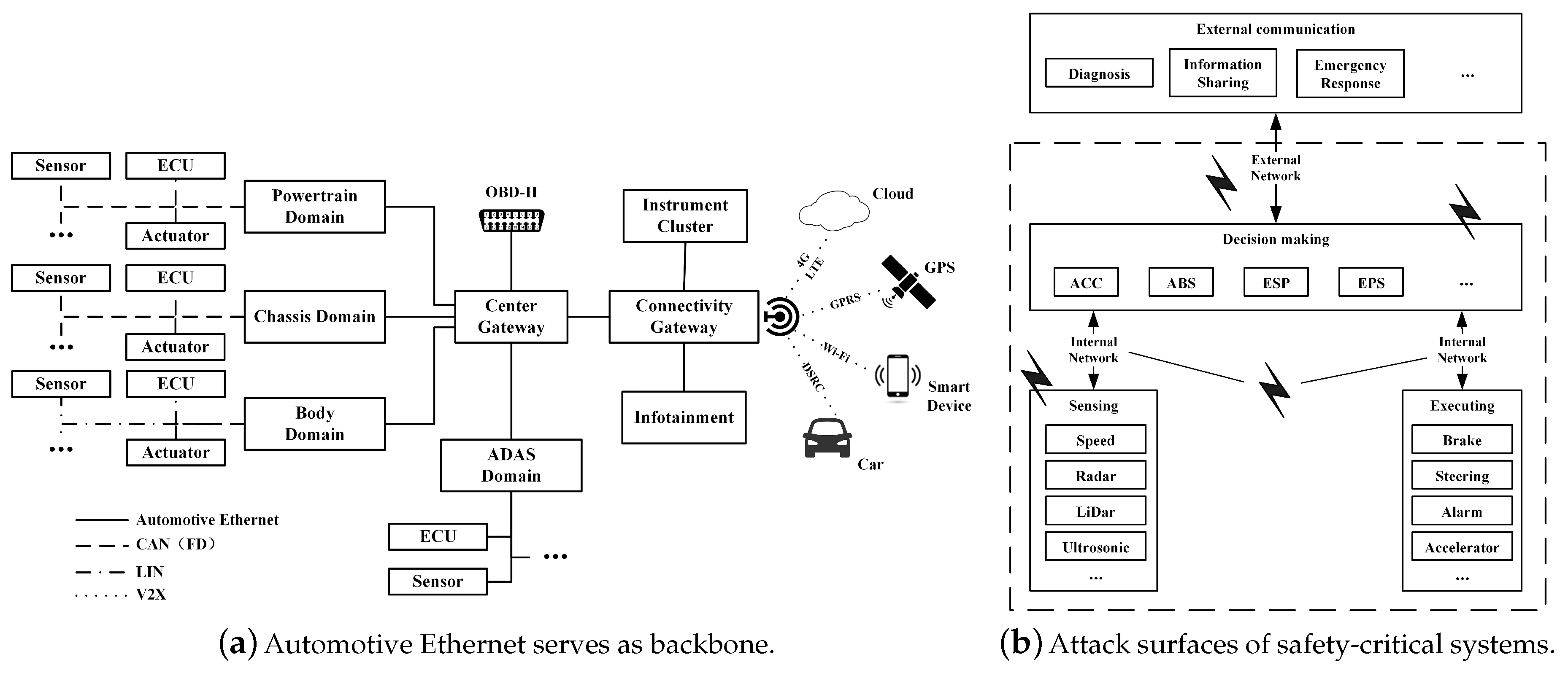
In this section, the proposed framework is applied to the actual automotive collision warning system, which is a typical safety-critical system composed of various sensors, controllers, actuators, networks, and other components. As a contrast, we analyze the security risk of the system under the traditional distributed and the modern centralized in-vehicle architecture. In addition, as an assistant method, a model transformation algorithm is introduced to generate MDP expressions from a SysML activity diagram.
5.3. Model Generation
As mentioned above, our MDP model is composed of a system model, identified threats, and attacker model. For the purpose of reusability, we modeled the system model in the PRISM tool as four types of modules: an environment module, a sensor module, a controller module, and an actuator module. The environment module describes the uncertainty of the environment’s change, in our case representing the change of the vehicle’s distance and lane line. The sensor module describes the process of sensors perceiving environment changes. The controller module describes the process of how the output signal is generated according to the input signal by the controller. The actuator module describes the process in which the actuator performs corresponding actions according to the received control signals. To understand the behavior within each module,
Figure 6 shows two example statements in the ADAS controller module. Variable
att_mani = 0 indicates that the manipulation attack did not occur. In this case, the ADAS controller will generate control signals according to the ultrasonic sensor signal
dist_val and
lane_val to control the action of the engine, steering wheel, and alarm. By contrast,
att_mani = 1 indicates that a manipulation attack occured, and the ADAS controller will not generate correct control signals.
In each module, a boolean value is used to indicate whether an attack occurs (e.g.,
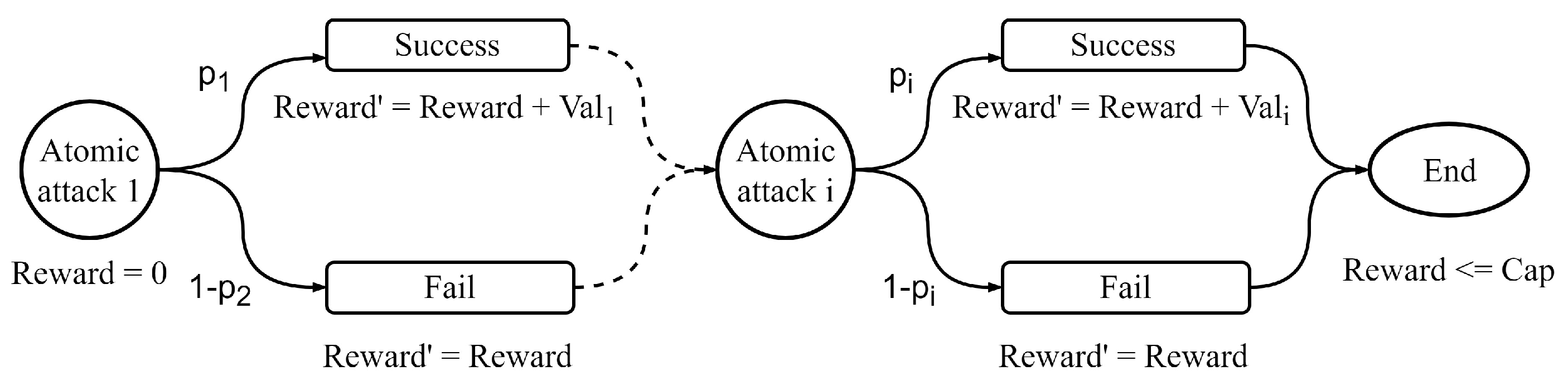
), which is determined by the attacker. As the behavior of the attacker is non-deterministic, the maximum rewards of the attacker are limited by the attacker’s capability. In this case, we built a module to describe the attacker’s behavior. In order to understand the uncertain behavior of attackers,
Figure 7 shows two example statements in the attacker module. The first statement describes that the probability of success of malware injection is 0.75 and the probability of failure is 0.25. If the atomic attack succeeds, the attacker’s reward
reward will be increased by 4 according to the impact level; otherwise, the reward
reward will not be increased. It is worth noting that the attacker’s reward can never exceed the attacker’s capability
att_cap. Similarly, the second statement describes that the probability of success of the head unit attack is 0.5. Other attacker behaviors can be created in a similar way.
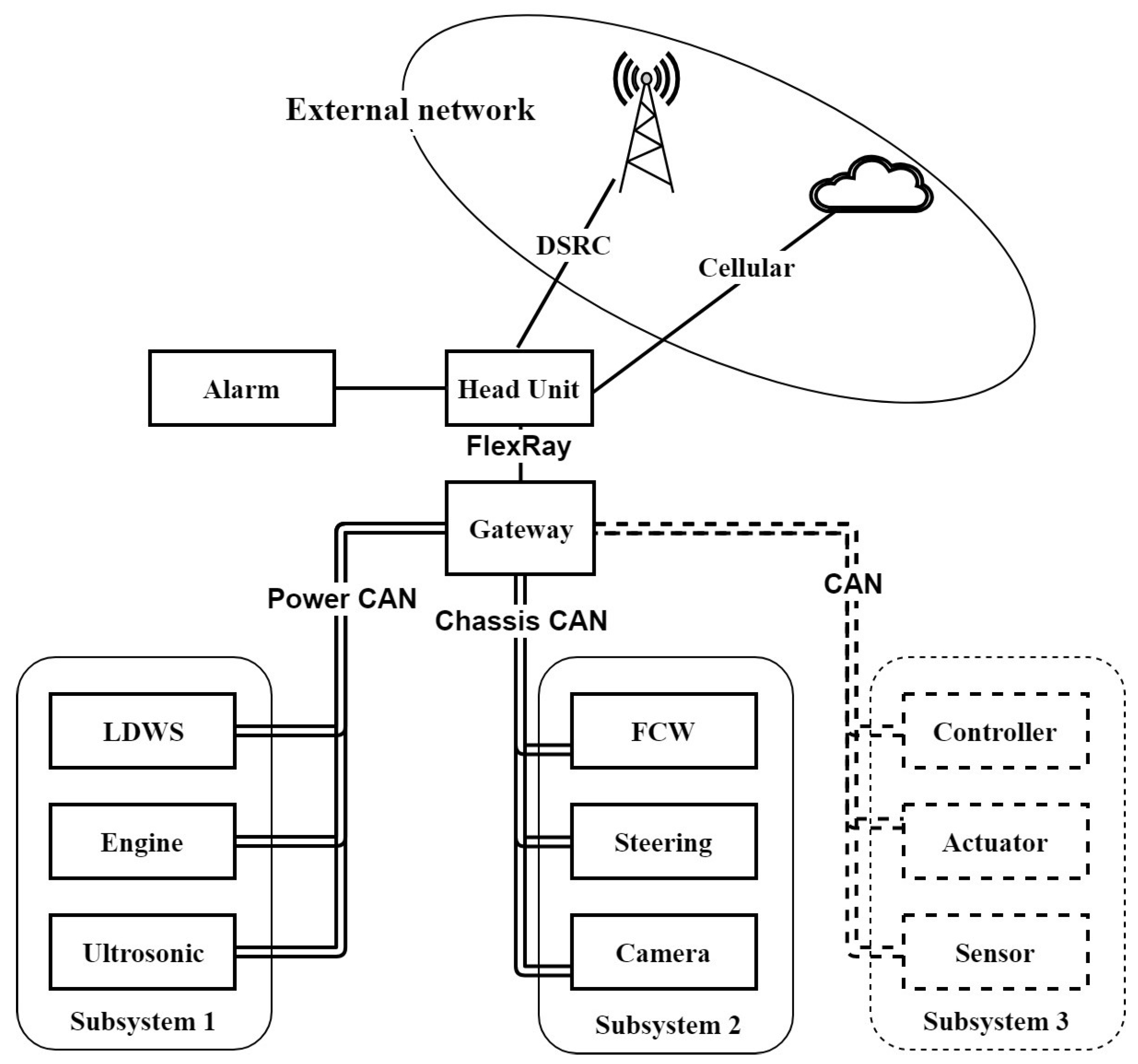
As a comparative analysis, the collision warning system under the traditional distributed EEA is shown in
Figure 8. The MDP model under this architecture can be built in a similar way to the one mentioned above. Under these two architectures, the description of security properties is universal, and the description and evaluation of security properties will be described in the next subsection.
5.4. Properties Specification and Evaluation
Here, we present six security properties to be verified against the TOE shown in
Figure 5. Each security property is first described in natural language, and then is translated into a formal description by using PCTL, which can be used as the input of the PRISM tool. After verification, we can get the attacker’s maximum probability to break each property. For easy understanding of property descriptions, some of the variables involved in this use case are shown in
Table 4.
Property 1. “Calculate the maximum probability that the alarm will not respond properly”. Whether the alarm works normally can be divided into two situations: one is that no control signal is received, and the other is that the received control signal was tampered with. A formal description in PRISM language of Property 1 is , where x is a variable that represents the attacker’s capability.
Property 2. “Calculate the maximum probability that an ultrasonic sensor signal is wrong”. Sensor data errors can be divided into three situations: sensor blinding, data manipulation, and denial of service. A formal description in PRISM language of Property 2 is , where x is a variable that represents the attacker’s capability.
Property 3. “Calculate the maximum probability that a steering control signal is wrong”. The steering control signal is generated by the ADAS controller according to the predefined strategy, which is affected by the correctness of the sensor data, the security of the gateway and the ADAS controller, and the security of the CAN bus in the vehicle. A formal description in PRISM language of Property 3 is , where x is a variable that represents the attacker’s capability.
Property 4. “Calculate the maximum probability that a remote diagnosis signal from the alarm to the cloud is wrong”. Sometimes remote cloud servers want to know if the alarm is triggered, and this information is usually sent from the local vehicle to the cloud through a diagnostic message. This information is likely to be tampered with in the process of transmission. A formal description in PRISM language of Property 4 is , where x is a variable that represents the attacker’s capability.
Property 5. “Calculate the maximum probability that the alarm causes a wrong response to a safety event”. When the vehicle is driving, infrastructure (such as RSU) usually reports the surrounding environment information to the vehicle through DSRC communication. A basic safety message (BSM) is an example of this information and wrong BSM can cause s life-threatening situation to drivers, passengers, and surrounding vehicles. A formal description in PRISM language of Property 5 is , where x is a variable that represents the attacker’s capability.
Property 6. “Calculate the maximum probability of denial of service”. In this particular case, a DoS means that all the signals we care about are in a “no signal” state. A formal description in PRISM language of Property 6 is , where x is a variable that represents the attacker’s capability.
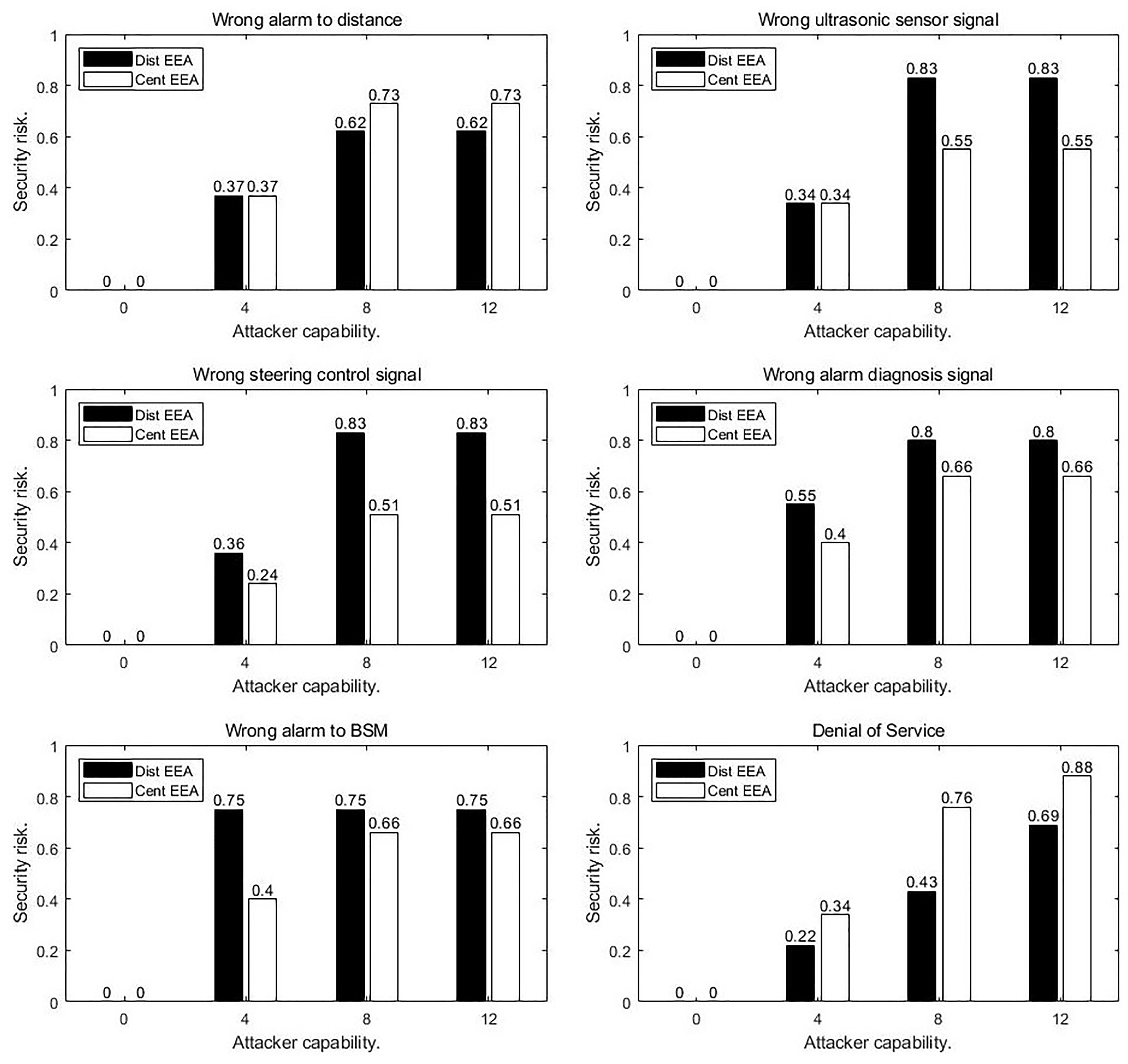
As an illustration only, we have not considered all of the security properties of the TOE. In a practical use case, we may define more security properties for verification according to our proposed method. After verification, as the attacker’s capability grows, the changes of the maximum probability of breaking each property under both EEAs are shown in
Figure 9. Up to now, we have realized the quantitative security risk analysis for a safety-critical system of connected vehicles. The results of the evaluation show that the risk of each security property is related to the capacity of the attacker and system architecture, and more discussion will be presented later. Another noteworthy result is that atomic attacks are exploited when the risk of attack reaches the maximum under the limited attacker’s ability. For each property is this case, when the attacker’s ability is 12, the corresponding atomic attacks are shown in
Table 5.
5.5. Implementation
Most of the work in the security risk assessment approach is to establish the MDP model. Automotive engineers are more familiar with the electrical and electronic architecture of the vehicle and are not good at model checking technology. Therefore, they prefer to focus on the description of the automotive electronic and electrical systems and their functions, while the MDP model generation work is handed over to the computer to complete. Therefore, we propose an engineering method to generate the MDP model for safety-critical systems of connected vehicles by using the SysML activity diagram. Firstly, we use the SysML activity diagram to describe our TOE’s structure and functions, and selected activity diagram elements are mapped to components and state transitions of TOE in the diagram. For example, is used to describe modules, is used to describe message passing, is used to describe atomic activities inside each module, and so on. Then, we use the Python API to implement a model generation tool, which takes the system model file described by XML as input, and the output results are MDP expressions described with the PRISM language. Finally, the generated MDP expressions can be reorganized together and imported into the PRISM tool for verification. The MDP expressions generation algorithm based on depth first search (DFS) is given in Algorithm 1.
| Algorithm 1: SysML Activity Diagram Transformation Algorithm. |
![Electronics 09 01242 i010 Electronics 09 01242 i010]() |
In Algorithm 1,
nodes is the activity diagram’s nodes stored in the stack,
cNode is the node being accessed, and
mdpExpress is the set of generated MDP expressions. The
MDPexp.gen() function converts the currently accessed SysML activity diagram elements to an MDP expression. The mapping rules between MDP expression and SysML activity diagram constructs are shown in
Table A1. The transition algorithm calls DFS at most once for each node in the activity diagram and searches the adjacency matrix every time it calls DFS. Therefore, the complexity of the algorithm is
, where
n represents the number of nodes in the activity diagram.
5.6. Discussion
In-vehicle embedded systems are becoming more and more complex, due to emerging connectivity and intelligent driving. As a result, it is becoming hard to analyze the security risk of the safety-critical systems inside connected vehicles. Automotive engineers have difficulty understanding the security threat of in-vehicle safety-critical systems by relying on traditional threat analysis methods. Our proposed approach can realize the system-level analysis of the security risk of the in-vehicle safety-critical system by formalizing a system model and a threat model. This formal method can avoid the ambiguity of the system security properties’ definition, which is very important for safety-critical systems of connected vehicles. The key findings from our illustration are summarized here:
For the same safety-critical system, the security risks faced by the system are very different under different automotive electronic and electrical architectures (as shown in
Figure 9).
In a traditional distributed architecture, sensor signals and control signals are transmitted in a CAN bus through broadcast. Moreover, the CAN bus is directly connected to the in-vehicle gateway, and these two signals have a probability of being successfully attacked of up to 0.83. In the centralized architecture, the CAN bus in the vehicle is isolated, so the attacker cannot penetrate the CAN bus, and thus the probability of being attacked is lower, at about 0.5.
Under the modern centralized electronic and electrical architecture, the automobile provides more external interfaces (i.e., connected gateway and head unit). Attackers can have more attack methods against alarm signals. Therefore, the probability of success of attacking an alarm signal in the centralized architecture is 0.73, higher than that in a distributed architecture.
When the vehicle communicates with the outside world, such as remote diagnosis and basic safety messages (BSM), the risk level of the traditional distributed architecture (at 0.8, and 0.75 respectively) is greater than that of the centralized architecture (at 0.6), because of the simple domain isolation mechanism.
Because the centralized architecture adopts an IP-based backbone network, this open network system is more vulnerable to denial of service (DoS) attacks.
In our proposed approach, due to having discretized and abstracted the sensor signal and control signal, we must know the internal strategy of the system. This kind of abstraction may be very different in different engineers’ concrete practices.
It is worth noting that because we aimed to test our implementation in an environment that is as realistic as possible, noise was inserted into the scenario. From the perspective of practice, model noise can be removed from three aspects: (1) threats in the actual work may come from different organizations and systems, which should be credible and categorized according to different modules and organizations; (2) a unified scoring system, similar to a common vulnerability scoring system (CVSS) and common vulnerabilities and exposures (CVE), should be adopted in the analysis process to assess the security risk of threats; and (3) security threat analysis conducted by a security engineer should be based on a system engineer’s description of the target system, and as many security engineers as possible should be involved in order to reduce the error.