Blockchain-Assisted Cybersecurity for the Internet of Medical Things in the Healthcare Industry
Abstract
1. Introduction
- The functional architecture of blockchain technology in ensuring cybersecurity aspects of the healthcare industry.
- An overview of the Internet of Medical Things and its functional features.
- Details on Blockchain-Assisted Cybersecurity for the Internet of Medical Things in the healthcare industry with the proposed model.
2. Literature Study
3. Functional Architecture of Blockchain
- Immutability indicates that falsifications of data kept in blockchain are exceedingly difficult since even little changes might result in incorrect data.
- Transactional non-repudiation can be enabled by digital signatures, non-symmetric encryption/decryption methods, and decentralized consensus procedures.
- Traceability denotes the ability to track data sources by examining currently accessible blockchain data with accompanying metadata.
- Diversity of blockchain enables transactions to be authenticated by the number of users spread across the network without the need for a central authority. In this manner, administrative costs may be reduced, while system dependability is improved.
- Open blockchains;
- Personal blockchains;
- Collaborative blockchains.
4. Overview of Internet of Medical Things (IoMT)
- A lack of compatibility across various IoMT domains;
- Confidentiality and cybersecurity flaws in the IoMT instruments and networks.
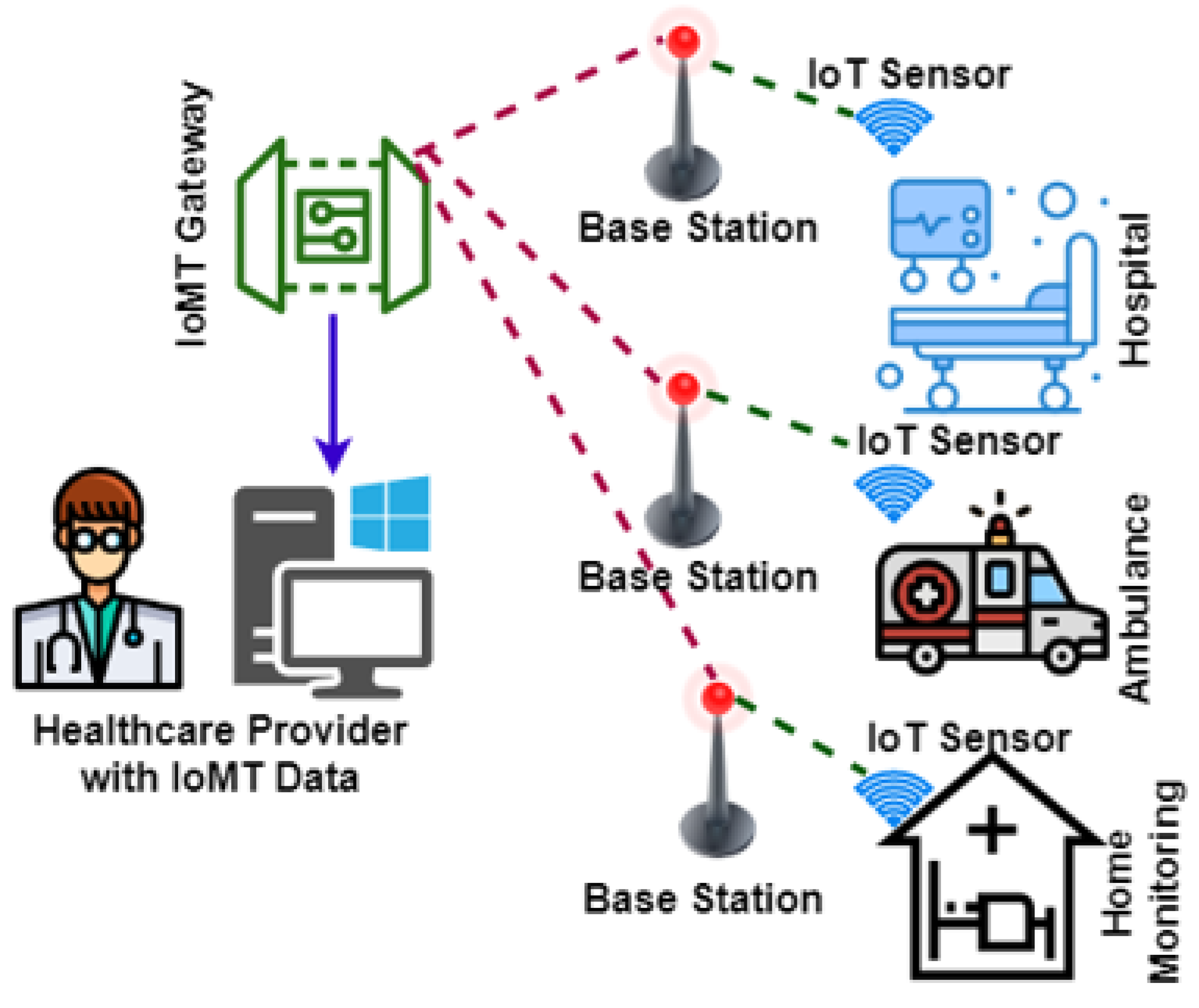
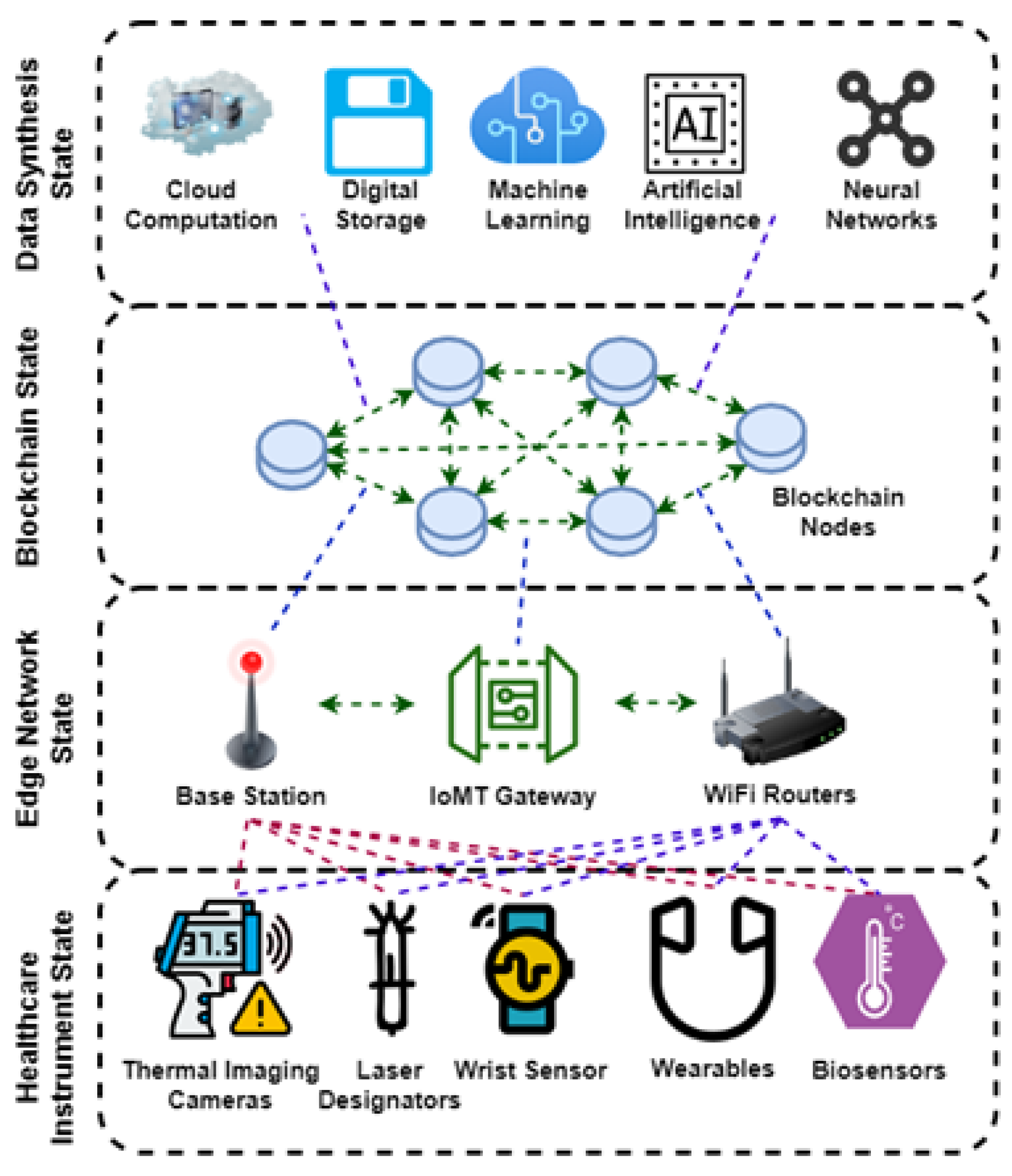
5. Blockchain-Assisted Cybersecurity for the Internet of Medical Things
- Healthcare instrument state;
- Blockchain state;
- Edge network state;
- Data synthesis state.
The BCCS Model
6. Experimental Results and Discussion
6.1. Precision Analysis
6.2. Reliability Aspects
6.3. Security Rate
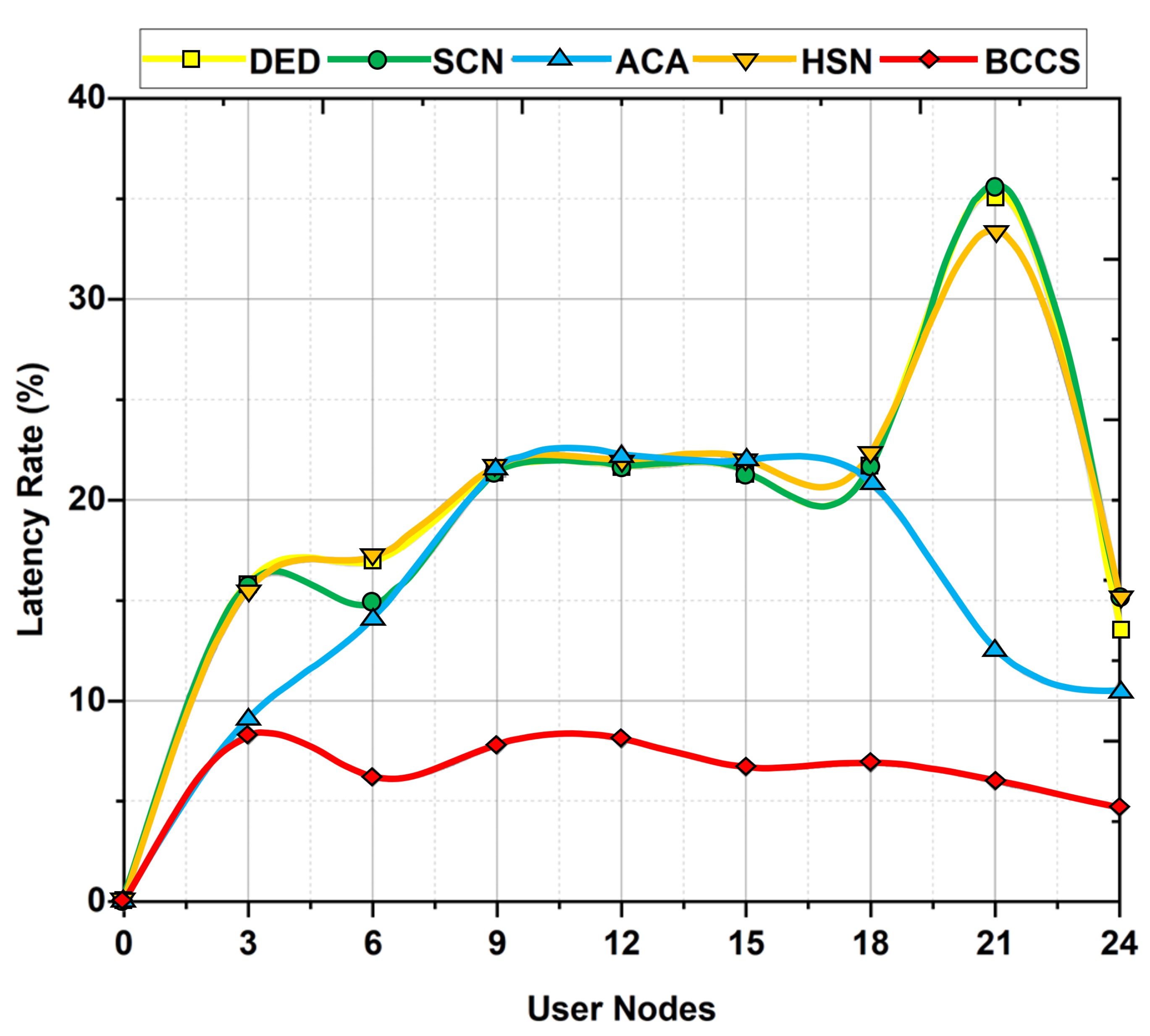
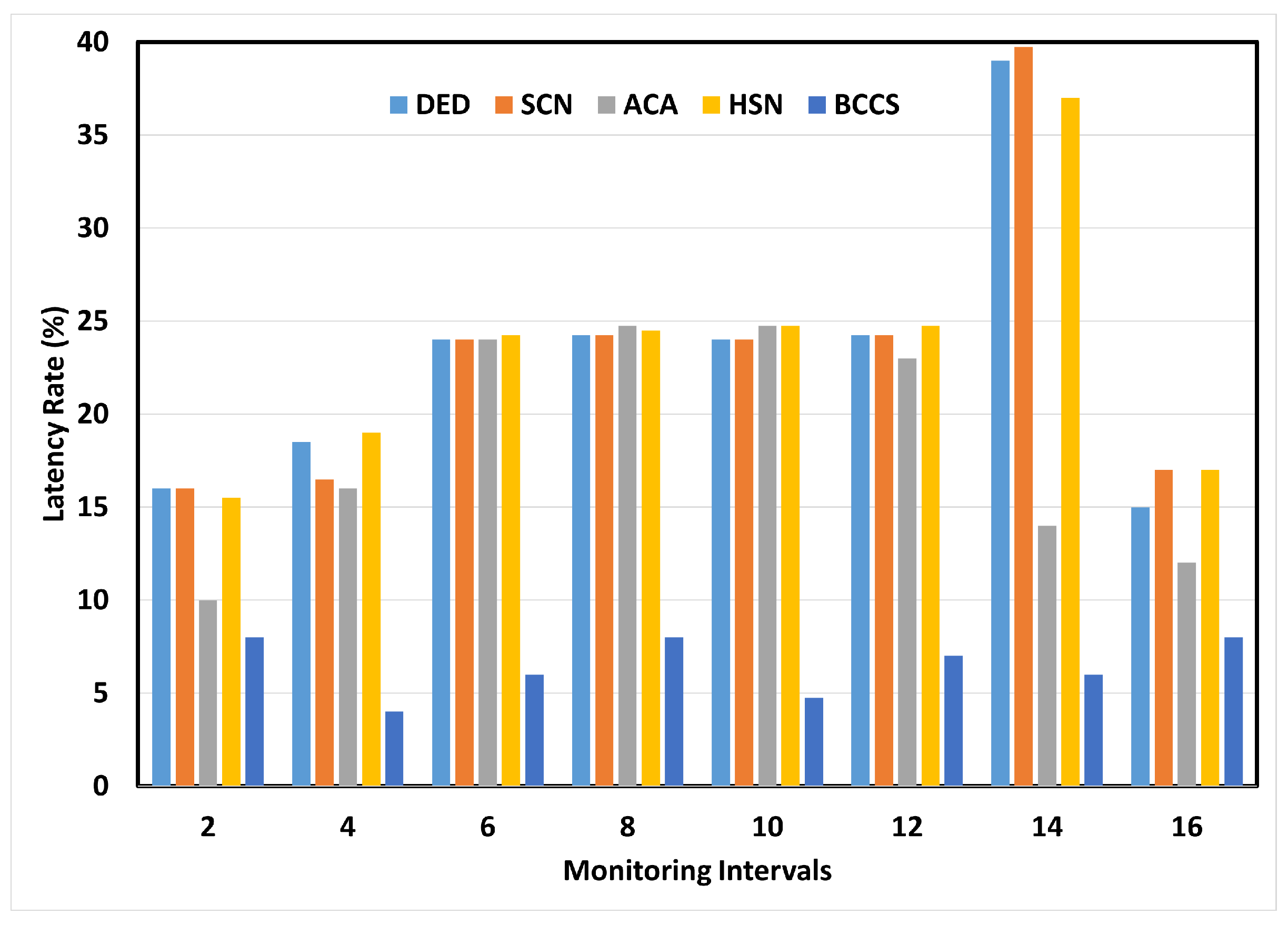
6.4. Latency Rate Analysis
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ray, P.P.; Dash, D. Blockchain for IoT-based medical delivery drones: State of the art, issues, and future prospects. Blockchain Technol. Emerg. Appl. 2022, 137–176. [Google Scholar] [CrossRef]
- Razdan, S.; Sharma, S. Internet of medical things (IoMT): Overview, emerging technologies, and case studies. IETE Tech. Rev. 2022, 39, 775–788. [Google Scholar] [CrossRef]
- Elsayeh, M.; Ezzat, K.A.; El-Nashar, H.; Omran, L.N. Cybersecurity architecture for the Internet of Medical Things and connected devices using blockchain. Biomed. Eng. Appl. Basis Commun. 2021, 33, 2150013. [Google Scholar] [CrossRef]
- Sharma, A.; Tomar, R.; Chilamkurti, N.; Kim, B.G. Blockchain based smart contracts for Internet of Medical Things in e-healthcare. Electronics 2020, 9, 1609. [Google Scholar] [CrossRef]
- Alqaralleh, B.A.; Vaiyapuri, T.; Parvathy, V.S.; Gupta, D.; Khanna, A.; Shankar, K. Blockchain-assisted secure image transmission and diagnosis model on Internet of Medical Things Environment. Pers. Ubiquitous Comput. 2021, 1–11. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Zeadally, S.; Vuduthala, A.B. Cyber-Physical Cloud Manufacturing Systems With Digital Twins. IEEE Internet Comput. 2021, 26, 15–21. [Google Scholar] [CrossRef]
- Karrupusamy, P.; Balas, V.E.; Shi, Y. Sustainable Communication Networks and Application: Proceedings of ICSCN 2021; Springer: New York, NY, USA, 2022. [Google Scholar]
- Hu, L.; Nguyen, N.T.; Tao, W.; Leu, M.C.; Liu, X.F.; Shahriar, M.R.; Al Sunny, S.N. Modeling of cloud-based digital twins for smart manufacturing with MT connect. Procedia Manuf. 2018, 26, 1193–1203. [Google Scholar] [CrossRef]
- Dash, R.K.; Nguyen, T.N.; Cengiz, K.; Sharma, A. Fine-tuned support vector regression model for stock predictions. Neural Comput. Appl. 2021, 1–15. [Google Scholar] [CrossRef]
- Khan, F.; Jan, M.A.; ur Rehman, A.; Mastorakis, S.; Alazab, M.; Watters, P. A secured and intelligent communication scheme for IIoT-enabled pervasive edge computing. IEEE Trans. Ind. Inform. 2020, 17, 5128–5137. [Google Scholar] [CrossRef]
- Yang, S.; Yin, D.; Song, X.; Dong, X.; Manogaran, G.; Mastorakis, G.; Mavromoustakis, C.X.; Batalla, J.M. Security situation assessment for massive MIMO systems for 5G communications. Future Gener. Comput. Syst. 2019, 98, 25–34. [Google Scholar] [CrossRef]
- Manogaran, G.; Alazab, M.; Shakeel, P.M.; Hsu, C.H. Blockchain assisted secure data sharing model for Internet of Things based smart industries. IEEE Trans. Reliab. 2021, 71, 348–358. [Google Scholar] [CrossRef]
- Khan, F.; Kumar, R.L.; Kadry, S.; Nam, Y.; Meqdad, M.N. Cyber physical systems: A smart city perspective. Int. J. Electr. Comput. Eng. 2021, 11, 3609–3616. [Google Scholar] [CrossRef]
- Jegadeesan, S.; Azees, M.; Kumar, P.M.; Manogaran, G.; Chilamkurti, N.; Varatharajan, R.; Hsu, C.H. An efficient anonymous mutual authentication technique for providing secure communication in mobile cloud computing for smart city applications. Sustain. Cities Soc. 2019, 49, 101522. [Google Scholar] [CrossRef]
- Ahmed, S.H.; Bashir, A.K.; Guibene, W. Introduction to the special section on emerging technologies for connected vehicles and ITS networks. Comput. Electr. Eng. 2019, 75, 309–311. [Google Scholar] [CrossRef]
- Fang, L.; Yin, C.; Zhu, J.; Ge, C.; Tanveer, M.; Jolfaei, A.; Cao, Z. Privacy protection for medical data sharing in smart healthcare. ACM Trans. Multimed. Comput. Commun. Appl. (TOMM) 2020, 16, 1–18. [Google Scholar] [CrossRef]
- Zhang, P.; Pang, X.; Kibalya, G.; Kumar, N.; He, S.; Zhao, B. GCMD: Genetic correlation multi-domain virtual network embedding algorithm. IEEE Access 2021, 9, 67167–67175. [Google Scholar] [CrossRef]
- Younan, M.; Houssein, E.H.; Elhoseny, M.; Ali, A.E.M. Performance analysis for similarity data fusion model for enabling time series indexing in internet of things applications. PeerJ Comput. Sci. 2021, 7, e500. [Google Scholar] [CrossRef]
- Raza, M.; Kumar, P.M.; Hung, D.V.; Davis, W.; Nguyen, H.; Trestian, R. A digital twin framework for industry 4.0 enabling next-gen manufacturing. In Proceedings of the IEEE 2020 9th International Conference on Industrial Technology and Management (ICITM), Oxford, UK, 11–13 February 2020; pp. 73–77. [Google Scholar]
- Xu, X.; Chen, Y.; Zhang, J.; Chen, Y.; Anandhan, P.; Manickam, A. A novel approach for scene classification from remote sensing images using deep learning methods. Eur. J. Remote Sens. 2021, 54, 383–395. [Google Scholar] [CrossRef]
- Zhang, R.; Ve, S.; Jackson Samuel, R.D. Fuzzy efficient energy smart home management system for renewable energy resources. Sustainability 2020, 12, 3115. [Google Scholar] [CrossRef]
- Xue, K.; Deng, Y.; Zhang, H.; Pandiyan, S.; Manickam, A. Cycling environment investigation and optimization of urban central road in Qingdao. Comput. Intell. 2021, 37, 1217–1235. [Google Scholar] [CrossRef]
- Muñoz-Araque, D.; Garcia, M.H.; Garcia, P.G.; Montenegro, C. Navigation of resources from tangible object recognition to improve virtual tours in botanical gardens. In Information Technology and Systems: Proceedings of ICITS 2020; Springer: New York, NY, USA, 2020; pp. 525–534. [Google Scholar]
- Thapliyal, M.; Ahuja, N.J.; Shankar, A.; Cheng, X.; Kumar, M. A differentiated learning environment in domain model for learning disabled learners. J. Comput. High. Educ. 2022, 34, 60–82. [Google Scholar] [CrossRef]
- Ramesh, S.; Yaashuwanth, C.; Muthukrishnan, B.A. Machine learning approach for secure communication in wireless video sensor networks against denial-of-service attacks. Int. J. Commun. Syst. 2020, 33, e4073. [Google Scholar] [CrossRef]
- Gupta, D.; Rani, S.; Ahmed, S.H.; Garg, S.; Piran, M.J.; Alrashoud, M. ICN-based enhanced cooperative caching for multimedia streaming in resource constrained vehicular environment. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4588–4600. [Google Scholar] [CrossRef]
- Srivastava, A.K.; Grotjahn, R.; Ullrich, P.A. A multimodel technique for estimating future changes in extreme precipitation. In Proceedings of the AGU Fall Meeting Abstracts, San Francisco, CA, USA, 9–13 December 2019; Volume 2019, p. A51Q-2832. [Google Scholar]
- Hammachukiattikul, P.; Sekar, E.; Tamilselvan, A.; Vadivel, R.; Gunasekaran, N.; Agarwal, P. Comparative study on numerical methods for singularly perturbed advanced-delay differential equations. J. Math. 2021, 2021, 6636607. [Google Scholar] [CrossRef]
- Abbas, K.; Tawalbeh, L.A.; Rafiq, A.; Muthanna, A.; Elgendy, I.A.; Abd El-Latif, A.A. Convergence of blockchain and IoT for secure transportation systems in smart cities. Secur. Commun. Netw. 2021, 2021, 5597679. [Google Scholar] [CrossRef]
- Abd El-Latif, A.A.; Abd-El-Atty, B.; Mazurczyk, W.; Fung, C.; Venegas-Andraca, S.E. Secure data encryption based on quantum walks for 5G Internet of Things scenario. IEEE Trans. Netw. Serv. Manag. 2020, 17, 118–131. [Google Scholar] [CrossRef]
- Gao, J.; Wang, H.; Shen, H. Machine learning based workload prediction in cloud computing. In Proceedings of the IEEE 2020 29th International Conference on Computer Communications and Networks (ICCCN), Honolulu, HI, USA, 3–6 August 2020; pp. 1–9. [Google Scholar]
- Gao, J.; Wang, H.; Shen, H. Task failure prediction in cloud data centers using deep learning. IEEE Trans. Serv. Comput. 2020, 15, 1411–1422. [Google Scholar] [CrossRef]
- Ray, P.P.; Dash, D.; Kumar, N. Sensors for Internet of Medical Things: State-of-the-art, security and privacy issues, challenges and future directions. Comput. Commun. 2020, 160, 111–131. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.; Mohanty, S.P. Fortified-chain: A blockchain-based framework for security and privacy-assured Internet of Medical Things with effective access control. IEEE Internet Things J. 2021, 8, 11717–11731. [Google Scholar] [CrossRef]
- Li, X.; Tao, B.; Dai, H.N.; Imran, M.; Wan, D.; Li, D. Is blockchain for Internet of Medical Things a panacea for COVID-19 pandemic? Pervasive Mob. Comput. 2021, 75, 101434. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Shetty, S.; Jo, M. A tutorial and future research for building a blockchain-based secure communication scheme for internet of intelligent things. IEEE Access 2020, 8, 88700–88716. [Google Scholar] [CrossRef]
- Dai, H.N.; Imran, M.; Haider, N. Blockchain-enabled Internet of Medical Things to combat COVID-19. IEEE Internet Things Mag. 2020, 3, 52–57. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. Towards design and implementation of security and privacy framework for Internet of Medical Things (iomt) by leveraging blockchain and ipfs technology. J. Supercomput. 2021, 77, 7916–7955. [Google Scholar] [CrossRef]
- Rayan, R.A.; Tsagkaris, C. Blockchain-based IoT for personalized pharmaceuticals. In Internet of Medical Things; CRC Press: Boca Raton, FL, USA, 2021; pp. 51–62. [Google Scholar]
- Ray, P.P.; Dash, D.; Salah, K.; Kumar, N. Blockchain for IoT-based healthcare: Background, consensus, platforms, and use cases. IEEE Syst. J. 2020, 15, 85–94. [Google Scholar] [CrossRef]
- Rahman, M.A.; Hossain, M.S. An internet-of-medical-things-enabled edge computing framework for tackling COVID-19. IEEE Internet Things J. 2021, 8, 15847–15854. [Google Scholar] [CrossRef] [PubMed]
- Meng, W.; Li, W.; Zhu, L. Enhancing medical smartphone networks via blockchain-based trust management against insider attacks. IEEE Trans. Eng. Manag. 2019, 67, 1377–1386. [Google Scholar] [CrossRef]
- Arul, R.; Raja, G.; Almagrabi, A.O.; Alkatheiri, M.S.; Chauhdary, S.H.; Bashir, A.K. A quantum-safe key hierarchy and dynamic security association for LTE/SAE in 5G scenario. IEEE Trans. Ind. Inform. 2019, 16, 681–690. [Google Scholar] [CrossRef]
- Lee, H.J.; Soe, M.T.; Chauhdary, S.H.; Rhee, S.; Park, M.S. A data aggregation scheme for boundary detection and tracking of continuous objects in WSN. Intell. Autom. Soft Comput. 2017, 23, 135–147. [Google Scholar] [CrossRef]
- Riya, K.; Surendran, R.; Tavera Romero, C.A.; Sendil, M.S. Encryption with User Authentication Model for Internet of Medical Things Environment. Intell. Autom. Soft Comput. 2023, 35, 507–520. [Google Scholar] [CrossRef]
- Raja, G.; Kottursamy, K.; Dev, K.; Narayanan, R.; Raja, A.; Karthik, K.B.V. Blockchain-Integrated Multiagent Deep Reinforcement Learning for Securing Cooperative Adaptive Cruise Control. IEEE Trans. Intell. Transp. Syst. 2022, 23, 9630–9639. [Google Scholar] [CrossRef]
- Sadayapillai, B.; Kottursamy, K. A Blockchain-Based Framework for Transparent, Secure, and Verifiable Online Examination System. J. Uncertain Syst. 2022, 15, 2241002. [Google Scholar] [CrossRef]

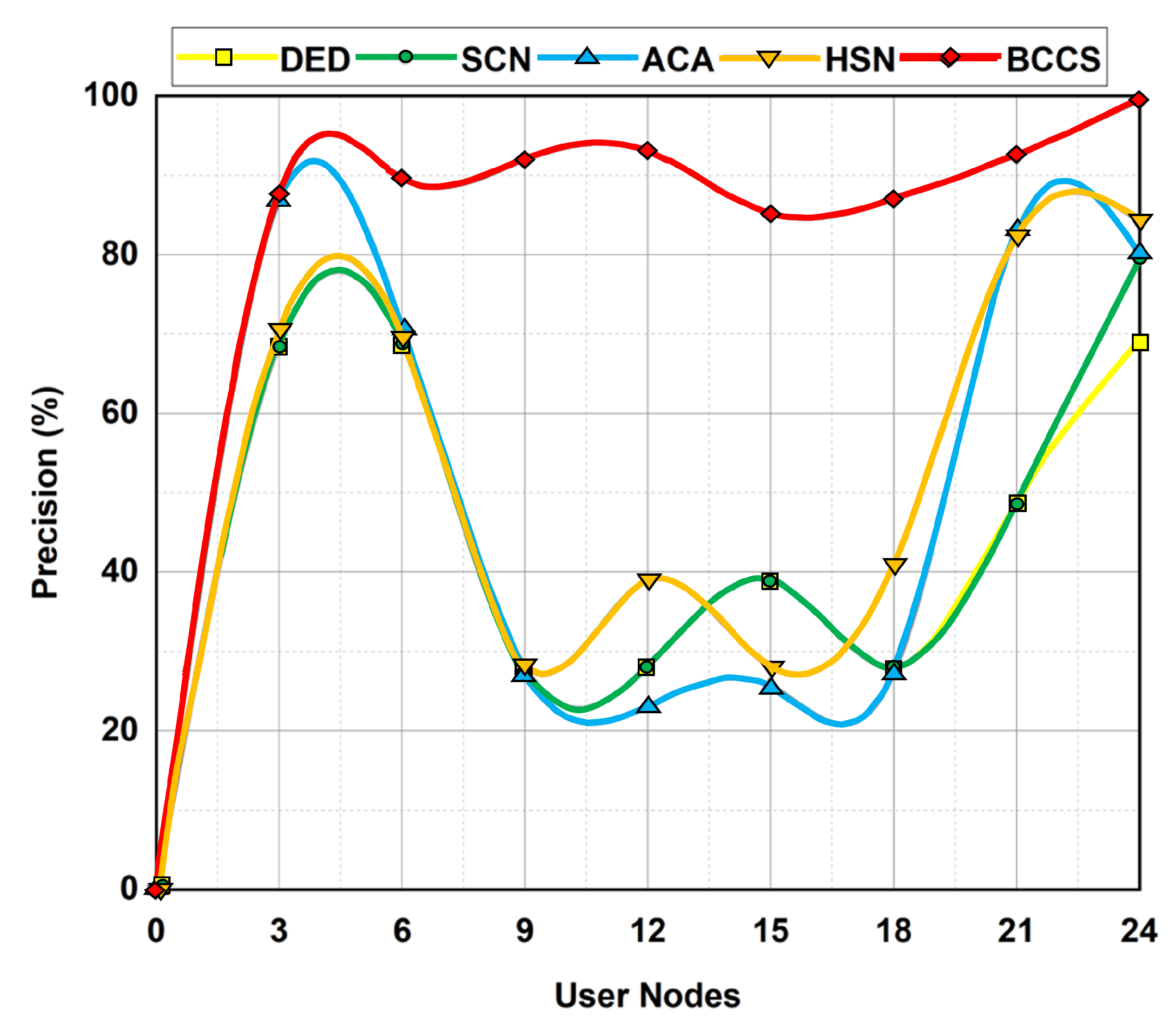
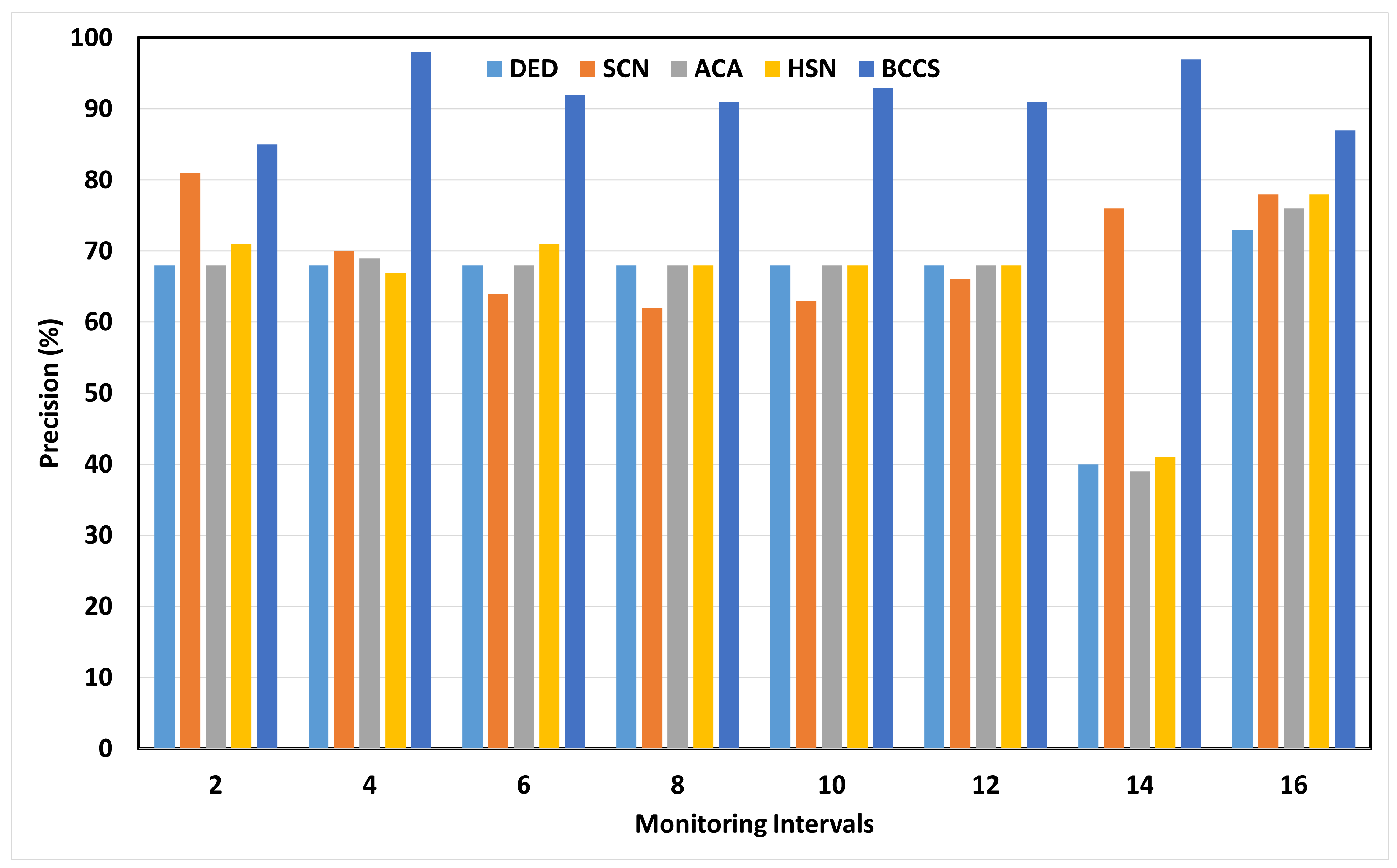
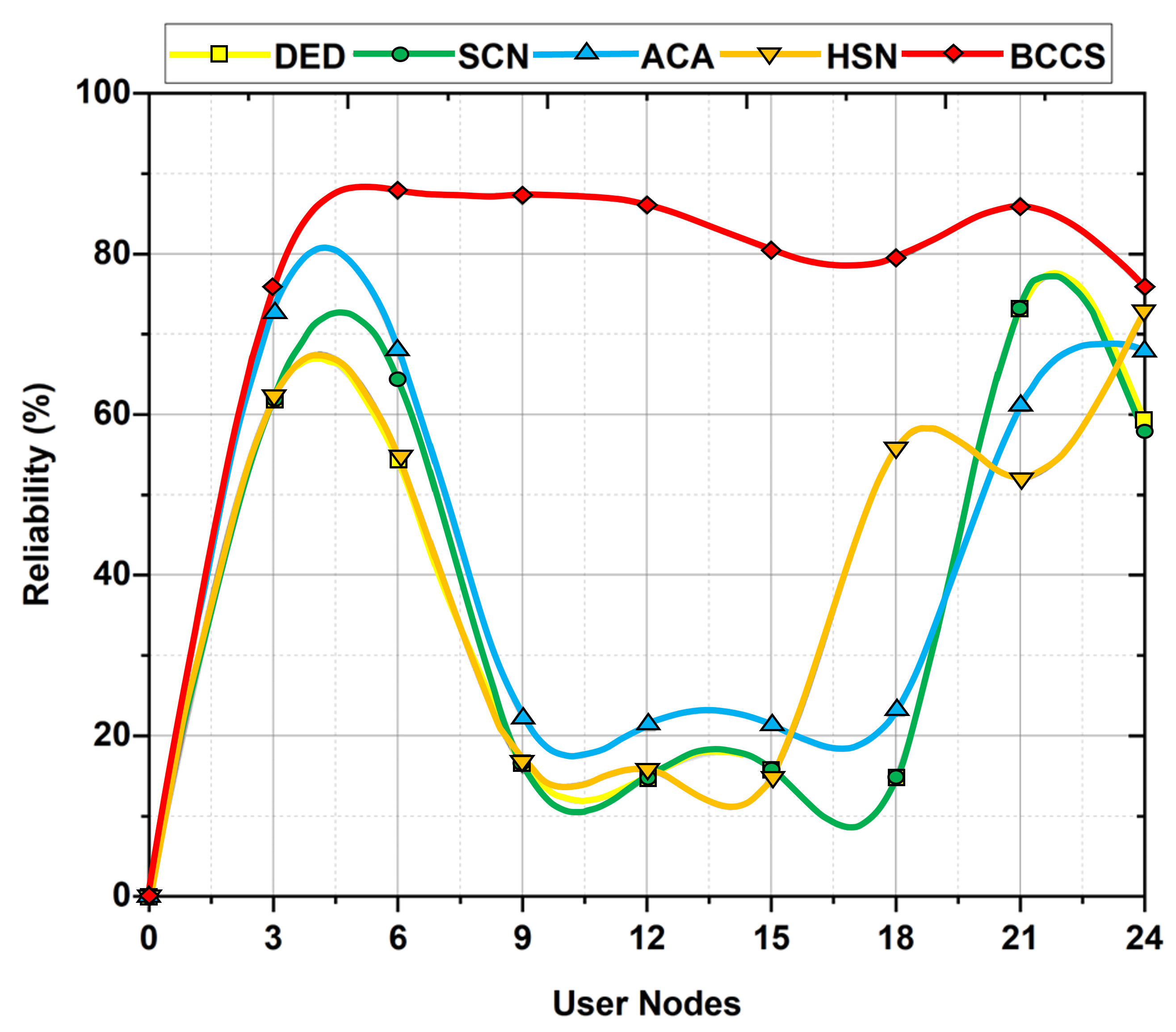
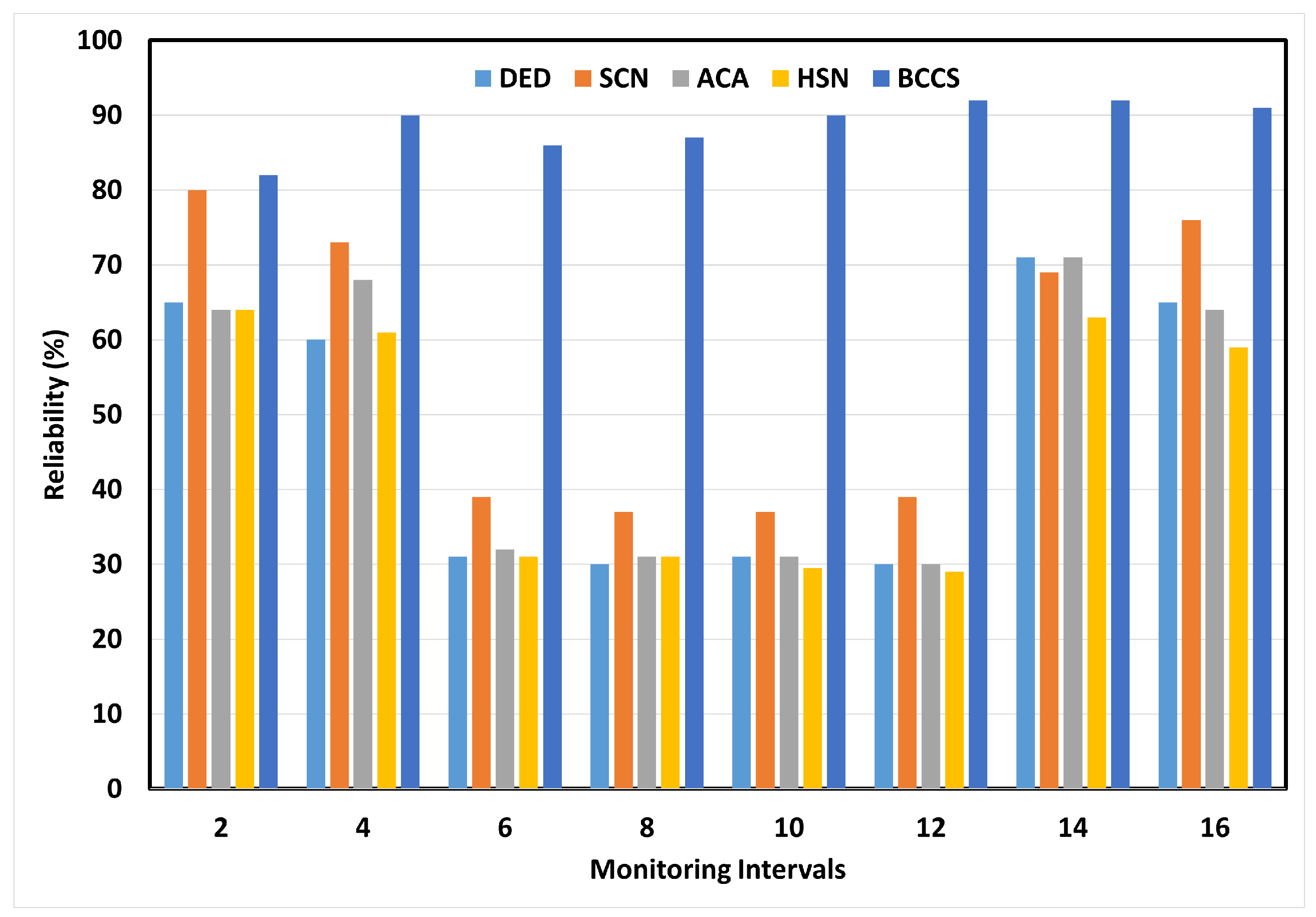
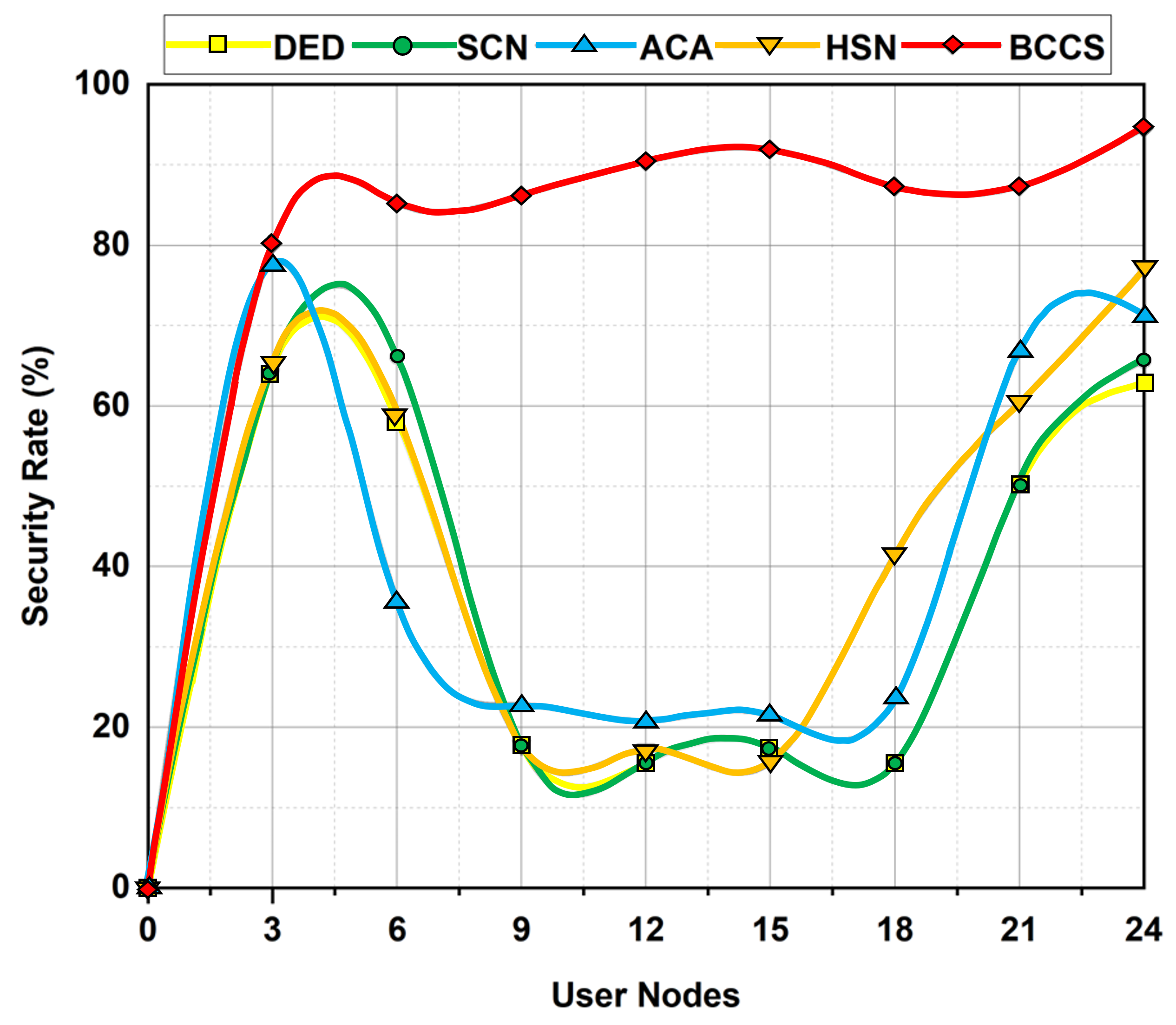
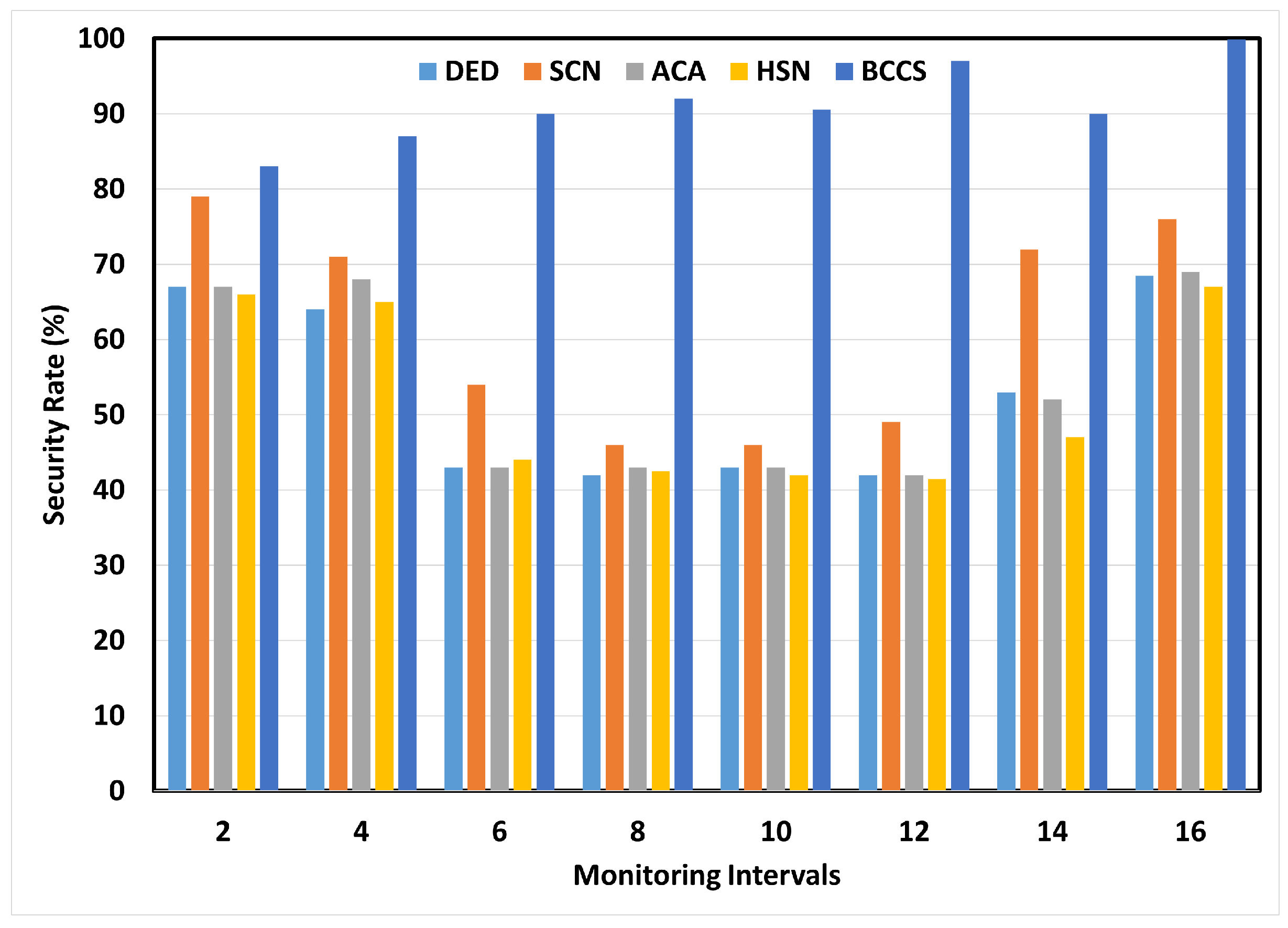
| Performance Metrics | DED | SCN | ACA | HSN | BCCS |
|---|---|---|---|---|---|
| Precision (%) | 67.6 | 77.4 | 86.9 | 84.1 | 98.1 |
| Reliability (%) | 73.1 | 73.9 | 73.9 | 72.1 | 87.9 |
| Security Rate (%) | 65.1 | 65.2 | 77.1 | 75.9 | 96.1 |
| Latency Rate (%) | 13.1 | 14.9 | 8.6 | 13.9 | 4.1 |
| Performance Metrics | DED | SCN | ACA | HSN | BCCS |
|---|---|---|---|---|---|
| Precision (%) | 70.9 | 80.8 | 76.1 | 78.2 | 99.3 |
| Reliability (%) | 65.1 | 79.9 | 71.7 | 64.3 | 99.4 |
| Security Rate (%) | 68.2 | 80.2 | 69.1 | 65.9 | 99.8 |
| Latency Rate (%) | 15.1 | 16.2 | 10.1 | 17.6 | 4.3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alkatheiri, M.S.; Alghamdi, A.S. Blockchain-Assisted Cybersecurity for the Internet of Medical Things in the Healthcare Industry. Electronics 2023, 12, 1801. https://doi.org/10.3390/electronics12081801
Alkatheiri MS, Alghamdi AS. Blockchain-Assisted Cybersecurity for the Internet of Medical Things in the Healthcare Industry. Electronics. 2023; 12(8):1801. https://doi.org/10.3390/electronics12081801
Chicago/Turabian StyleAlkatheiri, Mohammed Saeed, and Ahmed S. Alghamdi. 2023. "Blockchain-Assisted Cybersecurity for the Internet of Medical Things in the Healthcare Industry" Electronics 12, no. 8: 1801. https://doi.org/10.3390/electronics12081801
APA StyleAlkatheiri, M. S., & Alghamdi, A. S. (2023). Blockchain-Assisted Cybersecurity for the Internet of Medical Things in the Healthcare Industry. Electronics, 12(8), 1801. https://doi.org/10.3390/electronics12081801







