A Flexible Infrastructure-Sharing 5G Network Architecture Based on Network Slicing and Roaming
Abstract
1. Introduction
2. Background and Related Work
2.1. 5G Networks
2.2. Network Slicing
2.3. 5G Roaming
- Local breakout (LBO): In this model, the user’s authentication and authorization on the visited network are performed by the home network, while the traffic is directly routed through the visited PLMN (VPLMN).
- Home routed (HR): In this scenario, the data traffic from the VPLMN is routed to the data network (DN) via the HPLMN.
2.4. Neutral Hosts
2.5. Related Work
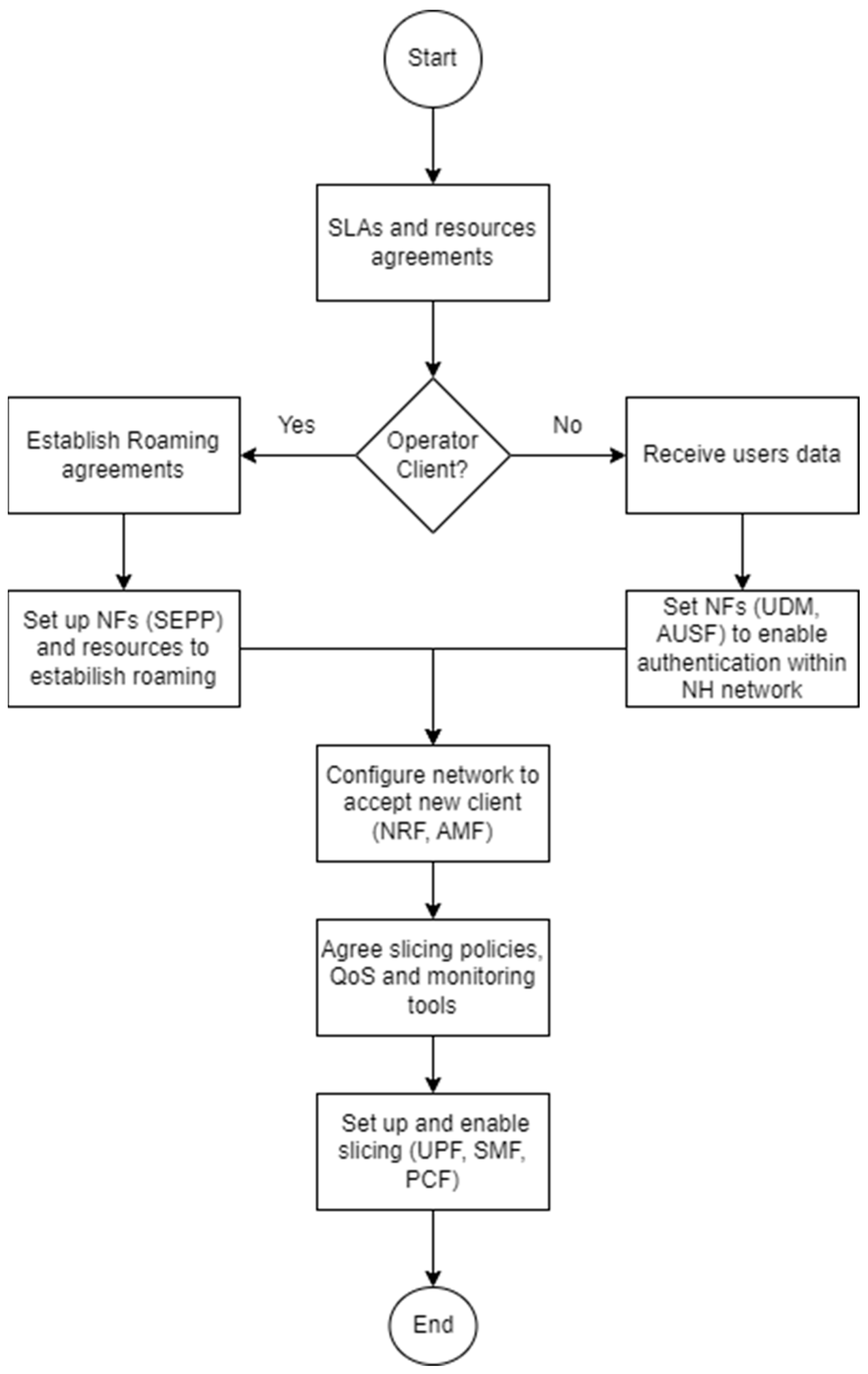
3. Proposed Architecture
3.1. Conceptual Architecture
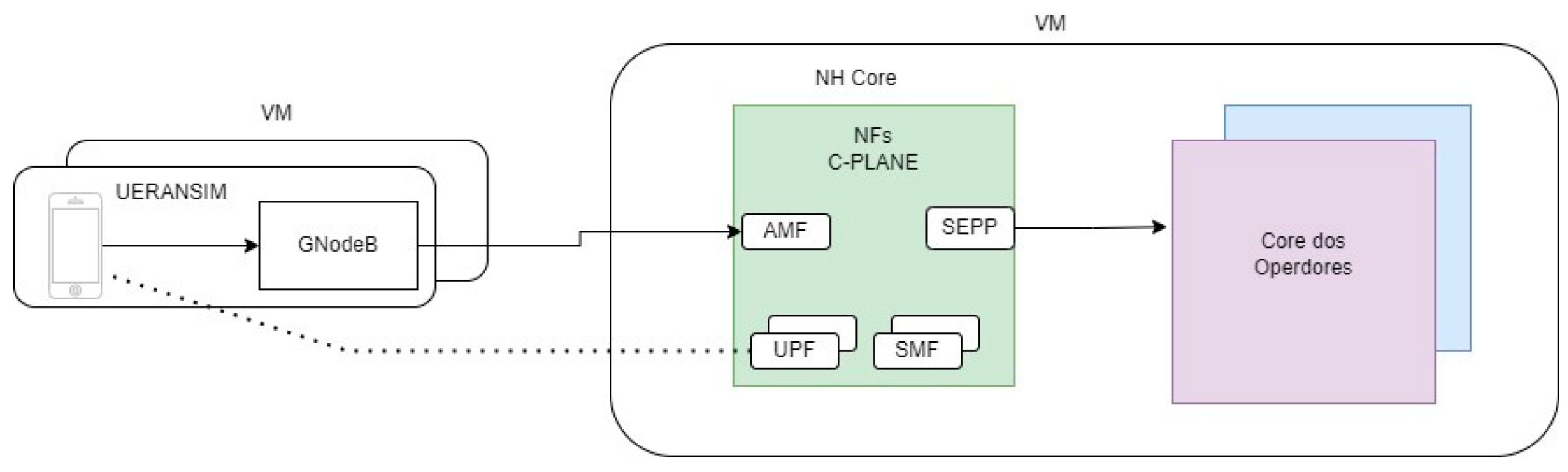
3.2. Architecture Implementation
3.2.1. Software Tools
3.2.2. Implemented System
4. Results and Discussion
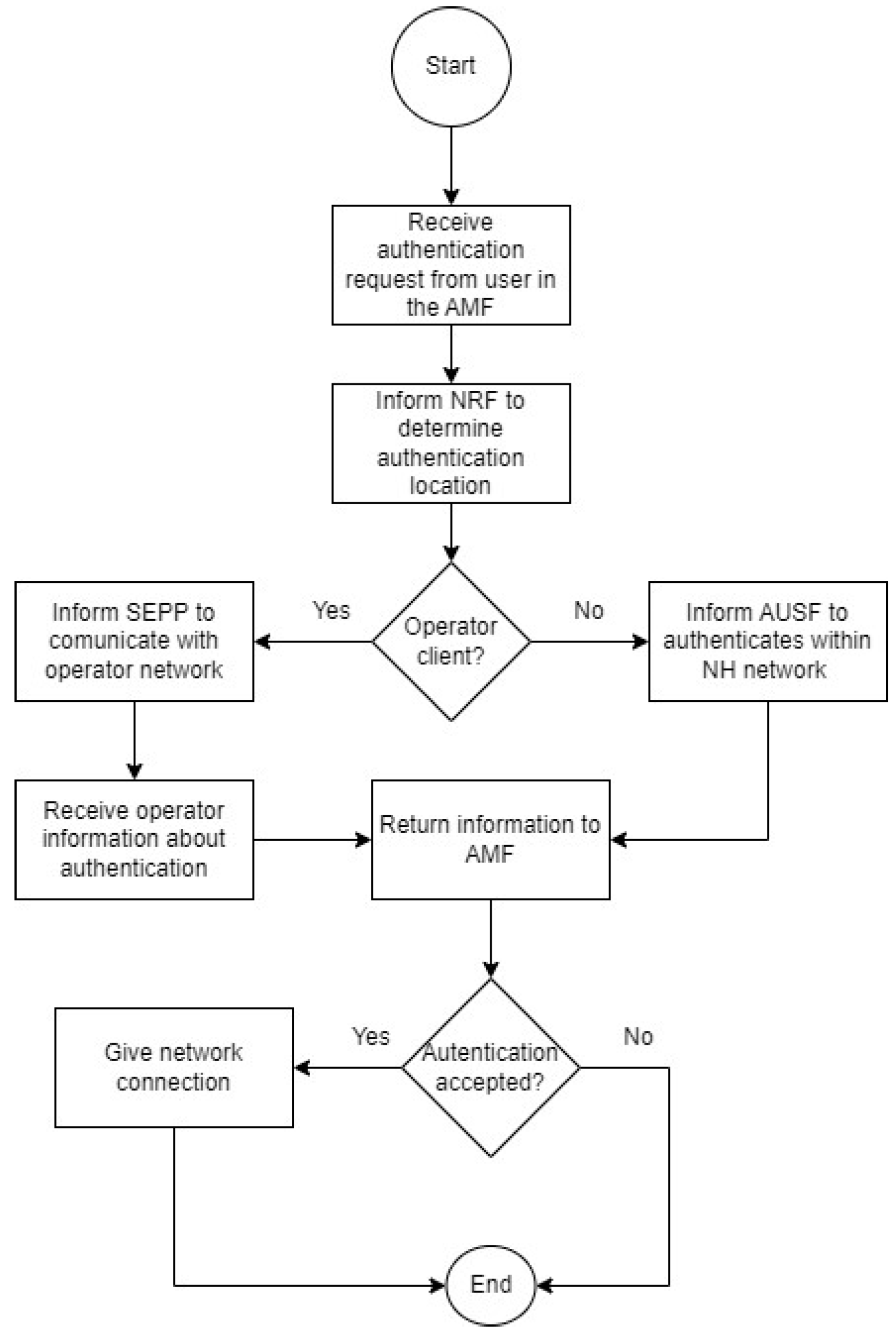
4.1. Authentication and Traffic Isolation
4.2. Throughput
4.3. Packet Loss Ratio
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Jabagi, N.; Park, A.; Kietzmann, J. The 5G Revolution: Expectations Versus Reality. IT Prof. 2020, 22, 8–15. [Google Scholar] [CrossRef]
- 5G PPP Architecture Working Group. View on 5G Architecture; Version 4.0; 5G PPP Architecture Working Group: Pisa, Italy, 2021. [Google Scholar]
- Kumar, S.K.A.; Crawford, D.; Stewart, R. Pricing Models for 5G Multi-Tenancy Using Game Theory Framework. IEEE Commun. Mag. 2023, 1–7. [Google Scholar] [CrossRef]
- Baldoni, G.; Cruschelli, P.; Paolino, M.; Meixner, C.C.; Albanese, A.; Papageorgiou, A.; Khalili, H.; Siddiqui, S.; Simeonidou, D. Edge Computing Enhancements in an NFV-Based Ecosystem for 5G Neutral Hosts. In Proceedings of the 2018 IEEE Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), Verona, Italy, 27–29 November 2018; pp. 1–5. [Google Scholar]
- 3rd Generation Partnership Project. 3GPP Technical Report 21.915; Version 15.0.0 Release 15; ETSI: Sophia Antipolis, France, 2019. [Google Scholar]
- Zhou, C.; Gao, J.; Li, M.; Shen, X.; Zhuang, W.; Li, X.; Shi, W. AI-Assisted Slicing-Based Resource Management for Two-Tier Radio Access Networks. IEEE Trans. Cogn. Commun. Netw. 2023, 9, 1691–1706. [Google Scholar] [CrossRef]
- Bajracharya, R.; Shrestha, R.; Jung, H.; Shin, H. Neutral Host Technology: The Future of Mobile Network Operators. IEEE Access 2022, 10, 99221–99234. [Google Scholar] [CrossRef]
- Chahbar, M.; Diaz, G.; Dandoush, A.; Cérin, C.; Ghoumid, K. A Comprehensive Survey on the E2E 5G Network Slicing Model. IEEE Trans. Netw. Serv. Manag. 2021, 18, 49–62. [Google Scholar] [CrossRef]
- Keller, R.; Castellanos, D.; Sander, A.; Robison, A.; Abtin, A. Roaming in the 5G system: The 5GS roaming architecture. Ericsson Technol. Rev. 2021, 2021, 2–11. [Google Scholar] [CrossRef]
- Fernández-Fernández, A.; Colman-Meixner, C.; Ochoa-Aday, L.; Betzler, A.; Khalili, H.; Siddiqui, M.S.; Carrozzo, G.; Figuerola, S.; Nejabati, R.; Simeonidou, D. Validating a 5G-Enabled Neutral Host Framework in City-Wide Deployments. Sensors 2021, 21, 8103. [Google Scholar] [CrossRef] [PubMed]
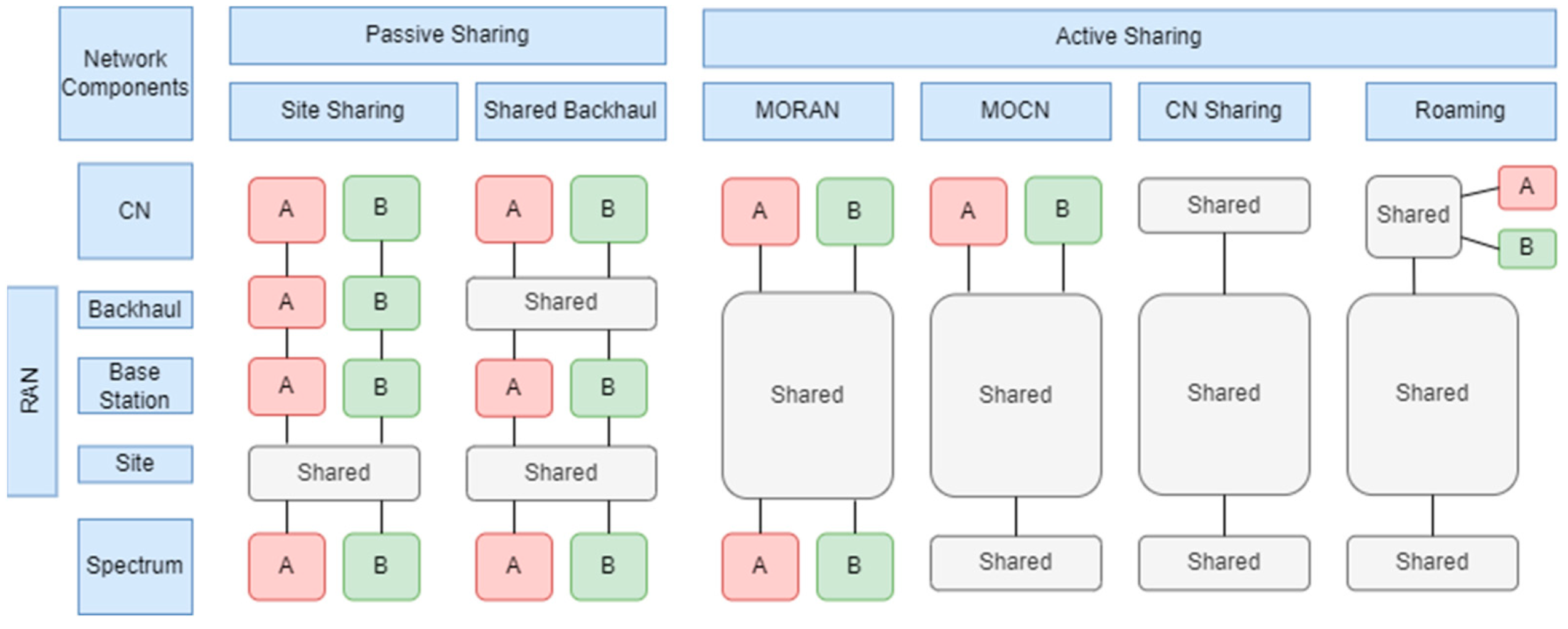
- GSMA. Infrastructure Sharing. Available online: https://www.gsma.com/futurenetworks/wiki/infrastructure-sharing-an-overview/ (accessed on 23 February 2024).
- Esmat, H.H.; Lorenzo, B.; Shi, W. Toward Resilient Network Slicing for Satellite–Terrestrial Edge Computing IoT. IEEE Internet Things J. 2023, 10, 14621–14645. [Google Scholar] [CrossRef]
- Kassis, M.; Costanzo, S.; Yassin, M. Flexible Multi-Operator RAN Sharing: Experimentation and Validation Using Open Source 4G/5G Prototype. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 205–210. [Google Scholar]
- Mun, K. Making Neutral Host a Reality with OnGo; Mobile Experts White Paper; Mobile Experts, Inc.: Campbell, CA, USA, 2018. [Google Scholar]
- Giannoulakis, I.; Xylouris, G.; Kafetzakis, E.; Kourtis, A.; Fajardo, J.O.; Khodashenas, P.S.; Albanese, A.; Mouratidis, H.; Vassilakis, V. System Architecture and Deployment Scenarios for SESAME: Small cEllS coodinAtion for Multi-Tenancy and Edge Services. In Proceedings of the 2016 IEEE NetSoft Conference and Workshops (NetSoft), Seoul, Republic of Korea, 6–10 June 2016; pp. 447–452. [Google Scholar]
- Spada, M.R.; Pérez-Romero, J.; Sanchoyerto, A.; Solozabal, R.; Kourtis, M.A.; Riccobene, V. Management of Mission Critical Public Safety Applications: The 5G ESSENCE Project. In Proceedings of the 2019 European Conference on Networks and Communications (EuCNC), Valencia, Spain, 8–21 June 2019; pp. 155–160. [Google Scholar]
- Güngör, A. UERANSIM. Available online: https://github.com/aligungr/UERANSIM (accessed on 16 October 2023).
- OpenAirInterface. OAI 5G RAN Project Group. Available online: https://openairinterface.org/oai-5g-ran-project/ (accessed on 16 October 2023).
- my5G. my5G-RANTester. Available online: https://github.com/my5G/my5G-RANTester (accessed on 16 October 2023).
- Open5GS. Available online: https://open5gs.org/ (accessed on 16 October 2023).
- free5GC. Available online: https://free5gc.org/ (accessed on 16 October 2023).
- OpenAirInterface. 5G Core Network. Available online: https://openairinterface.org/oai-5g-core-network-project/ (accessed on 16 October 2023).
- Reddy, R.; Lipps, C.; Schotten, H.D.; Gundall, M.; Schotten, H.D. Open Source 5G Core Network Implementations: A Qualitative and Quantitative Analysis. In Proceedings of the 2023 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Istanbul, Türkiye, 4–7 July 2023; IEEE: Piscataway, NJ, USA, 2023. [Google Scholar]
- iPerf—The Ultimate Speed Test Tool for TCP, UDP and SCTP. Available online: https://iperf.fr/ (accessed on 16 October 2023).


| RAN Simulator | Multiple PLMNs | Computational Resources | Multiple UEs in the Same VM | Minimal CPU Core Capacity per VM |
|---|---|---|---|---|
| OpenAirInterface | Yes | High | No | 4 |
| UERANSIM | No | Low | Yes | 1 |
| My-5GRANTester | No | Low | Yes | 1 |
| Throughput (Mbps) | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| VM2 | VM3 | VM4 | VM5 | TOTAL | |||||
| One client/slice | 22.0 ± 2.7 | 23.6 ± 2.9 | 21.0 ± 2.9 | 22.1 ± 2.9 | 22.4 ± 2.3 | 22.1 ± 2.5 | 21.7 ± 3.3 | 22.1 ± 2.3 | 177.2 |
| Four clients/slices | 31.5 ± 3.5 | 35.9 ± 5.1 | 36.4 ± 5.3 | 33.2 ± 4.4 | 38.3 ± 5.3 | 37.5 ± 3.2 | 38.1 ± 3.2 | 35.7 ± 3.6 | 286.7 |
| Throughput (Mbps) | |||||
|---|---|---|---|---|---|
| VM2 | VM3 | VM4 | VM5 | TOTAL | |
| One client/slice | 49.8 ± 3.2 | 50.7 ± 4.1 | 51.1 ± 3.3 | 49.8 ± 3.2 | 201.4 |
| Four clients/slices | 89.0 ± 13.0 | 66.6 ± 11.6 | 89.7 ± 11.9 | 80.3 ± 12.8 | 325.7 |
| PLR (%) | ||||||||
|---|---|---|---|---|---|---|---|---|
| VM2 | VM3 | VM4 | VM5 | |||||
| One client/slice | 1.11 ± 0.37 | 1.12 ± 0.38 | 1.10 ± 0.39 | 1.13 ± 0.41 | 1.06 ± 0.45 | 1.05 ± 0.44 | 1.19 ± 0.41 | 1.15 ± 0.39 |
| Four clients/slices | 0.05 ± 0.05 | 0.04 ± 0.03 | 0.03 ± 0.03 | 0.03 ± 0.02 | 0.04 ± 0.04 | 0.04 ± 0.04 | 0.03 ± 0.02 | 0.03 ± 0.02 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ferreira, J.P.; Ferreira, V.C.; Nogueira, S.L.; Faria, J.M.; Afonso, J.A. A Flexible Infrastructure-Sharing 5G Network Architecture Based on Network Slicing and Roaming. Information 2024, 15, 213. https://doi.org/10.3390/info15040213
Ferreira JP, Ferreira VC, Nogueira SL, Faria JM, Afonso JA. A Flexible Infrastructure-Sharing 5G Network Architecture Based on Network Slicing and Roaming. Information. 2024; 15(4):213. https://doi.org/10.3390/info15040213
Chicago/Turabian StyleFerreira, João P., Vinicius C. Ferreira, Sérgio L. Nogueira, João M. Faria, and José A. Afonso. 2024. "A Flexible Infrastructure-Sharing 5G Network Architecture Based on Network Slicing and Roaming" Information 15, no. 4: 213. https://doi.org/10.3390/info15040213
APA StyleFerreira, J. P., Ferreira, V. C., Nogueira, S. L., Faria, J. M., & Afonso, J. A. (2024). A Flexible Infrastructure-Sharing 5G Network Architecture Based on Network Slicing and Roaming. Information, 15(4), 213. https://doi.org/10.3390/info15040213







