Abstract
A group authenticated key exchange (GAKE) protocol allows a set of parties belonging to a certain designated group to agree upon a common secret key through an insecure communication network. In the last few years, many new cryptographic tools have been specifically designed to thwart attacks from adversaries which may have access to (different kinds of) quantum computation resources. However, few constructions for group key exchange have been put forward. Here, we propose a four-round GAKE which can be proven secure under widely accepted assumptions in the Quantum Random Oracle Model. Specifically, we integrate several primitives from the so-called Kyber suite of post-quantum tools in a (slightly modified) compiler from Abdalla et al. (TCC 2007). More precisely, taking as a starting point an IND-CPA encryption scheme from the Kyber portfolio, we derive, using results from Hövelmanns et al. (PKC 2020), a two-party key exchange protocol and an IND-CCA encryption scheme and prove them fit as building blocks for our compiled construction. The resulting GAKE protocol is secure under the Module-LWE assumption, and furthermore achieves authentication without the use of (expensive) post-quantum signatures.
1. Introduction
The search for cryptographic primitives that will remain secure once quantum computing is a reality has been on going for over twenty years. Noticeably, in the last few years this search has gained greater attention from academia and industry, especially since the US National Institute of Standards and Technology (NIST) launched a competition towards standardizing quantum-resistant (also called post-quantum) public-key cryptographic algorithms in 2017. While this competition is focused on constructions for public key encryption, two party key establishment and digital signatures, research towards different post-quantum primitives has also been aroused as a side effect.
Group key establishment protocols (GKE) are fundamental cryptographic constructions. Indeed, for many real life applications of information technologies, the crucial starting point is establishing a “secure session”, i.e., setting confidential communication channels among users. GKE protocols allow a group of 2 users, interacting through an insecure communication network, to establish a common known high entropy secret that can be used to secure their subsequent communication. Typically, once this secret has been agreed upon, tools from symmetric cryptography can be used to attain confidentiality, and thus the communication network is understood as secure for confidential transmissions within the group of honest users. Using a GKE in this setting clearly outperforms the use of two party solutions, as establishing different session keys for every pair of participants (e.g., using a two party key exchange) would force each participant to store a large number of keys. Moreover, every message intended for the whole group should be encrypted multiple times () with different keys, while GKE can be used in a broadcast fashion (as messages are processed the same way for each group member). There might, however, be no way of assessing origin and integrity of messages. In this case, when authenticated channels are not available, protocols pursuing this goal—GAKE protocols—get way more involved and often need to rely on an external public key infrastructure to be able to authenticate legitimate group members, frequently adding a significant cost to the constructions.
Related work. Several group key exchange protocols which can be considered to resist quantum attacks have been proposed so far. Fujioka et al. [1] presented two one-round authenticated protocols, whose security is based on a certain algebraic-geometric problem related to the problem of finding a so-called isogeny mapping between two supersingular elliptic curves with the same number of points.
Other protocols use lattice problems as a base. For instance, Apon et al. [2] constructed a three-round unauthenticated protocol proven secure under the so-called ring learning with errors (RLWE) assumption. This scheme may be transformed into an authenticated one by using the Katz and Yung compiler [3]. However, the resulting protocol has one additional round of communication and each message that is sent must be signed, adding a significant computation and communication overhead if a post-quantum signature scheme is employed. Using the same problem as a base, Choi et al. [4] built on [3] and proposed three group protocols: the first is unauthenticated, the second adds authentication, and the third is, in addition, dynamic. The second one, STAG, is a three-round authenticated protocol in which each user computes two signatures.
Finally, we have compilers which produce a quantum-resistant group authenticated key exchange (GAKE) from simpler post-quantum primitives. Persichetti et al. [5] presented a three-round protocol constructed from a key encapsulation mechanism (KEM) and a signature scheme; each user needs to compute only one signature. González Vasco et al. [6] introduced a two-round password GAKE protocol derived from a KEM and a message authentication code (MAC). However, in this construction, security holds in the so-called future-quantum scenario, where the adversary is assumed to have access to quantum computation only after the protocol execution is completed.
Our contribution. In this work, we take the so-called Kyber family [7] of post-quantum cryptographic tools and use it as a base for a GAKE design. More precisely, our construction is a compiled system using Abdalla et al.’s [8] as design frame. From the results of Hövelmanns et al. [9], we assess that both a suitable commitment scheme and a secure two-party AKE can be obtained from the encryption scheme Kyber.CPA (this result was hinted, yet not explicitly proven by Hövelmanns et al. [9]). As far as we are aware, our instantiation is the first group authenticated key exchange protocol which provides post-quantum security guarantees based solely on the so-called Module-LWE assumption, doing without (often unaffordably expensive) post-quantum signatures.
Our GAKE: overview. The workflow of our construction is depicted in Figure 1. Our construction relies on Abdalla et al.’s compiler [8] that requires a two-party AKE and a commitment scheme and we need both building blocks to fulfill post-quantum security. To achieve post-quantum security, we apply the Kyber family and its derived tools (see green rectangle in Figure 1).
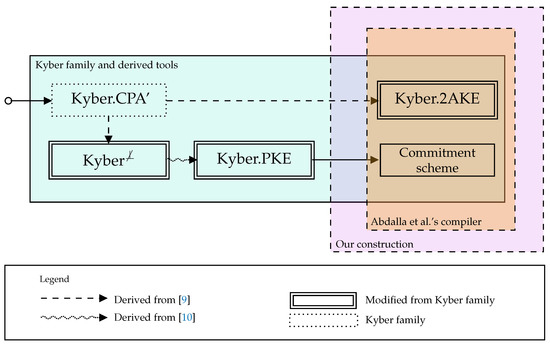
Figure 1.
Workflow of our construction.
Kyber [7] is a KEM based on lattices whose security relies on Module-LWE assumption (Definition 1), claimed to be post-quantum secure. Our GAKE inherits the Module-LWE assumption. The two-party AKE and the commitment scheme are derived from the initial IND-CPA PKE in [7] named Kyber.CPA. The two-party AKE (named Kyber.2AKE) is the result of applying the transformation [9] to Kyber.CPA. Finally, a commitment scheme can be achieved from any IND-CCA PKE, as pointed out in [8]. In our construction, we turn Kyber.CPA into a KEM applying the transformation [9] obtaining , which is transformed into an IND-CCA PKE (Kyber.PKE) as a result of [10].
Comparison with other schemes. We present two tables that summarize some features of other GAKE schemes with quantum-resistance and compare them with our proposal.
Table 1 summarizes some parameters related to the performance of the schemes. The number of communication rounds is one of the most important parameters when dealing with GAKE protocols. In addition, for each scheme, we point out whether the use of post-quantum signatures is avoided, which is a nice feature, as this kind of signatures are usually expensive in terms of both computation and size. Note that the scheme in [2] does not use post-quantum signatures but is unauthenticated. Finally, we include the total number of messages sent throughout an execution involving n parties, pointing out whether messages are broadcasted or just sent point-to-point (PtP) (i.e., from one party to another).

Table 1.
Some efficiency parameters for GKE/GAKE protocols claimed to be quantum-resistant.
Table 2 is focused on security issues. In the first column, we include the type of assumption (isogeny/lattice) the security of the scheme is based on. In the second column, we state in which of the idealized models the security claim and corresponding proof hold: either in the Random Oracle Model (ROM) or the Quantum Random Oracle Model (QROM). The latter is stronger than the former because, as discussed in Section 2, it assumes a more powerful adversary. Next, it is specified if quantum resistant features hold in a future quantum (FutQ) or post-quantum (PostQ) scenario. The latter, where it is assumed that the adversary has access to quantum computation during protocol executions, is preferable to the former, where key secrecy is only guaranteed against adversaries that cannot make quantum computations during protocol executions but have access to this option at some point in the future. Finally, we indicate if the key exchange is authenticated. Note that the compilers [5,6] have a special treatment, as the assumption type and the model depend on the underlying post-quantum tools used to implement them.

Table 2.
Security of GKE/GAKE protocols claimed to be quantum-resistant.
Seeing the two comparison tables, it seems clear that the only scheme outperforming our construction is n-UM [1], which is based on the isogeny paradigm. However, it is fair to say that lattice-based constructions such as ours seem somewhat more promising in this field, considering the recent outcome of the Third Round of the NIST competition for standardizing post-quantum tools. While several lattice-based constructions made it to this last round, no isogeny-based scheme is in the final (and only one proposal, SIKE [11], is considered as alternative for replacing finalists that may be discarded in the last phase).
Paper Roadmap. We start with a brief outline of the preliminaries in Section 2, where we introduce Abdalla et al.’s compiler from [8] and comment on the basics of post-quantum security. Further, we explain in Section 3 how to derive building blocks for our construction (AKE and a commitment scheme) from the Kyber family. In particular, we use the results from [9] to prove that we can obtain both a suitable commitment scheme and a secure two-party AKE from the encryption scheme Kyber.CPA. Our compiled construction is then described and proven secure in Section 4, where we also make explicit the security model used. We conclude this contribution with a brief conclusion.
2. Preliminaries
2.1. Abdalla et al.’s Compiler
Here, we describe a compiler constructed by Abdalla et al. in [8], which enables the derivation of a group authenticated key establishment protocol from an arbitrary two-party key establishment . The compiler does not rely on further authentication techniques than those used in , nor on further idealization assumptions. Moreover, if requires r rounds of communication, then requires rounds.
Let be the set of users that can participate in the protocol . This set is assumed to be of polynomial size. The set denotes the set of participants that wish to establish a common session key. Each protocol participant , , may be involved in distinct, possibly parallel, executions of .
Since is an authenticated key establishment protocol, it is assumed that long-term secrets required for have been established during a trusted authentication phase. One of the following three cases is assumed:
- Each user owns a pair consisting of a public key and a secret key , and all needed public keys may be distributed to all protocol participants during the initialization phase.
- Each pair of users , , shares a high entropy symmetric key, or the complete set of participants shares one common secret (different instances of a user may hold different long-term secrets).
- Each pair of users , , shares a low entropy password. In this case, we assume a publicly available dictionary from which passwords are chosen uniformly at random.
The compiler uses the following cryptographic tools:
- A non-interactive non-malleable commitment scheme that is perfectly binding and achieves non-malleability for multiple commitments.
- A collision-resistant pseudorandom function family with to be indexed by a set of polynomial size, and two publicly known values and such that no ppt adversary can find two different indices such that , .
- A hash function selected from a family of universal hash functions that maps the concatenation of bitstrings from and the set of participants onto , where n is the number of participants in and .
With these ingredients, the compiler proceeds as depicted in Figure 2. Our proposed protocol uses a simplified version of the aforementioned compiler and builds on a post-quantum . We describe it in detail in Section 4.
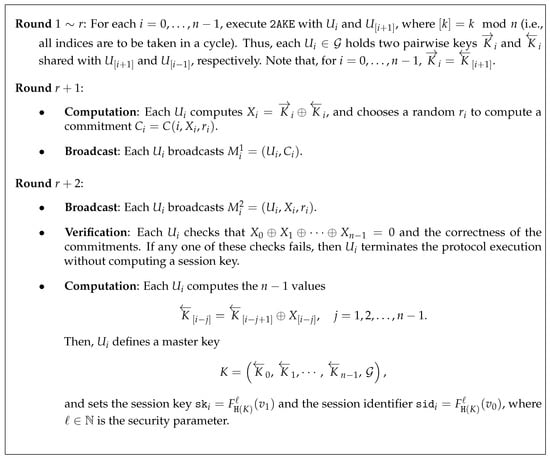
Figure 2.
Abdalla et al.’s compiler.
2.2. Security in a Post-Quantum Setting
When proving a certain cryptographic construction secure, it is necessary to depict a precise security model making explicit claims and assumptions that can be formally proven and verified. This is, however, not always the case in the post-quantum scenario, as quantum adversaries are often modeled in a very different fashion. Most often, constructions are substantiated on computational assumptions that explicitly state that an adversary is assumed not to be able to efficiently complete a certain computational task (e.g., decoding a word with respect to a certain partially known code or solving certain approximation problems in lattices). However, the way this quantum adversary is assumed to interact with other system-related idealizations (e.g., the oracles modeling information leakage or misuse) is often disregarded, while it may play a central role in a security proof. A paradigmatic example of this situation is the case of hash functions, typically modeled as so-called random oracles.
Random oracles are classically used in cryptography to model idealized hash functions, which are deterministic algorithms that select, for each new query, an output chosen uniformly at random from a certain given range. It is assumed that all users and processes from a certain system are given access to the same random oracles, which means that, for security proofs, if the real cryptographic environment is simulated for an adversary, all random oracle queries must be consistently answered with values that are indistinguishable from random (uniform). In the quantum setting, queries to a random oracle can be done in superposition, which complicates significantly the translations of many classical proofs into this new scenario.
Following Hövelmanns et al. [9], in this work, we consider quantum adversaries that are given quantum access to the (offline) quantum random oracle involved in our design. More precisely, we need to make use of two basic properties of this so-called quantum-accessible random oracles:
- Collision-freeness. In [12], it is proven that the best quantum algorithm for finding a collision for a random function (i.e., a pair of distinct such that ) is . (Notation “wipes out” logarithmic factors in , namely, ). The analogous classical bound is While being suboptimal in number of queries, this algorithm is the most efficient in terms of time complexity with small quantum memory. Thus, in the sequel, we may assume that (even for a quantum adversary) finding a collision pair for a quantum-accessible random oracle can only be done with negligible probability (this is used in Section 4.3.1).
- Pseudorandomness. Following again Hövelmanns et al. [9], we use the argument of Zhandry (see [13]) stating that no quantum algorithm, making at most q quantum queries to a quantum random oracle implementing a random function , can distinguish between and a random polynomial of degree defined over the field As a result, if the input to a quantum random oracle contains enough entropy, then the probability of distinguishing its output from a value chosen uniformly at random is negligible. In other words, when the input is unknown and chosen uniformly at random, the fact that the random oracle can be queried in superposition is of no help in distinguishing the oracle’s output from a randomly chosen element. This is used in the quantum random oracle proof from Section 4.3.
We strongly suggest the interested reader consult [14] for a comprehensive introduction to the quantum random oracle model.
3. Post-Quantum Primitives: and Commitment Scheme
In this section, we describe the post-quantum tools used in the construction of our , namely a two-party authenticated key exchange (AKE) and a commitment scheme. The relations between these tools are summarized in Figure 3.
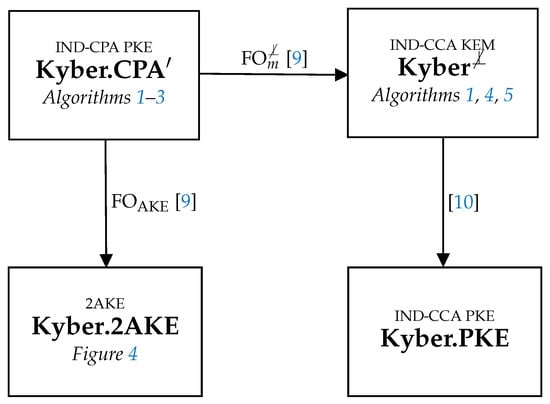
Figure 3.
Kyber and derived tools.
In the first subsection, we describe Kyber’s public key encryption (PKE) scheme and state its security properties that are of importance to the construction of the primitives mentioned above.
In the second subsection, we detail how the is obtained from a generic construction proposed in [9], of two-message AKE provably secure in the quantum random oracle model (QROM) from PKE schemes that possess both Disjoint Simulatability (DS) (Definition 2) and IND-CPA security. In particular, we use a slight modification (called Kyber.CPA) of the CPA-secure PKE scheme introduced in [7] as part of Kyber’s package submitted to NIST’s post-quantum standardization effort. We describe the transformation which turns a secure PKE into a secure AKE. This subsection ends by proving that Kyber.CPA is DS secure and, therefore, it is possible to construct an AKE secure in the QROM by applying the to it.
The third subsection is devoted to the construction of the post-quantum commitment scheme mentioned in Section 2. It must be a non-interactive non-malleable commitment scheme that is perfectly binding and achieves non-malleability for multiple commitments. As pointed out in [8], this can be directly constructed from a public key encryption scheme which achieves the well-known IND-CCA security notion. To this end, we use another transformation described in [9], specifically , which turns an IND-CPA and DS PKE into an IND-CCA KEM. Then, we recall that it is straightforward to obtain an IND-CCA PKE from an IND-CCA KEM. Putting everything together, we obtain the desired commitment scheme from Kyber.CPA, the same primitive we use to construct the two-party AKE.
3.1. Kyber’s IND-CPA PKE
In this subsection, we describe the CPA-secure PKE scheme Kyber.CPA introduced in [7] as part of the Cryptographic Suite for Algebraic Lattices (CRYSTALS), a package of cryptographic primitives submitted to NIST’s post-quantum standardization effort. In fact, what we really describe and work with is a slightly modified version, also proposed in [7], called Kyber.CPA.
First, we introduce some definitions needed to understand how the PKE has been constructed and summarize in Table 3 the notation used in the sequel. Then, we describe the key generation, encryption, and decryption algorithms used in Kyber.CPA, as well as its CPA-security under the Module-LWE hardness assumption (Definition 1).

Table 3.
Notation used for Kyber.CPA.
Denote by R the ring and by the ring , where such that is the th cyclotomic polynomial. As in [7], we fix the values for n, and q to 256, 9 and 7681.
For some positive integer , define the centered binomial distribution as follows ([7]):
The security assumption underlying Kyber.CPA is based on the hardness of the Module-LWE problem, which generalizes the Learning with Errors (LWE) problem. Learning with errors (LWE) is the computational problem of inferring a linear n-ary function f over a finite ring from given (slightly incorrect) samples . Recall that Ring Learning with Errors (RLWE) is the variant of LWE specialized to polynomial rings over finite fields. Informally, Module-LWE can be seen as the result of replacing single ring elements in the RLWE problem with module elements over the same ring (thus, RLWE can be seen as Module-LWE with module rank 1).
Definition 1
(Module-LWE assumption [7]). The Module-LWE problem consists in distinguishing uniform samples from samples where is uniform, common to all samples, and is fresh for every sample. The advantage of an adversary is defined as
The Module-LWE assumption states that the above advantage is negligible for any given adversary .
The authors of [7] defined a function that takes an element and outputs an integer in , where . Furthermore, a function is defined such that
is an element close to x. More specifically,
The functions satisfying these requirements are defined in [7] as:
Kyber’s PKE scheme Kyber.CPA = (KeyGen, Enc, Dec) is parameterized by the positive integers , and . The value of these parameters vary for different security levels. Moreover, is the message space and ciphertexts are of the form . The definition of the key generation, encryption, and decryption of Kyber.CPA is given in Algorithms 1–3 as defined in [7]. Unlike Kyber.CPA, the unmodified PKE scheme Kyber.CPA compresses on Line 4 of Algorithm 1 and, therefore, must decompress in Algorithm 2.
Kyber.CPA was shown to be IND-CPA secure under the Module-LWE hardness assumption in [7]. This result is stated in the following theorem.
Theorem 1
([7]). For any adversary against the CPA security ofKyber.CPA, let define the advantage
Then, there exists an adversary such that
Finally, it is worth pointing out that neither nor provides perfect correctness. This is discussed in [7], where a value for , the probability of decryption error, is obtained for . This is easily adapted to ; the details can be found in Appendix A.
| Algorithm 1:Kyber.CPA.KeyGen() |
| 1
2 3 4 5 return |
| Algorithm 2:Kyber.CPA.Enc() |
| 1 2 3 4 5 6 return |
| Algorithm 3:Kyber.CPA.Dec() |
| 1 2 3 return |
3.2. The Transformation: From PKE to AKE
is a generic construction proposed in [9], which transforms an IND-CPA secure PKE scheme into an AKE protocol, provably secure in the QROM. The construction admits that the PKE scheme has non-perfect correctness, which makes it suitable for the Kyber.CPA scheme we have previously introduced. Another nice feature is that it avoids the use of (usually expensive) quantum-secure signature schemes. can be seen as an extension of the Fujisaki–Okamoto transform (which turns IND-CPA encryption schemes into IND-CCA ones) for the AKE setting.
The resulting AKE after applying the transformation is quite efficient in terms of communication. In [9], it is called a two-message protocol, meaning that it is a two-round AKE protocol where one party sends a message in the first round while the other party answers with another message in the second round. As an interesting additional contribution, the authors of [9] defined a security model and two security notions for two-message AKEs: key indistinguishability agains active attacks (IND-AA) and the weaker notion of indistinguishability against active attacks without state reveal in the test session (IND-StAA). We are interested in the second one, as the security of the AKE obtained by using the transformation is proved in [9] under this slightly weaker model. Nevertheless, this is enough for our purposes because, as discussed in Section 5 of [15] (the extended version of [9]), IND-StAA implies security in the sense required in the compiler from [8].
A high level description of the IND-StAA model, as formulated in [9], is the following. It states that the session key remains indistinguishable from a random one even if:
- The attacker knows either the long-term secret key or the secret state information (but not both) of both parties involved in the test session, as long as it did not modify the message received by the test session.
- If the attacker modified the message received by the test session, as long as it obtained neither the long-term secret key of the test session’s peer nor the test session’s state.
The authors of the transformation proved its IND-StAA security in the QROM as long as the PKE is IND-CPA, and it is possible to efficiently fake ciphertexts that are indistinguishable from proper encryptions, while the probability that the sampling algorithm hits a proper encryption is small. This last notion is called Disjoint Simulatability (DS) of ciphertexts, and is defined in [9] as follows.
Definition 2
(DS). Let be a PKE scheme with message space and ciphertext space , coming with an additional ppt algorithm . For quantum adversaries , we define the advantage against ’s disjoint simulatability as
When there is no chance of confusion, we drop from the advantage’s subscript for convenience. We call -disjoint if for all ,
where is a finite randomness space defined by .
The authors of the transformation suggested that many lattice-based schemes fulfill DS in a natural way as follows: fake encryptions could be sampled uniformly random. DS would follow from the LWE assumption, and since LWE samples are relatively sparse, uniform sampling should be disjoint.
The following theorem establishes that the DS security of equipped with an additional algorithm reduces to its Module-LWE security.
Theorem 2
(DS security of ). Let , and be positive integer parameters for . If is equipped with a ppt algorithm which samples a uniform ciphertext when given a public key, then, for any adversary , there exists an adversary such that
Furthermore, is -disjoint with
Proof.
Let be an adversary attacking the DS security of . We obtain a bound for following the sequence of games in the proof of Theorem 2 in [7].
First, the value which is used in KeyGen is substituted by a uniform random value. It follows from the Module-LWE security of that the value and the uniform random value are indistinguishable from each other. Next, the values and used in the generation of the challenge ciphertext are simultaneously substituted with uniform random values. Again, it follows from the Module-LWE security of that and are indistinguishable from the random values. As in [7], we deduce that there exists an adversary with the same running time as that of such that .
To prove the -disjointness of with , we recall that , , and are the message, ciphertext and random spaces, respectively. Since , we obtain
which is the desired result. □
Now that Theorems 1 and 2 guarantee that satisfies the hypotheses of Theorem 3 in [9], we can use it to produce a two-party AKE which fulfills IND-StAA security in the QROM. The resulting scheme, which we denote by Kyber.2AKE, is depicted in Figure 4. Here, and are random oracles and , , , and are internal random oracles that cannot be accessed directly and could be implemented with a pseudorandom function. Note that this is not the same two-party AKE proposed in [7]. For reference, we include the precise statement of Theorem 3 [9] in Appendix B.
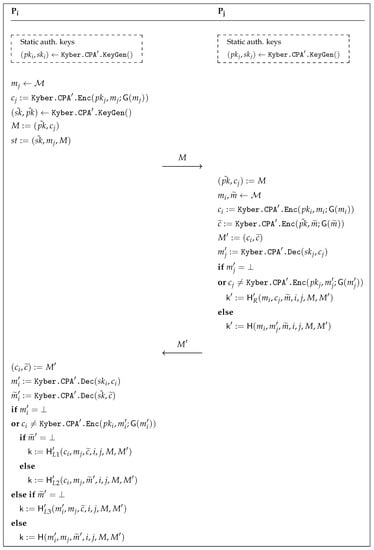
Figure 4.
Kyber.2AKE.
3.3. The Commitment Scheme
In this section, we describe how to obtain an IND-CCA PKE from an IND-CPA PKE. This process can be achieved in two steps:
- Apply the transformation [9] that converts an IND-CPA PKE into a IND-CCA KEM.
- Apply the transformation proposed in [10] to achieve an IND-CCA PKE from an IND-CCA KEM.
To achieve an IND-CCA secure KEM from Kyber.CPA, we apply the transformation. This is analogous to the transformation that transforms a PKE scheme that is both IND-CPA and DS secure into a CCA-secure KEM. As shown in [9], unlike similar transformations, is robust against correctness errors and its security reduction is tighter than the one that results from applying other known transformations. In cases where the PKE is not already DS, this requirement can be waived with negligible loss of efficiency. In the case of Kyber.CPA, there is no loss of efficiency since it is IND-CPA secure and, as shown in Theorem 2, it is DS secure as well. The Algorithms 1, 4, and 5 show the KEM = (Kyber.CPA.KeyGen, Encaps, Decaps) that results from applying the transformation to Kyber.CPA. Here, and are random oracles and is an internal random oracle that cannot be accessed directly and could be implemented with a pseudorandom function. For reference, we include the precise statement of Theorem 2 [9] in Appendix C.
| Algorithm 4:() |
| 1 2 3 k := H(m) 4 return |
| Algorithm 5:() |
 |
Finally, an IND-CCA PKE is obtained after applying the transformation introduced in [10] to with a secure one-time symmetric key encapsulation (SKE or DEM). We call this scheme Kyber.PKE. The security of this transformation follows from Theorem 5 in [10]. As pointed out in [8], a commitment scheme with the required security properties can be obtained in a straightforward way from the IND-CCA PKE.
4. Our Post-Quantum Group Key Exchange
In this section, we present our compiled construction of GAKE. Informally, let us recall the setting we are considering. Our participants are honest entities which can be modeled as probabilistic polynomial time Turing machines (thus, have no access to quantum computing resources). These participants can only exchange messages through an insecure network, which is fully under adversarial control (adversaries may insert, delay, suppress or forward messages at will). Moreover, the adversarial computing capabilities are superior to those of participants, as we assume adversaries can preform quantum polynomial time computations and have quantum access to any hash function (modeled as a random oracle) involved. With this in mind, the goal pursued by our protocol is to guarantee that, whenever a participant has computed a session key through the network, this key is indistinguishable from a random value for those outside the intended group of participants involved in that concrete execution. Note that (as is standard in GKE proposals) we cannot expect to prove that the protocol will always terminate when executed by honest parties, we rather pursue formal assurance that, whenever the protocol indeed produces an output key for a participant, this key is secure for subsequent use.
Now, to make the text fully self-contained, we start by describing the main notations and formalism used in the sequel.
4.1. Security Model
Our security model is inherited from Abdalla et al. [8], which in turn builds upon the seminal work of Bellare et al. [16]. However, ours is a less generic scenario; while in [8] all the proofs are in the common reference string model, our proofs are in the (quantum) random oracle model. More precisely, we assume that all public keys and parameters needed for implementing and are publicly known (and certified), as well as the description of all involved hash functions, which are idealized as random oracles. Further, we will assume that the long term keys needed for authentication in are generated and distributed to all potential protocol participants in a trusted initialization phase. As customary, we use variables to detail the information stored by users with respect to each protocol execution, and oracles to model adversarial action.
4.1.1. Protocol Instances
Each protocol participant () may execute a polynomial number of protocol instances in parallel. A single instance can be interpreted as a process executed by protocol participant . Throughout, the notation is used to refer to instance of protocol participant . To each instance, we assign seven variables:
- indicates whether this instance is or has been used for a protocol run. The flag can only be set through a protocol message received by the instance due to a call to the - or to the -oracle (see below).
- keeps the state information needed during the protocol execution as well as the long term keys needed for authentication.
- shows if the execution has terminated.
- denotes a public session identifier that can serve as identifier for the session key Note that, even though we do not construct session identifiers as session transcripts, the adversary is allowed to learn all session identifiers.
- stores the set of identities of those users that aims at establishing a key with—including himself.
- indicates if the protocol instance was successful, i. e., the user accepted the session key.
- stores the session key once it is accepted by Before acceptance, it stores a distinguished null value.
We do not make explicit the initialization and evolution of all variables mentioned above, yet omissions are straightforward to understand from the context.
4.1.2. Communication Network
We assume arbitrary point-to-point connections among users to be available. The network is non-private and fully asynchronous: The adversary may delay, eavesdrop, insert, and delete messages at will.
4.1.3. Adversarial Capabilities
Following Hövelmanns et al. [15], we consider adversaries that can preform (quantum) polynomial time computations, and have classical access to all (online) oracles listed below. Furthermore, as explained in Section 2.2, our adversaries are given quantum access to any (offline) random oracles involved.
The capabilities of an adversary are made explicit through access to oracles allowing to communicate with protocol instances run by the users:
- This sends message M to the instance and returns the reply generated by this instance. If queries this oracle with an unused instance and a set of identities of principals, the -flag is set, initialized with , and the initial protocol message of is returned.
- This executes a complete protocol run among the specified unused instances of the respective users. The adversary obtains a transcript of all messages sent over the network. A query to the Executeoracle is supposed to reflect a passive eavesdropping.
- This yields the value stored in .
- Let b be a bit chosen uniformly at random. Provided that the session key is defined (i. e., and ) and instance is fresh (see the definition of freshness below), can execute this oracle query at any time when being activated. Then, the session key is returned if and a uniformly chosen random session key is returned if . In this model, an arbitrary number of Testqueries is allowed for the adversary , but, once the oracle has returned a value for an instance , it will return the same value for all instances partnered with (see the definition of partnering below).
- This returns all long-term secrets of user —in our case, the private keys used for authentication in .
4.1.4. Correctness, Integrity and Secrecy
To define our correctness and security goals, we introduce partnering to express which instances are associated in a common protocol session.
Partnering. We refer to instances and as being partnered if , , and .
An instance is assumed to accept the session key constructed at the end of the corresponding protocol run if no deviation from the protocol specification has occurred. Moreover, without adversarial interference, all users involved in a certain session should come up with the same session key.
Definition 3.
We call a group key establishment protocol correct, if in the presence of a passive adversary —i. e., must neither use the Send nor the Corrupt oracle—the following holds: for all with both and , we have and .
Some sort of correctness should also be guaranteed even if adversaries actively participate in a concrete executions: the notion of integrity, introduced in [17], captures this idea.
Definition 4.
We say that a correct group key establishment protocol fulfills integrity if, with overwhelming probability, all instances of honest principals that have accepted with the same session identifier hold identical session keys and associated this key with the same principals .
Next, for detailing the security definition, we have to specify under which conditions a -query may be executed.
Definition 5.
A -query should only be allowed to those instances holding a key that is not for trivial reasons known to the adversary. To this aim, an instance is called fresh if none of the following holds:
- For some , a query was executed before a query of the form has taken place, for some message (or set of identities) M and some .
- The adversary earlier queried with and being partnered.
The idea of this definition is that revealing a session key from an instance trivially yields the session key of all instances partnered with , and hence this kind of “attack” will be excluded in the security definition.
For a secure group key establishment protocol, we have to impose a corresponding bound on the adversary’s advantage: The advantage of a ppt adversary in attacking protocol is a function in the security parameter ℓ, defined as
Here, is the probability that the adversary queries only on fresh instances and guesses correctly the bit b used by the oracle (without violating the freshness of those instances queried with
Definition 6.
We say that an authenticated group key establishment protocol is secure if for every ppt adversary the following inequality holds for some negligible function :
4.2. Our Construction
We aim at a full description of a GAKE protocol that can be proven secure against quantum adversaries, building on a post-quantum and using the compiler described in Section 2.1. Our proposal is depicted in Figure 5. Note that in our compiled design we take as starting point a slightly modified version of the compiler from [8], in two ways:

Figure 5.
Proposed Post-Quantum group-key establishment.
- We simplify the session key and session identifier computation using two hash functions to extract them from the shared master key K. Indeed, as the we use as building block is proven secure in the (quantum) random oracle model, it no longer makes sense to use the (somewhat complicated) key extraction procedure defined in [8] to dodge idealized hash functions. Thus, we forgo Tools 1 and 2 mentioned in Section 2.1 and use two hash functions and instead. Thus, at the final Computation phase, each user will set the session key as and the corresponding session identifier as , where K is the master key shared by everyone involved in the execution.
- Further, we make an additional requirement on the compiled , needed for the security proof. Indeed, as pointed out by Nam in [18], an extra condition on the two party protocol used as a base must be imposed in Theorem 1 of [8]. Indeed, the underlying should fulfill integrity in order to thwart a simple replay attack (in the proof of Theorem 1 of [8], it is actually assumed that integrity is fulfilled—see the argument related to Game 1). We thus slightly tune up the two-party to make sure integrity is achieved.
4.3. Security Arguments and Proofs
To prove that our compiled version is secure, we build upon the security of our underlying tools. More precisely, we use the following results:
- (i)
- , as depicted in Figure 4, is secure in the sense of IND-StAA and can be modified to also attain integrity as in Definition 4. Note that, as explained in Section 5 of [15], IND-StAA implies security in the sense required in the original compiler from [8].
- (ii)
- The encryption scheme yields a non-interactive commitment scheme that is both non-malleable for multiple commitments and perfectly binding. This comes straightforward as a result of this scheme being IND-CCA (see Section 3.3 and [15]).
4.3.1. A Variant of Attaining Integrity
Informally, it is easy to modify in a standard way the construction to attain integrity. The main idea is to add a second random oracle which, at the point of key derivation, will be applied to the same input as in order to derive a session identifier. Then, it is trivial to state that integrity of this modified construction is attained both in the ROM and in the QROM, due to the collision resistance of the involved random oracles (see Section 2.2). Indeed, suppose that . Since and are random oracles, their collision resistance guarantees that, with overwhelming probability, both participants have the same partner identifiers and, therefore, use the same session key k. This argument is valid both in the classical and quantum-accessible random oracle model (see Section 2.2). In the sequel, we assume this modification is in place and thus attains integrity.
4.3.2. Security of Our Proposed Group Protocol
Theorem 3.
In the random oracle model, the protocol presented in Figure 5 is a correct and secure authenticated group key establishment protocol fulfilling integrity, in the sense of Definitions 3, 6, and 4.
Proof.
This proof is a (somewhat) straightforward adaptation of the security proof of Theorem 1 of [8], which we use as a main tool in our construction.
Correctness. In an honest execution of the protocol, it is easy to verify that all participants in the protocol will terminate by accepting and computing the same session identifier and session key.
Integrity. Owing to the collision-resistance of the random oracle all oracles that accept with identical session identifiers also hold with overwhelming probability the same master key K and (which can be read from K) will therefore also derive the same session key
Key secrecy. The proof of key secrecy will proceed in a sequence of games, starting with the real attack against the key secrecy of the group key exchange protocol and ending in a game in which the adversary’s advantage is 0, and for which we can bound the difference in the adversary’s advantage between any two consecutive games. Following standard notation, we denote by the advantage of the adversary in Game i. Furthermore, for clarity, we classify the queries into three categories, depending on the stage of the protocol to which the query is associated, starting with and ending with . t denotes the query associated with round t for .
The first three games from this proof are exactly the same as those in the proof of Theorem 1 of [8]. We only summarize the reduction and refer the interested reader to the original paper for a detailed description.
Game . This first game corresponds to a real attack, in which all the parameters, such as the public parameters in the common reference string and the long-term secrets associated with each user, are chosen as in the actual scheme. By definition,
Game . In this game, for , we modify the simulation of the and oracles so that, whenever an instance is still considered fresh at the end of Round 2, the keys and that it shares with instances and are replaced with random values from the appropriate set.
It is easy to see that the distance between this game and the previous one is bounded by the probability that the adversary breaks the security of any of the underlying protocols. As a result, it holds
where represents the number of different protocol instances in queries.
Game . In this game, we change the simulation of the oracle so that a fresh instance does not accept in Round 4 whenever one commitment for it receives in Round 3 was generated by the simulator but not generated by the respective instance , in the same session.
The adversary can detect the difference to Game if replayed a commitment that should have led to acceptance in Round 4 in that game. Because the committed value is a random value independent of previous messages, the probability for this is negligible.
Game . This game reproduces the modification also for adversary-generated commitments: The simulation of the oracle changes so that a fresh instance does not accept in Round 4 whenever one commitment for it receives in Round 3 was adversary-generated. The adversary’s advantage diverges only negligibly from the previous game:
Game . Now, the simulations of the Execute and Send oracles are modified at the point of computing the session key. The simulator keeps a list of strings . Once an instance receives the last query, the simulator computes and checks if for the corresponding string a master key was already issued. If this is the case, it assigns the corresponding master key to the instance. If no such entry exists in the list, the simulator chooses a session key uniformly at random. Note that, even if the messages from Round 4 are sent out, the master key is still containing sufficient entropy so that the random oracle output is indistinguishable from a random with negligible probability only. As a result,
Now, clearly, in Game , all session keys are chosen uniformly at random and the adversary has no advantage.
□
Theorem 4.
In the quantum random oracle model, the protocol presented in Figure 5 is a correct and secure authenticated group key establishment protocol fulfilling integrity, in the sense of Definitions 3, 6, and 4.
Proof.
(sketch) The proof follows the exact reasoning of Theorem 3; we only need to stress that the argument from Game 4 is still valid when considering quantum-accessible random oracles. Indeed, in this last game, the simulations of the Execute and Send oracles are modified at the point of computing the session key. The simulator keeps a list of strings , and, upon receiving the last query, it computes the values and checks if a corresponding master key has already been issued previously. If this is the case, this master key will be assigned to the instance. Otherwise, the simulator chooses a session key uniformly at random. At this point, all two party keys are chosen uniformly at random and are unknown to the adversary. The adversary can only notice this last change if it has already queried the very same key string to the quantum random oracle . This event will happen with negligible probability. As a result, the output is indistinguishable from a random with overwhelming probability. Thus, we have
Now, clearly, in Game , all session keys are chosen uniformly at random and the adversary has no advantage.
□
5. Conclusions
We present in this paper a post-quantum GAKE using Abdalla et al.’s compiler from [8] as design frame. We choose the Kyber suite [7] as main building block, not only because it is a good design fit for our compiled strategy, but also considering its promising security properties (as Kyber is one of the four remaining finalists for public key encryption in the Third Round of the NIST competition). More precisely, we evidence that a secure 2AKE as needed for our compiled construction can be derived using the transformation proposed in [9], by proving the encryption scheme to be DS secure.
Our four-round instantiation can as a result be proven to provide post-quantum security guarantees under the Module-LWE assumption in the quantum random oracle model.
Author Contributions
All authors contributed equally to this work, in terms of Conceptualization, Methodology, Formal Analysis, Investigation, Writing—Original Draft Preparation and Review and Editing. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by NATO Science for Peace and Security Programme, grant number G5448 and by MINECO under Grants MTM2016-77213-R and PID2019-109379RB-I00.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Non-Perfect Correctness of Kyber.CPA′
As defined in [19], a PKE is said to be -correct if
where the expectation is taken over and the probability is taken over the random space of .
Following the proof of Theorem 1 in [7], it is not hard to prove the following theorem, which provides the value when dealing with .
Theorem A1.
Let k be a positive integer parameter. Let be random variables that have the same distribution as in Algorithms 1 and 2. In addition, let , be distributed according to the distribution ψ defined as follows:
Let be the following distribution over R:
- Choose uniformly-random
- return
Denote
where, for :
and, similarly, for :
Then, the modified scheme is -correct.
Appendix B. Transformation from IND-CPA PKE to Secure 2AKE
We reproduce here the result given in [9] about the IND-StAA security of the transformation. The following theorem states that the IND-StAA security of , where is a PKE scheme and are random oracles, reduces to the DS and IND-CPA security of . Note that some references to oracles appear in the statement; for details about these oracles and the formal definition of IND-StAA security, see [9].
Theorem A2
([9]). Assume PKE=(KG,Enc,Dec) to be -correct, and to come with a sampling algorithm such that it is ε-disjoint. Let N be the number of parties, and suppose that any attacker is granted access to an oracle REVEAL which reveals the respective session’s key (if already defined). Then, for any IND-StAA adversary that establishes S sessions and issues at most (classical) queries to REVEAL, at most (quantum) queries to random oracle G, and at most (quantum) queries to random oracle H, there exist adversaries and against PKE such that
and the running times of and is about that of . Here,
and
Appendix C. Transformation from IND-CPA PKE to IND-CCA KEM
We reproduce here the result given in [9] about the IND-CCA security of the transformation. The following theorem states that the IND-CCA security of , where is a PKE scheme and are random oracles, reduces to the DS and IND-CPA security of . Note that some references to oracles appear in the statement; for details about these oracles (see [9]).
Theorem A3
([9]). Assume PKE=(KG,Enc,Dec) to be -correct, and to come with a sampling algorithm such that it is -disjoint. Suppose that any attacker is granted access to an oracle DECAPS. Then, for any (quantum) IND-CCA adversary issuing at most (classical) queries to decapsulation oracle DECAPS, at most quantum queries to random oracle G, and at most quantum queries to random oracle H, there exist (quantum) adversaries and against PKE such that
and the running times of and is about that of .
References
- Fujioka, A.; Takashima, K.; Yoneyama, K. One-Round Authenticated Group Key Exchange from Isogenies. ProvSec. Lect. Notes Comput. Sci. 2019, 11821, 330–338. [Google Scholar]
- Apon, D.; Dachman-Soled, D.; Gong, H.; Katz, J. Constant-Round Group Key Exchange from the Ring-LWE Assumption. PQCrypto. Lect. Notes Comput. Sci. 2019, 11505, 189–205. [Google Scholar]
- Katz, J.; Yung, M. Scalable Protocols for Authenticated Group Key Exchange. In Advances in Cryptology— CRYPTO 2003, 23rd Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2003, Proceedings; Boneh, D., Ed.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2729, pp. 110–125. [Google Scholar] [CrossRef]
- Choi, R.; Hong, D.; Kim, K. Constant-round Dynamic Group Key Exchange from RLWE Assumption. IACR Cryptol. ePrint Arch. 2020, 2020, 35. [Google Scholar]
- Persichetti, E.; Steinwandt, R.; Corona, A.S. From Key Encapsulation to Authenticated Group Key Establishment—A Compiler for Post-Quantum Primitives †. Entropy 2019, 21, 1183. [Google Scholar] [CrossRef]
- González Vasco, M.; Pérez del Pozo, A.; Steinwandt, R. Group Key Establishment in a Quantum-Future Scenario. Informatica 2020, 1–18. [Google Scholar] [CrossRef]
- Bos, J.W.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS—Kyber: A CCA-Secure Module-Lattice-Based KEM. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 353–367. [Google Scholar]
- Abdalla, M.; Bohli, J.; Vasco, M.I.G.; Steinwandt, R. (Password) Authenticated Key Establishment: From 2-Party to Group. TCC. Lect. Notes Comput. Sci. 2007, 4392, 499–514. [Google Scholar]
- Hövelmanns, K.; Kiltz, E.; Schäge, S.; Unruh, D. Generic Authenticated Key Exchange in the Quantum Random Oracle Model. In Public-Key Cryptography—PKC 2020; Kiayias, A., Kohlweiss, M., Wallden, P., Zikas, V., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 389–422. [Google Scholar]
- Cramer, R.; Shoup, V. Design and Analysis of Practical Public-Key Encryption Schemes Secure against Adaptive Chosen Ciphertext Attack. SIAM J. Comput. 2003, 33, 167–226. [Google Scholar] [CrossRef]
- David Jao, E.A. Supersingular Lsogeny Key Encapsulation. Submission to NIST Post-Quantum Project. 2017. Available online: https://sike.org/#nist-submission (accessed on 16 October 2020).
- Chailloux, A.; Naya-Plasencia, M.; Schrottenloher, A. An Efficient Quantum Collision Search Algorithm and Implications on Symmetric Cryptography. In Advances in Cryptology—ASIACRYPT 2017—23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, 3–7 December 2017; Takagi, T., Peyrin, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2017; Volume 10625, pp. 211–240. [Google Scholar] [CrossRef]
- Zhandry, M. Secure Identity-Based Encryption in the Quantum Random Oracle Model. In Advances in Cryptology—CRYPTO 2012—32nd Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; Safavi-Naini, R., Canetti, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7417, pp. 758–775. [Google Scholar] [CrossRef]
- Boneh, D.; Dagdelen, Ö.; Fischlin, M.; Lehmann, A.; Schaffner, C.; Zhandry, M. Random Oracles in a Quantum World. In Advances in Cryptology—ASIACRYPT 2011—17th International Conference on the Theory and Application of Cryptology and Information Security, Seoul, Korea, 4–8 December 2011; Lee, D.H., Wang, X., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; Volume 7073, pp. 41–69. [Google Scholar] [CrossRef]
- Hövelmanns, K.; Kiltz, E.; Schäge, S.; Unruh, D. Generic Authenticated Key Exchange in the Quantum Random Oracle Model. IACR Cryptol. ePrint Arch. 2018, 2018, 928. [Google Scholar]
- Bellare, M.; Pointcheval, D.; Rogaway, P. Authenticated Key Exchange Secure against Dictionary Attacks. In Advances in Cryptology—EUROCRYPT 2000, International Conference on the Theory and Application of Cryptographic Techniques, Bruges, Belgium, 14–18 May 2000; Preneel, B., Ed.; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1807, pp. 139–155. [Google Scholar] [CrossRef]
- Bohli, J.; Vasco, M.I.G.; Steinwandt, R. Secure group key establishment revisited. Int. J. Inf. Sec. 2007, 6, 243–254. [Google Scholar] [CrossRef]
- Nam, J.; Paik, J.; Won, D. A security weakness in Abdalla et al.’s generic construction of a group key exchange protocol. Inf. Sci. 2011, 181, 234–238. [Google Scholar] [CrossRef]
- Hofheinz, D.; Hövelmanns, K.; Kiltz, E. A Modular Analysis of the Fujisaki-Okamoto Transformation. TCC (1). Lect. Notes Comput. Sci. 2017, 10677, 341–371. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).