In this section, we mainly analyze the security and performance evaluation of this protocol. In the above definition 1, PSI protocol satisfies the following three security properties:
1. Correctness: After executing the protocol, the client should obtain the correct set intersection ().
2. SP Privacy: The client learns no information about SP’s set except .
3. Client Privacy: SP cannot obtain any private information about the client’s set.
Next, we specifically analyze three properties of this protocol.
5.1. Correctness
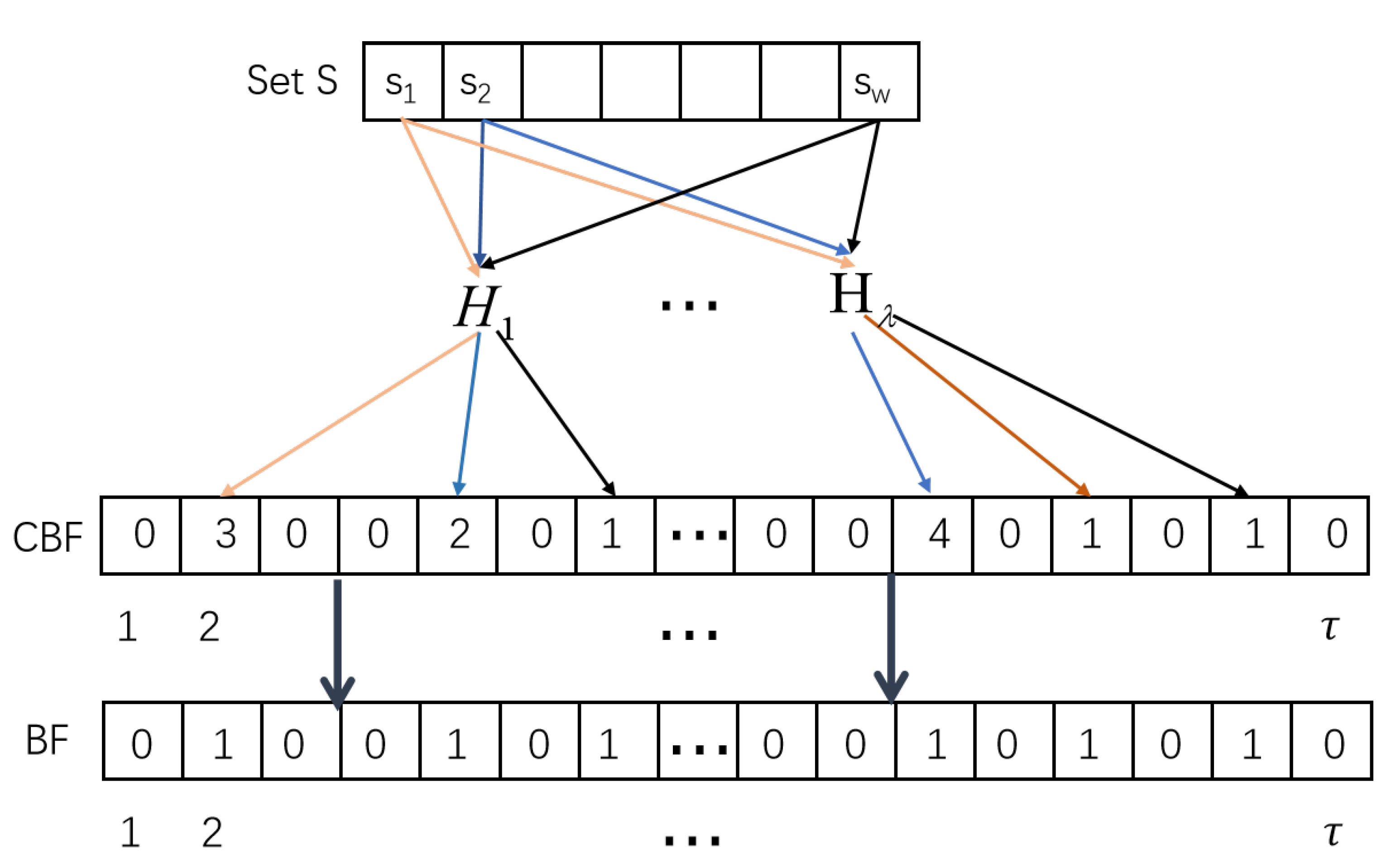
As we know, the client has a private set and SP has a private set , where . All elements of sets, i.e., C and S, lie in , where .
Furthermore, SP and the client have same count Bloom filter parameters: hash functions
and the size
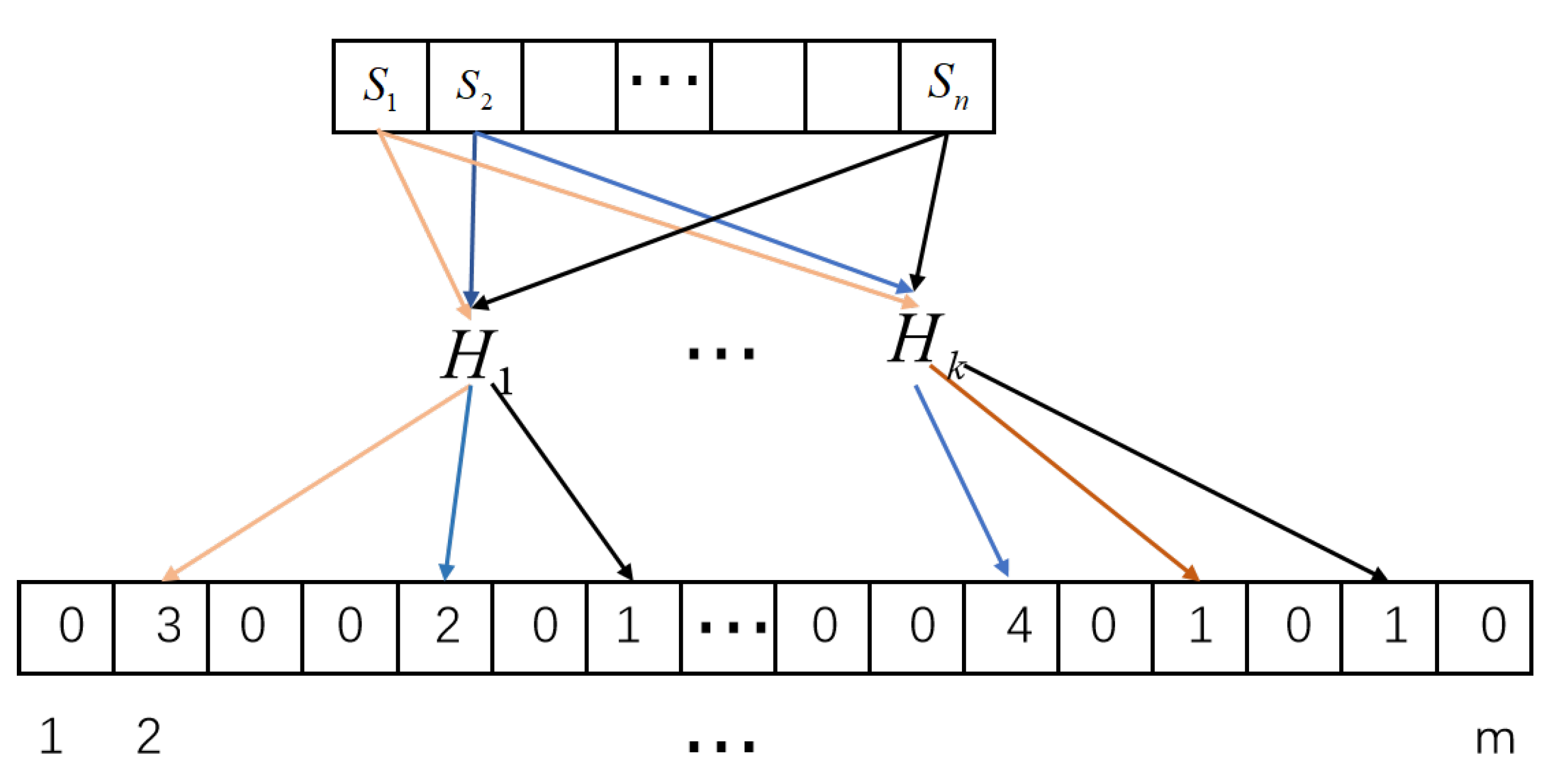
of the count Bloom filter. Then, SP has position indexes
of non-zero items in
. The client also has position indexes
of non-zero items in the count Bloom filter
. Then, we will obtain
Therefore, the set of all parameters i satisfying condition is equal to the intersection of their respective private sets, i.e., . Thus, the proposed protocol is correct.
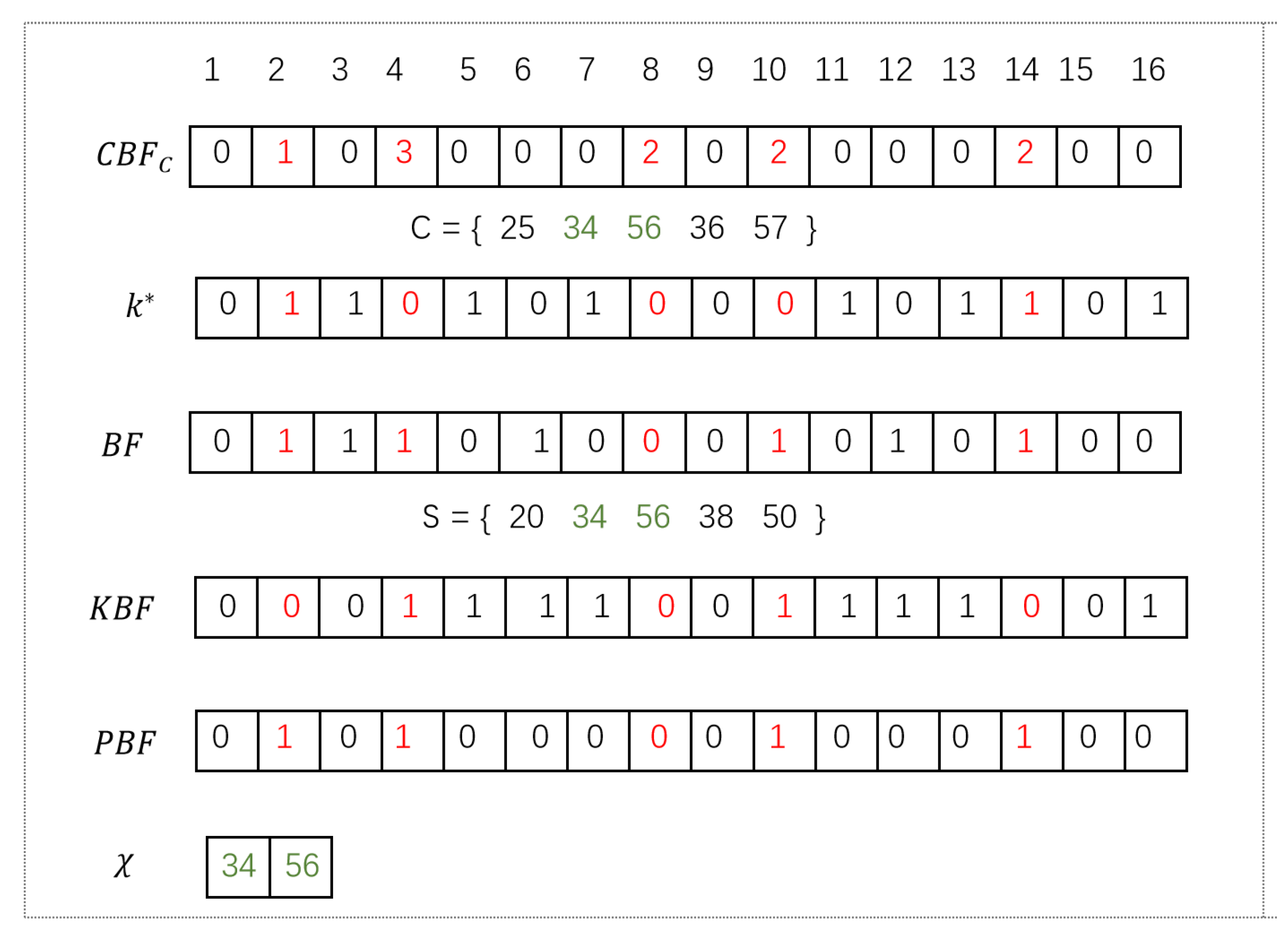
Furthermore, we give an example to clearly illustrate correctness of the protocol from
Figure 6. In this example, the client has a private set
and SP has a private set
, where all elements of sets
C and
S lie in
.
Two parties have the same count Bloom filter parameters: hash functions and the length of the count Bloom filter . First, SP and the client successfully construct their own count Bloom filters, i.e., and . In addition, SP extends count Bloom filter to obtain an array . Then, SP has position indexes of non-zero items in . The client also has position indexes of non-zero items in the count Bloom filter .
In addition, the quantum sequence has no influence on the correctness of the protocol. Therefore, we do not consider the quantum sequence in the following example.
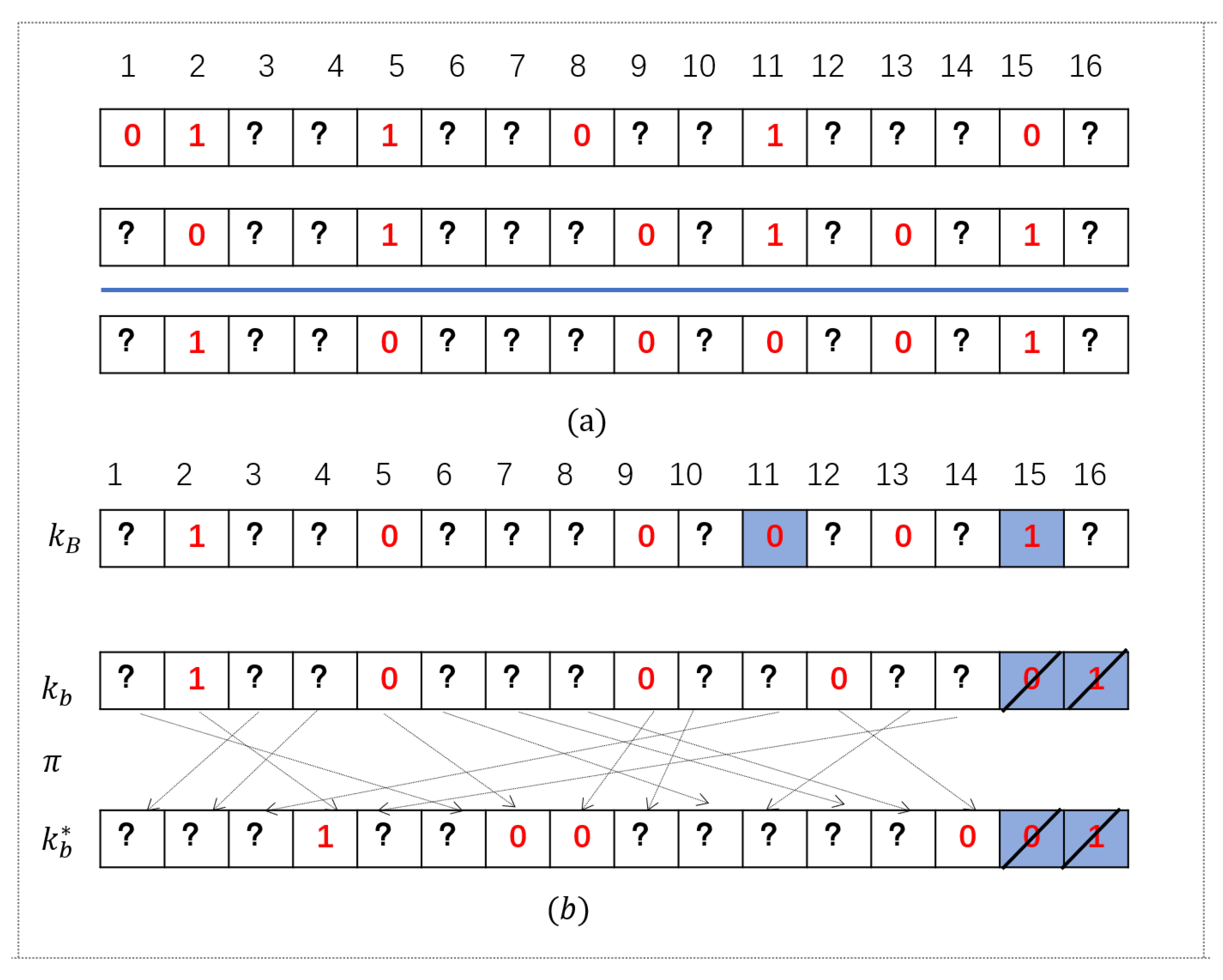
After the key generation phase, SP secretly obtains the final key , where the client obtains values of position indexes of red digits in the key . Obviously, and if . If , and , because and . Therefore, , if . Please look at those positions in , where the number color is red and the number is 1. After encryption and decryption, these positions are still representations of set intersection in the array , i.e., , if and . Furthermore, is an encrypted array of by the key , where SP knows all elements. This array is an array that partially decrypts with the key , where the client only knows part of the elements. In our example, , if . Then, the client uses the array to obtain the set intersection , i.e., , by Algorithm 4.
5.2. Security
The protocol consists of three main parts, i.e., key generation phase, encryption phase and decryption phase. The security analysis of the protocol will be orderly presented.
5.2.1. SP privacy
During key generation, the security of Step 1 is guaranteed by Xiao et al.’s OQKD protocol [
29]. By the analysis of reference [
29], a dishonest client will not receive more bits than expected, i.e.,
-bit, even with more efficient measures, such as the optimal unambiguous state discrimination (USD) measurement.
During the encryption phase, SP firstly maps a private set to an array through hash functions that the client also knows. Then, SP changes to obtain an array . That is, if a dishonest client obtains , she may obtain SP’s private set . However, SP encrypts by the key , where SP knows all the bits of the key, while the client only knows the partial bits. The security of has information-theoretic security because SP uses one-time pad encryption. During the decryption phase, the client can just decrypt the encrypted array to obtain partial values of by , where she only knows m-bit of the key. That is to say, the client cannot have more information about SP’s private set S.
In a word, the protocol can protect the privacy information of SP.
5.2.2. Client Privacy
Specifically, if a dishonest SP wants to eavesdrop on the client’s private key during the key generation phase, the probability that his dishonesty will be detected by his client is at least , where q is a secure parameter.
The security in Step 1 of key generation is guaranteed by Xiao et al.’s OQKD protocol [
29]. Based on reference [
29], a dishonest SP will introduce bit errors. That is, if SP obtains a message on the conclusiveness of the client’s bits, he will lose information on the bit values that the client has recorded. Actually, it is impossible for SP to have both correct bit value and conclusiveness message of the client’s measurement, i.e., position index of the correct basis. Therefore, SP cannot simultaneously obtain a bit value
that is a correct result deciphered by the client and its corresponding index
j.
In Step 2 of key generation, the client randomly compares q bits of the key with corresponding bits announced by SP to decide whether SP is dishonest. SP cannot know which bits will be taken as the checked bits before the client declares them.
Moreover, for each checked bit, if SP does not honestly execute the protocol, he will receive an error probability of in the honesty test. Therefore, for a dishonest SP, the successful probability of completely passing the honest test is less than .
Finally, in Step 4 of key generation, the client declares the permutation
to SP, which is defined by two sets
and
. Next, the condition probability
will be analyzed. Although the permutation
is randomly selected by the client, it still must satisfy Equation (
1). That is, the client announces a random permutation
with m fixed points, where fixed points are private, but the permutations are public. Accordingly, the number of permutations satisfies the condition
.
For simplicity, suppose that
denotes two arrays
and
.
and
denote the conditional probability and mutual information, respectively. Then, we deduce following results:
The probability of successfully guessing values of two arrays and through the public permutation is negligible, i.e., .
As we know that , so . In other words, the probability of successfully guessing these sets and with the public permutation is equal to the probability of directly guessing values of set without . In addition, the set is the client’s private message. Therefore, it is difficult for the SP to obtain the private set even if the client declares the permutation .
In a word, the honest test (i.e., q checked bits) ensures the honesty of SP during the key generation phase. The probability of successfully guessing the private sets by the public permutation is negligible, i.e., .
Furthermore, the client does not send any information during encryption and decryption phases, so private information is not leaked. Therefore, the protocol can protect the client’s private information.
5.3. External Security Analysis and Anonymity Analysis
In this protocol, we not only consider the three basic properties above but also consider external adversary security analysis and anonymity analysis.
5.3.1. External Security Analysis
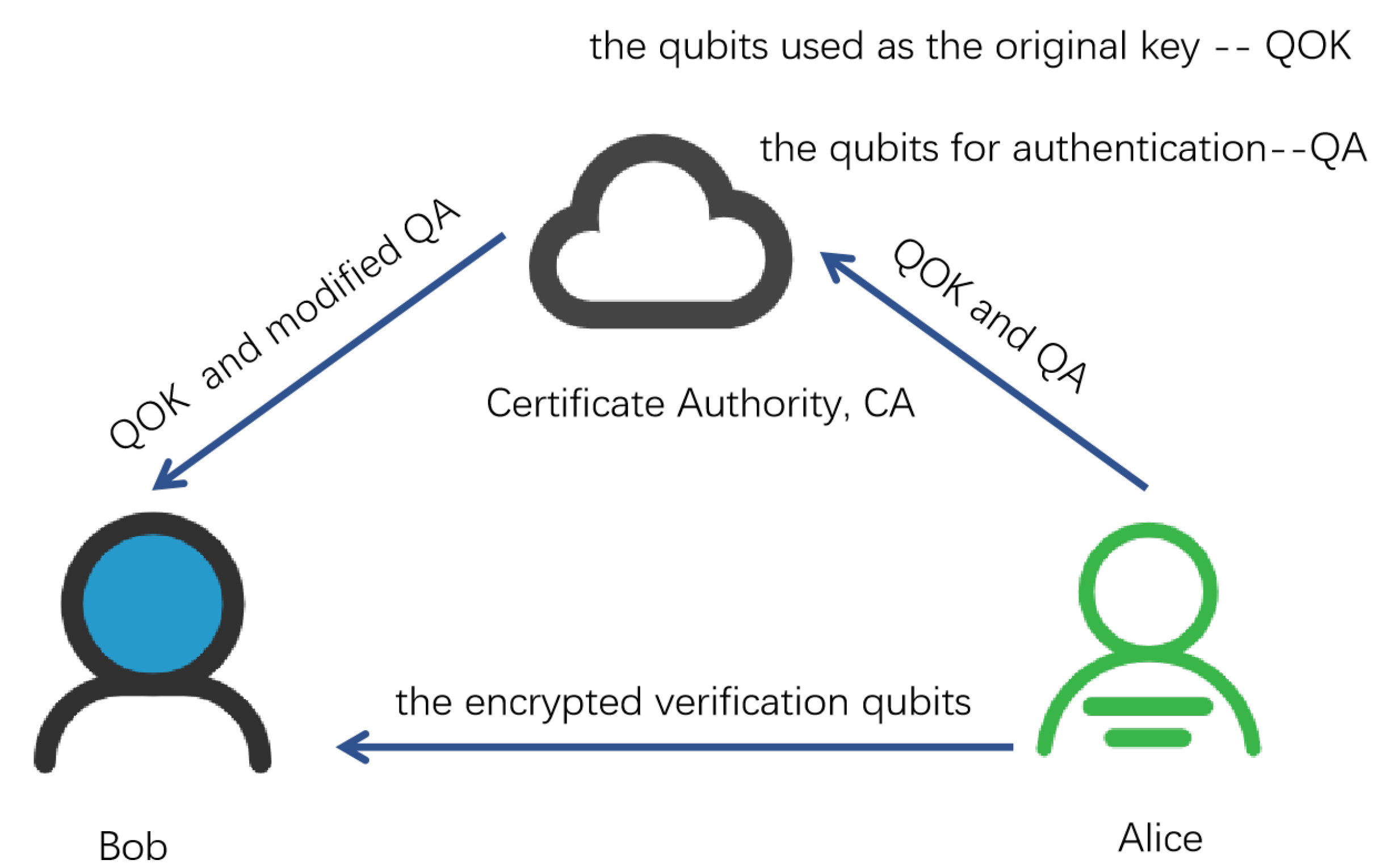
During the key generation phase, the external security of Step 1 is guaranteed by Xiao et al.’s OQKD protocol [
29]. Their protocol is resistant to external attacks, such as impersonation and man-in-the-middle attacks, through quantum bits for authentication (QA). Thus, our protocol can resist external attacks in the key generation phase.
Furthermore, they also use quantum bits to generate a key K, which is shared by SP and the client.
In the Step 7 of the encryption phase, even if a malicious adversary impersonates the client, she cannot obtain SP’s private set by the encrypted quantum sequence . First, the quantum sequence is obtained by encrypting the array with the key K. The adversary cannot obtain values of K, which is only known by the client and SP. Secondly, the adversary also cannot know the values of the array , where the security is information-theoretic security. Therefore, even if the adversary pretends to be the client to obtain the quantum sequence , he cannot obtain SP’s private information.
Furthermore, a malicious adversary may apply man-in-the-middle attack in Step 7 of encryption and Step 9 of decryption phases. She first intercepts the quantum sequence sent by SP and then sends fake information to the client so that the client decrypts fake information. However, the client verifies the correctness of the transmitted information. Once any bit is wrong, the client will think there is an external adversary or SP is dishonest. The adversary cannot obtain values of the key K, so fake information cannot pass verification. Therefore, in the encryption and decryption phases, our protocol can resist impersonation and man-in-the-middle attacks.
In a word, the protocol can resist external attacks, such as impersonation and man-in-the-middle attacks.
5.3.2. Anonymity Analysis
In the key generation phase, the anonymity analysis of Step 1 is guaranteed by Xiao et al.’s OQKD protocol [
29]. They send quantum sequences through CA.
During the encryption phase, SP only sends quantum sequences to clients that SP already knows in step 1 of the key generation phase. However, in decryption phase, the client cannot directly determine whether the quantum sequence is sent from the actual SP, even if quantum information indeed comes from SP. Because the client cannot determine the source of the quantum sequence. Therefore, the protocol provides an authentication function. That is, if the quantum sequence passes authentication, the sequence is indeed sent by SP. After the quantum sequence are authenticated, the client can obtain the actual encrypted array from SP.
Therefore, the protocol can guarantee the anonymity of the communicating parties.
5.4. Performance
In the key generation of the protocol, it uses single photons as quantum resources. There are no complicated quantum operators except projective measurements of single photons and simple single-bit operators. In encryption and decryption, the protocol only uses simple single-bit operators and projective measurements of single photons; thus, it is easy to implement this protocol in a real-life setting.
Next, we will consider the role of protocol in updatable databases. In encryption and decryption, counting Bloom filters are employed to reduce communication overhead and accommodate dynamic databases. Counting Bloom filters are employed to handle the updated data from Algorithms 2 and 3. With the increase in data, we only need to change corresponding values in the count Bloom filter according to updatable values, instead of creating a completely new Bloom filter at each modification. At the same time, the size of the count Bloom filter will not be changed when updating the database on a small scale. Instead, the protocol only increases the size of the counting Bloom filter to reduce the false rate after that data increases to a certain threshold.
With the size of the count Bloom filter remaining the same, if the client needs more key bits due to the increase in data, the client only needs to request insufficient key bits from SP, not all bits of the key. For example, the client and SP had the key of the length, where the client only knew k-bit values of the key, while SP knew all bits of the key. Now, the client has the size of position indexes of non-zero items in the count Bloom filter. Then, the client only needs to obtain a new key of the length from SP, where the client only knows ()-bit. Later, the client combines the key and to form a new key of length after applying the permutation , where the client knows l-bit of . The effect of is similar to the effect of . Then, the client announces the permutation to SP. In this way, we can reduce the communication overhead of keys and the cost of preparing them. Of course, we consider the semi-honesty model, where the client should not deceive SP. Thus, the protocol can significantly reduce computation and storage overhead.
From
Table 5, we can see a comparative summary of existing quantum private set intersection (QPSI) protocols. The communication complexity of our protocol is
-qubit. The transmitted qubits of the OQKD protocol [
29] in key generation are
qubits, where
z is the number of the qubits for authentication,
is a security parameter and
. Then, in the encryption phase, SP only transmits
-qubit to the client. Therefore, the communication complexity (qubit) of our protocol depends on the communication complexity (qubit) of OQKD protocol, i.e.,
, because
in
. The client needs a single-photon measurements of the
-qubit in the key generation phase. CA only needs to change the quantum state of the
z-bit in the key generation. Therefore, the computation complexity of the key is
. SP needs to generate
-qubit while performing quantum transformations on them in the encryption phase. The client needs single-photon measurements of
-qubit in the decryption phase. Therefore, the computation complexity of transmitted messages is
. The computation complexity of this protocol is
.
Similarly, we analyze that the communication complexity of the protocol [
24] should be
-qubit (
), because the OQKD protocol [
23] that they cite needs to transmit
-qubit, where a security parameter is
. The communication complexity of the protocol [
22] should be
-qubit (
) because the OQKD protocol [
23] that they cite needs to transmit
-qubit, where a security parameter is
.
In addition, our protocol only needs single photons, which are easier to achieve in a real-life setting. We also have a linear communication performance , where and in large-scale data. We need only one round of communication during the data transfer phase, i.e., .