Data-Driven Learning Models for Internet of Things Security: Emerging Trends, Applications, Challenges and Future Directions
Abstract
1. Introduction
2. Overview of IoT Network Security
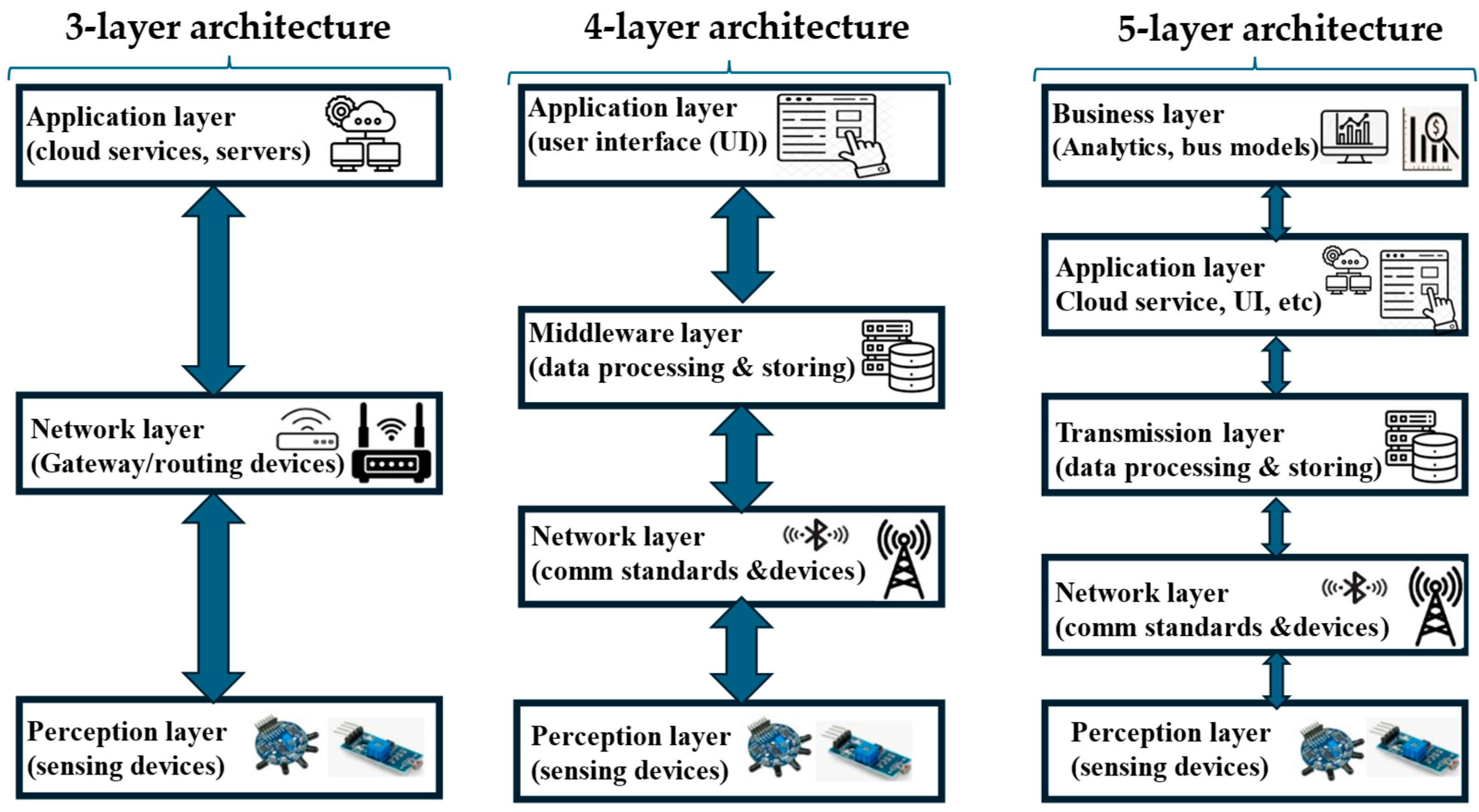
2.1. IoT Network Architectural Set-Up
- Three-layer architecture
- 2.
- Four-layer architecture
- 3.
- Similar to the three-layer architecture, the base of the four-layer architecture is the perception/sensing layer, which includes devices such as sensors that collect data from their surroundings. The next layer is the network layer, whereby data from the sensing layer are transported, typically to the internet, via the gateway devices. The service/middleware layer handles data analysis and processing. Depending on the application, the service layer is either located in the gateway or in the cloud. Similar to the three-layer architecture, the users interact with the applications and services at the application layer [36].
- 4.
- Five-layer architecture
2.2. IoT Network Popular Attacks
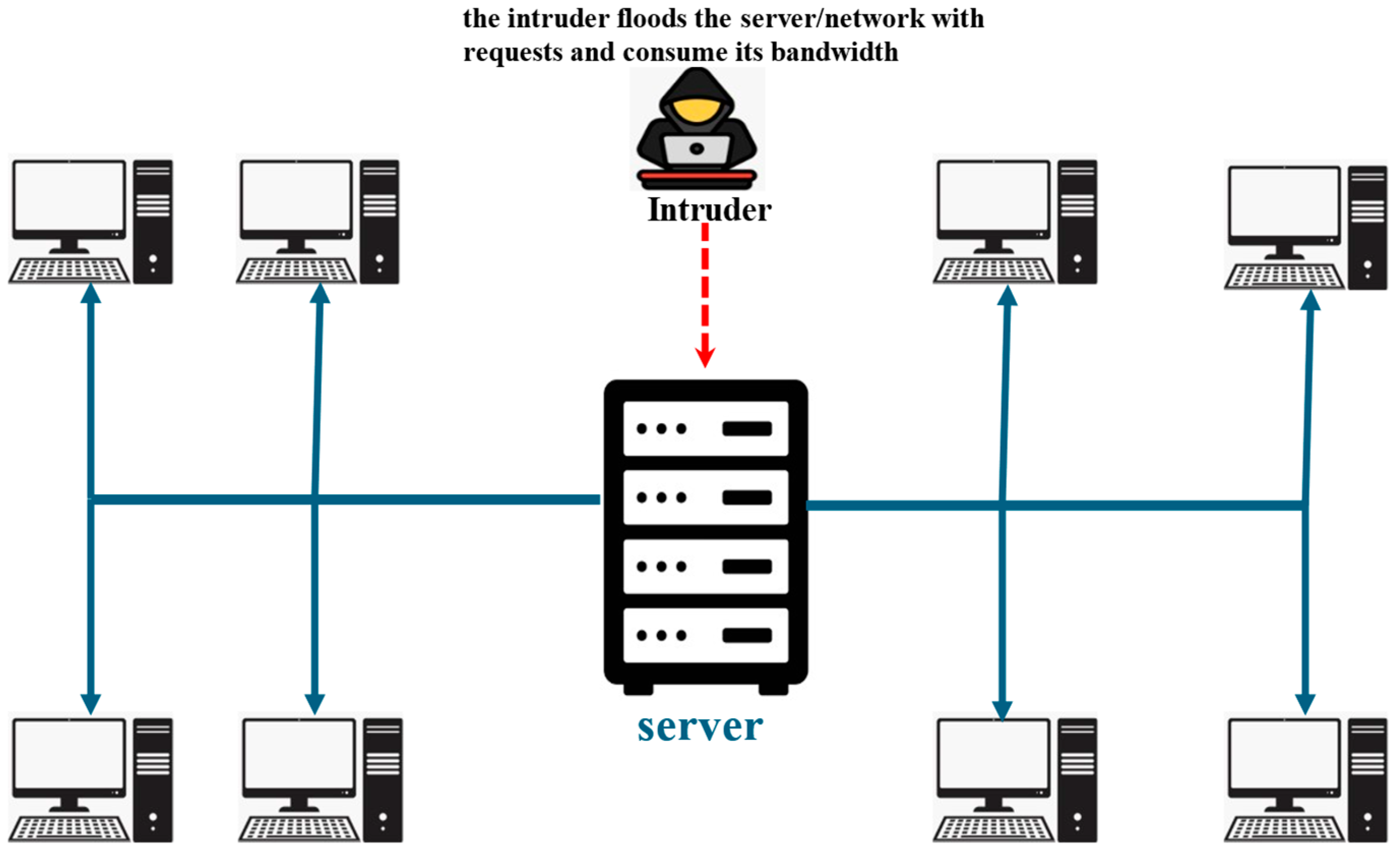
- Denial of Service (DoS)/Distributed Denial of Service (DDoS) Attacks
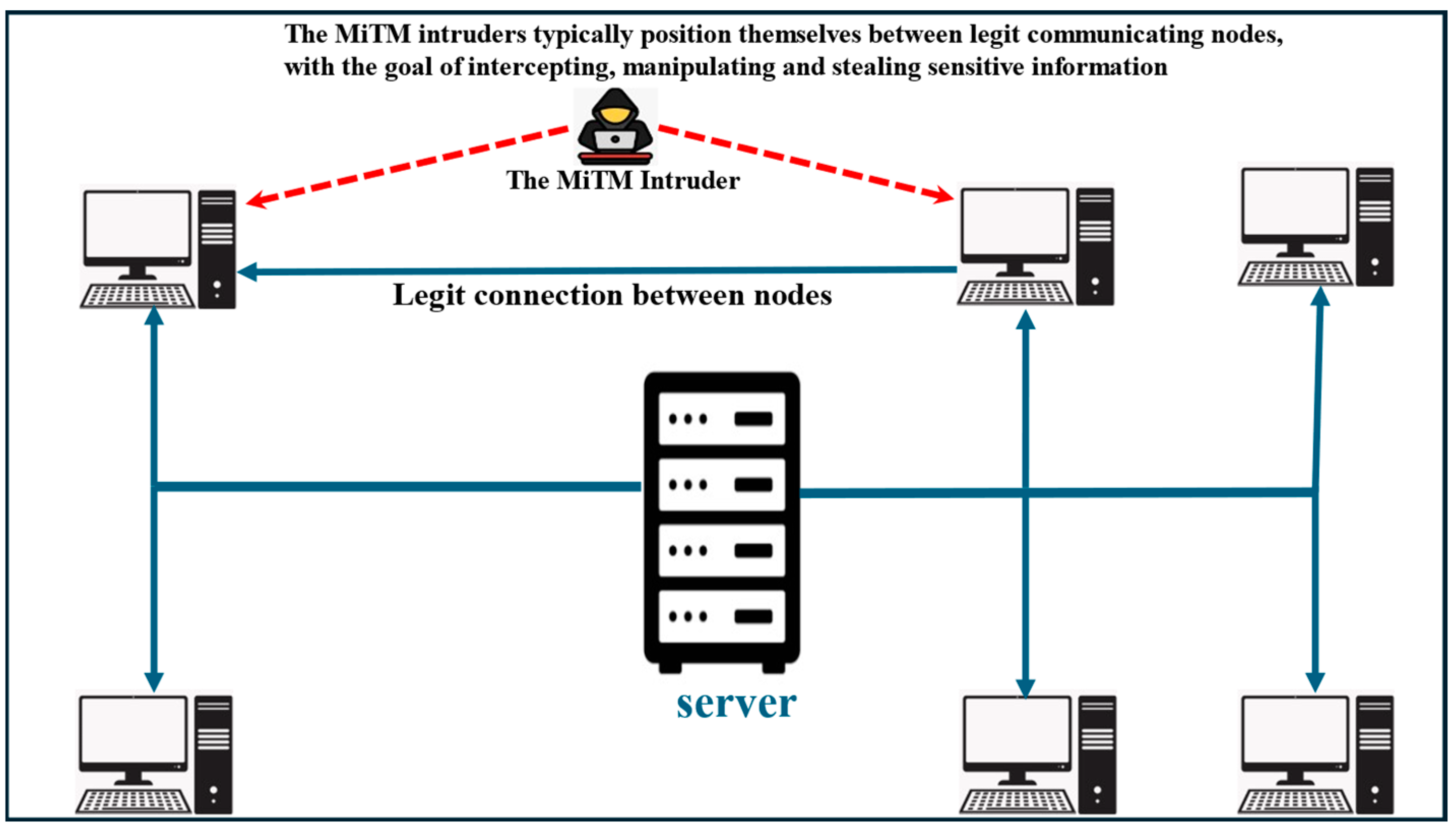
- Man-in-the-middle (MiTM) attacks
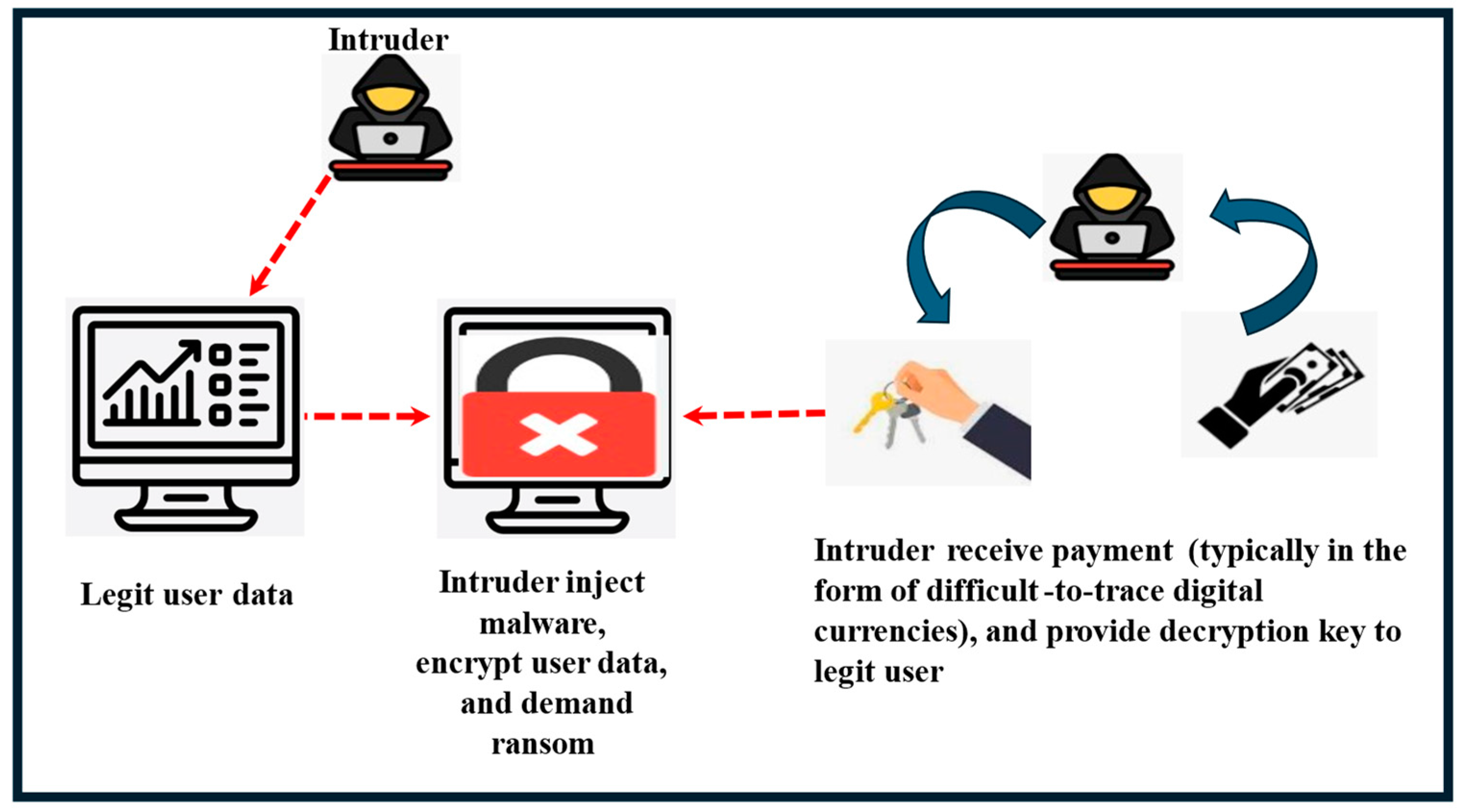
- Ransomware
- Physical Damage
- Replay Attack
3. IoT Network Security and Privacy Solutions
4. Performance Evaluation and Comparative Analysis of Data-Driven AI Models for IoT Network Security and Privacy Menaces
4.1. IoT Network Data Generation and Pre-Processing Phase
- IoT-23 Dataset
- TON_IoT Dataset
- Bot-IoT Dataset
- IoTID20 Dataset
4.2. IoT Network Data Analysis/ Classification Phase
5. Research Gaps and Future Directions
- The performance of the learning model(s) heavily depends on the heterogeneity and qualitative and quantitative properties of the dataset and test systems deployed. The heterogeneous, dynamic, and diverse nature of typical real-life IoT networks basically demands that the security analysis in this regard deploy typical IoT network setups that mimic real-life scenarios. However, due to the non-availability and inadequacy of data from real IoT networks, researchers have consistently turned to the use of simulated datasets, often outdated open-source datasets and/or scalable testbed developments, which often lack the characteristics of emerging real-life IoT networks. Thus, they have often shown inconsistency in the data-driven models’ learning processes.
- The majority of these benchmark datasets have class imbalance and noisy and missing data issues, which can negatively impact the performances of the learning models. These issues typically arise from the data generation phase, as IoT end devices can often produce noisy, incomplete, or inconsistent data. For example, a location determination technology such as sensor readings may be inconsistent due to environmental factors or technical issues, leading to erroneous data.
- Apart from the number of input dataset(s), another important factor is the pre-processing steps. Various studies have explored varieties of models and algorithms to pre-process the data with the sole aim of achieving better performance(s) from the learning model. While these methods have been quite effective, most often, the proposed models tend to be rigorous, leading to high computational complexity of the entire process. Thus, there is a need for effective yet scalable solutions. Additionally, the tuning of the parameters involved in achieving desired results often requires expertise and makes the process time-consuming.
- The black-box nature of emerging learning models, particularly deep learning models, whereby their decision-making process is not easily interpretable and transparent for general users. In a security context, it is crucial to understand why a model classifies something as an attack or normal behavior, as this can help security experts diagnose and respond to threats more effectively. Future research can also explore federated learning, whereby the training of a model is distributed across many decentralized devices or servers rather than relying on a centralized server to gather and store all the data. It allows multiple devices or clients to collaboratively train a shared model while keeping the data on local devices (such as smartphones, edge devices, or IoT devices), thereby preserving privacy and reducing the need for data transfer.
6. Conclusions
Funding
Conflicts of Interest
References
- Alzubi, O.A.; Alzubi, J.A.; Qiqieh, I.; Al-Zoubi, A.M. An IoT Intrusion Detection Approach Based on Salp Swarm and Artificial Neural Network. Int. J. Netw. Manag. 2025, 35, e2296. [Google Scholar] [CrossRef]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Tu, T.F.; Qin, J.W.; Zhang, H.; Chen, M.; Xu, T.; Huang, Y. A comprehensive study of Mozi botnet. Int. J. Intell. Syst. 2022, 37, 6877–6908. [Google Scholar] [CrossRef]
- Alimi, O.A. Hybrid Data-Driven Learning-Based Internet of Things Network Intrusion Detection Model. In Proceedings of the 2024 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 29–31 May 2024; pp. 496–501. [Google Scholar]
- Duguma, A.L.; Bai, X. How the internet of things technology improves agricultural efficiency. Artif. Intell. Rev. 2024, 58, 1–26. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M. A review of machine learning approaches to power system security and stability. IEEE Access 2020, 8, 113512–113531. [Google Scholar] [CrossRef]
- Margolis, J.; Oh, T.T.; Jadhav, S.; Kim, Y.H.; Kim, J.N. An in-depth analysis of the mirai botnet. In Proceedings of the International Conference on Software Security and Assurance (ICSSA), Altoona, PA, USA, 24–25 July 2017; pp. 6–12. [Google Scholar]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, K.O.A. Supervised learning based intrusion detection for SCADA systems. In Proceedings of the 4th International Conference on Disruptive Technologies for Sustainable Development (NIGERCON), Abuja, Nigeria, 5–7 April 2022; pp. 1–5. [Google Scholar]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, K.O.A. Intrusion Detection for Water Distribution Systems based on an Hybrid Particle Swarm Optimization with Back Propagation Neural Network. In Proceedings of the 2021 IEEE AFRICON, Virtual, 13–15 September 2021; pp. 1–5. [Google Scholar]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S.; Alimi, K.O.A. A review of research works on supervised learning algorithms for scada intrusion detection and classification. Sustainability 2021, 13, 9597. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Rimer, S. Power system events classification using genetic algorithm based feature weighting technique for support vector machine. Heliyon 2021, 7, e05936. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M.; Alimi, K.O.A. Empirical comparison of machine learning algorithms for mitigating power systems intrusion attacks. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020; pp. 1–5. [Google Scholar]
- Ahmid, M.; Kazar, O. A Comprehensive Review of the Internet of Things Security. J. Appl. Secur. Res. 2023, 18, 289–305. [Google Scholar] [CrossRef]
- Randolph, K.; Hunt, M. Verkada: March 9, 2021 Security Incident Report. Available online: https://docs.verkada.com/docs/Security_Incident_Report_Version1.2.pdf (accessed on 24 April 2025).
- Resul, D.; Gündüz, M.Z. Analysis of cyber-attacks in IoT-based critical infrastructures. Int. J. Inf. Secur. Sci. 2019, 8, 122–133. [Google Scholar]
- FDA In Brief: FDA Warns Patients, Providers about Cybersecurity Concerns with Certain Medtronic Implantable Cardiac Devices Food and Drug Administration. 2018. Available online: https://www.fda.gov/news-events/fda-brief/fda-brief-fda-warns-patients-providers-about-cybersecurity-concerns-certain-medtronic-implantable (accessed on 7 March 2025).
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Ahmad, I.; Niazy, M.S.; Ziar, R.A.; Khan, S. Survey on IoT: Security threats and applications. J. Robot. Control. (JRC) 2021, 2, 42–46. [Google Scholar] [CrossRef]
- Hwang, Y.H. IoT security & privacy: Threats and challenges. In Proceedings of the 1st ACM Workshop on IoT Privacy, Trust, and Security, Singapore, 14 April–14 March 2015; p. 1. [Google Scholar]
- Schiller, E.; Aidoo, A.; Fuhrer, J.; Stahl, J.; Ziörjen, M.; Stiller, B. Landscape of IoT security. Comput. Sci. Rev. 2022, 44, 100467. [Google Scholar] [CrossRef]
- Kamalov, F.; Pourghebleh, B.; Gheisari, M.; Liu, Y.; Moussa, S. Internet of medical things privacy and security: Challenges, solutions, and future trends from a new perspective. Sustainability 2023, 15, 3317. [Google Scholar] [CrossRef]
- WEF, The Global Risks Report 2019. Available online: https://www.weforum.org/publications/the-global-risks-report-2019/ (accessed on 6 March 2025).
- Mckinsey and Company. What is Cybersecurity? Available online: https://www.mckinsey.com/featured-insights/mckinsey-explainers/what-is-cybersecurity (accessed on 6 March 2025).
- Zoting, S.; Shivarkar, A. IoT Security Market Size, Share, And Trends 2025 to 2034. Available online: https://www.precedenceresearch.com/iot-security-market (accessed on 6 March 2025).
- Khan, A.R.; Kashif, M.; Jhaveri, R.H.; Raut, R.; Saba, T.; Bahaj, S.A. Deep learning for intrusion detection and security of Internet of things (IoT): Current analysis, challenges, and possible solutions. Secur. Commun. Netw. 2022, 2022, 4016073. [Google Scholar] [CrossRef]
- David, R.; John, G.; John, R. Data Age 2025: The Evolution of Data To Life-Critical Don’t Focus On Big Data; Focus On The Data That’s Big, Age, D. 2025. The Evolution of Data to Life-Critical. Don’t Focus on Big Data; Focus on the Data That’s Big. Available online: https://www.seagate.com/files/www-content/our-story/trends/files/Seagate-WP-DataAge2025-March-2017.pdf (accessed on 6 March 2025).
- HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Aledhari, M.; Karimipour, H. A survey on internet of things security: Requirements, challenges, and solutions. Internet Things 2019, 14, 100129. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Sahri, N.M.; Karie, N.M.; Ahmed, M.; Valli, C. Biometrics for internet-of-things security: A review. Sensors 2021, 21, 6163. [Google Scholar] [CrossRef]
- Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A. Internet of things: Security and solutions survey. Sensors 2022, 22, 7433. [Google Scholar] [CrossRef]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A systematic survey of industrial internet of things security: Requirements and fog computing opportunities. IEEE Commun. Surv. Tutorials 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an analysis of security issues, challenges, and open problems in the internet of things. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2025; pp. 21–28. [Google Scholar]
- Jamali, M.J.; Bahrami, B.; Heidari, A.; Allahverdizadeh, P.; Norouzi, F. Towards the Internet of Things: Architectures, Security, and Applications; Springer International Publishing: Cham, Switzerland, 2020. [Google Scholar]
- Giri, A.; Dutta, S.; Neogy, S.; Dahal, K.; Pervez, Z. Internet of Things (IoT) a survey on architecture, enabling technologies, applications and challenges. In Proceedings of the 1st International Conference on Internet of Things and Machine Learning, New York, NY, USA, 17–18 October 2017; pp. 1–12. [Google Scholar]
- Yıldırım, M.; Demiroğlu, U.; Şenol, B. An in-depth exam of IoT, IoT core components, IoT layers, and attack types. Avrupa Bilim Ve Teknol. Derg. 2021, 28, 665–669. [Google Scholar]
- Patnaik, R.; Padhy, N.; Raju, K.S. A systematic survey on IoT security issues, vulnerability and open challenges. In Proceedings of the Intelligent System Design: INDIA 2019; Springer: Singapore, 2020; pp. 723–730. [Google Scholar]
- Darwish, D. Improved layered architecture for Internet of Things. Intl. J. Comput. Acad. Res. (IJCAR) 2015, 4, 214–223. [Google Scholar]
- Kumar, N.M.; Mallick, P.K. The Internet of Things: Insights into the building blocks, component interactions, and architecture layers. Procedia Comput. Sci. 2018, 132, 109–117. [Google Scholar] [CrossRef]
- Zhong, C.; Zhu, Z.; Huang, R. Study on the IOT architecture and gateway technology. In Proceedings of the 14th International Symposium on Distributed Computing and Applications for Business Engineering and Science (DCABES), Guiyang, China, 18–24 August 2015; pp. 196–199. [Google Scholar]
- Antao, L.; Pinto, R.; Reis, J.; Gonçalves, G. Requirements for testing and validating the industrial internet of things. In Proceedings of the 2018 IEEE International Conference on Software Testing, Verification and Validation Workshops (ICSTW), Västerås, Sweden, 9–13 April 2018; pp. 110–115. [Google Scholar]
- Mishra, N.; Pandya, S. Internet of things applications, security challenges, attacks, intrusion detection, and future visions: A systematic review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- Liang, X.; Kim, Y. A survey on security attacks and solutions in the IoT network. In Proceedings of the 2021 IEEE 11th annual computing and communication workshop and conference (CCWC), Virtual, 27–30 January 2021; p. 853. [Google Scholar]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A Survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef] [PubMed]
- Liang, L.; Zheng, K.; Sheng, Q.; Huang, X. A denial of service attack method for an iot system. In Proceedings of the 8th international conference on Information Technology in Medicine and Education (ITME), Fuzhou, China, 23–25 December 2016; pp. 360–364. [Google Scholar]
- MIT Technology Review. The First DDoS Attack was 20 Years Ago. This is What we’ve Learned Since. Available online: https://www.technologyreview.com/2019/04/18/103186/the-first-ddos-attack-was-20-years-ago-this-is-what-weve-learned-since/ (accessed on 6 March 2025).
- Salim, M.M.; Rathore, S.; Park, J.H. Distributed denial of service attacks and its defenses in IoT: A survey. J. Supercomput. 2020, 76, 5320–5363. [Google Scholar] [CrossRef]
- Kupreev, O.; Gutnikov, A.; Shmelev, Y. DDoS Attacks in Q3 2022. Available online: https://stormwall.network/resources/blog/ddos-attacks-report-q3-2022?utm_source=google.com&utm_medium=organic&utm_campaign=google.com&utm_referrer=google.com (accessed on 6 March 2025).
- DoS Attack (Denial of Service). Available online: https://www.wallarm.com/what/dos-denial-of-service-attack (accessed on 6 March 2025).
- Bhushan, B.; Sahoo, G.; Rai, A.K. Man-in-the-middle attack in wireless and computer networking—A review. In Proceedings of the 3rd International Conference on Advances in Computing, Communication & Automation (ICACCA)(Fall), Dehradun, India, 15–16 September 2017; pp. 1–6. [Google Scholar]
- Mallik, A. MAN-in-the-middle-attack: Understanding in simple words. Cyberspace J. Pendidik. Teknol. Inf. 2019, 2, 109–134. [Google Scholar] [CrossRef]
- Salem, O.; Alsubhi, K.; Shaafi, A.; Gheryani, M.; Mehaoua, A.; Boutaba, R. Man-in-the-middle attack mitigation in internet of medical things. IEEE Trans. Ind. Informatics 2021, 18, 2053–2062. [Google Scholar] [CrossRef]
- Palatty, N.J. How Many Cyber Attacks Per Day: The Latest Stats and Impacts in 2024. Available online: https://www.getastra.com/blog/security-audit/how-many-cyber-attacks-per-day/#:~:text=Man%2DIn%2DThe%2DMiddle,login%20credentials%20and%20banking%20information. (accessed on 6 March 2025).
- Humayun, M.; Jhanjhi, N.Z.; Alsayat, A.; Ponnusamy, V. Internet of things and ransomware: Evolution, mitigation and prevention. Egypt. Inform. J. 2021, 22, 105–117. [Google Scholar] [CrossRef]
- Zahra, S.R.; Chishti, M.A. Ransomware and internet of things: A new security nightmare. In Proceedings of the 9th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 10–11 January 2019; pp. 551–555. [Google Scholar]
- Molina, R.M.A.; Bou-Harb, E.; Torabi, S.; Assi, C. RPM: Ransomware Prevention and Mitigation Using Operating Systems’ Sensing Tactics. In Proceedings of the IEEE International Conference on Communications, Rome, Italy, 28 May–1 June 2023; pp. 1–6. [Google Scholar]
- Alelyani, S.; Kumar, G.R.H. Overview of cyberattack on saudi organizations. J. Inf. Secur. Cybercrimes Res. 2018, 1, 32–39. [Google Scholar] [CrossRef]
- Ransomware Trends Report. Available online: https://shorturl.at/AZtJ2 (accessed on 6 March 2025).
- Mahamat, M.; Jaber, G.; Bouabdallah, A. Achieving efficient energy-aware security in IoT networks: A survey of recent solutions and research challenges. Wirel. Netw. 2023, 29, 787–808. [Google Scholar] [CrossRef]
- Wei, L.; Rondon, L.P.; Moghadasi, A.; Sarwat, A.I. Review of cyber-physical attacks and counter defense mechanisms for advanced metering infrastructure in smart grid. Proceedings of IEEE/PES Transmission and Distribution Conference and Exposition (T&D), Chicago, IL, USA, 16 April 2018; pp. 1–9. [Google Scholar]
- Dzansi, D.Y.; Rambe, P.; Mathe, L. Cable Theft and vandalism by employees of South Africa’s electricity utility companies: A theoretical explanation and research agenda. J. Soc. Sci. 2014, 39, 179–190. [Google Scholar] [CrossRef]
- Degambur, L.-N. Replay Attack Prevention in Decentralised Contact Tracing: A Blockchain-Based Approach. Open Access Libr. J. 2024, 11, 1–17. [Google Scholar] [CrossRef]
- Gargoum, S. Data-Driven Detection and Verification of Replay Attacks on Industrial Control Systems. Ph.D. Dissertation, University of British Columbia, Vancouver, BC, Canada, 2023. [Google Scholar]
- Rekha, S.; Thirupathi, L.; Renikunta, S.; Gangula, R. Study of security issues and solutions in Internet of Things (IoT). Mater. Today Proc. 2023, 80, 3554–3559. [Google Scholar] [CrossRef]
- Doukas, C.; Maglogiannis, I.; Koufi, V.; Malamateniou, F.; Vassilacopoulos, G. Enabling data protection through PKI encryption in IoT m-Health devices. In Proceedings of the 12th International Conference on Bioinformatics & Bioengineering (BIBE), Larnaca, Cyprus Cyprus, 11–13 November 2012; pp. 25–29. [Google Scholar]
- Shahzad, K.; Zia, T.; Qazi, E.-U. A review of functional encryption in IoT applications. Sensors 2022, 22, 7567. [Google Scholar] [CrossRef]
- Chandu, Y.; Kumar, K.R.; Prabhukhanolkar, N.V.; Anish, A.N.; Rawal, S. Design and implementation of hybrid encryption for security of IOT data. In Proceedings of the International Conference on Smart Technologies for Smart Nation (SmartTechCon), Singapore, 17–19 August 2017; pp. 1228–1231. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the International Conference on Pervasive Computing and Communications Workshops (PerCom workshops), Washington DC, USA, 13–17 March 2017; pp. 618–623. [Google Scholar]
- Wang, Q.; Zhu, X.; Ni, Y.; Gu, L.; Zhu, H. Blockchain for the IoT and industrial IoT: A review. Internet Things 2020, 10, 100081. [Google Scholar] [CrossRef]
- Minoli, D.; Occhiogrosso, B. Blockchain mechanisms for IoT security. Internet Things 2018, 1, 1–13. [Google Scholar] [CrossRef]
- Bandara, E.; Tosh, D.; Foytik, P.; Shetty, S.; Ranasinghe, N.; De Zoysa, K. Tikiri—Towards a lightweight blockchain for IoT. Future Gener. Comput. Syst. 2021, 119, 154–165. [Google Scholar] [CrossRef]
- Naha, A.; Teixeira, A.M.H.; Ahlén, A.; Dey, S. Sequential detection of replay attacks. IEEE Trans. Autom. Control 2022, 68, 1941–1948. [Google Scholar] [CrossRef]
- Google Safety Centre. Background Check, A Behind-the-Scenes Look at How Google is Making the Internet More Secure. Available online: https://safety.google/stories/backend/. (accessed on 6 March 2025).
- Security-Reference-Architecture Amazon. Available online: https://docs.aws.amazon.com/prescriptive-guidance/latest/security-reference-architecture/welcome.html (accessed on 6 March 2025).
- Xiao, L.; Wan, X.; Lu, X.; Zhang, Y.; Wu, D. IoT security techniques based on machine learning: How do IoT devices use AI to enhance security? IEEE Signal Process. Mag. 2018, 35, 41–49. [Google Scholar] [CrossRef]
- Aldahiri, A.; Alrashed, B.; Hussain, W. Trends in using IoT with machine learning in health prediction system. Forecasting 2021, 3, 181–206. [Google Scholar] [CrossRef]
- Bhayo, J.; Shah, S.A.; Hameed, S.; Ahmed, A.; Nasir, J.; Draheim, D. Towards a machine learning-based framework for DDOS attack detection in software-defined IoT (SD-IoT) networks. Eng. Appl. Artif. Intell. 2023, 123, 106432. [Google Scholar] [CrossRef]
- Islam, N.; Farhin, F.; Sultana, I.; Kaiser, M.S.; Rahman, S.; Mahmud, M.; Hosen, A.S.M.S.; Cho, G.H. Towards Machine Learning Based Intrusion Detection in IoT Networks. Comput. Mater. Contin. 2021, 69, 1801–1821. [Google Scholar] [CrossRef]
- Parmisano, A.; Garcia, S.; Erquiaga, M.J. A Labeled Dataset with Malicious and Benign IoT Network Traffic; Stratosphere Laboratory: Praha, Czech Republic, 2020. [Google Scholar]
- Alfares, H.; Banimelhem, O. Comparative Analysis of Machine Learning Techniques for Handling Imbalance in IoT-23 Dataset for Intrusion Detection Systems. In Proceedings of the 11th International Conference on Internet of Things: Systems, Management and Security (IOTSMS), Malmö, Sweden, 2–5 September 2024; pp. 112–119. [Google Scholar]
- Abdalgawad, N.; Sajun, A.; Kaddoura, Y.; Zualkernan, I.A.; Aloul, F. Generative deep learning to detect cyberattacks for the IoT-23 dataset. IEEE Access 2021, 10, 6430–6441. [Google Scholar] [CrossRef]
- Nanthiya, D.; Keerthika, P.; Gopal, S.B.; Kayalvizhi, S.B.; Raja, T.; Priya, R.S. SVM based DDoS attack detection in IoT using Iot-23 botnet dataset. In Proceedings of the 2021 Innovations in Power and Advanced Computing Technologies (i-PACT), Kuala Lumpur, Malaysia, 27–29 November 2021; pp. 1–7. [Google Scholar]
- Jeelani, F.; Rai, D.S.; Maithani, A.; Gupta, S. The detection of IoT botnet using machine learning on IoT-23 dataset. Proceedings of the 2nd International Conference on Innovative Practices in Technology and Management (ICIPTM) Volume 2, 634–639.
- Dutta, V.; Choraś, M.; Pawlicki, M.; Kozik, R. Detection of Cyberattacks Traces in IoT Data. JUCS J. Univers. Comput. Sci. 2020, 26, 1422–1434. [Google Scholar] [CrossRef]
- Ahli, A.; Raza, A.; Akpinar, K.O.; Akpinar, M. Binary and Multi-Class Classification on the IoT-23 Dataset. In Proceedings of the 2023 Advances in Science and Engineering Technology International Conferences (ASET), Dubai, United Arab Emirates, 20–23 February 2023; pp. 1–7. [Google Scholar]
- Wongvorachan, T.; He, S.; Bulut, O. A comparison of undersampling, oversampling, and SMOTE methods for dealing with imbalanced classification in educational data mining. Information 2023, 14, 54. [Google Scholar] [CrossRef]
- Zeeshan, M.; Riaz, Q.; Bilal, M.A.; Shahzad, M.K.; Jabeen, H.; Haider, S.A.; Rahim, A. Protocol-Based deep intrusion detection for DoS and DDoS attacks using UNSW-NB15 and Bot-IoT data-sets. IEEE Access 2021, 10, 2269–2283. [Google Scholar] [CrossRef]
- Brandt, J.; Lanzén, E. A Comparative Review of SMOTE and ADASYN in Imbalanced Data Classification, Dissertation, Uppsala University. 2021. Available online: https://urn.kb.se/resolve?urn=urn:nbn:se:uu:diva-432162, (accessed on 24 April 2025).
- Pradipta, G.A.; Wardoyo, R.; Musdholifah, A.; Sanjaya, I.N.H.; Ismail, M. SMOTE for Handling Imbalanced Data Problem: A Review. In Proceedings of the 2021 Sixth International Conference on Informatics and Computing (ICIC), Virtual, 3–4 November 2021; pp. 1–8. [Google Scholar]
- He, H.; Bai, Y.; Garcia, E.A.; Li, S. ADASYN: Adaptive synthetic sampling approach for imbalanced learning. In Proceedings of the 2008 IEEE International Joint Conference on Neural Networks (IEEE World Congress on Computational Intelligence), Hong Kong, China, 1–8 June 2008; pp. 1322–1328. [Google Scholar]
- EL Hariri, A.; Mouiti, M.; Habibi, O.; Lazaar, M. Improving Deep Learning Performance Using Sampling Techniques for IoT Imbalanced Data. Procedia Comput. Sci. 2023, 224, 180–187. [Google Scholar] [CrossRef]
- Stoian, N. No title. Machine Learning for Anomaly Detection in IoT Networks: Malware Analysis on the IoT-23 Data Set. Bachelor’s Thesis, University of Twente, Enschede, The Netherlands, 2020. [Google Scholar]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Gallagher, M.; Portmann, M. Feature extraction for machine learning-based intrusion detection in IoT networks. Digit. Commun. Netw. 2024, 10, 205–216. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Portmann, M. Feature analysis for machine learning-based IoT intrusion detection. arXiv 2021, arXiv:2108.12732. [Google Scholar]
- Moustafa, N.; Ahmed, M.; Ahmed, S. Data analytics-enabled intrusion detection: Evaluations of ToN_IoT linux datasets. In Proceedings of the 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 727–735. [Google Scholar]
- Elsayed, R.A.; Hamada, R.A.; Abdalla, M.I.; Elsaid, S.A. Securing IoT and SDN systems using deep-learning based automatic intrusion detection. Ain Shams Eng. J. 2023, 14, 102211. [Google Scholar] [CrossRef]
- Guo, G. A machine learning framework for intrusion detection system in iot networks using an ensemble feature selection method. In Proceedings of the IEEE 12th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 27–30 October 2021; p. 593. [Google Scholar]
- Guo, G. An intrusion detection system for the internet of things using machine learning models. In Proceedings of the 3rd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE), Nanchang, China, 15–17 July 2022; pp. 332–335. [Google Scholar]
- Guo, G.; Pan, X.; Liu, H.; Li, F.; Pei, L.; Hu, K. An IoT intrusion detection system based on TON IoT network dataset. Proceedings of 13th Annual Computing and Communication Workshop and Conference (CCWC), Virtual, 8 March 2023; p. 333. [Google Scholar]
- Gad, A.R.; Nashat, A.A.; Barkat, T.M. Intrusion detection system using machine learning for vehicular Ad Hoc networks based on ToN-IoT dataset. IEEE Access 2021, 9, 142206–142217. [Google Scholar] [CrossRef]
- Cao, Z.; Zhao, Z.; Shang, W.; Ai, S.; Shen, S. Using the ToN-IoT dataset to develop a new intrusion detection system for industrial IoT devices. Multimedia Tools Appl. 2024, 83, 1–29. [Google Scholar] [CrossRef]
- Gad, A.R.; Haggag, M.; Nashat, A.A.; Barakat, T.M. A distributed intrusion detection system using machine learning for IoT based on ToN-IoT dataset. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 130667. [Google Scholar] [CrossRef]
- Shtayat, M.M.; Hasan, M.K.; Sulaiman, R.; Islam, S.; Khan, A.U.R. An explainable ensemble deep learning approach for intrusion detection in industrial internet of things. IEEE Access 2023, 11, 115047–115061. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E. A new network forensic framework based on deep learning for Internet of Things networks: A particle deep framework. Future Gener. Comput. Syst. 2020, 110, 91–106. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Slay, J. Towards developing network forensic mechanism for botnet activities in the IoT based on machine learning techniques. Mob. Netw. Manag. 2019, 100, 30–44. [Google Scholar]
- Shafiq, M.; Tian, Z.; Bashir, A.K.; Du, X.; Guizani, M. CorrAUC: A malicious Bot-IoT traffic detection method in IoT network using machine-learning techniques. IEEE Internet Things J. 2020, 8, 3242–3254. [Google Scholar] [CrossRef]
- Pokhrel, S.; Abbas, R.; Aryal, B. IoT security: Botnet detection in IoT using machine learning. arXiv 2021, arXiv:2104.02231. [Google Scholar]
- Shafiq, M.; Tian, Z.; Sun, Y.; Du, X.; Guizani, M. Selection of effective machine learning algorithm and Bot-IoT attacks traffic identification for internet of things in smart city. Future Gener. Comput. Syst. 2020, 107, 433–442. [Google Scholar] [CrossRef]
- Leevy, J.L.; Hancock, J.; Khoshgoftaar, T.M.; Peterson, J. Detecting information theft attacks in the bot-iot dataset. In Proceedings of the 20th IEEE International Conference on Machine Learning and Applications (ICMLA), Pasadena, CA, USA, 13–16 December 2021; pp. 807–812. [Google Scholar]
- Pavaiyarkarasi, R.; Manimegalai, T.; Satheeshkumar, S.; Dhivya, K.; Ramkumar, G. A Productive Feature Selection Criterion for Bot-IoT Recognition based on Random Forest Algorithm. In Proceedings of the IEEE 11th International Conference on Communication Systems and Network Technologies (CSNT), Indore, India, 23–24 April 2022; pp. 539–545. [Google Scholar]
- Jayalaxmi, P.; Kumar, G.; Saha, R.; Conti, M.; Kim, T.-H.; Thomas, R. DeBot: A deep learning-based model for bot detection in industrial internet-of-things. Comput. Electr. Eng. 2022, 102, 108214. [Google Scholar] [CrossRef]
- Atuhurra, J.; Hara, T.; Zhang, Y.; Sasabe, M.; Kasahara, S. Dealing with Imbalanced Classes in Bot-IoT Dataset. arXiv 2024, arXiv:2403.18989. [Google Scholar]
- Ibrahimi, K.; Benaddi, H. Improving the ids for bot-iot dataset-based machine learning classifiers. In Proceedings of the 5th International Conference on Advanced Communication Technologies and Networking (CommNet), Marrakech, Morocco, 12–14 December 2022; pp. 1–6. [Google Scholar]
- Leevy, J.L.; Hancock, J.; Khoshgoftaar, T.M.; Peterson, J.M. An easy-to-classify approach for the bot-IoT dataset. In Proceedings of the 2021 IEEE Third International Conference on Cognitive Machine Intelligence (CogMI), Atlanta, GA, USA, 13–15 December 2021; pp. 172–179. [Google Scholar]
- Ullah, I.; Mahmoud, Q.H. A scheme for generating a dataset for anomalous activity detection in iot networks. In Proceedings of the Canadian Conference on Artificial Intelligence, Ottawa, ON, Canada, 6 May 2020; pp. 508–520. [Google Scholar]
- Al-Akhras, M.; Alshunaybir, A.; Omar, H.; Alhazmi, S. Botnet attacks detection in IoT environment using machine learning techniques. Int. J. Data Netw. Sci. 2023, 7, 1683–1706. [Google Scholar] [CrossRef]
- Alsaaidah, A.; Almomani, O.; Abu-Shareha, A.A.; Abualhaj, M.M.; Achuthan, A. ARP Spoofing Attack Detection Model in IoT Network using Machine Learning: Complexity vs. Accuracy. J. Appl. Data Sci. 2024, 5, 1850–1860. [Google Scholar] [CrossRef]
- Elmahfoud, E.; Elhajla, S.; Maleh, Y.; Mounir, S. Machine Learning Algorithms for Intrusion Detection in IoT Prediction and Performance Analysis. Procedia Comput. Sci. 2024, 236, 460–467. [Google Scholar] [CrossRef]
- Maniriho, P.; Niyigaba, E.; Bizimana, Z.; Twiringiyimana, V.; Mahoro, L.J.; Ahmad, T. Anomaly-based intrusion detection approach for IoT networks using machine learning. In Proceedings of the 2020 International Conference on Computer Engineering, Network, and Intelligent Multimedia (CENIM), Surabaya, Indonesia, 17–18 November 2020; pp. 303–308. [Google Scholar]
- Doghramachi, D.F.; Ameen, S.Y. Internet of Things (IoT) Security Enhancement Using XGboost Machine Learning Techniques. Comput. Mater. Contin. 2023, 77, 717–732. [Google Scholar] [CrossRef]
- Verma, R.; Chandra, S. RepuTE: A soft voting ensemble learning framework for reputation-based attack detection in fog-IoT milieu. Eng. Appl. Artif. Intell. 2023, 118, 105670. [Google Scholar] [CrossRef]
- Le, T.-T.; Shin, Y.; Kim, M.; Kim, H. Towards unbalanced multiclass intrusion detection with hybrid sampling methods and ensemble classification. Appl. Soft Comput. 2024, 157, 111517. [Google Scholar] [CrossRef]
- Yan, Y.; Yang, Y.; Gu, Y.; Shen, F. A Few-Shot Intrusion Detection Model for the Internet of Things. In Proceedings of the 3rd International Conference on Electronic Information Engineering and Computer Science (EIECS), Changchun, China, 22–24 September 2023; pp. 531–537. [Google Scholar]
- Iorli̇am, A. A Novel Additive Internet of Things (IoT) Features and Convolutional Neural Network for Classification and Source Identification of IoT Devices. Sak. Univ. J. Comput. Inf. Sci. 2023, 6, 218–225. [Google Scholar] [CrossRef]
- Van Huong, P.; Minh, N.H. Improving the feature set in IoT intrusion detection problem based on FP-Growth Algorithm. In Proceedings of the 2020 International Conference on Advanced Technologies for Communications (ATC), Nha Trang, Vietnam, 8–10 October 2020; pp. 18–23. [Google Scholar]
- Selvam, R.; Velliangiri, S. An Improving Intrusion Detection Model Based on Novel CNN Technique Using Recent CIC-IDS Datasets. In Proceedings of the 2024 International Conference on Distributed Computing and Optimization Techniques (ICDCOT), Bengaluru, India, 15–16 March 2024; pp. 1–6. [Google Scholar]
- Elhanashi, A.; Gasmi, K.; Begni, A.; Dini, P.; Zheng, Q.; Saponara, S. Machine learning techniques for anomaly-based detection system on CSE-CIC-IDS2018 dataset. In Proceedings of the International Conference on Applications in Electronics Pervading Industry, Environment and Society, Genoa, Italy, 2 September 2022; pp. 131–140. [Google Scholar]
- Hagar, A.A.; Gawali, B.W. Deep learning for improving attack detection system using CSE-CICIDS2018. NeuroQuantology 2022, 20, 3064. [Google Scholar]
- Kurniabudi; Stiawan, D.; Darmawijoyo; Bin Idris, M.Y.; Bamhdi, A.M.; Budiarto, R. CICIDS-2017 dataset feature analysis with information gain for anomaly detection. IEEE Access 2020, 8, 132911–132921. [Google Scholar] [CrossRef]
- Maseer, Z.K.; Yusof, R.; Bahaman, N.; Mostafa, S.A.; Foozy, C.F.M. Benchmarking of machine learning for anomaly based intrusion detection systems in the CICIDS2017 dataset. IEEE Access 2021, 9, 22351–22370. [Google Scholar] [CrossRef]
- Pelletier, Z.; Abualkibash, M. Evaluating the CIC IDS-2017 dataset using machine learning methods and creating multiple predictive models in the statistical computing language R. Science 2020, 5, 187–191. [Google Scholar]
- Peterson, J.M.; Leevy, J.L.; Khoshgoftaar, T.M. A review and analysis of the bot-iot dataset. In Proceedings of the 2021 IEEE International Conference on Service-Oriented System Engineering (SOSE), Oxford, UK, 23–26 August 2021; pp. 20–27. [Google Scholar]
- FortiGuard AI-Powered Security Services. Available online: https://www.fortinet.com/solutions/enterprise-midsize-business/security-as-a-service/fortiguard-subscriptions (accessed on 6 March 2025).
- Ullah, I.; Mahmoud, Q.H. Design and development of a deep learning-based model for anomaly detection in IoT networks. IEEE Access 2021, 9, 103906–103926. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, H.; Wang, P.; Sun, Z. RTIDS: A robust transformer-based approach for intrusion detection system. IEEE Access 2022, 10, 64375–64387. [Google Scholar] [CrossRef]
- Sana, L.; Nazir, M.M.; Yang, J.; Hussain, L.; Chen, Y.-L.; Ku, C.S.; Alatiyyah, M.; Alateyah, S.A.; Por, L.Y. Securing the IoT Cyber Environment: Enhancing Intrusion Anomaly Detection With Vision Transformers. IEEE Access 2024, 12, 82443–82468. [Google Scholar] [CrossRef]
- Benaddi, H.; Ibrahimi, K.; Benslimane, A.; Qadir, J. A deep reinforcement learning based intrusion detection system (drl-ids) for securing wireless sensor networks and internet of things. In Proceedings of the 12th EAI International Conference, WiCON 2019, TaiChung, Taiwan, 26–27 November 2019; pp. 73–87. [Google Scholar]
- Tharewal, S.; Ashfaque, M.W.; Banu, S.S.; Uma, P.; Hassen, S.M.; Shabaz, M. Intrusion detection system for industrial internet of things based on deep reinforcement learning. Wirel. Commun. Mob. Comput. 2022, 2022, 1–8. [Google Scholar] [CrossRef]
- Ren, K.; Zeng, Y.; Cao, Z.; Zhang, Y. ID-RDRL: A deep reinforcement learning-based feature selection intrusion detection model. Sci. Rep. 2022, 12, 1–18. [Google Scholar] [CrossRef]
- Otoum, S.; Kantarci, B.; Mouftah, H. Empowering reinforcement learning on big sensed data for intrusion detection. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–7. [Google Scholar]
- Al-Fawa’reh, M.; Abu-Khalaf, J.; Szewczyk, P.; Kang, J.J. MalBoT-DRL: Malware botnet detection using deep reinforcement learning in IoT networks. IEEE Internet Things J. 2023, 11, 9610–9629. [Google Scholar] [CrossRef]
- Ullah, S.; Ahmad, J.; Khan, M.A.; Alshehri, M.S.; Boulila, W.; Koubaa, A.; Jan, S.U.; Ch, M.M.I. TNN-IDS: Transformer neural network-based intrusion detection system for MQTT-enabled IoT Networks. Comput. Netw. 2023, 237, 110072. [Google Scholar] [CrossRef]
- Akuthota, U.C.; Bhargava, L. Transformer-Based Intrusion Detection for IoT Networks. IEEE Internet Things J. 2025, 12, 6062–6067. [Google Scholar] [CrossRef]
- Khanday, S.A.; Fatima, H.; Rakesh, N. Towards the Development of an Ensemble Intrusion Detection Model for DDoS and Botnet Mitigation using the IoT-23 Dataset. J. Harbin Eng. Univ. 2023, 44, 562–578. [Google Scholar]
- Vitorino, J.; Andrade, R.; Praça, I.; Sousa, O.; Maia, E. A comparative analysis of machine learning techniques for IoT intrusion detection. In Proceedings of the InInternational Symposium on Foundations and Practice of Security, Paris, France, 7 December 2021; pp. 191–207. [Google Scholar]
- Zhang, C.; Jia, D.; Wang, L.; Wang, W.; Liu, F.; Yang, A. Comparative research on network intrusion detection methods based on machine learning. Comput. Secur. 2022, 121, 102861. [Google Scholar] [CrossRef]
- de Souza, C.A.; Westphall, C.B.; Machado, R.B. Two-step ensemble approach for intrusion detection and identification in IoT and fog computing environments. Comput. Electr. Eng. 2022, 98, 107694. [Google Scholar] [CrossRef]
- Kabir, M.H.; Rajib, M.S.; Rahman, A.S.M.T.; Rahman, M.M.; Dey, S.K. Network intrusion detection using unsw-nb15 dataset: Stacking machine learning based approach. In Proceedings of the 2022 International Conference on Advancement in Electrical and Electronic Engineering (ICAEEE), Gazipur, Bangladesh, 24–26 February 2022; pp. 1–6. [Google Scholar]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M. Real time security assessment of the power system using a hybrid support vector machine and multilayer perceptron neural network algorithms. Sustainability 2019, 11, 3586. [Google Scholar] [CrossRef]
- Wang, M.; Yang, N.; Weng, N. Securing a smart home with a transformer-based IoT intrusion detection system. Electronics 2023, 12, 2100. [Google Scholar] [CrossRef]

| IoT Layer/Domain | Security Measures | Strengths | Limitations |
|---|---|---|---|
| Node devices/hardware devices | Tamper seals | Offer visible and digital evidence of intrusions. Seals cannot be restored once unsealed. Trust and deterrence on physical devices. | Easily triggered by environmental factors. Expensive to maintain. |
| Firmware updates | Easily fix exploitable bugs. Good performances (both functional and non-functional elements). | Compatibility issues. Easily exploitable trigger updates. | |
| Secure element | Tamper resistance to physical attacks and injections. Storage opportunity for cryptographic keys and certificates. | Implementation cost and complexity of integration. | |
| Data communication/Network protocol | Encryption, authentication, and access control models | Scalable, cheap, and efficient. Provide security against a wide range of attacks. | Cumbersome and computationally expensive. |
| Blockchain | Decentralized and transparent security solution. Immutability applies. | Cost and energy inefficient, scalability concerns. Application complexities. | |
| Application layer | Secure bootstrapping techniques | High effective solution. | Expensive. Scalability issues. |
| Dataset | Year Published | Devices Used | Attack Type | Attack Labelled (Y/N) | Data File Format | Key Limitations |
|---|---|---|---|---|---|---|
| BoT-IoT | 2019 | IoT home devices, including R-Pi, smart lights, plugs, thermostats, IP cameras, etc. | DDoS, DoS, reconnaissance (scanning and probing), theft (info theft and data exfiltration) | Y | PCAP and CSV | Imbalanced data, simulation-based environment, limited network size and data size |
| UNSW-NB15 | 2015 | Network infrastructure devices, including routers, switches, etc., servers and workstation machines, servers and firewalls, attack simulation tools including Nmap, Wireshack, etc. | Backdoor, DoS, exploits, fuzzers, port scans, recon, shell code, spam, worms | Y | CSV, PCAP, ARFF | Simulated attack scenarios, imbalanced data |
| CIC-IDS 2017 | 2017 | Network infrastructure devices (routers, switches), servers and workstations, virtual and physical machines, IoT end devices, and attack simulation tools | Botnet, XSS, DoS, DDoS, heart bleed, infiltration attack, SSH, brute force, SQLi | Y | PCAP, CSV | Imbalanced data, outdated attack variants, and numerous redundant data features |
| CIC-IDS 2018 | 2018 | Network infrastructure devices, including routers, switches, etc., servers and workstation machines, servers and firewalls, IoT devices (R-Pi, cameras, etc.), attack simulation tools, including Nmap, Wireshack, etc. | Botnet, brute force, port scan, DDoS, DoS, web attack, and infiltration attack | Y | CSV | Imbalanced dataset, limited and controlled ecosystem deployed to generate the dataset, several redundant features |
| IoTID20 | 2020 | IoT end devices (smart plugs, cameras, lights, speakers, etc.), attack simulation tools including Wireshack, hydra, medusa, etc. | Syn flooding, brute force, HTTP flooding, UDP flooding, ARP spoofing, host port, and OS Scan | Y | CSV | Imbalanced data, limited attack varieties. The ecosystem used for generating the data is limited. |
| MQTT-IoT-IDS 2020 | 2020 | IoT end devices (lights, thermostats, plugs, speakers, etc.), MQTT comm protocol, attack simulation tools including Wireshack, ettercap, hydra, medusa, etc. | DoS, DDoS, Brute force, MiTM, credential stuffing | Y | CSV | Class imbalance issue, limited attack varieties. Also, the dataset is captured in a static environment. |
| TON_IoT | 2020 | IoT end devices (weather stations, smart fridges, doors, lights, etc.), SCADA, PLC, servers (web servers, file transfer servers, database servers) | Ransomware, password attack, scanning, DoS, DDoS, data injection, backdoor, cross-site scripting (XSS), and MiTM | Y | CSV and PCAP | Class imbalance issue, the dataset is made up of static logs. Huge redundant features. |
| IoT-23 | 2020 | Smart home devices (Amazon Echo Home device, smart LED lamp, and a door lock). | DDoS, Brute Force and credential stuffing, malware infections (Mirai, Gafgyt), C2 communications, scanning and exploitation | Y | PCAP, CSV, and TXT | Imbalanced dataset. The ecosystem network deployed to generate the dataset is limited and lacks diversity. |
| Ref. | AI Model(s) | Dataset(s) | Contributions in Summary |
|---|---|---|---|
| [90] | LSTM, CNN, and CNN-LSTM | IoTID20 | Implemented SMOTE, ADASYN, and RUS to deal with the class imbalance issue. Metrics including accuracy, precision, recall, AUC, F1-score, and sensitivity were used to evaluate model performances. The results achieved were outstanding. |
| [150] | Transformer | TON_IoT | Focus on analysis of traffic data as well as IoT sensors’ telemetry data. The experimentation explored both binary classification and multiple classifications. Missing data points and invalid values of categorical features in the dataset are substituted with the string “-” while all invalid values of numerical features were substituted with the value “−1”. Each categorical feature with a value between 0 and U is encoded, whereby U is the number of unique contents for the categorical feature. The values are further used to calculate embedding vectors for categorical features, and numerical features are normalized. The model performed exceptionally well. |
| [122] | Ensemble AdaBoost, LightGBM, and XGBoost | IoTID20 and Car Hacking: Attack and Defense Challenge 2020 (CHADC2020) | Rigorous pre-processing, including dealing with missing values median imputation, correlation-based feature selection, and min/max normalization. Tomek links and edited nearest neighbors (ENN) for undersampling while SMOTE and BorderlineSMOTE for oversampling. Using metrics including precision, recall, F1-score, accuracy, and ROC-AUC, the hybrid-ensemble approach achieves remarkable results. |
| [1] | Neural networks | Edge-IIoTset, WUSTL-IIOT-2021, and IoTID20 | Optimization based on the Salp swarm algorithm (SSA) for selecting optimal networks for the neural network model. The combination performed well on the three datasets. |
| [117] | RF | IoTID20 | Pre-processing steps include removing duplicate data and irrelevant features such as Flow_ID, Src_IP, Timestamp, and Dst_IP. Also, replacing missing values using median values and using min/max normalization. Focusing on the ARP Spoofing attack detection. Comparison between simple and ensemble models and evaluating the performance using accuracy, precision, sensitivity, F-measure, and speed. The experimental results showed that wrapper feature selection with the RF classifier reduced around 50.6% of the IoTID20 features and achieved good performances. |
| [116] | Neural networks, RF, DT | IoTID20, N-BaIoT, and MedBIoT | Feature reduction and noise filtering based on RENN, Explore, and DROP5 algorithms. SMOTE for dealing with data imbalances. Standard metrics, including accuracy, precision, recall, specificity, F-score, and G-mean were used. Results showed that the RENN and DROP5 filtering models presented excellent results. |
| [86] | LSTM | UNSW-NB15 and Bot-IoT | Protocol-Based Deep Intrusion Detection (PB-DID) architecture, whereby a dataset of packets from IoT traffic involving features from the UNSW-NB15 and Bot-IoT datasets based on flow and TCP, was analyzed. Non-anomalous, DoS, and DDoS traffic were classified. Typical issues such as class imbalance and over-fitting issues were catered for. Exceptional performances were achieved based on the results. |
| [100] | KNN, RF, CART, and deep learning algorithms (CNN, LSTM, DNN) | TON_IoT | For the issue of class imbalance, SMOTE was deployed for oversampling, while a modified version of the redundant-based Tomek link removal technique was used to cater for under-sampling. Deployed the use of sine and cosine component cyclic encoding for temporal attributes. The learners performed well with the binary and multi-class classification based on the evaluation metrics which include accuracy, precision, recall, and F1 score. |
| [109] | Four ensembles (CatBoost, Light-GBM, XGBoost, and RF and four non-ensembles (DT, Logistic Regression, Naive Bayes, and a Multilayer Perceptron). | BoT-IoT | The subset of original data containing 3,668,522 instances and 43 features was used for experimentation. The focus was on the 477 normal instances and 79 information theft instances. To gauge the classifiers’ performances, AUC and AUPRC metrics were used. |
| [114] | DT | BoT-IoT | For easy learning, the subset of the original data was used (only 3 out of the 29 Bot-IoT features). For evaluating the classification performance of the algorithm, AUC and AUPRC metrics were used and the model performed well. |
| [107] | KNN, Naive Bayes and Multi-layer Perception | BoT-ToT | SMOTE was used for data feature engineering. Based on the accuracy, precision, recall, F1-Score, and ROC AUC results, the KNN algorithm performed the best among the learners. |
| [91] | RF, Naıve Bayes, Neural Networks, SVM and AdaBoost. | IoT-23 | A statistical correlation was deployed whereby a correlation matrix for each of the 33 data files in the IoT-23 data was drawn and the results were averaged. Data with no statistical correlation were removed. RF presented the best result. |
| [80] | Adversarial Autoencoders (AAE) and Bidirectional Generative Adversarial Networks (BiGAN) | IoT-23 | Preprocessing involves various tasks like feature selection, encoding, normalization, and balancing. The generative models outperform traditional machine learning models. |
| [99] | 8 classifiers, including logistic regression, naive Bayes, DT, SVM, KNN, RF, Adaboost, and XGBoost. | TON_IoT | Missing values are imputed and one-hot encoding was used to convert categorical features. Min/max normalization also formed part of the pre-processing steps. The Chi2 technique was used for feature selection and SMOTE was deployed for class balancing. XGBoost outperformed the other models. |
| [146] | DT, Naive Bayes, SVM, RF, CNN, RNN, XGBoost | KDD CUP 99 and NSL-KDD | PCA was used for dimensionality reduction. Metrics, including detection accuracy, F1, and AUC, were used to perform a comparative assessment of the learners. Analysis results showed that the ensemble learning algorithm performed generally better. The Naive Bayes algorithm has low accuracy in recognizing the learned data, but it has obvious advantages when facing new types of attacks, and the training speed is faster. |
| [145] | SVM), XGBoost, LightGBM, Isolation Forest (iForest), Local Outlier Factor (LOF), and Double Deep Q-Network (DDQN) | IoT-23 | A comparative analysis of supervised, unsupervised, and reinforcement learning techniques on nine malware captures of the IoT-23 dataset, whereby both binary and multi-class classification scenarios were considered. The most reliable result was achieved by the LightGBM model. The DDQN also performed well in specific tasks. |
| [4] | Gated recurrent unit, LSTM, and multilayer perceptron | IoT-23, IoTID-20 | An ensemble model was proposed. PCA was used for feature selection. The ensemble model’s performance was evaluated using IoT-23 and IoTID-20 datasets. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alimi, O.A. Data-Driven Learning Models for Internet of Things Security: Emerging Trends, Applications, Challenges and Future Directions. Technologies 2025, 13, 176. https://doi.org/10.3390/technologies13050176
Alimi OA. Data-Driven Learning Models for Internet of Things Security: Emerging Trends, Applications, Challenges and Future Directions. Technologies. 2025; 13(5):176. https://doi.org/10.3390/technologies13050176
Chicago/Turabian StyleAlimi, Oyeniyi Akeem. 2025. "Data-Driven Learning Models for Internet of Things Security: Emerging Trends, Applications, Challenges and Future Directions" Technologies 13, no. 5: 176. https://doi.org/10.3390/technologies13050176
APA StyleAlimi, O. A. (2025). Data-Driven Learning Models for Internet of Things Security: Emerging Trends, Applications, Challenges and Future Directions. Technologies, 13(5), 176. https://doi.org/10.3390/technologies13050176