Analysis of the SEU Tolerance of an FPGA-Based Time-to-Digital Converter Using Emulation-Based Fault Injection
Abstract
1. Introduction
2. Related Work
3. Architecture and Methodology for Fault Injection Based on Emulation
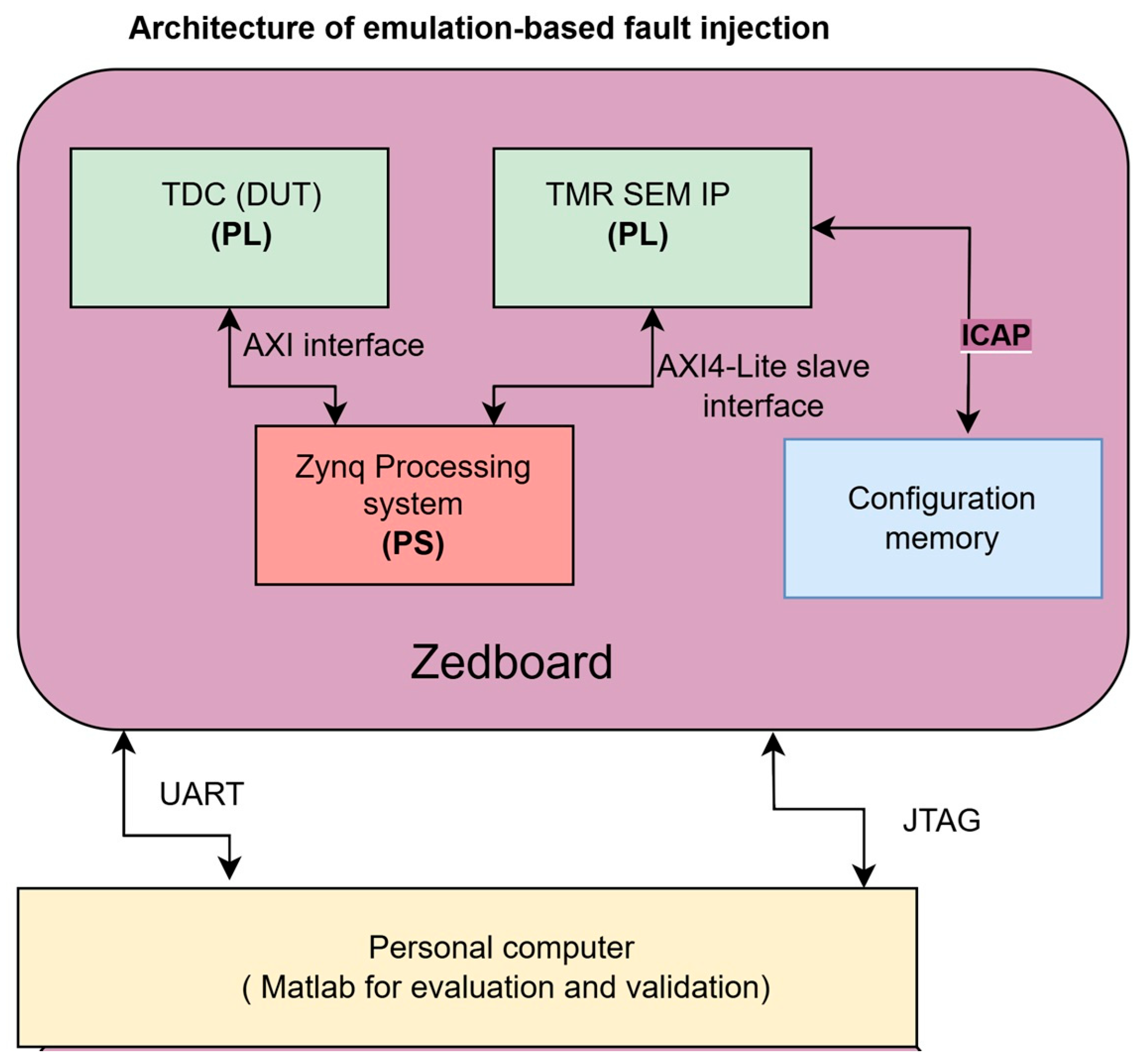
3.1. Proposed Architecture
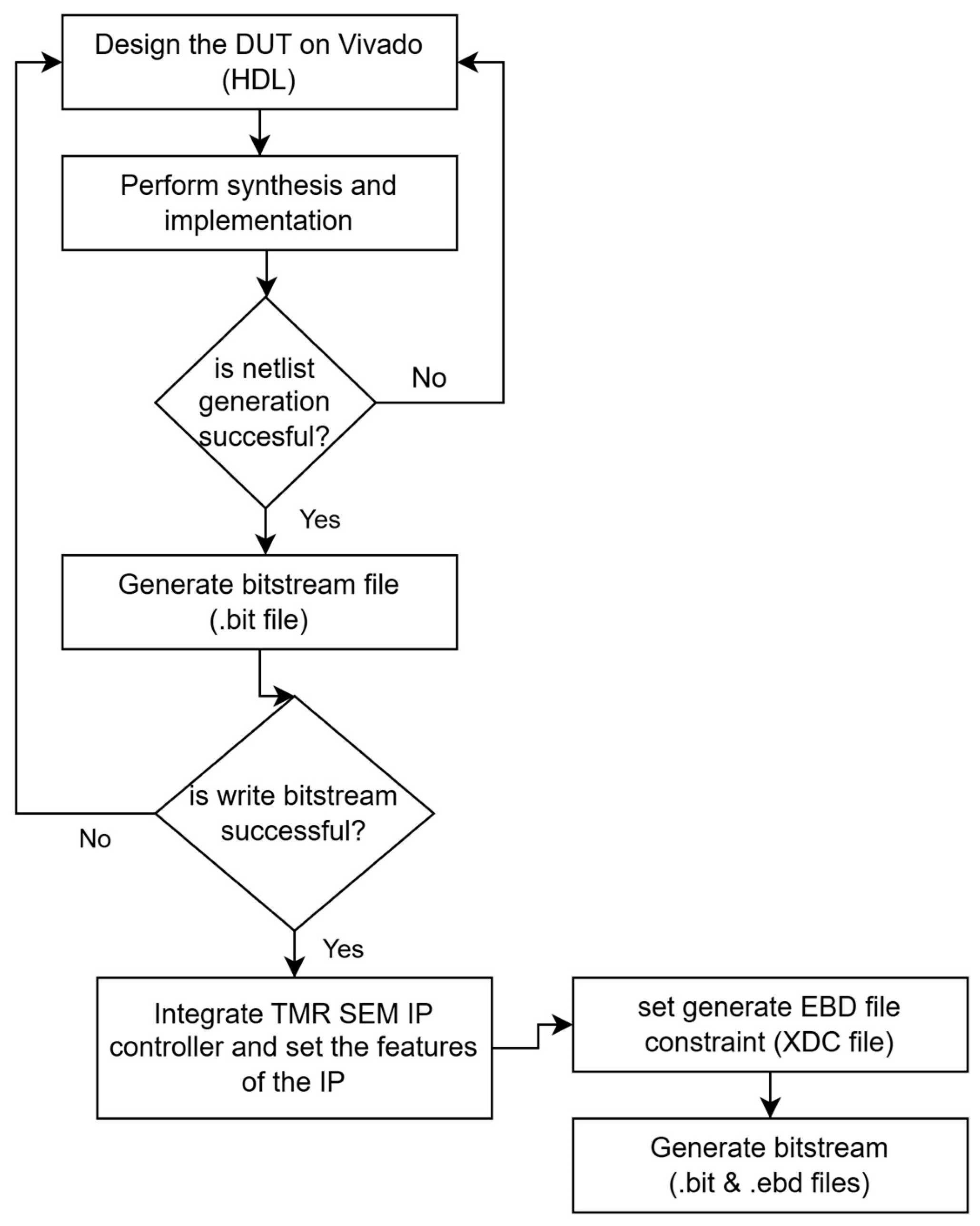
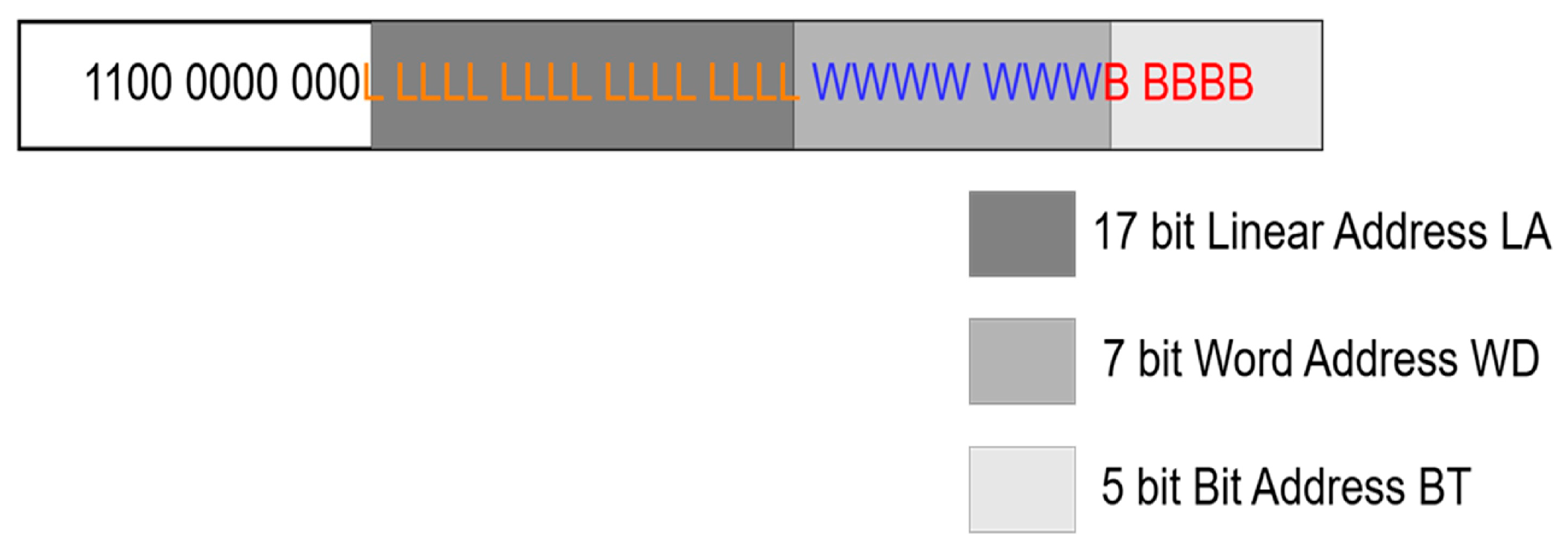
3.2. Fault Injection Methodology Using TMR SEM IP
4. Experimental Results and Discussion
4.1. Validating the Functionality of the TMR SEM IP
4.2. Performance of the TDC with SEUs
4.3. Performance Comparison with Other Works
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Roberts, G.W.; Ali-Bakhshian, M. A Brief Introduction to Time-to-Digital and Digital-to-Time Converters. IEEE Trans. Circuits Syst. II Express Briefs 2010, 57, 153–157. [Google Scholar] [CrossRef]
- Lai, J.; Luo, Y.; Shao, Q.; Bao, L.; Liu, X. A High-Resolution TDC Implemented in a 90nm Process FPGA. In Proceedings of the 2013 IEEE 10th International Conference on ASIC, Shenzhen, China, 28–31 October 2013; pp. 2–4. [Google Scholar] [CrossRef]
- Van Bockel, B.; Leroux, P.; Prinzie, J. Tradeoffs in Time-to-Digital Converter Architectures for Harsh Radiation Environments. IEEE Trans. Instrum. Meas. 2021, 70, 1–10. [Google Scholar] [CrossRef]
- Cheng, Z.; Zheng, X.; Deen, M.J.; Peng, H. Recent Developments and Design Challenges of High-Performance Ring Oscillator CMOS Time-to-Digital Converters. IEEE Trans. Electron. Devices 2016, 63, 235–251. [Google Scholar] [CrossRef]
- Akiba, K.; Ronning, P.; Van Beuzekom, M.; Van Beveren, V.; Borghi, S.; Boterenbrood, H.; Buytaert, J.; Collins, P.; Dosil Suárez, A.; Dumps, R.; et al. The Timepix Telescope for High Performance Particle Tracking. Nucl. Instrum. Methods Phys. Res. Sect. A Accel. Spectrometers Detect. Assoc. Equip. 2013, 723, 47–54. [Google Scholar] [CrossRef]
- Lecoq, P. Pushing the Limits in Time-of-Flight PET Imaging. IEEE Trans. Radiat. Plasma Med. Sci. 2017, 1, 473–485. [Google Scholar] [CrossRef]
- Nolet, F.; Lemaire, W.; Dubois, F.; Roy, N.; Carrier, S.; Samson, A.; Charlebois, S.A.; Fontaine, R.; Pratte, J.F. A 256 Pixelated SPAD Readout ASIC with In-Pixel TDC and Embedded Digital Signal Processing for Uniformity and Skew Correction. Nucl. Instrum. Methods Phys. Res. Sect. A Accel. Spectrometers Detect. Assoc. Equip. 2020, 949, 162891. [Google Scholar] [CrossRef]
- Dodd, P.E.; Massengill, L.W. Basic Mechanisms and Modeling of Single-Event Upset in Digital Microelectronics. IEEE Trans. Nucl. Sci. 2003, 50, 583–602. [Google Scholar] [CrossRef]
- Nidhin, T.S.; Bhattacharyya, A.; Behera, R.P.; Jayanthi, T.; Velusamy, K. Understanding Radiation Effects in SRAM-Based Field Programmable Gate Arrays for Implementing Instrumentation and Control Systems of Nuclear Power Plants. Nucl. Eng. Technol. 2017, 49, 1589–1599. [Google Scholar] [CrossRef]
- Aranda, L.A.; Sánchez-macián, A.; Maestro, J.A.; Member, S. ACME: A Tool to Improve Configuration Memory Fault Injection in SRAM-Based FPGAs. IEEE Access 2019, 7, 128153–128161. [Google Scholar] [CrossRef]
- Asadi, G.; Tahoori, M.B. Soft Error Rate Estimation and Mitigation for SRAM-Based FPGAs. In Proceedings of the 2005 ACM/SIGDA 13th International Symposium on Field-Programmable Gate Arrays, Monterey, CA, USA, 20–22 February 2005; pp. 149–160. [Google Scholar] [CrossRef]
- Ruano, Ó.; Garc, F.; Aranda, L.A.; Rodriguez, L.; Maestro, J.A.; Alfonso, S. Techniques and Methodology, A Tutorial. 2021. Available online: https://www.mdpi.com/1424-8220/21/4/1392 (accessed on 1 April 2025).
- Pereira, V.C.; de Santiago Júnior, V.A.; Manea, S. SEU Mitigation for SRAM FPGAs: A Comparison via Probabilistic Model Checking. In Workshop de Testes e Tolerância A Falhas (WTF), 18; Sociedade Brasileira de Computa ção: Porto Alegre, Brazil, 2007; ISSN 2595-2684. [Google Scholar]
- Carmichael, C.; Fuller, E.; Blain, P.; Caffrey, M. SEU Mitigation Techniques for Virtex FPGAs in Space Applications. Architecture 1999, 1–11. Available online: https://citeseerx.ist.psu.edu/document?repid=rep1&type=pdf&doi=fb201cea8d302762290c71b7071829f646c9c29c (accessed on 4 May 2025).
- Wang, X. Partitioning Triple Modular Redundancy for Single Event Upset Mitigation in FPGA. In Proceedings of the 2010 International Conference on E-Product E-Service and E-Entertainment, Henan, China, 7–9 November 2010; pp. 1–4. [Google Scholar] [CrossRef]
- Kubica, M.; Czerwinski, R. Performance Testing of the Triple Modular Redundancy Mitigation Circuit Test Environment Implementation in Field Programmable Gate Array Structures. Appl. Sci. 2024, 14, 8604. [Google Scholar] [CrossRef]
- Zheng, M.; Wang, Z.; Li, L. DAO: Dual Module Redundancy with AND/OR Logic Voter for FPGA Hardening. In Proceedings of the 2015 First International Conference on Reliability Systems Engineering (ICRSE), Beijing, China, 21–23 October 2015; pp. 1–5. [Google Scholar] [CrossRef]
- Matsuo, I.B.M.; Zhao, L.; Lee, W.J. A Dual Modular Redundancy Scheme for CPU-FPGA Platform-Based Systems. IEEE Trans. Ind. Appl. 2018, 54, 5621–5629. [Google Scholar] [CrossRef]
- Vlagkoulis, V.; Sari, A.; Antonopoulos, G.; Psarakis, M.; Tavoularis, A.; Furano, G.; Boatella-Polo, C.; Poivey, C.; Ferlet-Cavrois, V.; Kastriotou, M.; et al. Configuration Memory Scrubbing of SRAM-Based FPGAs Using a Mixed 2-D Coding Technique. IEEE Trans. Nucl. Sci. 2022, 69, 871–882. [Google Scholar] [CrossRef]
- Vlagkoulis, V.; Sari, A.; Proko, J.; Zografakis, D.; Psarakis, M.; Tavoularis, A.; Furano, G.; Boatella-Polo, C.; Poivey, C.; Ferlet-Cavrois, V.; et al. Configuration Memory Scrubbing of the Xilinx Zynq-7000 FPGA Using a Mixed 2-D Coding Technique. In Proceedings of the 2019 19th European Conference on Radiation and Its Effects on Components and Systems (RADECS), Montpellier, France, 16–20 September 2019; pp. 31–34. [Google Scholar] [CrossRef]
- Berg, M.; Poivey, C.; Petrick, D.; Espinosa, D.; Lesea, A.; LaBel, K.; Friendlich, M.; Kim, H.; Phan, A. Effectiveness of Internal vs. External Sed Scrubbing Mitigation Strategies in a Xilinx FPGA: Design, Test, and Analysis. In Proceedings of the 2007 9th European Conference on Radiation and Its Effects on Components and Systems, Deauville, France, 10–14 September 2007; pp. 1–8. [Google Scholar] [CrossRef]
- Tonfat, J.; Lima Kastensmidt, F.; Rech, P.; Reis, R.; Quinn, H.M. Analyzing the Effectiveness of a Frame-Level Redundancy Scrubbing Technique for SRAM-Based FPGAs. IEEE Trans. Nucl. Sci. 2015, 62, 3080–3087. [Google Scholar] [CrossRef]
- Giordano, R.; Perrella, S.; Izzo, V.; Milluzzo, G.; Aloisio, A. Redundant-Configuration Scrubbing of SRAM-Based FPGAs. IEEE Trans. Nucl. Sci. 2017, 64, 2497–2504. [Google Scholar] [CrossRef]
- Vavouras, M.; Bouganis, C.S. Area-Driven Partial Reconfiguration for SEU Mitigation on SRAM-Based FPGAS. In Proceedings of the 2016 International Conference on ReConFigurable Computing and FPGAs (ReConFig), Cancun, Mexico, 30 November–2 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Panek, R.; Lojda, J.; Podivinsky, J.; Kotasek, Z. Partial Dynamic Reconfiguration in an FPGA-Based Fault-Tolerant System: Simulation-Based Evaluation. In Proceedings of the 2018 IEEE East-West Design & Test Symposium (EWDTS), Kazan, Russia, 14–17 September 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Nidhin, T.S.; Bhattacharyya, A.; Behera, R.P.; Jayanthi, T. A Review on SEU Mitigation Techniques for FPGA Configuration Memory. IETE Tech. Rev. 2017, 35, 4602. [Google Scholar] [CrossRef]
- Ferlini, F.; Viel, F.; Seman, L.O.; Pettenghi, H.; Bezerra, E.A.; Reis, V.; Leithardt, Q. A Methodology for Accelerating FPGA Fault Injection Campaign Using ICAP. Electronics 2023, 12, 807. [Google Scholar] [CrossRef]
- De Oliveira, Á.B.; Tambara, L.A.; Benevenuti, F.; Benites, L.A.C.; Added, N.; Aguiar, V.A.P.; Medina, N.H.; Silveira, M.A.G.; Kastensmidt, F.L. Evaluating Soft Core RISC-V Processor in SRAM-Based FPGA Under Radiation Effects. IEEE Trans. Nucl. Sci. 2020, 67, 1503–1510. [Google Scholar] [CrossRef]
- Braga, G.; Benevenuti, F.; Gonçalves, M.M.; Hernandez, H.G.M.; Hübner, M.; Brandalero, M.; Kastensmidt, F.; Azambuja, J.R. Evaluating Softcore GPU in SRAM-Based FPGA under Radiation-Induced Effects. Microelectron. Reliab. 2021, 126, 114348. [Google Scholar] [CrossRef]
- Eslami, M.; Ghavami, B.; Raji, M.; Mahani, A. A Survey on Fault Injection Methods of Digital Integrated Circuits. Integration 2020, 71, 154–163. [Google Scholar] [CrossRef]
- Siecha, R.T.; Alemu, G.; Prinzie, J.; Leroux, P. 5.7 Ps Resolution Time-to-Digital Converter Implementation Using Routing Path Delays. Electronics 2023, 12, 3478. [Google Scholar] [CrossRef]
- Makowski, D. The Impact of Radiation on Electronic Devices with the Special Consideration of Neutron and Gamma Radiation Monitoring. Tech. Univ. Lodz 2006, 151. Available online: https://www.researchgate.net/publication/241771919_The_Impact_on_Electronic_Devices_with_the_Special_Consideration_of_Neutron_and_Gamma_Radiation_Monitoring (accessed on 21 May 2025).
- Bocquillon, A.; Foucard, G.; Miller, F.; Buard, N.; Leveugle, R.; Daniel, C.; Rakers, S.; Carriere, T.; Pouget, V.; Velazco, R. Highlights of Laser Testing Capabilities Regarding the Understanding of SEE in SRAM Based FPGAs. In Proceedings of the 2007 9th European Conference on Radiation and Its Effects on Components and Systems, Deauville, France, 10–14 September 2007; pp. 1–6. [Google Scholar] [CrossRef]
- Lesea, A.; Drimer, S.; Fabula, J.J.; Carmichael, C.; Alfke, P. The Rosetta Experiment: Atmospheric Soft Error Rate Testing in Differing Technology FPGAs. IEEE Trans. Device Mater. Reliab. 2005, 5, 317–328. [Google Scholar] [CrossRef]
- Allspaw, J. Fault Injection in Production. Commun. ACM 2012, 55, 48–52. [Google Scholar] [CrossRef]
- Da Silva, A.; Sánchez, S. LEON3 ViP: A Virtual Platform with Fault Injection Capabilities. In Proceedings of the 22nd IEEE International Symposium on Defect and Fault-Tolerance in VLSI Systems (DFT 2007), Rome, Italy, 26–28 September 2007; pp. 813–816. [Google Scholar] [CrossRef]
- Khatri, A.R.; Hayek, A.; Josef, B. RASP-FIT: A Fast and Automatic Fault Injection Tool for Code-Modification of FPGA Designs. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 30–40. [Google Scholar] [CrossRef]
- Monopoli, M.; Member, G.S.; Biondi, M. RADSAFiE: A Netlist-Level Fault Injection User Interface Application for FPGA-Based Digital Systems. IEEE Access 2025, 13, 28809–28823. [Google Scholar] [CrossRef]
- Fibich, C.; Rössler, P.; Tauner, S.; Taucher, H.; Matschnig, M. A Netlist-Level Fault-Injection Tool for FPGAs. Elektrotech. Inftech. 2015, 132, 274–281. [Google Scholar] [CrossRef]
- Entrena, L.; García-Valderas, M.; Fernández-Cardenal, R.; Lindoso, A.; Portela, M.G.; López-Ongil, C. Soft Error Sensitivity Evaluation of Microprocessors by Multilevel Emulation-Based Fault Injection. IEEE Trans. Comput. 2012, 61, 313–322. [Google Scholar] [CrossRef]
- Ĺopez-Ongil, C.; García-Valderas, M.; Portela-García, M.; Entrena, L. Autonomous Fault Emulation: A New FPGA-Based Acceleration System for Hardness Evaluation. IEEE Trans. Nucl. Sci. 2007, 54, 252–261. [Google Scholar] [CrossRef]
- Alderighi, M.; Casini, F.; D’Angelo, S.; Pastore, S.; Sechi, G.R.; Weigand, R. Evaluation of Single Event Upset Mitigation Schemes for SRAM Based FPGAs Using the FLIPPER Fault Injection Platform. In Proceedings of the 22nd IEEE International Symposium on Defect and Fault-Tolerance in VLSI Systems (DFT 2007), Rome, Italy, 26–28 September 2007; pp. 105–113. [Google Scholar] [CrossRef]
- Alderighi, M.; Casini, F.; D’Angelo, S.; Mancini, M.; Codinachs, D.M.; Pastore, S.; Poivey, C.; Sechi, G.R.; Weigand, G.S.R. Experimental Validation of Fault Injection Analyses by the FLIPPER Tool. In Proceedings of the 2009 European Conference on Radiation and Its Effects on Components and Systems, Brugge, Belgium, 14–18 September 2009; 57, pp. 544–548. [Google Scholar] [CrossRef]
- Fpgas, S.; Thurlow, C.; Rowberry, H.; Wirthlin, M. TURTLE: A Low-Cost Fault Injection Platform For. In Proceedings of the 2019 International Conference on ReConFigurable Computing and FPGAs (ReConFig), Cancun, Mexico, 9–11 December 2019; pp. 1–8. Available online: https://ieeexplore.ieee.org/document/8994782 (accessed on 5 May 2025).
- Smit, T.T.; Forlin, B.E.; Chen, K.; Souvatzoglou, I.; Psarakis, M.; Ottavi, M. An Enhanced Fault Injection Framework For. In Proceedings of the 2024 IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT), Didcot, UK, 8–10 October 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Aranda, L.A.; Ruano, O.; Garcia-Herrero, F.; Maestro, J.A. ACME-2: Improving the Extraction of Essential Bits in Xilinx SRAM-Based FPGAs. IEEE Trans. Circuits Syst. II Express Briefs 2022, 69, 1577–1581. [Google Scholar] [CrossRef]
- Wang, Y.; Xie, W.; Chen, H.; Day-Uei Li, D. High-Resolution Time-to-Digital Converters (TDCs) with a Bidirectional Encoder. Meas. J. Int. Meas. Confed. 2023, 206, 112258. [Google Scholar] [CrossRef]
- Chen, H.; Zhang, Y.; Li, D.D. A Low Nonlinearity, Missing-Code Free Time-to-Digital Converter Based on 28-Nm FPGAs With Embedded Bin-Width Calibrations. IEEE Trans. Instrum. Meas. 2017, 66, 1912–1921. [Google Scholar] [CrossRef]
- Wang, Y.; Xie, W.; Chen, H.; Li, D.D. Configurable Gray Code Oscillator Time-to- Digital Converters Implemented in 16nm. Available online: https://ieeexplore.ieee.org/document/9776629 (accessed on 13 May 2025).
- Zhang, M.; Wang, H.; Liu, Y. A 7.4 Ps FPGA-Based TDC with a 1024-Unit Measurement Matrix. Sensors 2017, 17, 865. [Google Scholar] [CrossRef] [PubMed]
- Xia, H.; Yu, X.; Zhang, J.; Cao, G. A Review of Advancements and Trends in Time-to-Digital Converters Based on FPGA. IEEE Trans. Instrum. Meas. 2024, 73, 1–25. [Google Scholar] [CrossRef]
- van Bockel, B.; Prinzie, J.; Leroux, P. Design of a 4 Ps Radiation Hardened TDC with an Improved Interpolation Technique. Proc. Sci. 2019, 370, 6. [Google Scholar] [CrossRef][Green Version]
- Van Bockel, B.; Prinzie, J.; Leroux, P. Radiation Assessment of a 15.6ps Single-Shot Time-to-Digital Converter in Terms of TID. Electronics 2019, 8, 558. [Google Scholar] [CrossRef]
- Garza-Reyes, J.A. Table of Contents Table of Contents ی ﺮ ﺘ ﮐ د ﻪ ﺒ ﺣ ﺎ ﺼ ﻣ ز ﺎ ﯿ ﭘ ﺎ ﺗ ﺮ ﯿ ﺳ ز ا. Eur. Univ. Inst. 2012, 2–5. Available online: https://docs.amd.com/r/en-US/pg036_sem/Integration-of-the-SEM-IP-Core (accessed on 20 May 2025).
- Guide, P. MicroBlaze Triple Modular Redundancy. 2022, pp. 1–101. Available online: https://docs.amd.com/r/en-US/pg268-tmr/Triple-Modular-Redundancy-TMR-v1.0-LogiCORE-IP-Product-Guide-PG268 (accessed on 20 May 2025).
- Wang, Y.; Liu, C. A Nonlinearity Minimization-Oriented Resource-Saving Time-to-Digital Converter Implemented in a 28 Nm Xilinx FPGA. IEEE Trans. Nucl. Sci. 2015, 62, 2003–2009. [Google Scholar] [CrossRef]
- Xie, W.; Chen, H.; Li, D.D.U. Efficient Time-to-Digital Converters in 20 Nm FPGAs with Wave Union Methods. IEEE Trans. Ind. Electron. 2022, 69, 1021–1031. [Google Scholar] [CrossRef]
- Siecha, R.T.; Alemu, G.; Prinzie, J.; Leroux, P. High-Performance Wave Union Time-to-Digital Converter Implementation Based on Routing Path Delays of FPGA. Electronics 2024, 13, 2359. [Google Scholar] [CrossRef]
- Kwiatkowski, P. Employing FPGA DSP Blocks for Time-to-Digital Conversion. Metrol. Meas. Syst. 2019, 26, 631–643. [Google Scholar] [CrossRef]
- Cao, Y.; De Cock, W.; Steyaert, M.; Leroux, P. 1-1-1 MASH ΔΣ Time-to-Digital Converters with 6 Ps Resolution and Third-Order Noise-Shaping. IEEE J. Solid-State Circuits 2012, 47, 2093–2106. [Google Scholar] [CrossRef]
- Karadamoglou, K.; Paschalidis, N.P.; Sarris, E.; Stamatopoulos, N.; Kottaras, G.; Paschalidis, V. An 11-Bit High-Resolution and Adjustable-Range CMOS Time-to-Digital Converter for Space Science Instruments. IEEE J. Solid-State Circuits 2004, 39, 214–222. [Google Scholar] [CrossRef]
- Christiansen, J. High Performance Time to Digital Converter. Cern/Epmic. 2004. Available online: https://cds.cern.ch/record/1067476/files/cer-002723234 (accessed on 13 May 2025).







| Work/ Year | Method | Technology | DUT | SEU Mitigation Strategy | Pros | Cons | Damage | #Injected Faults | Time/Fault | Layer |
|---|---|---|---|---|---|---|---|---|---|---|
| [33]/(2007) | Laser test | 220 nm | Xilinx XCV1000 FPGA | TMR + continuous scrubbing | Realistic results | Expensive | Permanent | 516 upsets of 6,127,744 configuration bits | - | Configuration layer |
| [34]/(2005) | Laser test | 90 nm | V4LX25 | None | Realistic results | Expensive | Permanent | 1.9 gigabits | = | Configuration layer |
| [38]/ (2025) | Netlist-level fault injection based on Verilog | 20 nm | KintexUltrascaleXQRKU060 | None | Early design-stage verification | Time-consuming for complex designs | None | 140 Mb | 25 ns | Application layer |
| [39]/(2015) | Netlist-level fault injection based on Verilog HDL | 65 nm | Virtex V | None | Early design-stage verification | Time-consuming for complex designs | None | _ | 15 ns | Application layer |
| [37]/(2018) | RTL-level fault injection based on Verilog | - | - | None | Early design-stage verification | Time-consuming for complex designs | None | 34,182 | 38.2 ms | Application layer |
| [40]/(2012) | Autonomous instrumentational emulation-based fault injection (RTL+GTL) | 45 nm | Xilinx XC6VLX240T FPGA | None | Early design-stage verification | Intrusive | None | 164,720,820 | 0.3 ms | Application layer |
| [41]/(2007) | Autonomous instrumentational emulation-based fault injection | 28 nm | Xilinx Virtex-2000E | TMR | Early design-stage verification | Intrusive | None | 1,000,000 | 1 µs | Application layer |
| [42]/(2007) | Fault emulation based on partial reconfiguration | 28 nm | Xilinx XQ2VR6000 | XTMR | Early design-stage verification | Targets all configuration memory bits | None | 3,300,000 | 18 ms | Configuration layer |
| [44]/(2019) | Fault emulation based on partial reconfiguration | 28 nm | Artix-7XC7A200T-1SBG484C | _ | Non-intrusive | Exhaustive testing | >170 million | 10 ms | Configuration layer | |
| [27]/(2023) | Fault emulation based on partial reconfiguration | 65 nm | Xilinx Virtex 5 XC5VLX110T | TMR | Targets only essential bits to the DUT | Limited to Xilinx FPGAs | None | 5425 | 0.2 s | Configuration layer |
| [45]/(2024) | Fault emulation | 28 nm | XC7Z030-1SBG485I ZYNQ-7000 | None | Non-intrusive | Takes more time | None | 2752 | 685 ms | Configuration + application layer |
| [10]/(2019) | Fault emulation based on partial reconfiguration | 20 nm | Kintex UltraScale FPGA KCU105 evaluation board | - | Non-intrusive Targets only essential bits to the DUT | Limited to Xilinx FPGAs | None | 9604 | 12 s | Configuration layer |
| This work | Fault emulation based on partial reconfiguration | 28 nm | XC7Z030-1SBG485I ZYNQ-7000 | TMR + scrubbing | Non-intrusive Targets only essential bits to the DUT | Limited to Xilinx FPGAs | None | 3,000,000 | 10 ns | Configuration layer |
| Resources | TDC Without TMR SEM IP | TDC with TMR SEM IP | Resource Overhead (%) | |||
|---|---|---|---|---|---|---|
| Total | Utilized | Utilized (%) | Utilized | Utilized (%) | ||
| Slice registers | 106,400 | 41,175 | 38.70 | 52,232 | 49.09 | 26.85 |
| Slice LUTs | 53,200 | 25,819 | 48.53 | 28,857 | 54.24 | 11.77 |
| LUTs as logic | 53,200 | 16,875 | 31.72 | 16,902 | 31.77 | 0.16 |
| LUTs as memory | 17,400 | 8944 | 51.40 | 11,955 | 68.71 | 33.67 |
| Slices | 13,300 | 11,041 | 83.02 | 12,612 | 94.83 | 14.23 |
| Block RAM | 140 | 32.5 | 23.21 | 66.5 | 47.50 | 104.62 |
| MMCME2-ADV | 4 | 3 | 75 | 3 | 75 | 0 |
| TDC Without TMR SEM IP | TDC with TMR SEM IP | Power Overhead (%) | |
|---|---|---|---|
| Static power (W) | 0.171 | 0.181 | 5.85 |
| Dynamic power (W) | 2.343 | 2.463 | 5.12 |
| Total on-chip power (W) | 2.514 | 2.644 | 5.17 |
| Golden TDC | 4K SEUs | 200K SEUs | 1M SEUs | 3M SEUs | |
|---|---|---|---|---|---|
| Mean Binsize (ps) | 5.69 | 5.69 | 5.69 | 5.69 | 5.69 |
| std (ps) | 2.4964 | 2.4962 | 2.4861 | 2.5027 | 2.5163 |
| INL (LSB) (RMS) | 0.5571 | 0.5686 | 0.5592 | 0.5951 | 0.606 |
| DNL (LSB)(RMS) | 0.4383 | 0.4382 | 0.4365 | 0.4394 | 0.4418 |
| Work/ Year | Technology (nm) | Topology | Delay Elements | LSB [ps] | INL [LSB] | DNL [LSB] | SEU Analysis and Mitigation |
|---|---|---|---|---|---|---|---|
| [47]/(2023) | 16 | TDL + wave union | Carry chains | 0.4 | 6.42 | 51.56 | None |
| [58]/(2024) | 28 | Counter matrix + wave union | Routing paths | 0.36 | 1.04 (rms) | 0.60 (rms) | None |
| [50]/(2017) | 40 | Counter matrix | Routing paths | 7.4 | 1.57 | 0.74 | None |
| [57]/(2022) | 20 | TDL + wave union | Carry chains | 1.23–2.53 | 5.97 | 1.75 | None |
| [59]/(2019) | 28 | DSP delay lines | DSPs | 4.2 | 31.54 | 20 | None |
| [56]/(2015) | 28 | TDL + calibration | Carry chains | 15 (rms) | 0.8 | 1 | None |
| This work | 28 | Counter matrix | Routing paths | 5.7 | 0.606 (rms) (with 3 million SEUs injected) | 0.4118 (rms) (with 3 million SEUs injected) | Yes |
| Work/Year | Technology | Topology | Fault Injection Method | Radiation Test Type | Resolution (ps) | INL [LSB] (rms) | DNL [LSB] (rms) |
|---|---|---|---|---|---|---|---|
| [60]/(2012) | 130 nm ASIC | Delta–sigma | Physical | TID | 10.5 | - | - |
| [61]/(2004) | 800 nm ASIC | Pulse shrinking | Physical | TID | 50 | 0.45 | - |
| [62]/(2004) | 250 nm ASIC | DLL | Physical | TID | 24 | 2.1 | 0.21 |
| [53]/(2019) | 65 nm ASIC | Ring oscillator | Physical | TID | 15.6 | 0.34 | 0.22 |
| This work | 28 nm FPGA | Counter matrix | Fault emulation | SEU | 5.7 | 0.606 | 0.4118 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Siecha, R.T.; Alemu, G.; Prinzie, J.; Leroux, P. Analysis of the SEU Tolerance of an FPGA-Based Time-to-Digital Converter Using Emulation-Based Fault Injection. Electronics 2025, 14, 2176. https://doi.org/10.3390/electronics14112176
Siecha RT, Alemu G, Prinzie J, Leroux P. Analysis of the SEU Tolerance of an FPGA-Based Time-to-Digital Converter Using Emulation-Based Fault Injection. Electronics. 2025; 14(11):2176. https://doi.org/10.3390/electronics14112176
Chicago/Turabian StyleSiecha, Roza Teklehaimanot, Getachew Alemu, Jeffrey Prinzie, and Paul Leroux. 2025. "Analysis of the SEU Tolerance of an FPGA-Based Time-to-Digital Converter Using Emulation-Based Fault Injection" Electronics 14, no. 11: 2176. https://doi.org/10.3390/electronics14112176
APA StyleSiecha, R. T., Alemu, G., Prinzie, J., & Leroux, P. (2025). Analysis of the SEU Tolerance of an FPGA-Based Time-to-Digital Converter Using Emulation-Based Fault Injection. Electronics, 14(11), 2176. https://doi.org/10.3390/electronics14112176







