CrossRef] [Green Version]
- Alam, I.; Sharif, K.; Li, F.; Latif, Z.; Karim, M.M.; Biswas, S.; Nour, B.; Wang, Y. A survey of network virtualization techniques for Internet of Things using SDN and NFV. ACM Comput. Surv. (CSUR) 2020, 53, 1–40. [Google Scholar] [CrossRef]
- Cheng, X.; Wu, Y.; Min, G.; Zomaya, A.Y. Network function virtualization in dynamic networks: A stochastic perspective. IEEE J. Sel. Areas Commun. 2018, 36, 2218–2232. [Google Scholar] [CrossRef]
- Qi, D.; Shen, S.; Wang, G. Towards an efficient VNF placement in network function virtualization. Comput. Commun. 2019, 138, 81–89. [Google Scholar] [CrossRef]
- Yi, B.; Wang, X.; Li, K.; Huang, M. A comprehensive survey of network function virtualization. Comput. Netw. 2018, 133, 212–262. [Google Scholar] [CrossRef]
- Mirjalily, G.; Luo, Z. Optimal network function virtualization and service function chaining: A survey. Chin. J. Electron. 2018, 27, 704–717. [Google Scholar] [CrossRef]
- Veeraraghavan, M.; Sato, T.; Buchanan, M.; Rahimi, R.; Okamoto, S.; Yamanaka, N. Network function virtualization: A survey. IEICE Trans. Commun. 2017, 2016NNI0001. [Google Scholar] [CrossRef] [Green Version]
- Yang, S.; Li, F.; Trajanovski, S.; Yahyapour, R.; Fu, X. Recent advances of resource allocation in network function virtualization. IEEE Trans. Parallel Distrib. Syst. 2020, 32, 295–314. [Google Scholar] [CrossRef]
- Shiomoto, K. Research challenges for network function virtualization-re-architecting middlebox for high performance and efficient, elastic and resilient platform to create new services. IEICE Trans. Commun. 2018, 101, 96–122. [Google Scholar] [CrossRef] [Green Version]
- Barakabitze, A.A.; Ahmad, A.; Mijumbi, R.; Hines, A. 5G network slicing using SDN and NFV: A survey of taxonomy, architectures and future challenges. Comput. Netw. 2020, 167, 106984. [Google Scholar] [CrossRef]
- Shah, S.D.A.; Gregory, M.A.; Li, S. Cloud-native network slicing using software defined networking based multi-access edge computing: A survey. IEEE Access 2021, 9, 10903–10924. [Google Scholar] [CrossRef]
- Chahbar, M.; Diaz, G.; Dandoush, A.; Cérin, C.; Ghoumid, K. A comprehensive survey on the e2e 5g network slicing model. IEEE Trans. Netw. Serv. Manag. 2020, 18, 49–62. [Google Scholar] [CrossRef]
- Afolabi, I.; Taleb, T.; Samdanis, K.; Ksentini, A.; Flinck, H. Network slicing and softwarization: A survey on principles, enabling technologies, and solutions. IEEE Commun. Surv. Tutor. 2018, 20, 2429–2453. [Google Scholar] [CrossRef]
- Zhang, S. An overview of network slicing for 5G. IEEE Wirel. Commun. 2019, 26, 111–117. [Google Scholar] [CrossRef]
- Kazmi, S.A.; Khan, L.U.; Tran, N.H.; Hong, C.S. Network Slicing for 5G and beyond Networks; Springer: Berlin/Heidelberg, Germany, 2019; Volume 1. [Google Scholar]
- Ben Azzouz, L.; Jamai, I. SDN, slicing, and NFV paradigms for a smart home: A comprehensive survey. Trans. Emerg. Telecommun. Technol. 2019, 30, e3744. [Google Scholar] [CrossRef]
- Rumyancev, I.A.; Korotkov, A.S. Survey on beamforming techniques and integrated circuits for 5G systems. In Proceedings of the 2019 IEEE International Conference on Electrical Engineering and Photonics (EExPolytech), St. Petersburg, Russia, 17–18 October 2019; pp. 76–80. [Google Scholar]
- Alsaba, Y.; Rahim, S.K.A.; Leow, C.Y. Beamforming in wireless energy harvesting communications systems: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 1329–1360. [Google Scholar] [CrossRef]
- Ahmed, I.; Khammari, H.; Shahid, A.; Musa, A.; Kim, K.S.; De Poorter, E.; Moerman, I. A survey on hybrid beamforming techniques in 5G: Architecture and system model perspectives. IEEE Commun. Surv. Tutor. 2018, 20, 3060–3097. [Google Scholar] [CrossRef] [Green Version]
- Sheeba, J.M.; Deepa, S. Beamforming Techniques for Millimeter Wave Communications-A Survey. In Proceedings of the International Conference on Emerging Current Trends in Computing and Expert Technology, Chennai, India, 22–23 March 2019; pp. 1563–1573. [Google Scholar]
- Hwang, D.; Nam, S.S.; Yang, J. Multi-antenna beamforming techniques in full-duplex and self-energy recycling systems: Opportunities and challenges. IEEE Commun. Mag. 2017, 55, 160–167. [Google Scholar] [CrossRef]
- Rezaei, F.; Tadaion, A. Multi-layer beamforming in uplink/downlink massive MIMO systems with multi-antenna users. Signal Process. 2019, 164, 58–66. [Google Scholar] [CrossRef]
- Vaigandla, K.K.; Venu, D.N. A Survey on Future Generation Wireless Communications-5G: Multiple Access Techniques, Physical Layer Security, Beamforming Approach. J. Inf. Comput. Sci. 2021, 11, 449–474. [Google Scholar]
- Caroline, B.E.; Xavier, S.C.; Kabilan, A.P.; William, J. Performance analysis and comparison of optical signal processing beamforming networks: A survey. Photonic Netw. Commun. 2019, 37, 38–52. [Google Scholar] [CrossRef]
- Usama, M.; Erol-Kantarci, M. A survey on recent trends and open issues in energy efficiency of 5G. Sensors 2019, 19, 3126. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Li, Y.; Martensson, J.; Skubic, B.; Zhao, Y.; Zhang, J.; Wosinska, L.; Monti, P. Flexible RAN: Combining dynamic baseband split selection and reconfigurable optical transport to optimize RAN performance. IEEE Netw. 2020, 34, 180–187. [Google Scholar] [CrossRef]
- Morais, F.Z.; da Costa, C.A.; Alberti, A.M.; Both, C.B.; da Rosa Righi, R. When SDN meets C-RAN: A survey exploring multi-point coordination, interference, and performance. J. Netw. Comput. Appl. 2020, 162, 102655. [Google Scholar] [CrossRef]
- Kiet, D.T.; Hieu, T.M.; Hung, N.Q.; Van Cuong, N.; Van, V.T.; Cuong, P.N. Research and Implementation of eCPRI Processing Module for Fronthaul Network on FPGA in 5G–NR gNodeB Base Station. In Proceedings of the 2020 4th International Conference on Recent Advances in Signal Processing, Telecommunications & Computing (SigTelCom), Hanoi, Vietnam, 28–29 August 2020; pp. 1–5. [Google Scholar]
- Pérez, G.O.; López, D.L.; Hernández, J.A. 5G new radio fronthaul network design for eCPRI-IEEE 802.1 CM and extreme latency percentiles. IEEE Access 2019, 7, 82218–82230. [Google Scholar] [CrossRef]
- Rabia, T.; Braham, O. A new SDN-based next generation fronthaul interface for a partially centralized C-RAN. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 393–398. [Google Scholar]
- Liu, X.; Deng, N. Emerging optical communication technologies for 5G. In Optical Fiber Telecommunications VII; Elsevier: Amsterdam, The Netherlands, 2020; pp. 751–783. [Google Scholar]
- Saliou, F.; Chanclou, P.; Neto, L.A.; Simon, G.; Potet, J.; Gay, M.; Bramerie, L.; Debregeas, H. Optical access network interfaces for 5G and beyond. J. Opt. Commun. Netw. 2021, 13, D32–D42. [Google Scholar] [CrossRef]
- Morgado, A.; Huq, K.M.S.; Mumtaz, S.; Rodriguez, J. A survey of 5G technologies: Regulatory, standardization and industrial perspectives. Digit. Commun. Netw. 2018, 4, 87–97. [Google Scholar] [CrossRef]
- Huq, K.M.S.; Busari, S.A.; Rodriguez, J.; Frascolla, V.; Bazzi, W.; Sicker, D.C. Terahertz-enabled wireless system for beyond-5G ultra-fast networks: A brief survey. IEEE Netw. 2019, 33, 89–95. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, H.; Hou, S.; Zhao, Z.; Xu, H.; Wu, X.; Wu, Q.; Zhang, R. A survey on 5G millimeter wave communications for UAV-assisted wireless networks. IEEE Access 2019, 7, 117460–117504. [Google Scholar] [CrossRef]
- Rinaldi, F.; Raschella, A.; Pizzi, S. 5G NR system design: A concise survey of key features and capabilities. Wirel. Netw. 2021, 27, 5173–5188. [Google Scholar] [CrossRef]
- Uwaechia, A.N.; Mahyuddin, N.M. A comprehensive survey on millimeter wave communications for fifth-generation wireless networks: Feasibility and challenges. IEEE Access 2020, 8, 62367–62414. [Google Scholar] [CrossRef]
- Hu, F.; Chen, B.; Zhu, K. Full spectrum sharing in cognitive radio networks toward 5G: A survey. IEEE Access 2018, 6, 15754–15776. [Google Scholar] [CrossRef]
- Al-Falahy, N.; Alani, O.Y. Millimetre wave frequency band as a candidate spectrum for 5G network architecture: A survey. Phys. Commun. 2019, 32, 120–144. [Google Scholar] [CrossRef]
- Huo, Y.; Dong, X.; Xu, W.; Yuen, M. Enabling multi-functional 5G and beyond user equipment: A survey and tutorial. IEEE Access 2019, 7, 116975–117008. [Google Scholar] [CrossRef]
- Kersting, K. Machine learning and artificial intelligence: Two fellow travelers on the quest for intelligent behavior in machines. Front. Big Data 2018, 1, 6. [Google Scholar] [CrossRef] [Green Version]
- Voulodimos, A.; Doulamis, N.; Doulamis, A.; Protopapadakis, E. Deep learning for computer vision: A brief review. Comput. Intell. Neurosci. 2018, 2018, 706834. [Google Scholar] [CrossRef] [PubMed]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Kuleto, V.; Ilić, M.; Dumangiu, M.; Ranković, M.; Martins, O.; Păun, D.; Mihoreanu, L. Exploring opportunities and challenges of artificial intelligence and machine learning in higher education institutions. Sustainability 2021, 13, 10424. [Google Scholar] [CrossRef]
- Chen, M.Y.; Fan, M.H.; Huang, L.X. AI-based vehicular network toward 6G and IoT: Deep learning approaches. ACM Trans. Manag. Inf. Syst. (TMIS) 2021, 13, 1–12. [Google Scholar] [CrossRef]
- Shafin, R.; Liu, L.; Chandrasekhar, V.; Chen, H.; Reed, J.; Zhang, J.C. Artificial intelligence-enabled cellular networks: A critical path to beyond-5G and 6G. IEEE Wirel. Commun. 2020, 27, 212–217. [Google Scholar] [CrossRef] [Green Version]
- Huang, T.; Yang, W.; Wu, J.; Ma, J.; Zhang, X.; Zhang, D. A survey on green 6G network: Architecture and technologies. IEEE Access 2019, 7, 175758–175768. [Google Scholar] [CrossRef]
- Saad, W.; Bennis, M.; Chen, M. A vision of 6G wireless systems: Applications, trends, technologies, and open research problems. IEEE Netw. 2019, 34, 134–142. [Google Scholar] [CrossRef] [Green Version]
- Mezgár, I. Collaborative Networks and ICT Trends for Future CPPS and Beyond. In Proceedings of the Working Conference on Virtual Enterprises, Turin, Italy, 23–25 September 2019; pp. 21–28. [Google Scholar]
- Zioga, P.; Pollick, F.; Ma, M.; Chapman, P.; Stefanov, K. “Enheduanna—A Manifesto of Falling” Live Brain-Computer Cinema Performance: Performer and Audience Participation, Cognition and Emotional Engagement Using Multi-Brain BCI Interaction. Front. Neurosci. 2018, 12, 191. [Google Scholar] [CrossRef] [Green Version]
- Braud, T.; Bijarbooneh, F.H.; Chatzopoulos, D.; Hui, P. Future networking challenges: The case of mobile augmented reality. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 1796–1807. [Google Scholar]
- Piran, M.J.; Suh, D.Y. Learning-driven wireless communications, towards 6G. In Proceedings of the 2019 International Conference on Computing, Electronics & Communications Engineering (iCCECE), London, UK, 22–23 August 2019; pp. 219–224. [Google Scholar]
- Yrjölä, S. Decentralized 6G business models. In Proceedings of the 6G Wirel. Summit, Levi, Finland, 24–26 March 2019; pp. 5–7. [Google Scholar]
- Mahmoud, H.H.H.; Amer, A.A.; Ismail, T. 6G: A comprehensive survey on technologies, applications, challenges, and research problems. Trans. Emerg. Telecommun. Technol. 2021, 32, e4233. [Google Scholar] [CrossRef]
- Giordani, M.; Polese, M.; Mezzavilla, M.; Rangan, S.; Zorzi, M. Toward 6G networks: Use cases and technologies. IEEE Commun. Mag. 2020, 58, 55–61. [Google Scholar] [CrossRef]
- Mucchi, L.; Jayousi, S.; Caputo, S.; Paoletti, E.; Zoppi, P.; Geli, S.; Dioniso, P. How 6G technology can change the future wireless healthcare. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–6. [Google Scholar]
- Saxena, N.; Rastogi, E.; Rastogi, A. 6G Use Cases, Requirements, and Metrics. In 6G Mobile Wireless Networks; Springer: Berlin/Heidelberg, Germany, 2021; pp. 7–24. [Google Scholar]
- Nawaz, S.J.; Sharma, S.K.; Wyne, S.; Patwary, M.N.; Asaduzzaman, M. Quantum machine learning for 6G communication networks: State-of-the-art and vision for the future. IEEE Access 2019, 7, 46317–46350. [Google Scholar] [CrossRef]
- Sharma, T.; Chehri, A.; Fortier, P. Review of optical and wireless backhaul networks and emerging trends of next generation 5G and 6G technologies. Trans. Emerg. Telecommun. Technol. 2021, 32, 1–16. [Google Scholar] [CrossRef]
- Hou, X.; Ren, Z.; Yang, K.; Chen, C.; Zhang, H.; Xiao, Y. IIoT-MEC: A novel mobile edge computing framework for 5G-enabled IIoT. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–7. [Google Scholar]
- Xia, W.; Zhang, J.; Quek, T.Q.; Jin, S.; Zhu, H. Mobile edge cloud-based industrial internet of things: Improving edge intelligence with hierarchical SDN controllers. IEEE Veh. Technol. Mag. 2020, 15, 36–45. [Google Scholar] [CrossRef]
- Liao, Y.; Shou, L.; Yu, Q.; Ai, Q.; Liu, Q. An intelligent computation demand response framework for iiot-mec interactive networks. IEEE Netw. Lett. 2020, 2, 154–158. [Google Scholar] [CrossRef]
- Spinelli, F.; Mancuso, V. Toward Enabled Industrial Verticals in 5G: A Survey on MEC-Based Approaches to Provisioning and Flexibility. IEEE Commun. Surv. Tutor. 2020, 23, 596–630. [Google Scholar] [CrossRef]
- Bebortta, S.; Senapati, D.; Panigrahi, C.R.; Pati, B. An adaptive performance modeling framework for QoS-aware offloading in MEC-based IIoT systems. IEEE Internet Things J. 2021, 1. [Google Scholar] [CrossRef]
- Yang, B.; Cao, X.; Li, X.; Zhang, Q.; Qian, L. Mobile-edge-computing-based hierarchical machine learning tasks distribution for IIoT. IEEE Internet Things J. 2019, 7, 2169–2180. [Google Scholar] [CrossRef]
- Qiu, T.; Chi, J.; Zhou, X.; Ning, Z.; Atiquzzaman, M.; Wu, D.O. Edge computing in industrial internet of things: Architecture, advances and challenges. IEEE Commun. Surv. Tutor. 2020, 22, 2462–2488. [Google Scholar] [CrossRef]
- Okwuibe, J.; Haavisto, J.; Harjula, E.; Ahmad, I.; Ylianttila, M. SDN Enhanced Resource Orchestration of Containerized Edge Applications for Industrial IoT. IEEE Access 2020, 8, 229117–229131. [Google Scholar] [CrossRef]
- Vilalta, R.; López, V.; Giorgetti, A.; Peng, S.; Orsini, V.; Velasco, L.; Serral-Gracia, R.; Morris, D.; De Fina, S.; Cugini, F.; et al. TelcoFog: A unified flexible fog and cloud computing architecture for 5G networks. IEEE Commun. Mag. 2017, 55, 36–43. [Google Scholar] [CrossRef] [Green Version]
- Velasco, L.; Ruiz, M. Flexible fog computing and telecom architecture for 5G networks. In Proceedings of the 2018 20th International Conference on Transparent Optical Networks (ICTON), Bucharest, Romania, 1–5 July 2018; pp. 1–4. [Google Scholar]
- Ray, P.P.; Kumar, N. SDN/NFV architectures for edge-cloud oriented IoT: A systematic review. Comput. Commun. 2021, 169, 129–153. [Google Scholar] [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms. J. Syst. Archit. 2018, 98, 289–330. [Google Scholar] [CrossRef]
- Sivasangari, A.; Lakshmanan, L.; Ajitha, P.; Deepa, D.; Jabez, J. Big Data Analytics for 5G-Enabled IoT Healthcare. In Blockchain for 5G-Enabled IoT; Springer: Cham, Switzerland, 2021; pp. 261–275. [Google Scholar]
- Arivazhagan, C.; Natarajan, V. A Survey on Fog computing paradigms, Challenges and Opportunities in IoT. In Proceedings of the 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 28–30 July 2020; pp. 385–389. [Google Scholar]
- Cheng, B.; Fuerst, J.; Solmaz, G.; Sanada, T. Fog function: Serverless fog computing for data intensive iot services. In Proceedings of the 2019 IEEE International Conference on Services Computing (SCC), Milan, Italy, 8–13 July 2019; pp. 28–35. [Google Scholar]
- Giannelli, C.; Poltronieri, F.; Stefanelli, C.; Tortonesi, M. Supporting the development of next-generation fog services. In Proceedings of the 2018 IEEE 23rd International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Barcelona, Spain, 17–19 September 2018; pp. 1–6. [Google Scholar]
- Rahimi, H.; Zibaeenejad, A.; Safavi, A.A. A novel IoT architecture based on 5G-IoT and next generation technologies. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 81–88. [Google Scholar]
- Sarrigiannis, I.; Ramantas, K.; Kartsakli, E.; Mekikis, P.V.; Antonopoulos, A.; Verikoukis, C. Online VNF lifecycle management in an MEC-enabled 5G IoT architecture. IEEE Internet Things J. 2019, 7, 4183–4194. [Google Scholar] [CrossRef]
- Huang, M.; Liu, A.; Xiong, N.N.; Wang, T.; Vasilakos, A.V. An effective service-oriented networking management architecture for 5G-enabled internet of things. Comput. Netw. 2020, 173, 107208. [Google Scholar] [CrossRef]
- Li, S.; Da Xu, L.; Zhao, S. 5G Internet of Things: A survey. J. Ind. Inf. Integr. 2018, 10, 1–9. [Google Scholar] [CrossRef]
- Chettri, L.; Bera, R. A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet Things J. 2019, 7, 16–32. [Google Scholar] [CrossRef]
- Gupta, N.; Sharma, S.; Juneja, P.K.; Garg, U. SDNFV 5G-IoT: A framework for the next generation 5G enabled IoT. In Proceedings of the 2020 International Conference on Advances in Computing, Communication & Materials (ICACCM), Dehradun, India, 21–22 August 2020; pp. 289–294. [Google Scholar]
- Rahimi, H.; Zibaeenejad, A.; Rajabzadeh, P.; Safavi, A.A. On the security of the 5g-IoT architecture. In Proceedings of the International Conference on Smart Cities and Internet of Things, Mashhad, Iran, 26–27 September 2018; pp. 1–8. [Google Scholar]
- Mudigonda, P.; Abburi, S.K. Abburi, S.K. A Survey: 5G in IoT is a Boon for Big Data Communication and Its Security. In ICDSMLA 2019; Springer: Berlin/Heidelberg, Germany, 2020; pp. 318–327. [Google Scholar]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for 5G and beyond networks: A state of the art survey. J. Netw. Comput. Appl. 2020, 166, 102693. [Google Scholar] [CrossRef]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Arshad, U.; Shah, M.A.; Javaid, N. Futuristic blockchain based scalable and cost-effective 5G vehicular network architecture. Veh. Commun. 2021, 31, 100386. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Kumar, N. Blockchain and 5G integrated softwarized UAV network management: Architecture, solutions, and challenges. Phys. Commun. 2021, 47, 101355. [Google Scholar] [CrossRef]
- Kiyomoto, S.; Basu, A.; Rahman, M.S.; Ruj, S. On blockchain-based authorization architecture for beyond-5G mobile services. In Proceedings of the 2017 12th International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017; pp. 136–141. [Google Scholar]
- Khujamatov, K.; Reypnazarov, E.; Akhmedov, N.; Khasanov, D. Blockchain for 5G Healthcare architecture. In Proceedings of the 2020 International Conference on Information Science and Communications Technologies (ICISCT), Tashkent, Uzbekistan, 4–6 November 2020; pp. 1–5. [Google Scholar]
- Honar Pajooh, H.; Rashid, M.; Alam, F.; Demidenko, S. Multi-layer blockchain-based security architecture for internet of things. Sensors 2021, 21, 772. [Google Scholar] [CrossRef]
- Hakiri, A.; Dezfouli, B. Towards a Blockchain-SDN Architecture for Secure and Trustworthy 5G Massive IoT Networks. In Proceedings of the 2021 ACM International Workshop on Software Defined Networks & Network Function Virtualization Security, Virtual Event, 28 April 2021; pp. 11–18. [Google Scholar]
- Zhani, M.F.; ElBakoury, H. FlexNGIA: A flexible Internet architecture for the next-generation tactile Internet. J. Netw. Syst. Manag. 2020, 28, 751–795. [Google Scholar] [CrossRef] [Green Version]
- Tariq, F.; Khandaker, M.R.; Wong, K.K.; Imran, M.A.; Bennis, M.; Debbah, M. A speculative study on 6G. IEEE Wirel. Commun. 2020, 27, 118–125. [Google Scholar] [CrossRef]
- Agiwal, M.; Roy, A.; Saxena, N. Next generation 5G wireless networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2016, 18, 1617–1655. [Google Scholar] [CrossRef]
- Morocho-Cayamcela, M.E.; Lee, H.; Lim, W. Machine learning for 5G/B5G mobile and wireless communications: Potential, limitations, and future directions. IEEE Access 2019, 7, 137184–137206. [Google Scholar] [CrossRef]
- Sanchez, J.M. Mobile revolution: From 2G to 5G. In Proceedings of the 2021 IEEE Colombian Conference on Communications and Computing (COLCOM), Cali, Colombia, 26–28 May 2021; pp. 1–6. [Google Scholar]
- Hussain, M.; Amin, Y.; Lee, K.G. A Compact and Flexible UHF RFID Tag Antenna for Massive IoT Devices in 5G System. Sensors 2020, 20, 5713. [Google Scholar] [CrossRef] [PubMed]
- Dilli, R. Analysis of 5G wireless systems in FR1 and FR2 frequency bands. In Proceedings of the 2020 2nd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bangalore, India, 5–7 March 2020; pp. 767–772. [Google Scholar]
- Samdanis, K.; Taleb, T. The road beyond 5G: A vision and insight of the key technologies. IEEE Netw. 2020, 34, 135–141. [Google Scholar] [CrossRef]
- Patil, M.V.; Pawar, S.; Saquib, Z. Coding techniques for 5G networks: A review. In Proceedings of the 2020 3rd International Conference on Communication System, Computing and IT Applications (CSCITA), Mumbai, India, 3–4 April 2020; pp. 208–213. [Google Scholar]
- Henry, S.; Alsohaily, A.; Sousa, E.S. 5G is real: Evaluating the compliance of the 3GPP 5G new radio system with the ITU IMT-2020 requirements. IEEE Access 2020, 8, 42828–42840. [Google Scholar] [CrossRef]
- Dandekar, A. Towards autonomic orchestration of machine learning pipelines in future networks. arXiv 2021, arXiv:2107.08194. [Google Scholar]
- Sridharan, S. Machine Learning (ML) In a 5G Standalone (SA) Self Organizing Network (SON). arXiv 2020, arXiv:2011.12288. [Google Scholar]
- Abdellah, A.; Koucheryavy, A. Survey on artificial intelligence techniques in 5G networks. J. Inf. Technol. Telecommun. SPbSUT Russ. 2020, 8, 1–10. [Google Scholar] [CrossRef]
- Lin, X.; Li, J.; Baldemair, R.; Cheng, J.F.T.; Parkvall, S.; Larsson, D.C.; Koorapaty, H.; Frenne, M.; Falahati, S.; Grovlen, A.; et al. 5G new radio: Unveiling the essentials of the next generation wireless access technology. IEEE Commun. Stand. Mag. 2019, 3, 30–37. [Google Scholar] [CrossRef] [Green Version]
- Bizaki, H.K. Towards 5G Wireless Networks: A Physical Layer Perspective; BoD–Books on Demand; InTechOpen: London, UK, 2016. [Google Scholar]
- Abubakar, I.; Din, J.; Alhilali, M.; Lam, H.Y. Interference and Electromagnetic Compatibility Challenges in 5G Wireless Network Deployments. Indones. J. Electr. Eng. Comput. Sci. 2017, 5, 612–621. [Google Scholar] [CrossRef]
- Kongara, G.; He, C.; Yang, L.; Armstrong, J. A comparison of CP-OFDM, PCC-OFDM and UFMC for 5G uplink communications. IEEE Access 2019, 7, 157574–157594. [Google Scholar] [CrossRef]
- Peccarelli, N.; James, B.; Irazoqui, R.; Metcalf, J.; Fulton, C.; Yeary, M. Survey: Characterization and mitigation of spatial/spectral interferers and transceiver nonlinearities for 5G MIMO systems. IEEE Trans. Microw. Theory Tech. 2019, 67, 2829–2846. [Google Scholar] [CrossRef]
- Dion, T.; Torres, P. Electromagnetic Interference Analysis of Industrial IoT Networks: From Legacy Systems to 5G. In Proceedings of the 2020 IEEE Microwave Theory and Techniques in Wireless Communications (MTTW), Riga, Latvia, 1–2 October 2020; Volume 1, pp. 41–46. [Google Scholar]
- Taheribakhsh, M.; Jafari, A.; Peiro, M.M.; Kazemifard, N. 5g implementation: Major issues and challenges. In Proceedings of the 2020 25th International Computer Conference, Computer Society of Iran (CSICC), Tehran, Iran, 1–2 January 2020; pp. 1–5. [Google Scholar]
- He, R.; Schneider, C.; Ai, B.; Wang, G.; Zhong, Z.; Dupleich, D.A.; Thomae, R.S.; Boban, M.; Luo, J.; Zhang, Y. Propagation channels of 5G millimeter-wave vehicle-to-vehicle communications: Recent advances and future challenges. IEEE Veh. Technol. Mag. 2019, 15, 16–26. [Google Scholar] [CrossRef]
- Shafi, M.; Zhang, J.; Tataria, H.; Molisch, A.F.; Sun, S.; Rappaport, T.S.; Tufvesson, F.; Wu, S.; Kitao, K. Microwave vs. millimeter-wave propagation channels: Key differences and impact on 5G cellular systems. IEEE Commun. Mag. 2018, 56, 14–20. [Google Scholar] [CrossRef]
- Kumari, M.S.; Kumar, N. Channel model for simultaneous backhaul and access for mmWave 5G outdoor street canyon channel. Wirel. Networks 2020, 26, 5997–6013. [Google Scholar] [CrossRef]
- Azpilicueta Fernández de las Heras, L.; López Iturri, P.; Zuñiga Mejia, J.; Aguirre Gallego, E.; Falcone Lanas, F.J. Fifth-generation (5G) mmwave spatial channel characterization for urban environments’ system analysis. Sensors 2020, 20, 5360. [Google Scholar] [CrossRef]
- Sánchez, J.D.V.; Urquiza-Aguiar, L.; Paredes Paredes, M.C. Fading channel models for mm-wave communications. Electronics 2021, 10, 798. [Google Scholar] [CrossRef]
- Segura, D.; Khatib, E.J.; Munilla, J.; Barco, R. 5G Numerologies Assessment for URLLC in Industrial Communications. Sensors 2021, 21, 2489. [Google Scholar] [CrossRef]
- Khan, I.; Zafar, M.H.; Jan, M.T.; Lloret, J.; Basheri, M.; Singh, D. Spectral and energy efficient low-overhead uplink and downlink channel estimation for 5G massive MIMO systems. Entropy 2018, 20, 92. [Google Scholar] [CrossRef] [Green Version]
- Al-Samman, A.M.; Azmi, M.H.; Al-Gumaei, Y.A.; Al-Hadhrami, T.; Fazea, Y.; Al-Mqdashi, A. Millimeter wave propagation measurements and characteristics for 5G system. Appl. Sci. 2020, 10, 335. [Google Scholar] [CrossRef] [Green Version]
- Chen, K.T.; Ma, W.H.; Hwang, Y.T.; Chang, K.Y. A Low Complexity, High Throughput DoA Estimation Chip Design for Adaptive Beamforming. Electronics 2020, 9, 641. [Google Scholar] [CrossRef] [Green Version]
- Shevada, L.; Raut, H.D.; Malekar, R.; Kumar, S. Comparative Study of different beamforming techniques for 5G: A Review. In Inventive Communication and Computational Technologies; Springer: Singapore, 2021; pp. 589–595. [Google Scholar]
- Ali, E.; Ismail, M.; Nordin, R.; Abdulah, N.F. Beamforming techniques for massive MIMO systems in 5G: Overview, classification, and trends for future research. Front. Inf. Technol. Electron. Eng. 2017, 18, 753–772. [Google Scholar] [CrossRef]
- Reddy, K.S. 5G VANETs: A Details Performance Analysis of Fusion Beam Forming Techniques for Vehicular Environment. Turk. J. Comput. Math. Educ. (TURCOMAT) 2021, 12, 5518–5533. [Google Scholar]
- Noh, S.; Zoltowski, M.D.; Love, D.J. Multi-resolution codebook and adaptive beamforming sequence design for millimeter wave beam alignment. IEEE Trans. Wirel. Commun. 2017, 16, 5689–5701. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Y.; Ai, B.; Liu, Y. A Novel Adaptive Beamforming with Combinational Algorithm in Wireless Communications. In Proceedings of the International Conference on Intelligent Computing, Liverpool, UK, 7–10 August 2017; pp. 637–646. [Google Scholar]
- Zhang, Q.; Zhao, J.; Chen, A.; Wang, C. Adaptive Beamforming and Power Allocation for mmWave Communication in High-Speed Railway. Radio Sci. 2021, 56, e2020RS007073. [Google Scholar] [CrossRef]
- Yashchyshyn, Y.; Derzakowski, K.; Bogdan, G.; Godziszewski, K.; Nyzovets, D.; Kim, C.H.; Park, B. 28 GHz switched-beam antenna based on S-PIN diodes for 5G mobile communications. IEEE Antennas Wirel. Propag. Lett. 2017, 17, 225–228. [Google Scholar] [CrossRef]
- Ikram, M.; Sharawi, M.; Klionovski, K.; Shamim, A. A switched-beam millimeter-wave array with MIMO configuration for 5G applications. Microw. Opt. Technol. Lett. 2018, 60, 915–920. [Google Scholar] [CrossRef]
- Zhang, W.; Wei, Y.; Wu, S.; Meng, W.; Xiang, W. Joint beam and resource allocation in 5G mmWave small cell systems. IEEE Trans. Veh. Technol. 2019, 68, 10272–10277. [Google Scholar] [CrossRef]
- Lee, S.; Lee, Y.; Shin, H. A 28-GHz Switched-Beam Antenna with Integrated Butler Matrix and Switch for 5G Applications. Sensors 2021, 21, 5128. [Google Scholar] [CrossRef]
- Moubadir, M.; Mchbal, A.; Touhami, N.A.; Aghoutane, M. A Switched Beamforming Network for 5G Modern Wireless Communications Applications. Procedia Manuf. 2019, 32, 753–761. [Google Scholar] [CrossRef]
- Al-Tarifi, M.A.; Sharawi, M.S.; Shamim, A. Massive MIMO antenna system for 5G base stations with directive ports and switched beamsteering capabilities. IET Microwaves Antennas Propag. 2018, 12, 1709–1718. [Google Scholar] [CrossRef] [Green Version]
- Orakwue, S.; Ngah, R. Switched-beam array antenna at 28 GHz for 5G wireless system based on butler matrix beamforming network. Niger. J. Technol. 2019, 38, 484–489. [Google Scholar] [CrossRef]
- Vilas Boas, E.C.; Filgueiras, H.R.D.; Feliciano da Costa, I.; Ribeiro, J.A.J.; Sodre, A.C., Jr. Dual-band switched-beam antenna array for MIMO systems. IET Microwaves Antennas Propag. 2020, 14, 82–87. [Google Scholar] [CrossRef]
- Ge, L.; Zhang, Y.; Chen, G.; Tong, J. Compression-based LMMSE channel estimation with adaptive sparsity for massive MIMO in 5G systems. IEEE Syst. J. 2019, 13, 3847–3857. [Google Scholar] [CrossRef]
- Wu, W.; Liu, D.; Hou, X.; Liu, M. Low-complexity beam training for 5G millimeter-wave massive MIMO systems. IEEE Trans. Veh. Technol. 2019, 69, 361–376. [Google Scholar] [CrossRef]
- Wu, X.; Beaulieu, N.C.; Liu, D. On favorable propagation in massive MIMO systems and different antenna configurations. IEEE Access 2017, 5, 5578–5593. [Google Scholar] [CrossRef]
- Shinjo, S.; Nakatani, K.; Tsutsumi, K.; Nakamizo, H. Integrating the front end: A highly integrated RF front end for high-SHF wide-band massive MIMO in 5G. IEEE Microw. Mag. 2017, 18, 31–40. [Google Scholar] [CrossRef]
- Kammoun, A.; Debbah, M.; Alouini, M.S. Design of 5G full dimension massive MIMO systems. IEEE Trans. Commun. 2017, 66, 726–740. [Google Scholar]
- Dicandia, F.A.; Genovesi, S. Exploitation of triangular lattice arrays for improved spectral efficiency in massive MIMO 5G systems. IEEE Access 2021, 9, 17530–17543. [Google Scholar] [CrossRef]
- Huang, J.; Wang, C.X.; Feng, R.; Sun, J.; Zhang, W.; Yang, Y. Multi-frequency mmWave massive MIMO channel measurements and characterization for 5G wireless communication systems. IEEE J. Sel. Areas Commun. 2017, 35, 1591–1605. [Google Scholar] [CrossRef]
- Suk, G.Y.; Kim, S.M.; Kwak, J.; Hur, S.; Kim, E.; Chae, C.B. Full duplex integrated access and backhaul for 5G NR: Analyses and prototype measurements. arXiv 2020, arXiv:2007.03272. [Google Scholar]
- Zhang, L.; Ansari, N. A framework for 5G networks with in-band full-duplex enabled drone-mounted base-stations. IEEE Wirel. Commun. 2019, 26, 121–127. [Google Scholar] [CrossRef]
- de Melo Guimarães, L.; Luiz Bordim, J. A Full-duplex MAC tailored for 5G Wireless Networks. Wirel. Commun. Mob. Comput. 2018, 2018, 5408973. [Google Scholar] [CrossRef] [Green Version]
- Yadav, A.; Dobre, O.A.; Ansari, N. Energy and traffic aware full-duplex communications for 5G systems. IEEE Access 2017, 5, 11278–11290. [Google Scholar] [CrossRef]
- Kolodziej, K.E.; Perry, B.T.; Herd, J.S. In-band full-duplex technology: Techniques and systems survey. IEEE Trans. Microw. Theory Tech. 2019, 67, 3025–3041. [Google Scholar] [CrossRef]
- Xia, X.; Xu, K.; Wang, Y.; Xu, Y. A 5G-enabling technology: Benefits, feasibility, and limitations of in-band full-duplex mMIMO. IEEE Veh. Technol. Mag. 2018, 13, 81–90. [Google Scholar] [CrossRef]
- Biswas, S.; Bishnu, A.; Khan, F.A.; Ratnarajah, T. In-Band Full-Duplex Dynamic Spectrum Sharing in Beyond 5G Networks. IEEE Commun. Mag. 2021, 59, 54–60. [Google Scholar] [CrossRef]
- Abbas, F.; Yuan, X.; Bute, M.S.; Fan, P. Performance Analysis Using Full Duplex Discovery Mechanism in 5G-V2X Communication Networks. IEEE Trans. Intell. Transp. Syst. 2021, 12, 1–12. [Google Scholar] [CrossRef]
- Matthaiou, M.; Yurduseven, O.; Ngo, H.Q.; Morales-Jimenez, D.; Cotton, S.L.; Fusco, V.F. The road to 6G: Ten physical layer challenges for communications engineers. IEEE Commun. Mag. 2021, 59, 64–69. [Google Scholar] [CrossRef]
- Wu, N.; Wang, X.; Lin, B.; Zhang, K. A CNN-based end-to-end learning framework toward intelligent communication systems. IEEE Access 2019, 7, 110197–110204. [Google Scholar] [CrossRef]
- Qin, Z.; Ye, H.; Li, G.Y.; Juang, B.H.F. Deep learning in physical layer communications. IEEE Wirel. Commun. 2019, 26, 93–99. [Google Scholar] [CrossRef] [Green Version]
- Hong, T.; Liu, C.; Kadoch, M. Machine learning based antenna design for physical layer security in ambient backscatter communications. Wirel. Commun. Mob. Comput. 2019, 2019. [Google Scholar] [CrossRef]
- Vora, A.; Thomas, P.X.; Chen, R.; Kang, K.D. CSI classification for 5G via deep learning. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; pp. 1–5. [Google Scholar]
- Anand, A.; Rani, S.; Anand, D.; Aljahdali, H.M.; Kerr, D. An Efficient CNN-Based Deep Learning Model to Detect Malware Attacks (CNN-DMA) in 5G-IoT Healthcare Applications. Sensors 2021, 21, 6346. [Google Scholar] [CrossRef]
- Yuan, L.; Zhang, H.; Xu, M.; Zhou, F.; Wu, Q. A Multi-Scale CNN Framework for Wireless Technique Classification in Internet of Things. IEEE Internet Things J. 2021, 1. [Google Scholar] [CrossRef]
- Bao, X.; Feng, W.; Zheng, J.; Li, J. Deep CNN and equivalent channel based hybrid precoding for mmWave massive MIMO systems. IEEE Access 2020, 8, 19327–19335. [Google Scholar] [CrossRef]
- Liao, R.; Wen, H.; Pan, F.; Song, H.; Xu, A.; Jiang, Y. A Novel Physical Layer Authentication Method with Convolutional Neural Network. In Proceedings of the 2019 IEEE International Conference on Artificial Intelligence and Computer Applications (ICAICA), Dalian, China, 29–31 March 2019; pp. 231–235. [Google Scholar]
- Strodthoff, N.; Göktepe, B.; Schierl, T.; Hellge, C.; Samek, W. Enhanced machine learning techniques for early HARQ feedback prediction in 5G. IEEE J. Sel. Areas Commun. 2019, 37, 2573–2587. [Google Scholar] [CrossRef] [Green Version]
- Storck, C.R.; Duarte-Figueiredo, F. A survey of 5G technology evolution, standards, and infrastructure associated with vehicle-to-everything communications by internet of vehicles. IEEE Access 2020, 8, 117593–117614. [Google Scholar] [CrossRef]
- Agiwal, M.; Kwon, H.; Park, S.; Jin, H. A Survey on 4G-5G Dual Connectivity: Road to 5G Implementation. IEEE Access 2021, 9, 16193–16210. [Google Scholar] [CrossRef]
- El Rhayour, A.; Mazri, T. 5G Architecture: Deployment scenarios and options. In Proceedings of the 2019 International Symposium on Advanced Electrical and Communication Technologies (ISAECT), Rome, Italy, 27–29 November 2019; pp. 1–6. [Google Scholar]
- Kim, H.; Kim, J.; Hong, D. Dynamic TDD systems for 5G and beyond: A survey of cross-link interference mitigation. IEEE Commun. Surv. Tutor. 2020, 22, 2315–2348. [Google Scholar] [CrossRef]
- Khan, M.S.; Kim, Y.J.; Sultan, Q.; Joung, J.; Cho, Y.S. Downlink Synchronization for OTFS-Based Cellular Systems in High Doppler Environments. IEEE Access 2021, 9, 73575–73589. [Google Scholar] [CrossRef]
- Kishore, G.S.; Rallapalli, H. Towards 5G: A Survey on Waveform Contenders. In Advances in Decision Sciences, Image Processing, Security and Computer Vision; Springer: Berlin/Heidelberg, Germany, 2020; pp. 243–250. [Google Scholar]
- Alammouri, A.; Mo, J.; Ng, B.L.; Zhang, J.C.; Andrews, J.G. Hand grip impact on 5G mmWave mobile devices. IEEE Access 2019, 7, 60532–60544. [Google Scholar] [CrossRef]
- Yang, X.; Matthaiou, M.; Yang, J.; Wen, C.K.; Gao, F.; Jin, S. Hardware-constrained millimeter-wave systems for 5G: Challenges, opportunities, and solutions. IEEE Commun. Mag. 2019, 57, 44–50. [Google Scholar] [CrossRef] [Green Version]
- Su, Y.; LiWang, M.; Huang, L.; Du, X.; Guizani, N. Green Communications for Future Vehicular Networks: Data Compression Approaches, Opportunities, and Challenges. IEEE Netw. 2020, 34, 184–190. [Google Scholar] [CrossRef]
- Lai, S.; Zhao, R.; Tang, S.; Xia, J.; Zhou, F.; Fan, L. Intelligent secure mobile edge computing for beyond 5G wireless networks. Phys. Commun. 2021, 45, 101283. [Google Scholar] [CrossRef]
- Shakarami, A.; Shahidinejad, A.; Ghobaei-Arani, M. An autonomous computation offloading strategy in Mobile Edge Computing: A deep learning-based hybrid approach. J. Netw. Comput. Appl. 2021, 178, 102974. [Google Scholar] [CrossRef]
- Xu, S.; Liu, X.; Guo, S.; Qiu, X.; Meng, L. MECC: A Mobile Edge Collaborative Caching Framework Empowered by Deep Reinforcement Learning. IEEE Netw. 2021, 35, 176–183. [Google Scholar] [CrossRef]
- Omar, T.; Ketseoglou, T.; Naffaa, I. A novel self-healing model using precoding & big-data based approach for 5G networks. Pervasive Mob. Comput. 2021, 73, 101365. [Google Scholar]
- Jin, Z.; Zhang, C.; Zhao, G.; Jin, Y.; Zhang, L. A Context-aware Task Offloading Scheme in Collaborative Vehicular Edge Computing Systems. KSII Trans. Internet Inf. Syst. 2021, 15, 383–403. [Google Scholar]
- Xu, Y.; Gui, G.; Gacanin, H.; Adachi, F. A survey on resource allocation for 5G heterogeneous networks: Current research, future trends and challenges. IEEE Commun. Surv. Tutor. 2021, 23, 668–695. [Google Scholar] [CrossRef]
- Stainton, S.; Johnston, M.; Dlay, S.; Haigh, P.A. EVM Loss: A Loss Function for Training Neural Networks in Communication Systems. Sensors 2021, 21, 1094. [Google Scholar] [CrossRef] [PubMed]
- Arnold, M.; Hoydis, J.; ten Brink, S. Novel massive MIMO channel sounding data applied to deep learning-based indoor positioning. In Proceedings of the 12th International ITG Conference on Systems, Communications and Coding (SCC 2019), Rostock, Germany, 11–14 February 2019; pp. 1–6. [Google Scholar]
- Kojima, S.; Maruta, K.; Ahn, C.J. Adaptive modulation and coding using neural network based SNR estimation. IEEE Access 2019, 7, 183545–183553. [Google Scholar] [CrossRef]
- Kalinov, A.; Bychkov, R.; Ivanov, A.; Osinsky, A.; Yarotsky, D. Machine Learning-Assisted PAPR Reduction in Massive MIMO. IEEE Wirel. Commun. Lett. 2020, 10, 537–541. [Google Scholar] [CrossRef]
- Shen, S.; Zhang, T.; Mao, S.; Chang, G.K. DRL-Based Channel and Latency Aware Radio Resource Allocation for 5G Service-Oriented RoF-MmWave RAN. J. Light. Technol. 2021, 39, 5706–5714. [Google Scholar] [CrossRef]
- Arnold, M.; Dörner, S.; Cammerer, S.; Yan, S.; Hoydis, J.; Brink, S.T. Enabling FDD massive MIMO through deep learning-based channel prediction. arXiv 2019, arXiv:1901.03664. [Google Scholar]
- Singh, K.K.; Katiyar, H. A Survey Paper on 5G Suitable Waveform Candidates. In Advances in Intelligent Computing and Communication; Springer: Berlin/Heidelberg, Germany, 2021; pp. 717–724. [Google Scholar]
- Jijo, B.T.; Zeebaree, S.R.; Zebari, R.R.; Sadeeq, M.A.; Sallow, A.B.; Mohsin, S.; Ageed, Z.S. A comprehensive survey of 5G mm-wave technology design challenges. Asian J. Res. Comput. Sci. 2021, 8, 1–20. [Google Scholar] [CrossRef]
- Hamid, N. Evaluation of Power Receiving Signal of 5G Small Cells for Outdoor/Indoor Environment at Millimeterwave Bands. Appl. Comput. Electromagn. Soc. J. 2021, 36, 84–189. [Google Scholar] [CrossRef]
- Lee, J.; Kim, H.; Wymeersch, H.; Kim, S. Dirichlet process approach for radio-based simultaneous localization and mapping. arXiv 2021, arXiv:2107.00864. [Google Scholar]
- Alsadik, B.; Karam, S. The Simultaneous Localization and Mapping (SLAM)-An Overview. Surv. Geospat. Eng. J. 2021, 2, 34–45. [Google Scholar] [CrossRef]
- Dilli, R. Performance of Multi-User Massive Mimo in 5G NR networks AT 28 GHz band. Telecommun. Radio Eng. 2021, 80, 61–74. [Google Scholar] [CrossRef]
- Sakkas, L.; Stergiou, E.; Tsoumanis, G.; Angelis, C.T. 5G UFMC Scheme Performance with Different Numerologies. Electronics 2021, 10, 1915. [Google Scholar] [CrossRef]
- Mathur, H.; Deepa, T. A Survey on Advanced Multiple Access Techniques for 5G and Beyond Wireless Communications. Wirel. Pers. Commun. 2021, 118, 1775–1792. [Google Scholar] [CrossRef]
- Ramadhan, A. Overview and implementation of the two most important candidate 5G waveforms. J. Theor. Appl. Inf. Technol. 2019, 97, 2551–2560. [Google Scholar]
- de Almeida, I.B.F.; Mendes, L.L.; Rodrigues, J.J.; da Cruz, M.A. 5G waveforms for IoT applications. IEEE Commun. Surv. Tutorials 2019, 21, 2554–2567. [Google Scholar] [CrossRef]
- Khudhair, S.A.; Singh, M.J. Review in FBMC to Enhance the Performance of 5G Networks. J. Commun. 2020, 15, 415–426. [Google Scholar] [CrossRef]
- Zhang, J.; Rakhimov, D.; Haardt, M. Gridless Channel Estimation for Hybrid mmWave MIMO Systems via Tensor-ESPRIT Algorithms in DFT Beamspace. IEEE J. Sel. Top. Signal Process. 2021, 15, 816–831. [Google Scholar] [CrossRef]
- Meshkov, I.K.; Gizatulin, A.R.; Vinogradova, I.L.; Meshkova, A.G.; Sultanov, A.K.; Bagmanov, V.K.; Bourdine, A.V. Usage of SDM technology in radio-over-fiber (RoF) transmission systems in high-speed scalable 6G wireless networks. In Optical Technologies for Telecommunications 2020; International Society for Optics and Photonics: Bellingham, WA, USA, 2021; Volume 11793, p. 117931G. [Google Scholar]
- Gorre, P.; Vignesh, R.; Arya, R.; Kumar, S. A Review of mm-Wave Power Amplifiers for Next-Generation 5G Communication. In Soft Computing: Theories and Applications; Springer: Singapore, 2020; pp. 173–184. [Google Scholar]
- Nalband, A.H.; Sarvagya, M.; Ahmed, M.R. Spectral Efficient Beamforming for mmWave MISO Systems using Deep Learning Techniques. Arab. J. Sci. Eng. 2021, 46, 9783–9795. [Google Scholar] [CrossRef]
- Omotere, O.; Fuller, J.; Qian, L.; Han, Z. Spectrum occupancy prediction in coexisting wireless systems using deep learning. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–7. [Google Scholar]
- Vidal-Beltrán, S.; López-Bonilla, J.L. Improving Spectral Efficiency in the SCMA Uplink Channel. Mathematics 2021, 9, 651. [Google Scholar] [CrossRef]
- Khan, R.; Kumar, P.; Jayakody, D.N.K.; Liyanage, M. A survey on security and privacy of 5G technologies: Potential solutions, recent advancements, and future directions. IEEE Commun. Surv. Tutor. 2019, 22, 196–248. [Google Scholar] [CrossRef] [Green Version]
- Olfati, M.; Parmar, K. Deep Learning and AI for 5G Technology: Paradigms. In Proceedings of the IFIP International Conference on Artificial Intelligence Applications and Innovations, Hersonissos, Crete, Greece, 25–27 June 2021; pp. 398–407. [Google Scholar]
- Alves, H.; Jo, G.D.; Shin, J.; Yeh, C.; Mahmood, N.H.; Lima, C.; Yoon, C.; Rahatheva, N.; Park, O.S.; Kim, S.; et al. Beyond 5G URLLC Evolution: New Service Modes and Practical Considerations. arXiv 2021, arXiv:2106.11825. [Google Scholar]
- Mchangama, A.; Ayadi, J.; Jiménez, V.P.G.; Consoli, A. MmWave massive MIMO small cells for 5G and beyond mobile networks: An overview. In Proceedings of the 2020 12th International Symposium on Communication Systems, Networks and Digital Signal Processing (CSNDSP), Porto, Portugal, 20–22 July 2020; pp. 1–6. [Google Scholar]
- Jia, C.; Gao, H.; Chen, N.; He, Y. Machine learning empowered beam management for intelligent reflecting surface assisted MmWave networks. China Commun. 2020, 17, 100–114. [Google Scholar] [CrossRef]
- Khan, M.S.; Sultan, Q.; Cho, Y.S. Position and Machine Learning-Aided Beam Prediction and Selection Technique in Millimeter-Wave Cellular System. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 21–23 October 2020; pp. 603–605. [Google Scholar]
- Mumtaz, S.; Rodriguez, J.; Dai, L. MmWave Massive MIMO: A Paradigm for 5G; Academic Press: Cambridge, MA, USA, 2016. [Google Scholar]
- Wen, F.; Wymeersch, H.; Peng, B.; Tay, W.P.; So, H.C.; Yang, D. A survey on 5G massive MIMO localization. Digit. Signal Process. 2019, 94, 21–28. [Google Scholar] [CrossRef] [Green Version]
- Khwandah, S.A.; Cosmas, J.P.; Lazaridis, P.I.; Zaharis, Z.D.; Chochliouros, I.P. Massive MIMO Systems for 5G Communications. Wirel. Pers. Commun. 2021, 120, 2101–2115. [Google Scholar] [CrossRef]
- Arjoune, Y.; Faruque, S. Smart jamming attacks in 5G new radio: A review. In Proceedings of the 2020 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 1010–1015. [Google Scholar]
- Zhang, Y.; Du, J.; Chen, Y.; Li, X.; Rabie, K.M.; Khkrel, R. Dual-iterative hybrid beamforming design for millimeter-wave massive multi-user MIMO systems with sub-connected structure. IEEE Trans. Veh. Technol. 2020, 69, 13482–13496. [Google Scholar] [CrossRef]
- Papadopoulos, H.; Wang, C.; Bursalioglu, O.; Hou, X.; Kishiyama, Y. Massive MIMO technologies and challenges towards 5G. IEICE Trans. Commun. 2016, 99, 602–621. [Google Scholar] [CrossRef] [Green Version]
- Cao, L.; Hu, X.; Zhang, M.; Wang, X.; Zhang, X. Interactive CoMP with user-centric clustering based on load balancing in 5G dense networks. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Sultan, Q.; Khan, M.S.; Cho, Y.S. Fast 3D beamforming technique for millimeter-wave cellular systems with uniform planar arrays. IEEE Access 2020, 8, 123469–123482. [Google Scholar] [CrossRef]
- Rao, L.; Pant, M.; Malviya, L.; Parmar, A.; Charhate, S.V. 5G beamforming techniques for the coverage of intended directions in modern wireless communication: In-depth review. Int. J. Microw. Wirel. Technol. 2020, 13, 1039–1062. [Google Scholar] [CrossRef]
- Gao, L.; Rebeiz, G.M. A 22–44-GHz phased-array receive beamformer in 45-nm CMOS SOI for 5G applications with 3–3.6-dB NF. IEEE Trans. Microw. Theory Tech. 2020, 68, 4765–4774. [Google Scholar] [CrossRef]
- Molisch, A.F.; Ratnam, V.V.; Han, S.; Li, Z.; Nguyen, S.L.H.; Li, L.; Haneda, K. Hybrid beamforming for massive MIMO: A survey. IEEE Commun. Mag. 2017, 55, 134–141. [Google Scholar] [CrossRef] [Green Version]
- Chataut, R.; Akl, R. Massive MIMO systems for 5G and beyond networks—overview, recent trends, challenges, and future research direction. Sensors 2020, 20, 2753. [Google Scholar] [CrossRef]
- Wu, S.X.; Luo, Y.; Wang, H. Some New Results on Stochastic Beamforming Schemes. In Proceedings of the 2019 IEEE 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019; pp. 107–112. [Google Scholar]
- Abdelkader, A.; Jorswieck, E. Robust adaptive distributed beamforming for energy-efficient network flooding. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 1–15. [Google Scholar] [CrossRef]
- Chen, D.; Kuehn, V. Robust resource allocation and clustering formulation for multicast C-RAN with impaired CSI. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar]
- Liao, Y.; Yang, X.; Yao, H.; Chen, L.; Wan, S. Spatial correlation based channel compression feedback algorithm for massive MIMO systems. Digit. Signal Process. 2019, 94, 38–44. [Google Scholar] [CrossRef]
- Chataut, R.; Akl, R. Efficient and low complex uplink detection for 5G massive MIMO systems. In Proceedings of the 2018 IEEE 19th Wireless and Microwave Technology Conference (WAMICON), Sand Key, FL, USA, 9–10 April 2018; pp. 1–6. [Google Scholar]
- Pappa, M.; Ramesh, C.; Kumar, M.N. Performance comparison of massive MIMO and conventional MIMO using channel parameters. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 1808–1812. [Google Scholar]
- Garcia, N.; Wymeersch, H.; Larsson, E.G.; Haimovich, A.M.; Coulon, M. Direct localization for massive MIMO. IEEE Trans. Signal Process. 2017, 65, 2475–2487. [Google Scholar] [CrossRef] [Green Version]
- Rithe, J.P.; Khairnar, D.; Sharma, M. Performance of cooperative massive MIMO 5G cellular system. In Proceedings of the 2017 International Conference on Information, Communication, Instrumentation and Control (ICICIC), Indore, India, 17–19 August 2017; pp. 1–5. [Google Scholar]
- Kashima, T.; Qiu, J.; Shen, H.; Tang, C.; Tian, T.; Wang, X.; Hou, X.; Jiang, H.; Benjebbour, A.; Saito, Y.; et al. Large scale massive MIMO field trial for 5G mobile communications system. In Proceedings of the 2016 International symposium on antennas and propagation (ISAP), Okinawa, Japan, 24–28 October 2016; pp. 602–603. [Google Scholar]
- Dikmen, O.; Kulac, S. A New Method in Pilot Reuse Factor Selection in Spectrum Efficient Massive MIMO Systems. Elektron. Ir Elektrotechnika 2019, 25, 70–77. [Google Scholar] [CrossRef] [Green Version]
- Gao, X.; Edfors, O.; Rusek, F.; Tufvesson, F. Massive MIMO performance evaluation based on measured propagation data. IEEE Trans. Wirel. Commun. 2015, 14, 3899–3911. [Google Scholar] [CrossRef] [Green Version]
- Mahyiddin, W.A.; Martin, P.A.; Smith, P.J. Massive MIMO systems in time-selective channels. IEEE Commun. Lett. 2015, 19, 1973–1976. [Google Scholar] [CrossRef]
- Fang, X.; Fang, S.; Ying, N.; Cao, H.; Liu, C. The performance of massive MIMO systems under correlated channel. In Proceedings of the 2013 19th IEEE international conference on networks (ICON), Singapore, 11–13 December 2013; pp. 1–4. [Google Scholar]
- Chataut, R.; Akl, R. Channel Gain Based User Scheduling for 5G Massive MIMO Systems. In Proceedings of the 2019 IEEE 16th International Conference on Smart Cities: Improving Quality of Life Using ICT & IoT and AI (HONET-ICT), Charlotte, NC, USA, 6–9 October 2019; pp. 49–53. [Google Scholar]
- Xing, P.; Liu, J.; Zhai, C.; Yu, Z. Self-interference suppression with imperfect channel estimation in a shared-antenna full-duplex massive MU-MIMO system. EURASIP J. Wirel. Commun. Netw. 2017, 2017, 1–13. [Google Scholar] [CrossRef] [Green Version]
- Raza, Z.; Akhtar, Z.; Nawaz, N.; Hussain, G.; Nawaz, S. Single Cell Massive Mimo Downlink System: Energy Efficiency Solution. Pak. J. Sci. 2019, 71, 78. [Google Scholar]
- Ha, T.N.; Nguyen, X.X.; Ha, H.K. Energy Efficiency Maximization for Full Duplex MIMO Cloud Radio Access Networks. Sci. Technol. Dev. J.-Eng. Technol. 2020, 3, 488–499. [Google Scholar] [CrossRef]
- Gong, Z.; Li, C.; Jiang, F. Pilot contamination mitigation strategies in massive MIMO systems. IET Commun. 2017, 11, 2403–2409. [Google Scholar] [CrossRef]
- Demir, Ö.T.; Björnson, E. Joint power control and LSFD for wireless-powered cell-free massive MIMO. IEEE Trans. Wirel. Commun. 2020, 20, 1756–1769. [Google Scholar] [CrossRef]
- Zhao, K.; Zhang, S.; Ho, Z.; Zander, O.; Bolin, T.; Ying, Z.; Pedersen, G.F. Spherical coverage characterization of 5G millimeter wave user equipment with 3GPP specifications. IEEE Access 2018, 7, 4442–4452. [Google Scholar] [CrossRef]
- Kim, H.; Kim, S.; Lee, H.; Jang, C.; Choi, Y.; Choi, J. Massive MIMO channel prediction: Kalman filtering vs. machine learning. IEEE Trans. Commun. 2020, 69, 518–528. [Google Scholar] [CrossRef]
- Xia, N.; Chen, H.H.; Yang, C.S. Radio resource management in machine-to-machine communications—A survey. IEEE Commun. Surv. Tutor. 2017, 20, 791–828. [Google Scholar] [CrossRef]
- Yesilkaya, A.; Basar, E.; Miramirkhani, F.; Panayirci, E.; Uysal, M.; Haas, H. Optical MIMO-OFDM with generalized LED index modulation. IEEE Trans. Commun. 2017, 65, 3429–3441. [Google Scholar] [CrossRef] [Green Version]
- Liu, J.; Lu, H. IMNet: A Learning Based Detector for Index Modulation Aided MIMO-OFDM Systems. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea, 25–28 May 2020; pp. 1–6. [Google Scholar]
- He, H.; Wen, C.K.; Jin, S.; Li, G.Y. Model-driven deep learning for MIMO detection. IEEE Trans. Signal Process. 2020, 68, 1702–1715. [Google Scholar] [CrossRef]
- Trestian, R. 5G Radio Access Networks: Centralized RAN, Cloud-RAN, and Virtualization of Small Cells: Centralized RAN, Cloud-RAN and Virtualization of Small Cells; CRC Press: Boca Raton, FL, USA, 2017. [Google Scholar]
- Gomes, R.; Reis, J.; Al-Daher, Z.; Hammoudeh, A.; Caldeirinha, R.F. 5G: Performance and evaluation of FS-FBMC against OFDM for high data rate applications at 60 GHz. IET Signal Process. 2018, 12, 620–628. [Google Scholar] [CrossRef]
- Katzis, K.; Ahmadi, H. Challenges implementing Internet of Things (IoT) using cognitive radio capabilities in 5G mobile networks. In Internet of Things (IoT) in 5G Mobile Technologies; Springer: Berlin/Heidelberg, Germany, 2016; pp. 55–76. [Google Scholar]
- Li, Y.; Guan, Z.; Luo, H.; Wang, X.; Wang, M.; Li, Y.; Wei, Y.; Ma, Y. Crosstalk and Equivalent Circuit Model of Segmented Coplanar Waveguide Transmission Line at 5G FR2 Band. In Proceedings of the 2021 13th Global Symposium on Millimeter-Waves & Terahertz (GSMM), Nanjing, China, 23–26 May 2021; pp. 1–3. [Google Scholar]
- Lien, S.Y.; Shieh, S.L.; Huang, Y.; Su, B.; Hsu, Y.L.; Wei, H.Y. 5G new radio: Waveform, frame structure, multiple access, and initial access. IEEE Commun. Mag. 2017, 55, 64–71. [Google Scholar] [CrossRef]
- Zaidi, A.A.; Baldemair, R.; Molés-Cases, V.; He, N.; Werner, K.; Cedergren, A. OFDM numerology design for 5G new radio to support IoT, eMBB, and MBSFN. IEEE Commun. Stand. Mag. 2018, 2, 78–83. [Google Scholar] [CrossRef]
- Rebola, J.L.; Cartaxo, A.V.; Marques, A.S. 10 Gbps CPRI signals transmission impaired by intercore crosstalk in 5G network fronthauls with multicore fibers. Photonic Netw. Commun. 2019, 37, 409–420. [Google Scholar] [CrossRef]
- Ackermann, T.; Potschka, J.; Maiwald, T.; Hagelauer, A.; Fischer, G.; Weigel, R. A Robust Digital Predistortion Algorithm for 5G MIMO: Modeling a MIMO Scenario With Two Nonlinear MIMO Transmitters Including a Cross-Coupling Effect. IEEE Microw. Mag. 2020, 21, 54–62. [Google Scholar] [CrossRef]
- Ahamed, M.M.; Faruque, S. 5G backhaul: Requirements, challenges, and emerging technologies. In Broadband Communications Networks: Recent Advances and Lessons from Practice; BoD–Books on Demand: Norderstedt, Germany, 2018; Volume 43. [Google Scholar]
- Peralta, E.; Levanen, T.; Ihalainen, T.; Nielsen, S.; Ng, M.H.; Renfors, M.; Valkama, M. 5G new radio base-station sensitivity and performance. In Proceedings of the 2018 15th International Symposium on Wireless Communication Systems (ISWCS), Lisbon, Portugal, 28–31 August 2018; pp. 1–6. [Google Scholar]
- Bashir, A.K.; Arul, R.; Basheer, S.; Raja, G.; Jayaraman, R.; Qureshi, N.M.F. An optimal multitier resource allocation of cloud RAN in 5G using machine learning. Trans. Emerg. Telecommun. Technol. 2019, 30, e3627. [Google Scholar] [CrossRef]
- Zhang, Y.; Xin, J.; Li, X.; Huang, S. Overview on routing and resource allocation based machine learning in optical networks. Opt. Fiber Technol. 2020, 60, 102355. [Google Scholar] [CrossRef]
- Jere, S.; Fan, Q.; Shang, B.; Li, L.; Liu, L. Federated Learning in Mobile Edge Computing: An Edge-Learning Perspective for Beyond 5G. arXiv 2020, arXiv:2007.08030. [Google Scholar]
- Nama, M.; Nath, A.; Bechra, N.; Bhatia, J.; Tanwar, S.; Chaturvedi, M.; Sadoun, B. Machine learning-based traffic scheduling techniques for intelligent transportation system: Opportunities and challenges. Int. J. Commun. Syst. 2021, 34, e4814. [Google Scholar] [CrossRef]
- Sengupta, R.; Sengupta, D.; Pandey, D.; Pandey, B.K.; Nassa, V.K.; Dadeech, P. A Systematic Review of 5G Opportunities, Architecture and Challenges. In Future Trends in 5G and 6G: Challenges, Architecture, and Applications; CRC Press: Boca Raton, FL, USA, 2021; p. 247. [Google Scholar]
- Park, J.H.; Rathore, S.; Singh, S.K.; Salim, M.M.; Azzaoui, A.E.; Kim, T.W.; Pan, Y.; Park, J.H. A Comprehensive Survey on Core Technologies and Services for 5G Security: Taxonomies, Issues, and Solutions. Hum.-Centric Comput. Inf. Sci. 2021, 11. [Google Scholar] [CrossRef]
- Ree, M.d.; Parsamehr, R.; Adat, V.; Mantas, G.; Politis, I.; Rodriguez, J.; Kotsopoulos, S.; Otung, I.E.; Martínez-Ortega, J.F.; Gil-Castiñeira, F. Security for UDNs: A Step Toward 6G. In Enabling 6G Mobile Networks; Springer: Berlin/Heidelberg, Germany, 2022; pp. 167–201. [Google Scholar]
- Ferrag, M.A.; Maglaras, L.; Argyriou, A.; Kosmanos, D.; Janicke, H. Security for 4G and 5G cellular networks: A survey of existing authentication and privacy-preserving schemes. J. Netw. Comput. Appl. 2018, 101, 55–82. [Google Scholar] [CrossRef] [Green Version]
- Malhi, A.K.; Batra, S.; Pannu, H.S. Security of vehicular ad-hoc networks: A comprehensive survey. Comput. Secur. 2020, 89, 101664. [Google Scholar] [CrossRef]
- Zoli, M.; Barreto, A.N.; Köpsell, S.; Sen, P.; Fettweis, G. Physical-Layer-Security Box: A concept for time-frequency channel-reciprocity key generation. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 1–24. [Google Scholar] [CrossRef]
- Melki, R.; Noura, H.N.; Mansour, M.M.; Chehab, A. An efficient OFDM-based encryption scheme using a dynamic key approach. IEEE Internet Things J. 2018, 6, 361–378. [Google Scholar] [CrossRef]
- Melki, R.; Noura, H.N.; Mansour, M.M.; Chehab, A. A survey on OFDM physical layer security. Phys. Commun. 2019, 32, 1–30. [Google Scholar] [CrossRef]
- Lisi, F.; Losquadro, G.; Tortorelli, A.; Ornatelli, A.; Donsante, M. Multi-Connectivity in 5G terrestrial-Satellite Networks: The 5G-ALLSTAR Solution. arXiv 2020, arXiv:2004.00368. [Google Scholar]
- Lee, J.; Han, S.; Lee, J.; Kang, B.; Bae, J.; Jang, J.; Oh, S.; Chang, J.S.; Kang, S.; Son, K.Y.; et al. A sub-6-GHz 5G new radio RF transceiver supporting EN-DC with 3.15-Gb/s DL and 1.27-Gb/s UL in 14-nm FinFET CMOS. IEEE J. Solid-State Circuits 2019, 54, 3541–3552. [Google Scholar] [CrossRef]
- Linning, P.; Li, G.; Zhang, J.; Woods, R.; Liu, M.; Hu, A. An investigation of using loop-back mechanism for channel reciprocity enhancement in secret key generation. IEEE Trans. Mob. Comput. 2018, 18, 507–519. [Google Scholar]
- Vogt, H.; Awan, Z.H.; Sezgin, A. Secret-key generation: Full-duplex versus half-duplex probing. IEEE Trans. Commun. 2018, 67, 639–652. [Google Scholar] [CrossRef]
- Kalbande, D.; Haji, S.; Haji, R. 6G-Next Gen mobile wireless communication approach. In Proceedings of the 2019 3rd international conference on electronics, communication and aerospace technology (ICECA), Coimbatore, India, 12–14 June 2019; pp. 1–6. [Google Scholar]
- Mistry, Z.; Kumar Yadav, A.; Kothari, M.A.; Kothari, M. A Review on 6th Generation Wireless Communication Networks Based on Artificial Intelligence. In Innovations in Cyber Physical Systems; Springer: Berlin/Heidelberg, Germany, 2021; pp. 275–286. [Google Scholar]
- Sánchez, J.D.V.; Urquiza-Aguiar, L.; Paredes, M.C.P. Physical layer security for 5G wireless networks: A comprehensive survey. In Proceedings of the 2019 3rd cyber security in networking conference (CSNet), Quito, Ecuador, 23–25 October 2019; pp. 122–129. [Google Scholar]
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. Overview of 5G security challenges and solutions. IEEE Commun. Stand. Mag. 2018, 2, 36–43. [Google Scholar] [CrossRef] [Green Version]
- Suraci, C.; Araniti, G.; Abrardo, A.; Bianchi, G.; Iera, A. A stakeholder-oriented security analysis in virtualized 5G cellular networks. Comput. Netw. 2021, 184, 107604. [Google Scholar] [CrossRef]
- Köksal, S.; Dalveren, Y.; Maiga, B.; Kara, A. Distributed denial-of-service attack mitigation in network functions virtualization-based 5G networks using management and orchestration. Int. J. Commun. Syst. 2021, 34, e4825. [Google Scholar] [CrossRef]
- Prabakaran, D.; Nizar, S.M.; Kumar, K.S. Software-defined network (SDN) architecture and security considerations for 5G communications. In Design Methodologies and Tools for 5G Network Development and Application; IGI Global: Hershey, PA, USA, 2021; pp. 28–43. [Google Scholar]
- Khan, H.; Martin, K.M. A survey of subscription privacy on the 5G radio interface-The past, present and future. J. Inf. Secur. Appl. 2020, 53, 102537. [Google Scholar] [CrossRef]
- Zhang, S.; Wang, Y.; Zhou, W. Towards secure 5G networks: A Survey. Comput. Netw. 2019, 162, 106871. [Google Scholar] [CrossRef]
- Prasad, V.K.; Tanwar, S.; Bhavsar, M.D. Advance Cloud Data Analytics for 5G Enabled IoT. In Blockchain for 5G-Enabled IoT; Springer: Berlin/Heidelberg, Germany, 2021; pp. 159–180. [Google Scholar]
- Zhang, R.; Zhou, W.; Hu, H. Towards 5G Security Analysis against Null Security Algorithms Used in Normal Communication. Secur. Commun. Netw. 2021, 2021, 4498324. [Google Scholar] [CrossRef]
- Wijethilaka, S.; Liyanage, M. Survey on network slicing for Internet of Things realization in 5G networks. IEEE Commun. Surv. Tutor. 2021, 23, 957–994. [Google Scholar] [CrossRef]
- Madi, T.; Alameddine, H.A.; Pourzandi, M.; Boukhtouta, A. NFV security survey in 5G networks: A three-dimensional threat taxonomy. Comput. Netw. 2021, 197, 108288. [Google Scholar] [CrossRef]
- Yurekten, O.; Demirci, M. SDN-based cyber defense: A survey. Future Gener. Comput. Syst. 2021, 115, 126–149. [Google Scholar] [CrossRef]
- Yang, P.; Xiong, N.; Ren, J. Data security and privacy protection for cloud storage: A survey. IEEE Access 2020, 8, 131723–131740. [Google Scholar] [CrossRef]
- Yue, K.; Zhang, Y.; Chen, Y.; Li, Y.; Zhao, L.; Rong, C.; Chen, L. A Survey of Decentralizing Applications via Blockchain: The 5G and Beyond Perspective. IEEE Commun. Surv. Tutor. 2021, 23, 2191–2217. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.; Liyanage, M. Mec-enabled 5g use cases: A survey on security vulnerabilities and countermeasures. ACM Comput. Surv. (CSUR) 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Ubale, T.; Jain, A.K. Survey on DDoS attack techniques and solutions in software-defined network. In Handbook of Computer Networks and Cyber Security; Springer: Berlin/Heidelberg, Germany, 2020; pp. 389–419. [Google Scholar]
- Sharma, A.; Balasubramanian, V.; Jolfaei, A. Security Challenges and Solutions for 5G HetNet. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December–1 January 2021; pp. 1318–1323. [Google Scholar]
- Mahdi, M.N.; Ahmad, A.R.; Qassim, Q.S.; Natiq, H.; Subhi, M.A.; Mahmoud, M. From 5G to 6G Technology: Meets Energy, Internet-of-Things and Machine Learning: A Survey. Appl. Sci. 2021, 11, 8117. [Google Scholar] [CrossRef]
- Arfaoui, M.A.; Soltani, M.D.; Tavakkolnia, I.; Ghrayeb, A.; Safari, M.; Assi, C.M.; Haas, H. Physical layer security for visible light communication systems: A survey. IEEE Commun. Surv. Tutorials 2020, 22, 1887–1908. [Google Scholar] [CrossRef] [Green Version]
- Sánchez, J.D.V.; Urquiza-Aguiar, L.; Paredes, M.C.P.; Osorio, D.P.M. Survey on physical layer security for 5G wireless networks. Ann. Telecommun. 2021, 76, 155–174. [Google Scholar] [CrossRef]
- Ning, B.; Chen, Z.; Tian, Z.; Wang, X.; Pan, C.; Fang, J.; Li, S. Joint Power Allocation and Passive Beamforming Design for IRS-Assisted Physical-Layer Service Integration. IEEE Trans. Wirel. Commun. 2021, 20, 7286–7301. [Google Scholar] [CrossRef]
- Jayakody, D.N.K.; Srinivasan, K.; Sharma, V. 5G Enabled Secure Wireless Networks; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Mei, W.; Chen, Z.; Fang, J.; Li, S. Physical layer service integration in 5G: Potentials and challenges. IEEE Access 2018, 6, 16563–16575. [Google Scholar] [CrossRef]
- Ahmed, M.; Bai, L. Secrecy capacity of artificial noise aided secure communication in MIMO Rician channels. IEEE Access 2018, 6, 7921–7929. [Google Scholar] [CrossRef]
- Rommel, S.; Grivas, E.; Cimoli, B.; Dodane, D.; Morales, A.; Pikasis, E.; Bourderionnet, J.; Feugnet, G.; Carvalho, J.B.; Katsikis, M.; et al. Real-time high-bandwidth mm-wave 5G NR signal transmission with analog radio-over-fiber fronthaul over multi-core fiber. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 1–20. [Google Scholar] [CrossRef]
- Yousefi, F.; Rahbar, A.G. Novel crosstalk, fragmentation-aware algorithms in space division multiplexed-Elastic Optical Networks (SDM-EON) with considering physical layer security. Opt. Switch. Netw. 2020, 37, 100566. [Google Scholar] [CrossRef]
- Brasileiro, Í.; Costa, L.; Drummond, A. A survey on crosstalk and routing, modulation selection, core and spectrum allocation in elastic optical networks. arXiv 2019, arXiv:1907.08538. [Google Scholar]
- Cao, Y.; Zhao, Y.; Yu, X.; Ou, Q.; Liu, Z.; Liao, X.; Zhang, J. Mode conversion-based crosstalk-aware routing, spectrum and mode assignment in space-division multiplexing elastic optical networks. In Proceedings of the 2017 16th International Conference on Optical Communications and Networks (ICOCN), Wuzhen, China, 7–10 August 2017; pp. 1–3. [Google Scholar]
- Zhu, J.; Zhu, Z. Physical-layer security in MCF-based SDM-EONs: Would crosstalk-aware service provisioning be good enough? J. Light. Technol. 2017, 35, 4826–4837. [Google Scholar] [CrossRef]
- Zhao, Y.; Hu, L.; Zhu, R.; Yu, X.; Wang, X.; Zhang, J. Crosstalk-aware spectrum defragmentation based on spectrum compactness in space division multiplexing enabled elastic optical networks with multicore fiber. IEEE Access 2018, 6, 15346–15355. [Google Scholar] [CrossRef]
- Yang, H.; Zhan, K.; Kadoch, M.; Liang, Y.; Cheriet, M. BLCS: Brain-like distributed control security in cyber physical systems. IEEE Netw. 2020, 34, 8–15. [Google Scholar] [CrossRef]
- Nguyen, V.L.; Lin, P.C.; Cheng, B.C.; Hwang, R.H.; Lin, Y.D. Security and privacy for 6G: A survey on prospective technologies and challenges. IEEE Commun. Surv. Tutorials 2021, 23, 2384–2428. [Google Scholar] [CrossRef]
- Ziegler, V.; Viswanathan, H.; Flinck, H.; Hoffmann, M.; Räisänen, V.; Hätönen, K. 6G architecture to connect the worlds. IEEE Access 2020, 8, 173508–173520. [Google Scholar] [CrossRef]
- Zhang, Z.; Xiao, Y.; Ma, Z.; Xiao, M.; Ding, Z.; Lei, X.; Karagiannidis, G.K.; Fan, P. 6G wireless networks: Vision, requirements, architecture, and key technologies. IEEE Veh. Technol. Mag. 2019, 14, 28–41. [Google Scholar] [CrossRef]
- Kakkar, A. A survey on secure communication techniques for 5G wireless heterogeneous networks. Inf. Fusion 2020, 62, 89–109. [Google Scholar] [CrossRef]
- Suomalainen, J.; Juhola, A.; Shahabuddin, S.; Mämmelä, A.; Ahmad, I. Machine learning threatens 5G security. IEEE Access 2020, 8, 190822–190842. [Google Scholar] [CrossRef]
- Haider, N.; Baig, M.Z.; Imran, M. Artificial Intelligence and Machine Learning in 5G Network Security: Opportunities, advantages, and future research trends. arXiv 2020, arXiv:2007.04490. [Google Scholar]
- Dogra, A.; Jha, R.K.; Jain, S. A survey on beyond 5G network with the advent of 6G: Architecture and emerging technologies. IEEE Access 2020, 9, 67512–67547. [Google Scholar] [CrossRef]
- Jiang, W.; Han, B.; Habibi, M.A.; Schotten, H.D. The road towards 6G: A comprehensive survey. IEEE Open J. Commun. Soc. 2021, 2, 334–366. [Google Scholar] [CrossRef]
- Yrjola, S. Technology antecedents of the platform-based ecosystemic business models beyond 5G. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Seoul, Korea, 6–9 April 2020; pp. 1–8. [Google Scholar]
- Boulogeorgos, A.A.A.; Alexiou, A.; Merkle, T.; Schubert, C.; Elschner, R.; Katsiotis, A.; Stavrianos, P.; Kritharidis, D.; Chartsias, P.K.; Kokkoniemi, J.; et al. Terahertz technologies to deliver optical network quality of experience in wireless systems beyond 5G. IEEE Commun. Mag. 2018, 56, 144–151. [Google Scholar] [CrossRef] [Green Version]
- Basu, D.; Datta, R.; Ghosh, U. Softwarized Network Function Virtualization for 5G: Challenges and Opportunities. In Internet of Things and Secure Smart Environments; Chapman and Hall/CRC: Boca Raton, FL, USA, 2020; pp. 147–192. [Google Scholar]
- Santos, J.F.; Liu, W.; Jiao, X.; Neto, N.V.; Pollin, S.; Marquez-Barja, J.M.; Moerman, I.; DaSilva, L.A. Breaking Down Network Slicing: Hierarchical Orchestration of End-to-End Networks. IEEE Commun. Mag. 2020, 58, 16–22. [Google Scholar] [CrossRef]
- Nguyen, V.L.; Lin, P.C.; Hwang, R.H. Enhancing misbehavior detection in 5G vehicle-to-vehicle communications. IEEE Trans. Veh. Technol. 2020, 69, 9417–9430. [Google Scholar] [CrossRef]
- Jain, A.; Lopez-Aguilera, E.; Demirkol, I. Are mobility management solutions ready for 5G and beyond? Comput. Commun. 2020, 161, 50–75. [Google Scholar] [CrossRef]
- Alotaibi, D. Survey on Network Slice Isolation in 5G Networks: Fundamental Challenges. Procedia Comput. Sci. 2021, 182, 38–45. [Google Scholar] [CrossRef]
- Ziani, A.; Medouri, A. A Survey of Security and Privacy for 5G Networks. In Emerging Trends in ICT for Sustainable Development; Springer: Berlin/Heidelberg, Germany, 2021; pp. 201–208. [Google Scholar]
- Kakkavas, G.; Stamou, A.; Karyotis, V.; Papavassiliou, S. Network Tomography for Efficient Monitoring in SDN-Enabled 5G Networks and Beyond: Challenges and Opportunities. IEEE Commun. Mag. 2021, 59, 70–76. [Google Scholar] [CrossRef]
- Yuan, G. Key Technologies and Analysis of Computer-based 5G Mobile Communication Network. In Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2021; Volume 1992, p. 042001. [Google Scholar]
- Zhang, Y.; Kishk, M.A.; Alouini, M.S. A survey on integrated access and backhaul networks. arXiv 2021, arXiv:2101.01286. [Google Scholar] [CrossRef]
- Döhler, A. Report from the Next Generation Mobile Networks Alliance. IEEE Netw. 2021, 35, 3. [Google Scholar] [CrossRef]
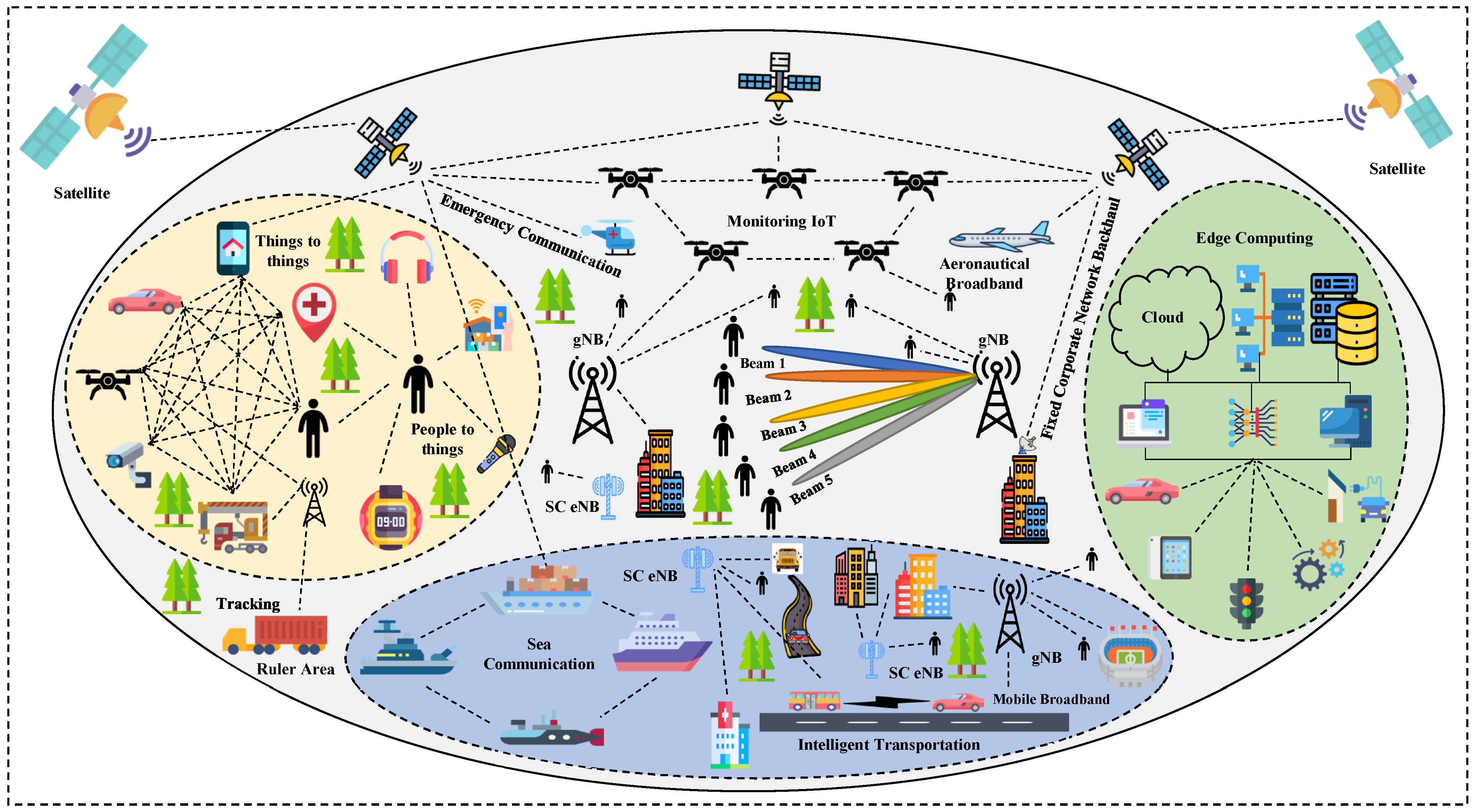
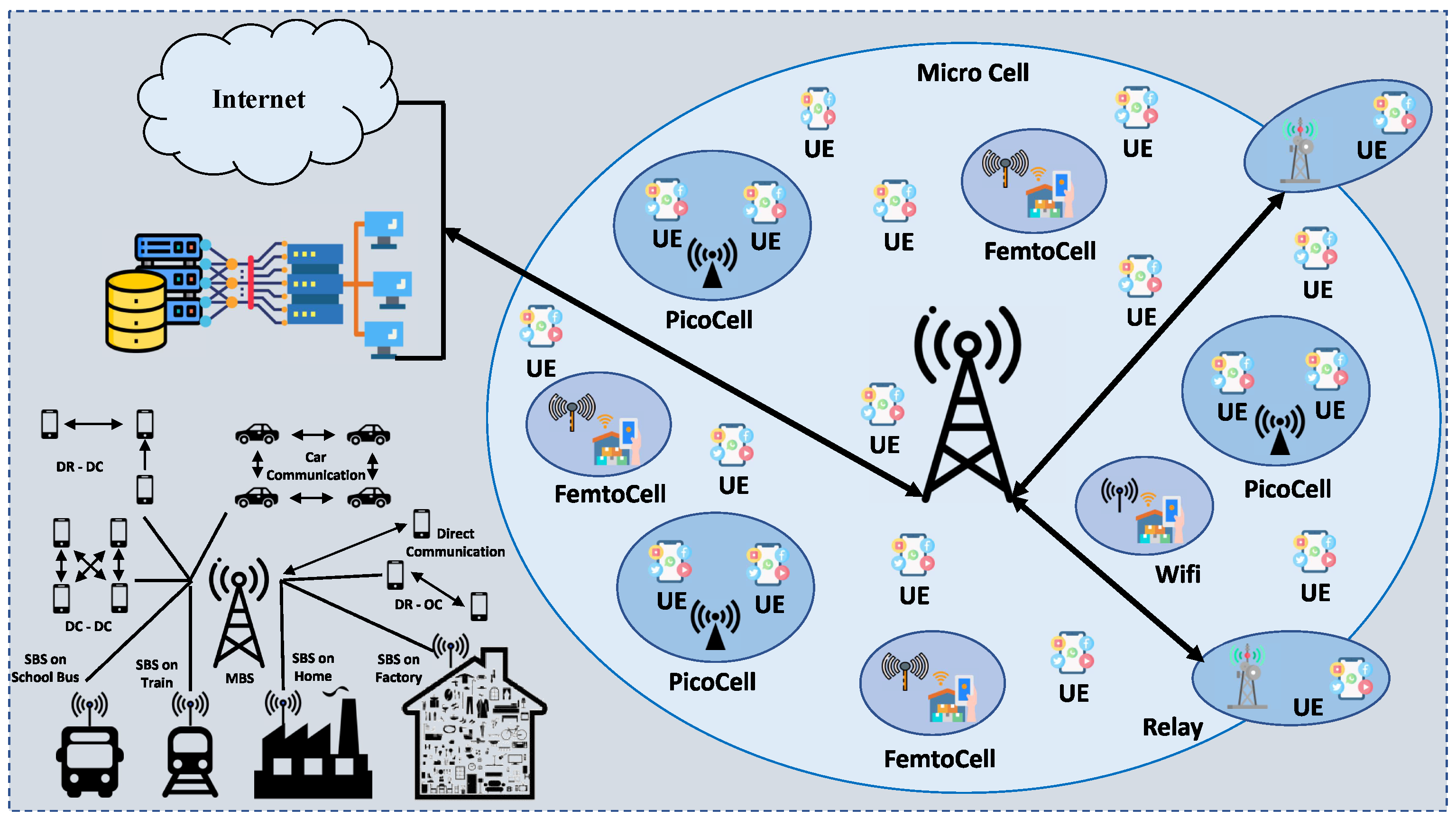
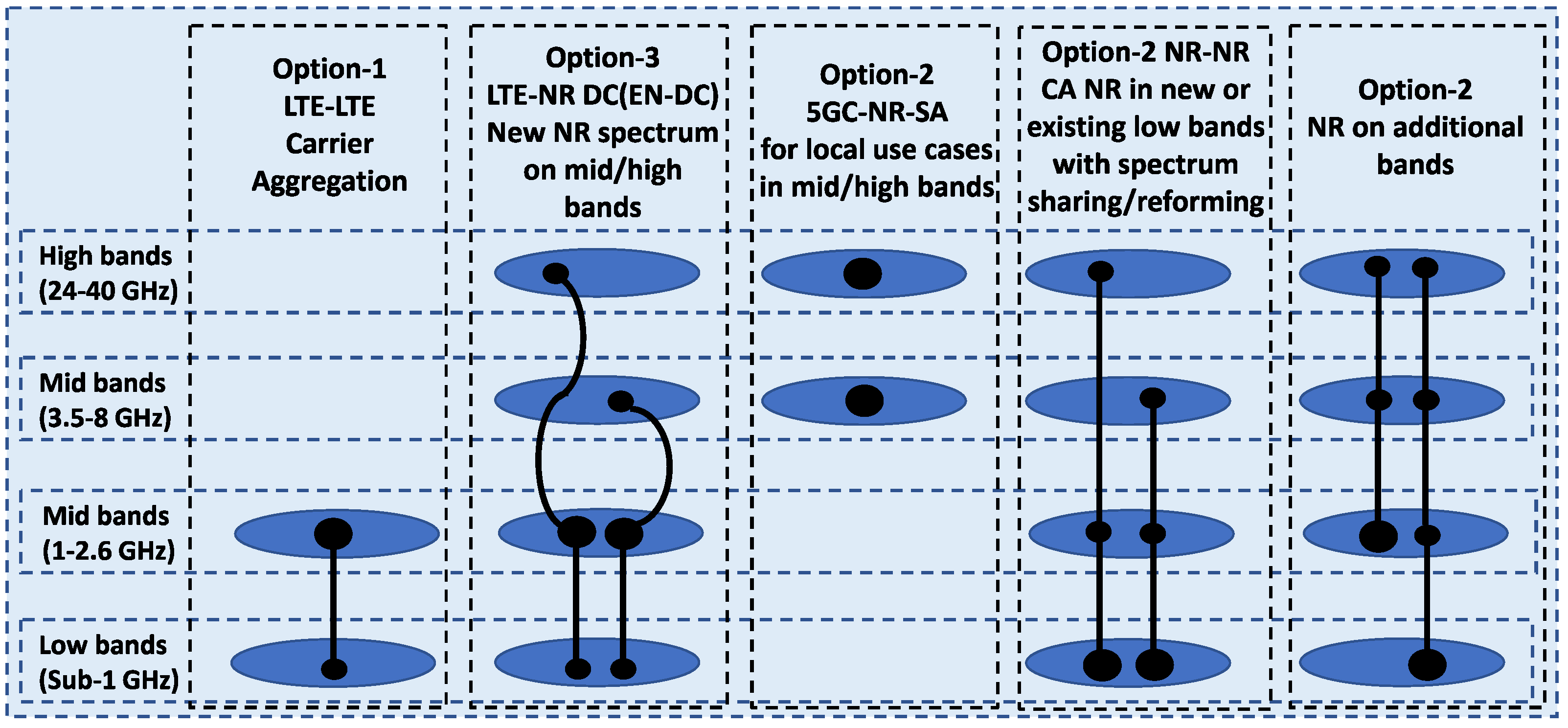
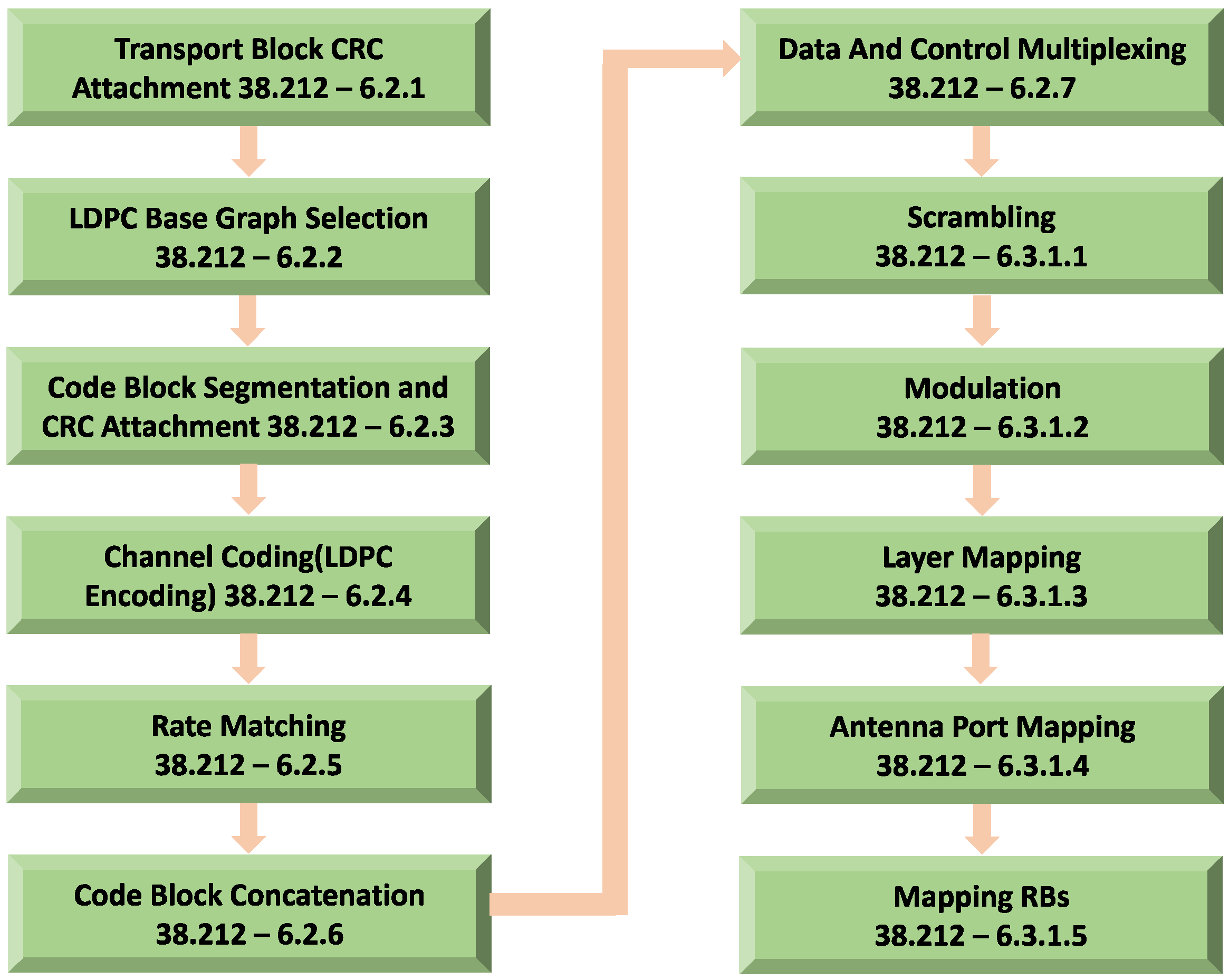
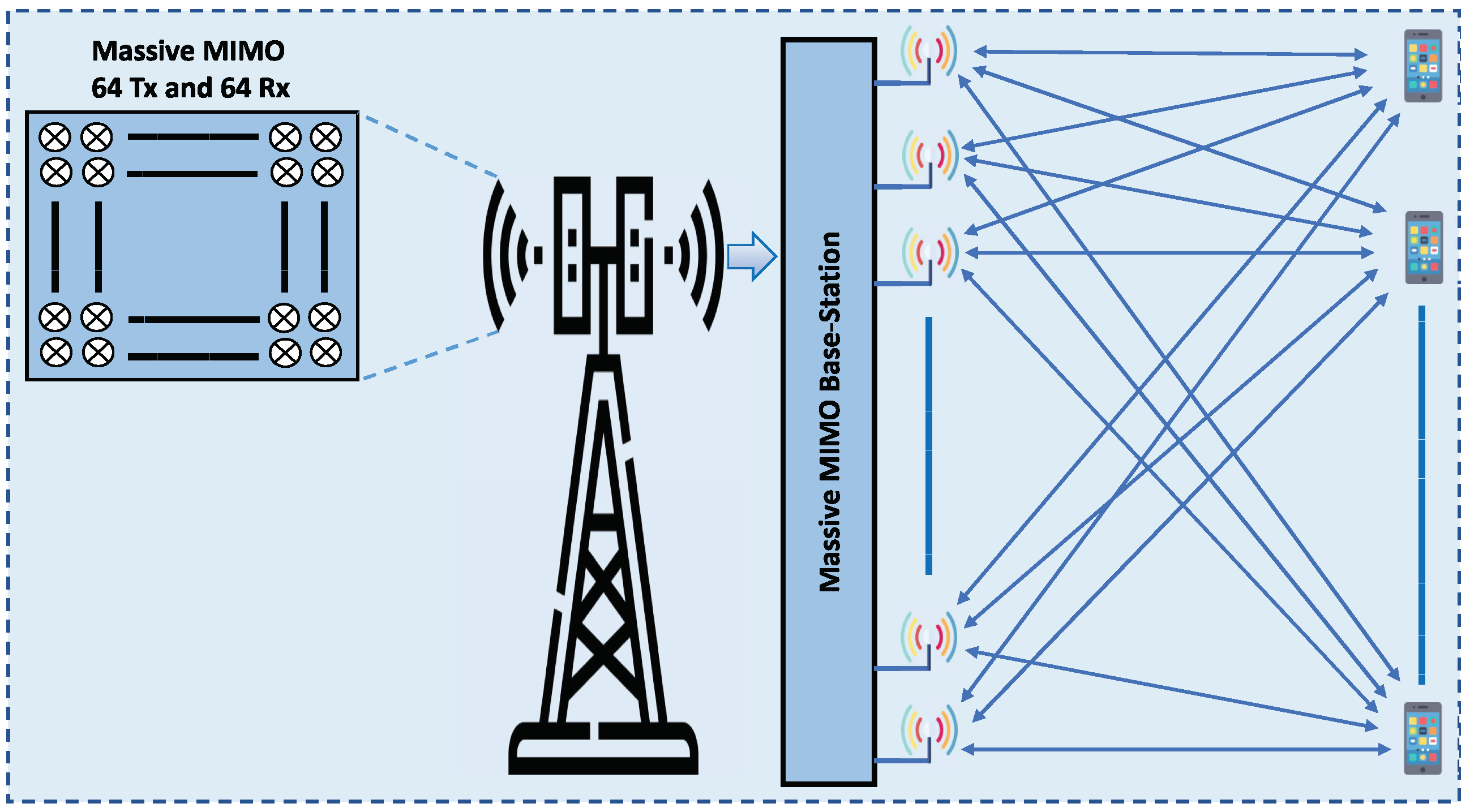
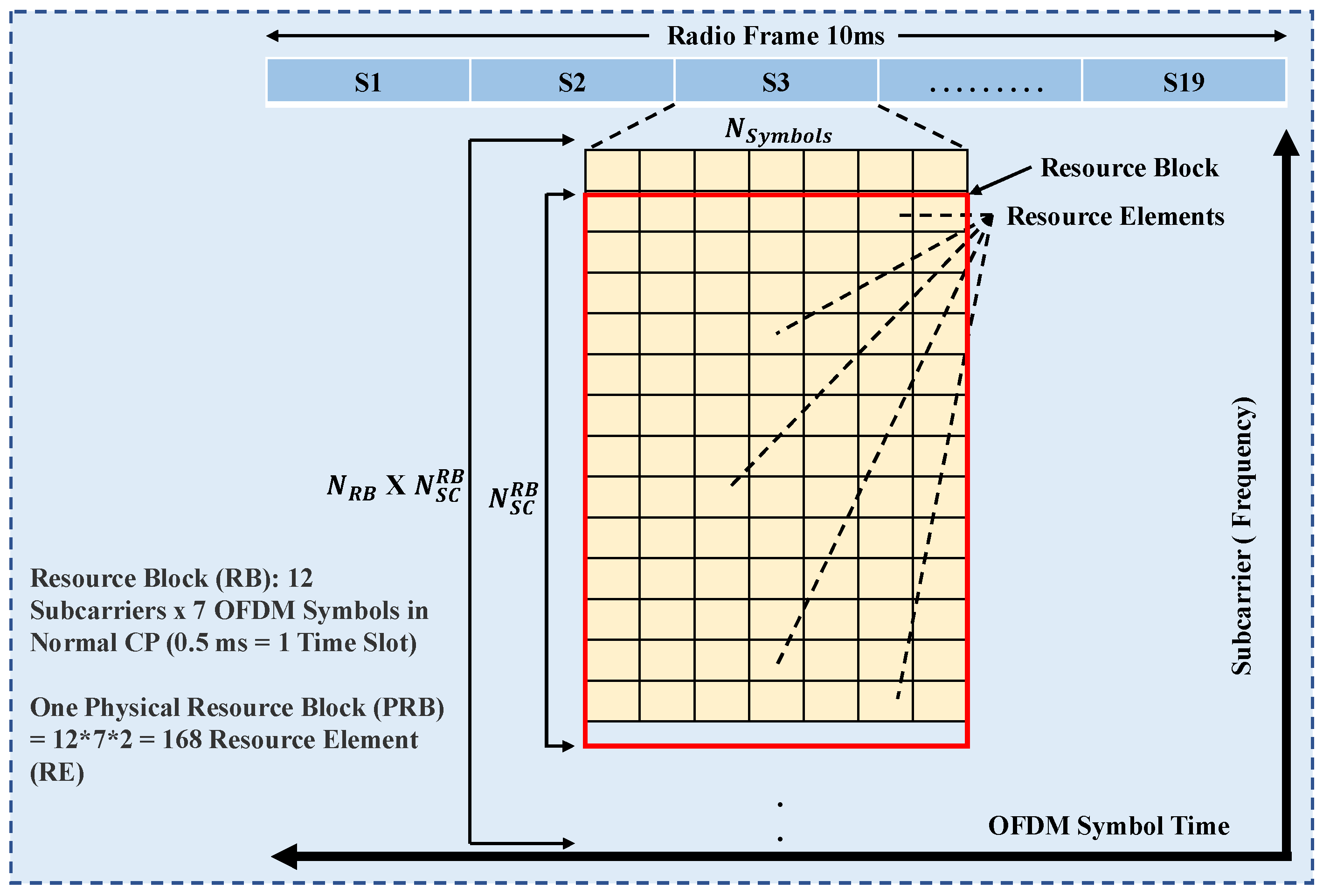
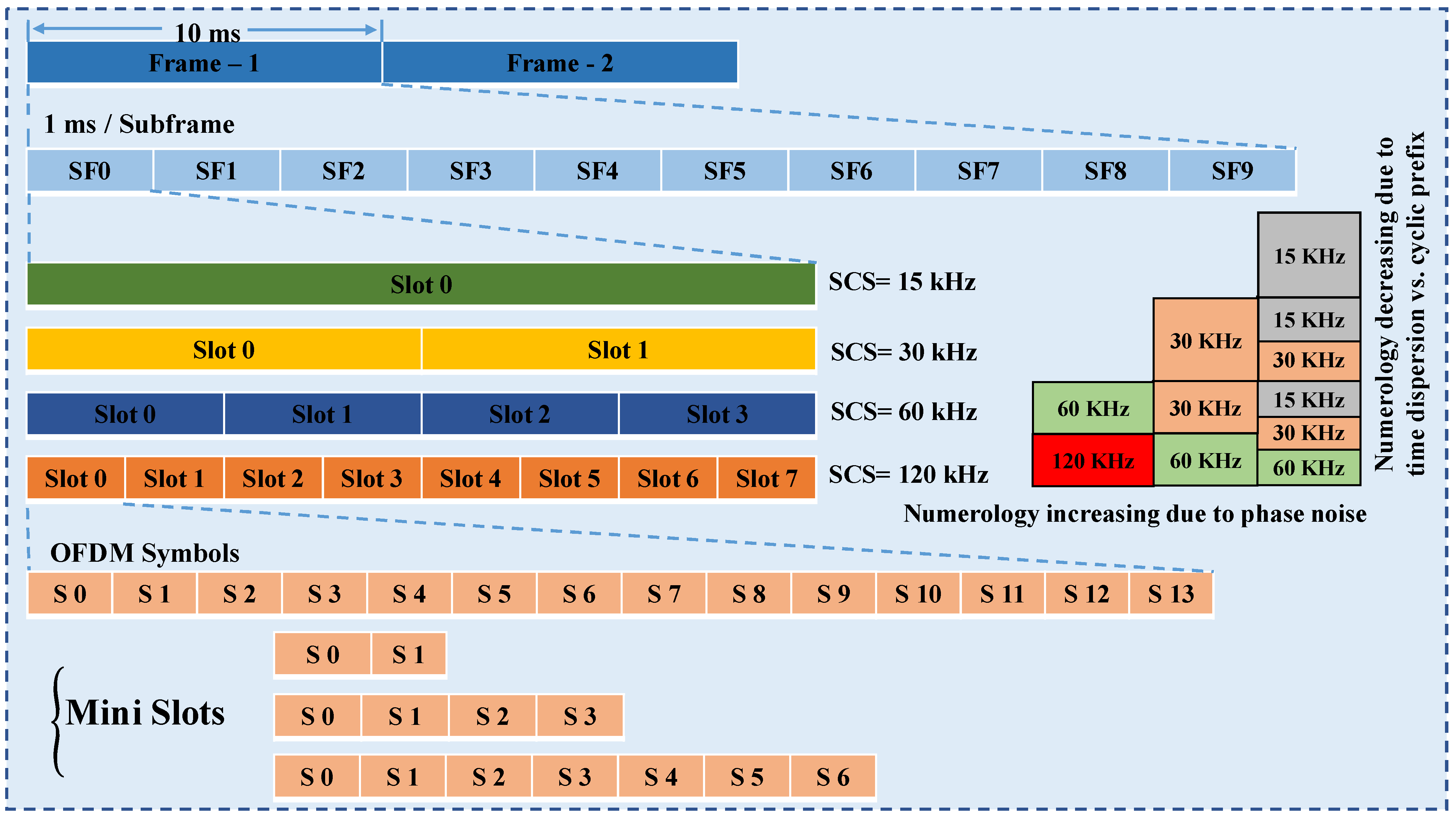
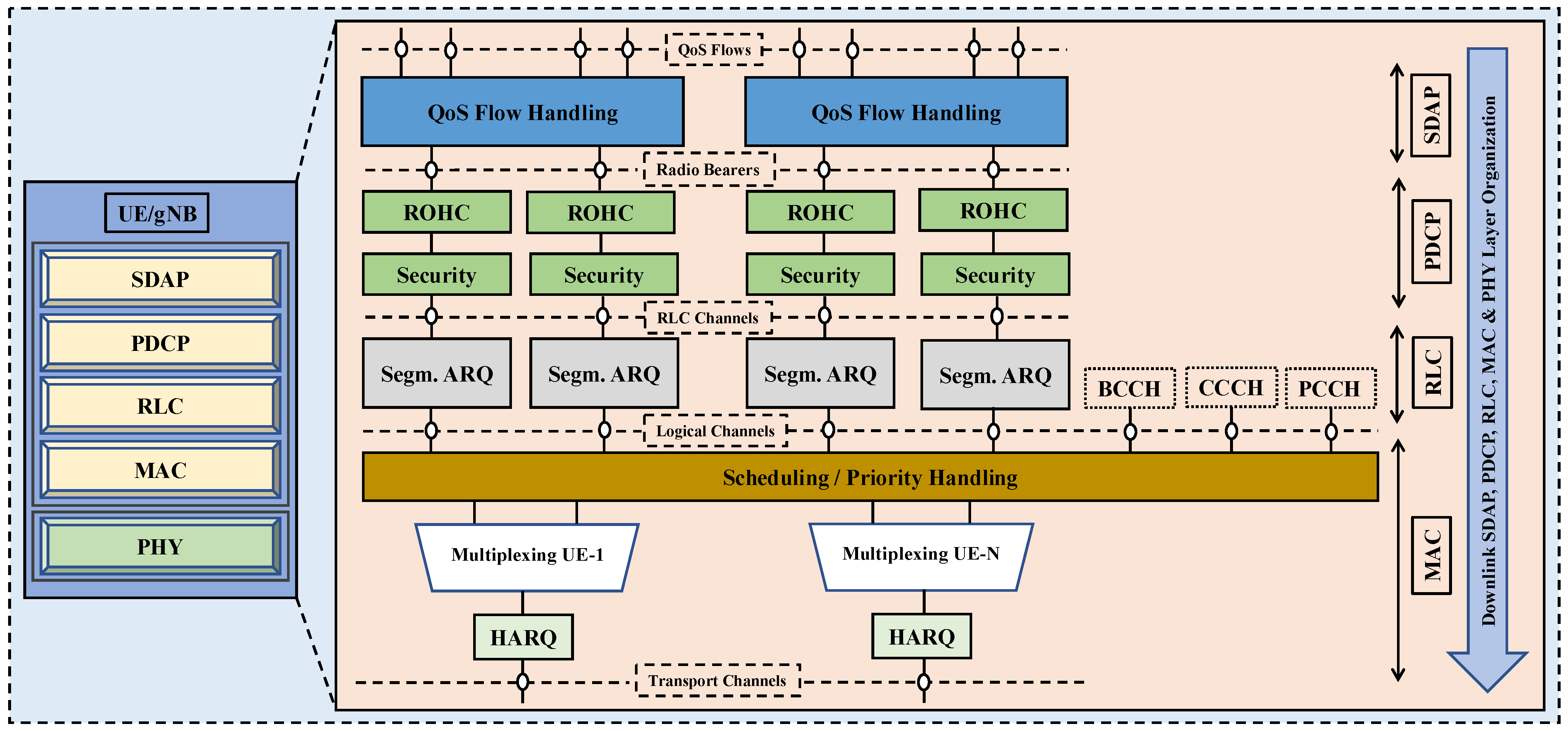
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tanveer, J.; Haider, A.; Ali, R.; Kim, A. Machine Learning for Physical Layer in 5G and beyond Wireless Networks: A Survey. Electronics 2022, 11, 121. https://doi.org/10.3390/electronics11010121
Tanveer J, Haider A, Ali R, Kim A. Machine Learning for Physical Layer in 5G and beyond Wireless Networks: A Survey. Electronics. 2022; 11(1):121. https://doi.org/10.3390/electronics11010121
Chicago/Turabian StyleTanveer, Jawad, Amir Haider, Rashid Ali, and Ajung Kim. 2022. "Machine Learning for Physical Layer in 5G and beyond Wireless Networks: A Survey" Electronics 11, no. 1: 121. https://doi.org/10.3390/electronics11010121
APA StyleTanveer, J., Haider, A., Ali, R., & Kim, A. (2022). Machine Learning for Physical Layer in 5G and beyond Wireless Networks: A Survey. Electronics, 11(1), 121. https://doi.org/10.3390/electronics11010121







