A Holistic Approach to Ransomware Classification: Leveraging Static and Dynamic Analysis with Visualization
Abstract
1. Introduction
Paper Contribution
- Comparative analysis of infection behaviors across various ransomware families.
- Utilization of data visualization methods for the identification of similar ransomware samples within extensive datasets.
- Employing a similarity matrix approach for the analysis of static and dynamic features in ransomware samples.
- Assessment of the merits and limitations associated with static and dynamic feature analysis.
- Comprehensive survey and comparative evaluation of varied ransomware detection approaches, alongside an in-depth exploration of the ransomware detection ecosystem.
- Development and proposal of an automated methodology for extracting diverse feature sets from ransomware samples.
2. Related Work
- Encrypting Ransomware: This category involves ransomware that encrypts files on the victim’s system, rendering them inaccessible until a ransom is paid.
- Locker Ransomware: Locker ransomware locks the victim out of their entire system, preventing access until a ransom is provided.
- Doxware or Leakware: This type threatens to release sensitive information unless a ransom is paid, often compromising privacy.
- Scareware: Scareware displays false warnings or claims of malware infections, extorting money for their removal.
- Mobile Ransomware: Designed for mobile devices, this category targets smartphones and tablets, encrypting data or locking the device.
- Ransomware-as-a-Service (RaaS): RaaS platforms allow cybercriminals to easily create and distribute ransomware, contributing to its proliferation.
- Targeted Ransomware: Some ransomware attacks are highly targeted, focusing on specific organizations or individuals, often with higher ransom demands.
- Cryptojacking: While it is not traditional ransomware, cryptojacking malware hijacks computer resources to mine cryptocurrencies, often without the victim’s consent.
2.1. Ransomware Detection Approaches and Techniques
2.1.1. Machine Learning
2.1.2. Honeypots
2.1.3. Statistics
3. Background
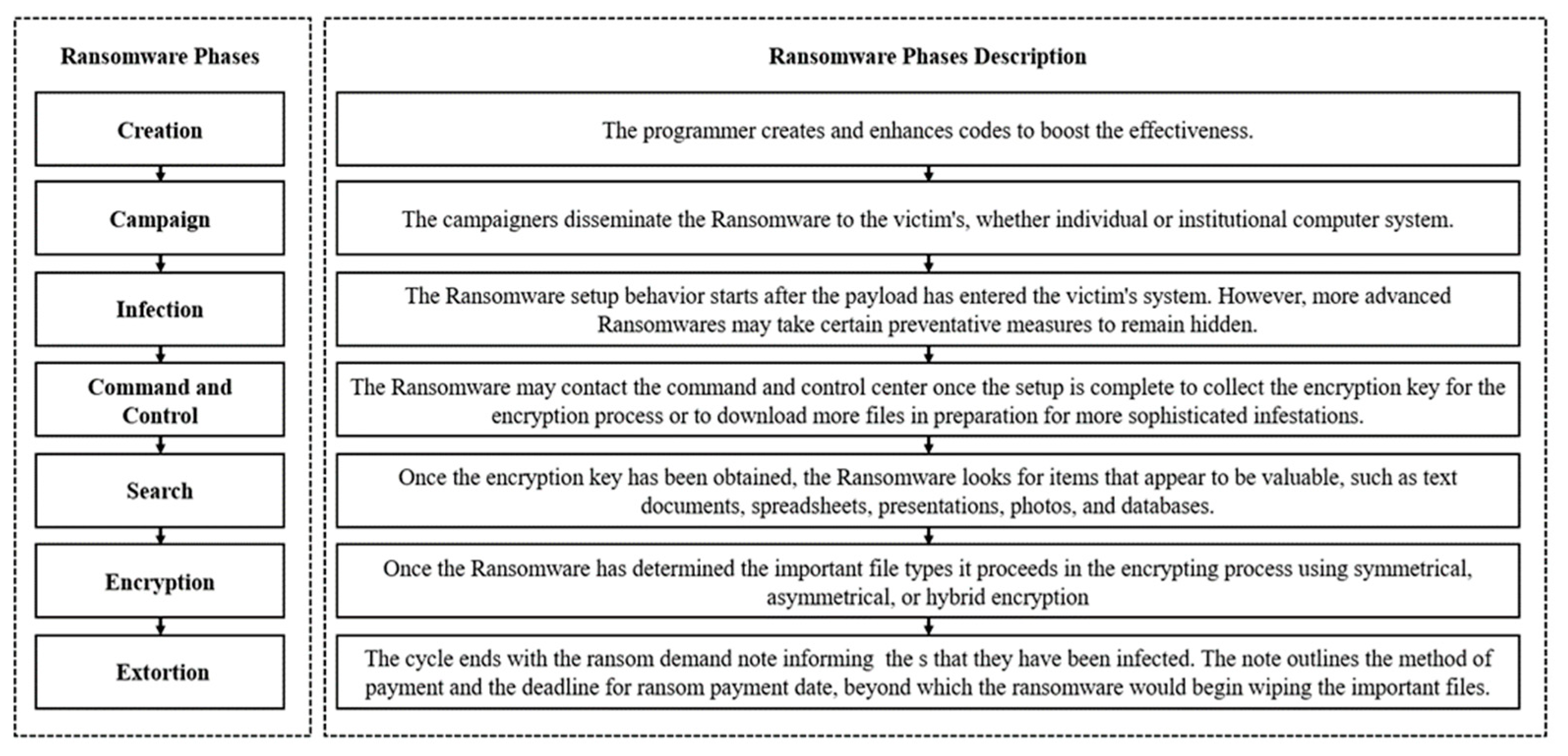
3.1. Ransomware Types and History
3.2. Ransowmare Classification with Visualization Techniques
3.3. Ransomware’s Features Tracking System
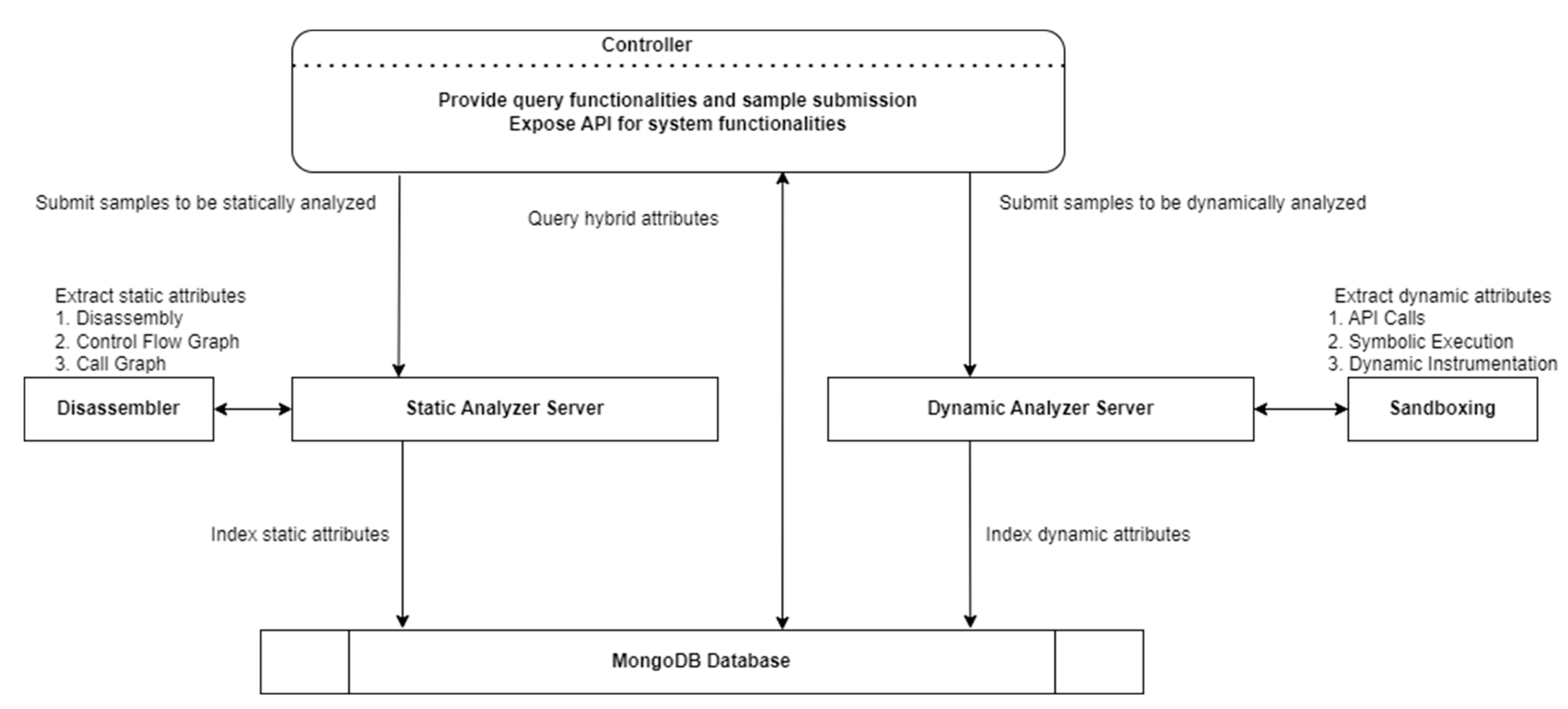
4. Experimental Work and Detection Scheme
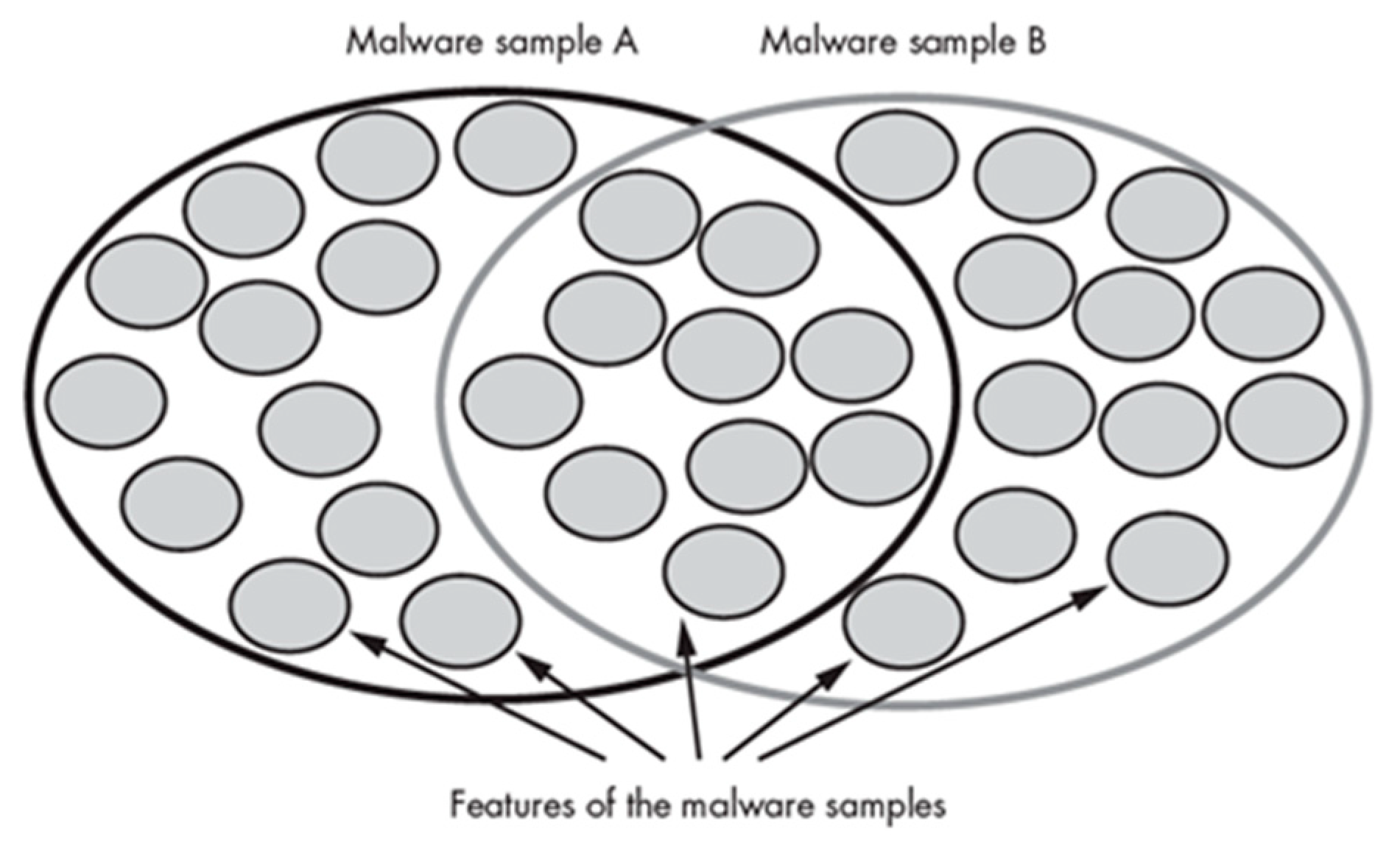
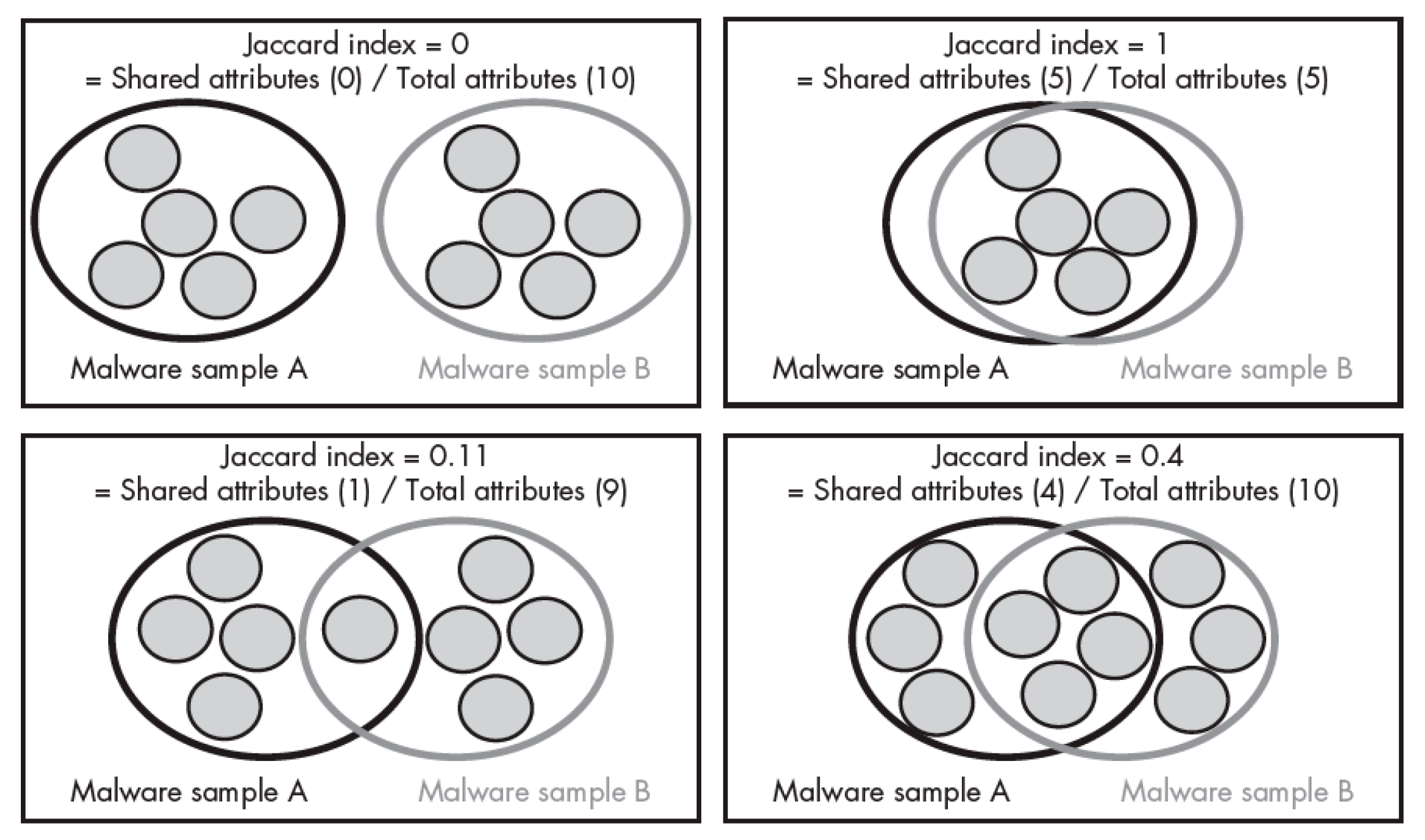
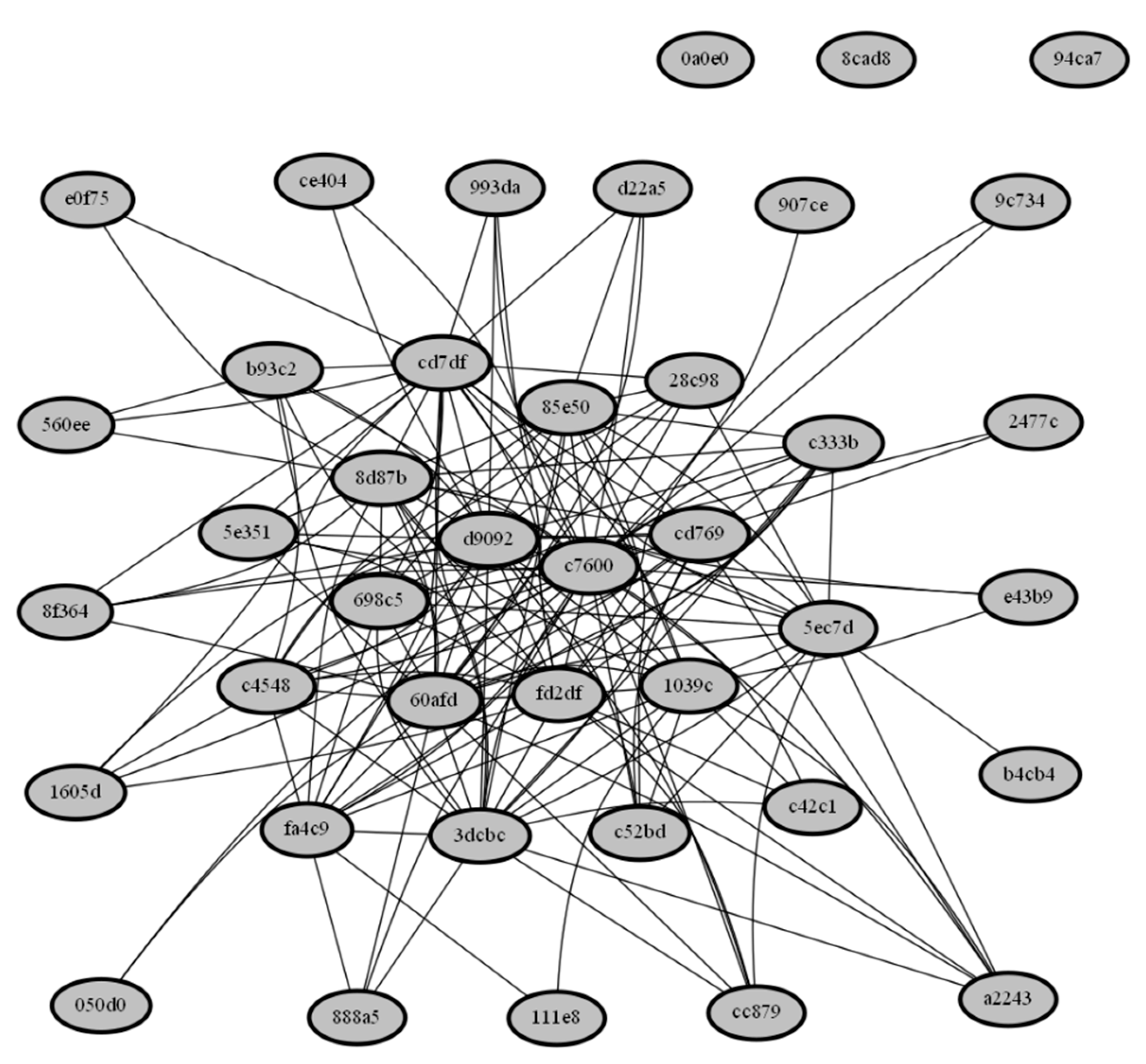
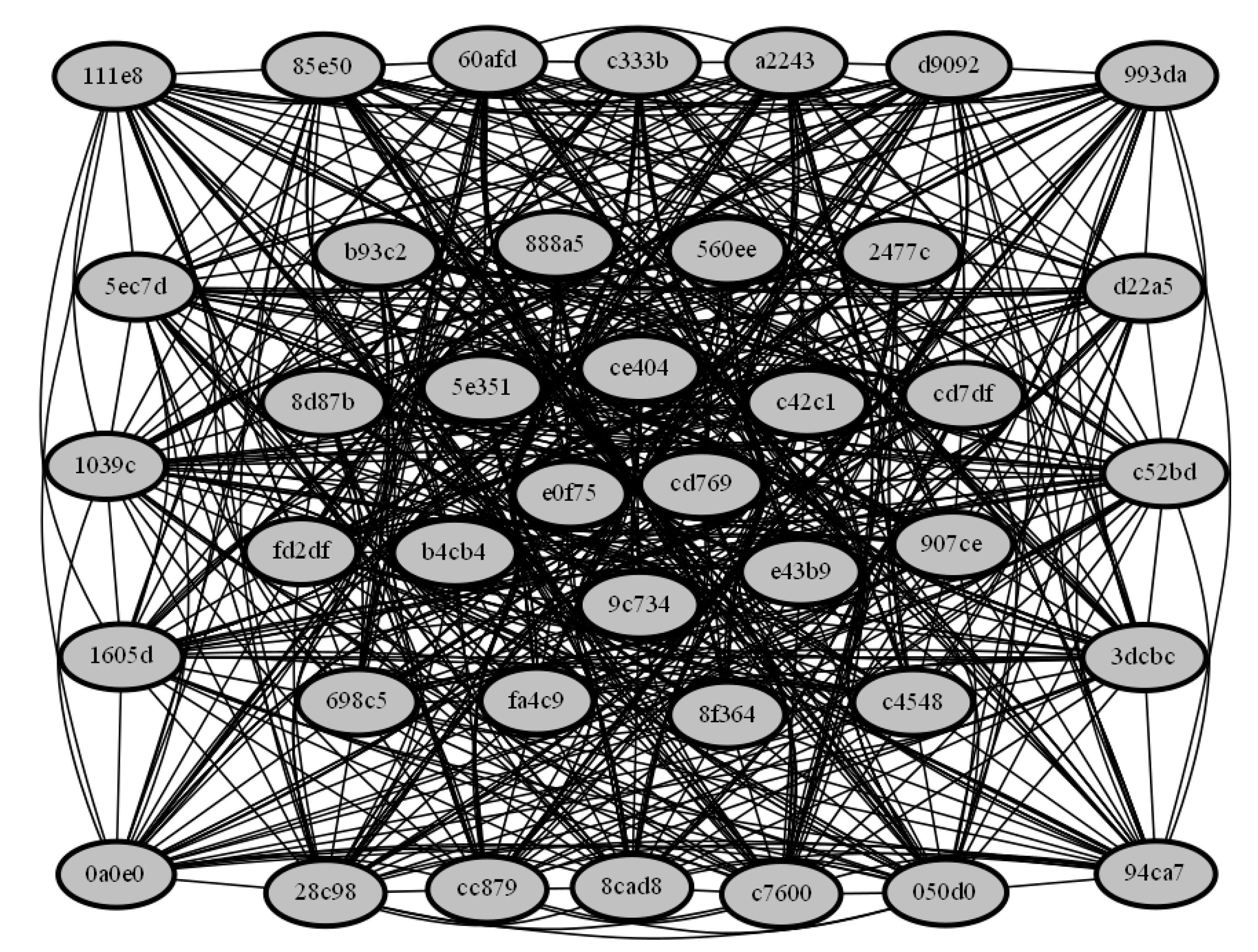
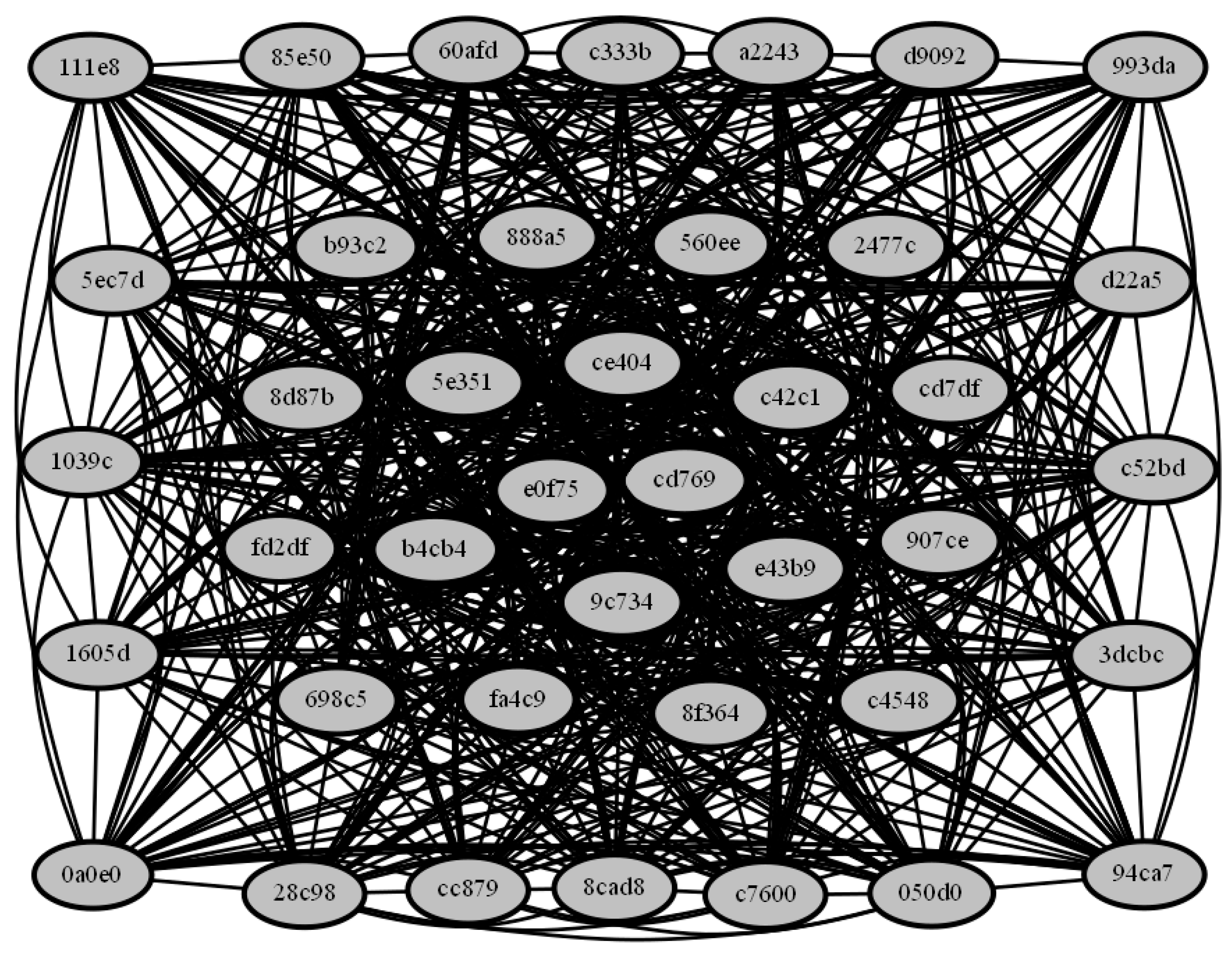
4.1. Visualization Techniques
- The cluster engine reported the most similar samples from the set.
- There is a need to validate the query-sample similarity with the matched samples.
- It is also important to reveal intelligence from the data and discover the patterns.
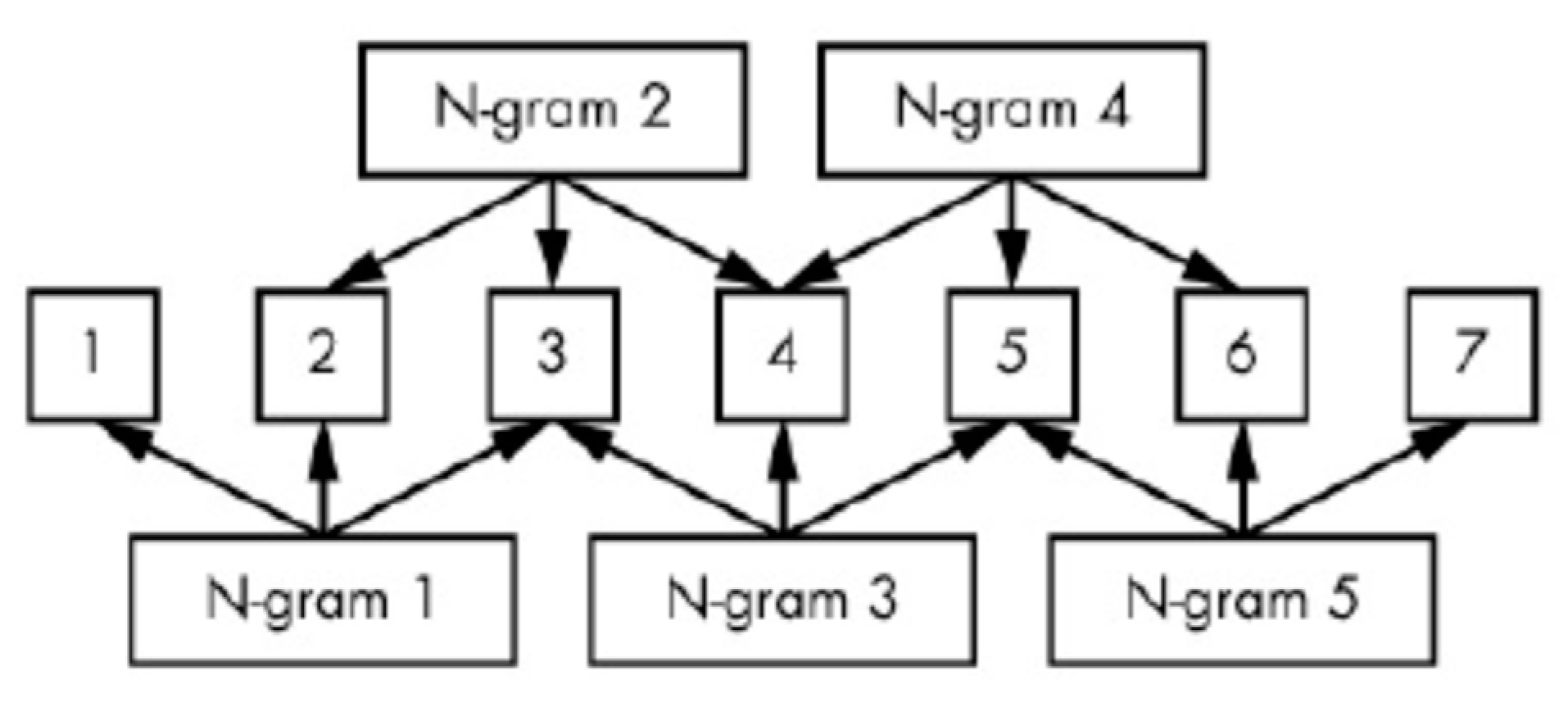
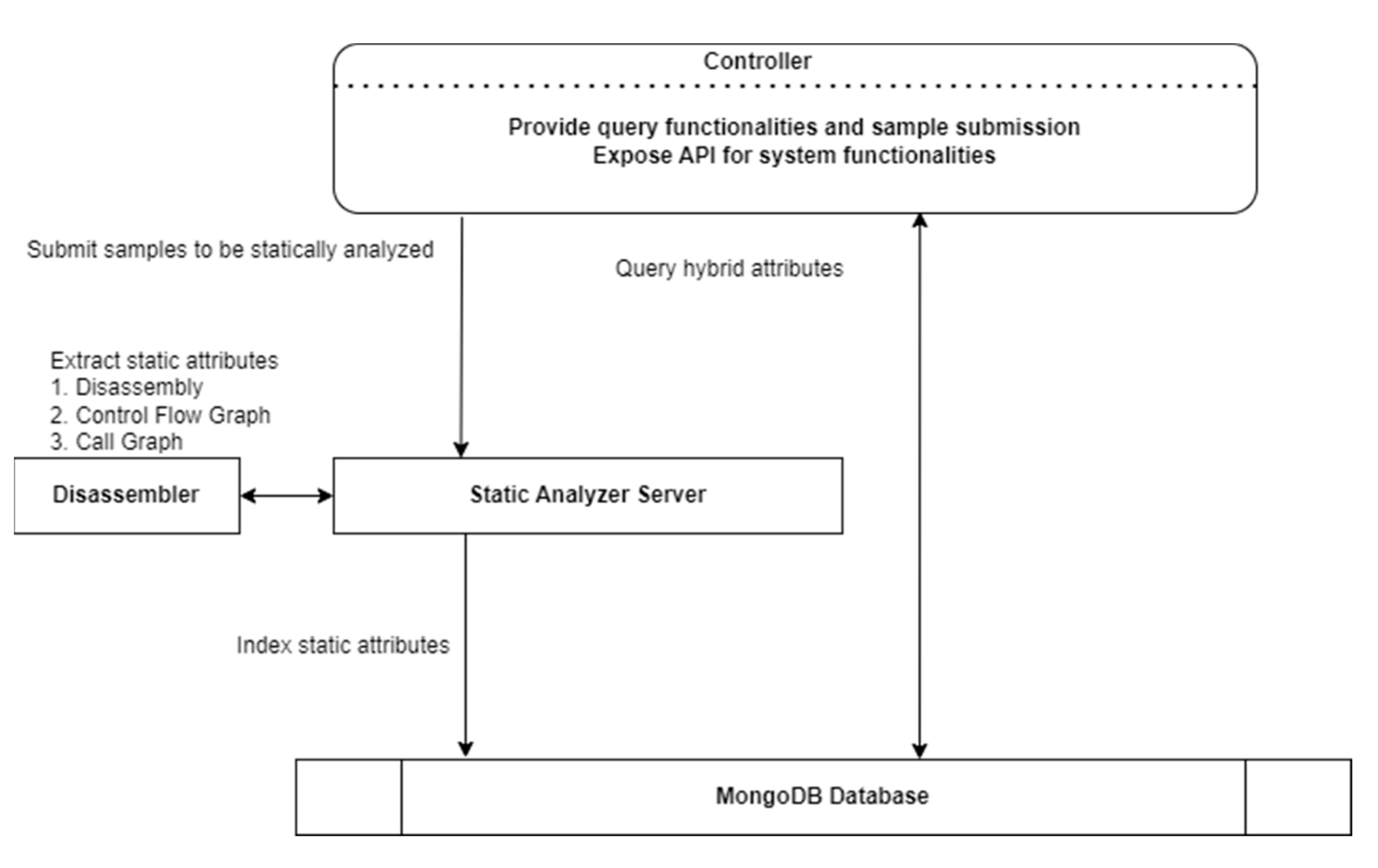
4.2. Static Ransomware Classification System
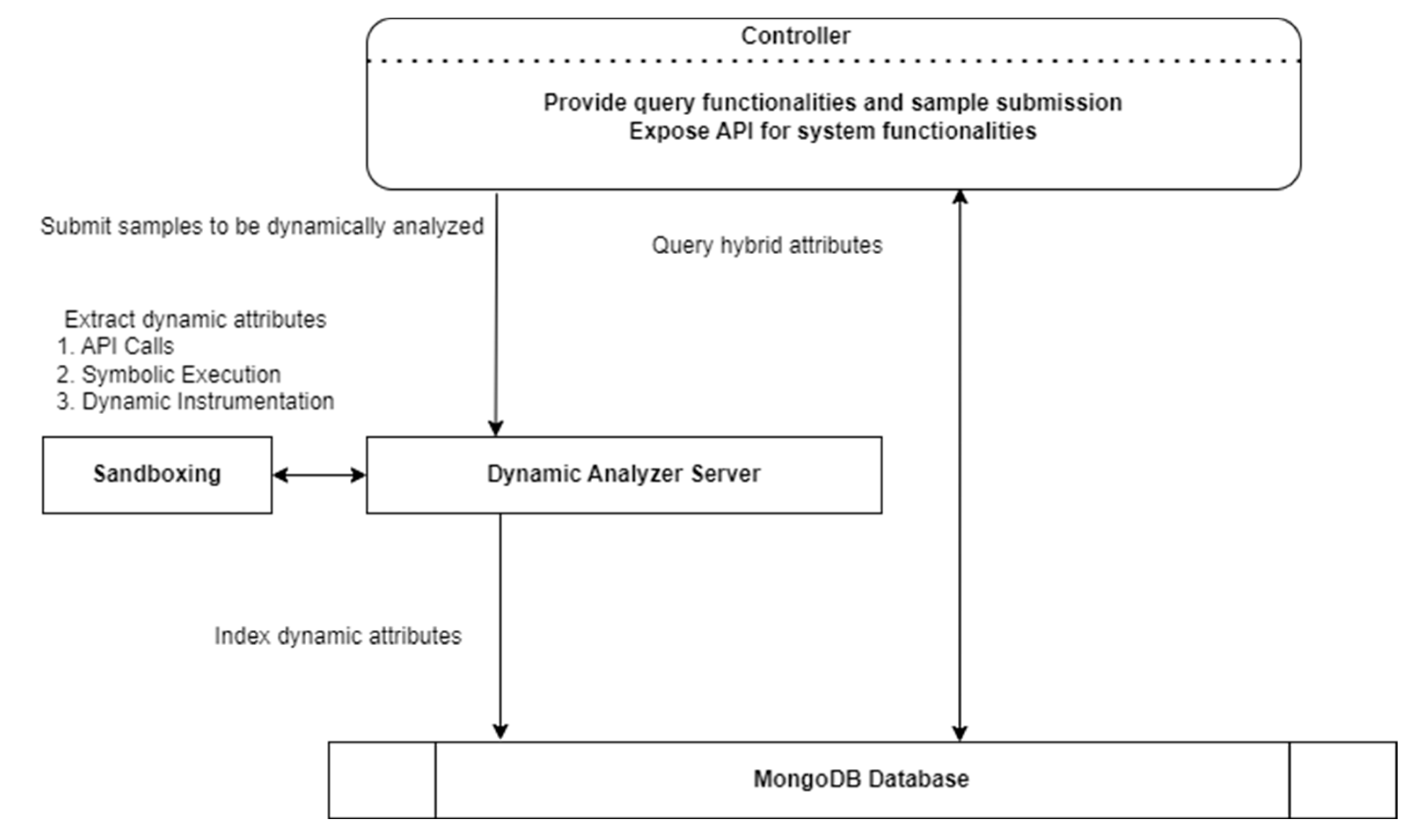
4.3. Dynamic Ransomware Classification System
4.4. Lab Setup
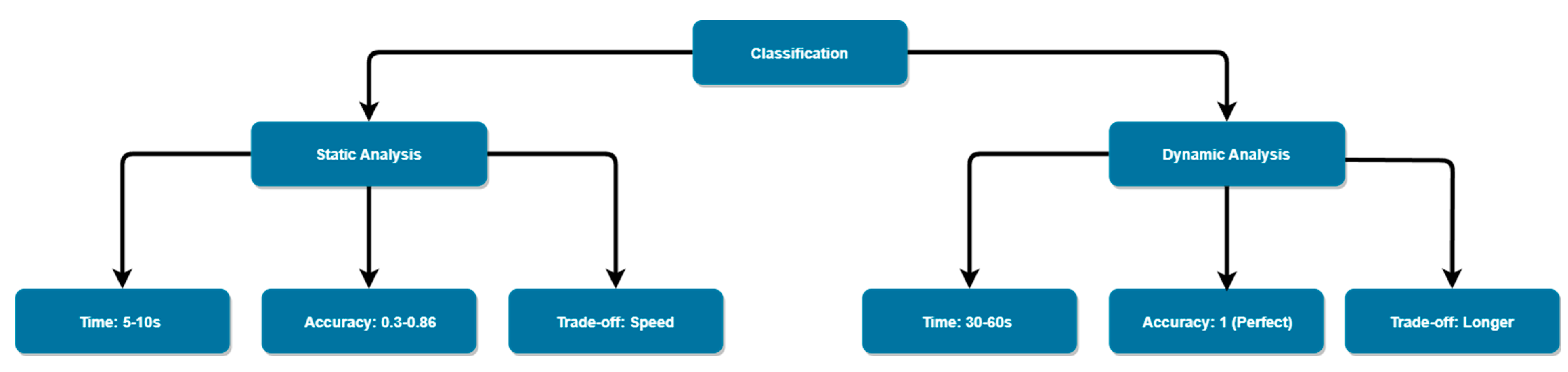
4.5. Time Complexity
4.5.1. Static vs. Dynamic Analysis
4.5.2. Hybrid Approach for Optimal Time Efficiency
- Static analysis time: approximately 5–10 s per sample.
- Dynamic analysis time: approximately 30–60 s per sample.
4.5.3. Continuous Database Augmentation
4.5.4. Proactive Sample Analysis
4.6. Results
- i.
- Strings-Based Similarity
- ii.
- Import Address Table–Based Similarity
- iii.
- API calls-Based Similarity
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gopinath, M.; Sethuraman, S.C. A comprehensive survey on deep learning based malware detection techniques. Comput. Sci. Rev. 2023, 47, 100529. [Google Scholar]
- Brown, A.; Gupta, M.; Abdelsalam, M. Automated machine learning for deep learning based malware detection. Comput. Secur. 2024, 137, 103582. [Google Scholar]
- Kok, S.; Abdullah, A.; Jhanjhi, N.; Supramaniam, M. Ransomware, threat and detection techniques: A review. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 136. [Google Scholar]
- Yadav, C.S.; Singh, J.; Yadav, A.; Pattanayak, H.S.; Kumar, R.; Khan, A.A.; Haq, M.A.; Alhussen, A.; Alharby, S. Malware analysis in iot & android systems with defensive mechanism. Electronics 2022, 11, 2354. [Google Scholar]
- Rey, V.; Sánchez, M.S.; Celdrán, A.H.; Bovet, G. Federated learning for malware detection in IoT devices. Comput. Netw. 2022, 204, 108693. [Google Scholar] [CrossRef]
- Johnson, S.; Gowtham, R.; Nair, A.R. Ensemble Model Ransomware Classification: A Static Analysis-based Approach. In Inventive Computation and Information Technologies: Proceedings of ICICIT 2021; Springer Nature: Singapore, 2022; pp. 153–167. [Google Scholar]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Ransomware threat success factors, taxonomy, and countermeasures: A survey and research directions. Comput. Secur. 2018, 74, 144–166. [Google Scholar] [CrossRef]
- Akhtar, Z. Malware detection and analysis: Challenges and research opportunities. arXiv 2021, arXiv:2101.08429. [Google Scholar]
- Tahir, R. A study on malware and malware detection techniques. Int. J. Educ. Manag. Eng. 2018, 8, 20. [Google Scholar] [CrossRef]
- Yamany, B.; Elsayed, M.S.; Jurcut, A.D.; Abdelbaki, N.; Azer, M.A. A New Scheme for Ransomware Classification and Clustering Using Static Features. Electronics 2022, 11, 3307. [Google Scholar] [CrossRef]
- Yamany, B.E.M.; Azer, M.A. SALAM Ransomware Behavior Analysis Challenges and Decryption. In Proceedings of the 2021 Tenth International Conference on Intelligent Computing and Information Systems (ICICIS), Cairo, Egypt, 5–7 December 2021; pp. 273–277. [Google Scholar]
- Fernando, D.W.; Komninos, N.; Chen, T. A study on the evolution of ransomware detection using machine learning and deep learning techniques. IoT 2020, 1, 551–604. [Google Scholar] [CrossRef]
- Khan, F.; Ncube, C.; Ramasamy, L.K.; Kadry, S.; Nam, Y. A digital DNA sequencing engine for ransomware detection using machine learning. IEEE Access 2020, 8, 119710–119719. [Google Scholar] [CrossRef]
- Liu, K.; Xu, S.; Xu, G.; Zhang, M.; Sun, D.; Liu, H. A review of android malware detection approaches based on machine learning. IEEE Access 2020, 8, 124579–124607. [Google Scholar] [CrossRef]
- Bae, S.I.; Lee, G.B.; Im, E.G. Ransomware detection using machine learning algorithms. Concurr. Comput. Pract. Exp. 2020, 32, e5422. [Google Scholar] [CrossRef]
- Chakkaravarthy, S.S.; Sangeetha, D.; Cruz, M.V.; Vaidehi, V.; Raman, B. Design of intrusion detection honeypot using social leopard algorithm to detect IoT ransomware attacks. IEEE Access 2020, 8, 169944–169956. [Google Scholar] [CrossRef]
- El-Kosairy, A.; Azer, M.A. Intrusion and ransomware detection system. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–7. [Google Scholar]
- Vishwakarma, R.; Jain, A.K. A honeypot with machine learning based detection framework for defending IoT based botnet DDoS attacks. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 1019–1024. [Google Scholar]
- Keong Ng, C.; Rajasegarar, S.; Pan, L.; Jiang, F.; Zhang, L.Y. VoterChoice: A ransomware detection honeypot with multiple voting framework. Concurr. Comput. Pract. Exp. 2020, 32, e5726. [Google Scholar] [CrossRef]
- Pont, J.; Arief, B.; Hernandez-Castro, J. Why current statistical approaches to ransomware detection fail. In Proceedings of the International Conference on Information Security, Bali, Indonesia, 16–18 December 2020; Springer International Publishing: Cham, Switzerland, 2020; pp. 199–216. [Google Scholar]
- Yewale, A.; Singh, M. Malware detection based on opcode frequency. In Proceedings of the 2016 International Conference on Advanced Communication Control and Computing Technologies (ICACCCT), Ramanathapuram, India, 25–27 May 2016; pp. 646–649. [Google Scholar]
- Rezaei, S.; Afraz, A.; Rezaei, F.; Shamani, M.R. Malware detection using opcodes statistical features. In Proceedings of the 2016 8th International Symposium On Telecommunications (IST), Tehran, Iran, 27–28 September 2016; pp. 151–155. [Google Scholar]
- Verma, V.; Muttoo, S.K.; Singh, V.B. Multiclass malware classification via first-and second-order texture statistics. Comput. Secur. 2020, 97, 101895. [Google Scholar] [CrossRef]
- Du, P.; Sun, Z.; Chen, H.; Cho, J.H.; Xu, S. Statistical estimation of malware detection metrics in the absence of ground truth. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2965–2980. [Google Scholar] [CrossRef]
- Bijitha, C.V.; Sukumaran, R.; Nath, H.V. A survey on ransomware detection techniques. In Secure Knowledge Management in Artificial Intelligence Era: 8th International Conference, SKM 2019, Goa, India, 21–22 December 2019; Proceedings 8; Springer: Singapore, 2020; pp. 55–68. [Google Scholar]
- Bello, A.; Maurushat, A. Synthesis of Evidence on Existing and Emerging Social Engineering Ransomware Attack Vectors. In Cybersecurity Issues, Challenges, and Solutions in the Business World; IGI Global: Hershey, PA, USA, 2023; pp. 234–254. [Google Scholar]
- Cai, C.X.; Zhao, R. Salience theory and cryptocurrency returns. J. Bank. Financ. 2024, 159, 107052. [Google Scholar] [CrossRef]
- Oz, H.; Aris, A.; Levi, A.; Uluagac, A.S. A survey on ransomware: Evolution, taxonomy, and defense solutions. ACM Comput. Surv. (CSUR) 2022, 54, 1–37. [Google Scholar] [CrossRef]
- Alzahrani, S.; Xiao, Y.; Sun, W. An analysis of conti ransomware leaked source codes. IEEE Access 2022, 10, 100178–100193. [Google Scholar] [CrossRef]
- Shu, R.; Xia, T.; Williams, L.; Menzies, T. Omni: Automated ensemble with unexpected models against adversarial evasion attack. Empir. Softw. Eng. 2022, 27, 26. [Google Scholar] [CrossRef]
- Alagappan, A.; Venkatachary, S.K.; Andrews, L.J.B. Augmenting Zero Trust Network Architecture to enhance security in virtual power plants. Energy Rep. 2022, 8, 1309–1320. [Google Scholar] [CrossRef]
- Whyte, C.; Mazanec, B. Understanding Cyber-Warfare: Politics, Policy and Strategy; Routledge: Oxford, UK, 2023. [Google Scholar]
- Berrueta, E.; Morato, D.; Magaña, E.; Izal, M. A survey on detection techniques for cryptographic ransomware. IEEE Access 2019, 7, 144925–144944. [Google Scholar] [CrossRef]
- Kara, I.; Aydos, M. The rise of ransomware: Forensic analysis for windows based ransomware attacks. Expert Syst. Appl. 2022, 190, 116198. [Google Scholar] [CrossRef]
- Gómez-Hernández, J.A.; Sánchez-Fernández, R.; García-Teodoro, P. Inhibiting crypto-ransomware on windows platforms through a honeyfile-based approach with R-Locker. IET Inf. Secur. 2022, 16, 64–74. [Google Scholar] [CrossRef]
- Almomani, I.; Alkhayer, A.; El-Shafai, W. A crypto-steganography approach for hiding ransomware within HEVC streams in android IoT devices. Sensors 2022, 22, 2281. [Google Scholar] [CrossRef]
- Ahmed, M.; Afreen, N.; Ahmed, M.; Sameer, M.; Ahamed, J. An inception V3 approach for malware classification using machine learning and transfer learning. Int. J. Intell. Netw. 2023, 4, 11–18. [Google Scholar] [CrossRef]
- Chaganti, R.; Ravi, V.; Pham, T.D. A multi-view feature fusion approach for effective malware classification using Deep Learning. J. Inf. Secur. Appl. 2023, 72, 103402. [Google Scholar] [CrossRef]
- Eren, M.E.; Bhattarai, M.; Rasmussen, K.; Alexandrov, B.S.; Nicholas, C. MalwareDNA: Simultaneous Classification of Malware, Malware Families, and Novel Malware. In Proceedings of the 2023 IEEE International Conference on Intelligence and Security Informatics (ISI), Charlotte, NC, USA, 2–3 October 2023; pp. 1–3. [Google Scholar]
- Marques, A.B.; Branco, V.; Costa, R.; Costa, N. Data Visualization in Hybrid Space—Constraints and Opportunities for Design. In Proceedings of the International Conference on Design and Digital Communication, Barcelos, Portugal, 3–5 October 2022; Springer Nature: Cham, Switzerland, 2022; pp. 3–15. [Google Scholar]
- Rimon, S.I.; Haque, M.M. Malware Detection and Classification Using Hybrid Machine Learning Algorithm. In Proceedings of the International Conference on Intelligent Computing & Optimization, Hua Hin, Thailand, 27–28 October 2022; Springer International Publishing: Cham, Switzerland, 2022; pp. 419–428. [Google Scholar]
- Mallik, A.; Khetarpal, A.; Kumar, S. ConRec: Malware classification using convolutional recurrence. J. Comput. Virol. Hacking Tech. 2022, 18, 297–313. [Google Scholar] [CrossRef]
- Abbasi, M.S.; Al-Sahaf, H.; Mansoori, M.; Welch, I. Behavior-based ransomware classification: A particle swarm optimization wrapper-based approach for feature selection. Appl. Soft Comput. 2022, 121, 108744. [Google Scholar] [CrossRef]
- Kim, J.; Lee, S. Malware Visualization and Similarity via Tracking Binary Execution Path. Teh. Vjesn. 2022, 29, 221–230. [Google Scholar]
- Saxe, J.; Sanders, H. Malware Data Science: Attack Detection and Attribution; No Starch Press: San Francisco, CA, USA, 2018. [Google Scholar]
- Kong, K.; Zhang, Z.; Guo, C.; Han, J.; Long, G. PMMSA: Security analysis system for android wearable applications based on permission matching and malware similarity analysis. Future Gener. Comput. Syst. 2022, 137, 349–362. [Google Scholar] [CrossRef]
- Mudgil, P.; Gupta, P.; Mathur, I.; Joshi, N. A novel similarity measure for context-based search engine. In Proceedings of the International Conference on Innovative Computing and Communications: Proceedings of ICICC 2022; Springer Nature: Singapore; 2022, Volume 2, pp. 791–808.
- Abbas, A.R.; Mahdi, B.S.; Fadhil, O.Y. Breast and lung anticancer peptides classification using N-Grams and ensemble learning techniques. Big Data Cogn. Comput. 2022, 6, 40. [Google Scholar] [CrossRef]
- Cucchiarelli, A.; Morbidoni, C.; Spalazzi, L.; Baldi, M. Algorithmically generated malicious domain names detection based on n-grams features. Expert Syst. Appl. 2021, 170, 114551. [Google Scholar] [CrossRef]
- Di Mauro, M.; Galatro, G.; Liotta, A. Experimental review of neural-based approaches for network intrusion management. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2480–2495. [Google Scholar] [CrossRef]
- Dong, S.; Xia, Y.; Peng, T. Network abnormal traffic detection model based on semi-supervised deep reinforcement learning. IEEE Trans. Netw. Serv. Manag. 2021, 18, 4197–4212. [Google Scholar] [CrossRef]
- Pelletier, C.; Webb, G.I.; Petitjean, F. Deep learning for the classification of Sentinel-2 image time series. In Proceedings of the IGARSS 2019-2019 IEEE International Geoscience and Remote Sensing Symposium, Yokohama, Japan, 28 July–2 August 2019; pp. 461–464. [Google Scholar]

| Ransomware Detection Approach | Ref. | Description | Advantages | Disadvantages |
|---|---|---|---|---|
| Machine Learning | [12,13,14,15] | The most used machine learning techniques in ransomware detection include supervised learning, unsupervised learning, and semi-supervised learning. Supervised learning involves training a model on labeled data, where the input and output are both known. This allows the model to make predictions based on the relationships learned from the training data. Unsupervised learning involves training a model on data where the output is not known, and the model must find patterns and relationships within the data on its own. Semi-supervised learning is a combination of supervised and unsupervised learning, where the model is trained on a mix of labeled and unlabeled data. | One of the main advantages of using machine learning for ransomware detection is that it allows for the automatic identification of patterns and relationships within large datasets. This can be particularly useful for identifying new and emerging threats, as the model can learn from past data to identify patterns and make predictions about future threats. Machine learning algorithms can also be trained on a wide variety of data types, including text, images, and audio, which makes them useful for detecting ransomware in different formats. | Machine learning algorithms can be vulnerable to bias and can produce inaccurate results if the training data are not representative of the real-world data. They also require frequent retraining to ensure that they continue to perform well as the data distribution changes. |
| Honeypot | [16,17,18,19,20] | Honeypots are a type of decoy system that is designed to attract and detect malware or cyber-attacks. They are used to lure attackers into a controlled and isolated environment, where their actions can be observed and studied. By setting up a honeypot, it is possible to monitor and track ransomware activity and identify new strains or variants of the malware. | One advantage of using a honeypot is that it allows researchers to gather valuable data and intelligence about the tactics, techniques, and procedures (TTPs) used by attackers. This information can be used to improve the effectiveness of ransomware detection and prevention measures. Additionally, honeypots can help mitigate the impact of ransomware attacks by preventing the malware from reaching the target system or data. | There are also some disadvantages to using honeypots. One potential issue is the risk of false positives, where legitimate activity is mistaken for malicious activity. Another issue is the cost and resources required to maintain and operate a honeypot, as well as the potential legal and ethical considerations. Additionally, honeypots may not be suitable for all types of environments or organizations and may not provide comprehensive protection against all types of ransomware attacks. |
| Statistical | [21,22,23,24,25] | The statistical analysis approach involves collecting and analyzing data about ransomware behavior to identify patterns and trends. This can be done through various methods, such as collecting data about the frequency and types of ransom demands, the types of files targeted, and the tactics used by ransomware operators. | The advantage of using statistical analysis is that it allows researchers to gain a deeper understanding of ransomware behavior and identify key trends that can inform prevention and detection efforts. | The disadvantage of this approach is that it relies on the availability of accurate and comprehensive data, which may be difficult to obtain in some cases. Additionally, statistical analysis may not be able to identify specific instances of ransomware in real time, making it less effective for immediate detection and response. |
| Crypto Worm | Human-Operated Ransomware | Ransomware-as-a-Service (RaaS) | Automated Active Adversary | |
|---|---|---|---|---|
| Key Features | Self-propagating | Targeted attacks | Ransomware-as-a-Service model | Advanced evasion tactics |
| Spreading techniques | Wormhole | Social engineering | Email attachments, web links | Customized attack vectors |
| Exploitation techniques | Vulnerabilities in systems | Targeted vulnerabilities | Vulnerabilities in systems | Customized exploits |
| Detection modules | Antivirus | User awareness, network monitoring | Antivirus, network monitoring | Network monitoring, user awareness |
| Ransomware Family Example | WannaCry | Ryuk | REvil | SolarWinds |
| Date | Ransomware Family | Event Description |
|---|---|---|
| 1989 | AIDS | First ransomware, called “AIDS” or “PC Cyborg”, is released. |
| 1991 | PC Cyborg | It displays a message on the infected computer’s screen demanding payment. |
| 2005 | Gpcode | Gpcode ransomware uses strong encryption to lock users’ files, demanding payment to decrypt them. |
| 2013 | Cryptolocker | Cryptolocker ransomware is released, using encryption to hold users’ files hostage and demanding payment for the decryption key. |
| 2014 | Cryptowall | Cryptowall ransomware is released, using encryption to hold users’ files hostage and demanding payment for the decryption key. |
| 2015 | TeslaCrypt | TeslaCrypt ransomware has been released, targeting video game files and demanding payment for the decryption key. |
| 2016 | Locky | Locky ransomware is released, using encryption to hold users’ files hostage and demanding payment for the decryption key. |
| 2017 | NotPetya | NotPetya ransomware attack causes widespread damage, affecting thousands of computers and causing disruptions to various industries. |
| 2018 | LockerGoga | LockerGoga ransomware attack targets industrial control systems, causing disruptions to manufacturing and other industries. |
| 2019 | Ryuk | Ryuk ransomware targets government and healthcare organizations for large ransoms, causing widespread damage. |
| 2020 | REvil (Sodinokibi) | REvil (also known as Sodinokibi) ransomware attack causes widespread damage, affecting thousands of users and organizations. |
| 2021 | Babuk | Babuk ransomware attack targets government agencies and high-profile companies, threatening to release stolen data if a ransom is not paid. |
| 2022 | Egregor | Egregor ransomware attack causes widespread damage, affecting thousands of users and organizations. |
| 2023 | Black Cat | BlackCat ransomware is a type of malicious software that encrypts a victim’s files and demands a ransom for the decryption key. |
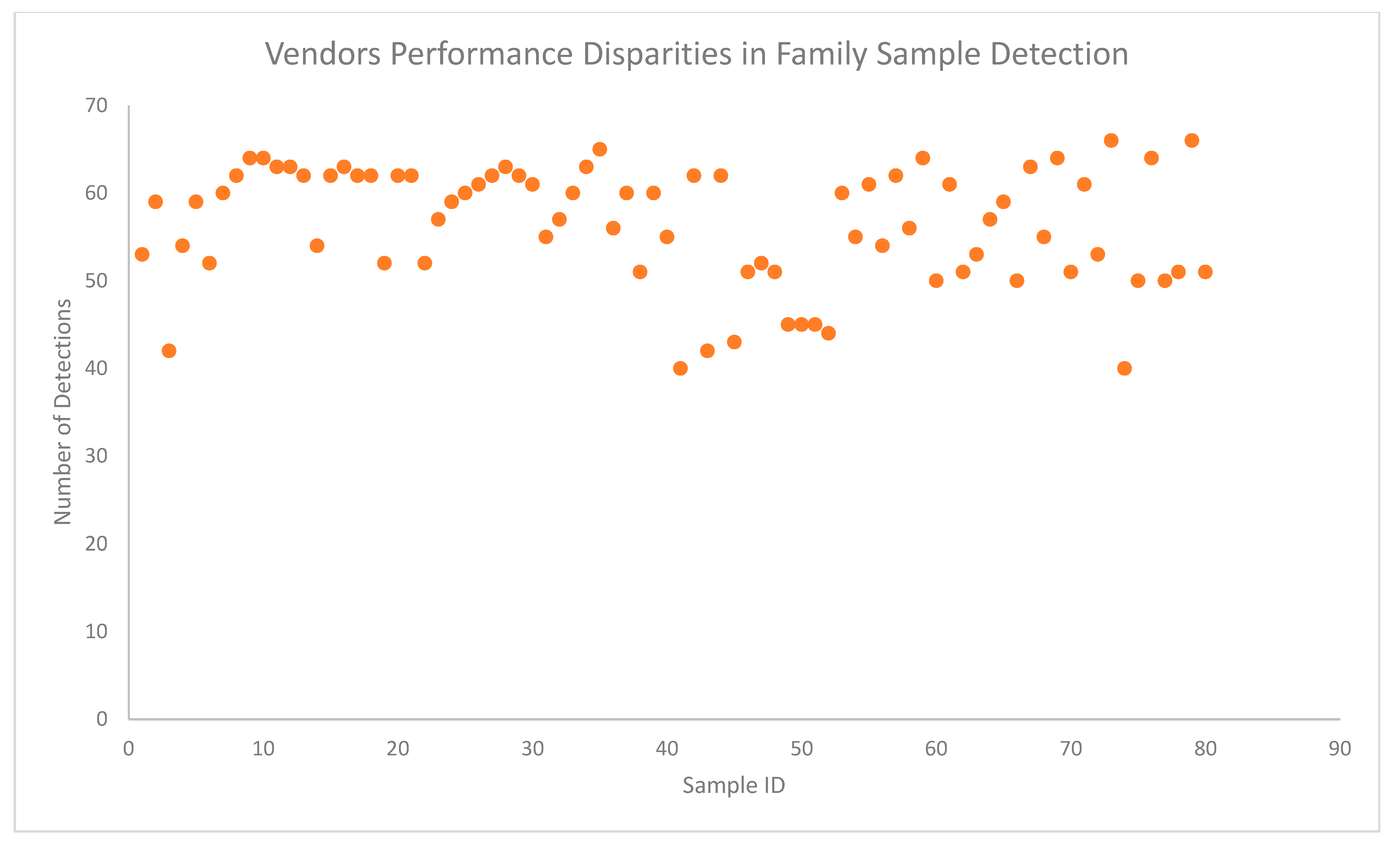
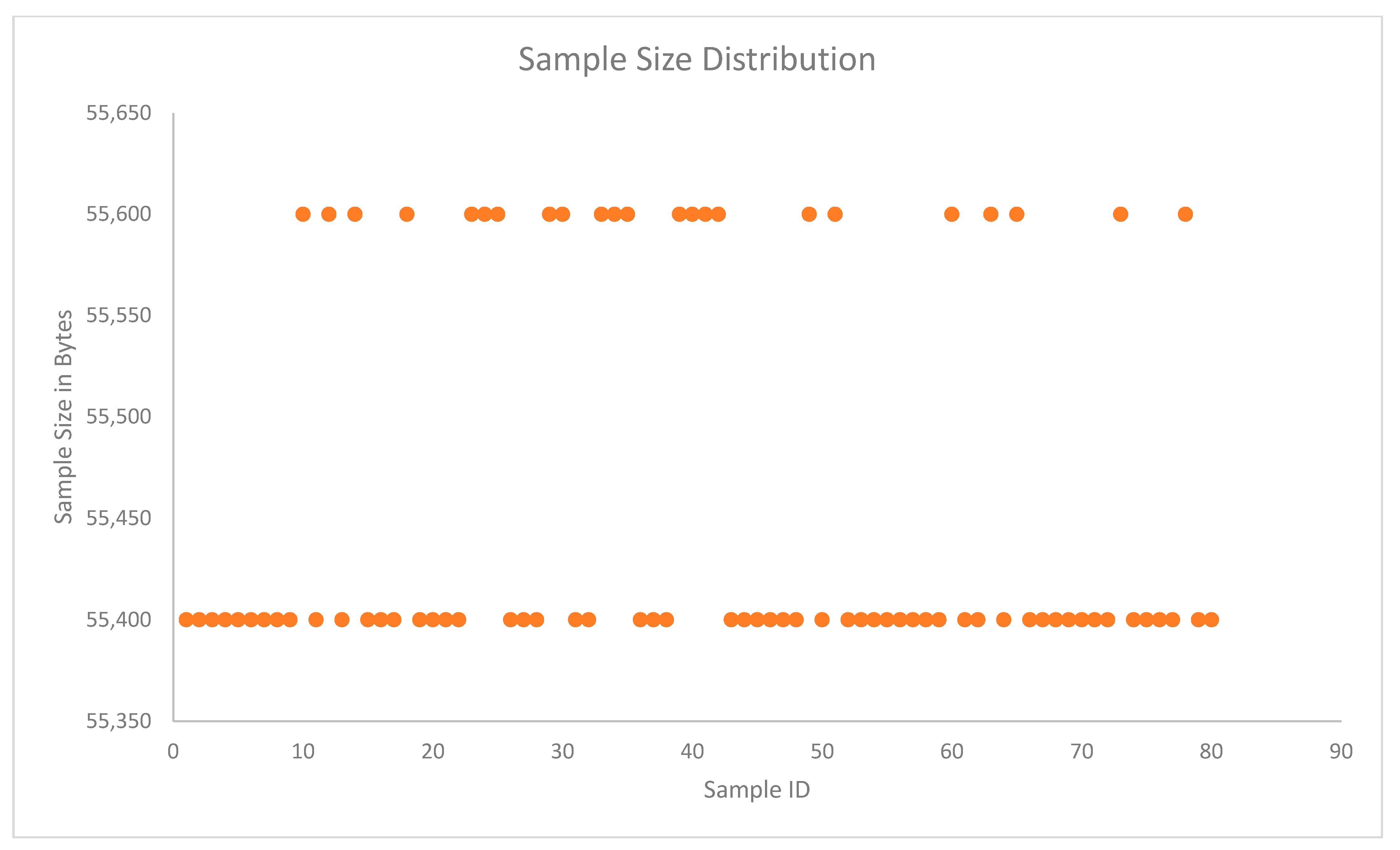
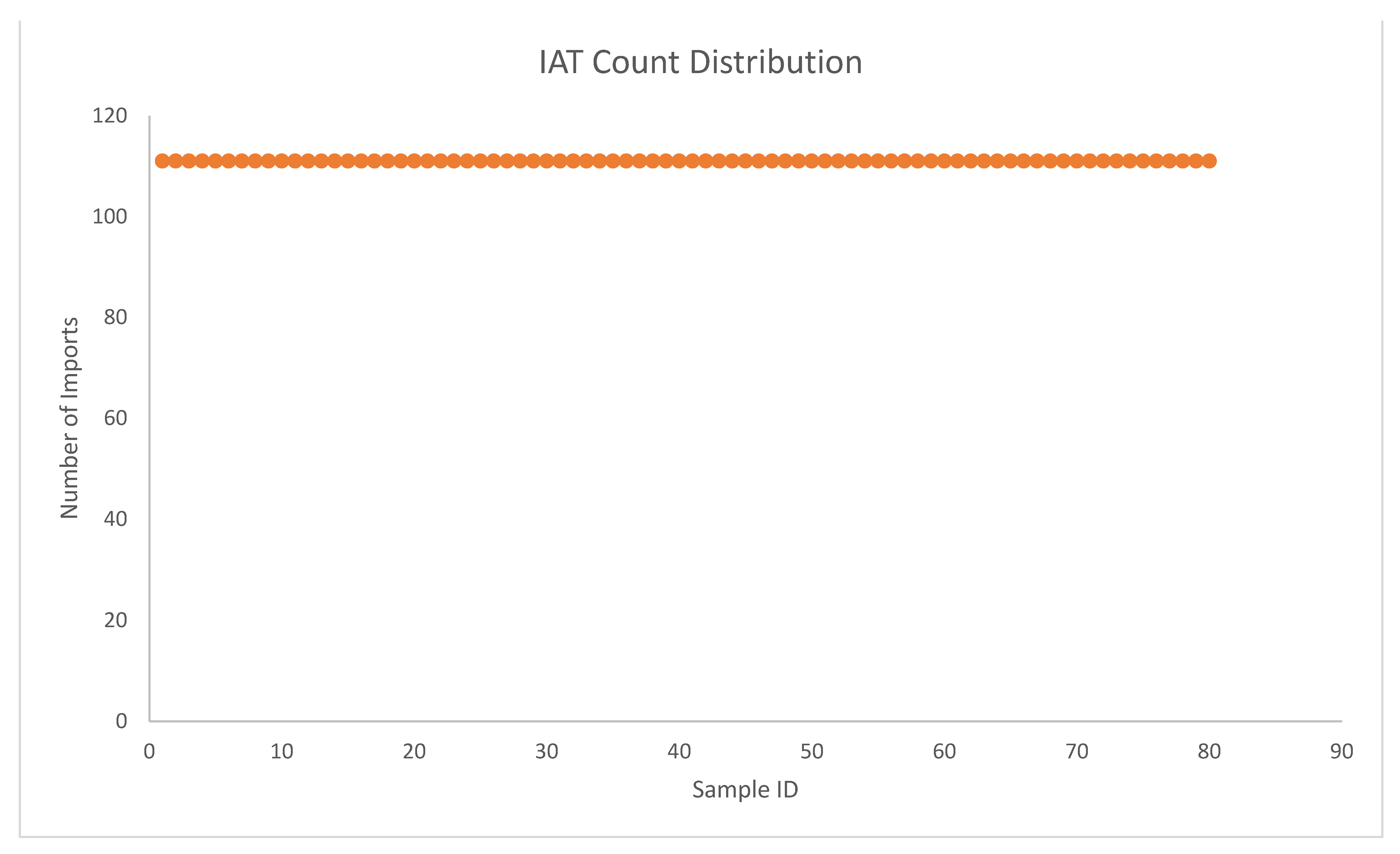
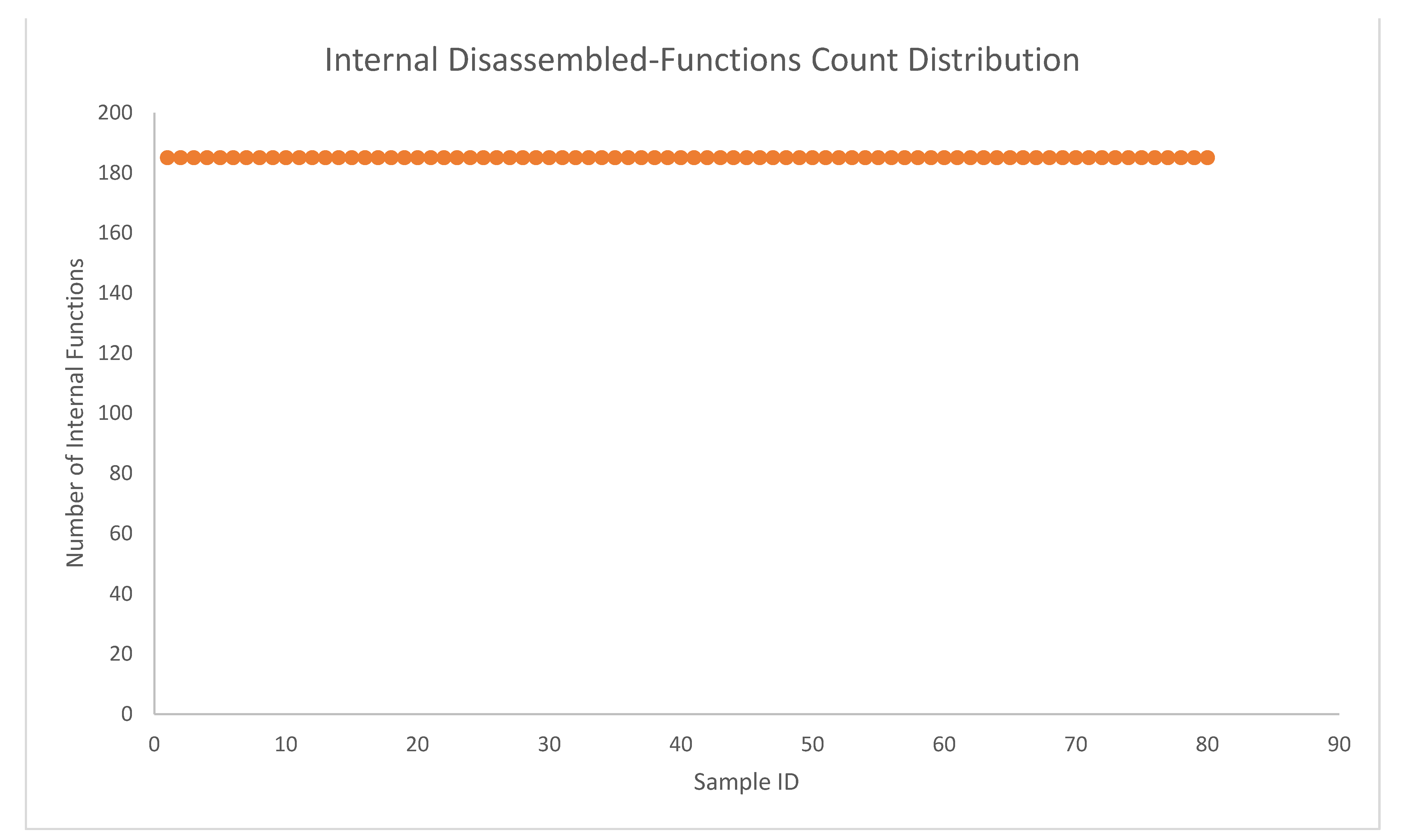
| Number of Samples | 80 Samples |
|---|---|
| Vendor Detection | 100% (40 + vendors) detectability |
| Sample Size | 57 samples with 55,200 bytes 23 samples with 55,300 bytes |
| IAT Count | 111 imports |
| Internal Disassembled Functions Count | 185 functions |
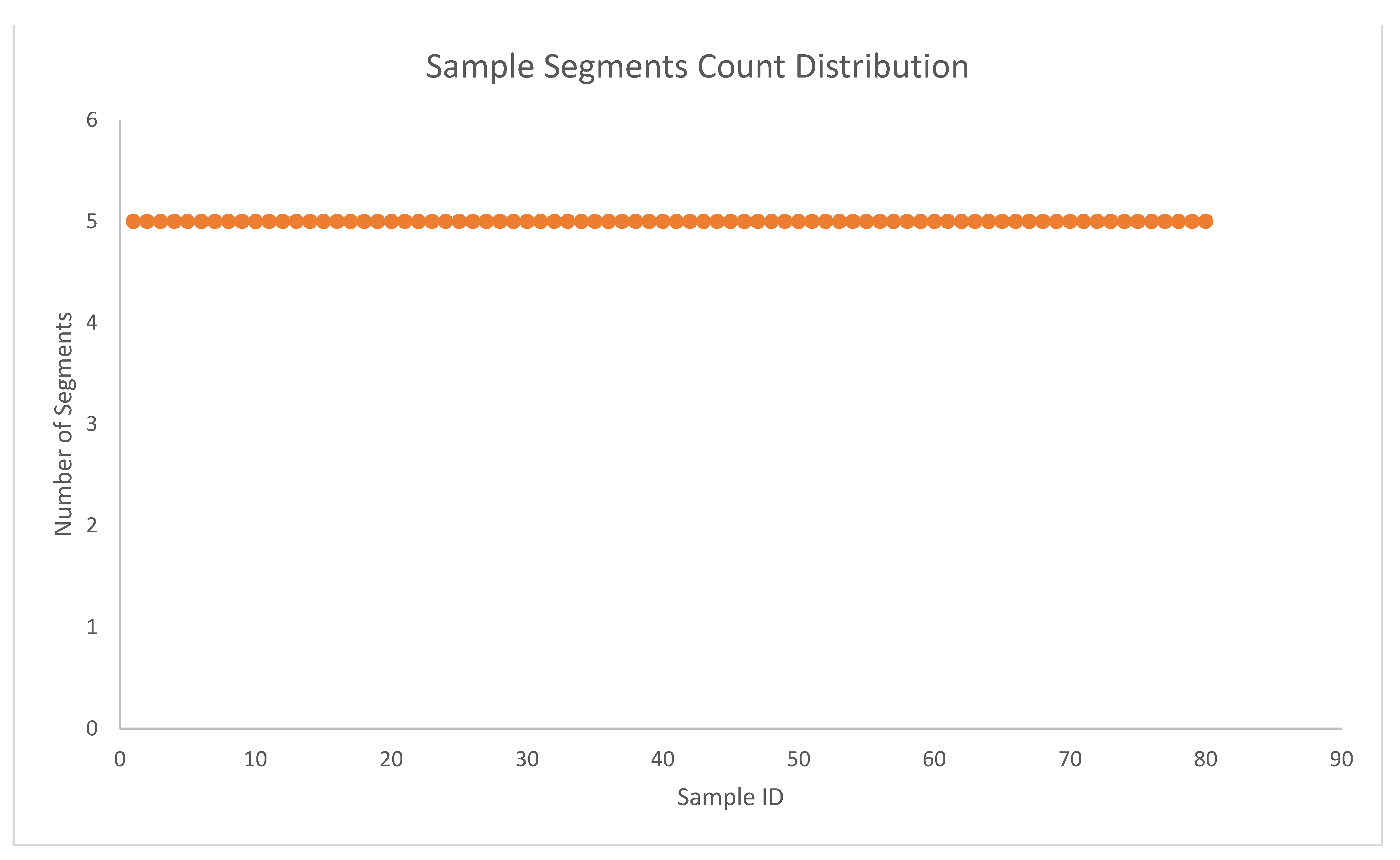
| Sample Segments | 5 sections |
| Components | Purpose | Technology | Output |
|---|---|---|---|
| System Controller | The main component that interacts with all the analysis engines and performs database queries to retrieve relevant samples in response to analyst requests is the controller. This component is the central hub of the malware indexing system and is responsible for coordinating the analysis and classification of different types of malware, including ransomware. It receives requests from analysts and communicates with the various analysis engines to gather the necessary data and information. The controller also interacts with the database to retrieve relevant samples based on the analyst’s requests, ensuring that the analyst has access to the most up-to-date and relevant data. Overall, the controller plays a critical role in the operation of the malware indexing system, enabling analysts to access the data and information quickly and easily in order to effectively analyze and classify different types of malware. | APIs modules | Hybrid attributes |
| Analyzer Engine | The analyzer server is responsible for converting executable binaries into a set of static features through disassembly to extract relevant static attributes that can be used by the controller to classify the binaries. This process involves breaking down the samples into their constituent parts and extracting the relevant features, such as function names, imported libraries, and other characteristics. The analyzer server uses a disassembler tool to perform this process, which is an important part of the overall malware indexing system. In addition to extracting static features, the analyzer server is also responsible for converting the set of binaries into dynamic attributes through sandboxing. Sandboxing involves running the samples in a controlled environment and observing their behavior to extract dynamic attributes, such as network traffic, file system changes, and other activities. These dynamic attributes can be used to supplement the static features to classify and analyze the samples more accurately. Overall, the analyzer server plays a critical role in the operation of the malware indexing system, providing the necessary data and information that enables analysts to effectively analyze and classify different types of malware. | Disassembling Decompiling | Static features: Function names Imported libraries Strings and string patterns File size and metadata Dynamic features: Network traffic and connection information API Calls File system changes Process and thread behavior Memory modifications Registry changes System and library calls |
| MonogoDB | MongoDB is a document-based store for all the extracted attributes by the analysis engines. It is an NoSQL database that is designed to handle large amounts of data and to support flexible and scalable data models. In the context of the malware indexing system, MongoDB is used to store all the extracted static and dynamic features from the analyzer server, as well as any additional metadata or information about the samples. These data are then used by the controller to perform various analysis and classification tasks, such as calculating the Jaccard Index similarity between different samples or clustering the samples into different categories. By providing a centralized repository for all the extracted features, MongoDB enables analysts to access and analyze the data more easily, and to perform complex queries and searches across the entire dataset. | Receive controller queries for binaries features and attributes. | Hybrid attributes |
| Disassembler (Ghidra 11.0) | Ghidra used to extract static features from malware samples. Ghidra is a powerful and feature-rich tool that is developed and maintained by the National Security Agency (NSA). It provides a wide range of features and functionality that are useful in the analysis of malware, including the ability to disassemble code, view and edit assembly instructions, and perform various other tasks. In the context of the malware indexing system, Ghidra could be used to disassemble the samples to extract static features such as function names, imported libraries, and other characteristics. These features could then be stored in the MongoDB database for use in various analysis and classification tasks. | Disassembling | Static features of the samples |
| Sandbox (Cuckoo) | Cuckoo Sandbox is a powerful and widely used tool that is used to extract dynamic features from malware samples. It is an open-source sandboxing platform that allows users to analyze the behavior of malware in a controlled environment. By analyzing the behavior of malware in a sandbox, analysts can extract various dynamic features such as network traffic, file system changes, and other characteristics that may not be visible through static analysis alone. In the context of the malware indexing system, Cuckoo Sandbox could be used to extract dynamic features from the samples and store them in the MongoDB database. These dynamic features could be used in conjunction with the static features extracted through disassembly to provide a more complete picture of the malware’s behavior and capabilities. | Sandboxing | Dynamic features of the samples |
| Python PyCharm (2023.3.2) | Python PyCharm is a powerful integrated development environment (IDE) that is often used in the development of Python programs. It is a popular choice among developers due to its feature-rich set of tools and capabilities, including code completion, debugging, testing, and deployment. In the context of the malware indexing system, Python PyCharm could be used to develop and maintain the various components of the system, including the analysis engines, the controller, and the database. | Python IDE | System scripts Database connections script Sample submissions script |
| VirusTotal | VirusTotal is a powerful tool that allows users to scan files and URLs against a vast array of antivirus engines and other security tools. This enables analysts to identify malicious content and track the evolution of malware over time quickly and easily. In our study, we used VirusTotal to collect a large dataset of ransomware samples, which we then analyzed using various techniques such as static analysis, dynamic analysis, and visualization. By leveraging the power of VirusTotal, we were able to gather a large and diverse set of ransomware samples quickly and efficiently, which allowed us to more accurately and effectively classify and cluster the samples. Overall, VirusTotal proved to be a valuable resource in our study, and it is a powerful tool that is widely used in the field of malware analysis | VirusTotal Hunting feature | Collected ransomware samples |
| Feature | Strings | Import Adress Table | API Calls |
|---|---|---|---|
| Analysis Method | Static | Static | Dynamic |
| Time Complexity (per sample) | 5 s | 5–10 s | 30–60 s |
| Similarity Accuracy | 0.3 | 0.86 | 1 (Perfect Matching) |
| Analysis Efficiency | Fast processing | Balanced speed and comprehensive examination | Thorough analysis, longer processing time |
| Trade-off (Speed vs. Accuracy) | Emphasis on speed, lower accuracy | Balanced approach, high accuracy | Longer processing time for thorough dynamic analysis |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yamany, B.; Elsayed, M.S.; Jurcut, A.D.; Abdelbaki, N.; Azer, M.A. A Holistic Approach to Ransomware Classification: Leveraging Static and Dynamic Analysis with Visualization. Information 2024, 15, 46. https://doi.org/10.3390/info15010046
Yamany B, Elsayed MS, Jurcut AD, Abdelbaki N, Azer MA. A Holistic Approach to Ransomware Classification: Leveraging Static and Dynamic Analysis with Visualization. Information. 2024; 15(1):46. https://doi.org/10.3390/info15010046
Chicago/Turabian StyleYamany, Bahaa, Mahmoud Said Elsayed, Anca D. Jurcut, Nashwa Abdelbaki, and Marianne A. Azer. 2024. "A Holistic Approach to Ransomware Classification: Leveraging Static and Dynamic Analysis with Visualization" Information 15, no. 1: 46. https://doi.org/10.3390/info15010046
APA StyleYamany, B., Elsayed, M. S., Jurcut, A. D., Abdelbaki, N., & Azer, M. A. (2024). A Holistic Approach to Ransomware Classification: Leveraging Static and Dynamic Analysis with Visualization. Information, 15(1), 46. https://doi.org/10.3390/info15010046







