Smart Random Walk Distributed Secured Edge Algorithm Using Multi-Regression for Green Network
Abstract
1. Introduction
- A smart multisensory interaction system to deal with delay tolerance and energy requirements with minimal network complexity.
- Performing an initial random walk on the vertices and edges of graphs to identify random routes based on certain probabilities to formulate the network topology.
- An optimized goal function to investigate a multi-regression model, and network devices computing optimal routes by adopting the learning process. In addition, lossy channels are determined to increase the data delivery performance.
- A trusted paradigm coping with the identification of malicious activities and increasing the reliability of traffic flow. Moreover, to lower the network threats, it also manages effective communication between edges and sink nodes.
2. Related Work
3. Problem Statement
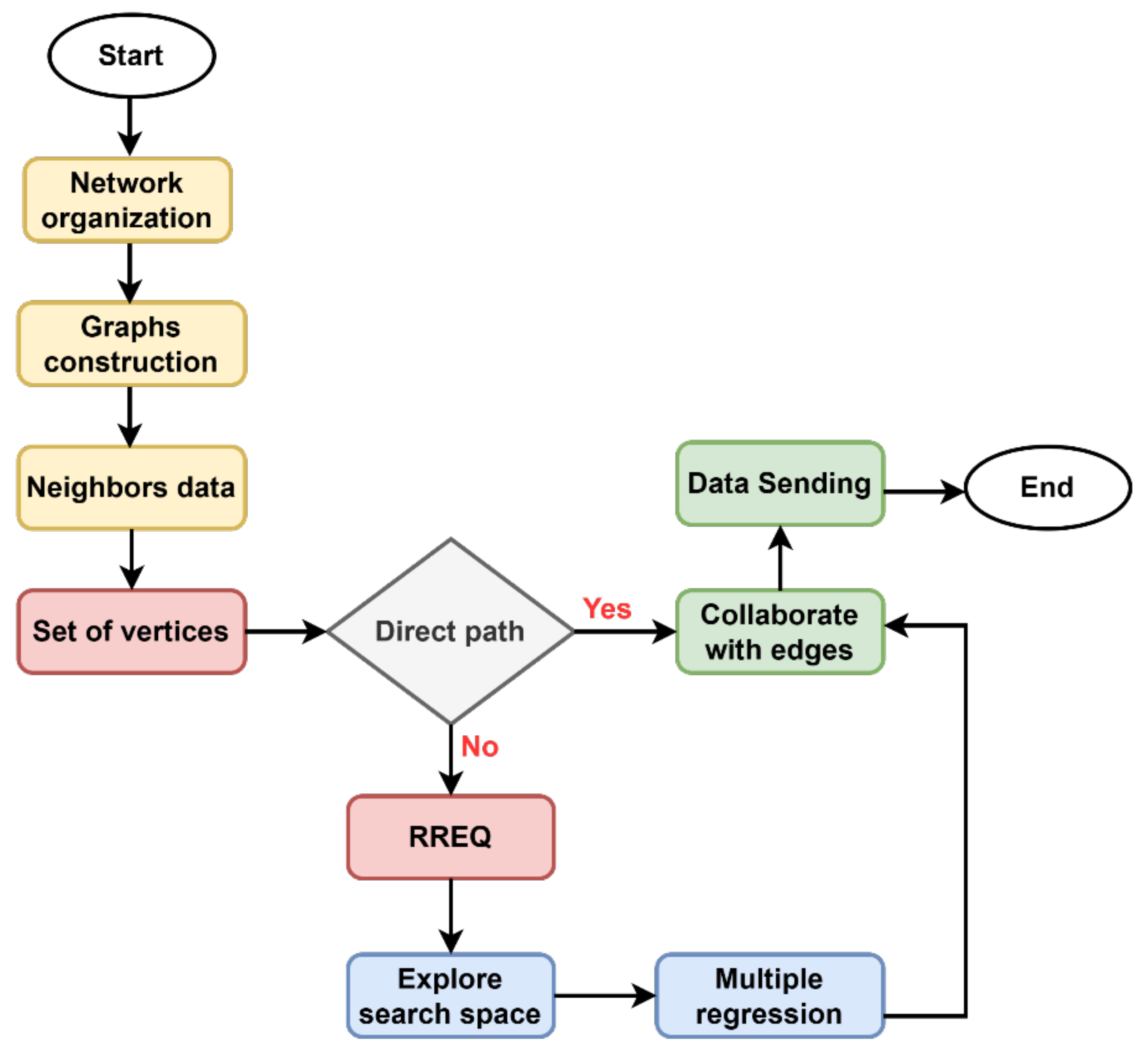
4. Distributed Random Walk Cooperative Edge Routing for Green Network
4.1. Proposal Overview
4.2. Proposed RDSE Algorithm
5. Simulation Environment
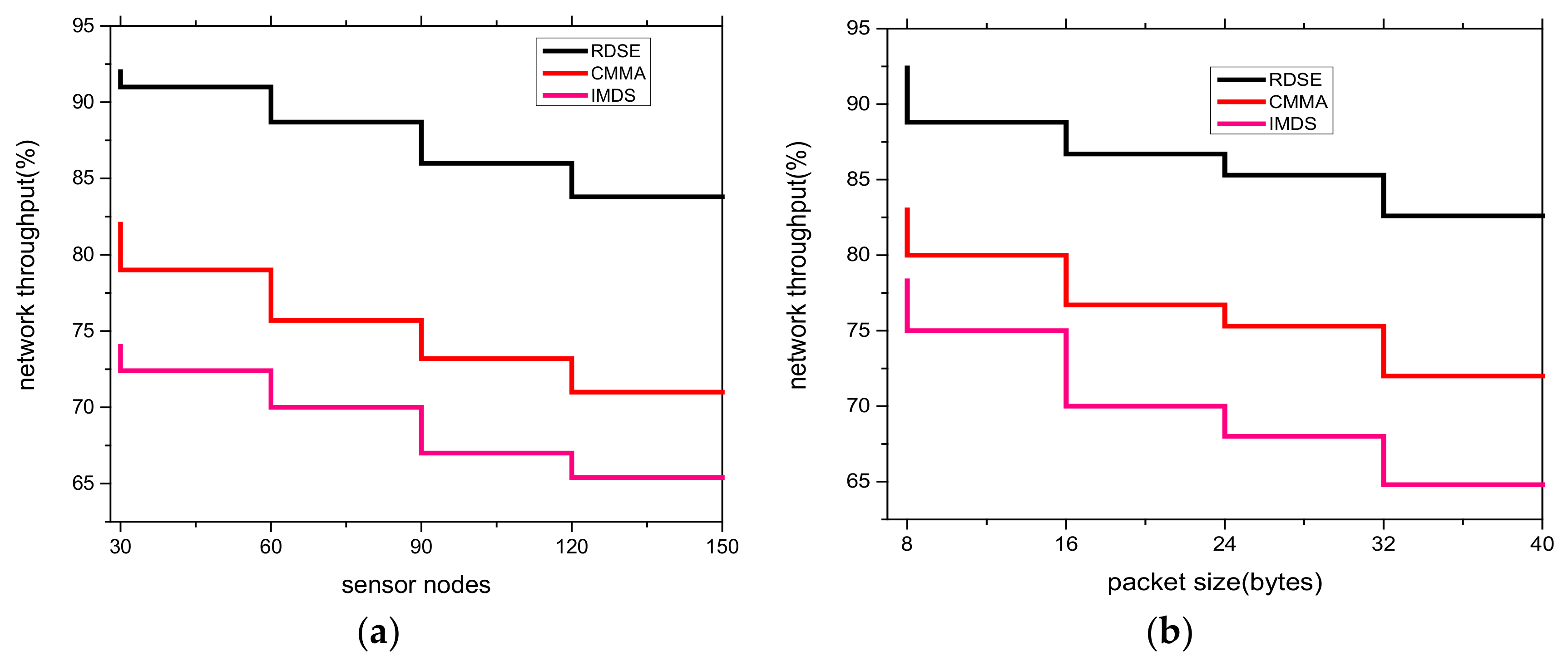
5.1. Network Throughput
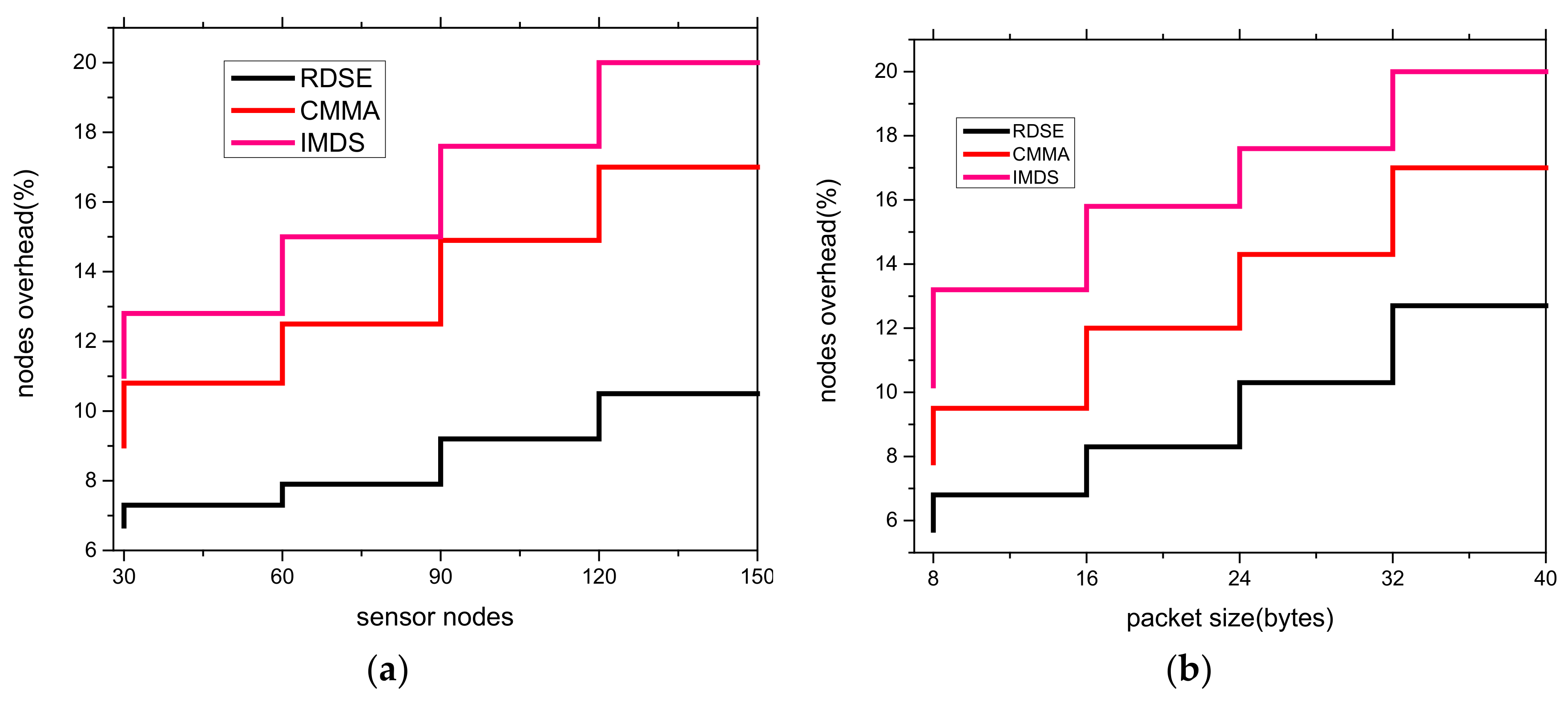
5.2. Nodes Overhead
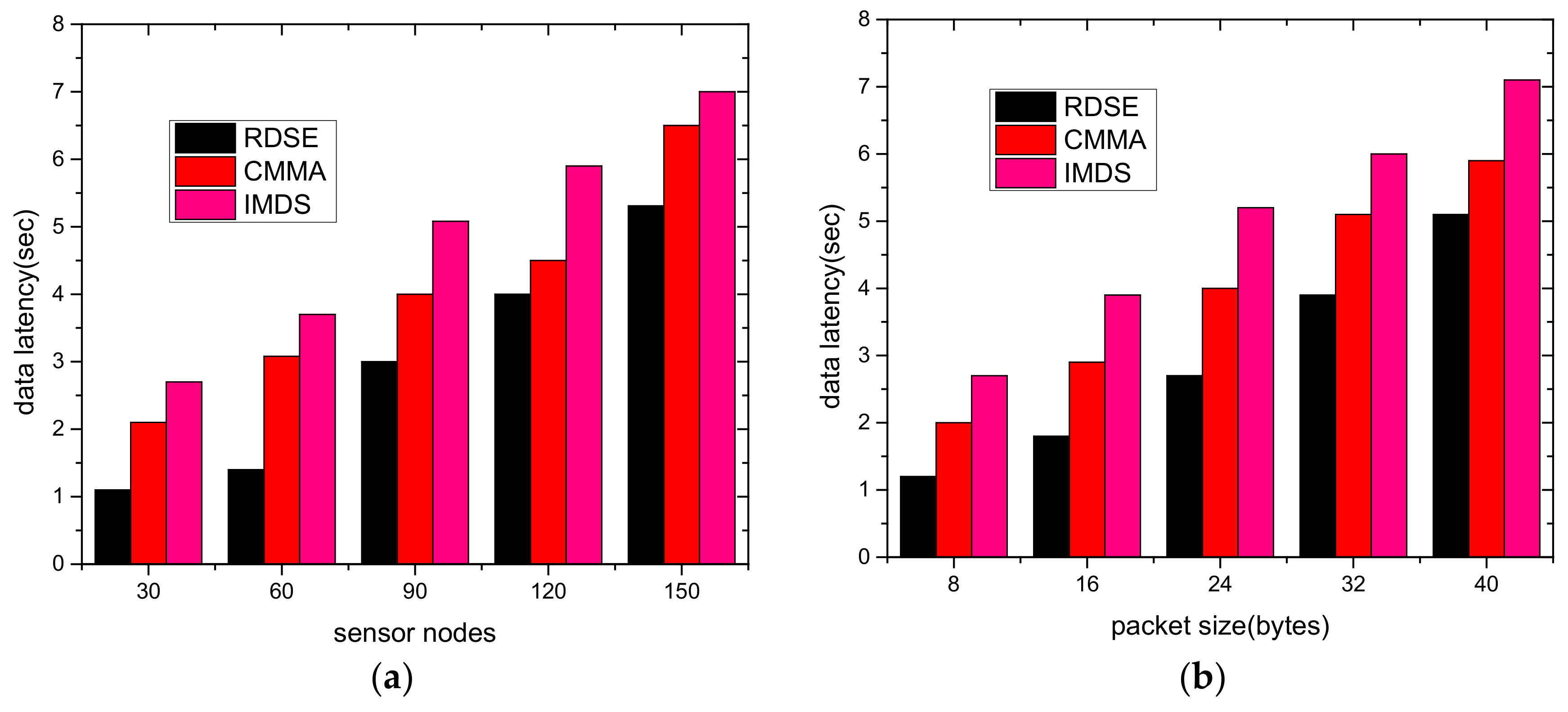
5.3. Data Latency
5.4. Number of Rounds
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| RDSE | Random walk Distributed Secured Edge algorithm |
| WSNs | Wireless Sensor Networks |
| M2M | Machine to Machine |
| NLP | Natural Language Processing |
| FBIS | Fuzzy-Based Inference System |
| CMMA | Clustering Model for Medical Applications |
| CMs | Cluster Members |
| IMDS | Intelligent Multimedia Data Segregation |
| Decision Tree | DT |
| CH | Cluster Head |
| DoS | Denial-of-Service |
| DT | Data Trustworthiness |
| CWSNs | clustered-WSNs |
| N2N | Node-to-Node |
| OTP | One-Time Pad |
| RREQ | Route REQuest |
References
- Al-Ansi, A.; Al-Ansi, A.M.; Muthanna, A.; Elgendy, I.A.; Koucheryavy, A. Survey on intelligence edge computing in 6G: Characteristics, challenges, potential use cases, and market drivers. Future Internet 2021, 13, 118. [Google Scholar] [CrossRef]
- Dai, W.; Nishi, H.; Vyatkin, V.; Huang, V.; Shi, Y.; Guan, X. Industrial edge computing: Enabling embedded intelligence. IEEE Ind. Electron. Mag. 2019, 13, 48–56. [Google Scholar] [CrossRef]
- Attaran, M. The impact of 5G on the evolution of intelligent automation and industry digitization. J. Ambient. Intell. Humaniz. Comput. 2021, 1–17. [Google Scholar] [CrossRef] [PubMed]
- Tang, Y.; Dananjayan, S.; Hou, C.; Guo, Q.; Luo, S.; He, Y. A survey on the 5G network and its impact on agriculture: Challenges and opportunities. Comput. Electron. Agric. 2021, 180, 105895. [Google Scholar] [CrossRef]
- Chettri, L.; Bera, R. A comprehensive survey on Internet of Things (IoT) toward 5G wireless systems. IEEE Internet Things J. 2019, 7, 16–32. [Google Scholar] [CrossRef]
- Yunana, K.; Alfa, A.A.; Misra, S.; Damasevicius, R.; Maskeliunas, R.; Oluranti, J. Internet of Things: Applications, Adoptions and Components—A Conceptual Overview. In Hybrid Intelligent Systems; Springer International Publishing: Cham, Switzerland, 2021; pp. 494–504. [Google Scholar] [CrossRef]
- Yasin, Q.; Iqbal, Z.; Khan, M.A.; Kadry, S.; Nam, Y. Reliable multipath flow for link failure recovery in 5G networks using SDN paradigm. Inf. Technol. Control. 2022, 51, 5–17. [Google Scholar] [CrossRef]
- Verma, P.K.; Verma, R.; Prakash, A.; AshishAgrawal, A.; Naik, K.; Tripathi, R.; Alsabaan, M.; Khalifa, T.; Abdelkader, T.; Abogharaf, A. Machine-to-Machine (M2M) communications: A survey. J. Netw. Comput. Appl. 2016, 66, 83–105. [Google Scholar] [CrossRef]
- Zhang, S.; Xu, X.; Wu, Y.; Lu, L. 5G: Towards energy-efficient, low-latency and high-reliable communications networks. In Proceedings of the 2014 IEEE International Conference on Communication Systems, Macau, China, 19–21 November 2014. [Google Scholar]
- Agiwal, M.; Roy, A.; Saxena, N. Next generation 5G wireless networks: A comprehensive survey. IEEE Commun. Surv. Tutor. 2016, 18, 1617–1655. [Google Scholar] [CrossRef]
- Qian, X.; Chen, H.; Cai, Y.; Chu, K.-C.; Xu, W.; Huang, M.-C. Transfer Learning Model Knowledge Across Multi-sensors Locations over Body Sensor Network. IEEE Sens. J. 2022, 22, 10663–10670. [Google Scholar] [CrossRef]
- Jabbar, M.; Shandilya, S.K.; Kumar, A.; Shandilya, S. Applications of cognitive internet of medical things in modern healthcare. Comput. Electr. Eng. 2022, 102, 108276. [Google Scholar] [CrossRef]
- Sangulagi, P.; Sutagundar, A.V. Sensor Cloud-Based Theoretical Machine Learning Models for Predicting Pandemic Diseases. In Intelligent Interactive Multimedia Systems for E-Healthcare Applications; Apple Academic Press: Palm Bay, FL, USA, 2022; pp. 167–196. [Google Scholar]
- Okewu, E.; Misra, S.; Maskeliūnas, R.; Damaševičius, R.; Fernandez-Sanz, L. Optimizing green computing awareness for environmental sustainability and economic security as a stochastic optimization problem. Sustainability 2017, 9, 1857. [Google Scholar] [CrossRef]
- Saba, T.; Rehman, A.; Haseeb, K.; Bahaj, S.A.; Damaševičius, R. Sustainable data-driven secured optimization using dynamic programming for green internet of things. Sensors 2022, 22, 7876. [Google Scholar] [CrossRef]
- Fedele, R.; Merenda, M. An IoT system for social distancing and emergency management in smart cities using multi-sensor data. Algorithms 2020, 13, 254. [Google Scholar] [CrossRef]
- Pekar, A.; Mocnej, J.; Seah, W.K.G.; Zolotova, I. Application domain-based overview of IoT network traffic characteristics. ACM Comput. Surv. (CSUR) 2020, 53, 1–33. [Google Scholar] [CrossRef]
- Ye, F.; Zhou, X.; Ren, Z.; Yang, S. Energy allocation for stochastic event detection in rechargeable sensor networks. Inf. Technol. Control. 2022, 51, 283–293. [Google Scholar] [CrossRef]
- Abdulkareem, K.H.; Mohammed, M.A.; Gunasekaran, S.S.; Al-Mhiqani, M.N.; Mutlag, A.A.; Mostafa, S.A.; Ali, N.S.; Ibrahim, D.A. A review of fog computing and machine learning: Concepts, applications, challenges, and open issues. IEEE Access 2019, 7, 153123–153140. [Google Scholar] [CrossRef]
- Aceto, G.; Persico, V.; Pescapé, A. A survey on information and communication technologies for industry 4.0: State-of-the-art, taxonomies, perspectives, and challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3467–3501. [Google Scholar] [CrossRef]
- Wang, Y.; Wang, K.; Huang, H.; Miyazaki, T.; Guo, S. Traffic and computation co-offloading with reinforcement learning in fog computing for industrial applications. IEEE Trans. Ind. Inform. 2018, 15, 976–986. [Google Scholar] [CrossRef]
- Saba, T.; Haseeb, K.; Shah, A.A.; Rehman, A.; Tariq, U.; Mehmood, Z. A Machine-Learning-Based Approach for Autonomous IoT Security. IT Prof. 2021, 23, 69–75. [Google Scholar] [CrossRef]
- Shanmuganathan, V.; Kalaivani, L.; Kadry, S.; Suresh, A.; Harold Robinson, Y.; Lim, S. Eeccrn: Energy enhancement with css approach using q-learning and coalition game modelling in crn. Inf. Technol. Control. 2021, 50, 171–187. [Google Scholar] [CrossRef]
- Ogundokun, R.O.; Arowolo, M.O.; Misra, S.; Damasevicius, R. An Efficient Blockchain-Based IoT System Using Improved KNN Machine Learning Classifier. In Blockchain based Internet of Things; Springer: Singapore, 2022; pp. 171–180. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Ni, J.; Zhang, N.; Shen, X. Blockchain-empowered space-air-ground integrated networks: Opportunities, challenges, and solutions. IEEE Commun. Surv. Tutor. 2021, 24, 160–209. [Google Scholar] [CrossRef]
- Rehman, A.; Haseeb, K.; Saba, T.; Lloret, J.; Tariq, U. Secured Big Data Analytics for Decision-Oriented Medical System Using Internet of Things. Electronics 2021, 10, 1273. [Google Scholar] [CrossRef]
- Moin, S.; Karim, A.; Safdar, Z.; Safdar, K.; Ahmed, E.; Imran, M. Securing IoTs in distributed blockchain: Analysis, requirements and open issues. Future Gener. Comput. Syst. 2019, 100, 325–343. [Google Scholar] [CrossRef]
- Tariq, N.; Asim, M.; Al-Obeidat, F.; Zubair Farooqi, M.; Baker, T.; Hammoudeh, M.; Ghafir, I. The security of big data in fog-enabled IoT applications including blockchain: A survey. Sensors 2019, 19, 1788. [Google Scholar] [CrossRef] [PubMed]
- Wu, Y.; Dai, H.-N.; Wang, H. Convergence of blockchain and edge computing for secure and scalable IIoT critical infrastructures in industry 4.0. IEEE Internet Things J. 2020, 8, 2300–2317. [Google Scholar] [CrossRef]
- Alrowaily, M.; Lu, Z. Secure edge computing in IoT systems: Review and case studies. In Proceedings of the 2018 IEEE/ACM Symposium on Edge Computing (SEC), Seattle, WA, USA, 25–27 October 2018. [Google Scholar]
- El Zouka, H.A.; Hosni, M.M. Secure IoT communications for smart healthcare monitoring system. Internet Things 2021, 13, 100036. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Prieta, F.D.L.; Prieto, J.; Corchado, J. Blockchain Framework for IoT Data Quality via Edge Computing. In Proceedings of the 1st Workshop on Blockchain-Enabled Networked Sensor Systems 2018, Shenzhen, China, 4 November 2018. [Google Scholar]
- Wang, T.; Qiu, L.; Sangaiah, A.K.; Liu, A.; Alam Bhuiyan, Z.; Ma, Y. Edge-computing-based trustworthy data collection model in the internet of things. IEEE Internet Things J. 2020, 7, 4218–4227. [Google Scholar] [CrossRef]
- Han, T.; Zhang, L.; Pirbhulal, S.; Wu, W.; de Albuquerque, V.H.C. A novel cluster head selection technique for edge-computing based IoMT systems. Comput. Netw. 2019, 158, 114–122. [Google Scholar] [CrossRef]
- Wang, T.; Zhang, G.; Liu, A.; Alam Bhuiyan, Z.; Jin, Q. A secure IoT service architecture with an efficient balance dynamics based on cloud and edge computing. IEEE Internet Things J. 2018, 6, 4831–4843. [Google Scholar] [CrossRef]
- Kishor, A.; Chakraborty, C.; Jeberson, W. A novel fog computing approach for minimization of latency in healthcare using machine learning. Int. J. Interact. Multimedia Artif. Intell. 2021, 6, 7–17. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Muta, O. A game-theoretic approach for enhancing security and data trustworthiness in IoT applications. IEEE Internet Things J. 2020, 7, 11250–11261. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Fouda, M.M.; Ibrahem, M.I. Data Privacy Preservation and Security in Smart Metering Systems. Energies 2022, 15, 7419. [Google Scholar] [CrossRef]
- Moustafa, S.S.R.; Abdalzaher, M.S.; Yassien, M.H.; Wang, T.; Elwekeil, M.; Hafiez, H.E.A. Development of an optimized regression model to predict blast-driven ground vibrations. IEEE Access 2021, 9, 31826–31841. [Google Scholar] [CrossRef]
- Abdalzaher, M.S.; Samy, L.; Muta, O. Non-zero-sum game-based trust model to enhance wireless sensor networks security for IoT applications. IET Wirel. Sens. Syst. 2019, 9, 218–226. [Google Scholar] [CrossRef]
- Corchado, J.M.; Ossowski, S.; Rodríguez-González, S.; De la Prieta, F. Advances in explainable artificial intelligence and edge computing applications. Electronics 2022, 11, 3111. [Google Scholar] [CrossRef]
- Venckauskas, A.; Stuikys, V.; Damasevicius, R.; Jusas, N. Modelling of internet of things units for estimating security-energy-performance relationships for quality of service and environment awareness. Secur. Commun. Netw. 2016, 9, 3324–3339. [Google Scholar] [CrossRef]
- Yigitcanlar, T.; Mehmood, R.; Corchado, J.M. Green artificial intelligence: Towards an efficient, sustainable and equitable technology for smart cities and futures. Sustainability 2021, 13, 8952. [Google Scholar] [CrossRef]


| 1 Byte | 1 Byte | 2 Bytes |
|---|---|---|
| Node identity | Node position | Computed weight |
| Notations | Description |
|---|---|
| threshold | |
| random routes | |
| vertices | |
| weighted value | |
| composite metrics | |
| residual variable | |
| random walk | |
| radius | |
| probability | |
| symmetric key | |
| sink node | |
| edges | |
| data forwarder | |
| edge identity | |
| sensor identity | |
| message | |
| decryption | |
| Xor |
| Parameters | Values |
|---|---|
| IoT Devices | 30–150 |
| Initial energy | 5 J |
| Simulator | NS-3 |
| Network diameter | 500 m × 500 m |
| Topology | Wireless |
| Packet size | 8 bytes to 40 bytes |
| Transmission range | 5 m |
| Sink deployment | Random |
| Simulation interval | 5000 s |
| Edges | 10 |
| Malicious devices | 20 |
| Number of simulations | 30 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saba, T.; Haseeb, K.; Rehman, A.; Damaševičius, R.; Bahaj, S.A. Smart Random Walk Distributed Secured Edge Algorithm Using Multi-Regression for Green Network. Electronics 2022, 11, 4141. https://doi.org/10.3390/electronics11244141
Saba T, Haseeb K, Rehman A, Damaševičius R, Bahaj SA. Smart Random Walk Distributed Secured Edge Algorithm Using Multi-Regression for Green Network. Electronics. 2022; 11(24):4141. https://doi.org/10.3390/electronics11244141
Chicago/Turabian StyleSaba, Tanzila, Khalid Haseeb, Amjad Rehman, Robertas Damaševičius, and Saeed Ali Bahaj. 2022. "Smart Random Walk Distributed Secured Edge Algorithm Using Multi-Regression for Green Network" Electronics 11, no. 24: 4141. https://doi.org/10.3390/electronics11244141
APA StyleSaba, T., Haseeb, K., Rehman, A., Damaševičius, R., & Bahaj, S. A. (2022). Smart Random Walk Distributed Secured Edge Algorithm Using Multi-Regression for Green Network. Electronics, 11(24), 4141. https://doi.org/10.3390/electronics11244141













