Physically Encrypted Wireless Transmission Based on XOR between Two Data in Terahertz Beams
Abstract
1. Introduction
2. The Physically Encrypted Transmission
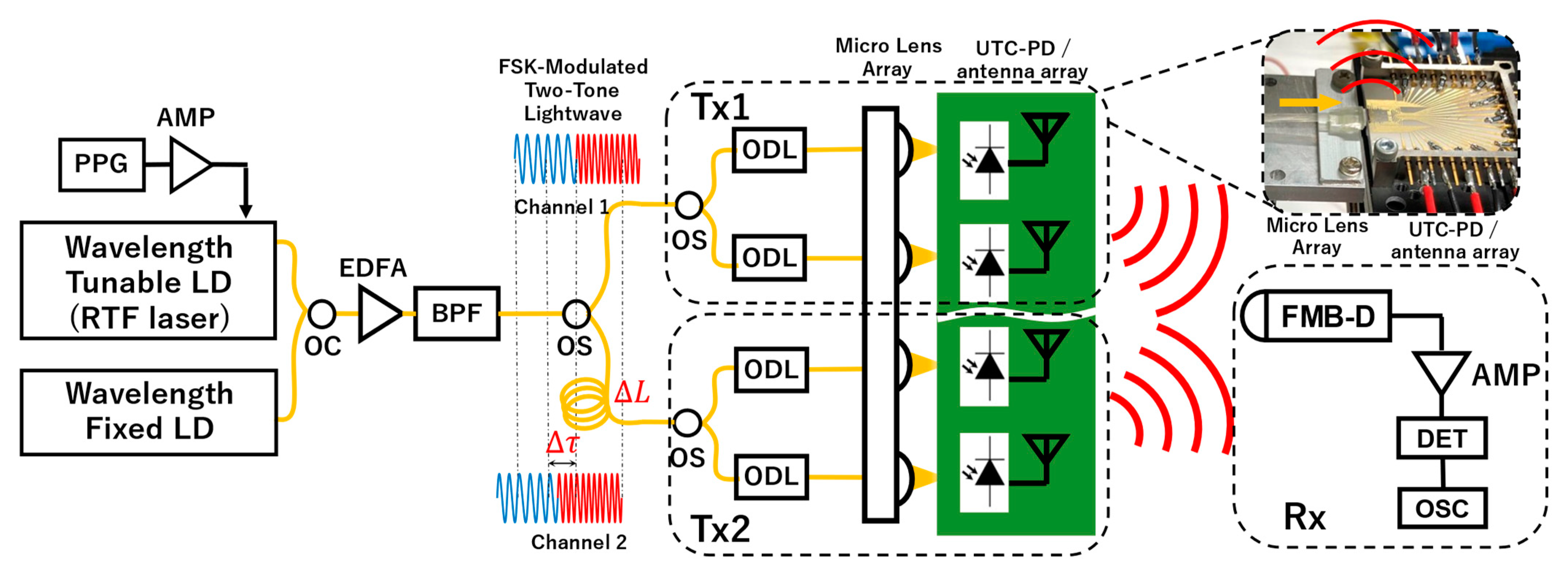
2.1. Configuration of the Proposed System
2.2. THz Beam Steering Enabled by Arrayed UTC-PD
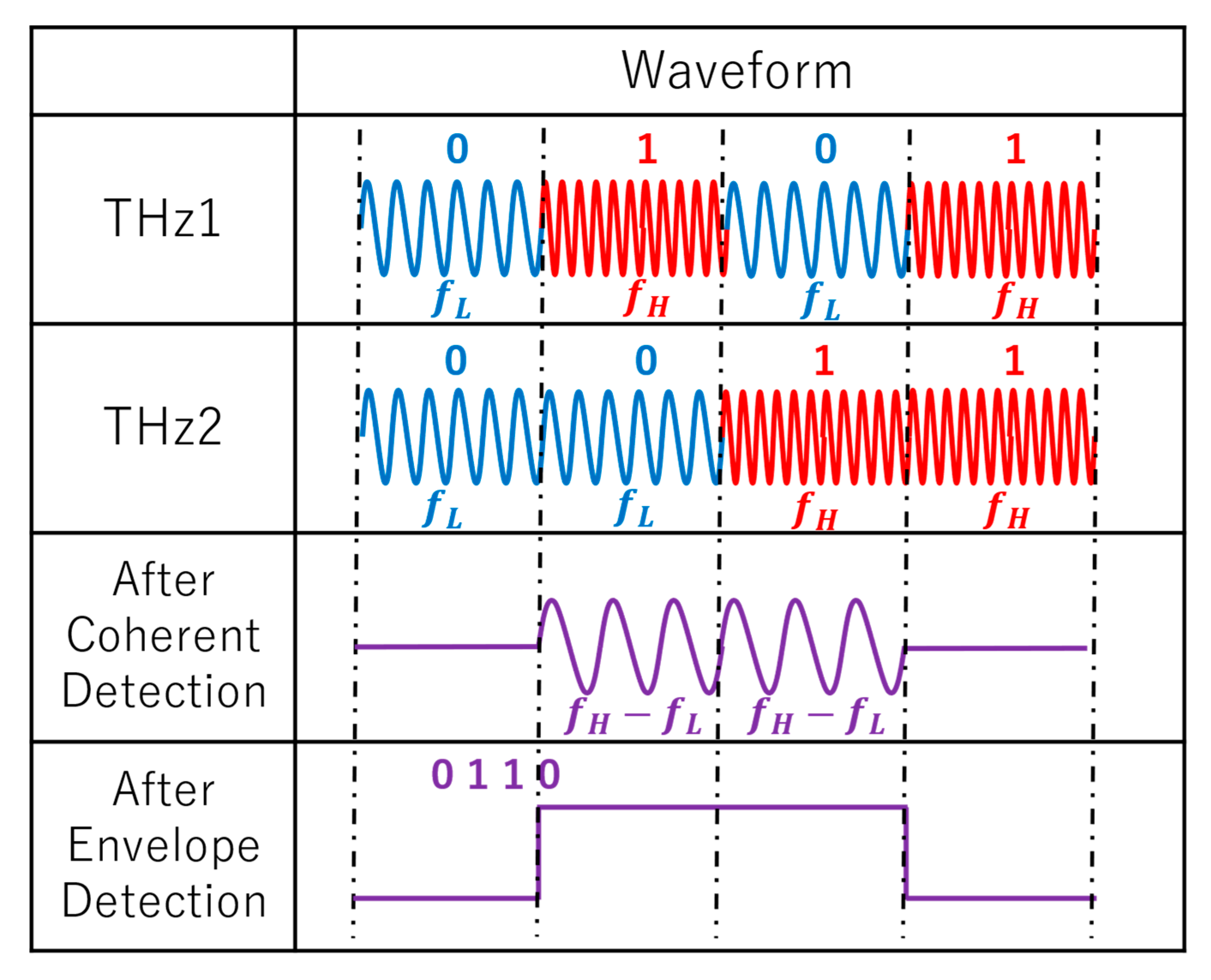
2.3. Decryption Based on Coherent Detection
2.4. XOR Encryption Compared with AND Encryption
3. Experimental Setup
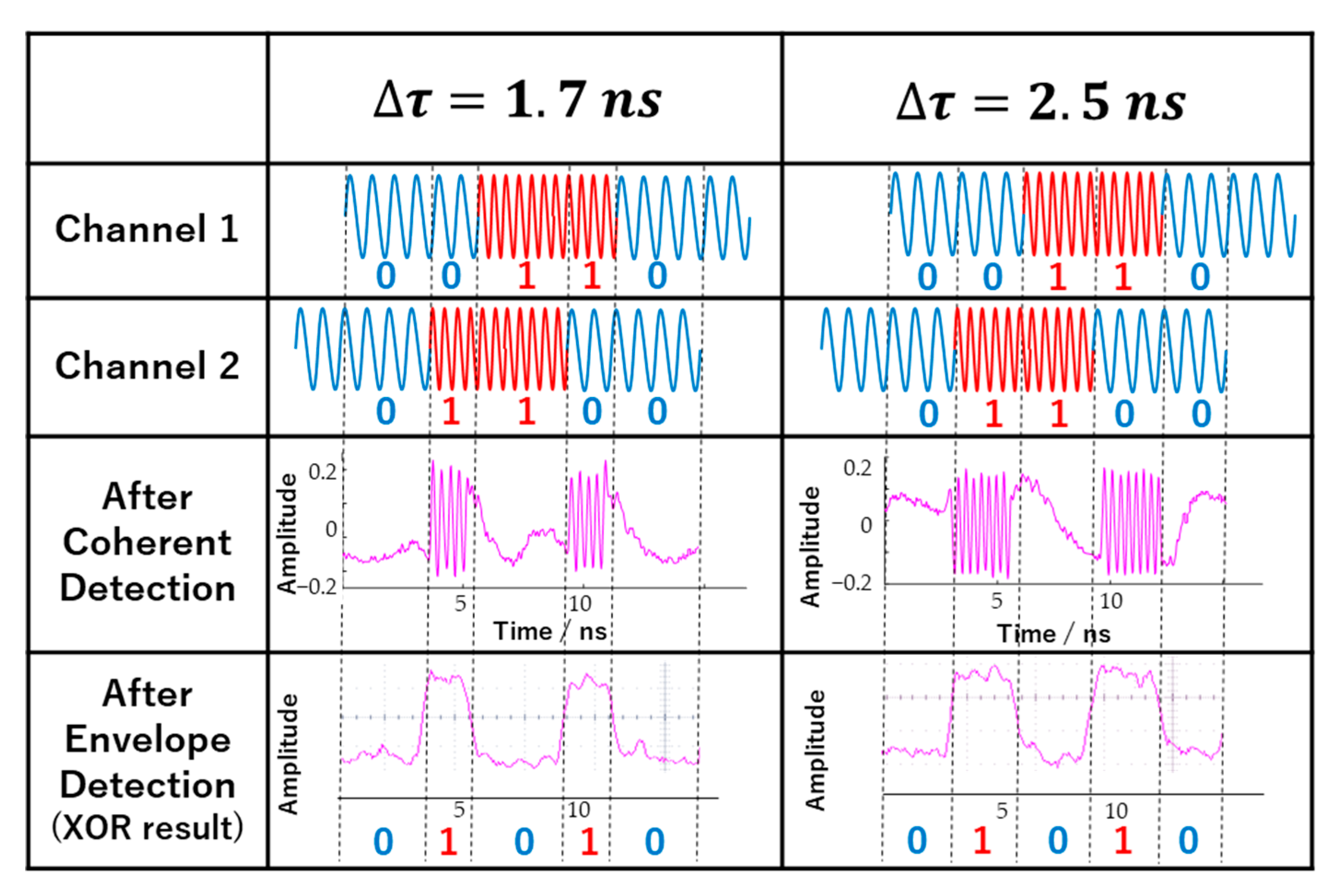
4. Result and Future Directions
4.1. Experiment Result and Discussion
4.2. Future Directions
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Ito, H.; Kodama, S.; Muramoto, Y.; Furuta, T.; Nagatsuma, T.; Ishibashi, T. High-Speed and High-Output InP–InGaAs Unitraveling-Carrier Photodiodes. IEEE J. Select. Topics Quantum Electron. 2004, 10, 709–727. [Google Scholar] [CrossRef]
- Nagatsuma, T.; Ducournau, G.; Renaud, C.C. Advances in Terahertz Communications Accelerated by Photonics. Nat. Photon. 2016, 10, 371–379. [Google Scholar] [CrossRef]
- Seeds, A.J.; Shams, H.; Fice, M.J.; Renaud, C.C. TeraHertz Photonics for Wireless Communications. J. Lightwave Technol. 2015, 33, 579–587. [Google Scholar] [CrossRef]
- Nagatsuma, T.; Ducournau, G. Photonics-Based Transmitters and Receivers. In THz Communications; Kürner, T., Mittleman, D.M., Nagatsuma, T., Eds.; Springer Series in Optical Sciences; Springer International Publishing: Cham, Switzerland, 2022; Volume 234, pp. 299–314. ISBN 978-3-030-73737-5. [Google Scholar]
- Sengupta, K.; Nagatsuma, T.; Mittleman, D.M. Terahertz Integrated Electronic and Hybrid Electronic–Photonic Systems. Nat. Electron. 2018, 1, 622–635. [Google Scholar] [CrossRef]
- You, X.; Wang, C.-X.; Huang, J.; Gao, X.; Zhang, Z.; Wang, M.; Huang, Y.; Zhang, C.; Jiang, Y.; Wang, J.; et al. Towards 6G Wireless Communication Networks: Vision, Enabling Technologies, and New Paradigm Shifts. Sci. China Inf. Sci. 2021, 64, 110301. [Google Scholar] [CrossRef]
- Che, M.; Matsuo, Y.; Kanaya, H.; Ito, H.; Ishibashi, T.; Kato, K. Optoelectronic THz-Wave Beam Steering by Arrayed Photomixers With Integrated Antennas. IEEE Photon. Technol. Lett. 2020, 32, 979–982. [Google Scholar] [CrossRef]
- Shiu, Y.-S.; Chang, S.; Wu, H.-C.; Huang, S.; Chen, H.-H. Physical Layer Security in Wireless Networks: A Tutorial. IEEE Wirel. Commun. 2011, 18, 66–74. [Google Scholar] [CrossRef]
- Joseph, D.; Misoczki, R.; Manzano, M.; Tricot, J.; Pinuaga, F.D.; Lacombe, O.; Leichenauer, S.; Hidary, J.; Venables, P.; Hansen, R. Transitioning Organizations to Post-Quantum Cryptography. Nature 2022, 605, 237–243. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Lange, T. Post-Quantum Cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef] [PubMed]
- Anastasova, M.; Azarderakhsh, R.; Kermani, M.M. Fast Strategies for the Implementation of SIKE Round 3 on ARM Cortex-M4. IEEE Trans. Circ. Syst. I 2021, 68, 4129–4141. [Google Scholar] [CrossRef]
- Anastasova, M.; Azarderakhsh, R.; Kermani, M.M.; Beshaj, L. Time-Efficient Finite Field Microarchitecture Design for Curve448 and Ed448 on Cortex-M4. In Information Security and Cryptology—ICISC 2022; Seo, S.-H., Seo, H., Eds.; Lecture Notes in Computer Science; Springer Nature: Cham, Switzerland, 2023; Volume 13849, pp. 292–314. ISBN 978-3-031-29370-2. [Google Scholar]
- Wang, N.; Wang, P.; Alipour-Fanid, A.; Jiao, L.; Zeng, K. Physical-Layer Security of 5G Wireless Networks for IoT: Challenges and Opportunities. IEEE Internet Things J. 2019, 6, 8169–8181. [Google Scholar] [CrossRef]
- Erdogan, O.; Ozbek, B.; Busari, S.A.; Gonzalez, J. Hybrid Beamforming for Secure Multiuser MmWave MIMO Communications. In Proceedings of the 2020 IEEE 31st Annual International Symposium on Personal, Indoor and Mobile Radio Communications; IEEE: London, UK, 2020; pp. 1–6. [Google Scholar]
- Zhang, L.; Deng, Q.; Zhang, H.; Yang, Z.; Pang, X.; Bobrovs, V.; Popov, S.; Wu, Y.; Yu, X.; Ozolins, O.; et al. Quantum Noise Secured Terahertz Communications. IEEE J. Select. Topics Quantum Electron. 2023, 29, 8400110. [Google Scholar] [CrossRef]
- Yeh, C.-Y.; Ghasempour, Y.; Amarasinghe, Y.; Mittleman, D.M.; Knightly, E.W. Security in Terahertz WLANs with Leaky Wave Antennas. In Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks; ACM: Linz, Austria, 2020; pp. 317–327. [Google Scholar]
- Rappaport, T.S.; Xing, Y.; Kanhere, O.; Ju, S.; Madanayake, A.; Mandal, S.; Alkhateeb, A.; Trichopoulos, G.C. Wireless Communications and Applications Above 100 GHz: Opportunities and Challenges for 6G and Beyond. IEEE Access 2019, 7, 78729–78757. [Google Scholar] [CrossRef]
- Kato, K. Photonics-Assisted Terahertz-Wave Beam Steering and Its Application in Secured Wireless Communication. Photonics 2021, 9, 9. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication Theory of Secrecy Systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Fu, X.; Yang, F.; Liu, C.; Wu, X.; Cui, T.J. Terahertz Beam Steering Technologies: From Phased Arrays to Field-Programmable Metasurfaces. Adv. Opt. Mater. 2020, 8, 1900628. [Google Scholar] [CrossRef]
- Saito, Y.; Ueda, Y.; Shindo, T.; Kanazawa, S.; Matsuzaki, H.; Ishikawa, M. Burst-Tolerant Tuning of Reflection-Type Transversal Filter Laser With Single Active Region. IEEE Photon. Technol. Lett. 2022, 34, 23–26. [Google Scholar] [CrossRef]
- Ueda, Y.; Shindo, T.; Kanazawa, S.; Fujiwara, N.; Ishikawa, M. Electro-Optically Tunable Laser with Ultra-Low Tuning Power Dissipation and Nanosecond-Order Wavelength Switching for Coherent Networks. Optica 2020, 7, 1003. [Google Scholar] [CrossRef]
- Ito, H.; Ishibashi, T. Low-noise Heterodyne Detection of Terahertz Waves at Room Temperature Using Zero-biased Fermi-level Managed Barrier Diode. Electron. Lett. 2018, 54, 1080–1082. [Google Scholar] [CrossRef]
- Galappaththige, D.L.; Amarasuriya, G. Active Pilot Contamination Attack Detection in Sub-6 GHz Massive MIMO NOMA Systems. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM); IEEE: Waikoloa, HI, USA, 2019; pp. 1–6. [Google Scholar]
- Moriai, S.; Wang, H. (Eds.) Advances in Cryptology—ASIACRYPT 2020: 26th International Conference on the Theory and Application of Cryptology and Information Security, Daejeon, South Korea, 7–11 December 2020, Proceedings, Part II; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2020; Volume 12492, ISBN 978-3-030-64833-6. [Google Scholar]
- Sarker, A.; Kermani, M.M.; Azarderakhsh, R. Fault Detection Architectures for Inverted Binary Ring-LWE Construction Benchmarked on FPGA. IEEE Trans. Circ. Syst. II 2021, 68, 1403–1407. [Google Scholar] [CrossRef]
- Aghaie, A.; Mozaffari Kermani, M.; Azarderakhsh, R. Fault Diagnosis Schemes for Low-Energy Block Cipher Midori Benchmarked on FPGA. IEEE Trans. VLSI Syst. 2017, 25, 1528–1536. [Google Scholar] [CrossRef]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, H.; Che, M.; Seiki, N.; Shiramizu, T.; Yano, T.; Mikami, Y.; Ueda, Y.; Kato, K. Physically Encrypted Wireless Transmission Based on XOR between Two Data in Terahertz Beams. Electronics 2023, 12, 2629. https://doi.org/10.3390/electronics12122629
Chen H, Che M, Seiki N, Shiramizu T, Yano T, Mikami Y, Ueda Y, Kato K. Physically Encrypted Wireless Transmission Based on XOR between Two Data in Terahertz Beams. Electronics. 2023; 12(12):2629. https://doi.org/10.3390/electronics12122629
Chicago/Turabian StyleChen, Hanwei, Ming Che, Naoya Seiki, Takashi Shiramizu, Takuya Yano, Yuya Mikami, Yuta Ueda, and Kazutoshi Kato. 2023. "Physically Encrypted Wireless Transmission Based on XOR between Two Data in Terahertz Beams" Electronics 12, no. 12: 2629. https://doi.org/10.3390/electronics12122629
APA StyleChen, H., Che, M., Seiki, N., Shiramizu, T., Yano, T., Mikami, Y., Ueda, Y., & Kato, K. (2023). Physically Encrypted Wireless Transmission Based on XOR between Two Data in Terahertz Beams. Electronics, 12(12), 2629. https://doi.org/10.3390/electronics12122629







