1. Introduction
Data hiding is one of the techniques used for securing data, apart from encrypting data. In data encryption technique, the original data are converted into a non-interpretable form so that adversary cannot extract any useful information. In data hiding, additional data are embedded into the carrier cover media (text, audio, video and image) in such a way that they remain concealed and can be extracted from the cover media later. Cover media is the original media that is used to carry additional data.
However, it is notable that, in data hiding, when data are extracted from the cover media, some form of distortion remains in the recovered cover media. In some scenarios (e.g., medical and satellite imagery), distortion in the cover image is inadmissible. That is, the image to be recovered on the receiver’s side needs to be lossless. To cope with this problem, several reversible data hiding (RDH) techniques have been proposed. RDH is a technique to manipulate pixel bits of the cover image to create some space for embedding the additional data into the cover image, where both the additional data and the original cover image can be recovered completely. This is done while maintaining the perceptible quality of the carrier media. RDH schemes can be broadly classified into three categories: difference expansion [
1], lossless compression [
2] and histogram shifting [
3].
With the growth of cloud-based applications [
4,
5], data outsourcing is one of the fields where the users are dependent on cloud for processing and storage. Security concern of the data owners using cloud for the cover media is addressed using encryption for the cover image. For the sake of management (using timestamp, tagging, image source information, etc.) of the encrypted media, the data hider embeds some additional data into the encrypted image. To achieve security and reversibility, the technique of RDH is used in the encrypted domain.
Reversible data hiding in encrypted images (RDHEI) is a method where additional data are embedded by the data hider into the encrypted cover image (obtained from the content-owner) to obtain marked encrypted image. This marked encrypted image is sent to the receiver, where recovery of both additional data and the cover image from the marked encrypted image is made losslessly.
Many RDHEI schemes based on the symmetric key have been proposed until now. In symmetric key cryptography, there is only one secret-key for both encryption and decryption, and key management is needed to share the secret key between the sender and the receiver. Some of the RDH schemes based on symmetric key cryptography are discussed below.
In 2008, Puech et al. [
6] proposed the first RDHEI scheme where the Advanced Encryption Standard (AES) is used for encryption. Here, the encrypted image is divided into non-overlapping blocks of n-pixels each, and each block is responsible to carry one bit of additional data. The local standard deviation of the marked encrypted image is used to retrieve additional data on the receiver’s side. In 2011, Zhang [
7] successfully recovered an image similar to the original image with a secret key, which is encrypted using a stream cipher. With the help of data hiding key and spatial co-relation in the image, additional data and original image are recovered losslessly. Embedding is done using a two-step block division of the encrypted original image, and using least significant bit (LSB) flipping to identify the type of embedded bit (0 or 1). Hong et al. [
8] improved Zhang’s scheme [
7] by exploiting the correlations in neighboring border pixels, which were not taken into consideration by Zhang [
7].
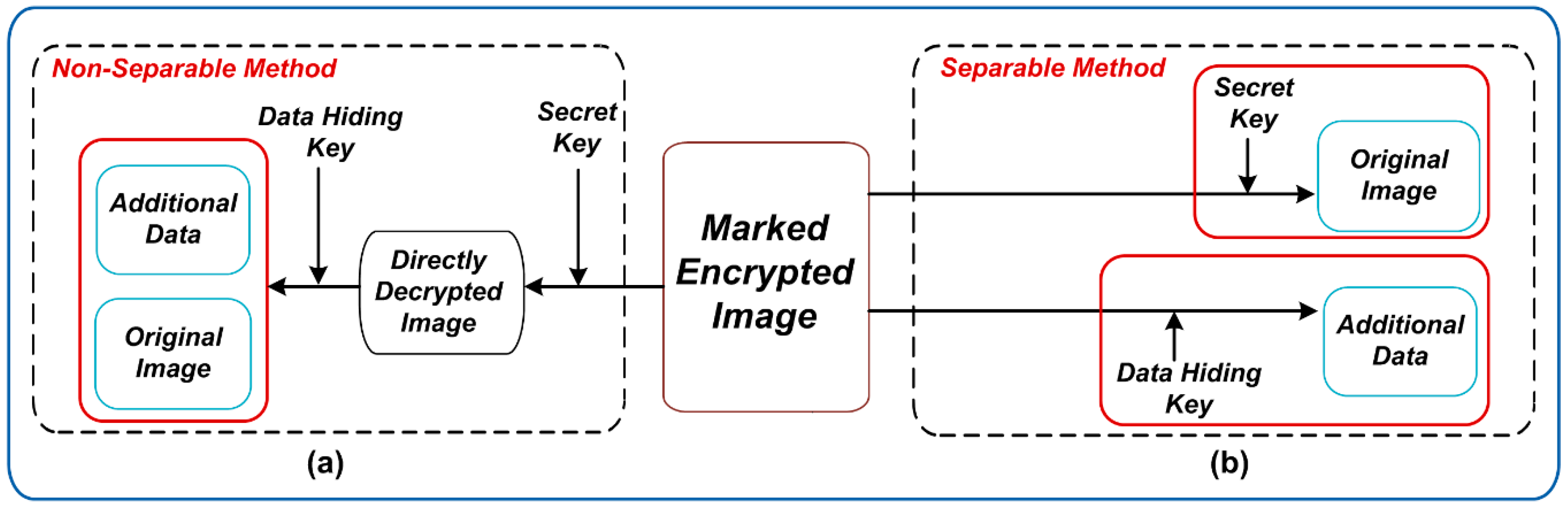
At the receiver side, additional data in RDHEI are broadly recovered in two ways, namely non-separable and separable techniques, which are respectively depicted in
Figure 1a,b. To extract the additional data from the marked encrypted image using the aforementioned schemes, the receiver must have the data-hiding key and the secret key. As the additional data can only be extracted after image decryption, this type of schemes falls under the category of non-separable RDHEI, as depicted in
Figure 1a, where the additional data cannot be extracted without decrypting the marked encrypted image.
Figure 1b depicts the separable method used in RDHEI, where the receiver can extract the additional data independent of image decryption, with the use of data hiding key only. The original image can be recovered by only using the secret key.
Zhang [
9] proposed the first separable RDHEI method in 2012. RDHEI methods are fit for the cloud applications, where the data hider using the cloud can embed additional data for the sake of management. In addition, the receiver can extract additional data without knowing the content of the original image. The privacy of the cover image is still preserved as the additional data can be extracted without image decryption. Yin et al. [
10] proposed a separable RDHEI scheme by breaking the cover image into non-overlapping blocks and the additional data are embedded into the blocks using block smoothness order and peak points.
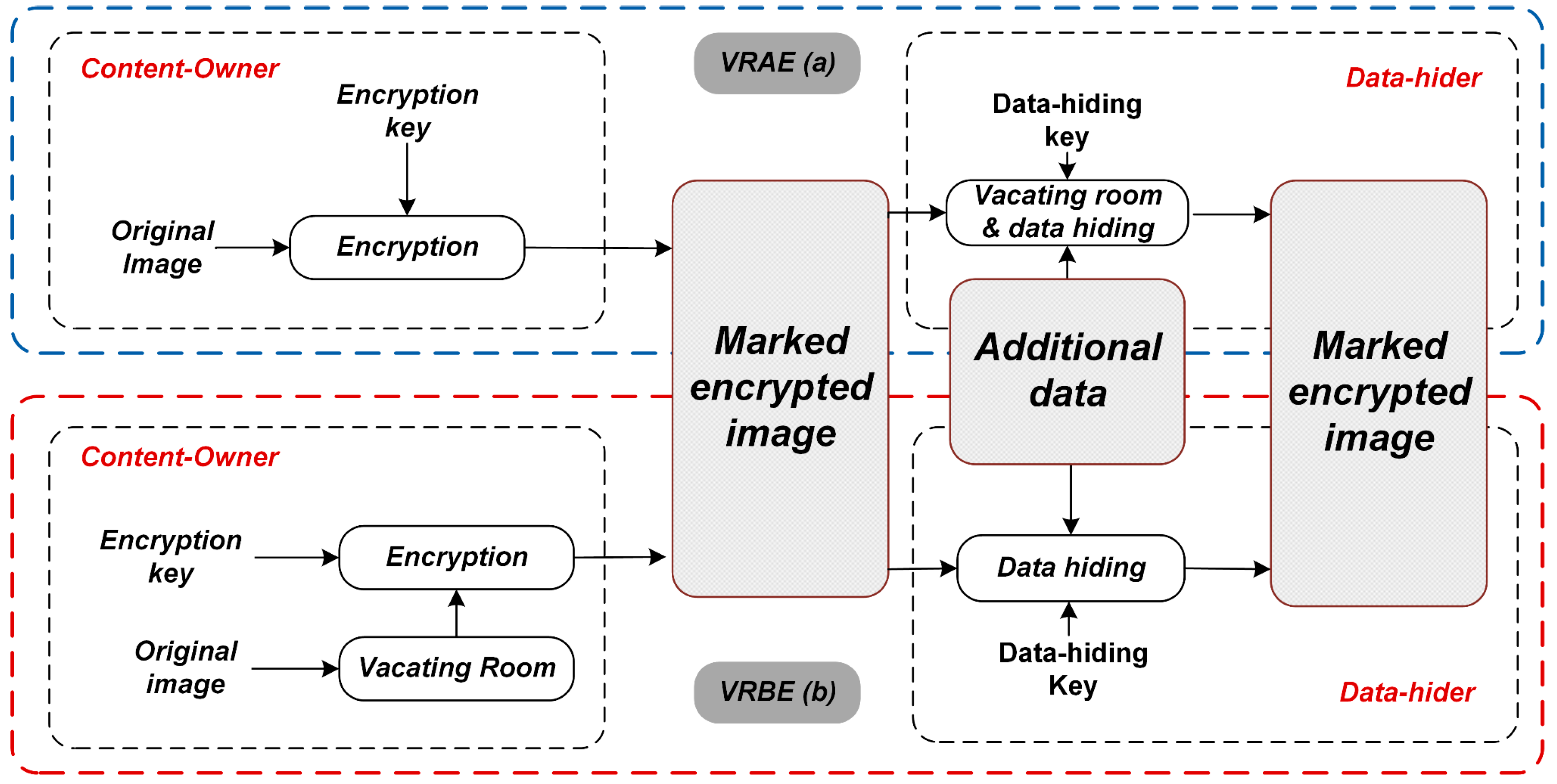
Generally, at the content-owner’s side, creating space for embedding data is done mainly in two ways: Vacating room after encryption (VRAE) (
Figure 2a) and vacating room before encryption (VRBE) (
Figure 2b). In VRAE, the space to embed additional data by the data hider is created after the image encryption. However, in VRBE, the space to embed additional data by the data hider is created before the image encryption. The framework followed by the above schemes is VRAE.
After the image encryption, entropy rises, which allows less space for payload (additional data). To tackle this problem, Ma et al. [
11] proposed the first VRBE scheme by preprocessing the cover image, using traditional RDH scheme. Zhang et al. [
12] preprocessed the cover image by estimating some pixels in the cover image. Then, they embedded additional data by using histogram shifting for estimated prediction errors.
Qian et al. [
13] significantly enhanced image quality and embedding rate using histogram modification, based on n-nary histogram intensities. However, the image histogram leakage reduced image security. Zhang et al. [
14] embedded compressed additional data into an encrypted image using low-density parity check code. Zheng et al. [
15] compressed the pixel LSBs, in the chaotic-encrypted image, using Hamming distance to embed data. Cao et al. [
16] used patch level sparse representation to embed data, using the sparse coding technique. Self-embedding of leading residual errors and embedding over-complete dictionary (created by using sparse coefficients to represent cover image) into the encrypted image is used in this technique.
Recently, public key cryptography is used for efficient key management over cloud [
17,
18], specifically in RDHEI [
19,
20,
21,
22,
23,
24]. In asymmetric key (or public key) cryptography, the key for encryption (public-key) and the key for decryption (private-key) are different. In the context of RDHEI using public-key, Chen et al. [
19] proposed the first signal based reversible data hiding, for multiple signals and data hiders, using Paillier cryptosystem [
25]. Shiu et al. [
20] improved the work of Chen et al. [
19], having a drawback of inherent overflow, by grouping 64-pixels of the encrypted image followed by compression. Li et al. [
21] used difference histogram shifting based on the additive homomorphic property to embed additional data. Wei et al. [
22] enhanced the work of Li et al. [
21], by taking the cross-shaped division mask instead of block-based division mask to use all the embedding opportunities. Zhang et al. [
23] proposed reversible and lossless RDHEI in public-key, with better performance in terms of PSNR of the directly decrypted image compared to some of the previous schemes.
Tai et al. [
24] proposed RDHEI scheme based on Paillier’s cryptosystem. Here, the image is preprocessed before encryption by dividing each pixel into two parts, called encrypted units:
and
. The order of the two encrypted parts of a pixel, namely
and
, is exploited to embed the bits of additional data in the data hiding phase. If the additional bit to be embedded is 1 and
, then swap
and
. If the additional bit to be embedded is 0 and
, then swap
and
. On the receiver side, the additive homomorphic property of Paillier’s cryptosystem is used to recover the original image losslessly. Again, the order of the two encrypted parts,
and
, is used to extract the bits of additional data from the encrypted image. In [
24], the image is preprocessed before encryption and this makes the content-owner to send double the size of image to the data hider. This issue is the one addressed in our proposed scheme.
In this paper, an efficient separable reversible data hiding scheme for encrypted images is proposed. It enjoys the benefits of using Paillier cryptosystem [
25], which provides privacy preserving advantage over the cloud. The usage of our scheme befits cloud domain. Thus, a real-life application scenario of the proposed scheme over cloud is vividly explained in
Section 3.6. Paillier’s cryptosystem is used to encrypt the original image with the public key. When the encrypted image is received by the data hider, the data-hiding key and the public key is used to embed additional data into the encrypted image to obtain marked encrypted image. The additional data and the original image are recovered losslessly at the receiver’s side using respective data hiding and private keys, independent of each other. This is done in a separable manner, which means for embedded additional data extraction, encrypted image is not required to be decrypted and vice versa.
After the brief discussion of previous schemes, we move on to a brief introduction to Paillier’s public key cryptosystem in
Section 2. In
Section 3, the proposed scheme is discussed with an example. Experimental results and discussions are covered in
Section 4. Finally, a conclusion is drawn in
Section 5.
3. Proposed Scheme
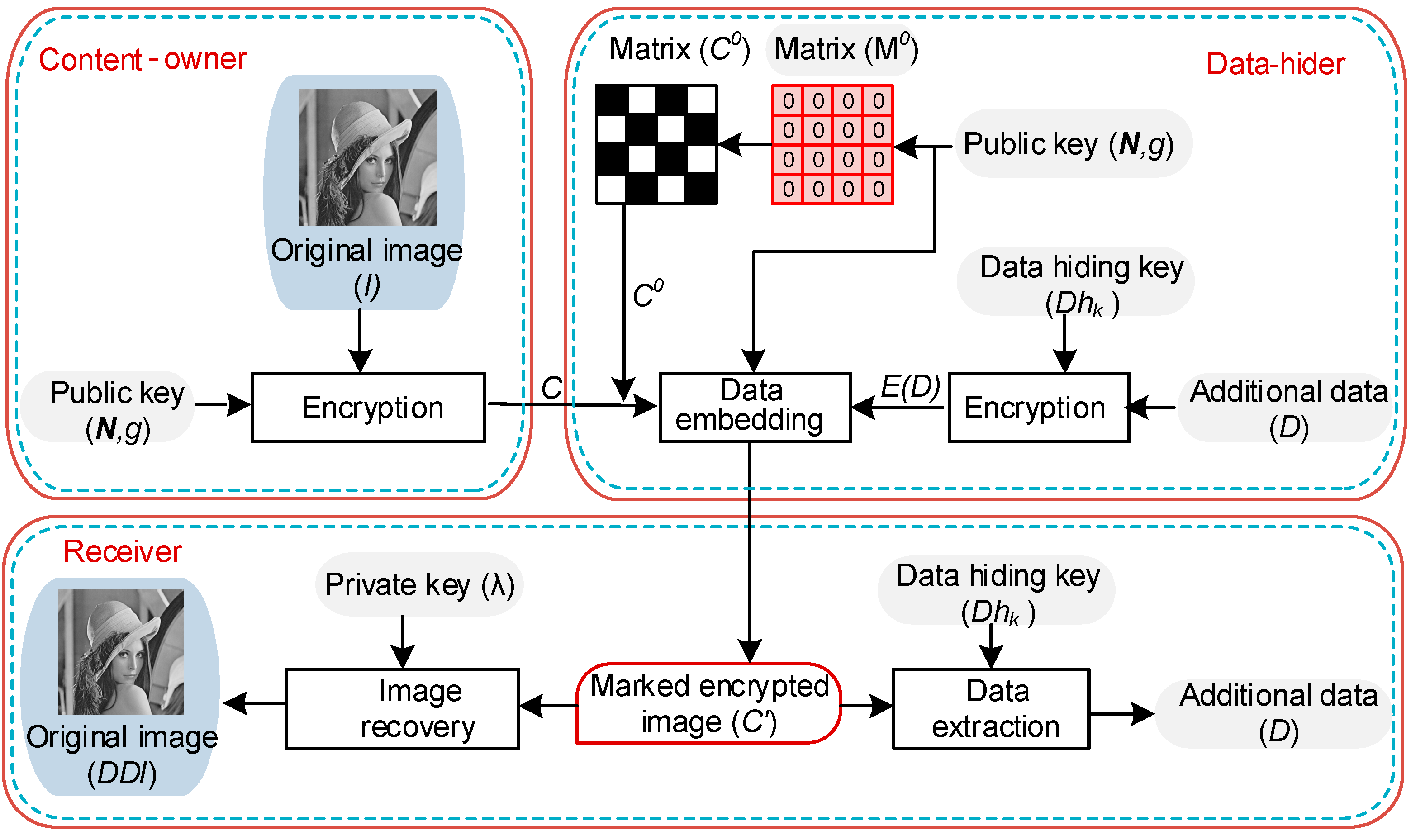
The idea of our scheme is based on the separable method, as illustrated in
Figure 3. The notations used in the proposed scheme are denoted in
Table 1. It comprises of three stakeholders: the content-owner, the data-hider, and the receiver.
Data-hider uses to encrypt the additional data and uses to embed the encrypted additional data into the encrypted image. At the receiver’s end, additional data are recovered from the marked encrypted image using , and the original image is completely recovered in a separable manner, using owned by the receiver.
3.1. Image Encryption
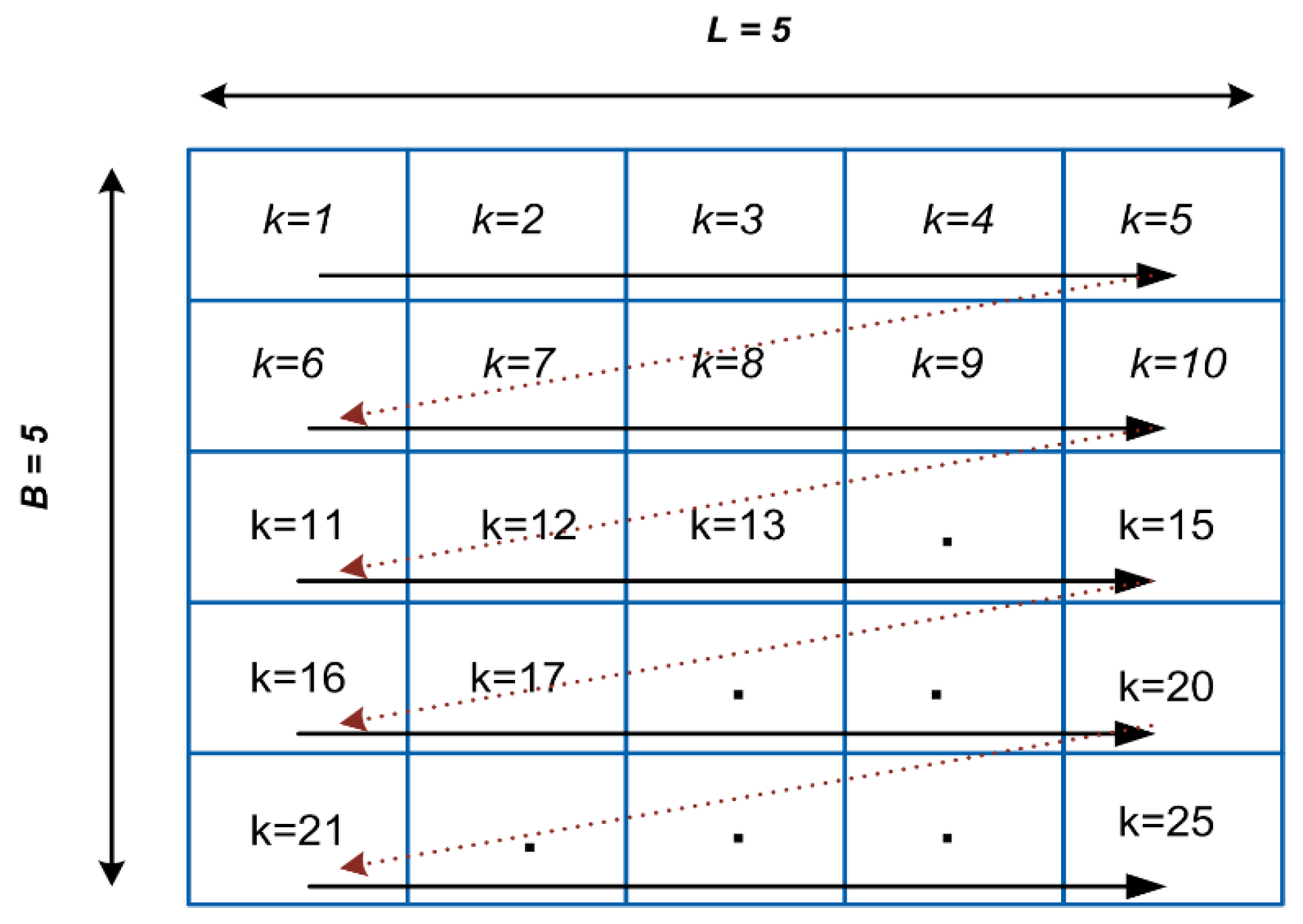
In this step, the content-owner scans each pixel of the original image
in the order from left to right and top to bottom, as shown in
Figure 4 (for an image of size
), to get the index
for each pixel. The size of
I is
, where
. This order is used throughout our proposed scheme to get the value at index
.
After scanning, the content-owner encrypts each
taken from original image
. Public key and Equation (1) are used to encrypt
to get the corresponding encrypted value
as follows:
where
is the encryption function and
is randomly selected integer for each
such that
. Step-wise encryption of the original image is as follows.
Step 1. Scan
for each pixel
in order from left to right and top to bottom (
Figure 4).
Step 2. Encrypt each using the public key as in Equation (6) to get the encrypted pixel .
Step 3. After encrypting all the pixels, the encrypted image generated is .
3.2. Data Embedding
In this step, initially, the data hider uses the data hiding key
, to encrypt the additional data
to obtain
. Here (also refer to
Section 3.5), it is assumed that the number of bits in
is equal to the number of pixels in the encrypted image
. Before embedding, the data hider generates a separate zero matrix
of size
, where all the elements are zero. The data hider uses Equation (1) and the public key to encrypt
, to obtain the encrypted matrix
. Thus, after encryption the size of matrix
, is the same as the size of the encrypted image
. It can be noted that each element of the matrix
is distinct but of the same size, by the property of semantic security (Equation (5)) inherent in Pallier cryptosystem.
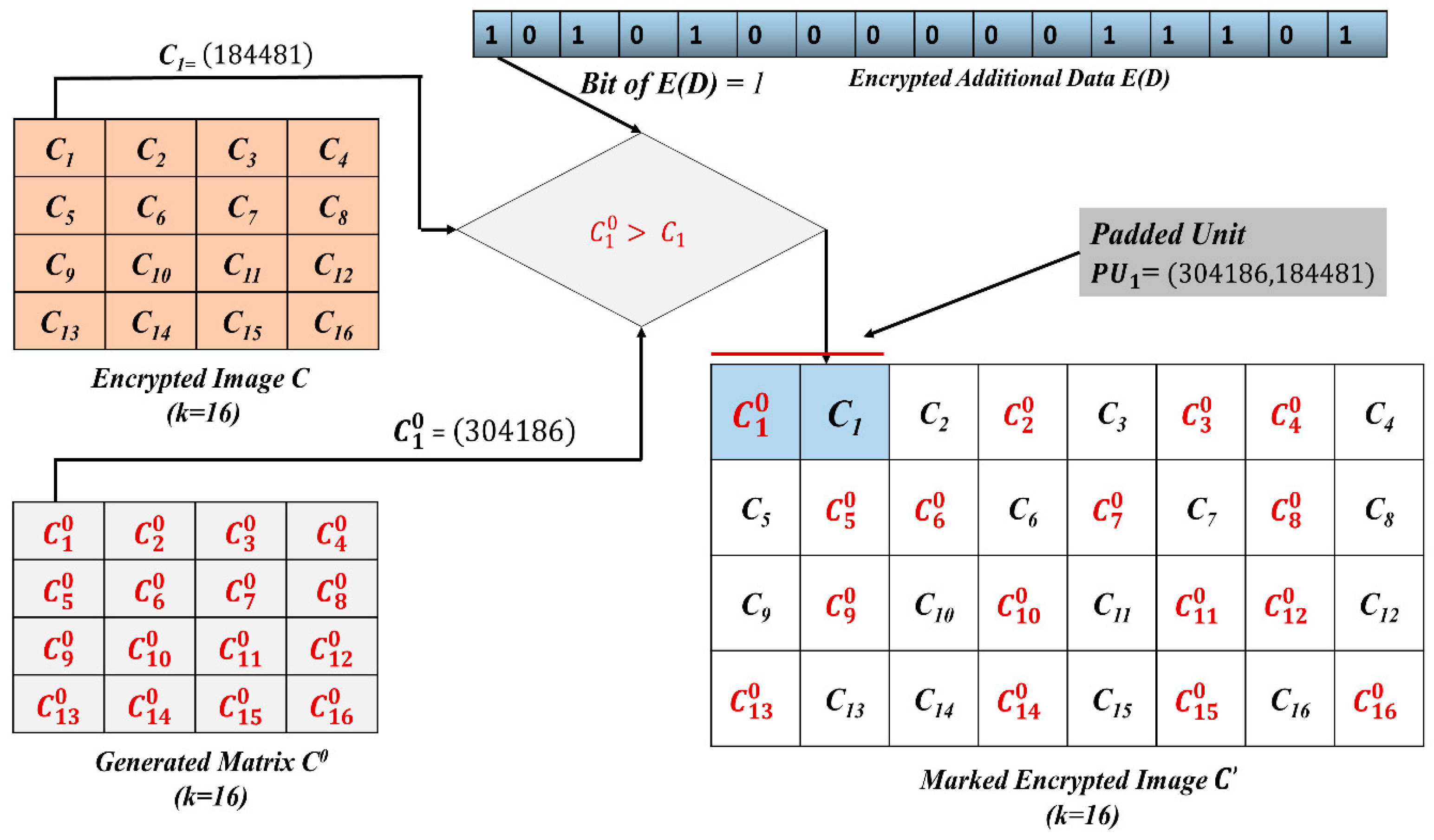
In the next step, each bit of is embedded into the corresponding of the encrypted image . That is, each encrypted pixel is responsible for carrying one bit of . For embedding, the data hider has to pad kth encrypted value of “0” (i.e., ) from the matrix , with the corresponding kth encrypted pixel (i.e., ) of . This padding results into a matrix of padded units (PUs). As each PU is composed of two encrypted values (), padding units make encrypted values. This makes the size of the PU matrix equal to , which is double the size of the i.e., . All the PUs constitute the encrypted image with additional data, i.e., the marked encrypted image .
Padding Procedure
In padding, four cases arise as depicted in
Figure 5: two cases, if the bit of
is “0”, and two cases, if the bit of
is “1”. For embedding, we compare values
and
.
When the bit of
is equal to 1, the padding is done such that the bigger value (between
and
) is at the first position in
. Thus, if
, then
is placed first in the
, as in
Figure 5 (Case 1). If
, then
is placed first in the
, as in
Figure 5 (Case 2).
When the bit of
is equal to 0, the padding is done in such a way that the bigger value (between
and
) will be at the second position in the
. If
, then
is placed second in the
, as in
Figure 5 (Case 3). If
, then
is placed second in the
, as in
Figure 5 (Case 4).
The step by step procedure for data embedding into the encrypted image can be understood from the following algorithm:
Let us assume to be the encrypted image for the pixel where and be the encrypted value of “0” for pixel .
Step 1. With the help of data hiding key , bits of additional data are encrypted in order to generate bits of encrypted additional data .
Step 2. If the bit of to be embedded is 1:
If in the selected , then we rearrange the order in by appending after .
(That is, the bigger value is first and the smaller value is second in the
(
Figure 5, Case 1).)
Otherwise, we append after .
(That is, the bigger value is first and the smaller value is second in the
(
Figure 5, Case 2).)
Step 3. If the bit of to be embedded is 0:
If in the selected , then we rearrange the order in by appending after .
(That is, the smaller value is first and the bigger value is second in the
(
Figure 5, Case 3).)
Otherwise, we append after .
(That is, the smaller value is first and the bigger value is second in the
(
Figure 5, Case 4).)
Step 4. After the encrypted image has been embedded with the , the marked encrypted image is obtained with all the .
3.3. Data Extraction
After the receipt of the marked encrypted image on the receiver side, the embedded is extracted using the data-hiding key . The step by step procedure for data extraction from is as follows:
Step 1. Scan the marked encrypted image
in the same manner as used in the encryption and embedding phase, i.e., left to right and top to bottom (
Figure 4).
Step 2. For each of the selected , Steps 3 and 4 are performed.
Step 3. If the first value of the pair (,) in the selected is bigger than the second value, then the embedded bit of is “1”.
In this case, “1” will be extracted.
Step 4. If the first value of the pair (,) in the selected is smaller than the second value, then the embedded bit of is “0”.
In this case, “0” will be extracted.
Step 5. After extracting all the bits, the encrypted additional data is constituted.
Data hiding key is used to regenerate the original additional data ).
3.4. Image Recovery
In this step, if the receiver wants to recover the original image
, he must own the private key
. After receiving the marked encrypted image
, the receiver applies homomorphic multiplication on each pair of (
,
) in
of
, to get the corresponding
, and then, decrypts each
to get
kth pixel of the directly decrypted image
with private key
using:
where
is the decryption function,
is the private key and
is the directly decrypted image. In our scheme,
results in the completely recovered original image
, i.e., no post-processing on
is further required. Step-wise procedure used to recover the original image using the private key
is as follows:
Step 1. Scan the marked encrypted image
in the same manner as used in the encryption and embedding phase, i.e., left to right and top to bottom (
Figure 4).
Step 2. For each selected .
Step 3. Apply homomorphic multiplication () to each pair () in , to obtain , such that .
(The order of and does not affect the result.)
Step 4. Each is decrypted using the private key to give the corresponding .
Step 5. is obtained constituting all the .
It can be noted that, in Step 3., the original values (unencrypted values) of and are “0” and respectively. When homomorphic multiplication is applied to (, it means internally zero is added to the value . Thus, we get encrypted value (i.e., encrypted value of .
3.5. Exemplifying Our Proposed Scheme
Figure 6 shows the working of the proposed scheme at the data-hider side. It is supported by the following example: our example shows the working for the 1st pixel value
, of the original image. Let the public key
and the private key =
. Using the public key and the encryption function
, we get
and
. Let the bit to be embedded be 1, i.e.,
= 1. For embedding, we compare
and
. According to Step 2 of
Section 3.2 (
Figure 5, Case 2), when
, we put
after
in
.Thus, here,
i.e., the bigger value is first and the smaller value is second. The receiver extracts the first bit of
, by reading the order in
. In
, the first value is bigger than the second value, so the embedded bit of
is 1. However, this bit will be further decrypted using data-hiding key
to get
Furthermore, the receiver having the private key
gets the first pixel value
, for the directly decrypted image
, from the
by using homomorphic multiplication. This is done as:
. Thus, the pixel value
is same as the original pixel value
= 65.
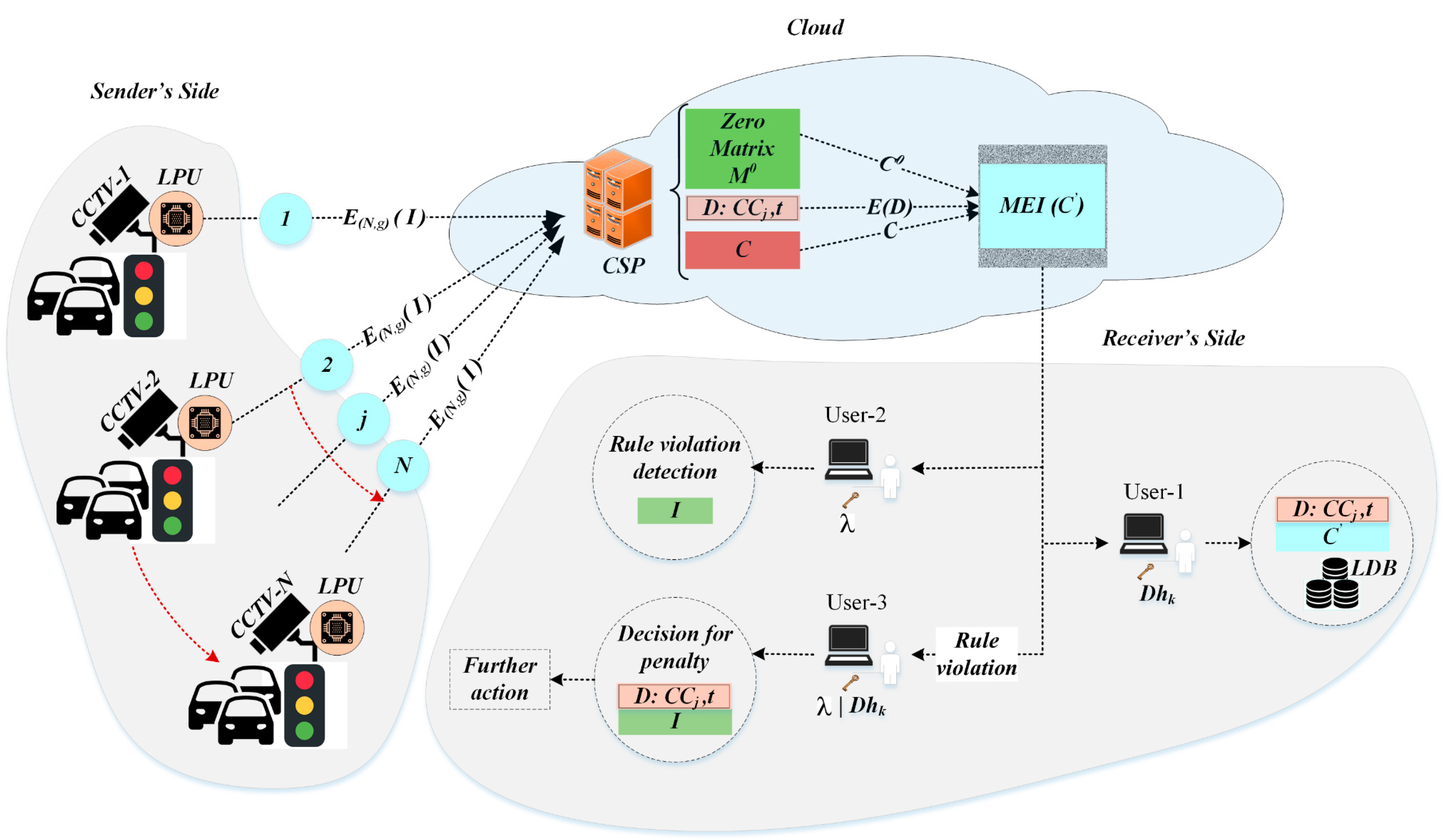
3.6. Proposed Scheme in Cloud Domain
There are a number of resource constrained devices based on cloud services; to show the process flow, involved hardware and software services we take an example of closed circuit television (CCTV) cameras installed on roads for monitoring the traffic against any traffic law violation. As shown in
Figure 7, the workflow of the given scenario can be divided into following three phases:
(1) Image capturing and encryption at the sender’s end
(2) Generating MEI over the cloud
(3) Authorized complete recovery of the D and I
(1) Image capturing and encryption: As shown in
Figure 7, at the sender’s end, there can be a number of CCTVs
, all of which are programmed to capture the images with a fixed time interval. To obtain the encrypted image
, the local processing unit (LPU) encrypts the image
captured from
jth CCTV. This is done using public key
and the encryption algorithm
. Once the image is encrypted, it is sent to the cloud service provider (CSP) acting as the data hider, for marking.
(2) Generating marked encrypted image (MEI): The data hider embeds the additional data , such as the time of the captured image or CCTV camera-id . To make secret, it is encrypted with the data hiding key to obtain . A zero matrix equal to the size of the original image , is encrypted with public key , to obtain . is used, to embed into the encrypted image , to obtain as .
(3) Authorized access and recovery: There are three type of end users with different access policies. The first category of users hold the data-hiding key These users are authorized to access additional data (e.g., the camera-id , capturing time t, etc.) from the MEI. This type of data can be used to categorize and store the MEI in a local data base . The second type of users hold private key for retrieving original image. This type of authorized users exploit the original image for detecting any traffic rule violation such as wrongful crossing, incorrect overtake, etc. The third type of users hold both data hiding and private keys. This enables users to access both additional data and the original image. Thus, for any rule violation, the image can be crosschecked with the corresponding additional data (time , camera-id , location, etc.) for validity. Reasonable penalties can be applied to the subjects flouting the rules.