Abstract
The Internet of Things is a system of interconnected smart devices that can communicate with each other and with other devices over the Internet, with or without human-to-human or human-to-computer interaction. Although IoT devices, which have IPs, make living easier, they are also a threat to the security and privacy of people. This research work presents a solution to the problem of security in the network of IoT, based on the idea of implementing the blockchain in IoT. Blockchain is a decentralized technology that adds blocks at the end of the chain. It saves the hash value for every block, and corresponds to the previous block. The decentralized behavior of blockchain is best for IoT as an extensive network, because IoT must not have a single point of failure, and one entity must not decide what to do. All the capable storage devices will save the same data entered from any device, removing the risk of receiving altered data.
1. Introduction
The current era is one of technology, and a decision’s success or failure depends on data. The COVID-19 pandemic has generated a considerable amount of fear globally and has caused a significant number of deaths. Healthcare workers are doing their best to fight against this disease. The IoT plays a vital role in real-time health monitoring, tracking, and reporting of the disease in this situation. In today’s world, everything depends on human beings being able to obtain all types of information. Even modern computers and the Internet include the information physically added by humans by typing, pressing buttons, scanning bar codes, capturing pictures using digital or analog cameras, and many other convenient means of adding records. Unfortunately, humans are not good enough to capture accurate data from the real world, which is also a problem. IoT is defined as the network of physical objects that can be located independently and communicate [1]. Kevin Ashton used the phrase “Internet of Things” [2] as the name of his presentation. Since then, the Internet of Things has become a popular topic, from titles of articles to the name of the European Union Conference. To decrease human effort and obtain more information for a better world, IoT has been used in sensors and actuators [3] to collect data and enable them to communicate with each other. However, with increasing ease comes the disadvantages of technology. The main drawback is data breaches. To maintain the privacy of individuals, it is necessary to protect their corresponding data.
The IoT is a resource-constrained field with many challenges; in addition, because it is the beginning of commercial use of this field, much more work needs to be done.
The five key challenges reported by [4] can be stated as:
Limited computation power and memory: Almost all the devices have limited computation capacity due to the limitation of battery life.
Insecure network options: To be easily available to a network, these devices allow insecure and vulnerable networking options such as Bluetooth and do not support complex communication protocols such as TCP/IP, making the system vulnerable to hackers.
Strong passwords are not enough: In IoT networks, people use simple devices such as smart home appliances, which only include single-factor password support. People also do not pay attention to password support, and in most cases, owners do not prefer to change the default password, which makes them an easy target for attacks.
High performance, lightweight cryptography: IoT devices must perform for high-level data purposes, but due to resource constraint problems, they possess very lightweight cryptography.
Enabling secure updates: IoT devices have less memory and computation power, which does not allow them to receive constant updates, and owners may forget to update the devices. This allows attackers to install their own framework and update it according to their wishes. To date, several solutions have been proposed to secure the network. However, all of these have challenges, making it difficult for users to trust the IoT.
The main objective of the research was to develop a distributed IoT-based system by implementing the idea of blockchain for the security and privacy of the data resulting from the network of IoT. The motivation to carry out this research is that it can help to secure sensitive healthcare data, such as those produced during the COVID-19 pandemic. Implementing blockchain makes the data of IoT secure by making them unalterable and distributed.
This research work contributes by developing a prototype of a system that is distributed. The proposed system is decentralized and captures the data linearly. It not only stores the data in a time-stamped manner, showing the origin of the data, but also stores it immutable, preventing the modification of the entered record. Based on this system, auditing is easy because the entities involved can be held accountable. Making the system transparent provides openness to all devices.
2. Literature Review
The growth of IoT devices is continually increasing. According to Gartner [5], the number of new IoT devices rose from 1.691 billion in 2015 to 3.054 billion in 2019; the number of IoT devices exceeded the world population in 2020; the number of IoT devices exceeded the total number of PCs, tablet PCs, and smartphones in 2018, and reached 20.4 billion in 2020. The value of the IoT field is estimated to have reached USD 235 billion in 2021, with an annual growth rate of 16%. This third wave of the information technology industry will change how we see and observe the world based on accurate, immediate, and timely data. Moreover, in a recent report, Ericsson projected that, by 2024, 22.3 billion IoT devices would be connected to the Internet, with a compound annual growth rate (CAGR) of 17%. The greatest increases in cellular IoT devices, given in billions, are shown in Table 1.

Table 1.
All IoT devices are connected to the Internet, as projected by Ericsson.
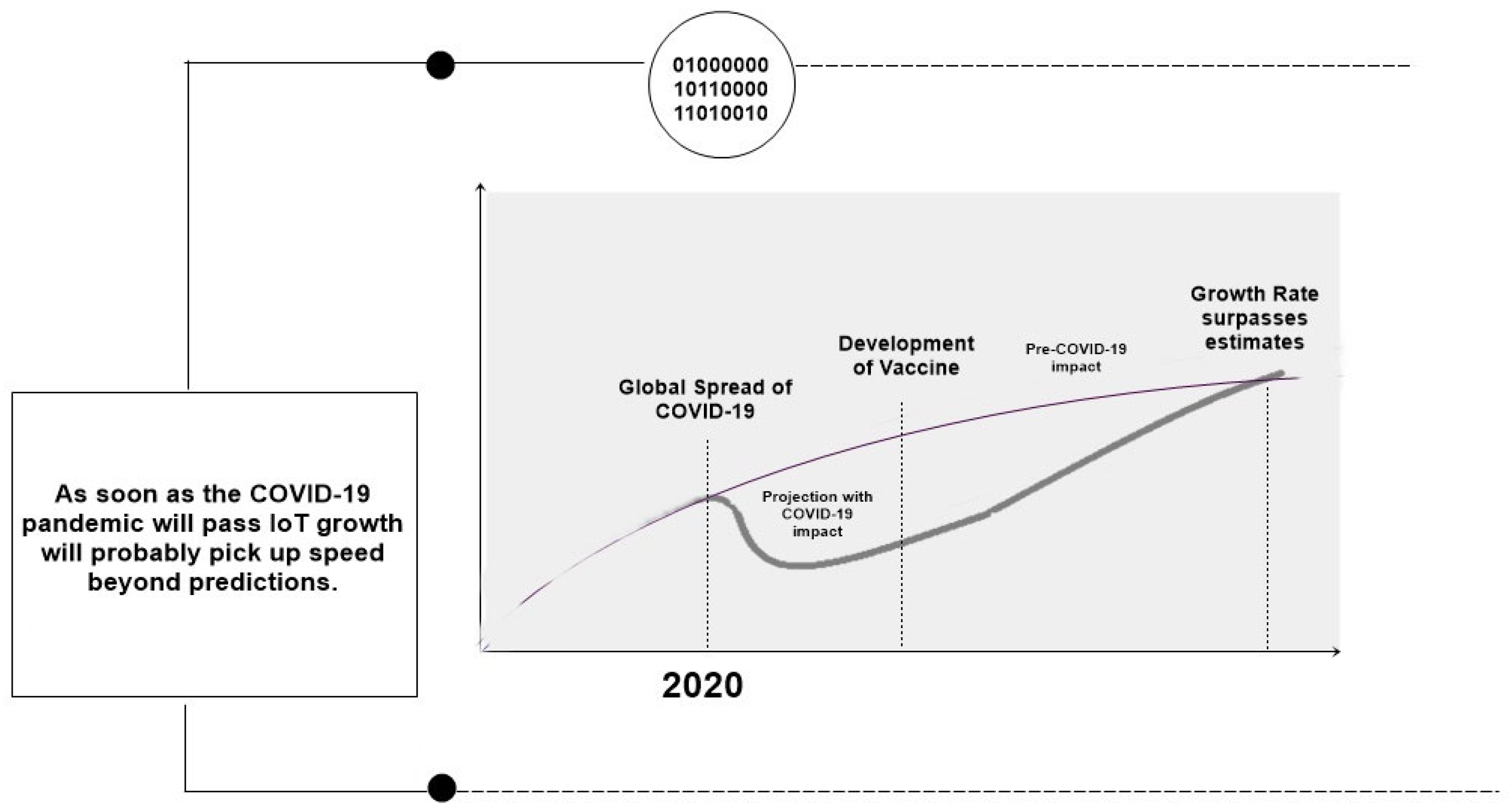
In the COVID-19 pandemic situation, the number of IoT devices increased rapidly. Figure 1 shows the growth in IoT during the COVID-19 pandemic.
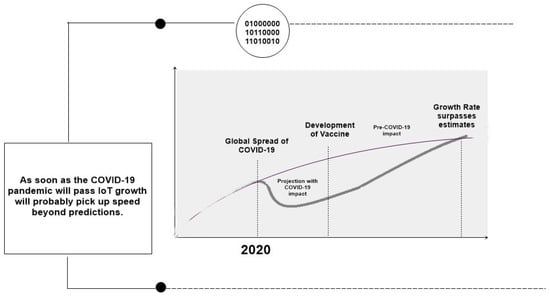
Figure 1.
Growth in IoT in the COVID-19 pandemic [6].
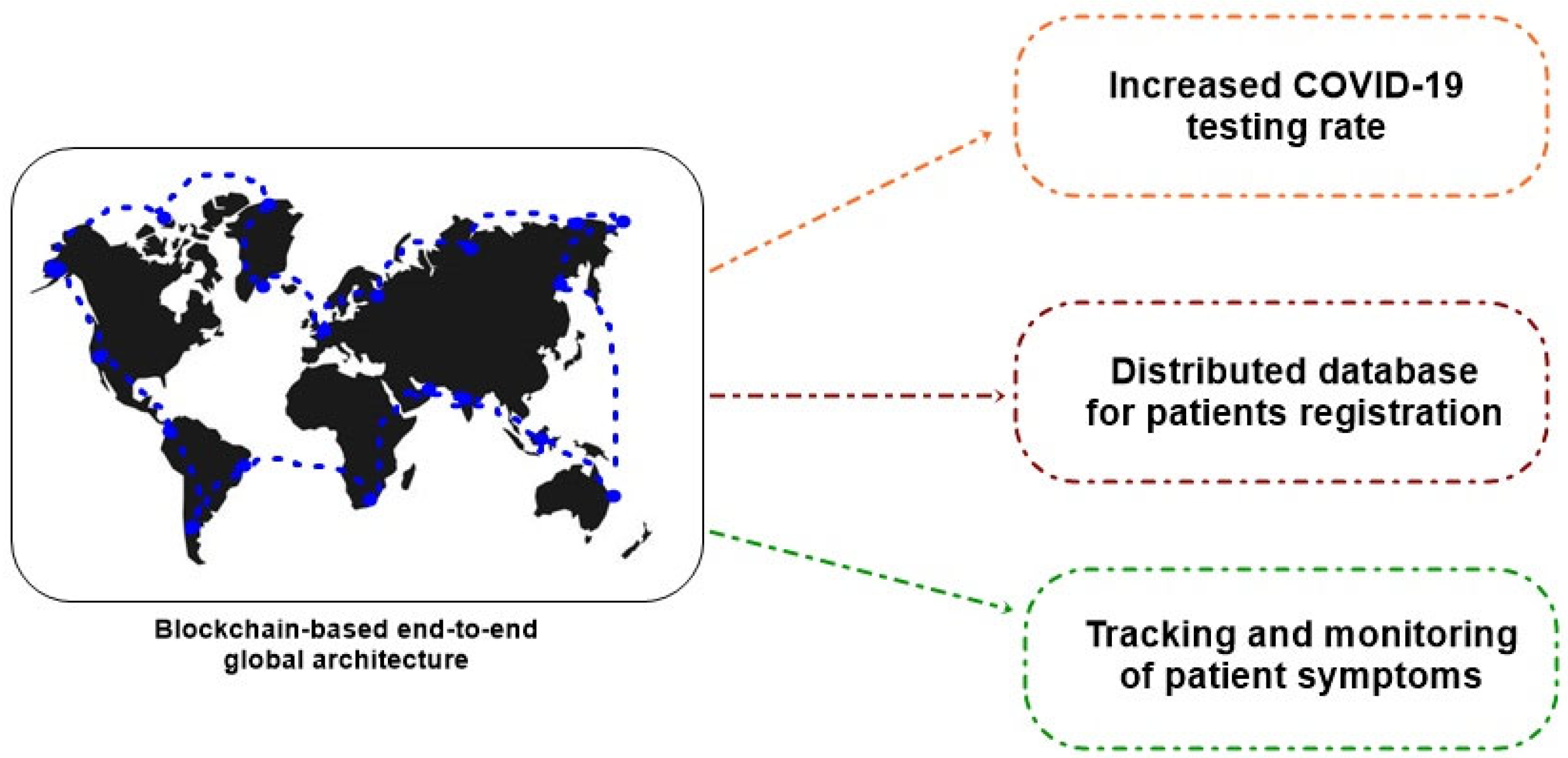
IoT GPS can be used in ambulance systems, and automated robots can take care of COVID-19 patients. Blockchain is used to track medical supplies, facilitate increased testing and reporting, record the details of COVID-19 patients, enable a secure donation platform for supporters, limit supply chain disruptions, etc. [7]. Figure 2 describes the blockchain-based system for COVID-19 management [8].
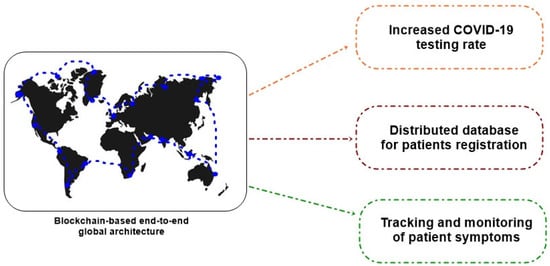
Figure 2.
COVID-19 impact management using blockchain.
For a sensitive network such as IoT, it is necessary that the network is secured to provide bespoke services to the users. According to experts [9,10,11], data is the lifeblood of IoT. Thus, to physically secure the IoT heterogeneous devices, which do not have memory capacity and have almost no computation power, the idea is to safeguard the most important data. Roberta Rottigni stated that over 3000 people in Sweden selected a smart chip [10] to be embedded inside their bodies instead of using a card or several keys, giving us a clearer perspective of IoT than the field involving things. Now, this domain also includes the human being itself. IoT services will be a key technology for enabling the growth of smart cities [11], and will transform how we do business, sustain health, develop serious infrastructure, conduct education, and secure, defend, and amuse ourselves. Incorporating physical and cyber systems and human behaviors and interactions (e.g., producers, consumers, and attackers) will increase dependent infrastructure ecosystems’ openness and attack surfaces. Building Automation Systems and Supervisory Control and Data Acquisition systems are the most common architectures to monitor and control intelligent structures such as smart homes and smart buildings. Building Automation Systems and Supervisory Control and Data Acquisition systems are interrelated with Internet resources and services, so they become easy targets for cyber adversaries. When discussing security challenges, IoT faces the same cyber security challenges faced by traditional Internet users, including DoS attacks, malware, and jamming attacks [12]. IoT devices are also being used to launch DoS attacks [3] for other systems, which are also dangerous for IoT devices. Distributed denial of service attacks (DDoS) is a well-known form of attack on IoT devices. Sensors and RFIDs are primary devices for collecting data; thus, for DDoS attacks, it is elementary to perform jamming, kill commands, and de-synchronizing assaults [13]. Users’ privacy is always a sensitive topic whenever there is a discussion about the challenges of IoT. Table 2 presents the existing security issues in IoT and their proposed solutions. Table 3 describes past and recent proposed IoT security solutions and their challenges.

Table 2.
Security issues of IoT at different layers and their proposed solutions.

Table 3.
Past and recent proposed IoT security solutions and their challenges.
Previous research has found that IoT networks can be secured by applying data provenance, blockchain, fog computing, edge computing, and machine learning techniques. Table 3 presents the proposed solutions to overcome the IoT security issues.
The network of IoT produces a massive amount of data, which can be considered big data. For a large amount of data, such as big data, usual data processing techniques are not enough. Tas et al. [46] suggested a decentralized system and concluded that a centralized system would not help. Moreover, many frameworks working on new big data tools have been proposed to work with enormous amounts of data, such as supporting IoT, RIS-aided, and SLNR-based secure energy [47,48,49,50]. They claim that distributed tools will help with searching and querying the data.
3. Materials and Methods
This study used a decentralized solution to support IoT in different fields, especially healthcare. The essence of IoT lies in the data it collects. The system ensures the availability of the correct data so that decisions taken on the collected data are reliable. Research assumes that data collection and decision-making are performed on the user side to decentralize the system, where services from a third party, such as the cloud, are not involved. The goal is to secure the IoT network, keeping in mind the resource-constrained behavior of IoT. A prototype using the programming language Python was developed to show the research results; this is an extra layer of security at the local store level. In blockchain technology, it is almost impossible to change the data accepted by all the nodes when they are not altered at the database level. Thus, it provides a basic level of data security in the system, ensuring that the data from resource-constrained devices can be trusted.
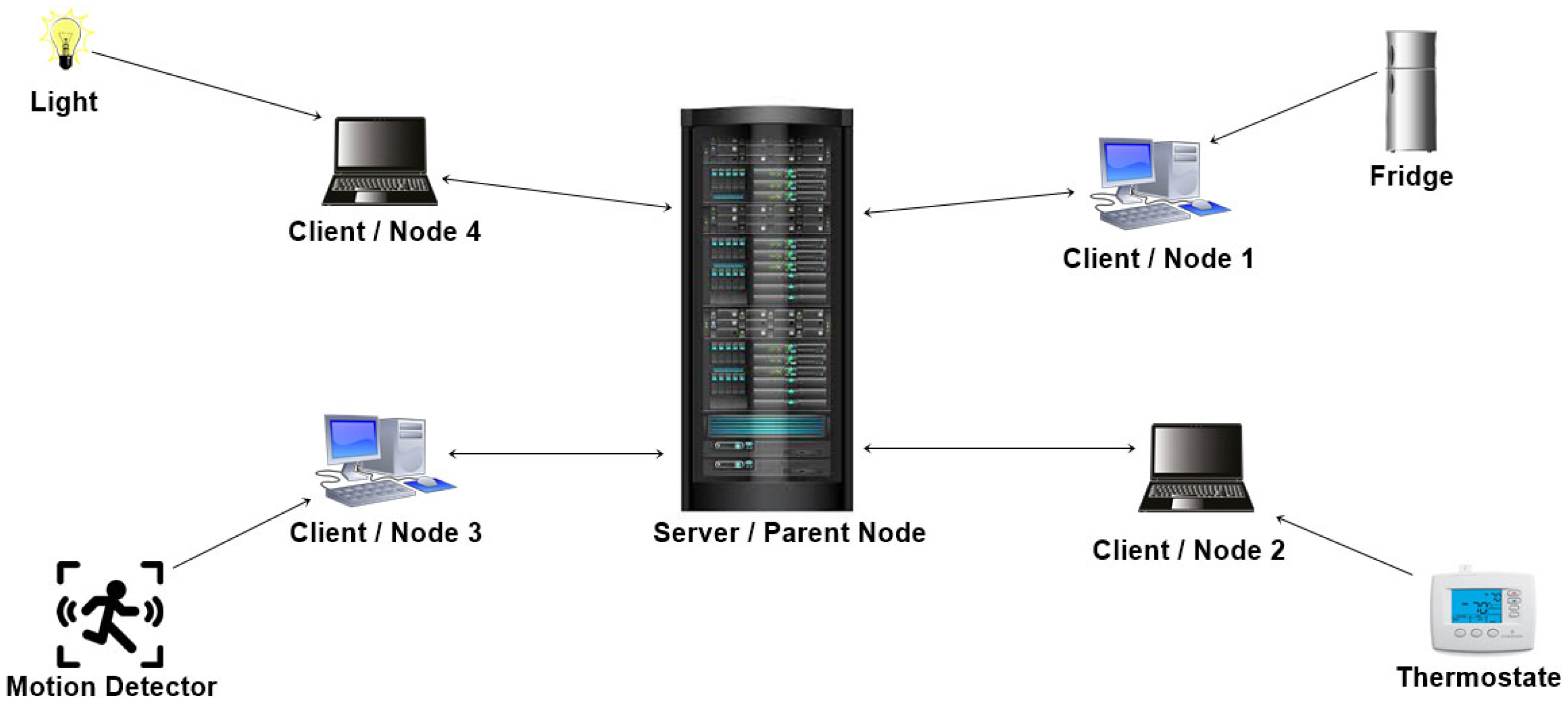
In the proposed model, all the devices are IoT devices with resource constraints, no computational power, low storage, and lower communication bandwidth. Suppose that the system is implemented in the traditional blockchain with complex algorithms, such as proof of work, requiring immense computational power; then, the idea of blockchain completely fails in the case of resource-constrained IoT devices. The proposed work and prototype system implements the basic concept of blockchain, which is decentralized, and the hash function, which is the backbone of blockchain. Each device that stores the data collected by the IoT device is a blockchain node; all of these storage devices make up the chain, and each new device is added at the end of the chain. When an IoT device collects data, that data string is sent and stored on every storage device, creating a decentralized system. When that string is entered and stored, a hash corresponding to that record is created and stored since the hash function ensures the same length of the line regardless of the size of the input string. Thus, it is almost impossible for attackers to guess or encrypt the original data. If the data are altered, the hash of that particular record is regenerated. This makes it impossible to modify or delete the data. The overall system works in three layers. The proposed IoT model is shown in Figure 3.
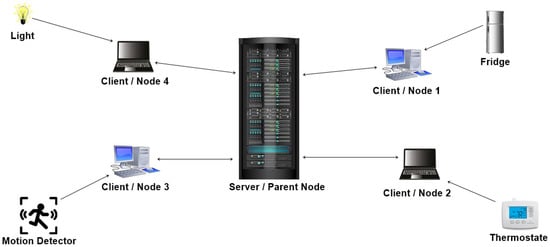
Figure 3.
Proposed IoT model.
4. Implementation
This section explains the solution proposed in this study. Additionally, it is shown that data can be stored in a decentralized manner. The proposed solution is implemented in Python. The prototype is implemented using the package/library language support to implement a hash function and server-side implementation. The implemented code for the proposed system is broken down into three parts: client-side, server-side, and the code implemented to show the data entered.
4.1. Client-Side Implementation Code
The client-side code allows the client to connect to the chain. Client-side code implements socket programming. A socket is an endpoint in a communication network where two or more programs run on the same network. The socket on each side is bound to a specific port number; the port number enables the system to identify where to send those data and which application is the destination. The client sends a request to the server for every connection, and further communication occurs if the server accepts the link.
4.2. Server-Side Implementation Code
The server hosts the request of the client. When the server is on, it listens to the new connection. When a client requests the link, the server connects to the clients, and communication occurs. Server-side codes were implemented through the socket library by the Python developers. The socket enables two-way communication by listening to the port destined for it. When a client requests the connection, the server listens to it and establishes a link that starts communication.
4.3. GUI Implementation Code
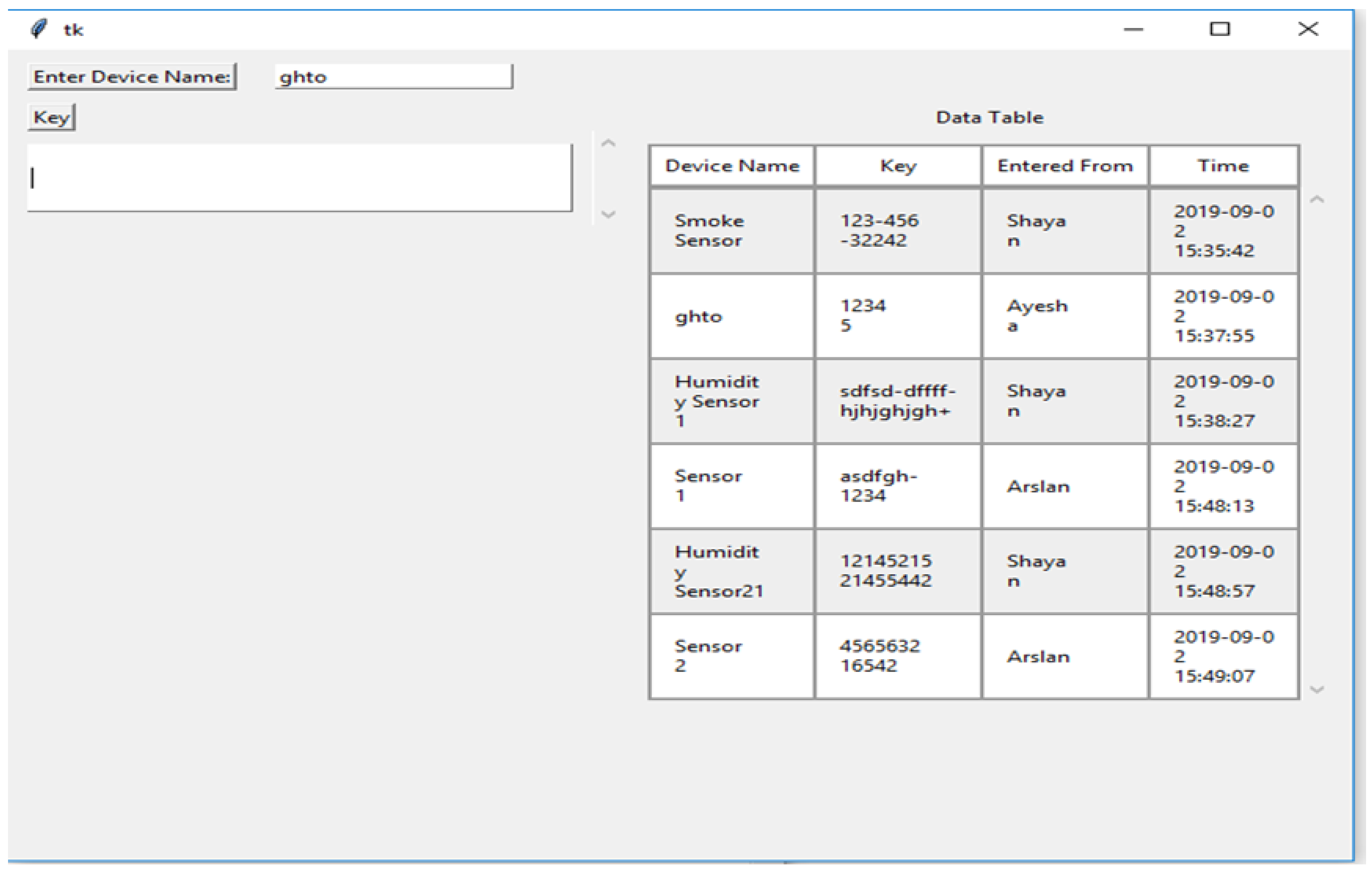
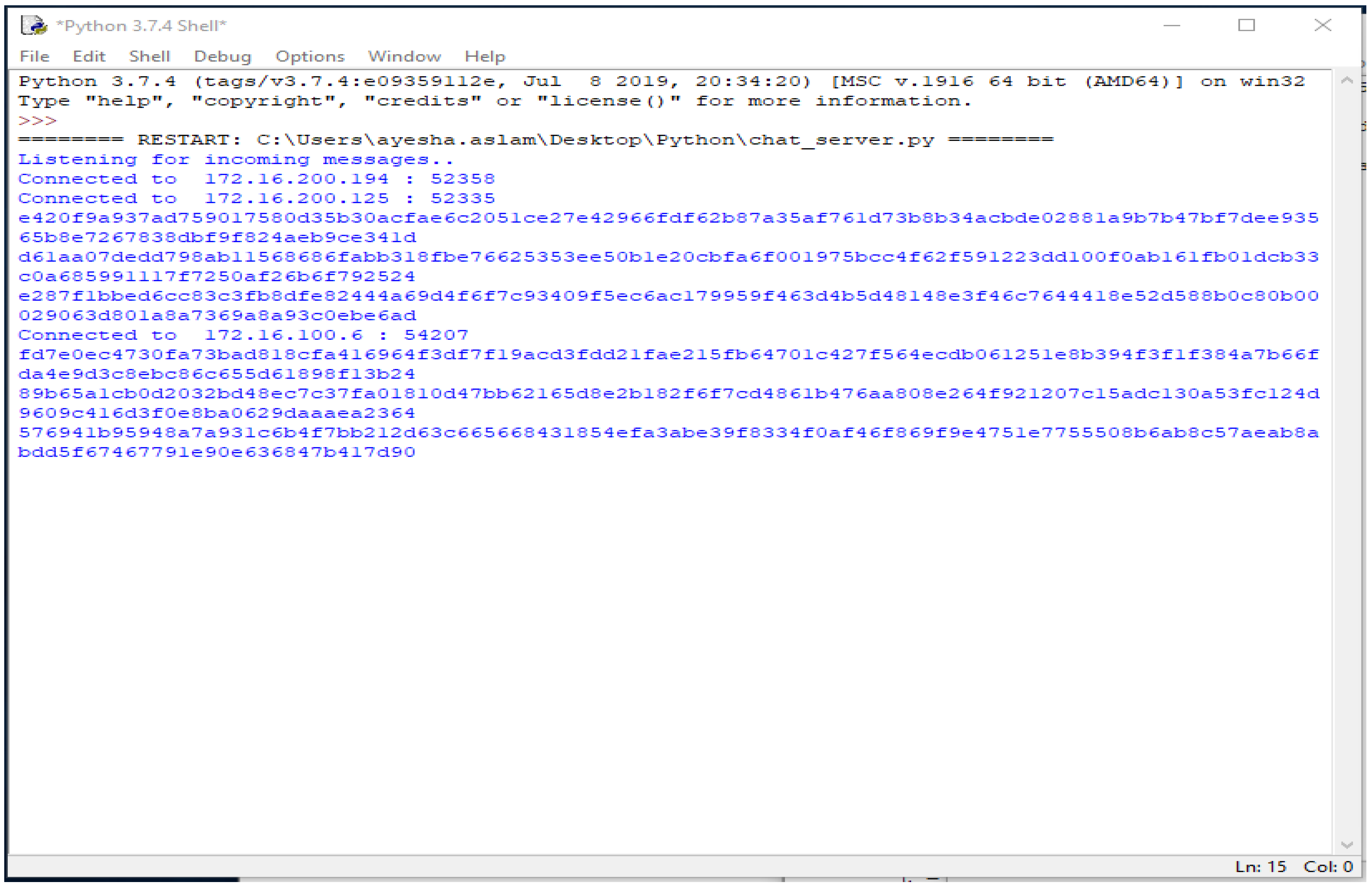
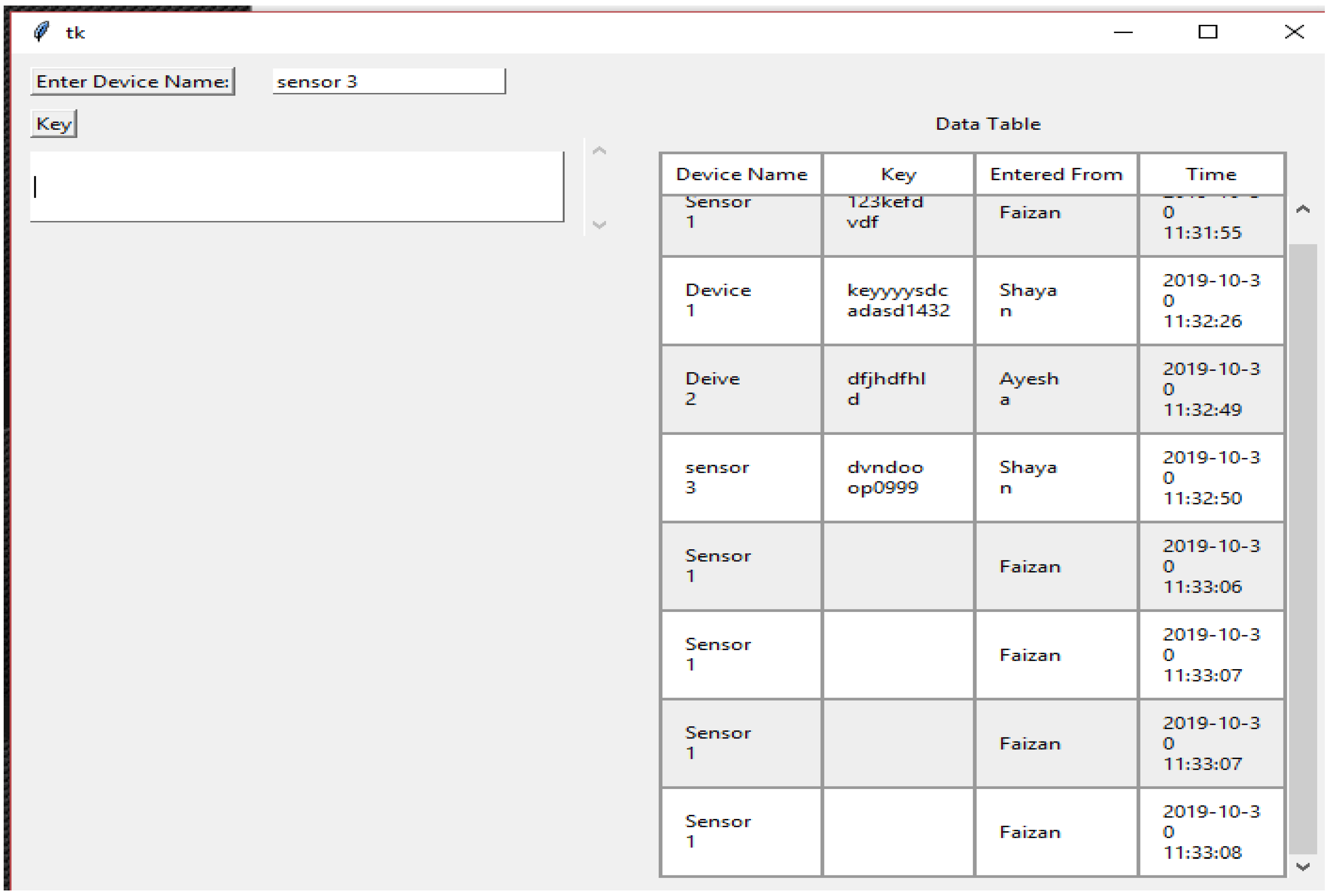
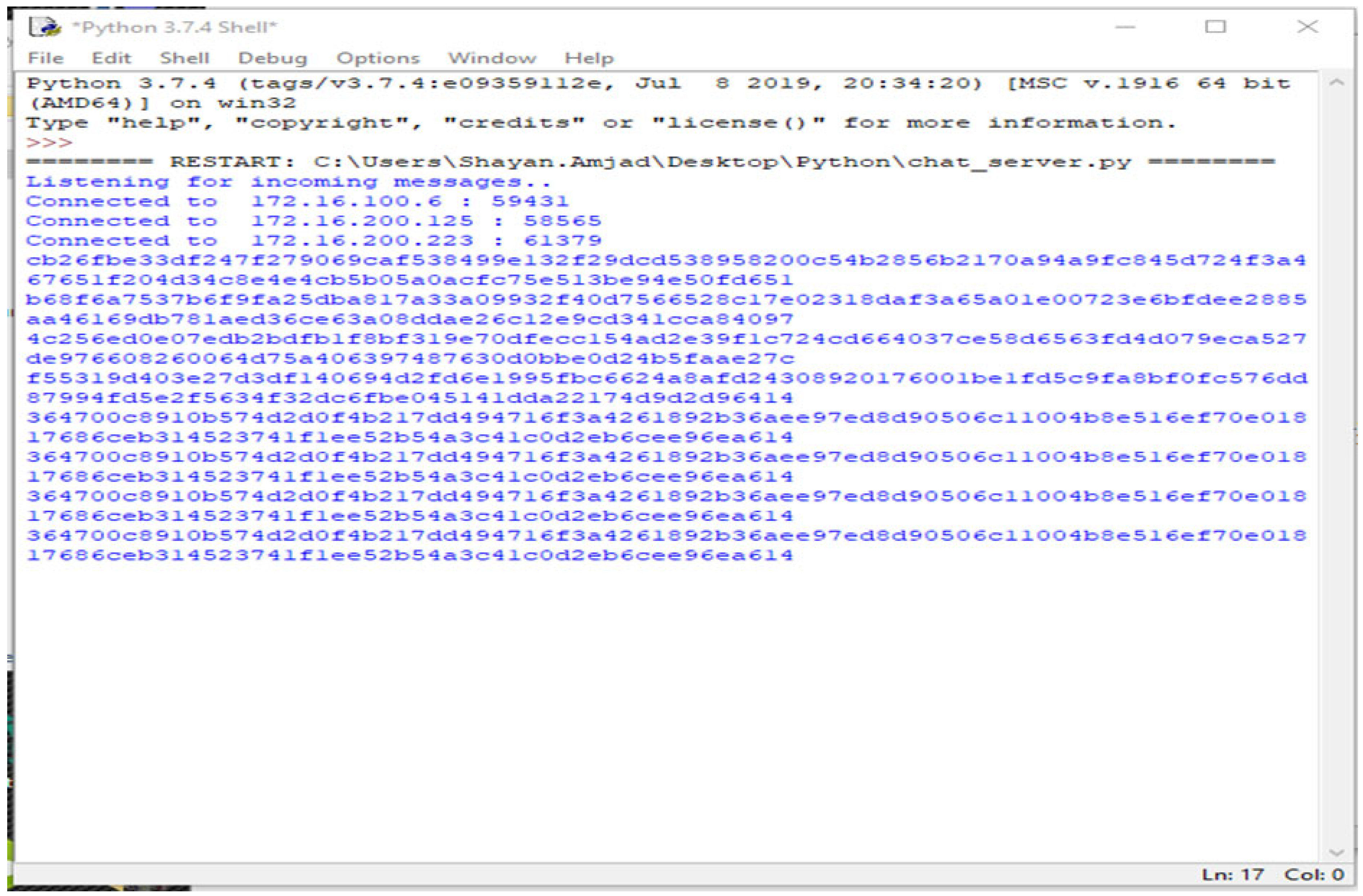
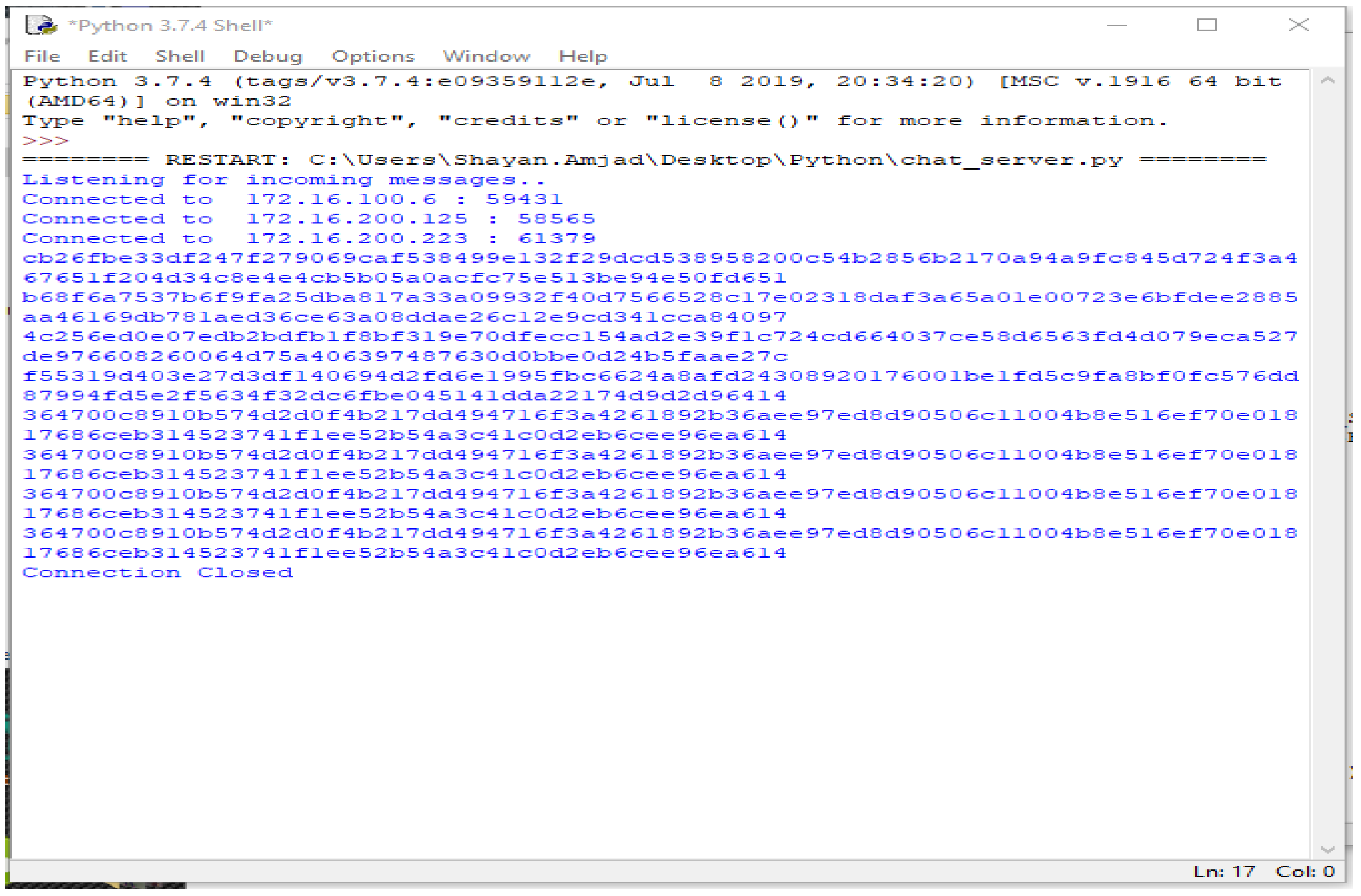
The third part of the code shows the graphical user interface. It helps all the nodes to view the data in the form of a table. Here, the GUI shows the results of the connected systems. It offers the three related systems, named Shayan, Ayesha, and Arslan, including manually added Device Names and the Key, and automatically showing the Name and the Time the data was entered. Figure 4, Figure 5, Figure 6, Figure 7 and Figure 8 illustrate the working of the proposed blockchain method applied to IoT. Every record has a hash responding to it.
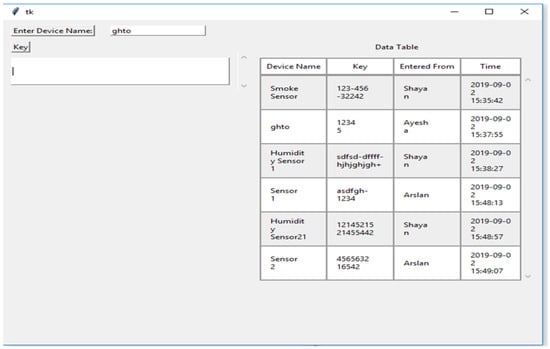
Figure 4.
Data of the chain.
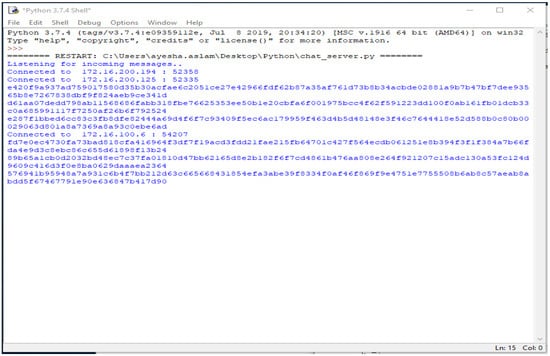
Figure 5.
Hash for every record.
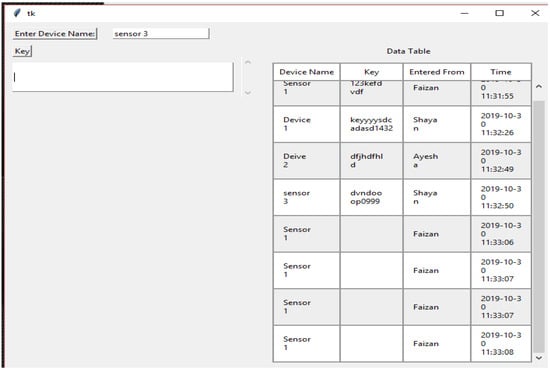
Figure 6.
New node joined.
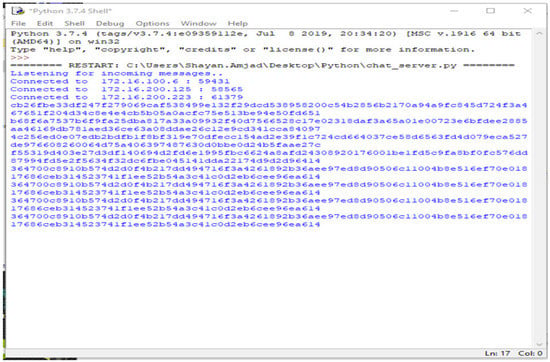
Figure 7.
Hash of record entered by the new node.
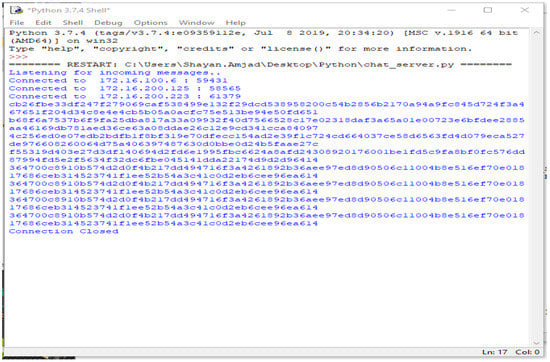
Figure 8.
One node disconnected.
A new connection joins, named Faizan, showing the timestamps and data entered. These data can be seen through every other node connected to the chain. In the table showing data, the entities “Time” and “Entered From” can never be changed by the user nodes. The entities “Key” and “Device Name” are the data entered and stored. Each record shown in the table has a hash value that is stored and visible only to the parent node. The following figure shows the corresponding hash values of each record entered.
When the new node joins and enters data, every activity is kept in the parent node, and every hash value is saved. This is shown in Figure 8 even if the node is disconnected and no longer connected to the system. The storage device still has the data entered by the node and their corresponding hash values.
When the node is disconnected server-side, or the parent node shows the message “Connection Closed”, entry of the data by the node is prevented. This is shown in Algorithm 1.
| Algorithm 1: Entry of the data |
| Server While(1) i = 0, data = null createsocket() communicateSocketAddress() listeningIncommingConnection() ConnectClient() while(i < no. of client) { Data = listen (client [i]) If data ≠ Ø Generate hash() J = 0 While(i < no. of clients) If(i ≠ j) Share(data, client[i]) Exit() } Client While(1) { createClientSocket() ConnectServer(IP, port) Save(data) Share(data) } closeConnection() |
A step-by-step explanation of the algorithm:
- Server
- Create a socket
- Share the socket address and continue to watch for incoming connection requests
- Link to client
- Data received
- Create a hash for each received string
- Share the received data with every other connected node
- Repeat steps 5 and 6 as desired by the user.
- Exit.
- Client/Nodes
- Make a distinct client socket for each node.
- Using the provided socket address, connect to the server (IP and port)
- Data sent and received.
- Repeat step 3 as configured.
- Close connection.
5. Analysis and Discussion
For an ever-growing technology such as IoT to succeed, it is necessary to make it secure. To date, all research that proposed implementing the blockchain for the network of IoT used a consensus algorithm to validate new nodes. The consensus algorithm requires computational power, and the addition of new nodes results in the non-availability and scalability of the chain. This research work presents a solution to solve the problem of security in IoT by making the system decentralized without implementing a consensus algorithm. The prototype implements a more straightforward cryptographic function known as a hash function. The hash function ensures the data’s security by mapping a variable-length string to a string having a fixed length. This mechanism makes the decryption hard for attackers, and it is almost impossible to guess the actual line. The prototype shows that, with decentralized technology, all the data will be linearly appended at the end of the chain, and cannot be changed once entered. Moreover, the data cannot be deleted once entered, provided it is kept on-chain. As a result, the data of the system can be used reliably.
In the case of damage to one system, the data is safe on the other points. In blockchain technology, each transaction has a saved hash value. The proposed solution applies an extra security layer on the storage side. All the storage devices that collect and save IoT data have a decentralized system. All these storage devices are connected when an IoT device enters data held in any storage device; these data will be updated on each storage device attached. On the same side, each record entered by the machines will create a hash value. This hash value will be stored in the parent node/server. The hash value is never the same as the actual data, so no one can access or alter the data. When information is deleted or changed on the storage device, the hash value will remain on the parent node, and decrypted to obtain the original data. Even if the system disconnects the devices, these data are saved and available. The data collected by the devices are stored in raw form, which can be used to obtain insights into the data and maximum results.
6. Conclusions
During the COVID-19 pandemic, it was difficult for people to physically perform most work. As a result, most people moved their work online. IoT currently plays an important role, and many people benefit from it. A large amount of data is converted from physical to online. As the data rate increases, the data need to be managed and secured more efficiently. Blockchain plays an essential role, in this context, in ensuring people’s data on the Internet. A literature review shows that many techniques have been proposed to secure the network of IoT, each of which has shortcomings, meaning the network of IoT is not reliable. As a tamper-proof distributed and shared database, blockchain has been proven to be the best fit for IoT due to its benefits. Blockchain provides necessary features for security, including transparency, immutability, and audibility. Data stored in a decentralized manner do not allow modification of the records and maintain the history, which fulfills the concept of provenance.
Hence, the proposed study designed a system to use blockchain to make IoT data reliable. As a result, the network of IoT is an acceptable solution, especially in healthcare (COVID-19) and for people who have moved their work online. This study contributes to the security of data produced by IoT devices, but it still has many shortcomings which can be researched and addressed. The approach used in this study can be authenticated by professionals using the system of IoT. The organizations implementing the IoT system to collect data and gain insights into the data will further elaborate on the system’s shortcomings.
Author Contributions
Conceptualization, H.A.M.M.; Methodology, A.A.S.; Software, A.K.; Formal analysis, A.A.S., A.M. and A.K.; Resources, A.A.; Data curation, A.A.; Writing—original draft, A.A.S. and A.A.; Writing—review & editing, H.A.M.M., A.M. and A.K.; Project administration, H.A.M.M. and A.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Lucero, S. IoT Platforms: Enabling the Internet of Things; White Paper; IHS TECHNOLOGY: Landisville, PA, USA, 2016; pp. 1–21. Available online: https://cdn.ihs.com/www/pdf/enabling-IOT.pdf (accessed on 10 October 2022).
- Singh, V.; Dahiya, N. Blockchain-Based Federated Machine Learning for Solving IoT Security Problems. In Applications of Blockchain and Big IoT Systems, 1st ed.; Apple Academic Press: Primary, FL, USA, 2022; pp. 27–56. [Google Scholar]
- Ning, H.; Liu, H.; Yang, L.T. Cyberentity Security in the Internet of Things. Computer 2013, 46, 46–53. [Google Scholar] [CrossRef]
- Heer, T.; Garcia-Morchon, O.; Hummen, R.; Keoh, S.L.; Kumar, S.S.; Wehrle, K. Security Challenges in the IP-based Internet of Things. Wirel. Pers. Commun. 2011, 61, 527–542. [Google Scholar] [CrossRef]
- Pettey, C.; Goasduff, L. Gartner Reveals Top Predictions for IT Organizations and Users for 2011 and Beyond; Gartner: Stamford, CT, USA, 2010; pp. 1–2. Available online: http://www.gartner.com/newsroom/id/1480514 (accessed on 10 October 2022).
- State of the Connected World. 2020 Edition. Available online: https://www.weforum.org/reports/state-of-the-connected-world-2020-edition (accessed on 10 October 2022).
- Abd-Alrazaq, A.A.; Alajlani, M.; Alhuwail, D.; Erbad, A.; Giannicchi, A.; Shah, Z.; Hamdi, M.; Househ, M. Blockchain technologies to mitigate COVID-19 challenges: A scoping review. Comput. Methods Programs Biomed. Update 2020, 1, 100001. [Google Scholar] [CrossRef] [PubMed]
- Chamola, V.; Hassija, V.; Gupta, V.; Guizani, M. A Comprehensive Review of the COVID-19 Pandemic and the Role of IoT, Drones, AI, Blockchain, and 5G in Managing its Impact. IEEE Access 2020, 8, 90225–90265. [Google Scholar] [CrossRef]
- The Economist. The World’s Most Valuable Resource Is No Longer Oil, but Data. 11 May 2017. Available online: https://www.economist.com/leaders/2017/05/06/the-worlds-most-valuable-resource-is-no-longer-oil-but-data (accessed on 10 October 2022).
- Pureswaran, V.; Brody, P. Device Democracy Saving the Future of the Internet of Things IBM Institute for Business Value. 2015, p. 26. Available online: https://www-935.ibm.com/services/multimedia/GBE03620USEN.pdf (accessed on 10 October 2022).
- Ericsson Mobility Report November 2021. Available online: https://www.ericsson.com/en/reports-and-papers/mobility-report/reports/ (accessed on 10 October 2022).
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Abdmeziem, R.; Tandjaoui, D. Internet of Things: Concept, Building blocks, Applications and Challenges. arXiv 2014, arXiv:1401.6877. [Google Scholar]
- Xu, W.; Trappe, W.; Zhang, Y.; Wood, T. The feasibility of launching and detecting jamming attacks in wireless networks. In Proceedings of the International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc), Urbana-Champaign, IL, USA, 25–28 May 2005; pp. 46–57. [Google Scholar] [CrossRef]
- Xu, W.; Wood, T.; Trappe, W.; Zhang, Y. Channel surfing and spatial retreats: Defenses against wireless denial of service. In Proceedings of the 2004 ACM Workshop on Wireless Security, WiSe, Philadelphia, PA, USA, 1 October 2004; pp. 80–89. [Google Scholar]
- Hong, C.-C.J.K.Y.-W.P.; Lan, P.-C. WLAN Security WP|MY Notes BLOG. Available online: https://glw168.wordpress.com/tag/wlan-security-wp/ (accessed on 25 November 2019).
- Pecorella, T.; Brilli, L.; Mucchi, L. The Role of Physical Layer Security in IoT: A Novel Perspective. Information 2016, 7, 49. [Google Scholar] [CrossRef]
- Xiao, L.; Greenstein, L.J.; Mandayam, N.B.; Trappe, W. Channel-Based Detection of Sybil Attacks in Wireless Networks. IEEE Trans. Inf. Forensics Secur. 2009, 4, 492–503. [Google Scholar] [CrossRef]
- Chen, Y.; Trappe, W.; Martin, R.P. Detecting and Localizing Wireless Spoofing Attacks. In Proceedings of the 2007 4th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, SECON, San Diego, CA, USA, 21 June 2007; pp. 193–202. [Google Scholar] [CrossRef]
- Top IoT Vulnerabilities—OWASP. Available online: https://www.owasp.org/index.php/Top_IoT_Vulnerabilities (accessed on 25 November 2019).
- Bhattasali, T.; Chaki, R. A Survey of Recent Intrusion Detection Systems for Wireless Sensor Network. In Communications in Computer and Information Science, Proceedings of the 4th International Conference, CNSA 2011, Chennai, India, 15–17 July 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 268–280. [Google Scholar] [CrossRef]
- Kim, H. Protection against Packet Fragmentation Attacks at 6LoWPAN Adaptation Layer. In Proceedings of the 2008 International Conference on Convergence and Hybrid Information Technology, ICHIT 2008, Daejeon, Korea, 28–29 August 2008; pp. 796–801. [Google Scholar] [CrossRef]
- Hummen, R.; Hiller, J.; Wirtz, H.; Henze, M.; Shafagh, H.; Wehrle, K. 6LoWPAN fragmentation attacks and mitigation mechanisms. In Proceedings of the 6th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Budapest, Hungary, 17–19 April 2013; pp. 55–66. [Google Scholar] [CrossRef]
- Riaz, R.; Kim, K.-H.; Ahmed, H.F. Security analysis survey and framework design for IP connected LoWPANs. In Proceedings of the International Symposium on Autonomous Decentralized Systems, ISADS 2009, Athens, Greece, 23–25 March 2009; pp. 1–6. [Google Scholar] [CrossRef]
- Dvir, A.; Holczer, T.; Buttyan, L. VeRA—Version Number and Rank Authentication in RPL. In Proceedings of the 2011 IEEE Eighth International Conference on Mobile Ad-Hoc and Sensor Systems, Valencia, Spain, 17–21 October 2011; IEEE: New York, NY, USA, 2011; pp. 709–714. [Google Scholar] [CrossRef]
- Weekly, K.; Pister, K. Evaluating sinkhole defense techniques in RPL networks. In Proceedings of the International Conference on Network Protocols, ICNP, Austin, TX, USA, 30 October–2 November 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Ahmed, F.; Ko, Y.-B. Mitigation of black hole attacks in Routing Protocol for Low Power and Lossy Networks. Secur. Commun. Netw. 2016, 9, 5143–5154. [Google Scholar] [CrossRef]
- Pirzada, A.; McDonald, C. Circumventing sinkholes and wormholes in wireless sensor networks. In Proceedings of the Conference on Wireless Ad Hoc Networks, Cancun, Mexico, 6–8 October 2005. [Google Scholar]
- Wazid, M.; Das, A.K.; Kumari, S.; Khan, M.K. Design of sinkhole node detection mechanism for hierarchical wireless sensor networks. Secur. Commun. Netw. 2016, 9, 4596–4614. [Google Scholar] [CrossRef]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil Attacks and Their Defenses in the Internet of Things. IEEE Internet Things J. 2014, 1, 372–383. [Google Scholar] [CrossRef]
- Wang, G.; Mohanlal, M.; Wilson, C.; Wang, X.; Metzger, M.; Zheng, H.; Zhao, B.Y. Social Turing Tests: Crowdsourcing Sybil Detection. arXiv 2012, arXiv:1205.3856. [Google Scholar]
- Granjal, J.; Monteiro, E.; Silva, J.S. Network-layer security for the Internet of Things using TinyOS and BLIP. Int. J. Commun. Syst. 2012, 27, 1938–1963. [Google Scholar] [CrossRef]
- Raza, S.; Duquennoy, S.; Chung, T.; Yazar, D.; Voigt, T.; Roedig, U. Securing communication in 6LoWPAN with compressed IPsec. In Proceedings of the 2011 International Conference on Distributed Computing in Sensor Systems and Workshops, DCOSS’11, Barcelona, Spain, 27–29 June 2011; pp. 1–8. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Enabling Network-Layer Security on IPv6 Wireless Sensor Networks. In Proceedings of the GLOBECOM—IEEE Global Telecommunications Conference, Miami, FL, USA, 6–10 December 2010; pp. 1–6. [Google Scholar] [CrossRef]
- Brachmann, M.; Garcia-Morchon, O.; Kirsche, M. Security for Practical CoAP Applications: Issues and Solution Approaches. In Proceedings of the 10th GI/ITG KuVS Fachgespraech Sensornetze (FGSN11), Paderborn, Germany, 2011; pp. 69–72. [Google Scholar]
- Granjal, J.; Monteiro, E.; Silva, J.S. End-to-end transport-layer security for Internet-integrated sensing applications with mutual and delegated ECC public-key authentication. In Proceedings of the IFIP Networking Conference, IFIP Networking 2013, Brooklyn, NY, USA, 22–24 May 2013. [Google Scholar]
- Raza, S.; Voigt, T.; Jutvik, V. Lightweight IKEv2: A Key Management Solution for both the Compressed IPsec and the IEEE 802.15.4 Security SPI NH ET ID 1 0 1 1. In Proceedings of the IETF Workshop on Smart Object Security, Citeseer, Paris, France, 23 March 2012. [Google Scholar]
- Peretti, G.; Lakkundi, V.; Zorzi, M. BlinkToSCoAP: An end-to-end security framework for the Internet of Things. In Proceedings of the 2015 7th International Conference on Communication Systems and Networks, COMSNETS 2015, Piscataway, NJ, USA, 6–10 January 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Park, N.; Kang, N. Mutual Authentication Scheme in Secure Internet of Things Technology for Comfortable Lifestyle. Sensors 2015, 16, 20. [Google Scholar] [CrossRef]
- Alkhalil, A.; Ramadan, R.A. IoT Data Provenance Implementation Challenges. Procedia Comput. Sci. 2017, 109, 1134–1139. [Google Scholar] [CrossRef]
- Miller, D. INTERNET OF THINGS Blockchain and the Internet of Things in the Industrial Sector. Available online: www.computer.org/itpro (accessed on 10 October 2022).
- Gao, W.; Hatcher, W.G.; Yu, W. A survey of blockchain: Techniques applications and challenges. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018. [Google Scholar]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X.S. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2017, 20, 601–628. [Google Scholar] [CrossRef]
- Alrowaily, M.; Lu, Z. Secure Edge Computing in IoT Systems: Review and Case Studies. In Proceedings of the 2018 IEEE/ACM Symposium on Edge Computing (SEC), Seattle, WA, USA, 25–27 October 2018; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2018; pp. 440–444. [Google Scholar]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Tas, Y.; Baeth, M.J.; Aktas, M.S. An Approach to Standalone Provenance Systems for Big Social Provenance Data. In Proceedings of the 2016 12th International Conference on Semantics, Knowledge and Grids, SKG 2016, Beijing, China, 15–17 August 2016; pp. 9–16. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Wang, J.-B.; de Cola, T.; Wang, J. Joint Beamforming and Power Allocation for Satellite-Terrestrial Integrated Networks with Non-Orthogonal Multiple Access. IEEE J. Sel. Top. Signal Process. 2019, 13, 657–670. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-based secure energy efficient beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022, 1–4. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; de Cola, T.; Wang, J.-B.; Zhu, W.-P.; Cheng, J. Supporting IoT With Rate-Splitting Multiple Access in Satellite and Aerial-Integrated Networks. IEEE Internet Things J. 2021, 8, 11123–11134. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).