A Gate-Level Information Leakage Detection Framework of Sequential Circuit Using Z3
Abstract
1. Introduction
- We introduce an automated formal verification framework detecting vulnerabilities in the gate-level net-list. The net-list data is formalized into a circuit model, and then security properties are designed based on the model. Confidentiality is enforced on the input hardware design by applying an automatic checking engine.
- GLIFT is, for the first time, statically applied in the gate-level hardware with a fully automated working procedure. The information leakage is addressed and localized by tracking sensitive information.
- An automatic tool, including a parser and a SMT Solver, is designed and demonstrated based on the developed framework. The parser for translating net-list files to formal models can support multiple net-list process libraries such as generic gate Verilog and 180nm CMOS library. An algorithm is developed to support analyzing the properties in sequential circuits using an SMT solver.
- The proposed framework can accurately analyze the sequential information flow, and its effectiveness is proven in 25 benchmarks, including combinational circuits and sequential circuits.
2. Background
2.1. Attack Model
2.2. Related Work
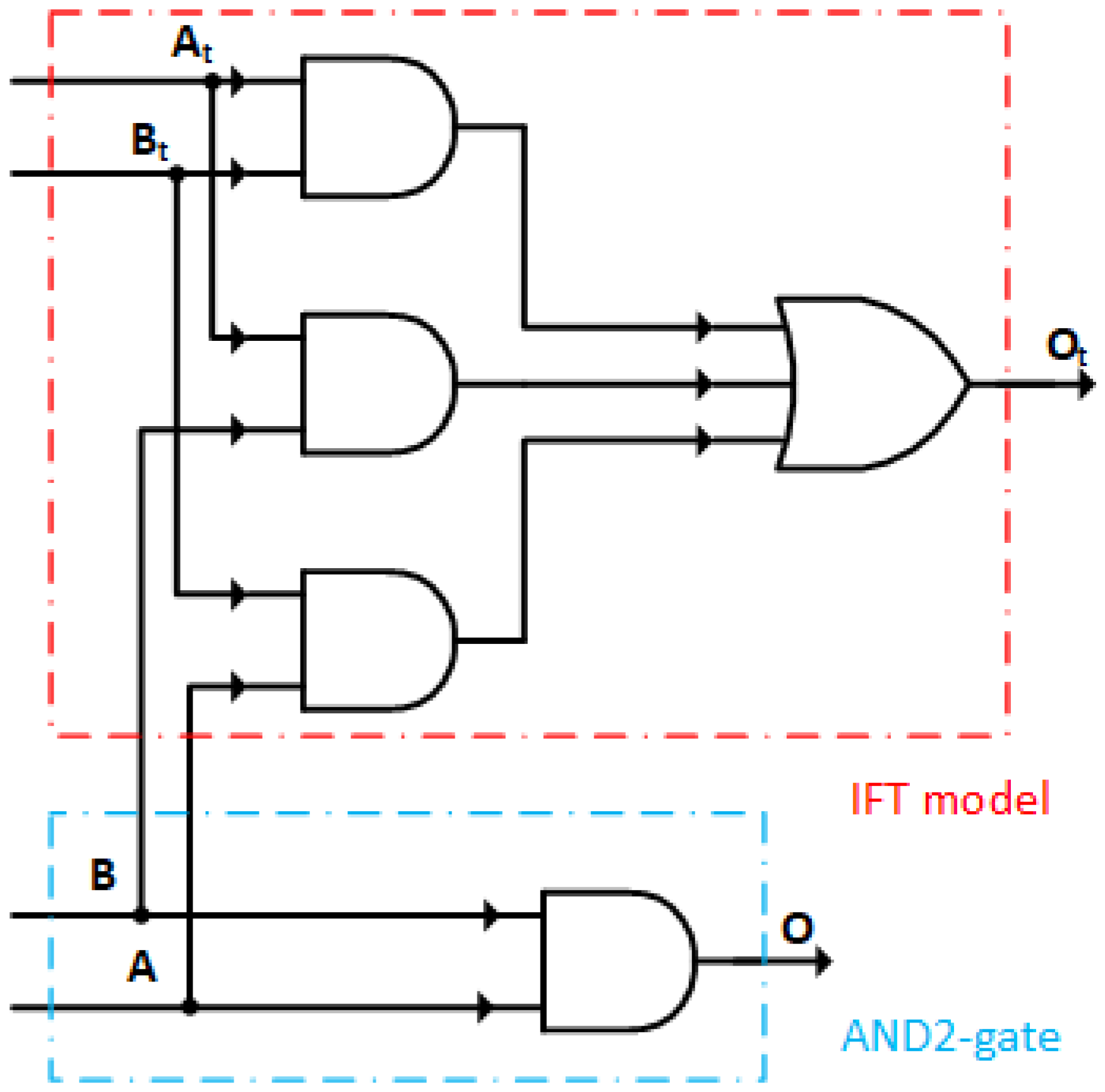
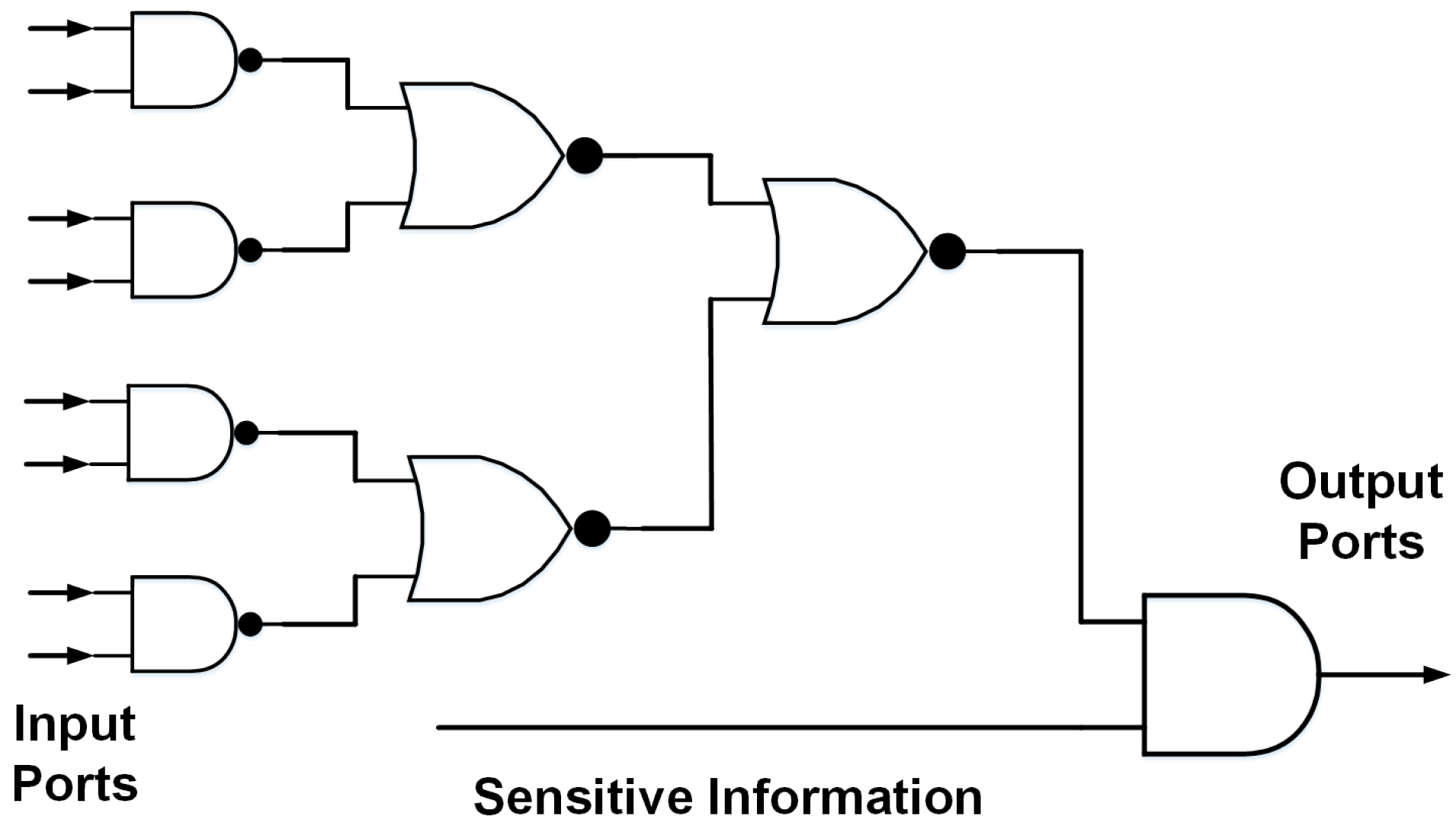
2.3. Modeling Gate-Level IFT
2.4. SMT Solver
3. Methodology
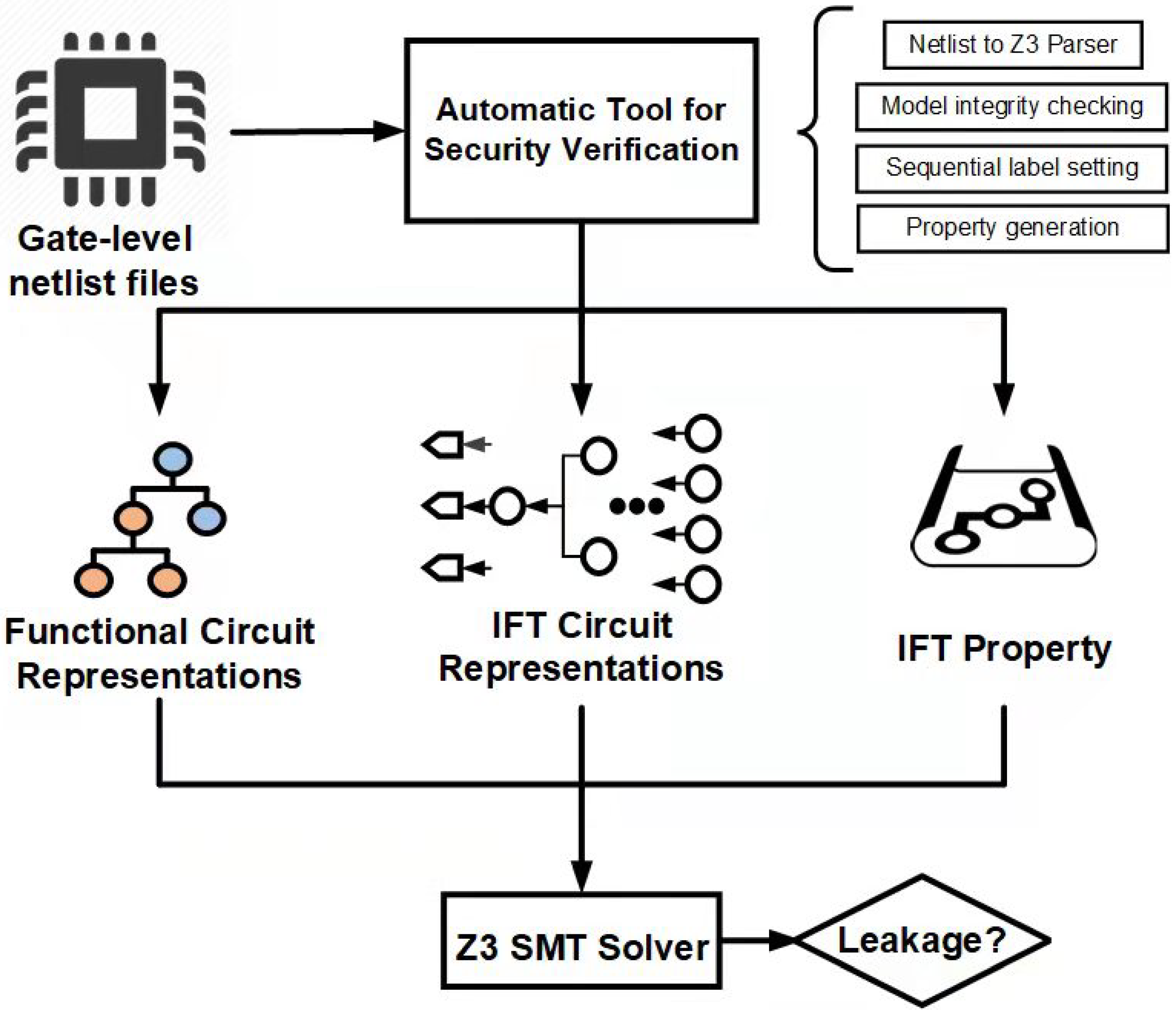
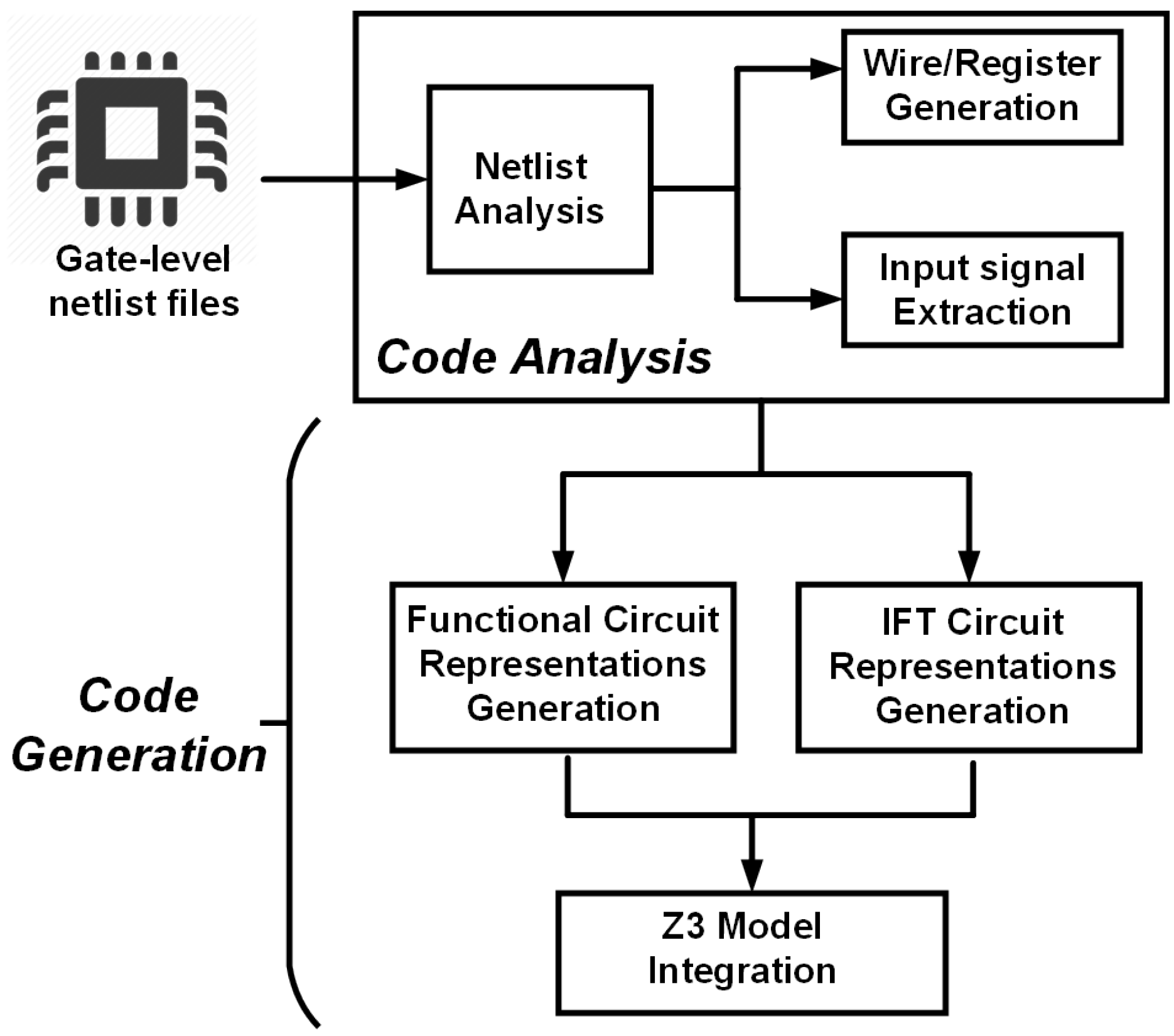
3.1. Framework Overview
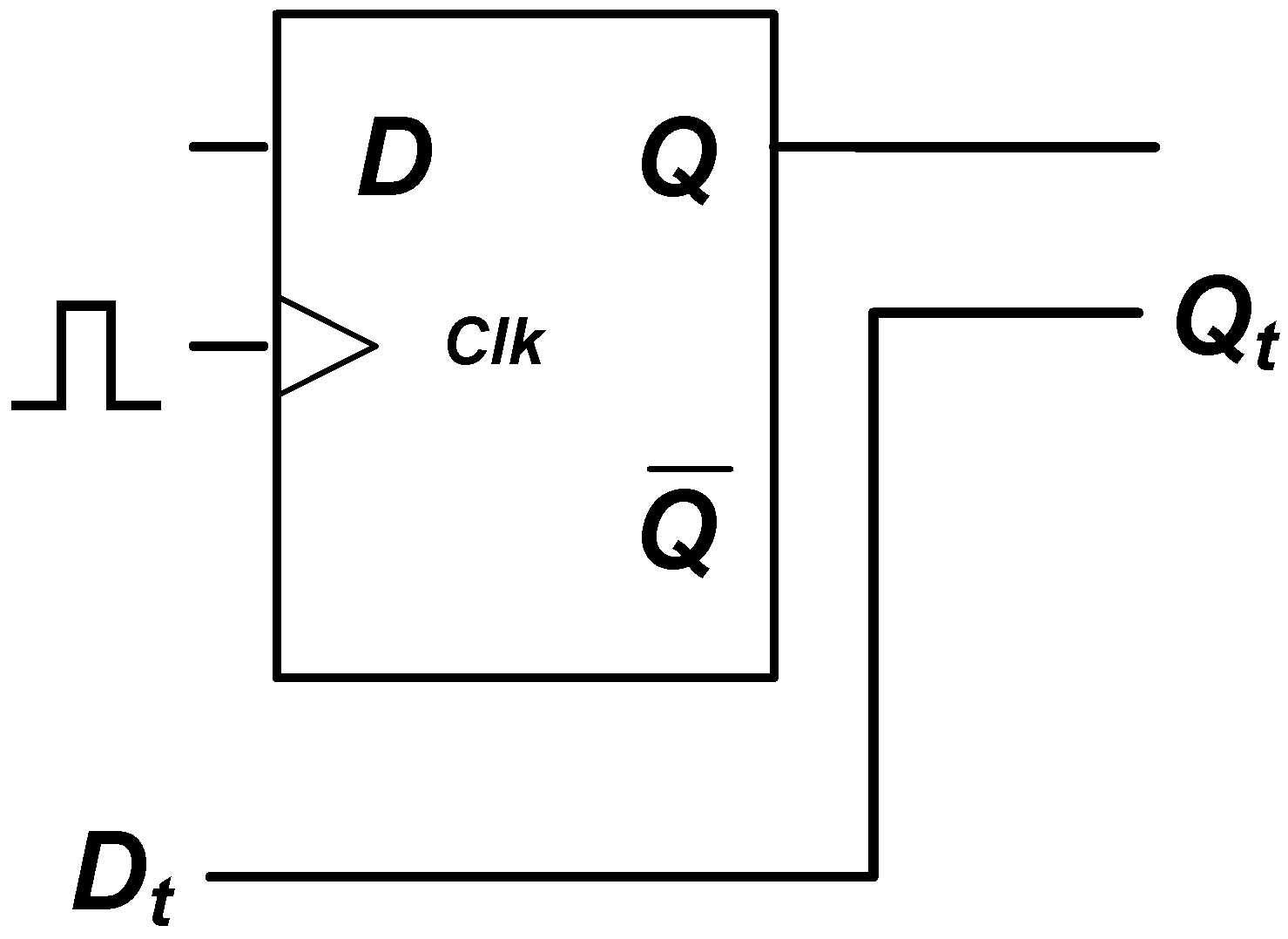
3.2. Sequential Split Strategy
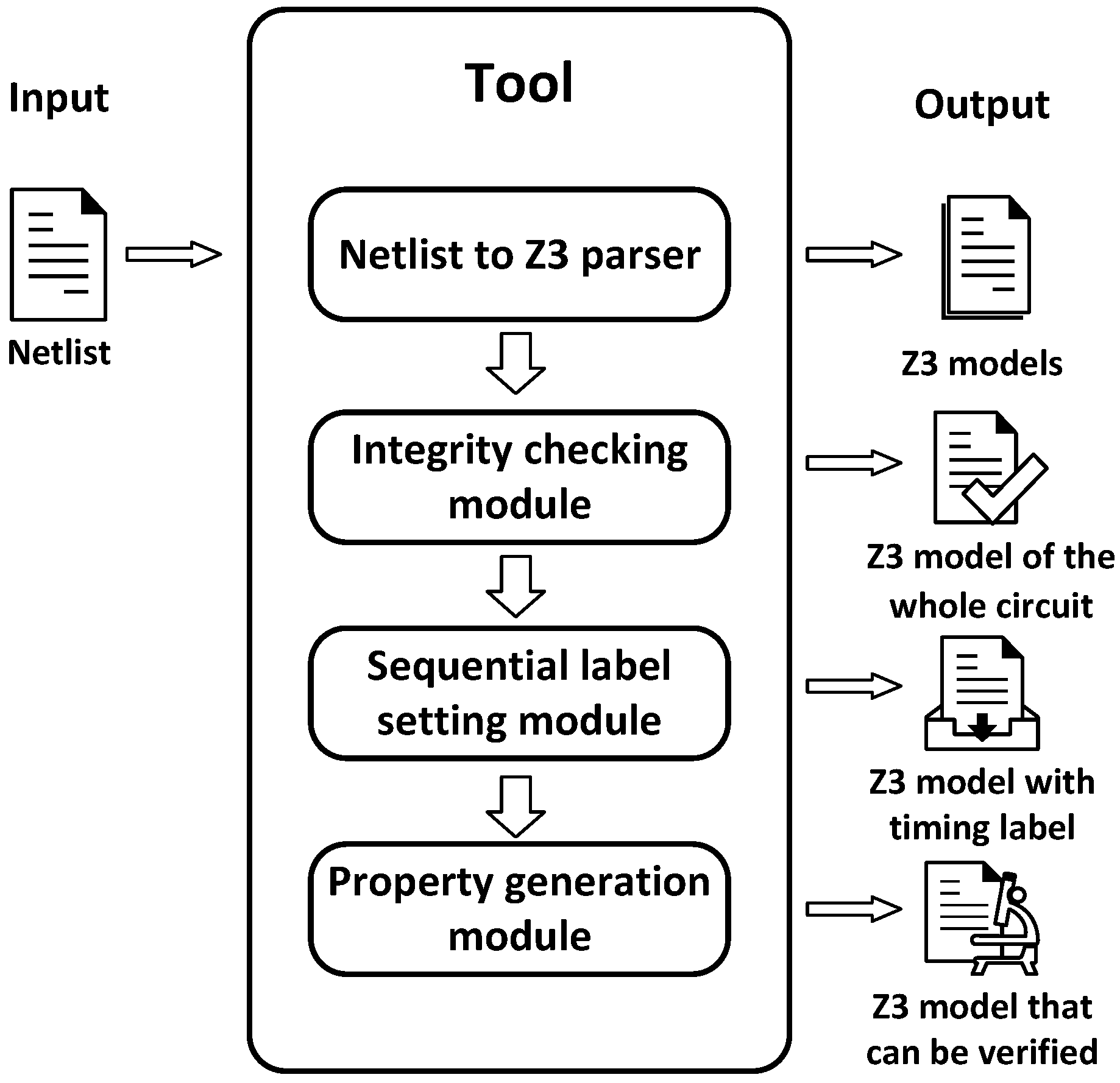
4. Tool Design
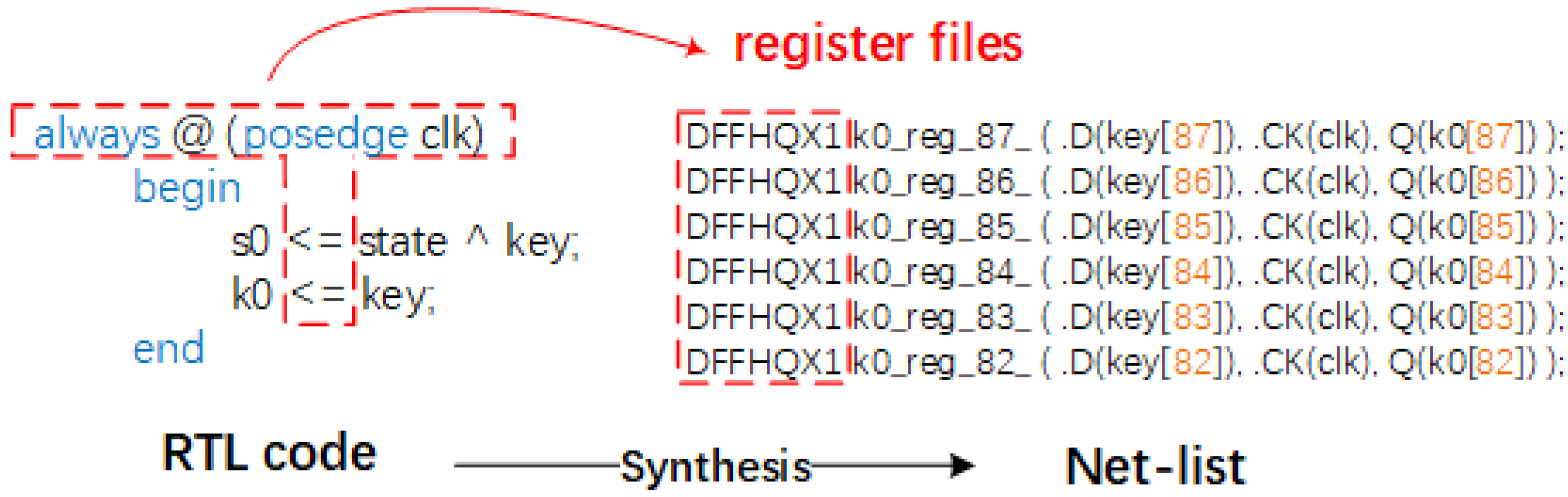
4.1. Net-list to Z3 Parser
4.2. Integrity Checking Module
4.3. Sequential Label Setting Module
4.4. Property Generation Module
5. Experiments
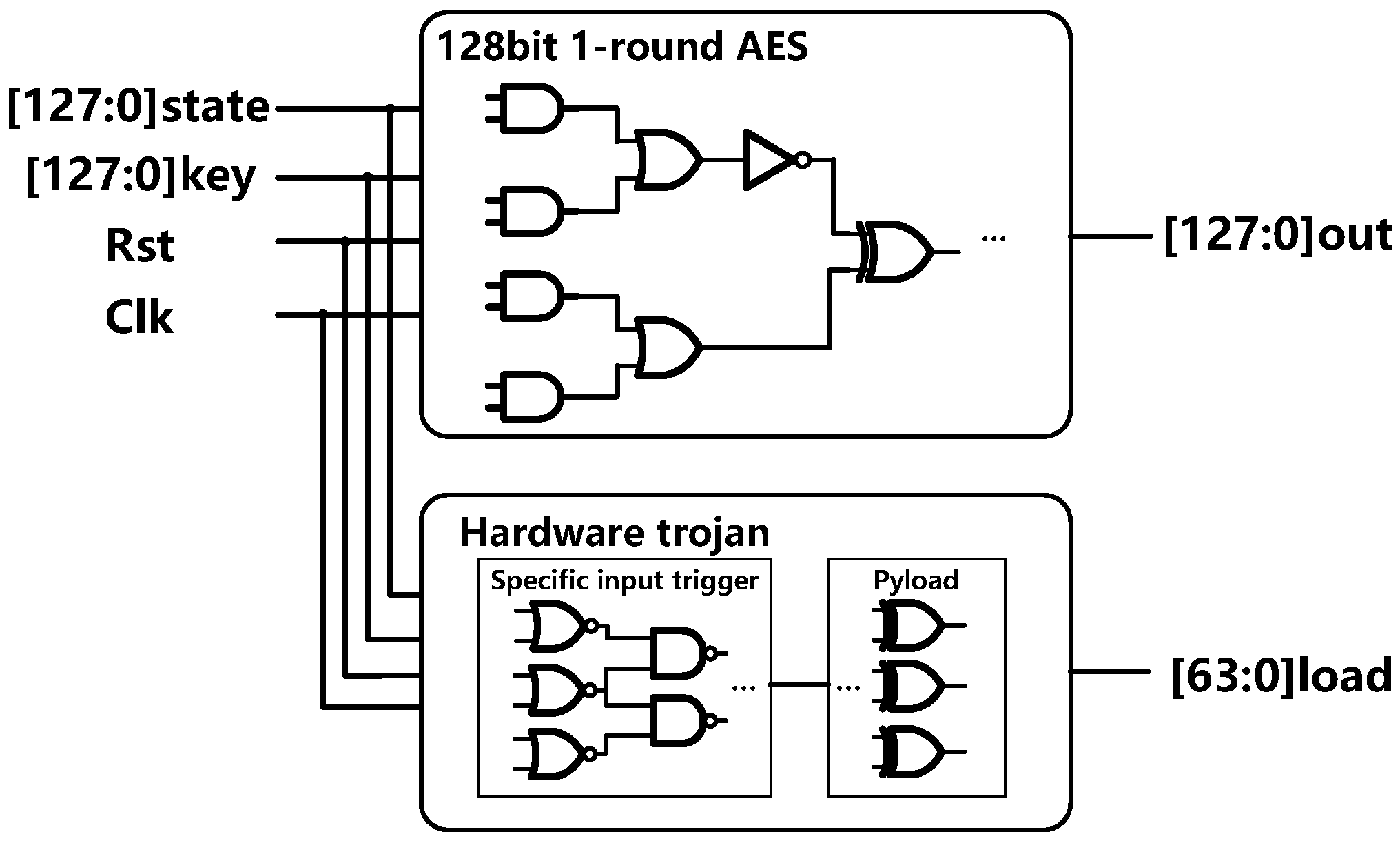
5.1. Experimental Setup
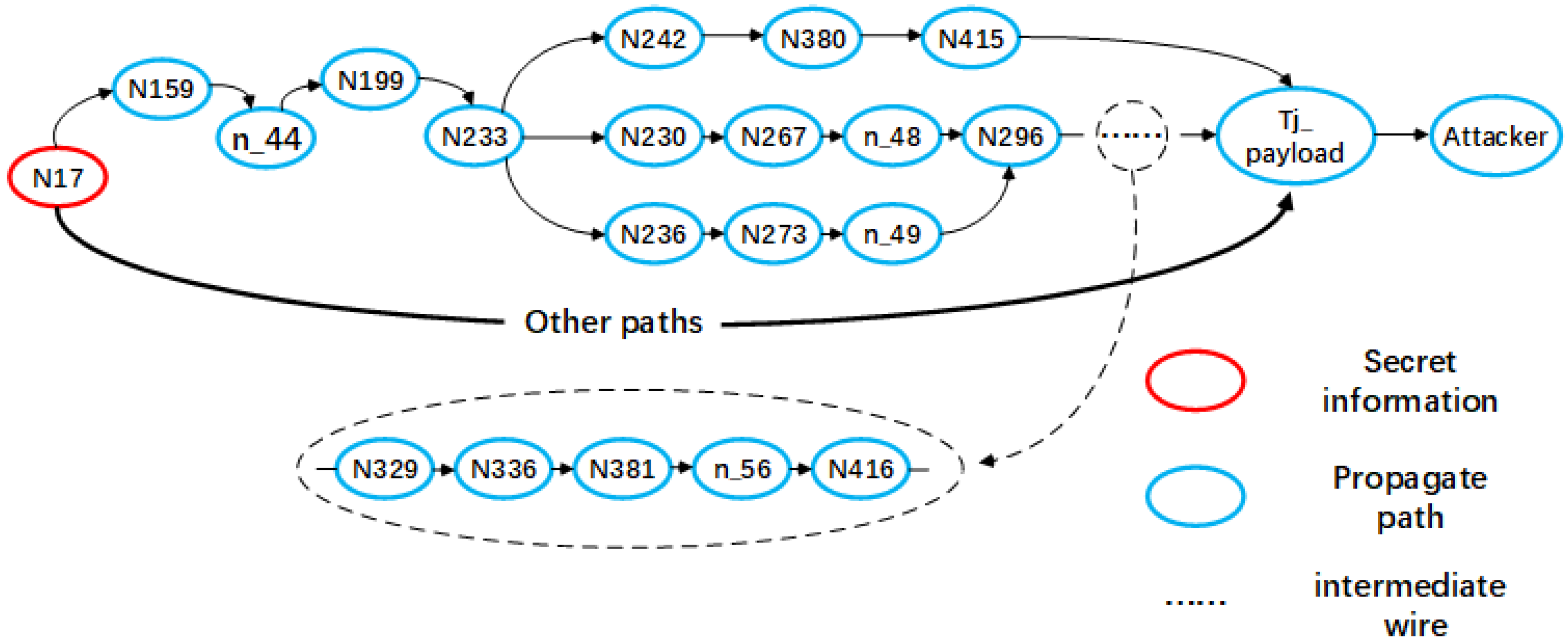
5.2. Leakage Paths Checking
5.3. Results and Analysis
6. Limitations and Discussion
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Agrawal, D.; Baktir, S.; Karakoyunlu, D.; Rohatgi, P.; Sunar, B. Trojan detection using IC fingerprinting. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ’07), Oakland, CA, USA, 20–23 May 2007; pp. 296–310. [Google Scholar] [CrossRef]
- Jin, Y.; Makris, Y. Hardware Trojan detection using path delay fingerprint. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, CA, USA, 9 June 2008; pp. 51–57. [Google Scholar]
- Zhang, X.; Tehranipoor, M. Case study: Detecting hardware trojans in third-party digital ip cores. In Proceedings of the 2011 IEEE International Symposium on Hardware-Oriented Security and Trust, San Diego, CA, USA, 5–6 June 2011; pp. 67–70. [Google Scholar]
- Love, E.; Jin, Y.; Makris, Y. Proof-carrying hardware intellectual property: A pathway to trusted module acquisition. IEEE Trans. Inf. Forensics Secur. 2012, 7, 25–40. [Google Scholar] [CrossRef]
- Jin, Y.; Yang, B.; Makris, Y. Cycle-accurate information assurance by proof-carrying based signal sensitivity tracing. IEEE Int. Symp. Hardw.-Oriented Secur. Trust (HOST) 2013, 99–106. [Google Scholar]
- Jin, Y. Design-for-security vs. design-for-testability: A case study on dft chain in cryptographic circuits. In Proceedings of the 2014 IEEE Computer Society Annual Symposium on VLSI, Tampa, FL, USA, 9–11 July 2014. [Google Scholar] [CrossRef]
- De Paula, F.M.; Gort, M.; Hu, A.J.; Wilton, S.J.; Yang, J. Backspace: Formal analysis for post-silicon debug. In Proceedings of the 2008 International Conference on Formal Methods in Computer-Aided Design; IEEE Press: Portland, OR, USA, 2008; p. 5. [Google Scholar]
- Guo, X.; Dutta, R.G.; Jin, Y.; Farahmandi, F.; Mishra, P. Pre-silicon security verification and validation: A formal perspective. In Proceedings of the 52nd Annual Design Automation Conference; ACM: San Francisco, CA, USA, 2015; p. 145. [Google Scholar]
- Drzevitzky, S. Proof-carrying hardware: Runtime formal verification for secure dynamic reconfiguration. In Proceedings of the 2010 International Conference on Field Programmable Logic and Applications, Milan, Italy, 31 August–2 September 2010; pp. 255–258. [Google Scholar]
- Rajendran, J.; Vedula, V.; Karri, R. Detecting Malicious Modifications of Data in Third-Party Intellectual Property Cores. Ser.; DAC ’15: New York, NY, USA, 2015; pp. 112:1–112:6. [Google Scholar]
- Henzinger, T.A.; Jhala, R.; Majumdar, R.; Sutre, G. Software verification with blast. In Model Checking Software; Springer: Berlin/Heidelberg, Germany, 2003; pp. 235–239. [Google Scholar]
- Guo, X.; Dutta, R.G.; Mishra, P.; Jin, Y. Automatic code converter enhanced pch framework for soc trust verification. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2017, 25, 3390–3400. [Google Scholar] [CrossRef]
- Myers, A.C.; Liskov, B. A decentralized model for information flow control. In Proceedings of the ACM Symposium on Operating Systems Principles (SOSP), Saint-Malo, France, 5–8 October 1997; pp. 129–142. [Google Scholar]
- Zhang, D.; Askarov, A.; Myers, A.C. Language-based control and mitigation of timing channels. ACM SIGPLAN Not. 2012, 47, 99–110. [Google Scholar] [CrossRef]
- Zhang, D.; Wang, Y.; Suh, G.E.; Myers, A.C. A hardware design language for timing-sensitive information-flow security. ACM SIGPLAN Not. 2015, 50, 503–516. [Google Scholar] [CrossRef]
- Li, X.; Tiwari, M.; Oberg, J.K.; Kashyap, V.; Chong, F.T.; Sherwood, T.; Hardekopf, B. Caisson: A hardware description language for secure information flow. ACM SIGPLAN Not. 2011, 46, 109–120. [Google Scholar] [CrossRef]
- Li, X.; Kashyap, V.; Oberg, J.K.; Tiwari, M.; Rajarathinam, V.R.; Kastner, R.; Sherwood, T.; Hardekopf, B.; Chong, F.T. Sapper: A language for hardware-level security policy enforcement. In ACM SIGARCH Computer Architecture News; ACM: New York, NY, USA, 2014; Volume 42, pp. 97–112. [Google Scholar]
- Guo, X.; Dutta, R.G.; He, J.; Tehranipoor, M.M.; Jin, Y. Qif-verilog: Quantitative information-flow based hardware description languages for pre-silicon security assessment. In 2019 IEEE International Symposium on Hardware Oriented Security and Trust (HOST); IEEE: McLean, VA, USA, 2019; pp. 91–100. [Google Scholar]
- Hu, W.; Oberg, J.; Irturk, A.; Tiwari, M.; Sherwood, T.; Mu, D.; Kastner, R. On the complexity of generating gate level information flow tracking logic. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1067–1080. [Google Scholar] [CrossRef]
- Hu, W.; Mao, B.; Oberg, J.; Kastner, R. Detecting hardware trojans with gate-level information-flow tracking. Computer 2016, 49, 44–52. [Google Scholar] [CrossRef]
- Qin, M.; Hu, W.; Wang, X.; Mu, D.; Mao, B. Theorem proof based gate level information flow tracking for hardware security verification. Comput. Secur. 2019, 85, 225–239. [Google Scholar] [CrossRef]
- Deng, S.; Gümüsoglu, D.; Xiong, W.; Gener, Y.S.; Demir, O.; Szefer, J. Secchisel: Language and tool for practical and scalable security verification of security-aware hardware architectures. IACR Cryptol. ePrint Arch. 2017, 2017, 193. [Google Scholar]
- De Moura, L.; Bjørner, N. Z3: An efficient smt solver. In International conference on Tools and Algorithms for the Construction and Analysis of Systems; Springer: Budapest, Hungary, 2008; pp. 337–340. [Google Scholar]
- Hu, W.; Wu, L.; Tai, Y.; Tan, J.; Zhang, J. A unified formal model for proving security and reliability properties. In Proceedings of the 2020 IEEE 29th Asian Test Symposium (ATS), Penang, Malaysia, 23–26 November 2020; pp. 1–6. [Google Scholar]
- Kumar, B.; Jaiswal, A.K.; Vineesh, V.S.; Shinde, R. Analyzing hardware security properties of processors through model checking. In Proceedings of the 2020 33rd International Conference on VLSI Design and 2020 19th International Conference on Embedded Systems (VLSID), Bangalore, India, 4–5 January 2020; pp. 107–112. [Google Scholar]
- Khalid, F.; Abbassi, I.H.; Rehman, S.; Kamboh, A.M.; Hasan, O.; Shafique, M. Forasec: Formal analysis of hardware trojan-based security vulnerabilities in sequential circuits. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2021, 41, 1167–1180. [Google Scholar] [CrossRef]
- Bouzafour, A.; Renaudin, M.; Garavel, H.; Mateescu, R.; Serwe, W. Model-checking synthesizable systemverilog descriptions of asynchronous circuits. In Proceedings of the 2018 24th IEEE International Symposium on Asynchronous Circuits and Systems (ASYNC), Vienna, Austria, 13–16 May 2018; pp. 34–42. [Google Scholar]
- He, J.; Guo, X.; Meade, T.; Dutta, R.G.; Zhao, Y.; Jin, Y. Soc interconnection protection through formal verification. Integration 2019, 64, 143–151. [Google Scholar] [CrossRef]
- Pieper, P.; Herdt, V.; Große, D.; Drechsler, R. Dynamic information flow tracking for embedded binaries using systemc-based virtual prototypes. In Proceedings of the 2020 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 1–5 June 2020; pp. 1–6. [Google Scholar]
- Solt, F.; Gras, B.; Razavi, K. Cellift: Leveraging cells for scalable and precise dynamic information flow tracking in RTL. In 31st USENIX Security Symposium, USENIX Security 2022, Boston, MA, USA, 10–12 August 2022; Butler, K.R.B., Thomas, K., Eds.; USENIX Association: Berkeley, CA, USA, 2022; pp. 2549–2566. Available online: https://www.usenix.org/conference/usenixsecurity22/presentation/solt (accessed on 11 December 2022).
- Tiwari, M.; Wassel, H.M.; Mazloom, B.; Mysore, S.; Chong, F.T.; Sherwood, T. Complete information flow tracking from the gates up. ACM Sigplan Not. 2009, 44, 109–120. [Google Scholar] [CrossRef]
- Blackstone, J.; Hu, W.; Althoff, A.; Ardeshiricham, A.; Zhang, L.; Kastner, R. A Unified Model for Gate Level Propagation Analysis. 2020. Available online: https://arxiv.org/abs/2012.02791 (accessed on 11 December 2022).
- Zhang, Q.; He, J.; Zhao, Y.; Guo, X. A formal framework for gate-level information leakage using z3. In 2020 Asian Hardware Oriented Security and Trust Symposium (AsianHOST); IEEE: Shanghai, China, 2020; pp. 1–6. [Google Scholar]
- Microsoft Research. Z3 api in Python. Available online: https://ericpony.github.io/z3py-tutorial/guide-examples.htm (accessed on 11 December 2022).
- Hansen, M.C.; Yalcin, H.; Hayes, J.P. Unveiling the iscas-85 benchmarks: A case study in reverse engineering. IEEE Des. Test Comput. 1999, 16, 72–80. [Google Scholar] [CrossRef]
- EPFL and ISCAS85. Epfl and iscas85 Combinational Benchmark Circuits in Generic Gate Verilog. Available online: https://github.com/jpsety/verilog_benchmark_circuits (accessed on 11 December 2022).
| Work | Target | Static or Dynamic | Automatic |
|---|---|---|---|
| [24] | Gate level HW design | Dynamic | Y |
| [25] | RTL HW design | Dynamic | Y |
| [26] | Gate level HW design | Dynamic | Y |
| [27] | RTL HW design | Dynamic | N |
| [28] | Gate level HW design | Dynamic | Y |
| [29] | HW/SW interactions | Dynamic | Y |
| This work | Gate level HW design | Static | Y |
| Benchmarks | Format | Trigger Mode | Functional Gate | IFT Gate | Model Time (ms) | Detection Time (ms) | Total (ms) | Detected |
|---|---|---|---|---|---|---|---|---|
| c17 | generic gate verilog | signal trigger | 6 | 24 | 70 | 24 | 94 | Yes |
| c432 | generic gate verilog | signal trigger | 160 | 775 | 77 | 143 | 220 | Yes |
| c499 | generic gate verilog | signal trigger | 202 | 888 | 65 | 130 | 195 | Yes |
| c880 | generic gate verilog | signal trigger | 383 | 1455 | 63 | 210 | 273 | Yes |
| c1355 | generic gate verilog | signal trigger | 546 | 3315 | 74 | 275 | 349 | Yes |
| c1908 | generic gate verilog | signal trigger | 880 | 2168 | 74 | 250 | 324 | Yes |
| c2670 | generic gate verilog | signal trigger | 1193 | 3290 | 81 | 509 | 590 | Yes |
| c3540 | generic gate verilog | signal trigger | 1669 | 4638 | 91 | 663 | 754 | Yes |
| c5315 | generic gate verilog | signal trigger | 2307 | 7995 | 116 | 1112 | 1228 | Yes |
| c6288 | generic gate verilog | signal trigger | 2416 | 9364 | 134 | 1085 | 1219 | Yes |
| c7552 | generic gate verilog | signal trigger | 3512 | 9809 | 138 | 1361 | 1499 | Yes |
| bar | generic gate verilog | signal trigger | 2960 | 15,271 | 1391 | 2553 | 3944 | Yes |
| max | generic gate verilog | signal trigger | 5065 | 14,216 | 4486 | 4486 | 8972 | Yes |
| sin | generic gate verilog | signal trigger | 7656 | 25,970 | 2634 | 2323 | 4957 | Yes |
| arbiter | generic gate verilog | signal trigger | 23,189 | 59,600 | 4605 | 7087 | 11,692 | Yes |
| voter | generic gate verilog | signal trigger | 25,993 | 69,436 | 9437 | 8805 | 18,242 | Yes |
| square | generic gate verilog | signal trigger | 35,264 | 91,406 | 7976 | 12,017 | 19,993 | Yes |
| sqrt | generic gate verilog | signal trigger | 36,787 | 122,891 | 34,187 | 38,399 | 72,586 | Yes |
| multiplier | generic gate verilog | signal trigger | 42,974 | 131,690 | 8664 | 19,698 | 28,562 | Yes |
| log2 | generic gate verilog | signal trigger | 46,746 | 155,981 | 27,165 | 26,367 | 53,532 | Yes |
| memctrl | generic gate verilog | always on | 81,588 | 224,428 | 24,932 | 32,611 | 57,543 | Yes |
| div | generic gate verilog | always on | 100,985 | 274,228 | 27,908 | 264,972 | 320,788 | Yes |
| AES1-T1 | 180 nm CMOS library | signal trigger | 6956 | 82,182 | 3,185,023 | 25,703 | 3,210,726 | Yes |
| AES1-T2 | 180 nm CMOS library | always on | 6,861 | 81,055 | 3,184,493 | 25,608 | 3,210,101 | Yes |
| AES1-T3 | 180 nm CMOS library | signal trigger | 6905 | 82,286 | 3,188,966 | 25,676 | 3,214,642 | Yes |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, Q.; Liu, L.; Yuan, Y.; Zhang, Z.; He, J.; Gao, Y.; Li, Y.; Guo, X.; Zhao, Y. A Gate-Level Information Leakage Detection Framework of Sequential Circuit Using Z3. Electronics 2022, 11, 4216. https://doi.org/10.3390/electronics11244216
Zhang Q, Liu L, Yuan Y, Zhang Z, He J, Gao Y, Li Y, Guo X, Zhao Y. A Gate-Level Information Leakage Detection Framework of Sequential Circuit Using Z3. Electronics. 2022; 11(24):4216. https://doi.org/10.3390/electronics11244216
Chicago/Turabian StyleZhang, Qizhi, Liang Liu, Yidong Yuan, Zhe Zhang, Jiaji He, Ya Gao, Yao Li, Xiaolong Guo, and Yiqiang Zhao. 2022. "A Gate-Level Information Leakage Detection Framework of Sequential Circuit Using Z3" Electronics 11, no. 24: 4216. https://doi.org/10.3390/electronics11244216
APA StyleZhang, Q., Liu, L., Yuan, Y., Zhang, Z., He, J., Gao, Y., Li, Y., Guo, X., & Zhao, Y. (2022). A Gate-Level Information Leakage Detection Framework of Sequential Circuit Using Z3. Electronics, 11(24), 4216. https://doi.org/10.3390/electronics11244216






