GNSS and LNSS Positioning of Unmanned Transport Systems: The Brief Classification of Terrorist Attacks on USVs and UUVs
Abstract
:1. Introduction
“As GPS further penetrates into the civil infrastructure, it becomes a tempting target”.
“Information on the capabilities, limitations, and operational procedures [of spoofers] would help identify vulnerable areas and detection strategies”[1].
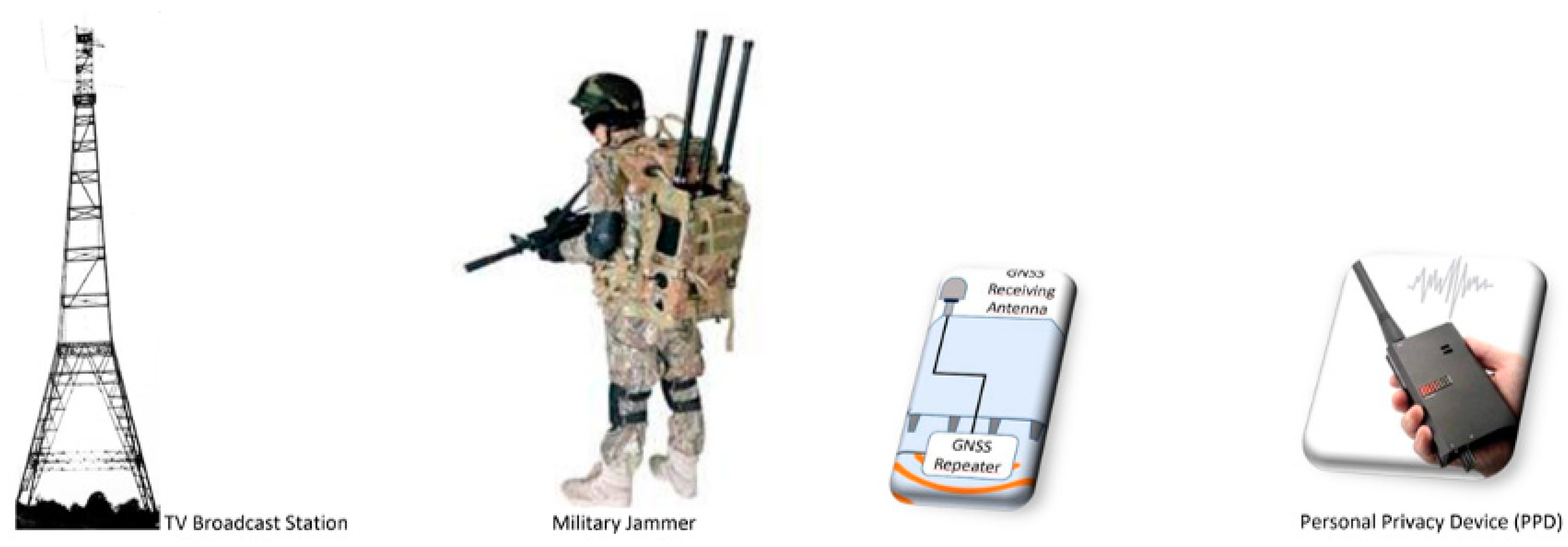
2. The Signal Energy Decreases with Distance from Satellites and Major GNSS Interference Sources
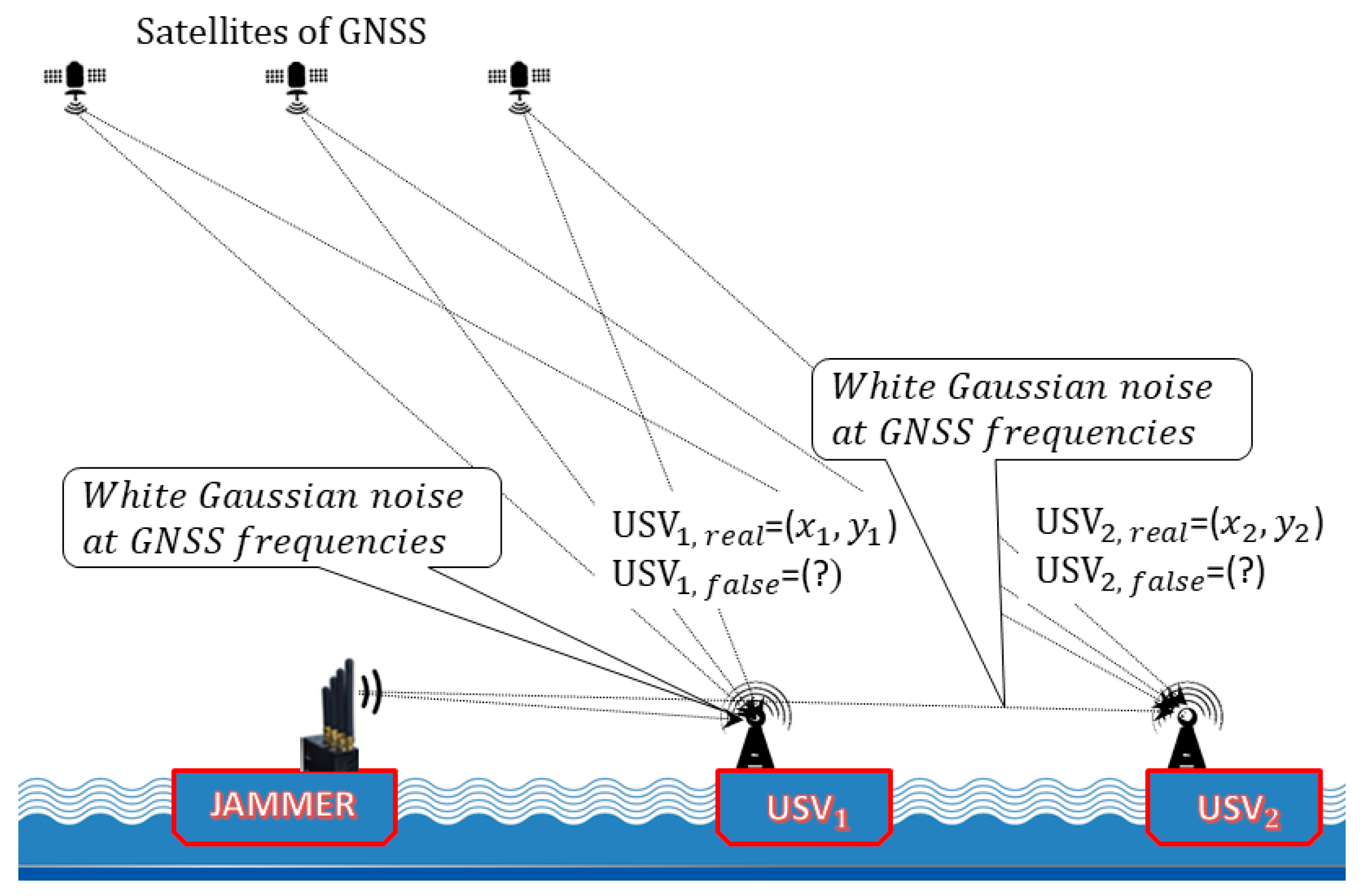
3. The GNSS Jamming as a Terrorist Attack on USVs
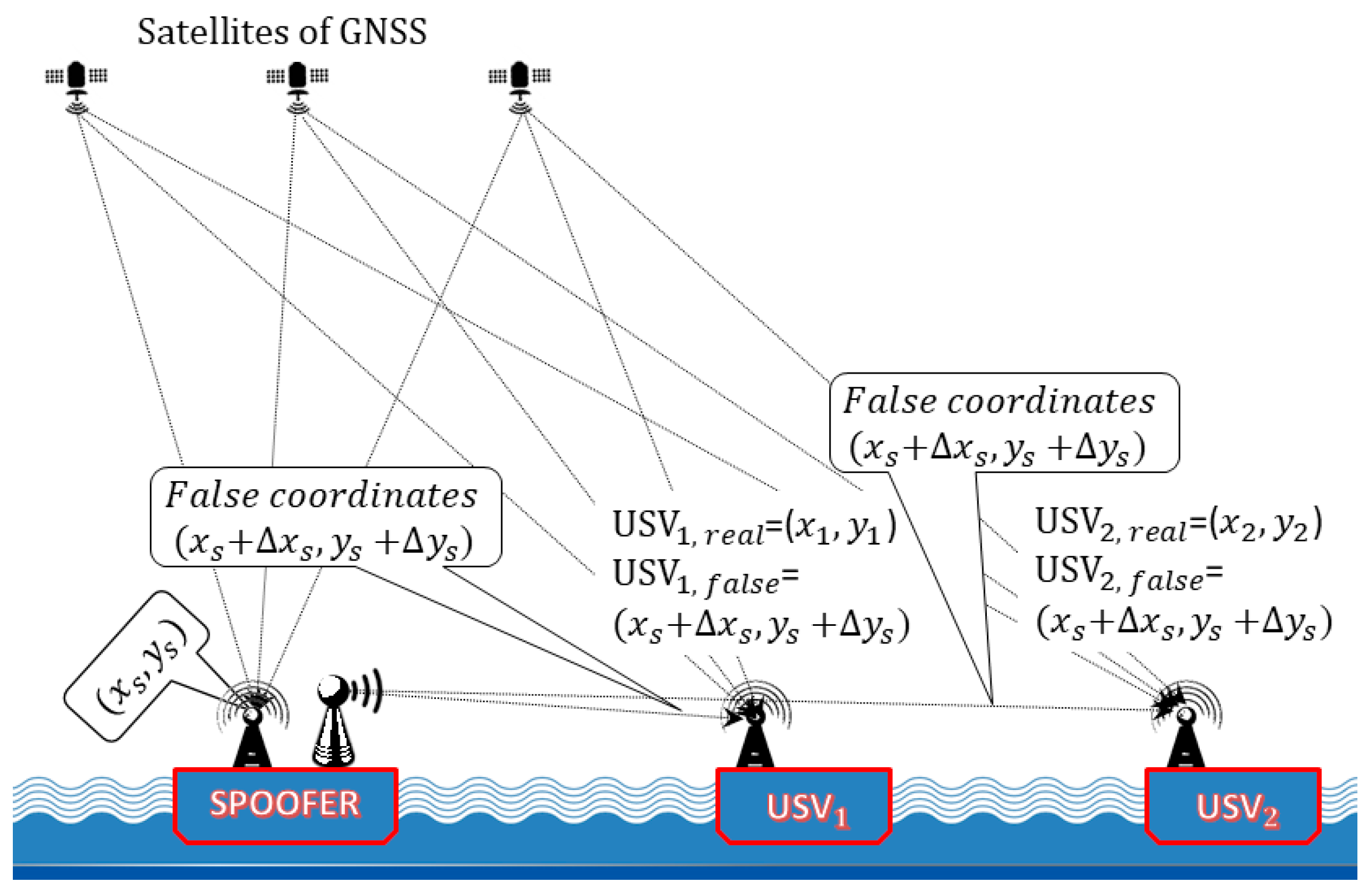
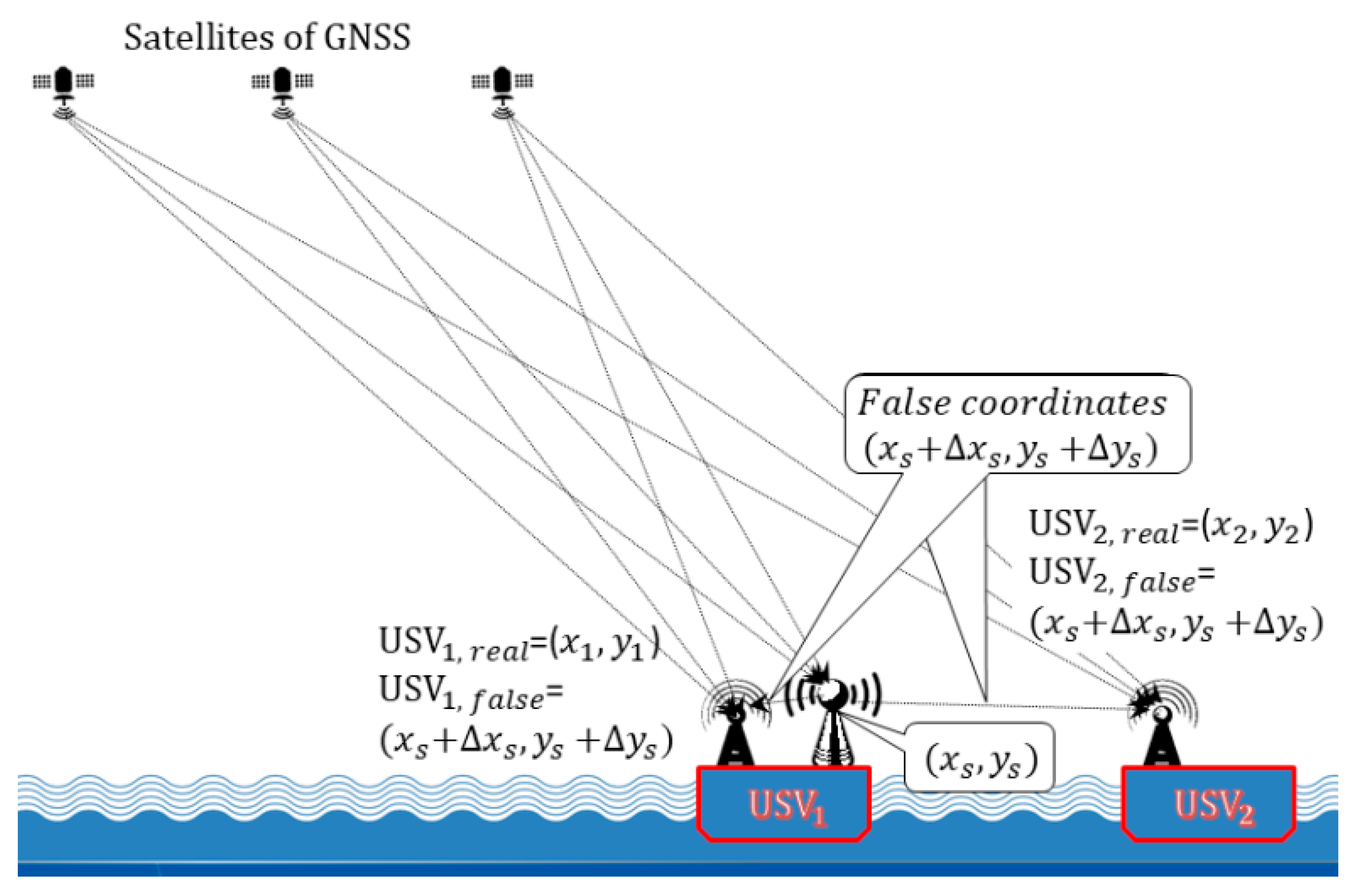
4. GNSS Spoofing as a Terrorist Attack on USVs
5. The Modelling of GNSS Spoofing
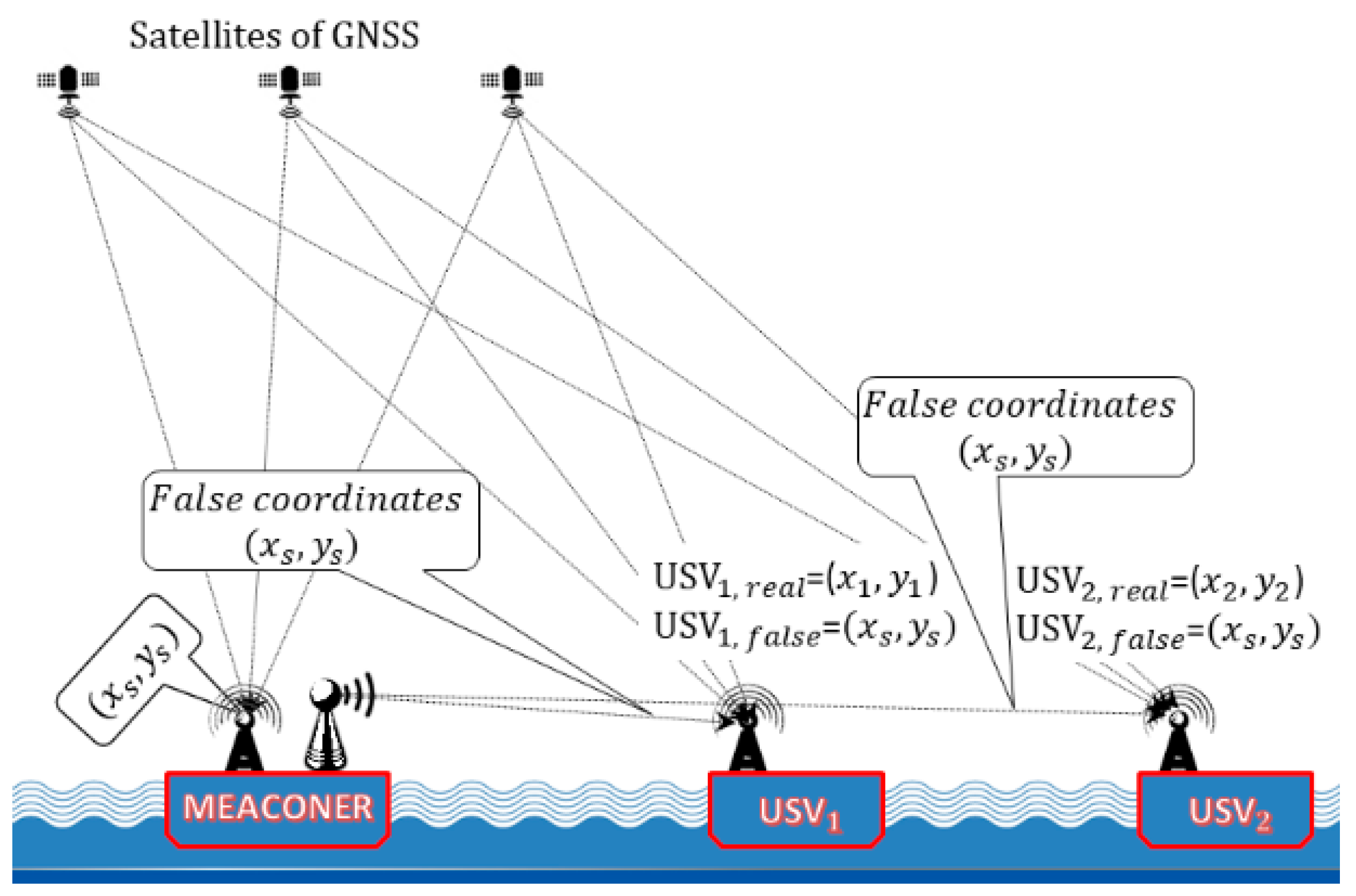
6. The GNSS Meaconing as a Terrorist Attack on USVs
7. The GNSS Self-Spoofing Attack on USVs
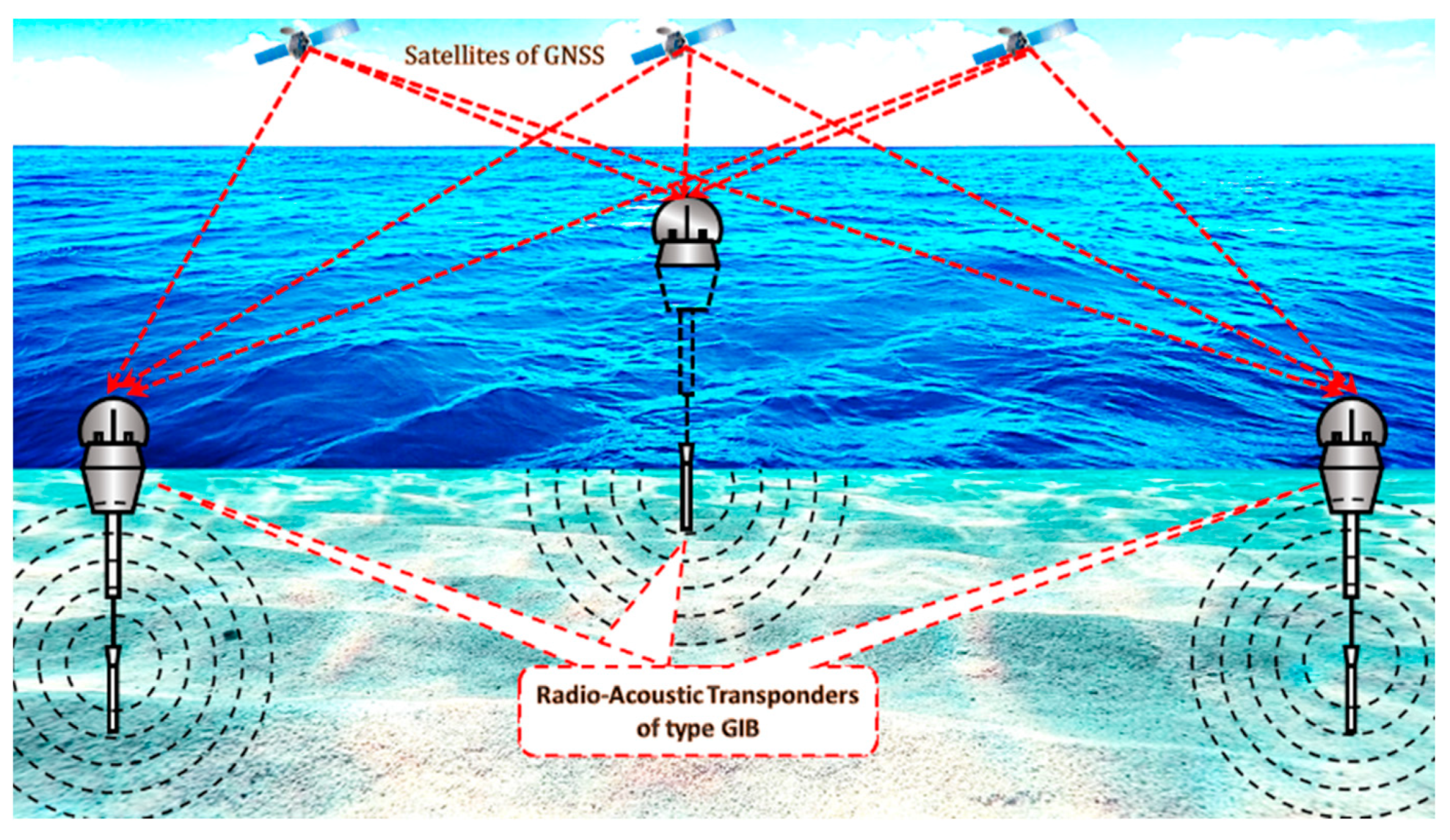
8. The Local Navigation Satellite Systems (LNSS)
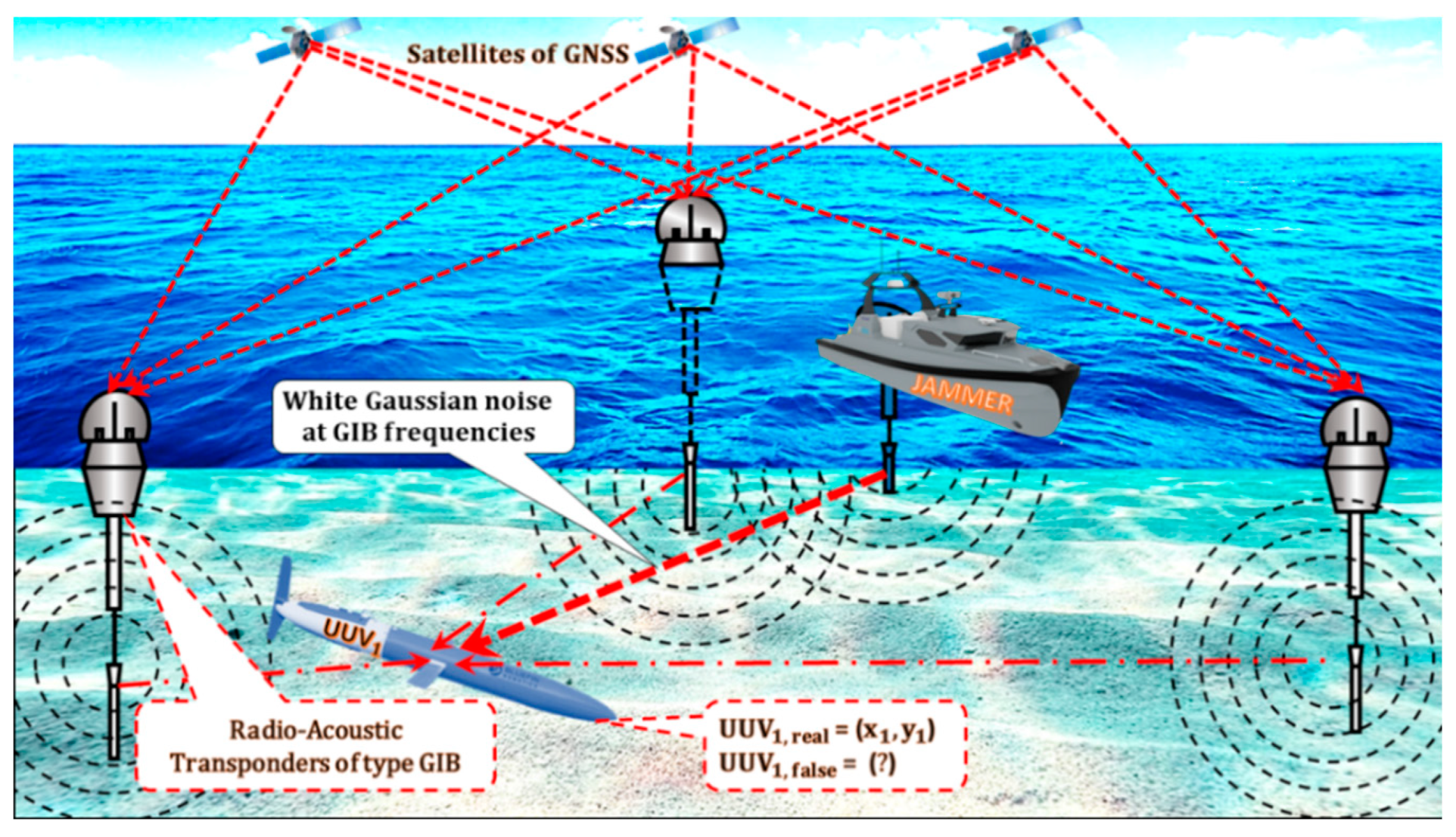
9. The LNSS Jamming as a Terrorist Attack on UUVs
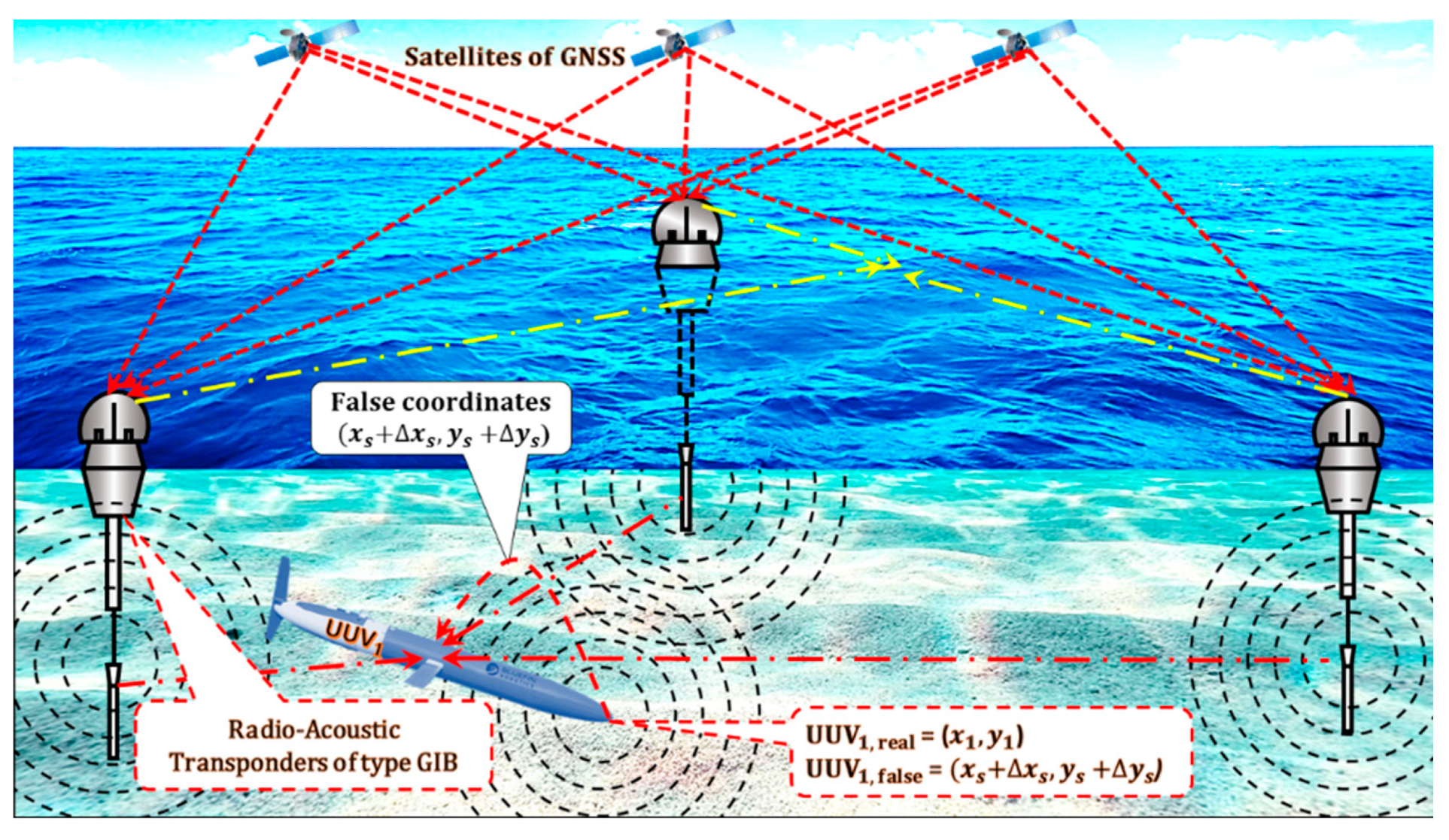
10. LNSS Spoofing as a Terrorist Attack on UUVs
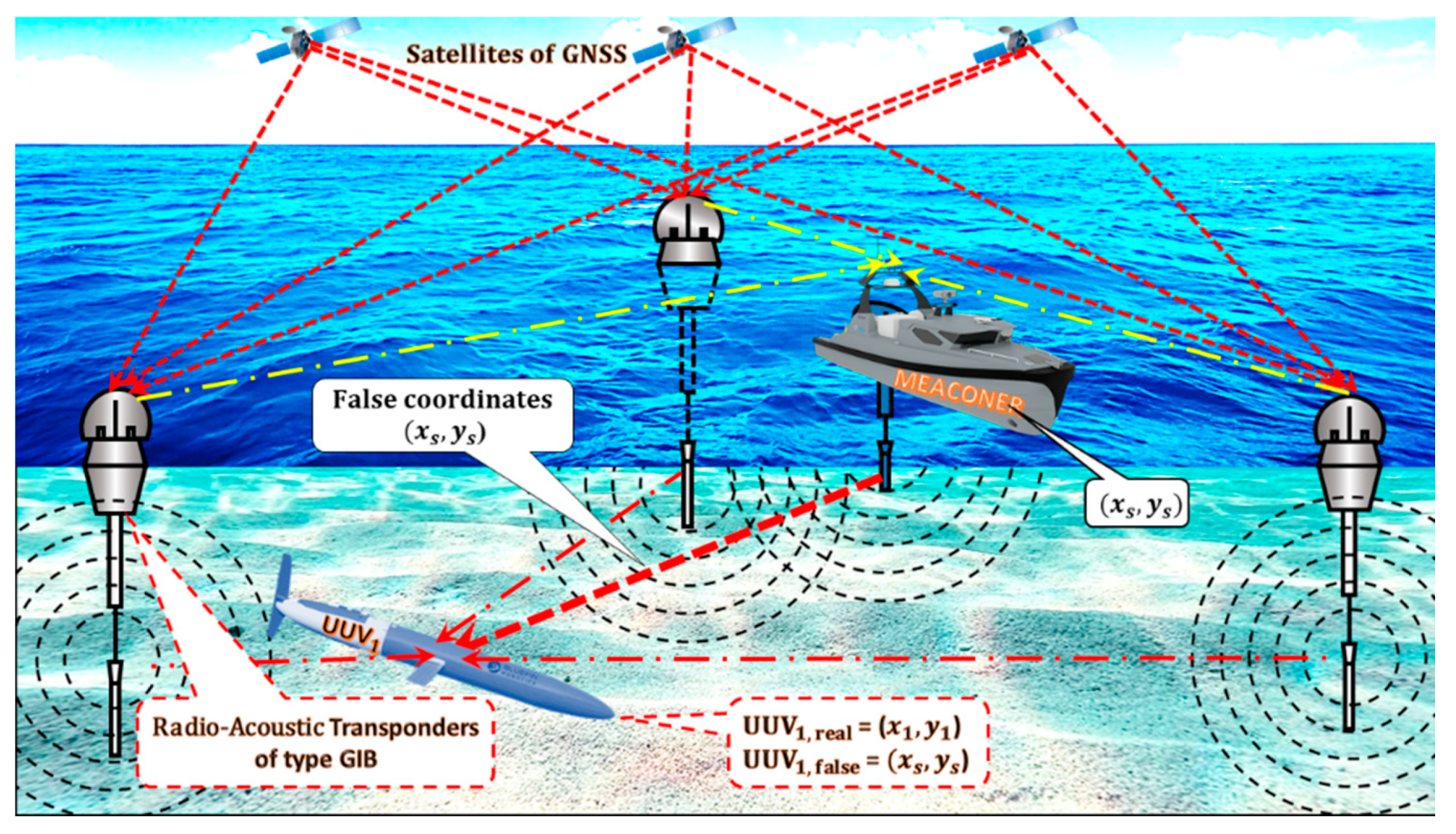
11. LNSS Meaconing as a Terrorist Attack on UUVs
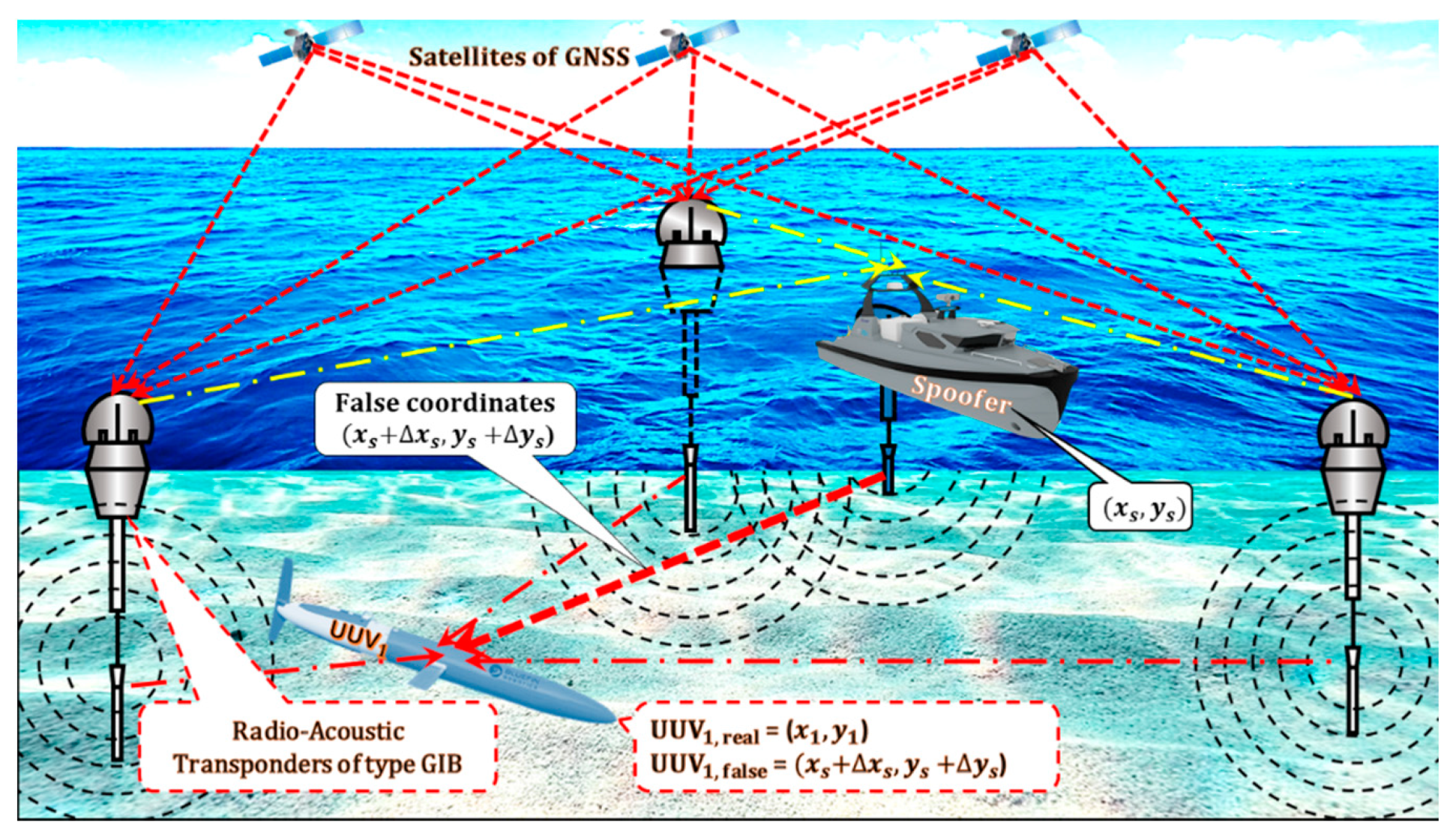
12. The LNSS Self-Spoofing Attack on UUVs
13. The Brief Classification of Terrorist Attacks on USVs and UUVs
14. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- 2001 DOT Volpe Report. Available online: https://www.navcen.uscg.gov/?pageName=pressRelease (accessed on 20 December 2020).
- GNSS Interference, Safety First. 29 September 2019. Available online: https://safetyfirst.airbus.com/app/themes/mh_newsdesk/pdf.php?p=27033 (accessed on 20 December 2020).
- Heue, R. GNSS Jamming and Spoofing: Hazard or Hype? Available online: https://space-of-innovation.com/gnss-jamming-and-spoofing-hazard-or-hype/ (accessed on 20 December 2020).
- Axell, E. GNSS Interference Detection. Available online: https://www.foi.se/rest-api/report/FOI-R--3839--SE (accessed on 20 December 2020).
- Joo, I.; Sin, C. Design of GNSS jamming propagation simulator using ITU-R P.1546 propagation model. In Proceedings of the 15th International Conference on Control, Automation and Systems (ICCAS), Busan, Korea, 13–16 October 2015; pp. 1359–1362. [Google Scholar]
- Axell, E.; Eklöf, F.M.; Johansson, P.; Alexandersson, M.; Akos, D.M. Jamming Detection in GNSS Receivers: Performance Evaluation of Field Trials. J. Inst. Navig. 2015, 62, 73–82. [Google Scholar] [CrossRef]
- Anti-Positioning GPS Signal Blocker Car Jammer. Available online: https://pl.gearbest.com/car-gps-tracker/pp_009466526749.html (accessed on 20 December 2020).
- Lockheed Martin RQ-170 Sentinel. Available online: https://pl.wikipedia.org/wiki/Lockheed_Martin_RQ-170_Sentinel (accessed on 20 December 2020).
- Method of the Operation of a Long Baseline (LBL) Acoustic Positioning System. Available online: https://en.wikipedia.org/wiki/Long_baseline_acoustic_positioning_system (accessed on 20 December 2020).
- Schmidt, D.; Radke, K.; Camtepe, S.A.; Foo, E.; Ren, M. A Survey and Analysis of the GNSS Spoofing Threat and Countermeasures. ACM Comput. Surv. 2016, 48, 1–31. [Google Scholar] [CrossRef]
- Huang, J.; Presti, L.L.; Motella, B.; Pini, M. GNSS spoofing detection: Theoretical analysis and performance of the Ratio Test metric in open sky. ICT Express 2016, 2, 37–40. [Google Scholar] [CrossRef] [Green Version]
- Dobryakova, L.; Lemieszewski, Ł.; Ochin, E. Design and Analysis of Spoofing Detection Algorithms for GNSS Signals. Sci. J. Marit. Univ. Szczec. 2014, 40, 47–52. [Google Scholar]
- Ochin, E. Detection of Spoofing using Differential GNSS. Sci. J. Marit. Univ. Szczec. 2017, 50, 59–67. [Google Scholar]
- Ochin, E. GNSS and DGNSS Spoofing Detection. Ural. Radio Eng. J. 2017, 1, 55–79. [Google Scholar] [CrossRef] [Green Version]
- Dobryakova, L.A.; Lemieszewski, Ł.S.; Ochin, E.F. GNSS Spoofing Detection Using Static or Rotating Single-Antenna of a Static or Moving Victim. IEEE Access 2018, 6, 79074–79081. [Google Scholar] [CrossRef]
- Simsky, M. How do We Ensure GNSS Security Against Spoofing? Available online: https://www.gpsworld.com/how-do-we-ensure-gnss-security-against-spoofing/ (accessed on 20 December 2020).
- Dobryakova, L.; Lemieszewski, Ł.; Ochin, E. The vulnerability of unmanned vehicles to terrorist attacks such as Global Navigation Satellite System spoofing. Sci. J. Marit. Univ. Szczec. 2016, 46, 181–188. [Google Scholar]
- Dobryakova, L.; Lemieszewski, Ł.; Ochin, E. Protecting vehicles vulnerable to terrorist attacks, such as GNSS jamming, by electromagnetic interference shielding of antenna. Sci. J. Marit. Univ. Szczec. 2017, 50, 77–83. [Google Scholar]
- Furno. Technology. Dead Reckoning (DR). Available online: https://www.furuno.com/en/gnss/technical/tec_dead (accessed on 20 December 2020).
- INS/GPS Inertial Navigation Systems. Accurate Positioning During GPS Outages. Available online: https://gladiatortechnologies.com/insgps/?gclid=CjwKCAiA8ov_BRAoEiwAOZogwUMZ0Dc18lhUer8ibICbC2rm7MSuCJcwWHgKsRgSTlxrAPyew-Y5rRoCdeIQAvD_BwE (accessed on 20 December 2020).
- Rodger, J.A. Toward reducing failure risk in an integrated vehicle health maintenance system: A fuzzy multi-sensor data fusion Kalman filter approach for IVHMS. Expert Syst. Appl. 2012, 39, 9821–9836. [Google Scholar] [CrossRef]
- Wang, H.; Dong, S. Adaptive Fusion Design Using Multiscale Unscented Kalman Filter Approach for Multisensor Data Fusion. Math. Probl. Eng. 2015, 2015, 854085. [Google Scholar] [CrossRef] [Green Version]
- Dobryakova, L.; Ochin, E. On the application of GNSS signal repeater as a spoofer. Sci. J. Marit. Univ. Szczec. 2014, 40, 53–57. [Google Scholar]
- Jones, M. Spoofing in the Black Sea: What Really Happened. GPS World. 2017. Available online: http://gpsworld.com/spoofing-in-the-black-sea-what-really-happened/ (accessed on 20 December 2020).
- Hans, J. Rund um den Kreml Spielt das GPS Verrückt. Süddeutsche Zeitung. 2016. Available online: https://www.sueddeutsche.de/digital/moskau-lost-in-navigation-1.3228389 (accessed on 20 December 2020).
- Lemieszewski, Ł. The Method of GNSS Spoofing Detection in Terms of Transport Safety. Ph.D. Thesis, Maritime Academy in Szczecin, Szczecin, Poland, 2016. [Google Scholar]
- Waterston, J. Positioning System for Deep Ocean Navigation (POSYDON). Available online: https://www.darpa.mil/program/positioning-system-for-deep-ocean-navigation (accessed on 20 December 2020).
- Osborn, K. DARPA Discovers “GPS-Like” Undersea Drone Connectivity. Available online: https://defensesystems.com/articles/2017/02/14/darpauuv.aspx (accessed on 20 December 2020).
- Ochin, E. The spoofing detection of Underwater Acoustic GNSS-like Positioning Systems. Sci. J. Marit. Univ. Szczec. 2019, 57, 38–46. [Google Scholar]
- Abramowski, T.; Bilewski, M.; Dobryakova, L.; Ochin, E.; Uriasz, J.; Zalewski, P. Safety of GNSS-Like Underwater Positioning Systems. Available online: https://www.preprints.org/manuscript/201909.0052/v1 (accessed on 20 December 2020).
- Abramowski, T.; Bilewski, M.; Dobryakova, L.; Ochin, E.; Uriasz, J.; Zalewski, P. Detection of Spoofing Used against the GNSS-Like Underwater Navigation Systems. Available online: https://www.preprints.org/manuscript/202001.0187/v1 (accessed on 20 December 2020).
- Dobryakova, L.; Lemieszewski, Ł.; Ochin, E. Cloud-based GNSS Navigation Spoofing Detection. Sci. J. Marit. Univ. Szczec. 2019, 57, 29–37. [Google Scholar]





Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lemieszewski, Ł.; Radomska-Zalas, A.; Perec, A.; Dobryakova, L.; Ochin, E. GNSS and LNSS Positioning of Unmanned Transport Systems: The Brief Classification of Terrorist Attacks on USVs and UUVs. Electronics 2021, 10, 401. https://doi.org/10.3390/electronics10040401
Lemieszewski Ł, Radomska-Zalas A, Perec A, Dobryakova L, Ochin E. GNSS and LNSS Positioning of Unmanned Transport Systems: The Brief Classification of Terrorist Attacks on USVs and UUVs. Electronics. 2021; 10(4):401. https://doi.org/10.3390/electronics10040401
Chicago/Turabian StyleLemieszewski, Łukasz, Aleksandra Radomska-Zalas, Andrzej Perec, Larisa Dobryakova, and Evgeny Ochin. 2021. "GNSS and LNSS Positioning of Unmanned Transport Systems: The Brief Classification of Terrorist Attacks on USVs and UUVs" Electronics 10, no. 4: 401. https://doi.org/10.3390/electronics10040401
APA StyleLemieszewski, Ł., Radomska-Zalas, A., Perec, A., Dobryakova, L., & Ochin, E. (2021). GNSS and LNSS Positioning of Unmanned Transport Systems: The Brief Classification of Terrorist Attacks on USVs and UUVs. Electronics, 10(4), 401. https://doi.org/10.3390/electronics10040401





