An Improved Multi-Authority Attribute Access Control Scheme Base on Blockchain and Elliptic Curve for Efficient and Secure Data Sharing
Abstract
1. Introduction
- In this paper, IPFS is used as a distributed storage platform, which not only achieves on-chain retrieval and off-chain storage, but also solves the shortcomings of privacy leakage, single point of failure and repeated storage (IPFS automatically deletes duplicate data content) in centralized storage mode.
- A data sharing scheme based on consortium blockchain and improved attribute encryption is proposed. It solves some problems in the past scheme with the idea of distribution, and the blockchain can provide auditable action logs to make the data sharing process more transparent.
- The MA-CPABE encryption algorithm improved by ECC is adopted. It solves the problem of attribute distribution, which depends on the centralized third party and is opaque in the traditional attribute encryption algorithm. Moreover, it reduces time and resource consumption in encryption and decryption.
- Use Hyperledger Fabric chaincode technology to realize data upload, query and access. Only users who meet the access control conditions set by the data owner can view the privacy information of the data.
2. Related Work
3. Preliminaries
3.1. ECC
- Key generation.
- (a)
- Alice and Bob select an elliptic curve with the same parameters and point G as the generator.
- (b)
- Alice randomly selects an integer as the private key and then computes the corresponding public key .
- (c)
- Bob randomly selects an integer as the private key and then computes the corresponding public key
- EncryptionEncrypt the information mapped to point Q. Alice calculates the ciphertexts and , where is an integer randomly selected by Alice. Alice sends the calculated ciphertexts to Bob.
- DecryptionAfter receiving the ciphertexts, Bob uses his private key to compute the point Q according to the formula .Then, he obtains plaintext information by mapping point Q back to E.
3.2. Linear Secret Sharing Scheme (LSSS)
- The secret shares of the parties form the vector on .
- The shared matrix A is composed of n rows and m columns. For each line i marked with a function is associated with one of the parties. Suppose is the secret to be shared. The first element of the column vector v is s, and the remaining elements need to be randomly selected from . Then, is computed as the sharing vector of the secret s, where vector , and .
- Suppose an arbitrary authorization set , where T is a self-defined access policy tree. is a constant set, compute the original secret , where is the share of secret s.
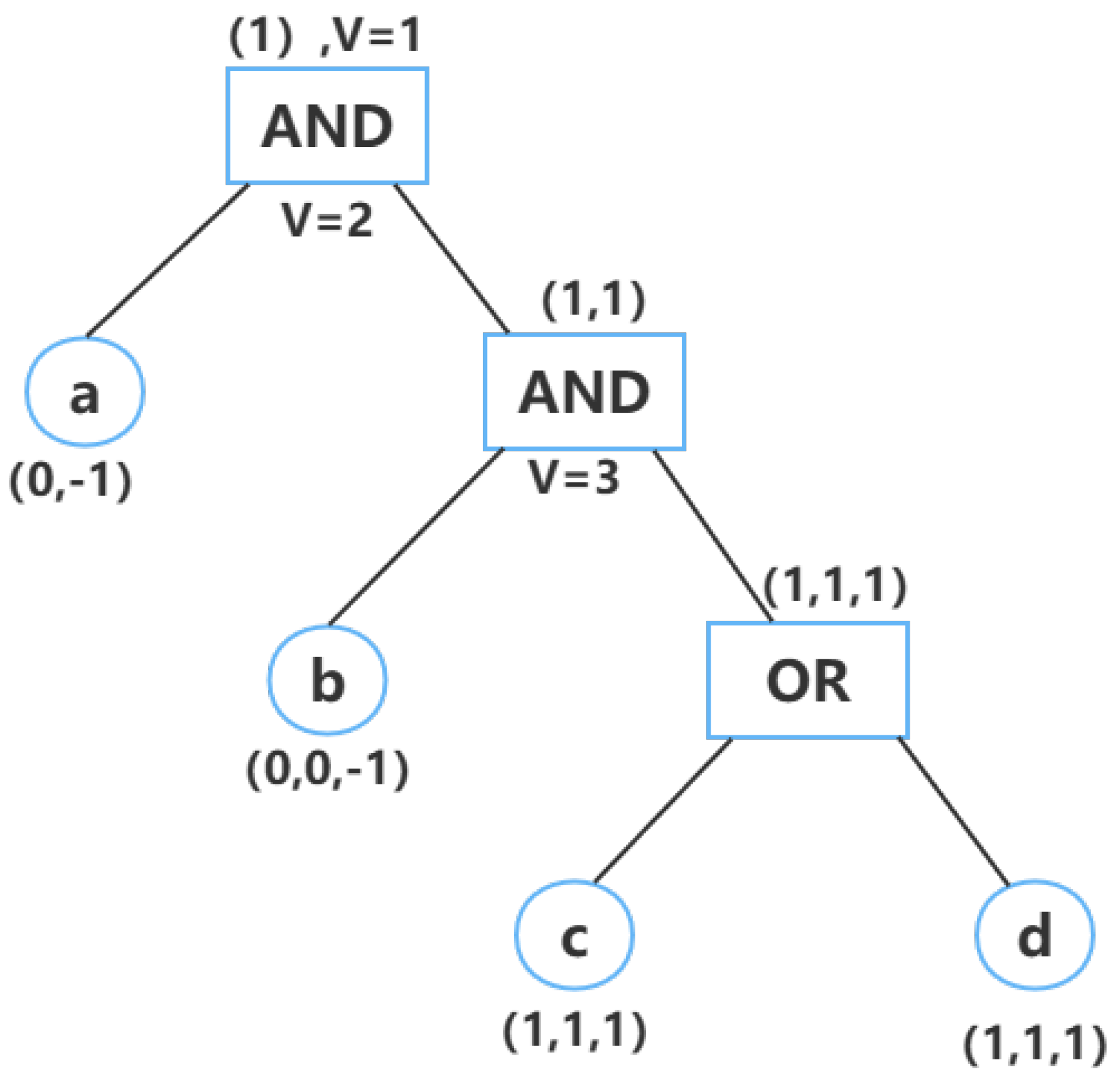
- If the parent node is an OR threshold marked with vector , then its two child nodes are represented by vector , and the value of the counter V is unchanged.
- If the parent node is an AND threshold marked with vector , nought is filled at the end of the vector to make the length of equal to the counter value. Then, the left node is marked with , where the number of zero is V, and the right node is marked with . Finally, the value of the counter V is increased by one.
3.3. Hyperledger Fabric
3.4. Interplanetary File System (IPFS)
3.5. MA-CPABE Scheme
4. System Model
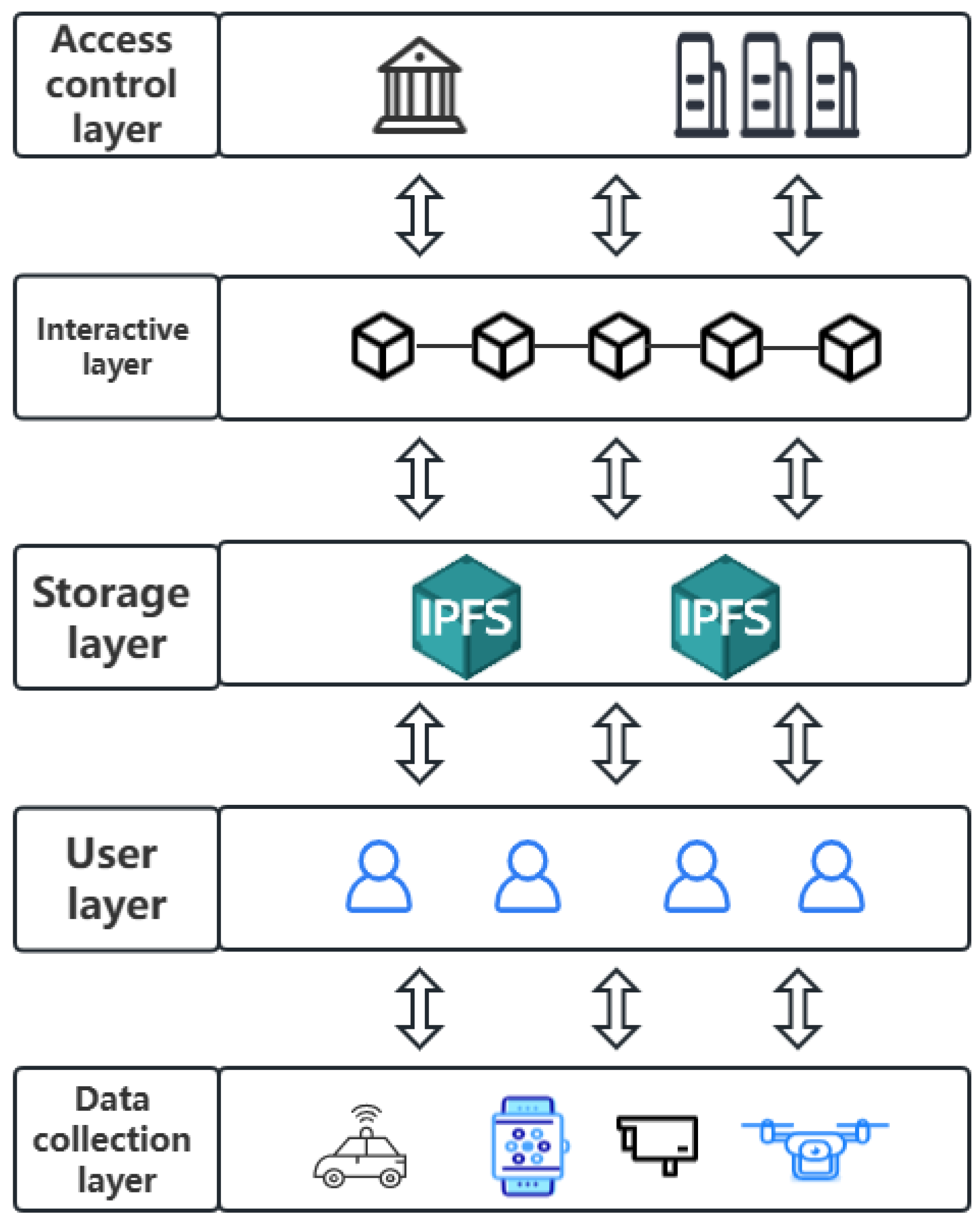
4.1. System Architecture
4.2. System Model
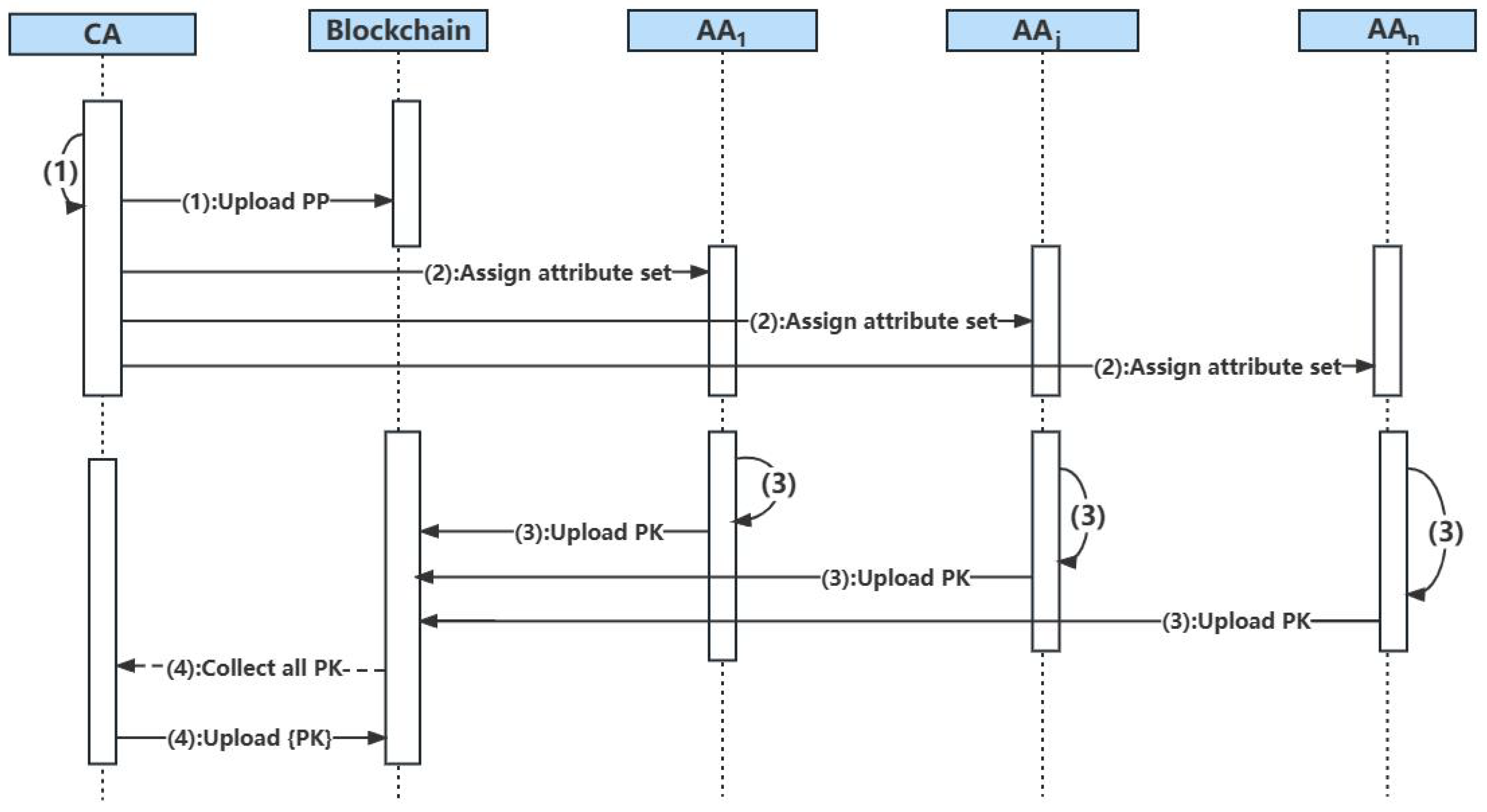
- CA generates the public parameter and publishes it to the blockchain. Moreover, it distributes different attribute sets for each attribute authority.
- Each attribute authority generates a key pair based on the attribute it manages and uploads its public key to the blockchain.
- CA collects all to the attribute public key set and publishes it to the blockchain.
- When system users such as DO and DV apply to join the blockchain, they need to register with the CA to obtain the corresponding digital certificate and system parameters (including the attribute public key set and public parameter ).
- DO encrypts data with the symmetric encryption algorithm AES to obtain ciphertext , where the key of the symmetric encryption algorithm AES is represented by .
- DO stores in IPFS.
- IPFS returns addressing hash to DO.
- DO constructs the access policy of the data and encrypts by using the MA-CPABE to obtain ciphertext .
- DO constructs a DET based on various pieces of information about the data, and each DET corresponds to the identity () of the data on the blockchain (one corresponds to a unique DET). The smart contract UploadData is called to upload the DET and the corresponding attribute threshold T in the access policy.
- DV applies for attribute sub-tokens to AA through blockchain. Attribute authority issues attribute sub-token to DV according to the identity of DV and the attribute at managed by them-self.
- DV calls the smart contract ReadData to query part of the data information of all DETs in the current blockchain ledger, such as data summary, data size, data identity, etc. DV determines which data it needs using the descriptive information of the data.
- DV determines the needed data, calls the data access smart contract AccessData according to the of the data, and uploads its attribute sub-token set. If the attribute sub-token set uploaded by the DV satisfies the access policy and attribute threshold set by DO, the DET of the data can be successfully accessed, and the decryption key will be generated.
- DV retrieves the ciphertext stored in IPFS according to the data hash address in DET.
- DV uses to decrypt the ciphertext in DET to obtain the symmetric key . Then, DV uses to decrypt the ciphertext to obtain the original data information .
5. Scheme Overview
5.1. Scheme Specific Process
5.1.1. System Initialization
- (1)
- CA runs the system initialization algorithm , in which the security parameter q is entered, and the global parameter of the system is obtained and published to the blockchain. The details are as follows.The initialization algorithm of the system is to input a large prime number q as the security parameter and output the public parameter of the system. E is an elliptic curve in the finite domain of the q order finite field. A point G on the r order cyclic group containing all points on E is selected as the generator, and all points in are generated by , where . The positive integer h is an auxiliary factor mainly used to calculate . Each user in the system has a unique identifier , and the user identifier is mapped to the element of through the hash function .
- (2)
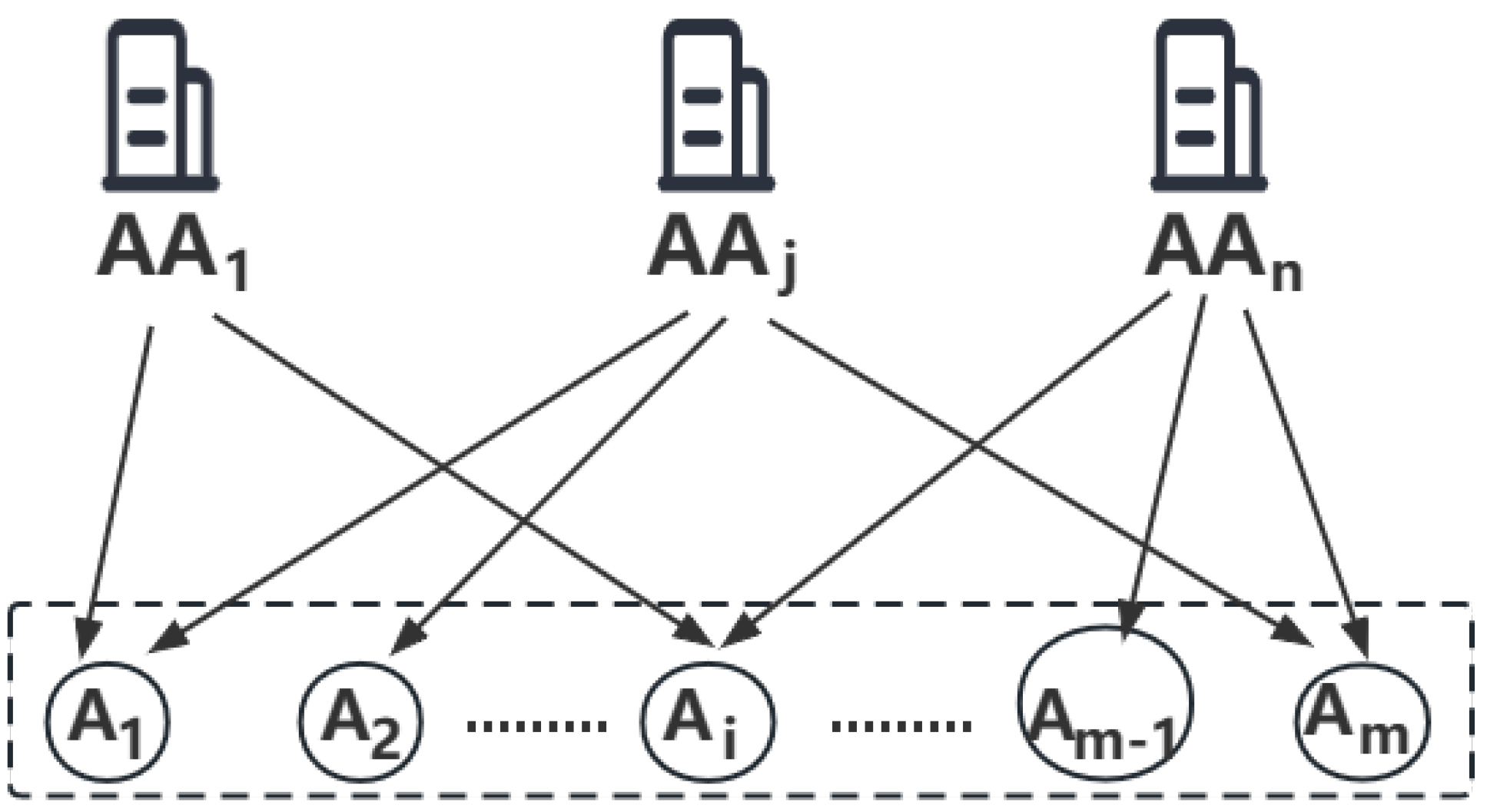
- CA randomly assigns attributes to AA, and each attribute needs to be jointly managed by x attribute authorities. Each AA obtains different attribute sets for management.
- (3)
- AA run algorithm . Each AA generates its key pairs according to the attribute set , then uploads its public key to the blockchain. The algorithm details are as follows.Each AA randomly selects an integer as its private key and the corresponding public key is calculated. For each attribute in the system, the AA randomly selects an integer as the private key and as the public key.
- (4)
- CA collects the public key uploaded by all AA, aggregates these attribute public keys into a public key set and publishes it to the blockchain.
5.1.2. Data Encryption
- 5.
- DO first computes a hash value for the with the SHA-1 algorithm and then encrypts to obtain ciphertext with AES algorithm.
- 6.
- DO stores the encrypted ciphertext in IPFS. Then, IPFS returns the corresponding address hash value .
- 7.
- DO applies for permission to join the blockchain network through CA. If the application is accepted, , digital certificate in the blockchain and attribute public key set will be returned.
- 8.
- DO constructs the access policy and executes the encryption algorithmto encrypt the AES key to obtain the key ciphertext . The algorithm is as follows.
- (a)
- First, it maps the key to be encrypted to point M on the elliptic curve E, then it randomly selects an integer and calculates .
- (b)
- It takes the access policy set by DO as the input, then outputs the access matrix A of n × l and maps the attributes in the access policy to matrix A using the function .
- (c)
- It selects vectors and at random and calculates and , respectively, where represents the x-th row of the matrix A.
- (d)
- Finally, the ciphertexts are calculated by and, respectively.
- 9.
- DO constructs DET based on information such as ciphertext and data hash address . The DET details are shown in Figure 7.Data description: Descriptive information of data.DataID: The unique identifier of data on the blockchain, including the enterprise name and number. This is the basis for querying the data information. Holder: Enterprise name of the data owner. DataSummary: Summary description of data information. ID: The unique identifier of DO in the blockchain is the blockchain address. Sign: Digital signature of DO. Size: The size of data.Data privacy: Data privacy information.Hash: The data address returned by IPFS and the only basis for querying data. CT: The ciphertext AES key is encrypted with MA-CPABE. hash: The hash of data plaintext is the basis for checking data integrity.
- 10.
- DO uploads the DET to the blockchain through the smart contract UploadData (see Section 5.2.1 for more information) and sets the access attribute threshold t for the data.
5.1.3. Data Access
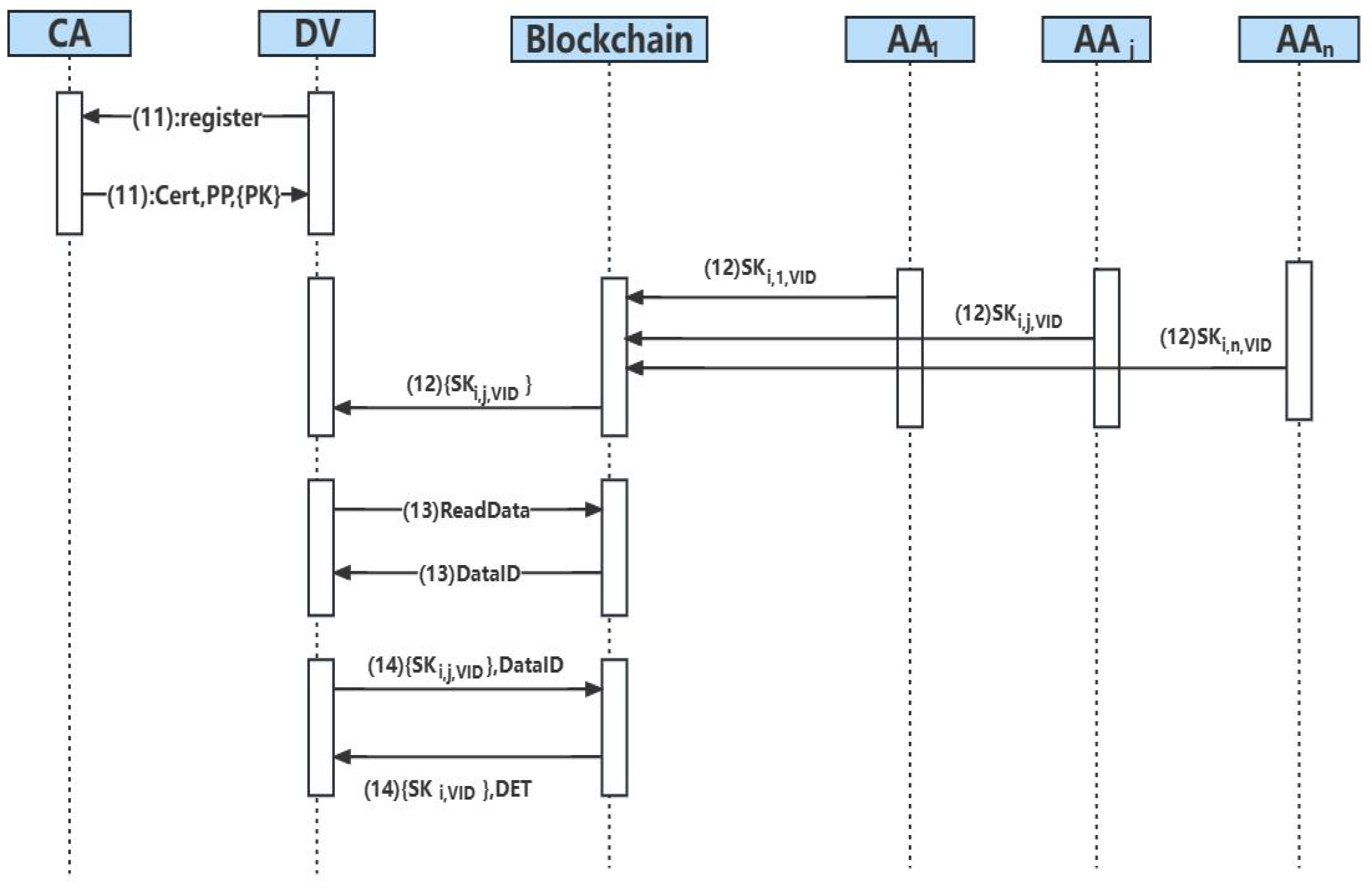
- 11.
- DV applies to join the blockchain. CA agrees to return DV’s digital certificate in the blockchain, which includes DV’s unique identifier in the system, as well as the global parameter and attribute public key set that needs to be used in the subsequent decryption process.
- 12.
- DV applies for attribute identity through blockchain. AA run algorithmin the system to issue attribute sub-token according to DV identity. The algorithm is as follows.The AA generates the attribute key of attribute for users with . The key calculation method is as follows.
- 13.
- DV uses the smart contract ReadData to query information of the data description part in all DET (see Section 5.2.2 for more information). Then, it finds the needed data according to the returned data description information, where is the basis for subsequent query.
- 14.
- The DV uploads its own set of attribute tokens and invokes smart contract AccessData to query all the corresponding information based on the (see Section 5.2.3 for details). If the attribute security threshold t set by DO is satisfied, the DET of the data can be successfully accessed, and the attribute decryption key is generated.
5.1.4. Data Decryption
- 15.
- DV Downloads DET and the decryption key , and retrieves the ciphertext from the IPFS according to the storage address in the DET.
- 16.
- DV runs the decryption algorithm to obtain the decryption key of AES. The algorithm is as follows.To successfully decrypt the ciphertext, the DV first needs to find a suitable set of rows in matrix A, where needs to be in these rows; submits its identity identifier and of each line x; and then performs the calculation.Based on the above results, it is necessary to continue calculating.The DV selects integer , which satisfies , and performs the computation.When and . DV decrypts the point M.Last maps M back to the AES key .
- 17.
- DV uses the symmetric key obtained by the attribute decryption algorithm to decrypt the data ciphertext .
- 18.
- DV hashes the data to obtain using SHA-1 and compares the calculated hash value with in DET. The data remain the same if the two hashes are the same.
5.2. Contract Introduction
5.2.1. UploadData
| Algorithm 1 UploadData() |
| Input: DataId,Holder,ID,Sign,DataSummary,Size,Hash,CT,hash,T Output: bool
|
5.2.2. ReadData
| Algorithm 2 ReadData() |
| Input: Output:
|
5.2.3. AccessData
| Algorithm 3 AccessData() |
| Input: () Output:
|
6. Experiments and Results
6.1. Security Analysis
6.2. Scheme Analysis
6.3. System Performance Analysis
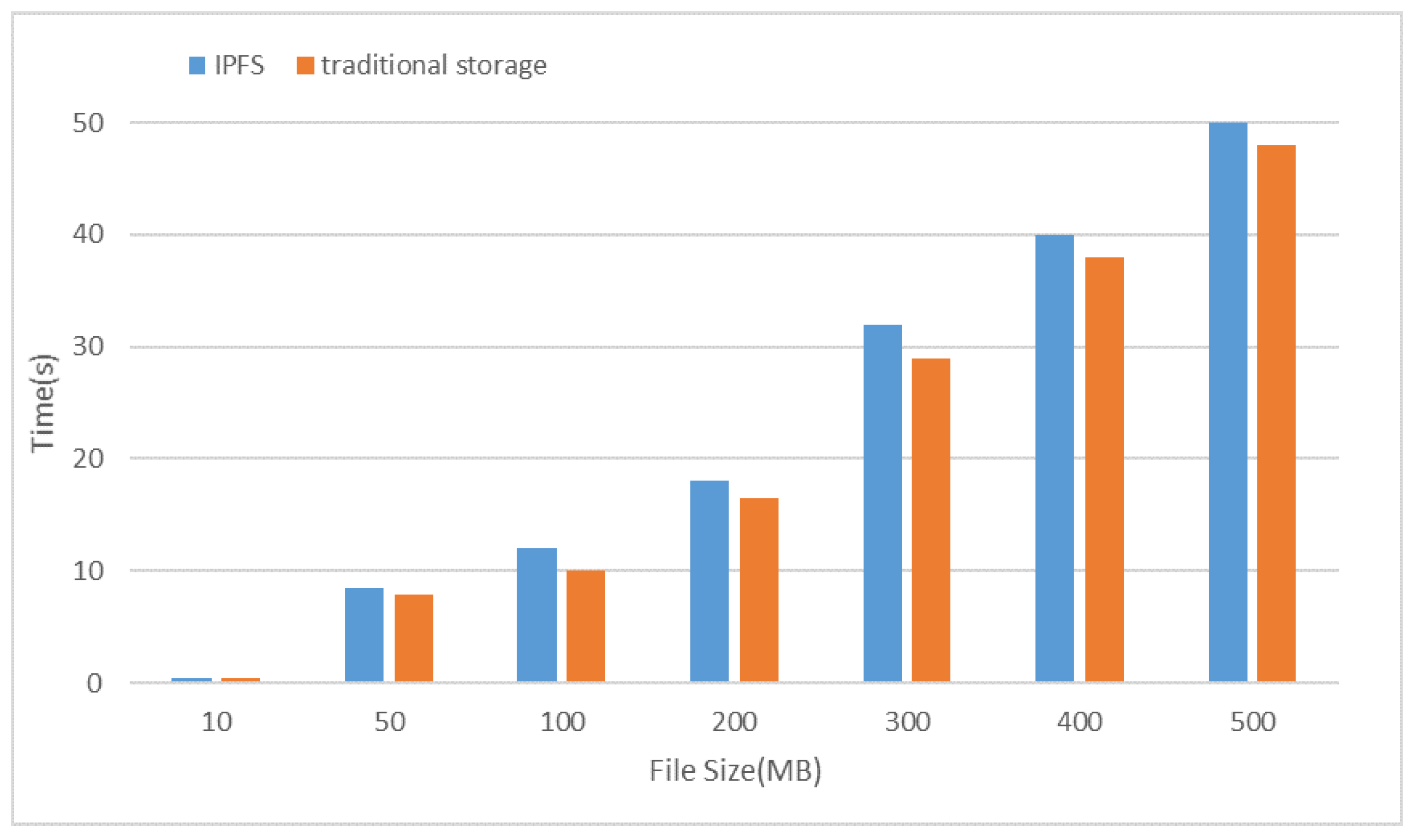
6.3.1. Data Storage Analysis
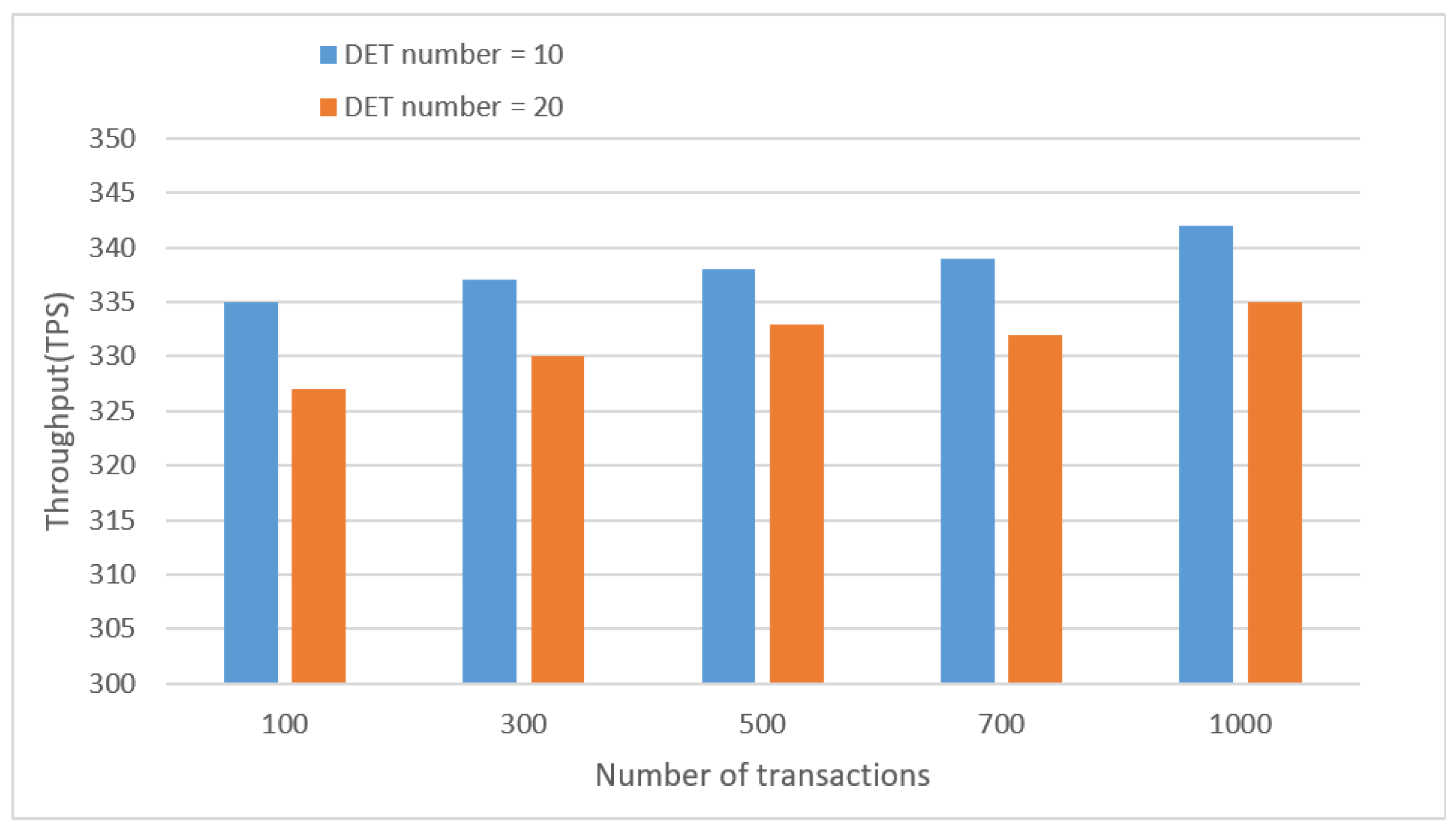
6.3.2. Smart Contract
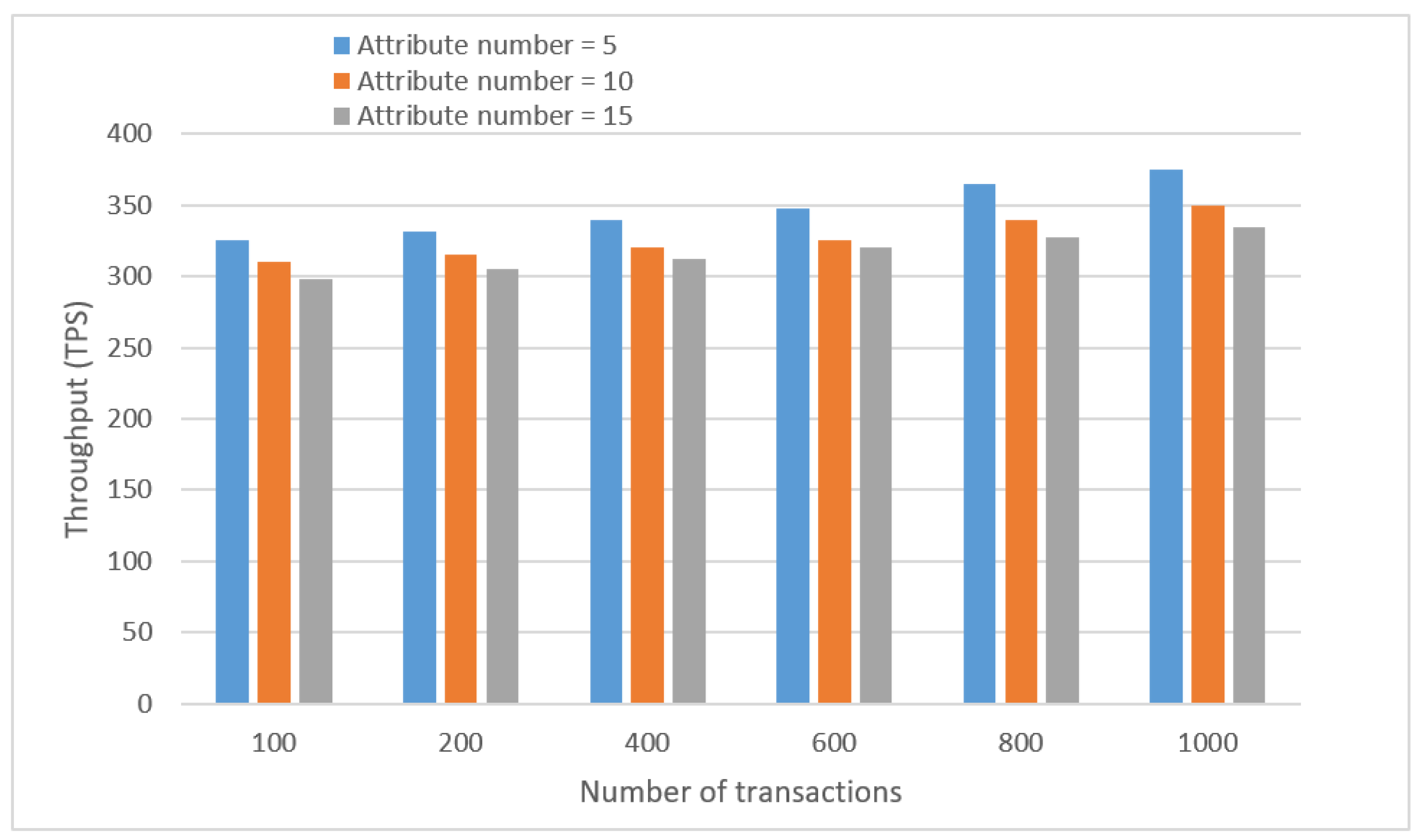
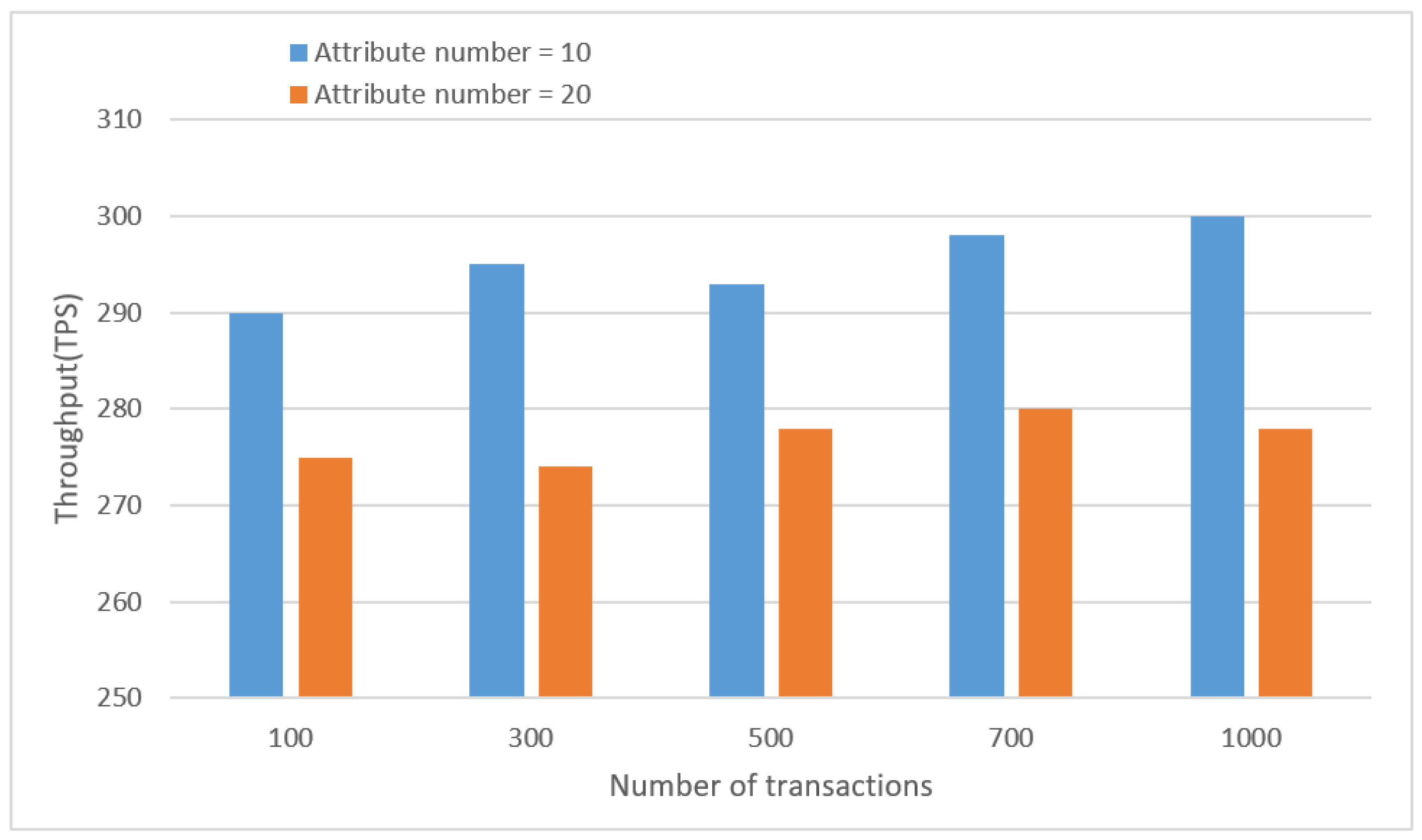
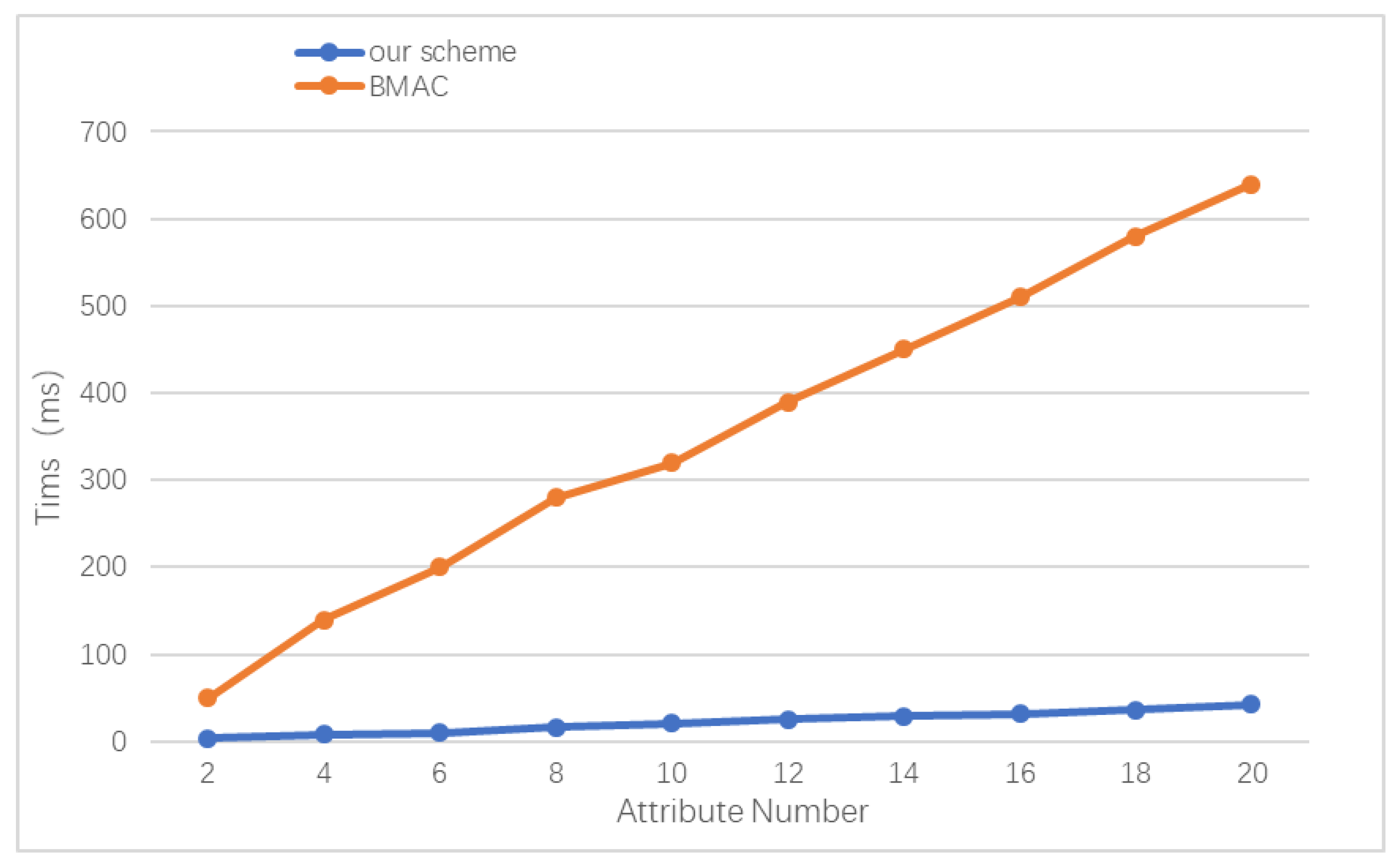
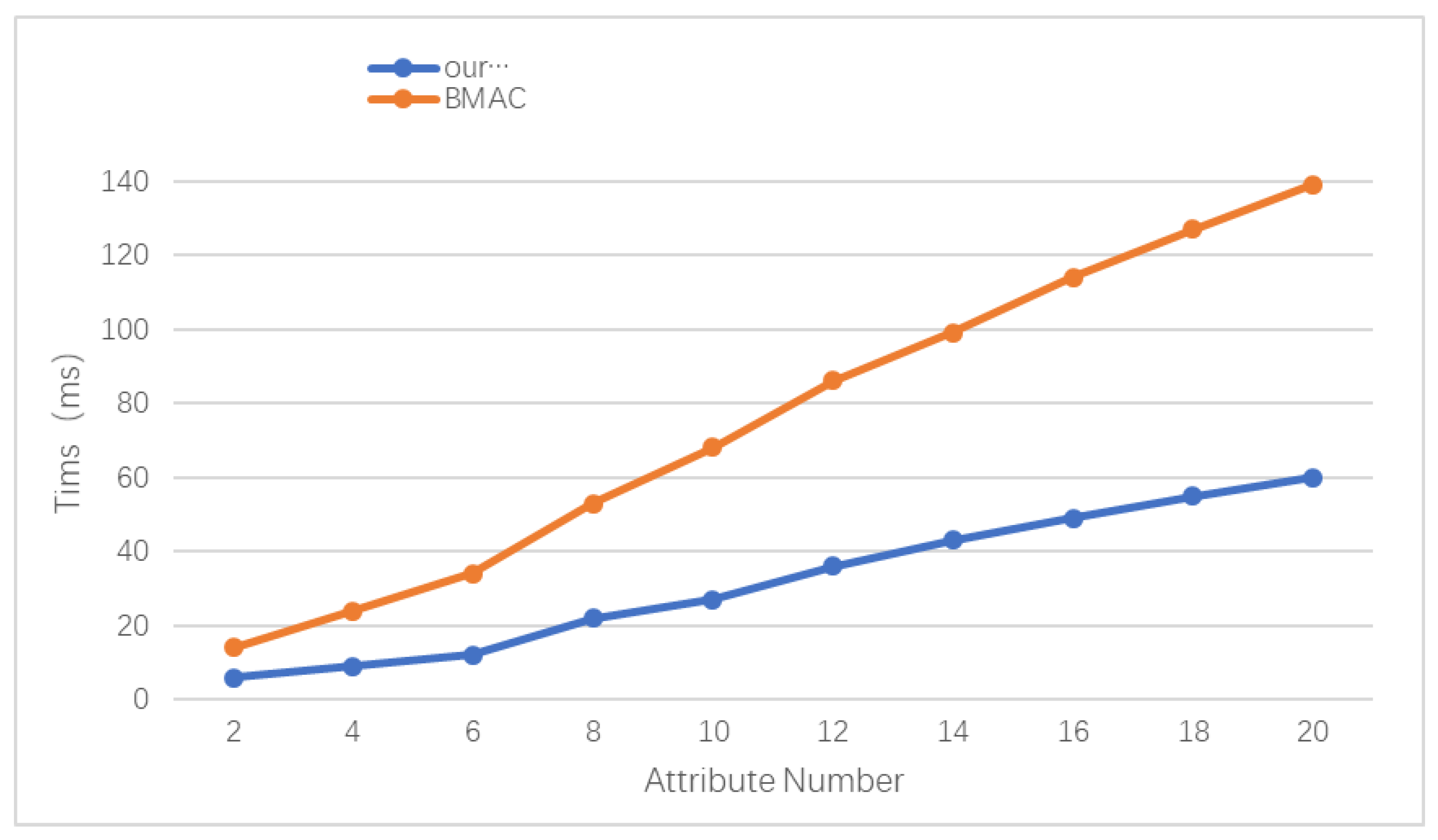
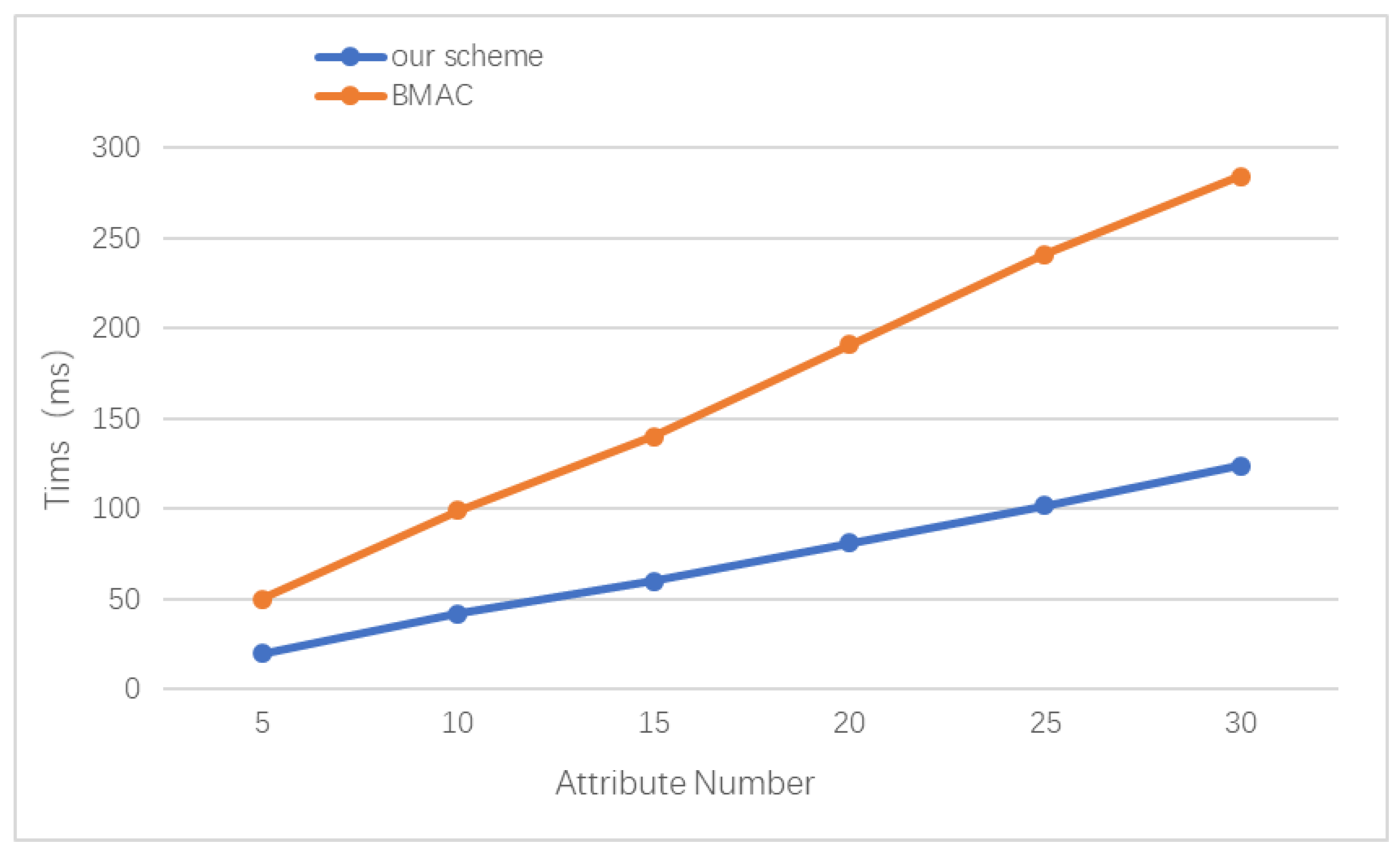
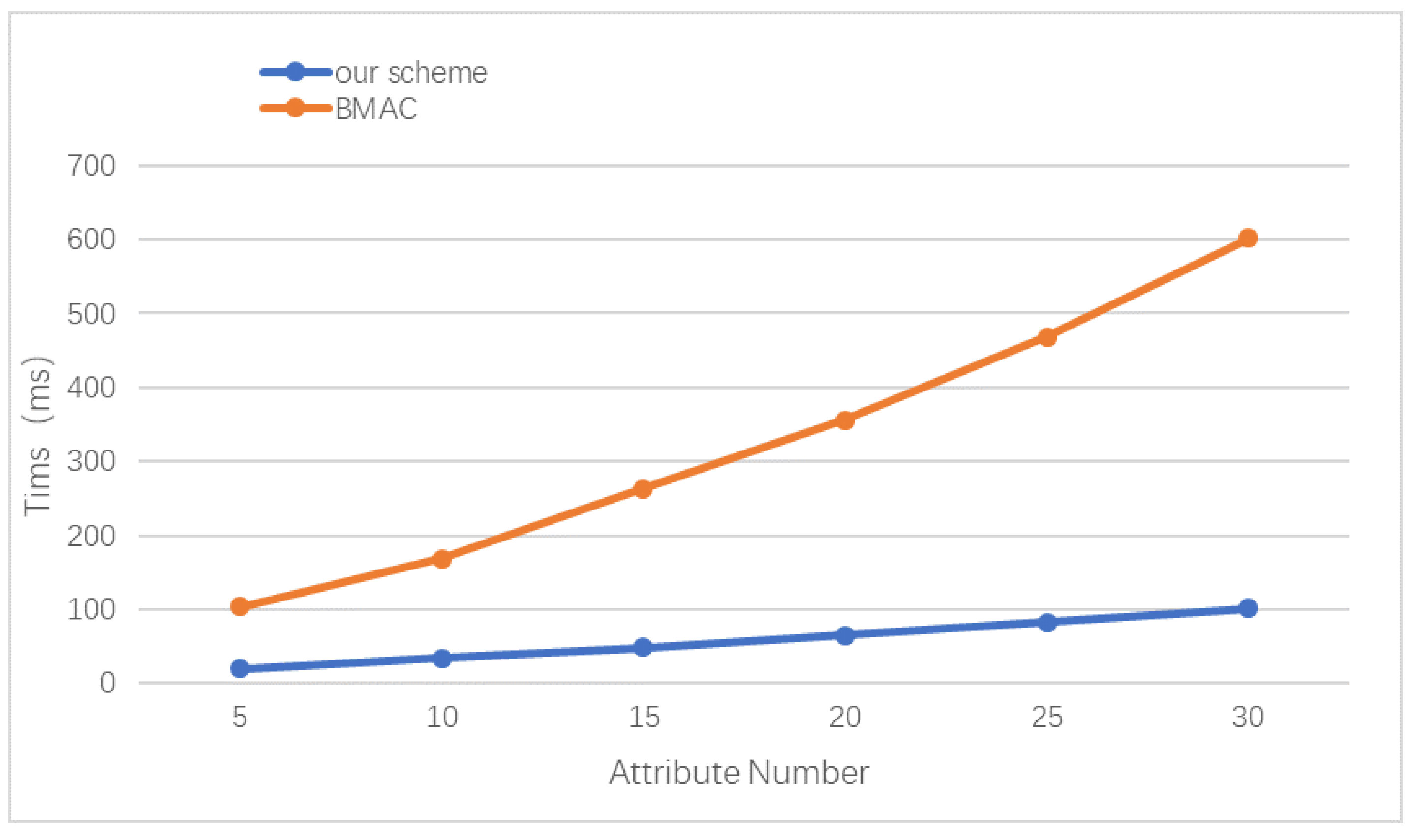
6.3.3. Attribute Encryption Analysis
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Qiu, J.; Tian, Z.; Du, C.; Zuo, Q.; Su, S.; Fang, B. A survey on access control in the age of internet of things. IEEE Internet Things J. 2020, 7, 4682–4696. [Google Scholar] [CrossRef]
- Feng, C.; Yu, K.; Bashir, A.K.; Al-Otaibi, Y.D.; Lu, Y.; Chen, S.; Zhang, D. Efficient and secure data sharing for 5G flying drones: A blockchain-enabled approach. IEEE Netw. 2021, 35, 130–137. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Nakamoto, S.; Bitcoin, A. A peer-to-peer electronic cash system. Bitcoin 2008, 4. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 February 2023).
- Javaid, M.; Haleem, A.; Singh, R.P.; Khan, S.; Suman, R. Blockchain technology applications for Industry 4.0: A literature-based review. Blockchain Res. Appl. 2021, 2, 100027. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H. Assessing blockchain consensus and security mechanisms against the 51% attack. Appl. Sci. 2019, 9, 1788. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Sun, P. Security and privacy protection in cloud computing: Discussions and challenges. J. Netw. Comput. Appl. 2020, 160, 102642. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; pp. 321–334. [Google Scholar]
- Lewko, A.; Waters, B. Decentralizing attribute-based encryption. In Advances in Cryptology–EUROCRYPT 2011: Proceedings of the 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, Estonia, 15–19 May 2011; Proceedings 30; Springer: Berlin/Heidelberg, Germany, 2011; pp. 568–588. [Google Scholar]
- Rouselakis, Y.; Waters, B. Efficient statically-secure large-universe multi-authority attribute-based encryption. In Financial Cryptography and Data Security: Proceedings of the 19th International Conference, FC 2015, San Juan, Puerto Rico, 26–30 January 2015; Revised Selected Papers; Springer: Berlin/Heidelberg, Germany, 2015; pp. 315–332. [Google Scholar]
- Sandhia, G.; Raja, S.K. Secure sharing of data in cloud using MA-CPABE with elliptic curve cryptography. J. Ambient. Intell. Humaniz. Comput. 2022, 13, 3893–3902. [Google Scholar] [CrossRef]
- Wang, Q.; Jin, H. Data leakage mitigation for discretionary access control in collaboration clouds. In Proceedings of the 16th ACM Symposium on Access Control Models and Technologies, Innsbruck Austria, 15–17 June 2011; pp. 103–112. [Google Scholar]
- Kamboj, P.; Khare, S.; Pal, S. User authentication using Blockchain based smart contract in role-based access control. Peer-to-Peer Netw. Appl. 2021, 14, 2961–2976. [Google Scholar] [CrossRef]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-based access control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Chase, M. Multi-authority attribute based encryption. In Theory of Cryptography: Proceedings of the 4th Theory of Cryptography Conference, TCC 2007, Amsterdam, The Netherlands, 21–24 February 2007; Proceedings 4; Springer: Berlin/Heidelberg, Germany, 2007; pp. 515–534. [Google Scholar]
- Yang, J.; Wen, J.; Jiang, B.; Wang, H. Blockchain-based sharing and tamper-proof framework of big data networking. IEEE Netw. 2020, 34, 62–67. [Google Scholar] [CrossRef]
- Guo, S.; Hu, X.; Guo, S.; Qiu, X.; Qi, F. Blockchain meets edge computing: A distributed and trusted authentication system. IEEE Trans. Ind. Inform. 2019, 16, 1972–1983. [Google Scholar] [CrossRef]
- Alshalali, T.; M’Bale, K.; Josyula, D. Security and privacy of electronic health records sharing using hyperledger fabric. In Proceedings of the 2018 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 12–14 December 2018; pp. 760–763. [Google Scholar]
- Chen, C.L.; Yang, J.; Tsaur, W.J.; Weng, W.; Wu, C.M.; Wei, X. Enterprise data sharing with privacy-preserved based on hyperledger fabric blockchain in IIOT’s application. Sensors 2022, 22, 1146. [Google Scholar] [CrossRef]
- Liu, H.; Han, D.; Li, D. Fabric-IoT: A blockchain-based access control system in IoT. IEEE Access 2020, 8, 18207–18218. [Google Scholar] [CrossRef]
- Lu, X.; Fu, S.; Jiang, C.; Lio, P. A fine-grained IoT data access control scheme combining attribute-based encryption and blockchain. Secur. Commun. Netw. 2021, 2021, 5308206. [Google Scholar] [CrossRef]
- Liang, W.; Yang, Y.; Yang, C.; Hu, Y.; Xie, S.; Li, K.C.; Cao, J. PDPChain: A consortium blockchain-based privacy protection scheme for personal data. IEEE Trans. Reliab. 2022, 1–13. [Google Scholar] [CrossRef]
- Eltayieb, N.; Elhabob, R.; Hassan, A.; Li, F. A blockchain-based attribute-based signcryption scheme to secure data sharing in the cloud. J. Syst. Archit. 2020, 102, 101653. [Google Scholar] [CrossRef]
- Cong, R.; Liu, Y.; Tago, K.; Li, R.; Asaeda, H.; Jin, Q. Individual-initiated auditable access control for privacy-preserved iot data sharing with blockchain. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Gao, H.; Ma, Z.; Luo, S.; Xu, Y.; Wu, Z. BSSPD: A blockchain-based security sharing scheme for personal data with fine-grained access control. Wirel. Commun. Mob. Comput. 2021, 2021, 6658920. [Google Scholar] [CrossRef]
- Zhang, L.; Kan, H.; Huang, H. Patient-centered cross-enterprise document sharing and dynamic consent framework using consortium blockchain and ciphertext-policy attribute-based encryption. In Proceedings of the 19th ACM International Conference on Computing Frontiers, Turin, Italy, 17–22 May 2022; pp. 58–66. [Google Scholar]
- Guo, H.; Li, W.; Nejad, M.; Shen, C.C. Access control for electronic health records with hybrid blockchain-edge architecture. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 44–51. [Google Scholar]
- Sammy, F.; Vigila, S. An efficient blockchain based data access with modified hierarchical attribute access structure with CP-ABE using ECC scheme for patient health record. Secur. Commun. Netw. 2022, 2022, 8685273. [Google Scholar] [CrossRef]
- Qin, X.; Huang, Y.; Yang, Z.; Li, X. A blockchain-based access control scheme with multiple attribute authorities for secure cloud data sharing. J. Syst. Archit. 2021, 112, 101854. [Google Scholar] [CrossRef]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer Science Business Media: New York, NY, USA, 2006. [Google Scholar]
- Beimel, A. Secure Schemes for Secret Sharing and Key Distribution; Technion-Israel Institute of Technology & Faculty of Computer Science: Haifa, Israel, 1996. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Trautwein, D.; Raman, A.; Tyson, G.; Castro, I.; Scott, W.; Schubotz, M.; Gipp, B.; Psaras, Y. Design and evaluation of IPFS: A storage layer for the decentralized web. In Proceedings of the ACM SIGCOMM 2022 Conference, Amsterdam, The Netherlands, 22–26 August 2022; pp. 739–752. [Google Scholar]




| Bitcoin | Ethereum | Corda | Hyperledger Fabric | |
|---|---|---|---|---|
| Category | Public Blockchain | Public Blockchain | Distributed Ledger Platform | Consortium Blockchain |
| Description | Generic blockchain platform | Generic blockchain platform | Financial Industry Special Platform | Modular blockchain platform |
| Consensus algorithms | POW | POW, POS | Notary mechanism | PBFT |
| Smart contract | No | Yes (Solidity) | Yes (Kotlin, Java) | Yes (Go, Java) |
| Privacy | No | No | Yes | Yes |
| Scalability | No | No | No | Yes |
| Currency | Yes | Yes | No | No |
| Identity Authentication | No | No | Yes (digital certificate) | Yes (digital certificate) |
| Scheme | Distributed Data Storage | Data Integrity | Eliminate Duplicate Data | ABAC | Decentralized Access Authorization |
|---|---|---|---|---|---|
| [21] | Y | N | Y | N | N |
| [23] | Y | Y | N | Y | N |
| [31] | N | N | N | Y | Y |
| Ours | Y | Y | Y | Y | Y |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, B.; Zhou, Y.-P.; Yi, X.-Y.; Wang, C.-Y. An Improved Multi-Authority Attribute Access Control Scheme Base on Blockchain and Elliptic Curve for Efficient and Secure Data Sharing. Electronics 2023, 12, 1691. https://doi.org/10.3390/electronics12071691
Xie B, Zhou Y-P, Yi X-Y, Wang C-Y. An Improved Multi-Authority Attribute Access Control Scheme Base on Blockchain and Elliptic Curve for Efficient and Secure Data Sharing. Electronics. 2023; 12(7):1691. https://doi.org/10.3390/electronics12071691
Chicago/Turabian StyleXie, Ben, Yu-Ping Zhou, Xin-Yu Yi, and Chen-Ye Wang. 2023. "An Improved Multi-Authority Attribute Access Control Scheme Base on Blockchain and Elliptic Curve for Efficient and Secure Data Sharing" Electronics 12, no. 7: 1691. https://doi.org/10.3390/electronics12071691
APA StyleXie, B., Zhou, Y.-P., Yi, X.-Y., & Wang, C.-Y. (2023). An Improved Multi-Authority Attribute Access Control Scheme Base on Blockchain and Elliptic Curve for Efficient and Secure Data Sharing. Electronics, 12(7), 1691. https://doi.org/10.3390/electronics12071691







