3.1. Yang et al.’s Scheme Description
Yang et al. recently proposed a blockchain-based authentication protocol that uses a public blockchain as the source of the public trust and also employs modular square roots as the main source of security in the primitive level [
19]. The proposed protocol includes four phases: initialization, registration, authentication, and update and revocation phases.
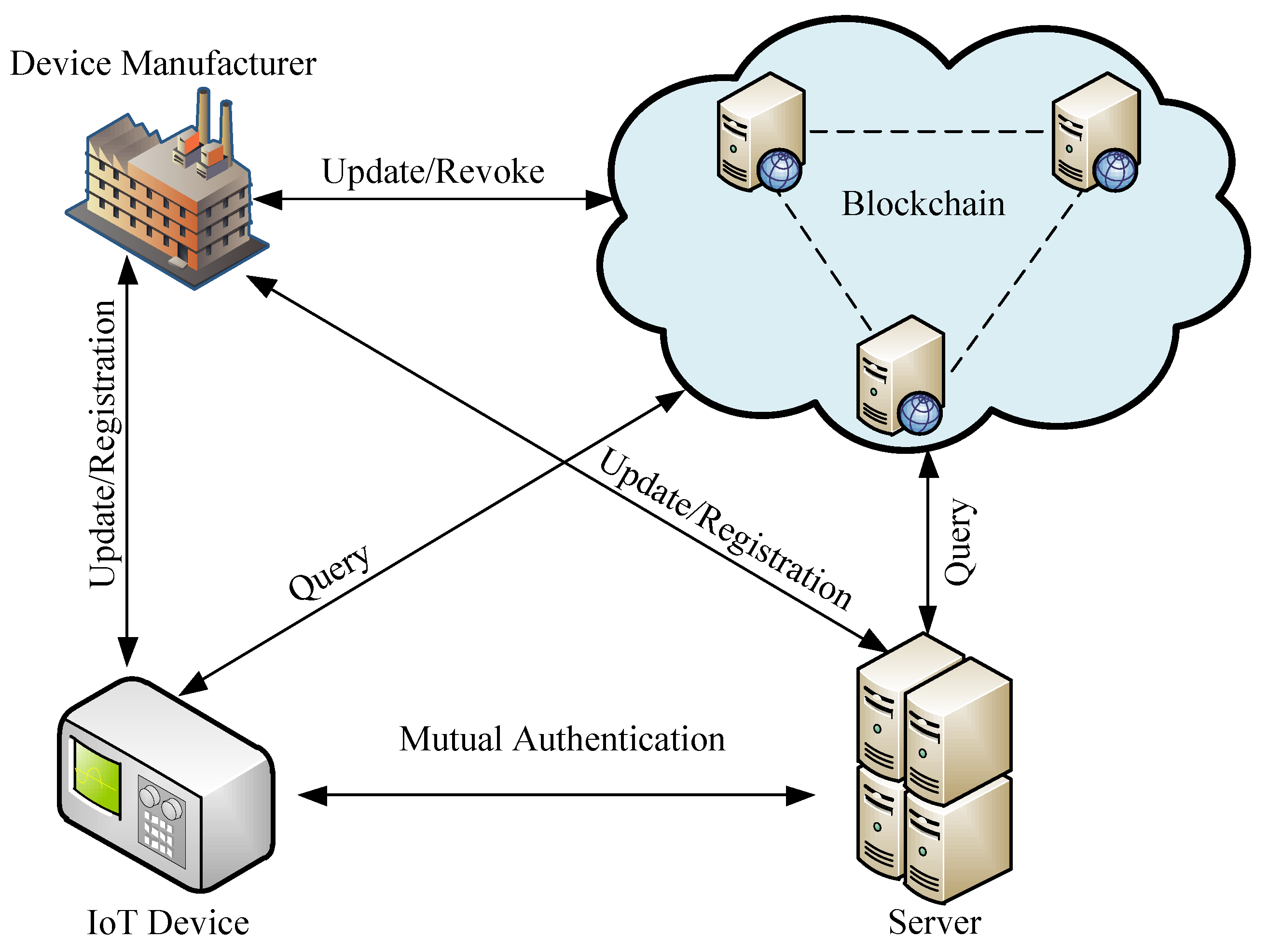
In the initialization phase of the protocol, the public parameters are announces, i.e., . In addition, the blockchain is also established, e.g., based on some existing blockchain systems such as Hyperledger Fabric or Ethereum.
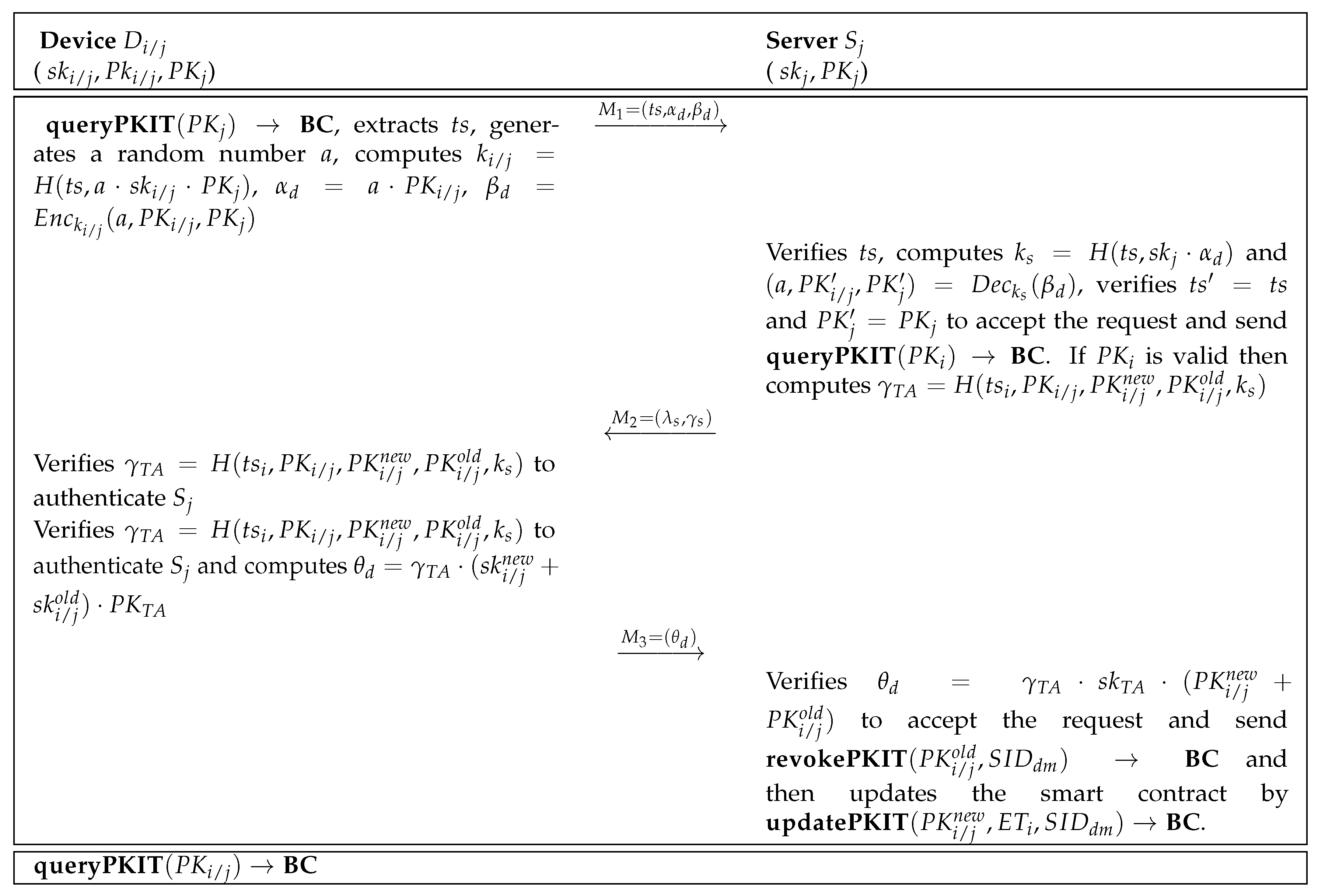
During the registration phase, all devices should be registered to a pre-authenticated device manager (DM), which is assumed to be trusted. Each IoT device, when it is produced by DM, selects two random primes and such that and computes . The device sends its identity along its public key to DM and it also confirms the validity and updates into the smart contract, through , where denotes expiry time of the IoT device and refers to the DM’s identity. The device can verify its validity by invoking . The registration of the server is also similar, where the server’s public key is , its identity is and its expiry time is .
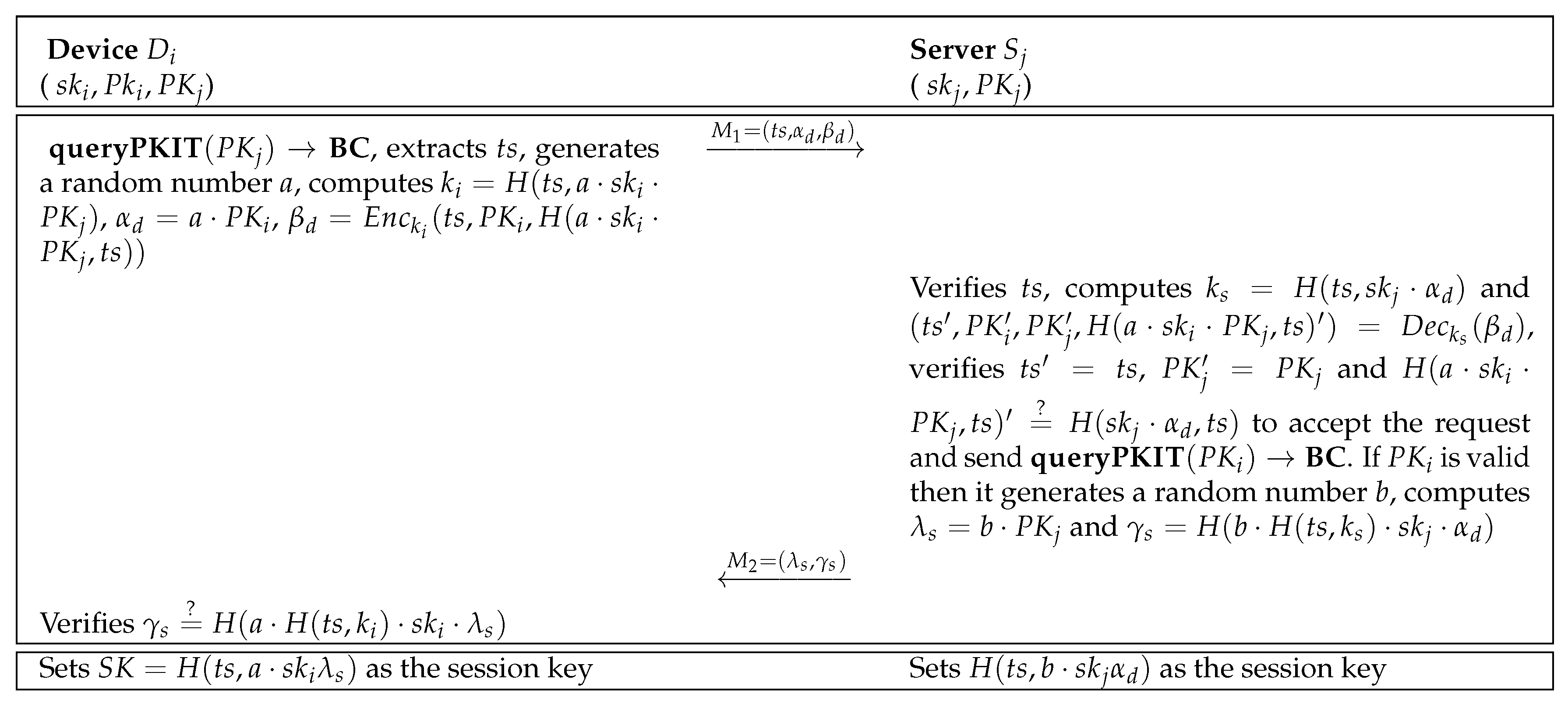
The authentication phase of the protocol between the i-th IoT device and the j-th server is initiated by the IoT device, where it first verifies the validity of by invoking the query function into the blockchain. Assuming that is confirmed by the blockchain, otherwise it should be authenticated with another server, obtains the timestamp and selects a random integer a such that , where . Then, given and , calculates the square roots of , i.e., , , and , and sets . Next, it computes , , and and sends to .
Once received , verifies its correctness to authenticate . More precisely, given and , it computes the roots of , i.e., , , and , and computes to identify the secret key as . Given , it decrypts and obtains . Afterward, the validity of is verified. Next, verifies the validity of by invoking the query function into the blockchain. Assuming that is legitimate, it verifies whether to authenticate the device. To be authenticated by , the server generates and sends it to the device as .
verifies the received to authenticate and sets as the session key; otherwise, the authentication process fails.
3.2. On the Security of Yang et al.’s Scheme
Although the scheme proposed by Yang et al. has interesting features and ensures mutual authentication between IoT devices and the server, it is also secure against most attacks assuming the adversary only has access to messages transferred over the public channel. Other attacks, on the other hand, are based on more serious assumptions about the adversary. For example, the security of previous sessions, if the long-term secret key has been leaked, or the security of the session key if the adversary has obtained the ephemeral session-dependent values.
These types of attacks are important because IoT devices are distributed across the network and the adversary may be able to access them and read their memory, which includes long-term secrets, for example. A privileged insider adversary can also leak the server’s data at any time. In this case, the security of previous sessions should be compromised as a result of this damage. In this section, we highlight some critical flaws in Yang et al.’s protocol in this framework.
3.2.1. The Lack of Perfect Forward Secrecy
The protocol provides perfect forward secrecy if compromising the entities’ long-term secrets at time t does not affect the security of the shared session keys at any time .
Let us assume that the adversary eavesdropped on the transferred messages over the public channel in a session, which are and where , , and . In addition, assume the adversary is given access to the long-term secrets of the server which are and . It is clear that the adversary, given and , can follow the used procedure by the server to retrieve the values. More precisely, she or he computes the roots of , i.e. , , and , and computes to identify the secret key as . Given , it decrypts and obtains . Afterward, the adversary verifies whether to make sure whether he or she retrieved the values correctly. It shows this protocol does not provide perfect forward secrecy.
3.2.2. Known Session-Specific Temporary Information Attack
Let us assume that the adversary knows the session-specific temporary values. In a secure protocol, it should not affect the security of the shared session key. Hence, we evaluate the security of Yang et al.’s scheme against the Known Session-specific Temporary Information Attack (KSTIA). More precisely, if the session’s short-term secrets are accidentally exposed to an attacker, the security of the produced session key should be unaffected. However, in Yang et al.’s scheme, the session key is computed as , where a is a selected random integer by the device . It is clear that exposing a leads to direct leakage of the session key . Hence, this protocol is valuable to KSTIA.
3.3. On the Efficiency of Yang et al.’s Scheme
Following description of Yang et al.’s scheme, to verify , computes the roots of , i.e., , , and , and computes to identify the secret key as . However, it is possible to verify the correctness of the driven roots after decryption of , where is obtained. Afterward, the validity of and are verified. Next, verifies the validity of by invoking the query function into the blockchain to authenticate the device. To be authenticated by , the server generates and sends it to the device as . In this way, it is not necessary to force the end device to also support MAC function and it also reduces the communication cost, because can be redesigned as . Hence, it shows that Yang et al.’s scheme is not optimum in the term of the used primitives and communication cost.