Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent Systems
Abstract
1. Introduction
Purpose of the Study
2. Literature Review
2.1. History of Intrustion Detection System
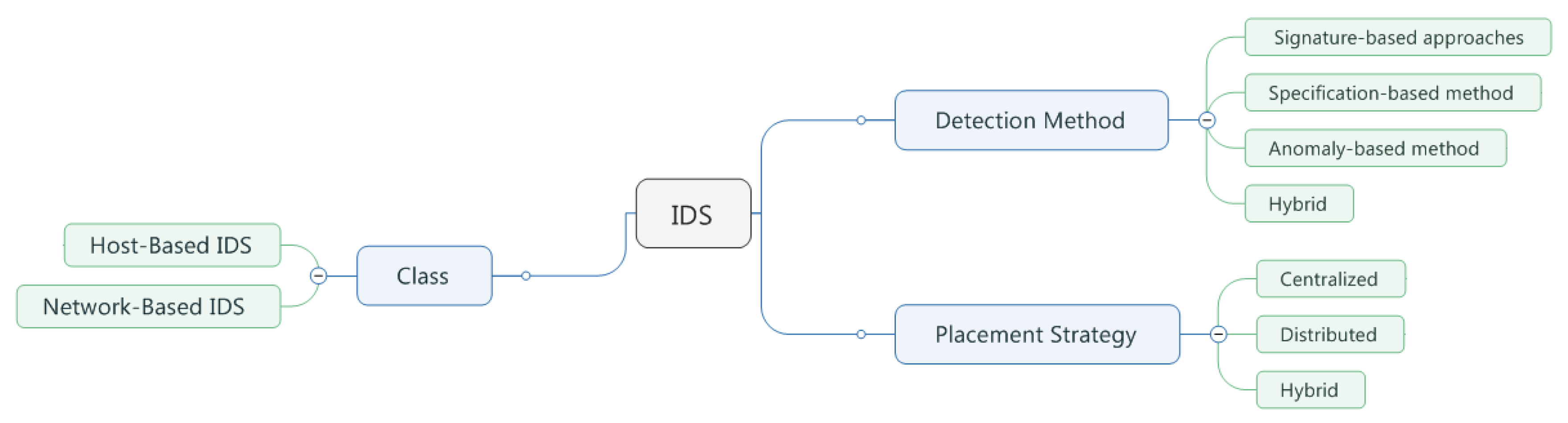
2.1.1. Classes of IDS
- Host-based IDS
- Network-based IDS
2.1.2. Detection Methods
2.1.3. Placement Strategy
2.2. Previous Research on IDS for IoT
2.3. Technology
2.3.1. Multi-Agent System
2.3.2. Machine Learning
Deep Learning
Multi-Agent Reinforcement Learning
2.3.3. Blockchain
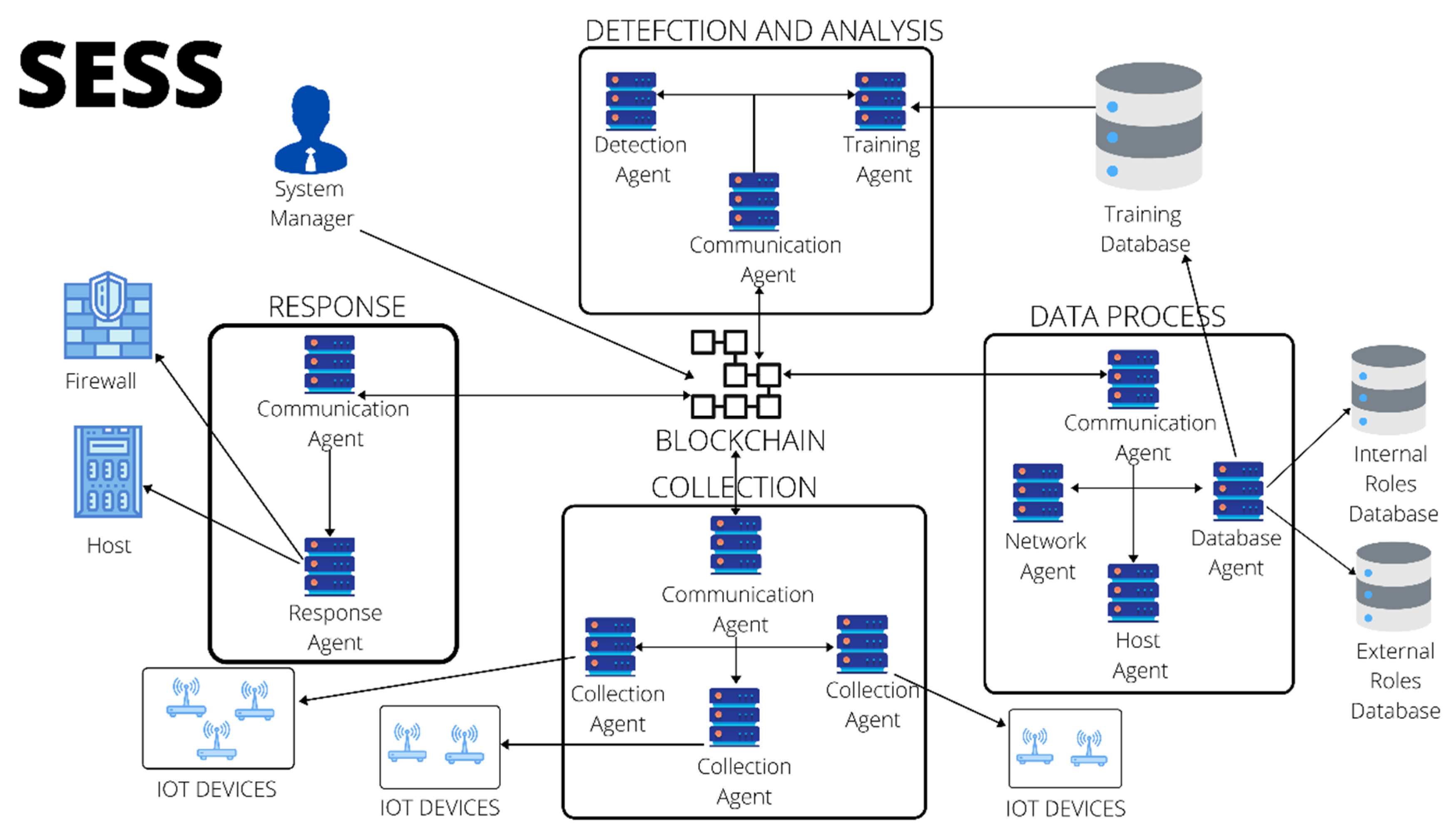
3. SESS (Smart Efficient Secure and Scalable) System
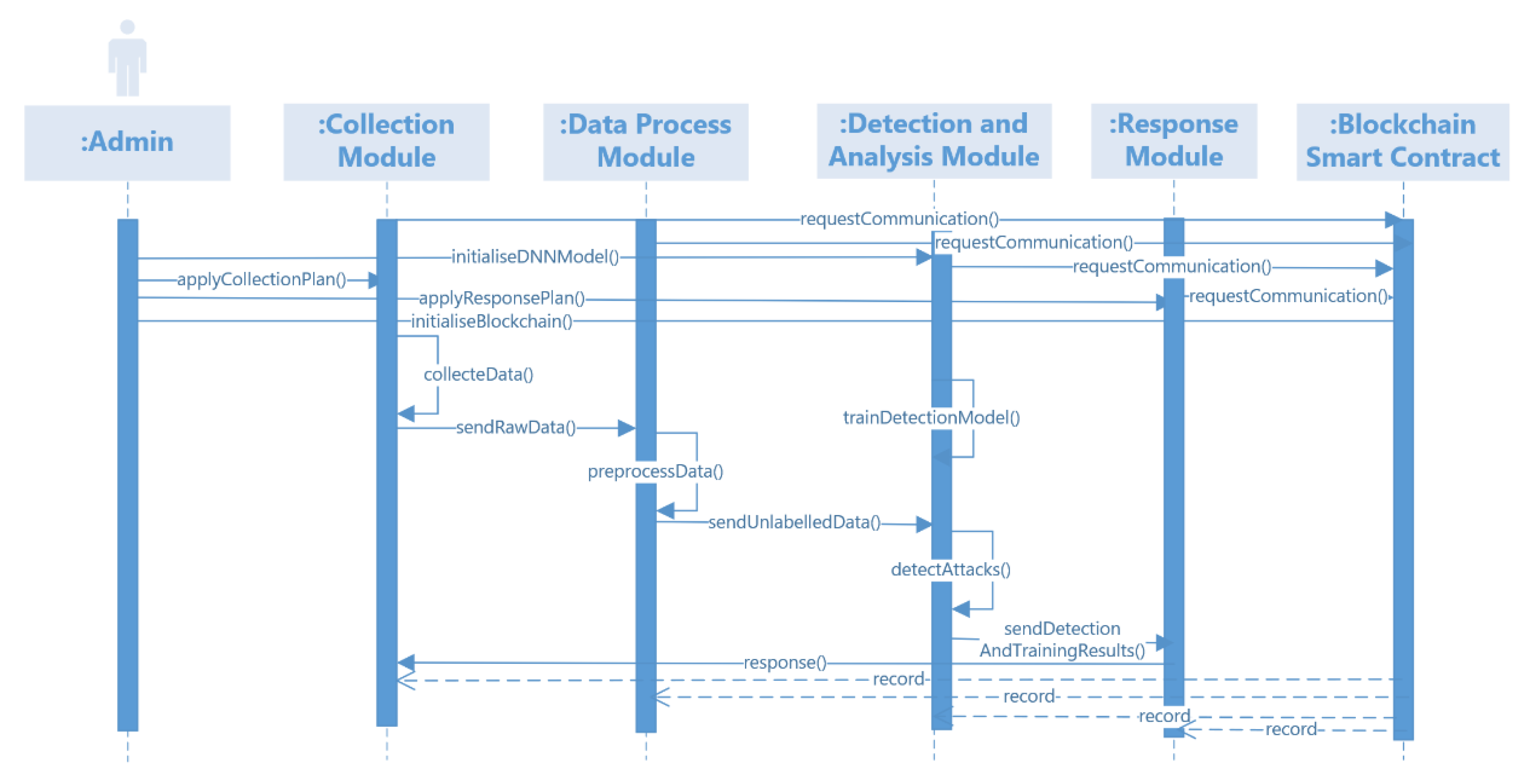
3.1. System Design
3.1.1. System Perspective
3.1.2. System Functions
3.1.3. User Characteristics
3.2. System Development
3.2.1. Blockchain Component
AgentAccount
BlockChainUtil
Communication
Block
Contract
3.2.2. Detection and Analysis Module
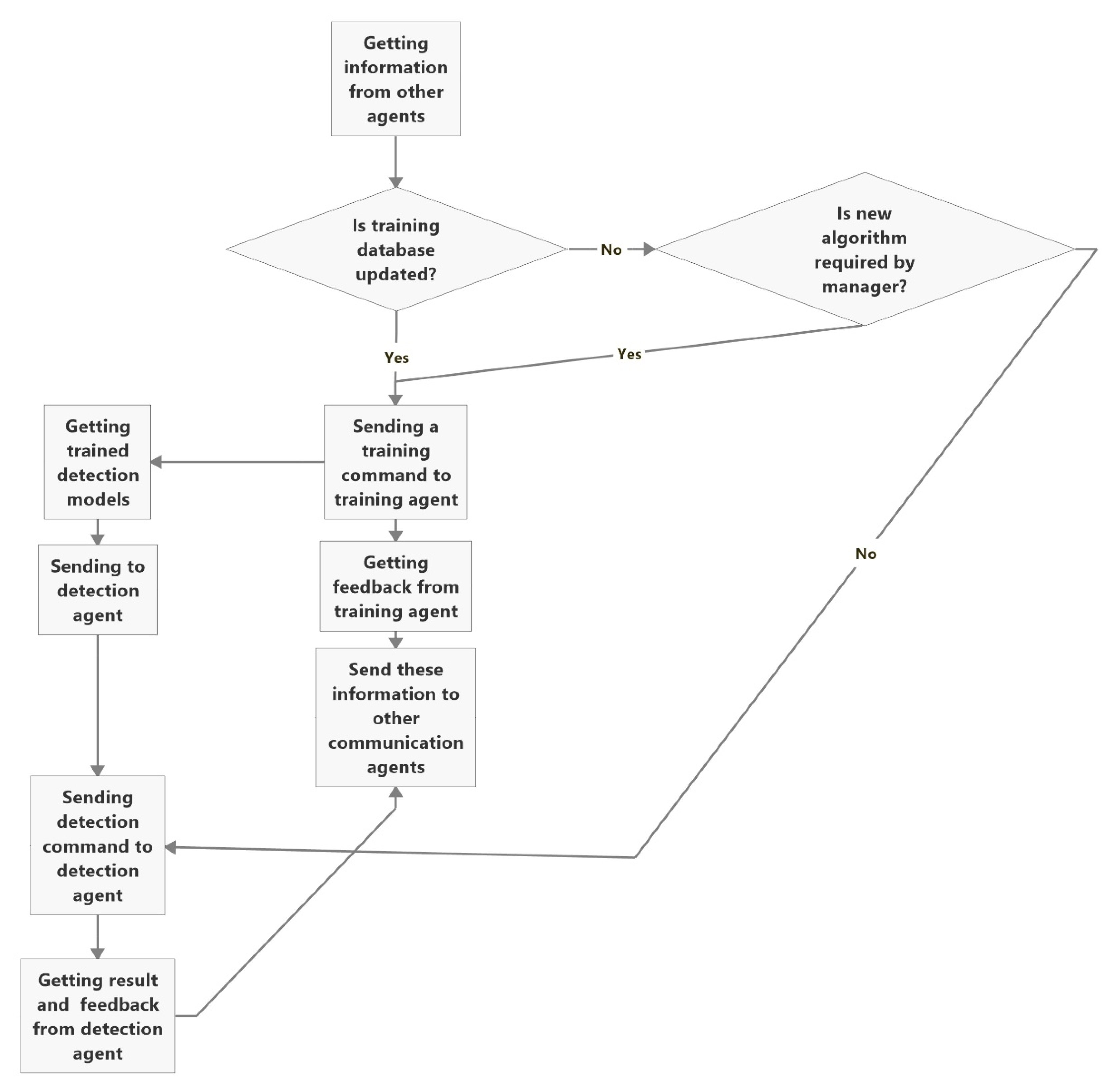
DACommunication Agent
Detection Agent
Training Agent
DNNUtil
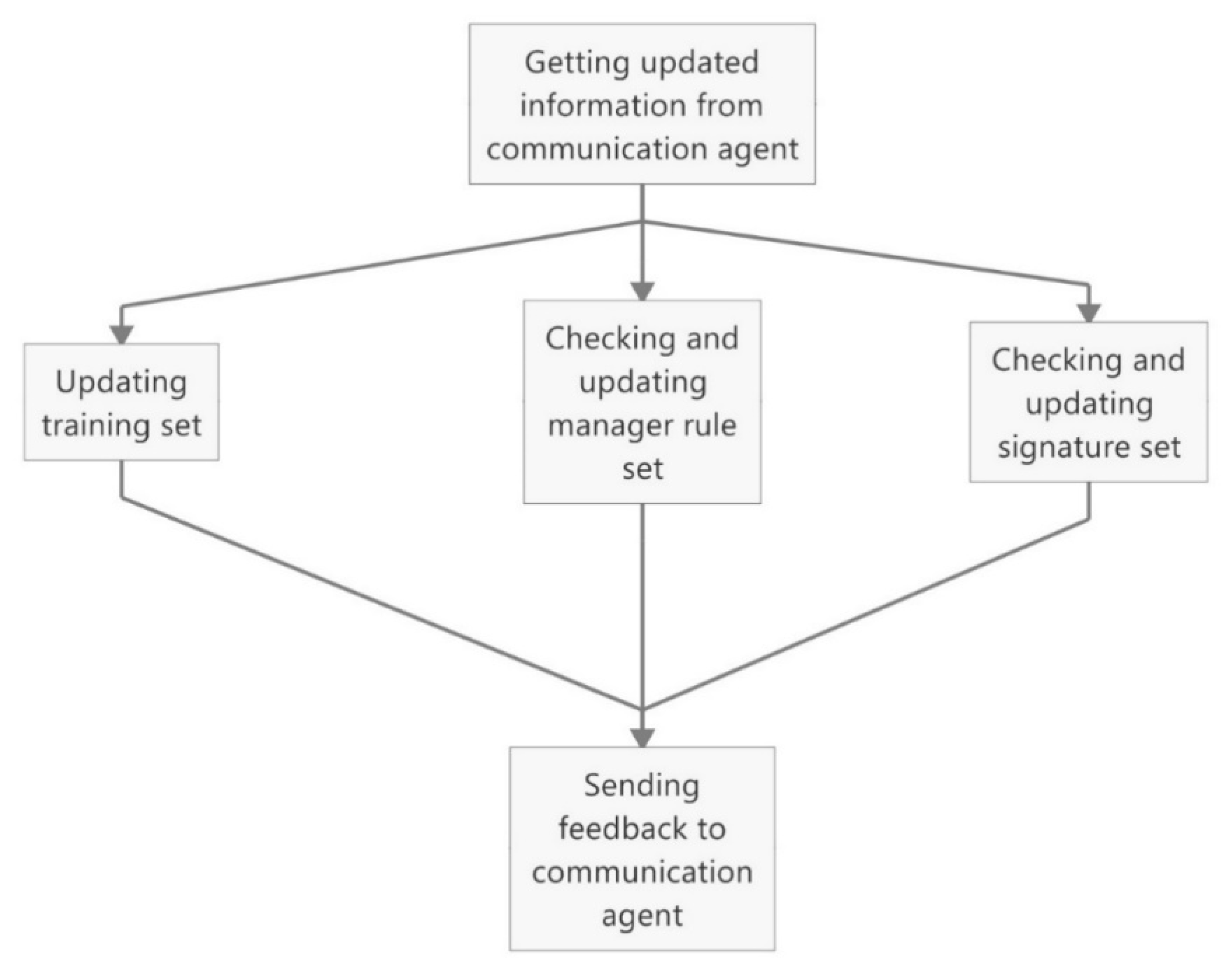
3.2.3. Response Module
RCommunication Agent
Response Agent
Data Visualization
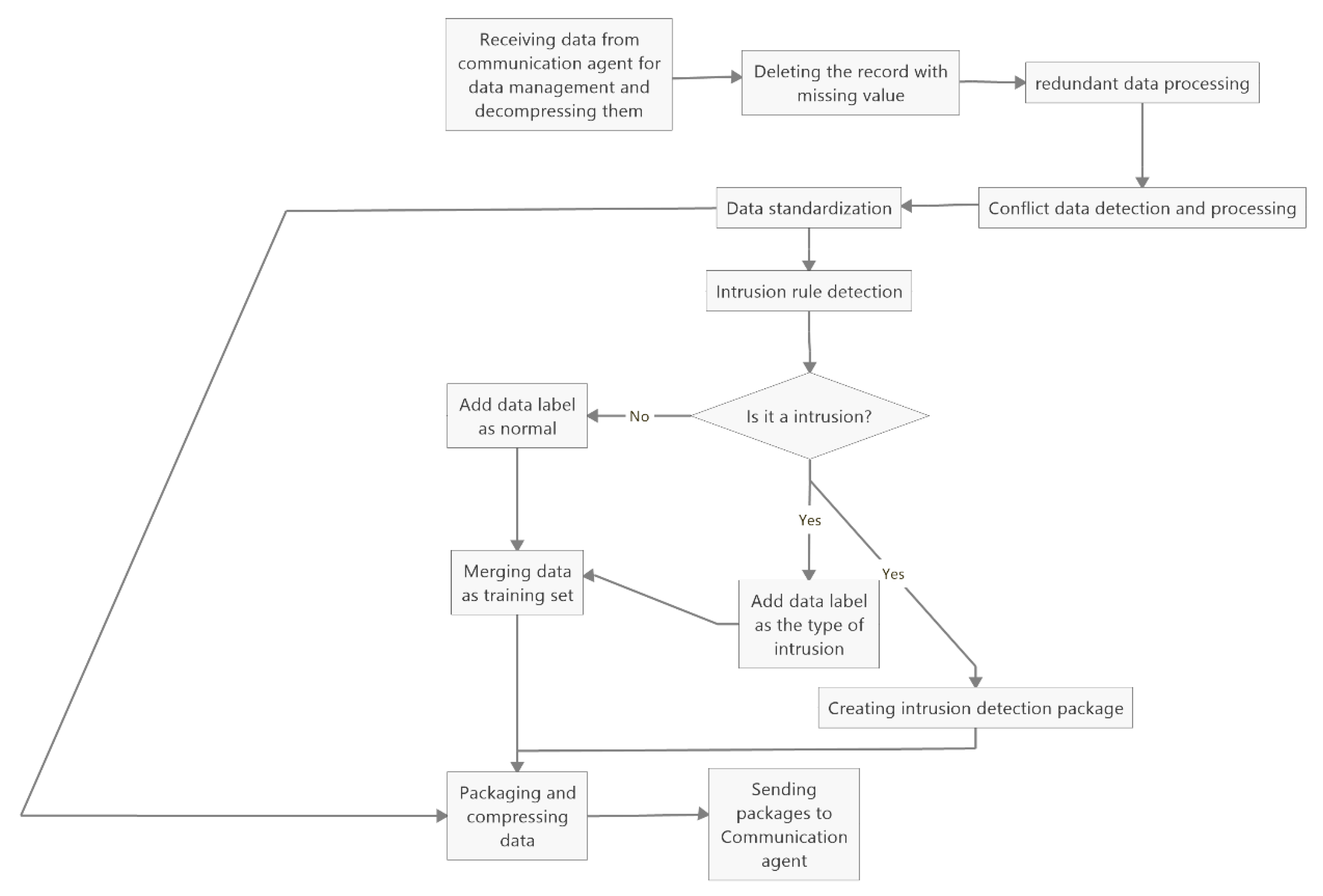
3.2.4. Data Process Module
4. Experimental Analysis
4.1. Dataset
4.2. Evaluation Measures
4.3. Pre-Processing
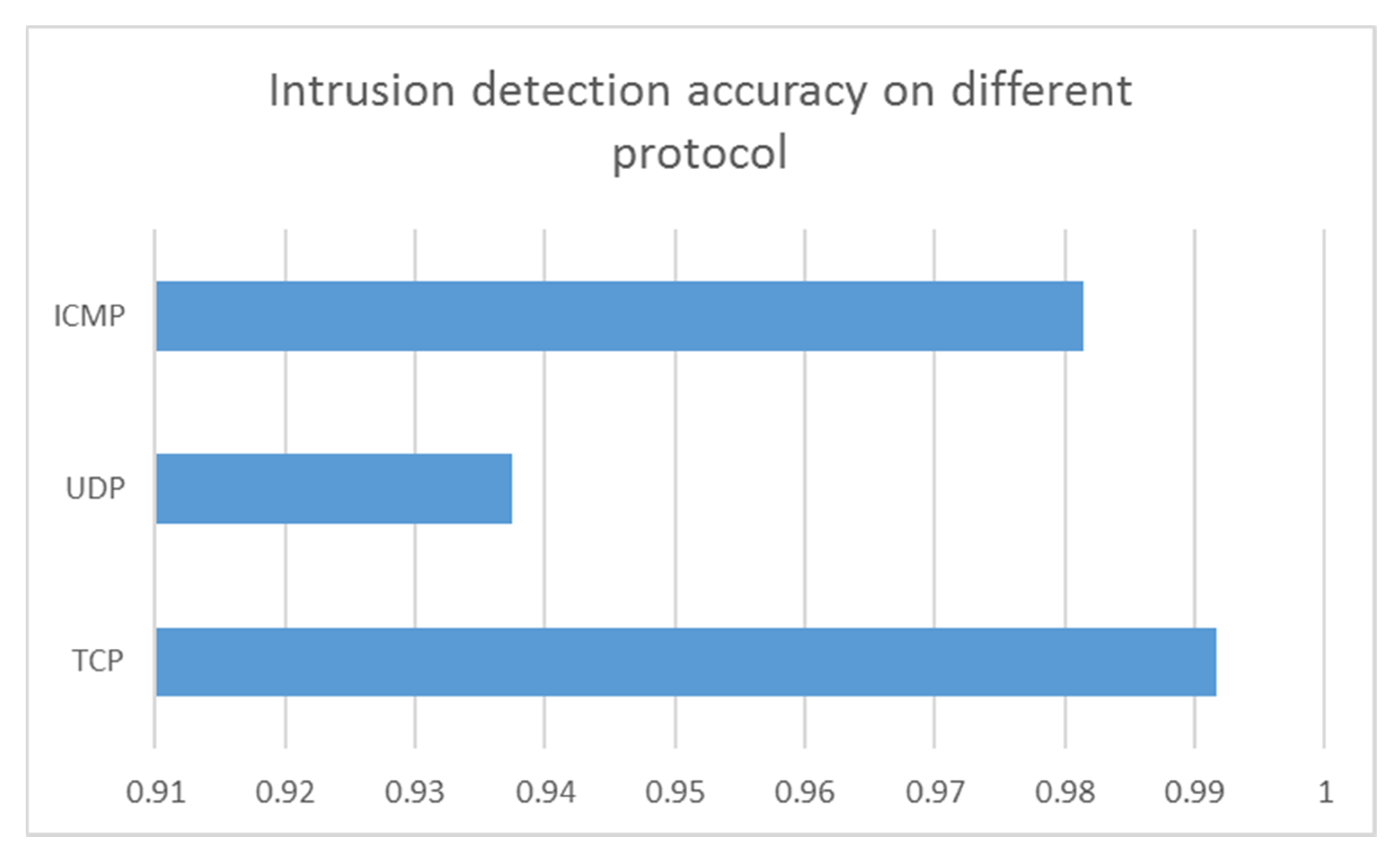
4.4. Findings and Discussions
4.5. Limitations
5. Conclusions
Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Adat, V.; Gupta, B. Security in Internet of Things: Issues, challenges, taxonomy, and architecture. Model. Anal. Des. Manag. 2018, 67, 423–441. [Google Scholar] [CrossRef]
- Statista Research Department. IoT: Number of connected devices worldwide 2012–2025. Available online: https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/ (accessed on 20 May 2020).
- Tahaei, H.; Afifi, F.; Asemi, A.; Zaki, F.; Anuar, N.B. The rise of traffic classification in IoT networks: A survey. J. Netw. Comput. Appl. 2020, 154. [Google Scholar] [CrossRef]
- Hajiheidari, S.; Wakil, K.; Badri, M.; Navimipour, N.J. Intrusion detection systems in the Internet of things: A comprehensive investigation. Comput. Netw. 2019, 160, 165–191. [Google Scholar] [CrossRef]
- Samaila, M.; Neto, M.; Fernandes, D.; Freire, M.; Inácio, P. Challenges of securing Internet of Things devices: A survey. Secur. Priv. 2018, 1. [Google Scholar] [CrossRef]
- Bhattarai, S.; Wang, Y. End-to-End Trust and Security for Internet of Things Applications. Computer 2018, 51, 20–27. [Google Scholar] [CrossRef]
- Spafford, E.; James, P. Anderson: An Information Security Pioneer. IEEE Secur. Priv. 2008, 6, 9. [Google Scholar] [CrossRef][Green Version]
- Alnaghes, M.S.; Gebali, F. A Survey on Some Currently Existing Intrusion Detection Systems for Mobile Ad Hoc Networks. In Proceedings of the Second International Conference on Electrical and Electronics Engineering, Clean Energy and Green Computing (EEECEGC2015), Antalya, Turkey, 26–28 May 2015; Volume 12. [Google Scholar]
- Hari, P.B.; Singh, S.N. Security Attacks at MAC and Network Layer in Wireless Sensor Networks. J. Adv. Res. Dyn. Control Syst. 2019, 11, 82–89. [Google Scholar] [CrossRef]
- Pacheco, J.; Hariri, S. IoT Security Framework for Smart Cyber Infrastructures. In Proceedings of the IEEE 1st International Workshops on Foundations and Applications of Self* Systems (FAS*W), Augsburg, Germany, 12–16 September 2016; pp. 242–247. [Google Scholar] [CrossRef]
- Liu, C.; Yang, J.; Chen, R.; Zhang, Y.; Zeng, J. Research on immunity-based intrusion detection technology for the Internet of Things. In Proceedings of the 2011 Seventh International Conference on Natural, Shanghai, China, 26–28 July 2011. [Google Scholar]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Wallgren, L.; Raza, S.; Voigt, T. Routing Attacks and Countermeasures in the RPL-Based Internet of Things. Int. J. Distrib. Sens. Netw. 2013, 9, 794326. [Google Scholar]
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time intrusion detection in the Internet of Things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Zegzhda, P.; Kort, S. Host-Based Intrusion Detection System: Model and Design Features. In Proceedings of the International Conference on Mathematical Methods, Models, and Architectures for Computer Network Security, St. Petersburg, Russia, 13–15 September 2007; pp. 340–345. [Google Scholar]
- Chakravarthi, S.S.; Veluru, S. A Review on Intrusion Detection Techniques and Intrusion Detection Systems in MANETs. In Proceedings of the International Conference on Computational Intelligence and Communication Networks, Bhopal, India, 14–16 November 2014. [Google Scholar]
- Santos, L.; Rabadao, C.; Goncalves, R. Intrusion detection systems in Internet of Things: A literature review. In Proceedings of the 13th Iberian Conference on Information Systems and Technologies (Cisti), Caceres, Spain, 13–16 June 2018. [Google Scholar]
- Mohamed, A.B.; Idris, N.B.; Shanmugum, B. A Brief Introduction to Intrusion Detection System. In Trends in Intelligent Robotics, Automation, and Manufacturing, Proceedings of the IRAM 2012, Kuala Lumpur, Malaysia, 28–30 November 2012; Communications in Computer and Information Science; Ponnambalam, S.G., Parkkinen, J., Ramanathan, K.C., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 330. [Google Scholar]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Bostani, H.; Sheikhan, M. Hybrid of anomaly-based and specification-based IDS for Internet of Things using unsupervised OPF based on MapReduce approach. Comput. Commun. 2017, 98, 52–71. [Google Scholar] [CrossRef]
- Fu, Y.; Yan, Z.; Cao, J.; Koné, O.; Cao, X. An Automata Based Intrusion Detection Method for Internet of Things. Mob. Inf. Syst. 2017, 2017, 1750637. [Google Scholar] [CrossRef]
- Kapitonov, A.; Lonshakov, S.; Krupenkin, A.; Berman, I. Blockchain-based protocol of autonomous business activity for multi-agent systems consisting of UAVs. In Proceedings of the Workshop on Research, Education and Development of Unmanned Aerial Systems (RED-UAS), Linkoping, Sweden, 3–5 October 2017; pp. 84–89. [Google Scholar] [CrossRef]
- Calvaresi, D.; Calbimonte, J.P.; Dubovitskaya, A.; Mattioli, V.; Piguet, J.G.; Schumacher, M. The Good, the Bad, and the Ethical Implications of Bridging Blockchain and Multi-Agent Systems. Information 2019, 10, 363. [Google Scholar] [CrossRef]
- Calvaresi, D.; Dubovitskaya, A.; Calbimonte, J.P.; Taveter, K.; Schumacher, M. Multi-Agent Systems and Blockchain: Results from a Systematic Literature Review. In Proceedings of the International Conference on Practical Applications of Agents and Multi-Agent Systems, Toledo, Spain, 20–22 June 2018. [Google Scholar]
- Shi, H.; Zhai, L.; Wu, H.; Hwang, M.; Hwang, K.; Hsu, H. A Multi-tier Reinforcement Learning Model for a Cooperative Multi-agent System. IEEE Trans. Cogn. Dev. Syst. 2020. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Duong, T.; Todi, K.K.; Chaudhary, U.; Truong, H. Decentralizing Air Traffic Flow Management with Blockchain-based Reinforcement Learning. In Proceedings of the IEEE 17th International Conference on Industrial Informatics (INDIN), Helsinki, Finland, 23–25 July 2019; pp. 1795–1800. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Prieta, F.D.L.; Prieto, J.; Corchado, J.M. Blockchain framework for IoT data quality via edge computing. In Proceedings of the BlockSys’18: 1st Workshop on Blockchain-enabled Networked Sensor System 2018, Shenzhen, China, 4 November 2018. [Google Scholar] [CrossRef]
- Li, D.; Deng, L.; Lee, M.; Wang, H. IoT data feature extraction and intrusion detection system for smart cities based on deep migration learning. Int. J. Inf. Manag. 2019, 49, 533–545. [Google Scholar] [CrossRef]
- Le, T.-T.-H.; Kim, Y.; Kim, H. Network Intrusion Detection Based on Novel Feature Selection Model and Various Recurrent Neural Networks. Appl. Sci. 2019, 9, 1392. [Google Scholar] [CrossRef]
- Arshad, J.; Azad, M.A.; Abdeltaif, M.M.; Salah, K. An intrusion detection framework for energy constrained IoT devices. Mech. Syst. Signal Process. 2020, 136, 106436. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Slowinska, M.; Theodorakopoulos, G.; Burnap, P. A Supervised Intrusion Detection System for Smart Home IoT Devices. IEEE Internet Things J. 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C.; Faruki, P. Network Intrusion Detection for IoT Security Based on Learning Techniques. IEEE Commun. Surv. Tutor. 2019, 21, 2671–2701. [Google Scholar] [CrossRef]
- Liang, C.; Shanmugam, B.; Azam, S.; Jonkman, M.; Boer, F.D.; Narayansamy, G. Intrusion Detection System for Internet of Things based on a Machine Learning approach. In Proceedings of the International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Savaglio, C.; Fortino, G.; Ganzha, M.; Paprzycki, M.; Badica, C.; Ivanovic, M. Agent-based Internet of Things: State-of-the-art and research challenges. Future Gener. Comput. Syst. 2019, 102. [Google Scholar] [CrossRef]
- Pipattanasomporn, M.; Feroze, H.; Rahman, S. Multi-agent systems in a distributed smart grid: Design and implementation. In Proceedings of the IEEE/PES Power Systems Conference & Exposition, Seattle, WA, USA, 15–18 March 2009. [Google Scholar]
- Fortino, G.; Russo, W.; Savaglio, C. Agent-oriented modeling and simulation of IoT networks. In Proceedings of the Federated Conference on Computer Science and Information Systems (FedCSIS), Gdansk, Poland, 11–14 September 2016; pp. 1449–1452. [Google Scholar]
- Wang, S.; Wan, J.; Zhang, D.; Li, D.; Zhang, C. Towards smart factory for industry 4.0: A self-organized multi-agent system with big data based feedback and coordination. Comput. Netw. 2016, 101, 158–168. [Google Scholar] [CrossRef]
- Bellifemine, F.L.; Caire, G.; Greenwood, D. Developing Multi-Agent Systems with JADE; Wiley: Hoboken, NJ, USA, 2007. [Google Scholar]
- Nguyen, L.C.; Nguyen-Xuan, H. Deep learning for computational structural optimization. ISA Trans. 2020, in press. [Google Scholar] [CrossRef] [PubMed]
- Schmidhuber, J. Deep learning in neural networks: An overview. Neural Netw. 2015, 61, 85–117. [Google Scholar] [CrossRef] [PubMed]
- Saleh, A.J.; Karim, A.; Shanmugam, B.; Azam, S.; Kannoorpatti, K.; Jonkman, M.; Boer, F.D. An Intelligent Spam Detection Model Based on Artificial Immune System. Information 2019, 10, 209. [Google Scholar] [CrossRef]
- Mnih, V.; Kavukcuoglu, K.; Silver, D.; Rusu, A.A.; Veness, J.; Bellemare, M.G.; Graves, A.; Riedmiller, M.; Fidjeland, A.K.; Ostrovski, G.; et al. Human-level control through deep reinforcement learning. Nature 2015, 518, 529–533. [Google Scholar] [CrossRef]
- Zilberstein, S. Book Review: “Multiagent Systems: A Modern Approach to Distributed Artificial Intelligence”, Gerhard Weiss. Int. J. Comput. Intell. Appl. 2001, 1, 331–334. [Google Scholar] [CrossRef]
- Vokerla, R.R.; Shanmugam, B.; Azam, S.; Karim, A.; Boer, F.D.; Jonkman, M.; Faisal, F. An Overview of Blockchain Applications and Attacks. In Proceedings of the International Conference on Vision Towards Emerging Trends in Communication and Networking (Vitecon), Vellore, India, 30–31 March 2019. [Google Scholar]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The Blockchain Model of Cryptography and Privacy-Preserving Smart Contracts. In Proceedings of the IEEE Symposium on Security and Privacy (Sp), San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Sun, T.; Yu, W. A Formal Verification Framework for Security Issues of Blockchain Smart Contracts. Electronics 2020, 9, 255. [Google Scholar] [CrossRef]
- Košt’ál, K.; Helebrandt, P.; Belluš, M.; Ries, M.; Kotuliak, I. Management and Monitoring of IoT Devices Using Blockchain. Sensors 2019, 19, 856. [Google Scholar] [CrossRef]
- Carstensen, A.-K.; Bernhard, J. Design science research—A powerful tool for improving methods in engineering education research. Eur. J. Eng. Educ. 2019, 44, 85–102. [Google Scholar] [CrossRef]
- Github Code. Available online: https://github.com/aymwxbb2012/intrusion_detection_system_SESS/tree/develop (accessed on 30 May 2020).
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009. [Google Scholar]
- Dhanabal, L.; Shantharajah, S.P. Intrusion Detection and Classification Using Hybrid Support Vector Machine and Dynamic Ant Colony Algorithm. Aust. J. Basic Appl. Sci. 2015, 9, 328–335. [Google Scholar]
- Manjula, B.; Balachandra, M. Performance Evaluation of Supervised Machine Learning Algorithms for Intrusion Detection. Procedia Comput. Sci. 2016, 89, 117–123. [Google Scholar] [CrossRef]
- IoT Data Simulator. Available online: https://assetwolf.com/learn/iot-data-simulator (accessed on 30 May 2020).

| Major Attack Types | Attack Types |
|---|---|
| DOS | Back, Land, Neptune, Pod, smurf, teardrop |
| Probe | Satan, IPsweep, Nmap, portsweep |
| R2L | ftp_write, phf, multihop, warezmaster, guess_passwd, warezclient, imap, spy |
| U2R | buffer_overflow, loadmodule, rootkit |
| Major Attack Types | Attack Types |
|---|---|
| DOS | Back, Land, Neptune, Pod, smurf, teardrop, mailbomb, processtable, udpstorm, apache2 |
| Probe | Satan, IPsweep, Nmap, portsweep, mscan, saint |
| R2L | Warezmaster, xsnoop, snmpguess, snmpgetattack, httptunnel, sendmail, named, guess_passwd |
| U2R | buffer_overflow, rootkit |
| Batch Size | Batch Number | Epoch | Accuracy on Validation Set | Accuracy on Test Set |
|---|---|---|---|---|
| 32 | 300 | 50 | 98.46% | 80.33% |
| 32 | 300 | 100 | 98.51% | 82.92% |
| 32 | 300 | 150 | 98.47% | 81.92% |
| 32 | 300 | 200 | 98.52% | 82.42% |
| 32 | 300 | 250 | 98.44% | 82.25% |
| 32 | 300 | 300 | 98.45% | 82.67% |
| Batch Size | Batch Number | Epoch | Accuracy on Validation Set | Accuracy on Test Set |
|---|---|---|---|---|
| 32 | 50 | 100 | 97.36% | 77.58% |
| 32 | 100 | 100 | 97.83% | 78.83% |
| 32 | 150 | 100 | 98.07% | 80.25% |
| 32 | 200 | 100 | 98.29% | 81.00% |
| 32 | 250 | 100 | 98.34% | 80.17% |
| 32 | 300 | 100 | 98.51% | 82.92% |
| 32 | 350 | 100 | 98.44% | 80.67% |
| 32 | 400 | 100 | 98.47% | 80.92% |
| Batch Size | Batch Number | Epoch | Accuracy on Validation Set | Accuracy on Test Set |
|---|---|---|---|---|
| 16 | 300 | 100 | 98.09% | 81.25% |
| 32 | 300 | 100 | 98.51% | 82.92% |
| 48 | 300 | 100 | 98.27% | 83.17% |
| 64 | 300 | 100 | 98.54% | 80.42% |
| 80 | 300 | 100 | 98.67% | 79.83% |
| Training set | AV | PV | RV | FV | AT | PT | RT | FT |
|---|---|---|---|---|---|---|---|---|
| Train+ | 98.27% | 98.27% | 98.24% | 98.12% | 83.17% | 83.53% | 84.14% | 83.94% |
| Test+ | 97.48% | 97.69% | 97.22% | 97.81% | 91.50% | 91.53% | 91.77% | 91.21% |
| Data Splitting Conditions | Accuracy on Validation Set AV% | Accuracy on Test Set AT% |
|---|---|---|
| 98.27 | 83.17 |
| 97.48 | 91.50 |
| SL# | Attribute Name | Description |
|---|---|---|
| 1 | Duration | Length of time duration of the connection |
| 2 | Protocol_type | Protocol used in the connection |
| 3 | Service | Destination network service used |
| 4 | Flag | Status of the connection—Normal or Error |
| 5 | Src_bytes | Number of data bytes transferred from source to destination in single connection |
| 6 | Dst_bytes | Number of data bytes transferred from destination to source in single connection |
| 7 | Land | If source and destination IP addresses and port numbers are equal then, this variable takes value 1 else 0 |
| 8 | Wrong_fragment | Total number of wrong fragments in this connection |
| 9 | Urgent | Number of urgent packets in this connection. Urgent packets are packets with the urgent bit activated |
| 10 | Hot | Number of ‘hot’ indicators in the content such as: entering a system directory, creating programs and executing programs |
| 11 | Num_failed_logins | Count of failed login attempts |
| 12 | Logged_in | Login Status: 1 if successfully logged in; 0 otherwise |
| 13 | Num_comp romised | Number of ‘compromised’ conditions’ |
| 14 | Root_shell | 1 if root shell is obtained; 0 otherwise |
| 15 | Su_attempted | 1 if ‘su root’ command attempted or used; 0 otherwise |
| 16 | Num_root | Number of ‘root’ accesses or number of operations performed as a root in the connection |
| 17 | Num_file_creations | Number of file creation operations in the connection |
| 18 | Num_shells | Number of shell prompts |
| 19 | Num_access_files | Number of operations on access control files |
| 20 | Num_outbo und_cmds | Number of outbound commands in an FTP session |
| 21 | Is_hot_login | 1 if the login belongs to the ‘hot’ list i.e., root or admin; else 0 |
| 22 | Is_guest_login | 1 if the login is a ‘guest’ login; 0 otherwise |
| 23 | Count | Number of connections to the same destination host as the current connection in the past two seconds |
| 24 | Srv_count | Number of connections to the same service (port number) as the current connection in the past two seconds |
| 25 | Serror_rate | The percentage of connections that have activated the flag (4) s0, s1, s2 or s3, among the connections aggregated in count (23) |
| 26 | Srv_serror_rate | The percentage of connections that have activated the flag (4) s0, s1, s2 or s3, among the connections aggregated in srv_count (24) |
| 27 | Rerror_rate | The percentage of connections that have activated the flag (4) REJ, among the connections aggregated in count (23) |
| 28 | Srv_rerror_rate | The percentage of connections that have activated the flag (4) REJ, among the connections aggregated in srv_count (24) |
| 29 | Same_srv_rate | The percentage of connections that were to the same service, among the connections aggregated in count (23) |
| 30 | Diff_srv_rate | The percentage of connections that were to different services, among the connections aggregated in count (23) |
| 31 | Srv_diff_host_rate | The percentage of connections that were to different destination machines among the connections aggregated in srv_count (24) |
| 32 | Dst_host_count | Number of connections having the same destination host IP address |
| 33 | Dst_host_srv_count | Number of connections having the same port number |
| 34 | Dst_host_same_srv_rate | The percentage of connections that were to the same service, among the connections aggregated in dst_host_count (32) |
| 35 | Dst_host_diff_ srv_rate | The percentage of connections that were to different services, among the connections aggregated in dst_host_count (32) |
| 36 | Dst_host_same_src_port_rate | The percentage of connections that were to the same source port, among the connections aggregated in dst_host_srv_count (33) |
| 37 | Dst_host_srv_diff_host_rate | The percentage of connections that were to different destination machines, among the connections aggregated in dst_host_srv_count (33) |
| 38 | Dst_host_serror_rate | The percentage of connections that have activated the flag (4) s0, s1, s2 or s3, among the connections aggregated in dst_host_count (32) |
| 39 | Dst_host_srv_s error_rate | The percent of connections that have activated the flag (4) s0, s1, s2 or s3, among the connections aggregated in dst_host_srv_count (33) |
| 40 | Dst_host_erro r_rate | The percentage of connections that have activated the flag (4) REJ, among the connections aggregated in dst_host_count (32) |
| 41 | Dst_host_srv_r error_rate | The percentage of connections that have activated the flag (4) REJ, among the connections aggregated in dst_host_srv_count (33) |
| Number of Parameters | Parameters Included | AV | PV | RV | FV | AT | PT | RT | FT |
|---|---|---|---|---|---|---|---|---|---|
| 41 | [1–41] | 98.27% | 98.27% | 98.24% | 98.12% | 83.17% | 83.53% | 84.14% | 83.94% |
| 40 | [1–2], [4–41] | 98.85% | 98.84% | 98.85% | 98.76% | 82.33% | 84.04% | 84.00% | 82.30% |
| 25 | [1–2], [4–6], [12], [23–41] | 97.82% | 97.84% | 97.77% | 97.63% | 80.75% | 82.56% | 82.45% | 80.64% |
| 17 | [1–2], [4–6], [12], [23–24], [29], [32–39] | 97.88% | 97.92% | 97.81% | 97.69% | 81.33% | 83.13% | 83.03% | 81.24% |
| 7 | [1–2], [4–6], [23–24] | 95.10% | 95.21% | 94.96% | 94.62% | 78.08% | 78.19% | 78.75% | 79.37% |
| 6 | [1–2], [5–6], [23–24] | 93.53% | 93.87% | 93.25% | 92.75% | 72.67% | 79.45% | 68.74% | 80.15% |
| 5 | [2], [5–6], [23–24] | 92.67% | 93.16% | 92.32% | 91.71% | 72.33% | 79.23% | 68.35% | 79.95% |
| 4 | [2], [5–6], [23] | 90.40% | 91.45% | 89.84% | 88.80% | 73.92% | 75.68% | 71.31% | 79.71% |
| 3 | [2], [5–6] | 58.15% | 69.92% | 54.95% | 20.87% | 71.75% | 78.83% | 67.67% | 79.62% |
| 2 | [5–6] | 84.27% | 86.25% | 85.16% | 85.12% | 68.50% | 71.95% | 64.68% | 76.89% |
| 1 | [6] | 53.72% | 53.72% | 50.00% | 0.00% | 43.00% | 43.00% | 50.00% | 0.00% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liang, C.; Shanmugam, B.; Azam, S.; Karim, A.; Islam, A.; Zamani, M.; Kavianpour, S.; Idris, N.B. Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent Systems. Electronics 2020, 9, 1120. https://doi.org/10.3390/electronics9071120
Liang C, Shanmugam B, Azam S, Karim A, Islam A, Zamani M, Kavianpour S, Idris NB. Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent Systems. Electronics. 2020; 9(7):1120. https://doi.org/10.3390/electronics9071120
Chicago/Turabian StyleLiang, Chao, Bharanidharan Shanmugam, Sami Azam, Asif Karim, Ashraful Islam, Mazdak Zamani, Sanaz Kavianpour, and Norbik Bashah Idris. 2020. "Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent Systems" Electronics 9, no. 7: 1120. https://doi.org/10.3390/electronics9071120
APA StyleLiang, C., Shanmugam, B., Azam, S., Karim, A., Islam, A., Zamani, M., Kavianpour, S., & Idris, N. B. (2020). Intrusion Detection System for the Internet of Things Based on Blockchain and Multi-Agent Systems. Electronics, 9(7), 1120. https://doi.org/10.3390/electronics9071120







