Group Key Management Scheme for Multicast Communication Fog Computing Networks
Abstract
1. Introduction
- Any legal fog user who belongs to a fog node will be able to decrypt a ciphertext encrypted by a secret shared key.
- The shared secret key is divided into key segments, In the rekeying operation process, each key segment is split into two factors with his shared production mechanism, key updates are required to belong to the fog provider or the group management device.
- For the security aspect, because a different random value is chosen by the source in every process of decrypting, it is not possible to damage the decryption key, and the proposed scheme can ensure the backward and forward security and can against the collusion attacks.
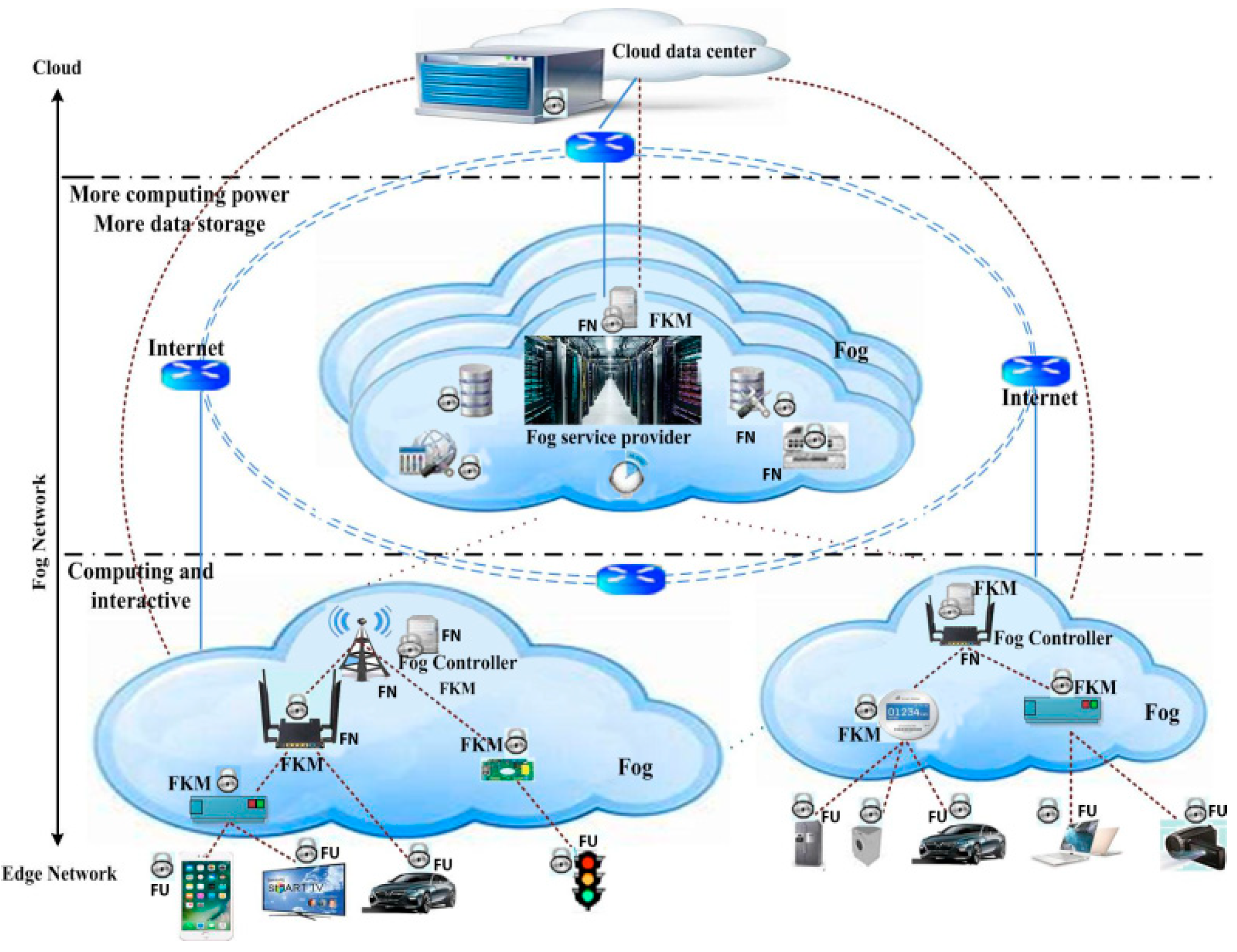
2. Fog Computing Environment
2.1. Fog Network
- Cloud: Store, control, handle all data centers, and online services. It receives all data from Fog nodes, analyzes, and processes data according to the requirements of some applications.
- Fog Node (FN): Is an important active component for processing, calculating, and storing secret keys. It includes devices between the cloud and end-users, such as the base stations, servers, gateways, routers, switches, and access points. Each fog node serves the end-users in its communication range. We assume that the entities are reliable and well protected.
- Fog User (FU): Are the types of terminals that use services provided by the cloud or the providers of fog services. These types of devices are structured as heterogeneous (such as vehicle networks, smartphones, IoT devices, etc.). They connect short communication with the Fog node, in which the devices can be equipped with sensors and the ability to communicate to perceive environmental phenomena and send data through channels of communication to the fog node.
- Fog Key Management Center (FKM): Computes and creates secret keys, session keys, and private keys for users. In the fog network system, it is completely trusted by all members. The results and discussions may be presented separately, or in one combined section, and may optionally be divided into headed subsections.
2.2. Security Requirements
- Backward security: When a new member joins the fog node to use the services, the GKM must ensure that a new member cannot decrypt the data before it joins the fog node. Then the GKM system is secure.
- Forward security: When a member loses the privilege of accessing the fog to use the service, it will not decrypt any group keys and any future group messages. Then the GKM system is secure.
- Collusion attacks: A secure GKM system will not be compromised, when some members cooperate to use the old keying documents to regain the group key.
2.3. Fog Security Devices Role
3. Key Establishment
3.1. Bilinear Pairings
- Bilinearity. For , we have and , where ;
- Computability. For , there continually exists an efficient algorithm to calculate the value of ;
- Nondegeneracy. If , then we have .
3.2. Threshold Cryptography
3.3. Shared Secret Product
4. Group Key Management Scheme in Fog Computing Network
4.1. Initialization Stage
4.2. Encryption Stage
- A random number q is selected by the source to calculates ;
- Session key with and handles encryption are calculated by the source;
- The source calculatesand ;
- Finally, the ciphertext is sent to the destinations by the source.
4.3. Decryption Stage
- An end-user calculates with and , where
- decrypts the ciphertext with ;
- The will accept a valid plaintext (Mas’) in case I’= I, else it will be rejected.
4.4. Rekeying Stage
- JoinWe assume a new user joins as , this activity will take place as follows:
- (1)
- FKM selects id random numbers for , having a new set ;
- (2)
- FKM selects , replaces with , so with degree polynomial
FKM calculates with
- LeaveWe assume a new user leaves as , this activity will take place as follows:
- (1)
- The FKM deletes from ;
- (2)
- FKM selects , replaces with , so with degree polynomial
FKM calculates with
5. Security Analysis
5.1. Adjusting
5.2. Security
| Algorithm 1 Steps for Building the Emulator |
Input: set , and is a random number
polynomial with degree, polynomial with degree, with degrees, then send to the attacker a set ; 5.2. The attacker selects and sends two same size keys to emulator; 5.3. The emulator chooses randomly, and sends that is ciphertext; 5.4. The attacker analyzes to receive and sends it to the emulator. If y′ = y, Then output . Else, output . If , Then is an valid ciphertext with . If Then is an invalid ciphertext with |
5.3. Collusion Attack
5.4. Forward/Backward Security
6. Analysis Performance of KMGSFC
6.1. Computation Overhead
- id for scalar multiplication , nKD scalar multiplication for in , scalar multiplication for are all done by FKM. Then we can calculate the total cost of computation, id + 2nKD + 2, for scalar multiplication in .
- For the encrypting phase, we can calculate the total cost of computation as id + nKD + 1, for scalar multiplication in and exponential modules. The source performs scalar multiplication for , id scalar multiplication for , nKD scalar multiplication for , and exponential module for .
- For the decoding phase, we can calculate the total cost of calculation as the scalar multiplication id + KD in G, KD + 1 in (Equation (25)), because id scalar multiplication is deployed for KD with scalar multiplication in with KD in , and multiplication in is done in the numerator of Formula (25).
6.2. Message Overhead
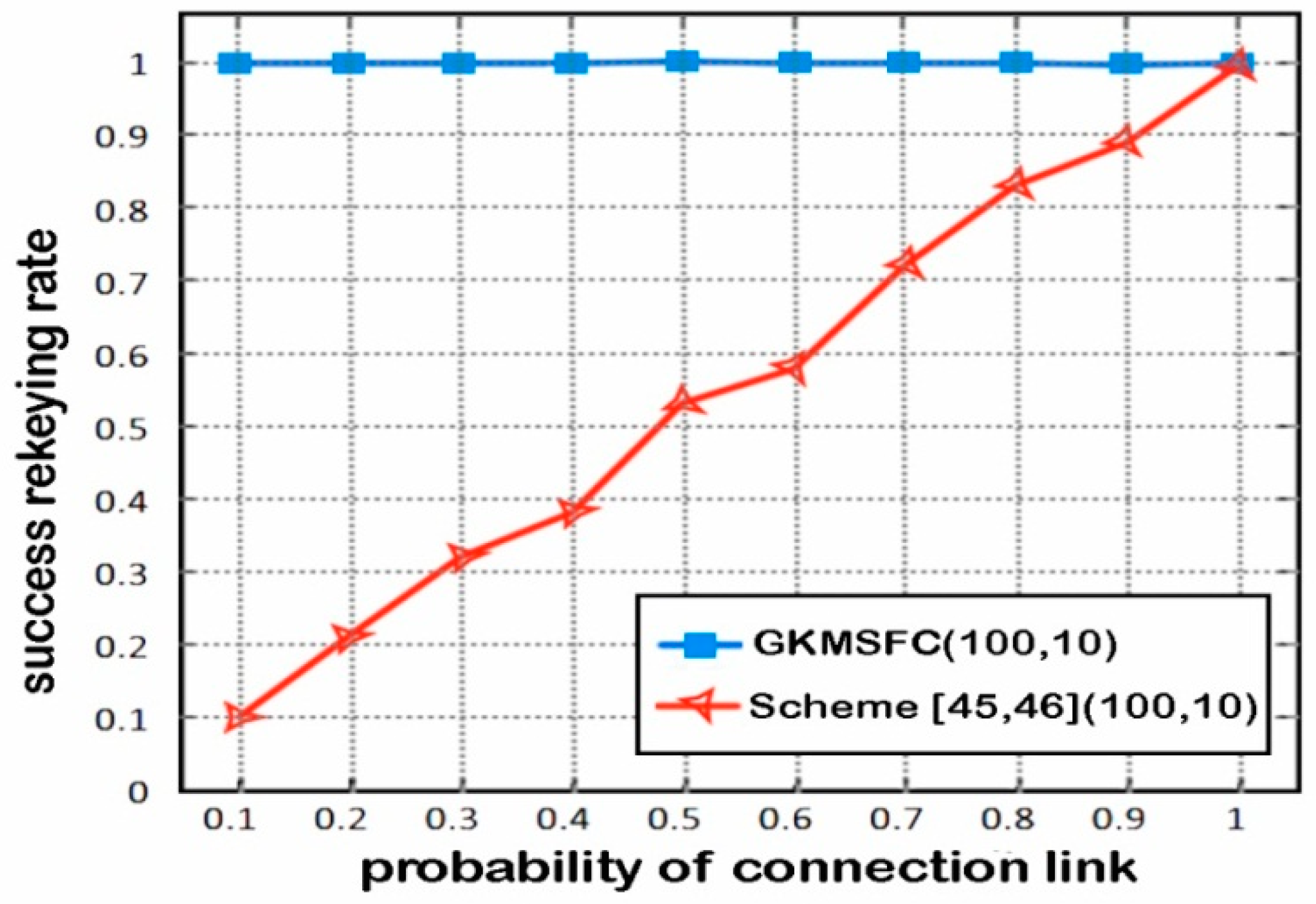
6.3. Rekeying Efficiency
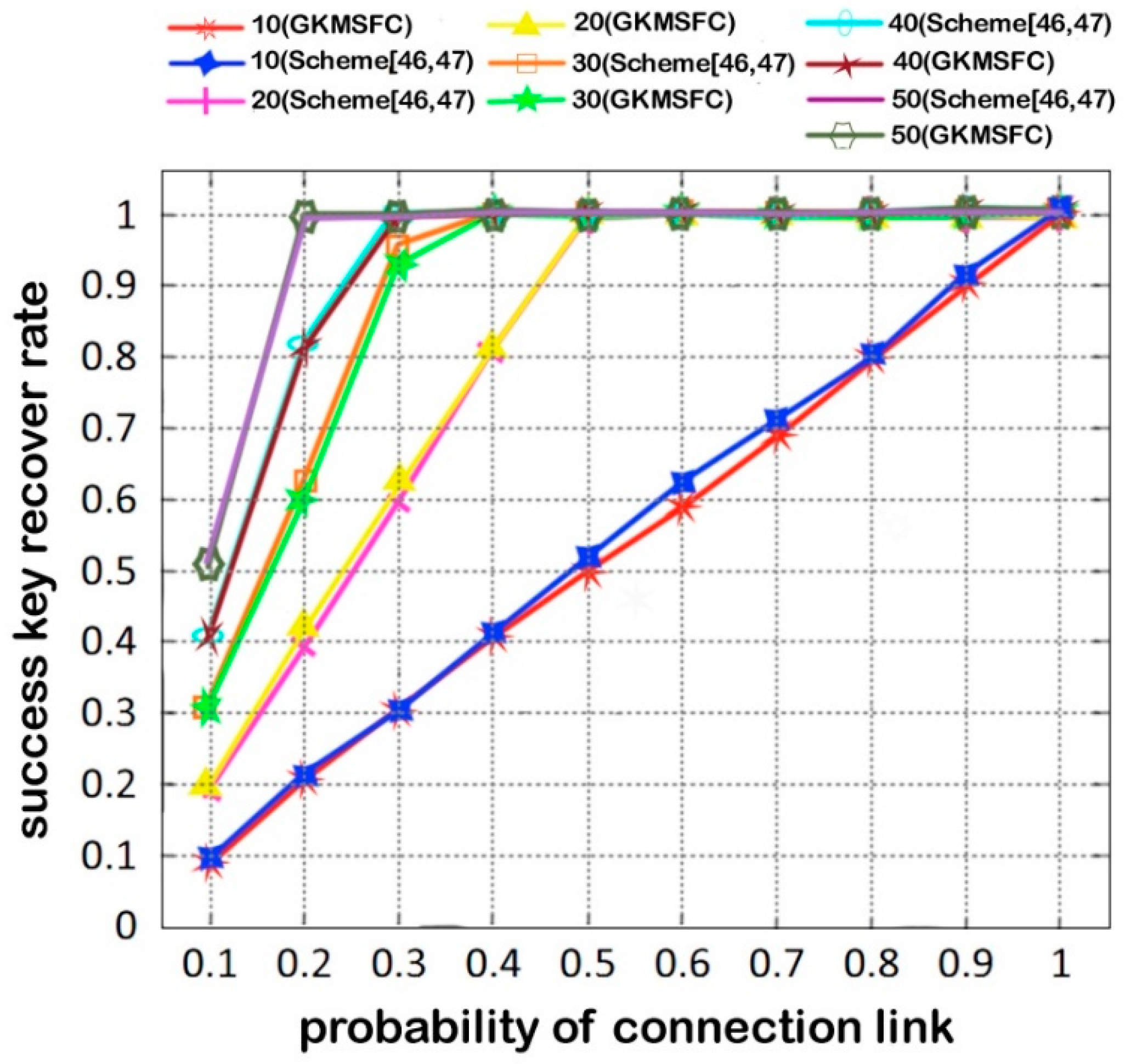
6.4. Scalability
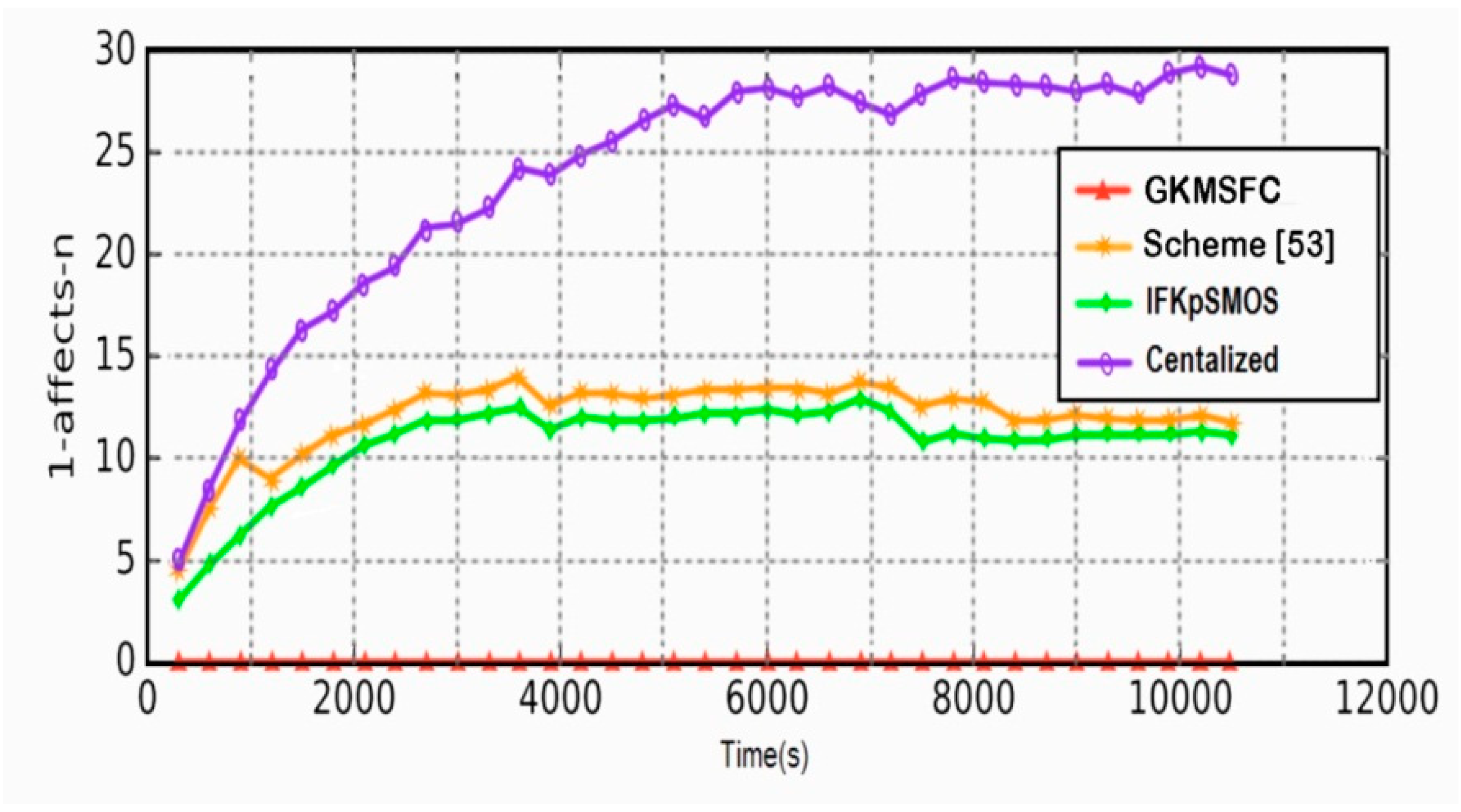
6.5. 1-affect-n Problem
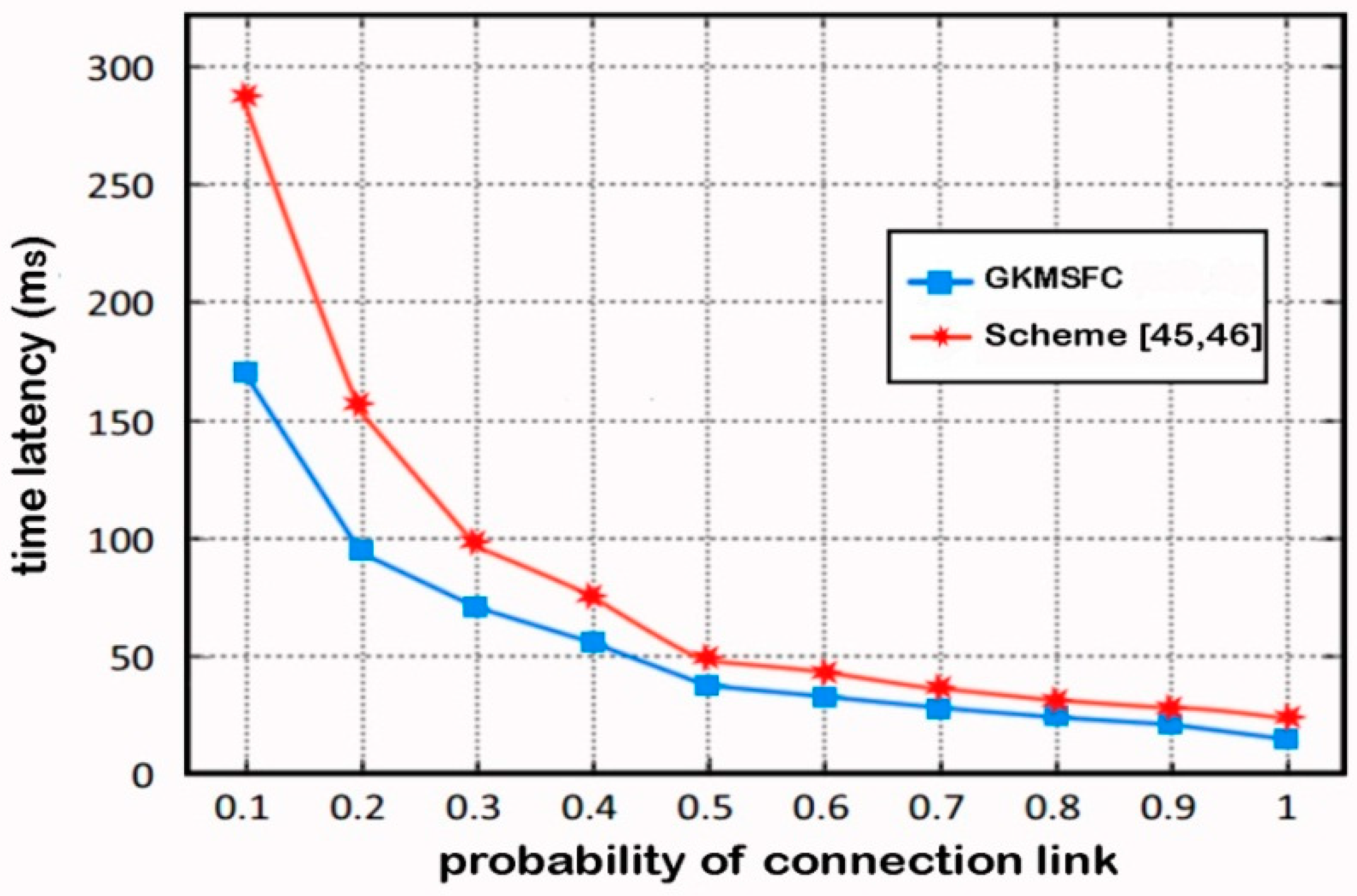
6.6. Time Latency
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Biradar, R.C.; Manvi, S.S. Review of multicast routing mechanisms in mobile ad hoc networks. J. Netw. Comput. Appl. 2012, 35, 221–239. [Google Scholar] [CrossRef]
- Dinesh, C.; Rajneesh, K. QoS Enabled Cross-Layer Multicast Routing over Mobile Ad Hoc Networks. Procedia Comput. Sci. 2018, 125, 215–227. [Google Scholar]
- Park, M.H.; Park, Y.H.; Jeong, H.Y.; Seo, S.W. Key Management for Multiple Multicast Groups in Wireless Networks. IEEE Trans. Mob. Comput. 2012, 12, 1712–1723. [Google Scholar] [CrossRef]
- Omar, C. Secure Group Communication in Wireless Sensor Networks: A Survey. J. Netw. Comput. Appl. 2013, 61, 115–132. [Google Scholar]
- Hui, H.; Zhou, C.; Xu, S.; Lin, F. A Novel Secure Data Transmission Scheme in Industrial Internet of Things. China Commun. 2020, 17, 73–88. [Google Scholar] [CrossRef]
- Gong, C.; Lin, F.; Gong, X.; Lu, Y. Intelligent Cooperative Edge Computing in the Internet of Things. IEEE Internet Things J. 2020, 7, 9372–9382. [Google Scholar] [CrossRef]
- Judge, P.; Ammar, M. Security issues and solutions in multicast content distribution: A survey. IEEE Netw. Mag. Glob. Internetworking 2003, 17, 30–36. [Google Scholar] [CrossRef]
- Saadawi, T. A delay-tolerant networking architecture for airborne networking. Def. Tech. Inf. Cent. 2010, 1–31. [Google Scholar]
- Mukherjee, J.; Ramamurthy, B. Communication technologies and architectures for space network and interplanetary Internet. IEEE Commun. Surv. Tutor. 2013, 15, 881–897. [Google Scholar] [CrossRef]
- Jiang, C.; Wang, X.; Wang, J.; Chen, H.H. Security in space networks. IEEE Commun. Mag. 2015, 53, 82–88. [Google Scholar] [CrossRef]
- Kadhim, A.J.; Seno, S.A.H. Energy-efficient multicast routing protocol based on SDN and fog computing for vehicular networks. Ad Hoc Netw. 2019, 84, 68–81. [Google Scholar] [CrossRef]
- Yi, S.; Qin, Z.; Li, Q. Security and Privacy Issues of Fog Computing: A Survey. In International Conference on Wireless Algorithms, Systems, and Applications; Springer: Cham, Switzerland, 2015; pp. 685–695. [Google Scholar]
- Stojmenovic, I.; Wen, S. The Fog Computing Paradigm: Scenarios and Security Issues. In Proceedings of the Federated Conference on Computer Science and Information Systems, Warsaw, Poland, 7–10 September 2014; pp. 1–8. [Google Scholar]
- Zhang, P.Y.; Zhou, M.C.; Fortino, G. Security and trust issues in Fog computing: A survey. Future Gener. Comput. Syst. 2018, 88, 16–27. [Google Scholar] [CrossRef]
- Wadood, A.; Ali, Z.A.; Ghouzali, S.; Alfawaz, B.; Muhammad, G.; Hossain, M.S. Biometric security through visual encryption for fog edge computing. IEEE Access 2017, 5, 5531–5538. [Google Scholar]
- Hu, P.; Ning, H.; Qiu, T.; Song, H.; Wang, Y.; Yao, X. Security and privacy preservation scheme of face identification and resolution framework using fog computing in the internet of things. IEEE Internet Things J. 2017, 4, 1143–1155. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on fog computing: Architecture, key technologies, applications and open issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Kooa, D.; Hura, J. Privacy-preserving deduplication of encrypted data with dynamic ownership management in fog computing. Future Gener. Comput. Syst. 2018, 78, 739–752. [Google Scholar] [CrossRef]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Xing, X.; Cheng, X. An attribute-based encryption scheme to secure fog communications. IEEE Access 2017, 5, 9131–9138. [Google Scholar] [CrossRef]
- Wang, H.; Wang, Z.; Domingo-Ferrer, J. Anonymous and secure aggregation scheme in fog-based public cloud computing. Future Gener. Comput. Syst. 2018, 78, 712–719. [Google Scholar] [CrossRef]
- Mukherjee, M.; Matam, R.; Shu, L.; Maglaras, L.; Ferrag, M.A.; Choudhury, N. Security and privacy in fog computing: Challenges. IEEE Access 2017, 5, 19293–19304. [Google Scholar] [CrossRef]
- Yacine, C.; Hamida, S. Group key management protocols: A novel taxonomy. Int. J. Inf. Technol. 2005, 2, 105–118. [Google Scholar]
- Sandro, R.; David, H. A survey of key management for secure group communication. ACM Comput. Surv. 2003, 35, 309–329. [Google Scholar]
- Manivannan, D.; Neelamegam, P. WSN: Key issues in key management schemes—A review. Res. J. Appl. Sci. Eng. Technol. 2012, 4, 3188–3200. [Google Scholar]
- Xu, Q.; Tan, C.; Fan, Z.; Zhu, W.; Xiao, Y.; Cheng, F. Open AccessArticle Secure Data Access Control for Fog Computing Based on Multi-Authority Attribute-Based Signcryption with Computation Outsourcing and Attribute Revocation. Sensors 2018, 18, 1609. [Google Scholar] [CrossRef]
- Chen, C.W.; Wang, S.J.; Tsai, Y.R. Fast-Refreshing Tree-Based Group Key Agreement for Mobile Ad Hoc Networks. In Proceedings of the Seventh Asia Joint Conference on Information Security, Tokyo, Japan, 9–10 August 2012. [Google Scholar]
- Kim, Y.; Perrig, A.; Tsudik, G. Tree-based group key agreement. ACM Trans. Inf. Syst. Secur. 2004, 7, 60–96. [Google Scholar] [CrossRef]
- Ermiş, O.; Bahtiyar, Ş.; Anarım, E.; Çağlayan, M.U. A secure and efficient group key agreement approach for mobile ad hoc networks. Ad Hoc Netw. 2017, 67, 24–39. [Google Scholar] [CrossRef]
- Steer, D.; Strawczynski, L.L.; Diffie, W.; Weiner, M.A. Secure Audio Teleconference System. In CRYPTO’88; Springer: Berlin/Heidelberg, Germany, 1988. [Google Scholar]
- Burmester, M.; Desmedt, Y. A Secure and Efficient Conference Key Distribution System. In EUROCRYPT’94; Springer: Berlin/Heidelberg, Germany, 1994; Volume 950, pp. 275–286. [Google Scholar]
- Steiner, M.; Tsudik, G.; Waidner, M. Diffle–Hellman Key Distribution Extended to Group Communication. In Proceedings of the 3rd ACM Conference on Computer and Communication Security, New Delhi, India, 14–16 March 1996; pp. 31–37. [Google Scholar]
- Zhou, J.; Song, M.; Song, J.; Zhou, X.W.; Sun, L. Autonomic group key management in deep space DTN. Wirel. Pers. Commun. 2014, 77, 269–287. [Google Scholar] [CrossRef]
- Zhou, J.; Zhou, X.W. Autonomous shared key management scheme for space networks. Wirel. Pers. Commun. 2013, 72, 2425–2443. [Google Scholar] [CrossRef]
- Haohua, C.; Lintian, Q.; Klara, N.; Hua, W.; Ritesh, J. A secure multicast protocol with copyright protection. ACM SIGCOMM Comput. Commun. Rev. 2002, 32, 42–60. [Google Scholar]
- Kishore, R.; Radha, S.; Ramasamy, P. A secure key predistribution scheme for WSN using elliptic curve cryptography. ETRI J. 2011, 33, 791–801. [Google Scholar]
- Haowen, C.; Perrig, A.; Song, D. Random key predistribution schemes for sensor networks. In Proceedings of the 2003 Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003; pp. 197–213. [Google Scholar]
- Chung, K.W.; Mohamed, G.; Simon, S.; Fellow, L. Secure group communications using key graphs. IEEE ACM Trans. Netw. 2000, 8, 16–29. [Google Scholar] [CrossRef]
- Yao, W.; Han, S.; Li, X. LKH++ based group key management scheme for wireless sensor network. Wirel. Pers. Commun. 2015, 83, 3057–3073. [Google Scholar] [CrossRef]
- Klaoudatou, E.; Konstantinou, E.; Kambourakis, G.; Gritzalis, S. A survey on cluster-based group key agreement protocols for WSNs. IEEE Commun. Surv. Tutor. 2011, 13, 429–442. [Google Scholar] [CrossRef]
- Li, H.; Zhou, C.; Xu, H.; Lv, X.; Han, Z. Joint Optimization Strategy of Computation Offloading and Resource Allocation in Multi-access Edge Computing Environment. IEEE Trans. Veh. Technol. 2020. [Google Scholar] [CrossRef]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. SIAM J. Comput. 2003, 32, 586–615. [Google Scholar] [CrossRef]
- Desmedt, Y.; Frankel, Y. Threshold cryptosystems, advances in cryptology. In CRYPTO’89 Proceedings; Springer: Berlin/Heidelberg, Germany, 1990; Volume 435, pp. 101–109, 307–315. [Google Scholar]
- Chiou, G.H.; Chen, W.T. Secure broadcast using secure lock. IEEE Trans. Softw. Eng. 1989, 15, 929–934. [Google Scholar] [CrossRef]
- Liao, J.P.; Hui, X.L.; Qing, Q.P.; Yi, L.; Yu, M.W. A public-key encryption scheme with one-encryption and multi-decryption. Chin. J. Comput. 2012, 35, 1059–1067. [Google Scholar]
- Kurosawa, K. Multi-Recipient Public-Key Encryption with Shortened Ciphertext. In Proceedings of the 5th International Workshop on Practice and Theory in Public-Key Cryptosystem, Paris, France, 12–14 February 2002; pp. 48–63. [Google Scholar]
- Wu, L.; Wang, J.; Choo, K.K.; Li, Y.; He, D. An efficient provably-secure identity-based authentication scheme using bilinear pairings for Ad hoc network. J. Inf. Secur. Appl. 2017, 37, 112–121. [Google Scholar] [CrossRef]
- Marín-Tordera, E.; Masip-Bruin, X.; García-Almiñana, J.; Jukan, A.; Ren, G.J.; Zhu, J. Do we all really know what a fog node is? Current trends towards an open definition. Comput. Commun. 2017, 109, 117–130. [Google Scholar] [CrossRef]
- Tordera, E.M.; Masip-Bruin, X.; Garcia-Alminana, J.; Jukan, A.; Ren, G.J.; Zhu, J.; Farré, J. What Is a Fog Node? A Tutorial on Current Concepts towards a Common Definition. Available online: https://arxiv.org/abs/1611.09193 (accessed on 28 November 2016).
- Teven, D.G.; Kenneth, G.P.; Nigel, P.S. Pairings for cryptographers. Discret. Appl. Math. 2008, 156, 3113–3121. [Google Scholar]
- Joux, A. A one round protocol for tripartite Diffie-Hellman. Lect. Notes Comput. Sci. 2000, 1838, 385–393. [Google Scholar]
- Desmedt, Y. Threshold cryptography. Eur. Trans. Telecommun. 1994, 5, 449–458. [Google Scholar] [CrossRef]
- Desmedt, Y. Some recent research aspects of threshold cryptography. Lect. Notes Comput. Sci. 1998, 1396, 158–173. [Google Scholar]
- Li, Z.; Liu, Y.; Liu, D.; Li, C.; Cui, W.; Hu, G. A Key Management Scheme Based on Hypergraph for Fog Computing. China Commun. 2018, 15, 158–170. [Google Scholar] [CrossRef]
- Challal, Y.; Fatima, Z.B.; Omar, N. Scalable Key Management for Elastic Security Domains in Fog Networks. In Proceedings of the IEEE 27th International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises, Paris, France, 27–29 June 2018; pp. 187–192. [Google Scholar]
- Han, S.; Tian, B.; Zhang, Y.; Hu, J. An Efficient Self-Healing Key Distribution Scheme with Constant-Size Personal Keys for Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010; pp. 1–5. [Google Scholar]
- Lin, J.C.; Huang, K.H.; Lai, F.; Lee, H.C. Secure and efficient group key management with shared key derivation. Comput. Stand. Interfaces 2009, 31, 192–208. [Google Scholar] [CrossRef]
- Sun, Y.; Chen, M.; Bacchus, A.; Lin, X. Towards collusion-attack-resilient group key management using one-way function tree. Comput. Netw. 2016, 104, 16–26. [Google Scholar] [CrossRef]
- Kim, J.; Susilo, W.; Au, M.H.; Seberry, J. Adaptively secure identity-based broadcast encryption with a constant-sized ciphertext. IEEE Trans. Inf. Forensics Secur. 2015, 10, 679–693. [Google Scholar]
- Harn, L.; Lin, C. Authenticated group key transfer protocol based on secret sharing. IEEE Trans. Comput. 2010, 59, 842–846. [Google Scholar] [CrossRef]
- Tang, S.; Xu, L.; Liu, N.; Huang, X.; Ding, J.; Yang, Z. Provably secure group key management approach based upon hyper-sphere. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 3253–3263. [Google Scholar] [CrossRef]
| Scheme | Communication | Computation | Storage | Security | Scale | ||||
|---|---|---|---|---|---|---|---|---|---|
| Joining | Leaving | Member (Operation) | Member | Bulletin | Collusion | Forward and Backward | |||
| Joining | Leaving | ||||||||
| Key Management for Fog Computing | |||||||||
| GKMSFC | 0 | 0 | id+(n + 1)KD | id+(n − 1)KD | n | 0 | Yes | Yes | Yes |
| Scheme [54] | 3 | No | Yes | Yes | |||||
| Scheme [55] | n + 1 | n − 1 | n + k + 1 | n + k + 1 | n | 1 | No | Yes | Yes |
| Key Management Center | |||||||||
| Scheme [45,46] | (n + 1)KD | (n + 1)KD | id+(n + 1)KD | id+(n − 1)KD | n | n | Yes | Yes | |
| AKMSN [56] | 4n + 7 | 4n − 1 | N + 2 | 1 | Yes | Yes | |||
| KeyDer-GKM+ [57] | 1 | 1 | 1 | 1 | N | Yes | |||
| Key Distribute Protocol (at Session j, 1 ≤ j ≤ m) | |||||||||
| LKH [58] | Yes | Yes | Yes | ||||||
| HK [59] | j(t + r) | t | m | m | mt | t-revoke | |||
| DCM [60] | t + r | t | m − j | m − j | t + r | No | |||
| NOFT &ROFT [61] | Yes | Yes | |||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dong, M.T.; Xu, H. Group Key Management Scheme for Multicast Communication Fog Computing Networks. Processes 2020, 8, 1300. https://doi.org/10.3390/pr8101300
Dong MT, Xu H. Group Key Management Scheme for Multicast Communication Fog Computing Networks. Processes. 2020; 8(10):1300. https://doi.org/10.3390/pr8101300
Chicago/Turabian StyleDong, Mai Trung, and Haitao Xu. 2020. "Group Key Management Scheme for Multicast Communication Fog Computing Networks" Processes 8, no. 10: 1300. https://doi.org/10.3390/pr8101300
APA StyleDong, M. T., & Xu, H. (2020). Group Key Management Scheme for Multicast Communication Fog Computing Networks. Processes, 8(10), 1300. https://doi.org/10.3390/pr8101300