The State of Ethereum Smart Contracts Security: Vulnerabilities, Countermeasures, and Tool Support
Abstract
:1. Introduction
- RQ1: What vulnerabilities in Ethereum smart contracts have been recently studied?
- RQ2: What are possible countermeasures to mitigate smart-contract vulnerabilities?
- RQ3: What are the accuracy, efficiency, and limitations of existing security-analysis tools for smart contracts?
1.1. Methodology
1.2. Contributions
1.3. Organization
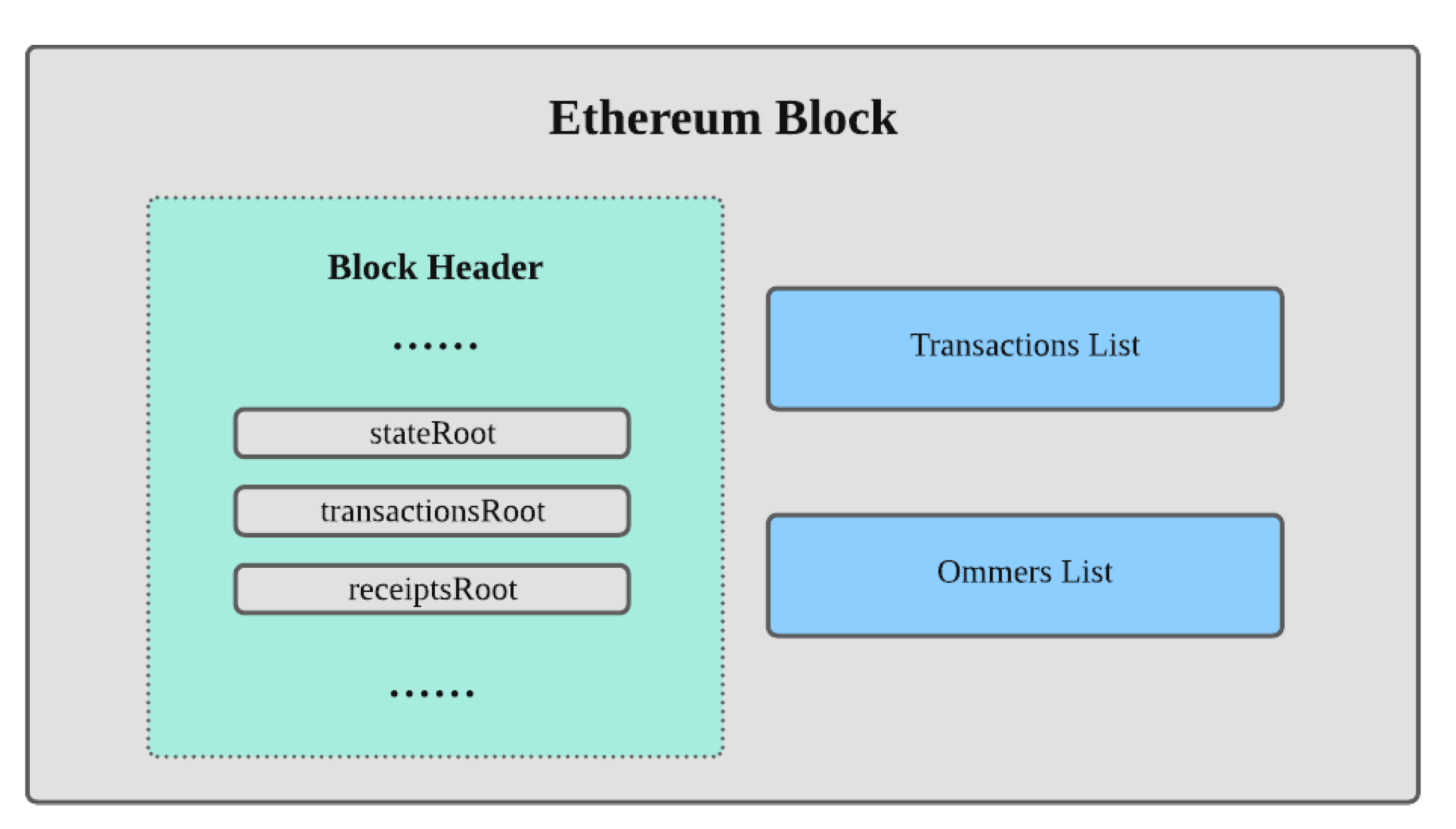
2. Background
2.1. Ethereum Accounts
2.2. Life Cycle of Smart Contracts
- Creation. In its creation stage, an EVM can be targeted by multiple high-level languages, such as Solidity [4], Serpent [23] or Bamboo [24]. The most commonly used one is Solidity. It is a JavaScript-like language and Turing-complete. EVM cannot run the Solidity codes directly, so they are compiled to opcodes(low-level instructions used by EVM) and encoded to bytecodes for storage reasons.
- Deployment. The Ethereum protocol outlines two kinds of transactions: one that invokes message calls, and the other that results in contract deployment [21]. The developer initiates a transaction that contains bytecodes (stored in a field called init in the transaction structure), and this action returns another fragment of the code that will be stored in the EVM running environment and will be executed later.
- Execution. While in the execution stage, a smart contract is a running program, like a process or thread in a stand-alone computer. It will receive transactions (the first type) and the data that will be passed to the contract as parameters. Then, the EVM executes the instructions one by one until finished or the gas limitation is reached. This process happens at the time a new block is mined.
- Completion. After the execution, states are updated and stored in blockchains together with transactions. This completes the life cycle of the smart contract.
2.3. Ethereum Running Environment
3. Related Work
3.1. Smart-Contracts Vulnerabilities
3.2. Security-Analysis Tools and Methods
3.2.1. Static Analysis
3.2.2. Dynamic Analysis
3.2.3. Formal Verification
4. Smart-Contracts Vulnerabilities and Countermeasures
4.1. The Proposed Taxonomy
4.2. Vulnerabilities and Countermeasures
4.2.1. Re-Entrancy
- contract A {
- mapping (address => uint) public balances;
- function withdraw (uint _amount) public {
- msg.sender.call{value: _amount}(“”);
- balances [msg.sender] −= _amount;
- }
- /∗Other codes∗/
- }
- contract Attacker {
- A public a;
- fallback() external payable {
- a.withdraw(1 ether);
- }
- function attack(){
- a.withdraw(1 ether);
- }
- }
4.2.2. Arithmetic Issues
4.2.3. Delegatecall to Insecure Contracts
- contract VulernableContract {
- address public owner;
- InsecureContract public c;
- constructor (InsecureContract _c) public {
- owner = msg.sender;
- c = InsecureContact (_c);
- }
- /∗Other codes...∗/
- c.delegatecall (abi.encodeWithSignature(“doSomething()”));
- /∗Other codes...∗/
- }
- contract InsecureContract {
- address public owner;
- function doSomething () public {
- /∗Other codes...∗/
- owner = msg.sender;
- /∗Other codes...∗/
- }
- }
4.2.4. Selfdestruct
4.2.5. Freezing Ether
4.2.6. Randomness Generation
4.2.7. tx.origin
4.2.8. Mishandled Exceptions
4.2.9. Timestamp Dependence
4.2.10. Transaction Order Dependence
4.2.11. Default Visibility
4.2.12. External Contract Referencing
4.2.13. Short Address/Parameter Issues
4.3. Vulnerability Causes
- Visibility: Ethereum records all of its validated historical transactions in world state (refer to Section 2), which is visible to the whole network. This visibility may cause some problems when the smart-contract owner wants to keep it from the public due to privacy concerns. Prior studies have shown that inspecting accumulated transactions’ statistic characteristics and leveraging analysis graph structures could reveal valuable and practical information, given users are granted anonymity with pseudonymous public keys [86,87].
- Opacity: On the other hand, the opacity of smart contracts poses another concern. Live contracts need rigid inspection and source-code audits since they manage millions of USD. However, 77% of running smart contracts are opaque and hold USD 3 billion [88].
- Immutability: Smart contracts cannot be modified once deployed on Ethereum. This immutability perpetuates problematic contracts on the chain. Workarounds such as updating contracts or addresses at the user side could solve the problem to a certain degree, however, they introduce other security concerns.
- Automated Execution: A control flow transfer (CFT) between two instructions A and B means that after A’s execution, B is excuted immediately. When smart contracts interact with each other, those CFTs are not always under control. In the uncontrolled-function call-permission cases, the self-elevation of a malicious attacker could happen by triggering some high-privilege functions [85].
- Mining: Which transactions to be processed depends on the miner’s choice. The deterministic result of a single transaction’s execution no longer exists when multiple transactions are involved. Their execution order may vary based on the miner’s choice. This uncertainty severely affects order-sensitive transactions. The final result of a series of transactions might reach vastly different outcomes.
- EVM: EVM structure provides a stand-alone, isolated running-time environment (sandbox) for smart contracts.EVM utilizes an oracle to handle the incoming real-world inputs. An oracle is a concept that bridges blockchain and the real world and acts as APIs on chain, which can be accessed by the smart contracts to receive feeds from the real world [89]. Centralized oracles introduce several attack vectors and issues to smart contract such as integrity, accuracy, and consistency [90]. However, the decentralized designs of oracle such as Chainlink [91] are trying to solve this problem.
- Immature Programming Language: Solidity is an evolving programming language and its widely known vulnerability is the re-entrancy problem, which is caused by the fallback mechanism in Solidity. Mishandled exceptions could be a severe problem for smart contracts too.
5. Security-Analysis Tools
5.1. Recent Security-Tools Support
5.2. Comparisons
6. Discussion
6.1. Findings
6.2. Threats to Validity
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Schär, F. Decentralized finance: On blockchain-and smart contract-based financial markets. SSRN 2020, 2020, 3571335. [Google Scholar] [CrossRef]
- Bartoletti, M.; Pompianu, L. An empirical analysis of smart contracts: Platforms, applications, and design patterns. In Proceedings of the International Conference on Financial Cryptography and Data Security, Sliema, Malta, 3–7 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 494–509. [Google Scholar]
- Ethereum. Available online: http://www.ethereum.org/ (accessed on 19 January 2022).
- Foundation, E. Available online: https://docs.soliditylang.org/en/v0.8.2/index.html (accessed on 19 January 2022).
- Coin Market Cap. 2013. Available online: https://coinmarketcap.com/currencies/ethereum/ (accessed on 19 January 2022).
- DefiPulse. 2019. Available online: https://defipulse.com/ (accessed on 19 January 2022).
- CoinMarketCap. 2013. Available online: https://coinmarketcap.com/ (accessed on 19 January 2022).
- Nakamoto, S.; Bitcoin, A. A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 19 January 2022).
- Patron, T. What’s the Big Idea Behind Ethereum’s World Computer? 2016. Available online: https://www.coindesk.com/whats-big-idea-behind-ethereums-world-computer (accessed on 19 January 2022).
- Mehar, M.I.; Shier, C.L.; Giambattista, A.; Gong, E.; Fletcher, G.; Sanayhie, R.; Kim, H.M.; Laskowski, M. Understanding a revolutionary and flawed grand experiment in blockchain: The DAO attack. J. Cases Inf. Technol. (JCIT) 2019, 21, 19–32. [Google Scholar] [CrossRef] [Green Version]
- Dika, A. Ethereum Smart Contracts: Security Vulnerabilities and Security Tools. Master’s Thesis, Norwegian University of Science and Technology, Trondheim, Norway, December 2017. [Google Scholar]
- Alharby, M.; Van Moorsel, A. Blockchain-based smart contracts: A systematic mapping study. arXiv 2017, arXiv:1710.06372. [Google Scholar]
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making Smart Contracts Smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security (CCS’16), Vienna, Austria, 24–28 October 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 254–269. [Google Scholar] [CrossRef]
- Chen, H.; Pendleton, M.; Njilla, L.; Xu, S. A Survey on Ethereum Systems Security: Vulnerabilities, Attacks, and Defenses. ACM Comput. Surv. 2020, 53, 67. [Google Scholar] [CrossRef]
- Tang, X.; Zhou, K.; Cheng, J.; Li, H.; Yuan, Y. The Vulnerabilities in Smart Contracts: A Survey. In Advances in Artificial Intelligence and Security; Sun, X., Zhang, X., Xia, Z., Bertino, E., Eds.; Springer International Publishing: Cham, Switzerland, 2021; pp. 177–190. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef] [Green Version]
- Zhu, L.H.; Zheng, B.K.; Shen, M.; Gao, F.; Li, H.Y.; Shi, K.X. Data Security and Privacy in Bitcoin System: A Survey. J. Comput. Sci. Technol. 2020, 35, 843–862. [Google Scholar] [CrossRef]
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the Attack Surface of Blockchain: A Systematic Overview. arXiv 2019, arXiv:1904.03487. [Google Scholar]
- di Angelo, M.; Salzer, G. A Survey of Tools for Analyzing Ethereum Smart Contracts. In Proceedings of the 2019 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPCON), Newark, CA, USA, 4–9 April 2019; pp. 69–78. [Google Scholar] [CrossRef]
- Buterin, V. A Next-Generation Smart Contract and Decentralized Application Platform; Ethereum Foundation: Zug, Switzerland, 2013. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, W.; Chen, X.; Weng, J.; Imran, M. An overview on smart contracts: Challenges, advances and platforms. Future Gener. Comput. Syst. 2020, 105, 475–491. [Google Scholar] [CrossRef] [Green Version]
- Vbuterin. Serpent. Available online: https://github.com/ethereum/serpent (accessed on 19 January 2022).
- CornellBlockchain. Bamboo. Available online: https://github.com/CornellBlockchain/bamboo (accessed on 19 January 2022).
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In Proceedings of the International Conference on Principles of Security and Trust, Uppsala, Sweden, 24–25 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 164–186. [Google Scholar]
- Dingman, W.; Cohen, A.; Ferrara, N.; Lynch, A.; Jasinski, P.; Black, P.E.; Deng, L. Defects and vulnerabilities in smart contracts, a classification using the NIST bugs framework. Int. J. Netw. Distrib. Comput. 2019, 7, 121–132. [Google Scholar] [CrossRef] [Green Version]
- Grishchenko, I.; Maffei, M.; Schneidewind, C. A Semantic Framework for the Security Analysis of Ethereum Smart Contracts. In Principles of Security and Trust; Bauer, L., Küsters, R., Eds.; Springer: Cham, Switzerland, 2018; pp. 243–269. [Google Scholar]
- Praitheeshan, P.; Pan, L.; Yu, J.; Liu, J.; Doss, R. Security analysis methods on Ethereum smart contract vulnerabilities: A survey. arXiv 2019, arXiv:1908.08605. [Google Scholar]
- Huang, Y.; Bian, Y.; Li, R.; Zhao, J.L.; Shi, P. Smart contract security: A software lifecycle perspective. IEEE Access 2019, 7, 150184–150202. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Durieux, T.; Ferreira, J.A.F.; Abreu, R.; Cruz, P. Empirical Review of Automated Analysis Tools on 47,587 Ethereum Smart Contracts. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Korea, 27 June–19 July 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 530–541. [Google Scholar] [CrossRef]
- Tantikul, P.; Ngamsuriyaroj, S. Exploring Vulnerabilities in Solidity Smart Contract. In Proceedings of the 6th International Conference on Information Systems Security and Privacy ICISSP, Valletta, Malta, 25–27 February 2020; pp. 317–324. [Google Scholar]
- Rameder, H. Systematic Review of Ethereum Smart Contract Security Vulnerabilities, Analysis Methods and Tools. Ph.D. Thesis, Manipal University, Wien, Austria, 2021. [Google Scholar]
- Kushwaha, S.S.; Joshi, S.; Singh, D.; Kaur, M.; Lee, H.N. Systematic Review of Security Vulnerabilities in Ethereum Blockchain Smart Contract. IEEE Access 2022, 10, 6605–6621. [Google Scholar] [CrossRef]
- Ghaleb, A.; Pattabiraman, K. How effective are smart contract analysis tools? Evaluating smart contract static analysis tools using bug injection. In Proceedings of the 29th ACM SIGSOFT International Symposium on Software Testing and Analysis, Online, 18–22 July 2020; pp. 415–427. [Google Scholar]
- Tsankov, P.; Dan, A.; Drachsler-Cohen, D.; Gervais, A.; Buenzli, F.; Vechev, M. Securify: Practical security analysis of smart contracts. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 67–82. [Google Scholar]
- ConsenSys. Mythril. 2021. Available online: https://github.com/ConsenSys/mythril (accessed on 19 January 2022).
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- Mossberg, M.; Manzano, F.; Hennenfent, E.; Groce, A.; Grieco, G.; Feist, J.; Brunson, T.; Dinaburg, A. Manticore: A user-friendly symbolic execution framework for binaries and smart contracts. In Proceedings of the 2019 34th IEEE/ACM International Conference on Automated Software Engineering (ASE), San Diego, CA, USA, 11–15 November 2019; pp. 1186–1189. [Google Scholar]
- Feist, J.; Grieco, G.; Groce, A. Slither: A static analysis framework for smart contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; pp. 8–15. [Google Scholar]
- Grech, N.; Kong, M.; Jurisevic, A.; Brent, L.; Scholz, B.; Smaragdakis, Y. Madmax: Surviving out-of-gas conditions in ethereum smart contracts. Proc. ACM Program. Lang. 2018, 2, 1–27. [Google Scholar] [CrossRef] [Green Version]
- Brent, L.; Jurisevic, A.; Kong, M.; Liu, E.; Gauthier, F.; Gramoli, V.; Holz, R.; Scholz, B. Vandal: A scalable security analysis framework for smart contracts. arXiv 2018, arXiv:1809.03981. [Google Scholar]
- Chen, J.; Xia, X.; Lo, D.; Grundy, J.; Luo, X.; Chen, T. DEFECTCHECKER: Automated Smart Contract Defect Detection by Analyzing EVM Bytecode. IEEE Trans. Softw. Eng. 2021, 1, 1. [Google Scholar] [CrossRef]
- Wang, W.; Song, J.; Xu, G.; Li, Y.; Wang, H.; Su, C. Contractward: Automated vulnerability detection models for ethereum smart contracts. IEEE Trans. Netw. Sci. Eng. 2020, 8, 1133–1144. [Google Scholar] [CrossRef] [Green Version]
- Torres, C.F.; Schütte, J.; State, R. Osiris: Hunting for integer bugs in ethereum smart contracts. In Proceedings of the 34th Annual Computer Security Applications Conference, San Juan, PR, USA, 3–7 December 2018; pp. 664–676. [Google Scholar]
- Wang, S.; Zhang, C.; Su, Z. Detecting nondeterministic payment bugs in Ethereum smart contracts. Proc. ACM Program. Lang. 2019, 3, 1–29. [Google Scholar] [CrossRef] [Green Version]
- Wang, A.; Wang, H.; Jiang, B.; Chan, W. Artemis: An improved smart contract verification tool for vulnerability detection. In Proceedings of the 2020 7th International Conference on Dependable Systems and Their Applications (DSA), Xi’an, China, 28–29 November 2020; pp. 173–181. [Google Scholar]
- Zhang, W.; Banescu, S.; Pasos, L.; Stewart, S.; Ganesh, V. MPro: Combining Static and Symbolic Analysis for Scalable Testing of Smart Contract. In Proceedings of the 2019 IEEE 30th International Symposium on Software Reliability Engineering (ISSRE), Berlin, Germany, 28–31 October 2019; pp. 456–462. [Google Scholar]
- Jiang, B.; Liu, Y.; Chan, W. Contractfuzzer: Fuzzing smart contracts for vulnerability detection. In Proceedings of the 2018 33rd IEEE/ACM International Conference on Automated Software Engineering (ASE), Montpellier, France, 3–7 September 2018; pp. 259–269. [Google Scholar]
- Ashraf, I.; Ma, X.; Jiang, B.; Chan, W. GasFuzzer: Fuzzing Ethereum Smart Contract Binaries to Expose Gas-Oriented Exception Security Vulnerabilities. IEEE Access 2020, 8, 99552–99564. [Google Scholar] [CrossRef]
- He, J.; Balunović, M.; Ambroladze, N.; Tsankov, P.; Vechev, M. Learning to fuzz from symbolic execution with application to smart contracts. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 531–548. [Google Scholar]
- Nguyen, T.D.; Pham, L.H.; Sun, J.; Lin, Y.; Minh, Q.T. sfuzz: An efficient adaptive fuzzer for solidity smart contracts. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Valencia, Spain, 29 June–2 July 2020; pp. 778–788. [Google Scholar]
- ethereum. ethereum/go-ethereum. 2021. Available online: https://github.com/ethereum/go-ethereum (accessed on 19 January 2022).
- Rodler, M.; Li, W.; Karame, G.O.; Davi, L. Sereum: Protecting existing smart contracts against re-entrancy attacks. arXiv 2018, arXiv:1812.05934. [Google Scholar]
- Fattahi, S.M.; Makanju, A.; Milani Fard, A. SIMBA: An efficient simulator for blockchain applications. In Proceedings of the 2020 50th IEEE-IFIP International Conference on Dependable Systems and Networks-Supplemental Volume (DSN-S), Valencia, Spain, 29 June–2 July 2020; pp. 51–52. [Google Scholar]
- Murray, Y.; Anisi, D.A. Survey of formal verification methods for smart contracts on blockchain. In Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–6. [Google Scholar]
- Garfatta, I.; Klai, K.; Gaaloul, W.; Graiet, M. A Survey on Formal Verification for Solidity Smart Contracts. In Proceedings of the 2021 Australasian Computer Science Week Multiconference, Dunedin, New Zealand, 1–5 February 2021; pp. 1–10. [Google Scholar]
- Mavridou, A.; Laszka, A. Designing secure ethereum smart contracts: A finite state machine based approach. In Proceedings of the International Conference on Financial Cryptography and Data Security, Nieuwpoort, Curaçao, 26 February–2 March 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 523–540. [Google Scholar]
- Mavridou, A.; Laszka, A.; Stachtiari, E.; Dubey, A. VeriSolid: Correct-by-design smart contracts for Ethereum. In Proceedings of the International Conference on Financial Cryptography and Data Security, Frigate Bay, St. Kitts and Nevis, 18–22 February 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 446–465. [Google Scholar]
- Kalra, S.; Goel, S.; Dhawan, M.; Sharma, S. ZEUS: Analyzing Safety of Smart Contracts. In Proceedings of the 25th Annual Network and Distributed System Security Symposium, NDSS 2018, San Diego, CA, USA, 18–21 February 2018; The Internet Society: Reston, VA, USA, 2018. [Google Scholar]
- Zhao, W. 30 Million Dollar: Ether Reported Stolen Due to Parity Wallet Breach. 2017. Available online: https://www.coindesk.com/30-million-ether-reported-stolen-parity-wallet-breach (accessed on 19 January 2022).
- Security, S.C. 2020. Available online: https://swcregistry.io/ (accessed on 19 January 2022).
- Corporation, M. 2021. Available online: https://cwe.mitre.org/index.html (accessed on 19 January 2022).
- Banisadr, E. How $800 k Evaporated from the PoWH Coin Ponzi Scheme Overnight. 2018. Available online: https://medium.com/@ebanisadr/how-800k-evaporated-from-the-powh-coin-ponzi-scheme-overnight-1b025c33b530 (accessed on 19 January 2022).
- Akentiev, A. Parity Multisig Hacked. Again—Chain. Cloud Company Blog—Medium; Cloud Company: Hong Kong, China, 2017. [Google Scholar]
- Technologies, P. A Postmortem on the Parity Multi-Sig Library Self-Destruct. 2017. Available online: https://www.parity.io/a-postmortem-on-the-parity-multi-sig-library-self-destruct/ (accessed on 19 January 2022).
- King of the Ether Throne. 2016. Available online: https://www.kingoftheether.com/postmortem.html (accessed on 19 January 2022).
- Qureshi, H. A hacker Stole $31 M of Ether-How It Happened, and What It Means for Ethereum. 2017. Available online: https://www.freecodecamp.org/news/a-hacker-stole-31m-of-ether-how-it-happened-and-what-it-means-for-ethereum-9e5dc29e33ce/ (accessed on 19 January 2022).
- CurrencyTycoon. Tricked by a Honeypot Contract or Beaten by Another Hacker. What Happened? 2018. Available online: https://www.reddit.com/r/ethdev/comments/7x5rwr/tricked_by_a_honeypot_contract_or_beaten_by/ (accessed on 19 January 2022).
- Bogatyy, I. Implementing Ethereum Trading Front-Runs on the Bancor Exchange in Python. 2017. Available online: https://hackernoon.com/front-running-bancor-in-150-lines-of-python-with-ethereum-api-d5e2bfd0d798 (accessed on 19 January 2022).
- Reutov, A. Predicting Random Numbers in Ethereum Smart Contracts. 2018. Available online: https://blog.positive.com/predicting-random-numbers-in-ethereum-smart-contracts-e5358c6b8620 (accessed on 19 January 2022).
- Bahrynovska, T. 2017. Available online: https://applicature.com/blog/blockchain-technology/history-of-ethereum-security-vulnerabilities-hacks-and-their-fixes (accessed on 19 January 2022).
- Academy, K. Re-Entrancy Example. 2021. Available online: https://solidity-by-example.org/hacks/re-entrancy/ (accessed on 19 January 2022).
- Antonopoulos, A.M.; Wood, G. Mastering Ethereum: Building Smart Contracts and Dapps; O’reilly Media: Sebastopol, CA, USA, 2018. [Google Scholar]
- OpenZeppelin. SafeMath Library. 2018. Available online: https://github.com/OpenZeppelin/openzeppelin-contracts/blob/v1.12.0/contracts/math/SafeMath.sol (accessed on 19 January 2022).
- OpenZeppelin. 2020. Available online: https://openzeppelin.com/ (accessed on 19 January 2022).
- Academy, K. Delegatedcall Example. 2021. Available online: https://solidity-by-example.org/hacks/delegatecall/ (accessed on 19 January 2022).
- Foundation, E. 2021. Available online: https://docs.soliditylang.org/en/latest/contracts.html?highlight=library#libraries (accessed on 19 January 2022).
- ConsenSys. Ethereum Smart Contract Best Practices. 2021. Available online: https://consensys.github.io/smart-contract-best-practices/ (accessed on 19 January 2022).
- Tjaden Hess, P.C. How Can I Securely Generate a Random Number in my Smart Contract? 2016. Available online: https://ethereum.stackexchange.com/questions/191/how-can-i-securely-generate-a-random-number-in-my-smart-contract (accessed on 19 January 2022).
- RANDAO. randao/randao. 2019. Available online: https://github.com/randao/randao (accessed on 19 January 2022).
- Security Considerations. 2021. Available online: https://docs.soliditylang.org/en/develop/security-considerations.html#tx-origin (accessed on 19 January 2022).
- Foundation, E. Introduction to Smart Contracts. Available online: https://docs.soliditylang.org/en/v0.8.2/introduction-to-smart-contracts.html?highlight=storage#storage-memory-and-the-stack (accessed on 19 January 2022).
- Wiki, E. Mining Process. 2021. Available online: https://eth.wiki/en/fundamentals/mining (accessed on 19 January 2022).
- He, D.; Deng, Z.; Zhang, Y.; Chan, S.; Cheng, Y.; Guizani, N. Smart Contract Vulnerability Analysis and Security Audit. IEEE Netw. 2020, 34, 276–282. [Google Scholar] [CrossRef]
- Meiklejohn, S.; Pomarole, M.; Jordan, G.; Levchenko, K.; McCoy, D.; Voelker, G.M.; Savage, S. A fistful of bitcoins: Characterizing payments among men with no names. In Proceedings of the 2013 Conference on Internet Measurement Conference, Barcelona, Spain, 23–25 October 2013; pp. 127–140. [Google Scholar]
- Ron, D.; Shamir, A. Quantitative analysis of the full bitcoin transaction graph. In Proceedings of the International Conference on Financial Cryptography and Data Security, Okinawa, Japan, 1–5 April 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 6–24. [Google Scholar]
- Zhou, Y.; Kumar, D.; Bakshi, S.; Mason, J.; Miller, A.; Bailey, M. Erays: Reverse Engineering Ethereum’s Opaque Smart Contracts. In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 1371–1385. [Google Scholar]
- Community, E. What Is Oracles? 2021. Available online: https://ethereum.org/en/developers/docs/oracles/#top (accessed on 19 January 2022).
- Community, E. Oracle Problems. 2021. Available online: https://docs.ethhub.io/built-on-ethereum/oracles/what-are-oracles/ (accessed on 19 January 2022).
- SmartContract Chainlink Ltd. 2021. Available online: https://chain.link/ (accessed on 19 January 2022).
- Parr, T. 2021. Available online: https://www.antlr.org/ (accessed on 19 January 2022).
- Aho, A.V.; Sethi, R.; Ullman, J.D. Compilers, principles, techniques. Addison Wesley 1986, 7, 9. [Google Scholar]
- W3C. 2011. Available online: https://www.w3.org/TR/xpath20/ (accessed on 19 January 2022).
- Cavnar, W.B.; Trenkle, J.M. N-gram-based text categorization. In Proceedings of the SDAIR-94, 3rd Annual Symposium on Document Analysis and Information Retrieval, Las Vegas, NV, USA, 11–13 April 1994. [Google Scholar]
- Foundation, L. The LLVM Compiler Infrastructure Project. 2021. Available online: https://llvm.org/ (accessed on 19 January 2022).
- Authors, G.E. Geth. 2013. Available online: https://geth.ethereum.org/ (accessed on 19 January 2022).
- Zalewski, M. Technical “whitepaper” for afl-fuzz. 2017. Available online: https://vyagers.com/2018/12/15/technical-whitepaper-for-afl-fuzz/ (accessed on 19 January 2022).
- Authors, A. Aleth. 2021. Available online: https://github.com/ethereum/aleth/ (accessed on 19 January 2022).
- Remix: An Online Smart Contract Development IDE; Remix Inc.: Osaka, Japan, 2021.
- Perez, D.; Livshits, B. Smart contract vulnerabilities: Does anyone care? arXiv 2019, arXiv:1902.06710. [Google Scholar]
- Chen, J.; Xia, X.; Lo, D.; Grundy, J.; Luo, X.; Chen, T. Defining smart contract defects on ethereum. IEEE Trans. Softw. Eng. 2020, 48, 327–345. [Google Scholar] [CrossRef] [Green Version]
- Proposals, E.I. Ethereum Improvement Proposals. 2021. Available online: https://eips.ethereum.org/ (accessed on 19 January 2022).
| Survey | Year | Vulnerabilities | Tools | Attacks | Countermeasures | Ethereum Specific |
|---|---|---|---|---|---|---|
| Our Work | 2022 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Luu et al. [13] | 2016 | ✓ | ✓ | ✓ | ||
| Atzei et al. [25] | 2017 | ✓ | ✓ | |||
| Dika [11] | 2017 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Alharby and Moorsel [12] | 2017 | ✓ | ✓ | |||
| Grishchenko et al. [27] | 2018 | ✓ | ✓ | |||
| Di Angelo and Salzer [19] | 2019 | ✓ | ✓ | |||
| Saad et al. [18] | 2019 | ✓ | ✓ | ✓ | ||
| Dingman [26] | 2019 | ✓ | ✓ | |||
| Praitheeshan et al. [28] | 2019 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Huang et al. [29] | 2019 | ✓ | ✓ | ✓ | ✓ | |
| Li et al. [16] | 2020 | ✓ | ✓ | ✓ | ||
| Zhu et al. [17] | 2020 | ✓ | ✓ | ✓ | ||
| Sayeed et al. [30] | 2020 | ✓ | ✓ | ✓ | ||
| Durieux et al. [31] | 2020 | ✓ | ||||
| Tantikul and Ngamsuriyaroj [32] | 2020 | ✓ | ✓ | ✓ | ✓ | |
| Chen et al. [14] | 2020 | ✓ | ✓ | ✓ | ✓ | |
| Tang et al. [15] | 2021 | ✓ | ✓ | |||
| Rameder [33] | 2021 | ✓ | ✓ | ✓ | ||
| Kushwaha et al. [34] | 2022 | ✓ | ✓ | ✓ | ✓ | ✓ |
| Level | Vulnerability | CWE Index | Real-World Attack |
|---|---|---|---|
| Solidity | Re-entrancy | CWE-841: Improper Enforcement of Behavioral Workflow | The DAO Attack [10] |
| Arithmetic issues | CWE-682: Incorrect Calculation | PoWHcoin attack [64] | |
| Delegatecall to insecure contracts | CWE-829: Inclusion of Functionality from Untrusted Control Sphere | Parity Wallet(Second Hack) [65] | |
| Selfdestruct | CWE-284: Improper Access Control | Parity Library bug [66] | |
| Tx.origin | CWE-477: Use of Obsolete Function | - | |
| Mishandled exceptions | CWE-252: Unchecked Return Value | KingofTheEther attack [67] | |
| Default visibility | CWE-710: Improper Adherence to Coding Standards | Parity Wallet(First Hack) [68] | |
| External contract referencing | CWE-829: Inclusion of Functionality from Untrusted Control Sphere | Honey Pot [69] | |
| EVM | Short address/parameter issues | CWE-88: Improper Neutralization of Argument Delimiters in a Command (`Argument Injection’) | - |
| Freezing Ether | CWE-17: Code Development (Specification, Design, and Implementation) | - | |
| Blockchain | Transaction order dependence | CWE-362: Concurrent Execution using Shared Resource with Improper Synchronization (`Race Condition’) | Attack on Bancor [70] |
| Generating randomness | CWE-330: Use of Insufficiently Random Values | PRNG contract [71] | |
| Timestamp dependence | CWE-829: Inclusion of Functionality from Untrusted Control Sphere | GovernMental attack [72] |
| Security Tool | Re-Entrancy | Arithmetic Issues | Delegatecall to Insecure Contracts | Selfdestruct | Tx.origin | Mishandled Exceptions | External Contract Referencing | Short Address | Freezing Ether | Transaction Order Dependence | Generating Randomness | Timestamp Dependence |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Oyente | ✓ | ✓ | ✓ | ✓ | ||||||||
| Securify | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| SmartCheck | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||
| DefectChecker | ✓ | ✓ | ✓ | ✓ | ✓ | |||||||
| ContractWard | ✓ | ✓ | ✓ | ✓ | ||||||||
| NPChecker | ✓ | ✓ | ✓ | |||||||||
| MadMax | ✓ | |||||||||||
| Osiris | ✓ | |||||||||||
| ContractFuzzer | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ||||||
| Sereum | ✓ | |||||||||||
| sFuzz | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Tools Name | Methods | Vulnerabilities Covered | Accuracy | Efficiency |
|---|---|---|---|---|
| Oyente [13] | Static | Vulnerabilities in the taxonomy: Transaction order dependence, Timestamp dependence, Mishandled exceptions, Re-entrancy. | High (94.3%) | 29.5 s per execution path |
| Securify [36] | Static | Vulnerabilities in the taxonomy: Freezing Ether, Re-entrancy, Delegatedcall to insecure contracts, Mishandled exceptions, Transaction order dependency, Short address/parameter issues | Not reported | 30 s per contract |
| SmartCheck [38] | Static | Vulnerabilities in the taxonomy: Re-entrancy, Tx.origin, Freezing Ether, Arithmetic Issues, Timestamp dependence; Self-defined vulnerabilities: Unchecked external calls, DoS by external contract | Low (31.11%) | 1.67 per contract |
| DefectChecker [43] | Static | Vulnerabilities in the taxonomy: Transaction order dependence, Re-entrancy, Freezing Ether, Mishandled exceptions, Timestamp dependence; Self-defined vulnerabilities: DoS, Strict balance equality, Nested call, Unchecked external calls. | Medium (84.16%) | 2.42 s per contract |
| ContractWard [44] | Static | Vulnerabilities in the taxonomy: Arithmetic issues, Transaction order dependency, timestamp dependency, Re-entrancy; Self-defined vulnerabilities: stack size limit (deprecated) | High (96%) | 4 s per contract |
| NPChecker [46] | Static | Vulnerabilities in the taxonomy: Timestamp dependence, Re-entrancy, Transaction order dependence; Self-defined vulnerabilities: external calls and other non-determinism-related smart-contract payment bugs. | High (94%) | 351 s per contract |
| MadMax [41] | Static | Vulnerabilities in the taxonomy: Arithmetic issues; Self-defined vulnerabilities: Unbounded mass operations, Non-isolated external calls. | Medium (81%) | 5.9 s per contract |
| Osiris [45] | Static | Vulnerabilities in the taxonomy: Arithmetic issues; Self-defined vulnerabilities: Division by zero, Modulo zero, Type cast, Signedness. | Not reported | 75 s per contract |
| ContractFuzzer [49] | Dynamic | Vulnerabilities in the taxonomy: Selfdestruct, Mishandled exception, Re-entrancy, Timestamp dependency, Delegatedcall to insecure contracts, Freezing ether. | High (98.91%) | Not reported |
| Sereum [54] | Dynamic | Self-defined Re-entrancy vulnerabilities: Cross-function reentrancy, Delegated renentrancy and Create-based reentrancy | High (99.4%) | 2494.5 ms per block runtime (2277.0ms on Geth) |
| sFuzz [52] | Dynamic | Vulnerabilities in the taxonomy: Selfdestruct, Mishandled exceptions, Re-entrancy, Timestamp dependency, Delegatecall to insecure contracts, Arithmetic Issues, freezing ether | High (90.56%) | Generates 208 test cases per second on average. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, H.; Milani Fard, A.; Makanju, A. The State of Ethereum Smart Contracts Security: Vulnerabilities, Countermeasures, and Tool Support. J. Cybersecur. Priv. 2022, 2, 358-378. https://doi.org/10.3390/jcp2020019
Zhou H, Milani Fard A, Makanju A. The State of Ethereum Smart Contracts Security: Vulnerabilities, Countermeasures, and Tool Support. Journal of Cybersecurity and Privacy. 2022; 2(2):358-378. https://doi.org/10.3390/jcp2020019
Chicago/Turabian StyleZhou, Haozhe, Amin Milani Fard, and Adetokunbo Makanju. 2022. "The State of Ethereum Smart Contracts Security: Vulnerabilities, Countermeasures, and Tool Support" Journal of Cybersecurity and Privacy 2, no. 2: 358-378. https://doi.org/10.3390/jcp2020019
APA StyleZhou, H., Milani Fard, A., & Makanju, A. (2022). The State of Ethereum Smart Contracts Security: Vulnerabilities, Countermeasures, and Tool Support. Journal of Cybersecurity and Privacy, 2(2), 358-378. https://doi.org/10.3390/jcp2020019






