SGM: Strategic Game Model for Resisting Node Misbehaviour in IoT-Cloud Ecosystem
Abstract
1. Introduction
- The proposed scheme introduces a matrix of transactional records to access distributed storage systems and retain encoded sensitive information related to trust.
- A novel dual controller scheme is introduced, viz. Global Trust Controller and Core node Selection Controller, to formulate a secure agreement system for validating the global trust of all nodes.
- A unique payoff management scheme is introduced, which mainly performs speedy calculations, allocations, and updates, resulting in faster processing during routing operations.
- The proposed scheme deploys IoT-based mobile nodes in an ad hoc manner considering the usage of both private and public clouds for role identification, payoff selection, and gain maximisation.
- The results of the study are compared to existing game models with respect to accuracy, response time, energy, and cost, unlike any current security scheme in IoT.
2. Existing Approaches
2.1. Studies on Misbehaviour
2.2. Game-Based Security Studies
2.3. Evolving Studies on Ad Hoc Security
3. Research Problems
- Gap between IoT and ad hoc network security: The current state of security solutions in ad hoc networks is not applicable when integrated with cloud or IoT systems. Due to the progress of technologies, the necessary revision has not been carried out considering the practical deployment environment. For example, when a mobile ad hoc network (MANET) node is deployed in IoT, the security protocol for it [13] differs from the security protocol of IoT [50]. Moreover, the ad hoc network concept is not considered much while all nodes are deployed in the IoT scenario; they are considered in terms of individual nodes and not in the form of a network. Currently, there are more IoT security schemes than conventional ad hoc security.
- Sophisticated Game Modelling: Studies prove that the game concept is one of the most rapidly evolving security solutions in the network [51,52]. However, most game concepts deployed to date associated the model with developing interactive game stages, including multiple steps. Although it was quite possible to use this multi-stage gaming model to address various traits of security, in the case of a complex environment, sophisticated measures had to be taken and there was less assurance of model sustainability. Hence, there is a need for a simplified and straightforward game model to perform better decision-making. Furthermore, it is notable that most of the existing game models have extensive payoff matrix computation, which also demands resources. Therefore, when applied to a sizeable practical network, such a sophisticated game model will call for a delay and higher response time. Thus, a lightweight game model is needed to secure a challenging communication environment.
- Computational Burden not emphasised: There are two forms of threats in the network; one form is when the attacker’s identity is well-known based on their attack patterns, while the second form is unknown. Hence, security modelling confirming the presence of misbehaved nodes calls for an extensive set of observations to be carried out. Such threat monitoring calls for deploying a method with a lesser dependence on resources and the inclusion of smart operational processes geared towards identifying the attacker’s intention in the least amount of time possible.
4. Proposed Methodology
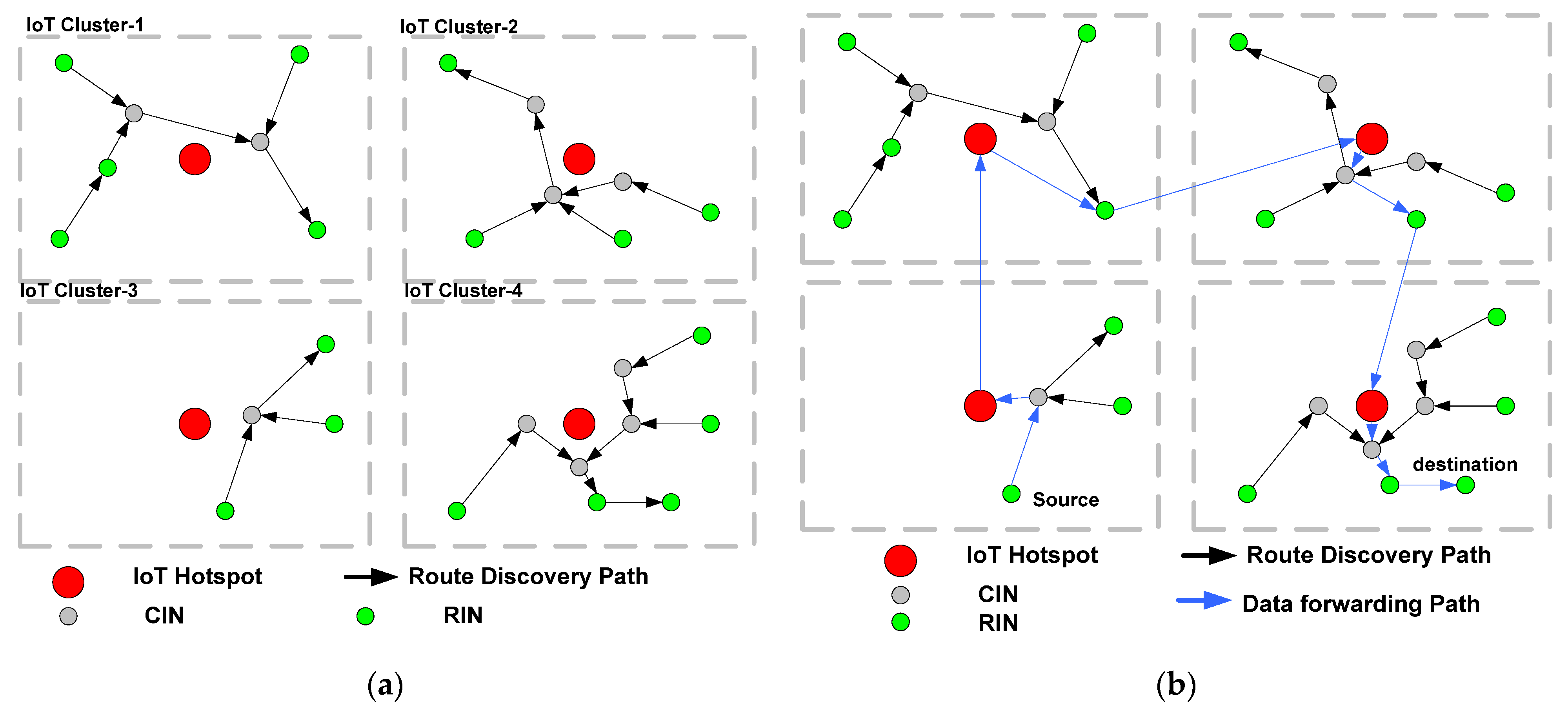
- Environment: The presence of both regular mobile IoT nodes and malicious nodes is regarded as misbehaving nodes by the environment. Nodes are assumed to adhere to any conventional on-demand routing scheme, which adds security to the existing routing scheme, and no mobile IoT nodes forward data on their own. Instead, a core IoT node is used to perform the task during the propagation process and thus save the most resources.
- Core Actors: There are two types of core actors in the proposed system, which are Core IoT Nodes (CIN) and Regular IoT Nodes (RIN). An RIN collects all the data and forwards them to a destination node in an ad hoc manner if it is located within its communication range. Otherwise, the RIN takes the assistance of the CIN by sending a request control message to the latter as a part of the interaction between CIN and RIN. CIN does not participate in data aggregation or typical forwarding processes, unlike the intermediate nodes in conventional ad hoc networks. Instead, CIN are selected based on potential connectivity with a higher probability of linking to the destination node. Hence, any node with a high number of connected links (apart from RIN) and better residual energy is selected as a CIN. The proposed scheme entails the process of CIN selection by RIN based on newly formulated quality metrics and global trust. Therefore, from a security viewpoint, any node with a higher value of computed trust in a proposed scheme is finalised to be selected as a CIN. Upon receiving the information of the destination node from the CIN, the RIN forwards the data.
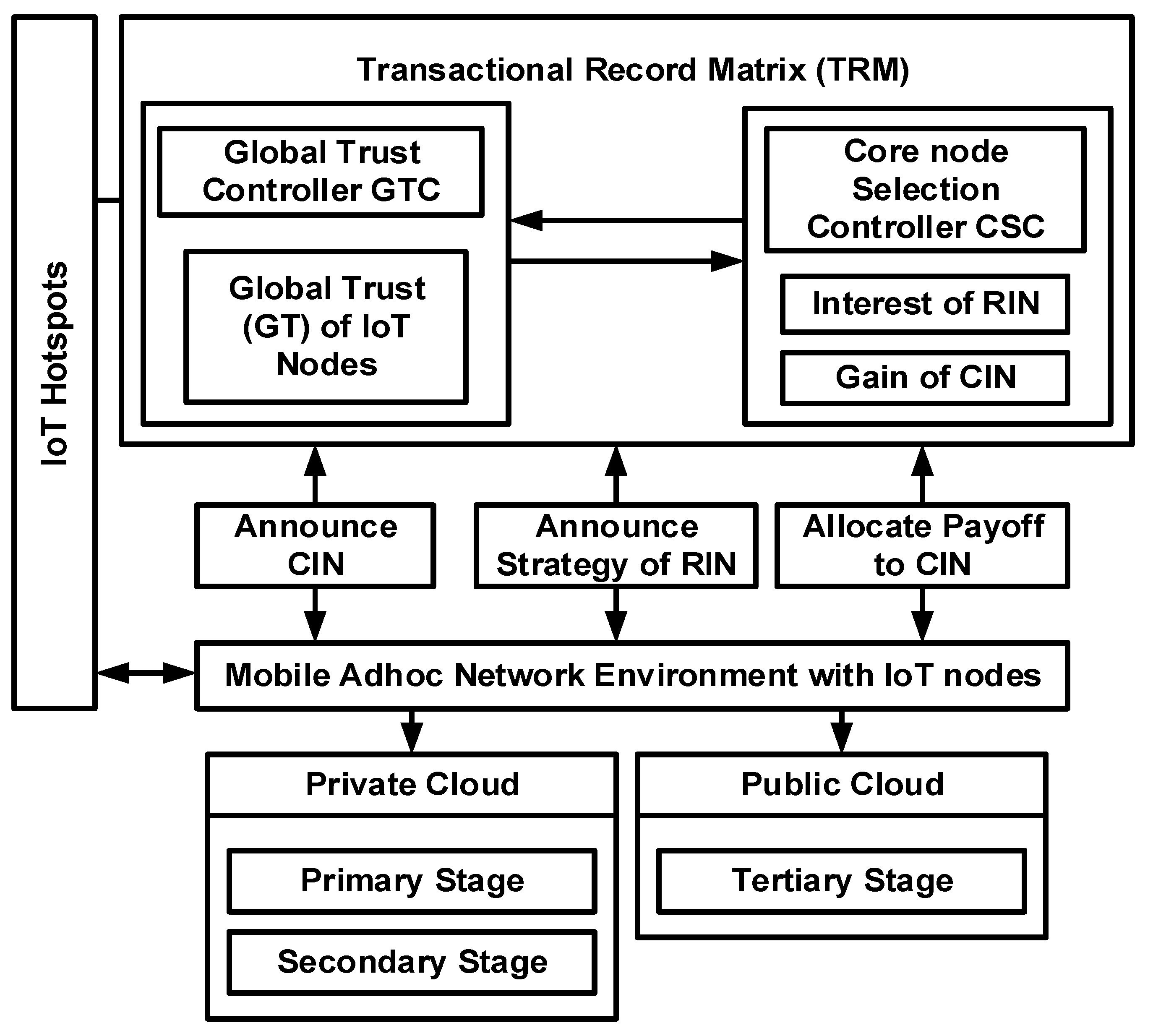
- Transactional Record Matrix (TRM): Unlike existing schemes, the proposed method does not retain or process the transactional routing data in one area of storage units. Instead, it creates a distributed database system where all of the transactional information is split and stored. The majority of the essential security-based processed information (global trust, Quality metric, roles, payoff, gains) evaluated by the controller system is managed in distributed order to restrict any form of direct accessibility by any unauthorised node.
- Cloud-Based Enabling Technologies: The proposed scheme makes use of both private and public clouds to improve privacy control and cost-effectiveness. Private cloud systems store information about the actors’ identified roles (primary level) and payments for RIN (secondary level), whereas public cloud systems store data on profit maximisation when it comes to selecting CIN (tertiary level). It should be noted that the cloud ecosystem is the underlying technology of the IoT environment, where the matrix of transaction records is explicitly maintained. Because of the discrete location, it becomes computationally extensive, making it impossible for any unauthorised node to intrude on both clouds at the same time.
- Modelling Game Concept: The development of the proposed scheme’s security condition is based on a strategic game model considering the selection of CIN using a Core node Selection Controller (CSC) and Global Trust Controller (GTC). The value of GTC is obtained from CSC to find the potential CIN. The main idea is to confirm the legitimacy of the CIN by encouraging the participation of a good number of RIN. The allocation of payoff and gain computation is based on trust, quality, and roles observed over a limited channel capacity. Unlike any conventional game model, the operation involved in this model is relatively straightforward and does not involve any conditional logic, which could cause contradictions in discovering node misbehaviour.
5. System Design
5.1. Private Cloud IoT System
5.2. Public Cloud IoT System
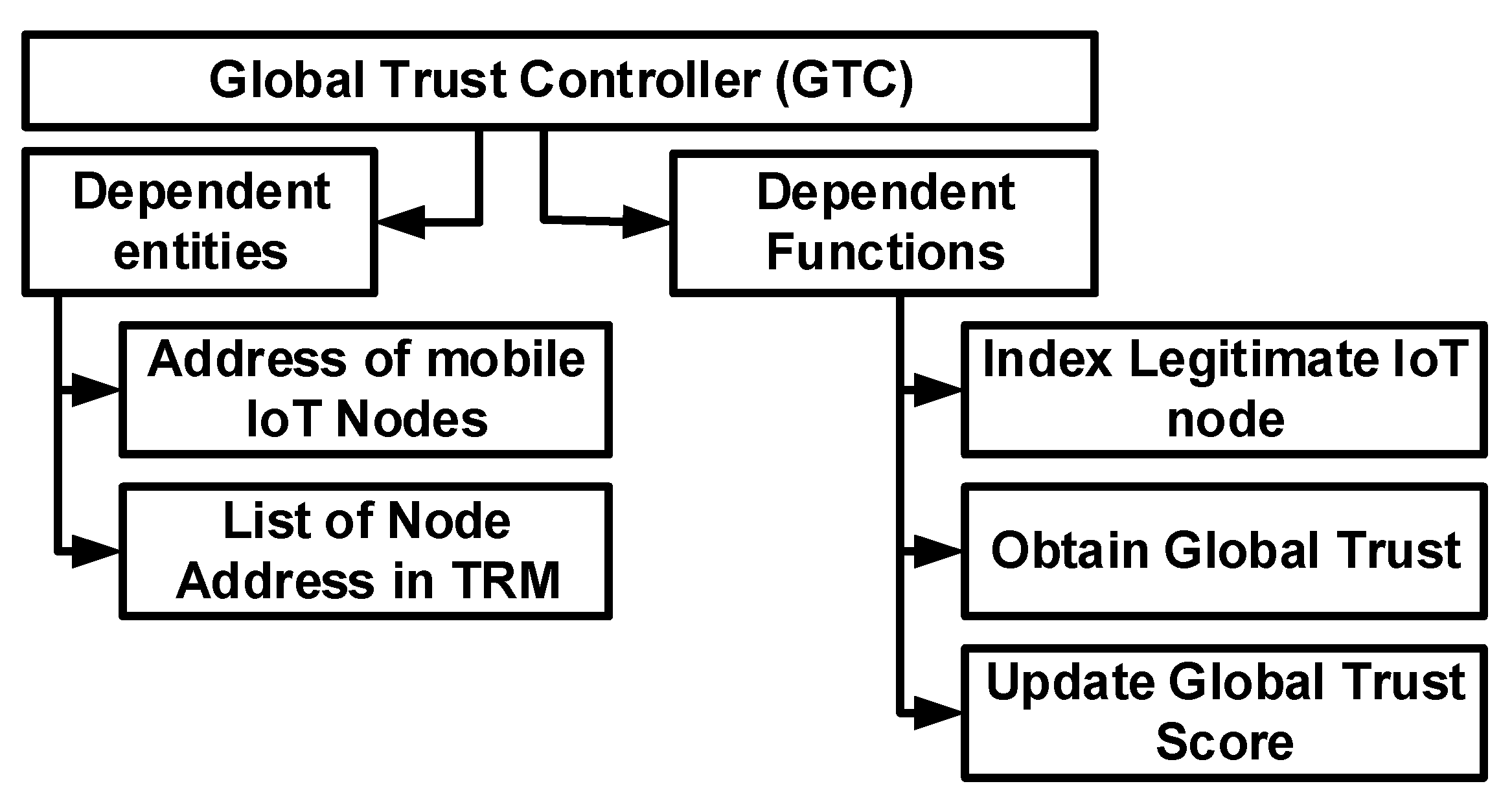
- Global Trust Controller (GTC): This controller system is responsible for managing all the updates for legitimate IoT nodes. The process is carried out over the public cloud system, making the operation in adherence to the agreement system as illustrated in Figure 3. A reliable source is provided to all nodes to perform the validation for the obtained controlled message.
- The classification of dependable parameters, as shown in Figure 3, demonstrates that the entire validation process carried out by GTC is done using the address of the mobile IoT node and a list of all connected nodes maintained in TRM. To access the legitimate IoT node, obtain its global trust, and update its value, an explicit set of functions is built. The first function, ‘index legitimate IoT node,’ is in charge of indexing the legitimate mobile IoT node while also determining whether the target node is present in the list of node addresses in TRM. In the case of a new mobile IoT node, it configures the address of the mobile IoT node with the address of the destination mobile IoT node, along with initialising the default value of global trust. This information is then added to the list. The second function, ‘obtain global trust’, is responsible for validating the global trust score that finally returns the score of global trust stored in the public cloud system. The new value of the global trust is configured using this function’s agreement system, which is the prime operation of the third function, ‘update global trust score’.
- Core node Selection Controller (CSC): This controller aggregates all the possible strategies of both the players, i.e., CIN and RIN, along with the constructs of the core structure that retain information about the RIN, CIN and local information of mobile IoT nodes. As shown in Figure 4, the core structure associated with the CIN maintains information about their respective identity and residual channel capacity. At the same time, the RIN holds information about the address of TRM and payoff. Furthermore, the dependent entities of CSC will consist of an object of CIN, as well as its respective address, as shown in Figure 4. The first function, ‘define CIN,’ is used to self-declare a mobile IoT node as a CIN in the public cloud. This function generates a CIN object by extracting the global trust score from GTC, while the second function, ‘obtain CIN,’ returns a list of all of the defined CIN. The third function, ‘Strategy,’ is used to build RIN.
5.3. Strategic Game Model
6. Result Discussion
6.1. Simulation Environment
6.2. Analysis Strategy
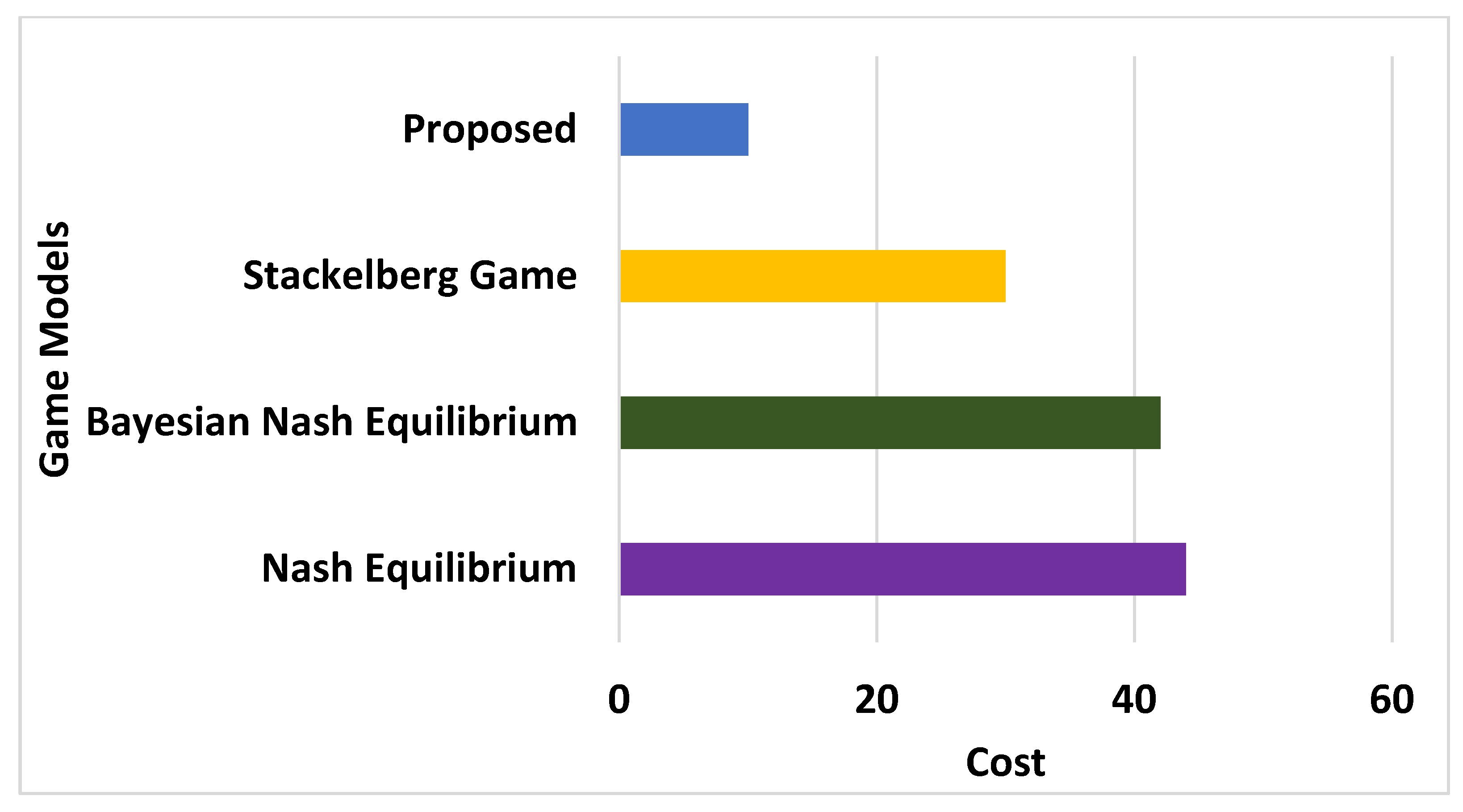
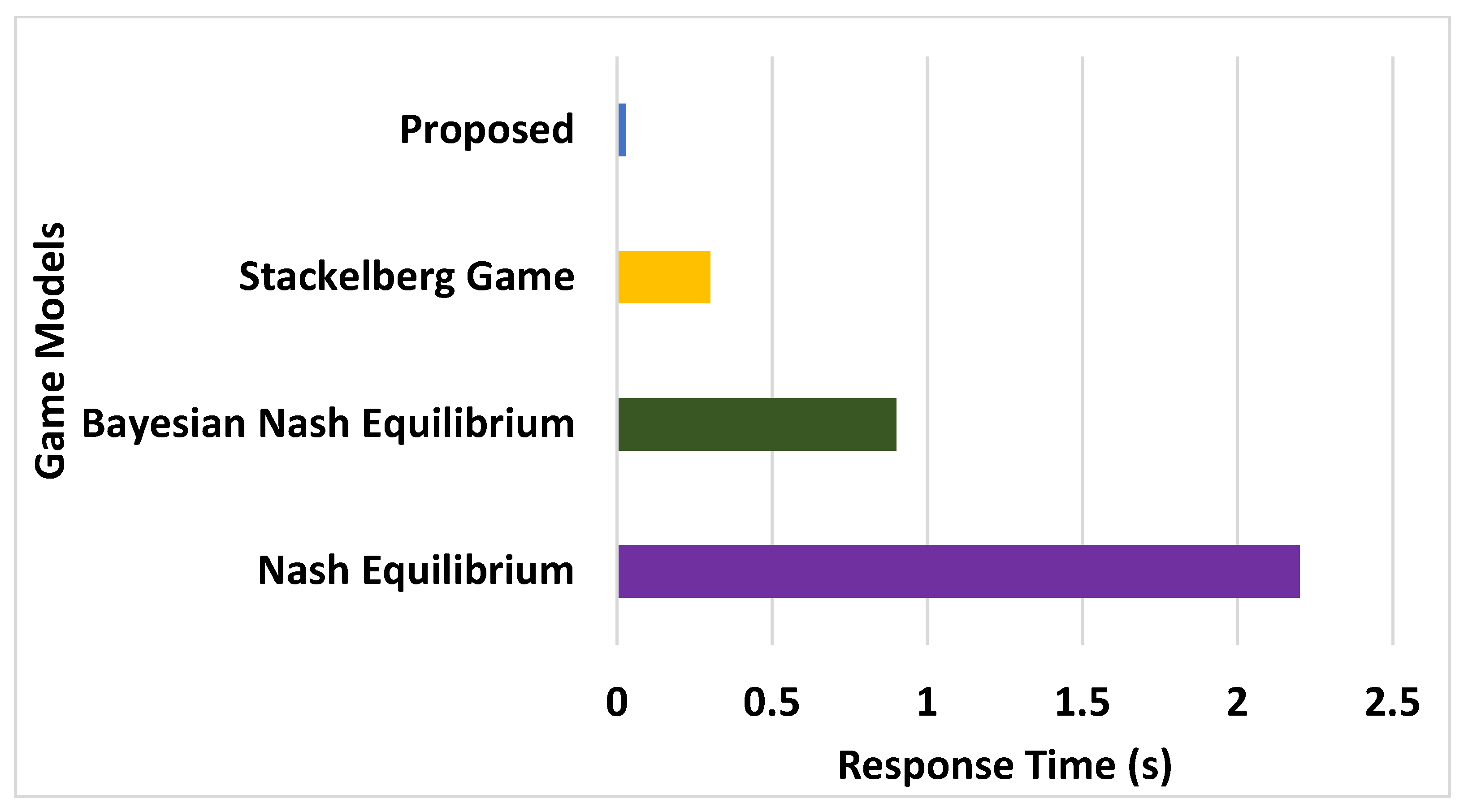
- Adoption of Nash equilibrium assists in accurately detecting the best payoff for a player based on the decision of the player and other players. Hence, when it comes to estimating global trust in ad hoc environments, Nash equilibrium offers an unbiased estimation of all the individual trust scores that can be applied for the cause of both routing and security in large IoT scenarios.
- Adoption of Bayesian Nash Equilibrium depends on retaining a belief in target players aligned with the adopted strategies of remnant players. This is a better option than Nash equilibrium as the latter does not offer the players’ belief score specifications. Eventually, it means that Bayesian Nash Equilibrium leads the nodes to converge into perfect strategically formulated beliefs with better consistency when exposed to vulnerable conditions. Hence, any deviation in trust score and belief will directly indicate the presence of malicious/misbehaved nodes.
- Stackelberg game is the most frequently implemented game model compared to other game models. According to this game mode, a sequential decision is prioritised over a simultaneous one. This model offers better decision making to the second mover, who can adopt a strategy based on action undertaken by the first mover. Apart from this, the best part of this model is the optimal acquisition of operational cost by the follower node. This eventually implies better decision making with higher clarity by the regular node, in order to perform secure routing upon detecting unknown/uncertainly behaved nodes in large-scale dynamic networks.
6.3. Result Accomplished
6.3.1. Identification Accuracy
6.3.2. Analysis of Energy Consumption
6.3.3. Analysis of Cost
6.3.4. Analysis of Response Time
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kanellopoulos, D.; Cuomo, F. Recent developments on mobile ad-hoc networks and vehicular ad-hoc networks. Electronics 2021, 10, 364. [Google Scholar] [CrossRef]
- Das, S.; Samanta, S.; Dey, N.; Patel, B.; Hassanien, A. Architectural Wireless Networks Solutions and Security Issues, 1st ed.; Springer: Singapore, 2021; p. 323. [Google Scholar]
- Srilakshmi, R.; Bhaskar, M. Prevention of attacks in mobile ad hoc network using African buffalo monitoring zone protocol. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 184–192. [Google Scholar] [CrossRef]
- Prasad, M.; Tripathi, S.; Dahal, K. An enhanced detection system against routing attacks in mobile ad-hoc network. Wirel. Netw. 2022, 28, 1411–1428. [Google Scholar] [CrossRef]
- Chiejina, E.; Xiao, H.; Christianson, B.; Mylonas, A.; Chiejina, C. A robust Dirichlet reputation and trust evaluation of nodes in mobile ad hoc networks. Sensors 2022, 22, 571. [Google Scholar] [CrossRef]
- Dai, J.; Xu, X. A Analysis Of Attack And Defense Mobile Ad Hoc Network Based On OPNET. IOP Conf. Ser. Mater. Sci. Eng. 2019, 611, 012081. [Google Scholar] [CrossRef]
- Mangla, M.; Satpathy, S.; Nayak, B.; Mohanty, S. Integration of Cloud Computing with Internet of Things-Foundations, Analytics and Applications; John Wiley & Sons: Hoboken, NJ, USA, 2021; p. 384. [Google Scholar]
- Bruzgiene, R.; Narbutaite, L.; Adomkus, T. MANET Network in Internet of Things System. In Ad Hoc Networks; Ortiz, J., Pachon De La Cruz, A., Eds.; BoD–Books on Demand: Norderstedt, Germany, 2017; pp. 89–114. [Google Scholar]
- Tournier, J.; Lesueur, F.; Mouël, F.; Guyon, L.; Ben-Hassine, H. A survey of IoT protocols and their security issues through the lens of a generic IoT stack. Internet Things 2021, 16, 100264. [Google Scholar] [CrossRef]
- Sobin, C. A Survey on architecture, protocols and challenges in IoT. Wirel. Pers. Commun. 2020, 112, 1383–1429. [Google Scholar] [CrossRef]
- Apparao, M.; Sambana, B.; Srinivasa Rao, D. Secure routing in MANETS and IoT. Sci. Technol. Dev. 2019, VIII, 325–333. [Google Scholar]
- Swain, J.; Pattanayak, B.; Pati, B. A Systematic Study and Analysis of Security Issues in Mobile Ad-Hoc Networks. In Research Anthology on Securing Mobile Technologies and Applications; Information Resources Management Association, Ed.; IGI Global: Hershey, PA, USA, 2022; pp. 144–150. [Google Scholar] [CrossRef]
- Simpson, S.; Nagarajan, G. Security Challenges and Attacks in MANET-IoT Systems. In Enterprise Digital Transformation; Auerbach Publications: New York, NY, USA, 2022; pp. 159–201. [Google Scholar]
- Sha, K.; Yang, T.; Wei, W.; Davari, S. A survey of edge computing-based designs for IoT security. Digit. Commun. Netw. 2020, 6, 195–202. [Google Scholar] [CrossRef]
- Chanal, P.; Kakkasageri, M. Security and privacy in IoT: A survey. Wirel. Pers. Commun. 2020, 115, 1667–1693. [Google Scholar] [CrossRef]
- Mrabet, H.; Belguith, S.; Alhomoud, A.; Jemai, A. A survey of IoT security based on a layered architecture of sensing and data analysis. Sensors 2020, 20, 3625. [Google Scholar] [CrossRef] [PubMed]
- Anh, V.; Cuong, P.; Vinh, P. Context-aware mobility in Internet of Thing: A survey. EAI Endorsed Trans. Context-Aware Syst. Appl. 2019, 6, 158875. [Google Scholar] [CrossRef]
- Rana, M.; Mamun, Q.; Islam, R. Lightweight cryptography in IoT networks: A survey. Future Gener. Comput. Syst. 2022, 129, 77–89. [Google Scholar] [CrossRef]
- Ahanger, T.; Aljumah, A.; Atiquzzaman, M. State-of-the-art survey of artificial intelligent techniques for IoT security. Comput. Netw. 2022, 206, 108771. [Google Scholar] [CrossRef]
- Thanh, C. A Survey of Machine Learning Techniques for IoT Security. In International Conference on Future Data and Security Engineering, Proceedings of the 8th International Conference, FDSE 2021, Virtual Event, 24–26 November 2021; Springer: Singapore, 2021; pp. 139–157. [Google Scholar] [CrossRef]
- Sadek, F.; Belkadi, K.; Abouaissa, A.; Lorenz, P. Identifying misbehaving greedy nodes in IoT networks. Sensors 2021, 21, 5127. [Google Scholar] [CrossRef]
- Banerjee, B.; Neogy, S. A Brief Overview of Security Attacks and Protocols In MANET. In Proceedings of the 2021 IEEE 18th India Council International Conference (INDICON), Guwahati, India, 19–21 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Khan, U.; Agrawal, S.; Silakari, S. A Detailed Survey on Misbehavior Node Detection Techniques in Vehicular Ad Hoc Networks. In Information Systems Design and Intelligent Applications. Advances in Intelligent Systems and Computing; Mandal, J., Satapathy, S., Kumar Sanyal, M., Sarkar, P., Mukhopadhyay, A., Eds.; Springer: New Delhi, India, 2015. [Google Scholar] [CrossRef]
- Khoda Parast, F.; Sindhav, C.; Nikam, S.; Izadi Yekta, H.; Kent, K.; Hakak, S. Cloud Computing Security: A Survey of Service-Based Models. Comput. Secur. 2022, 114, 102580. [Google Scholar] [CrossRef]
- Williams, P.; Dutta, I.; Daoud, H.; Bayoumi, M. A Survey on Security in Internet of Things with A Focus on The Impact of Emerging Technologies. Internet Things 2022, 19, 100564. [Google Scholar] [CrossRef]
- Maschler, M.; Zamir, S.; Solan, E. Game Theory; Cambridge University Press: New York, NY, USA, 2020. [Google Scholar]
- Lin, D.; Wang, Q.; Yang, P. The Game Theory: Applications in The Wireless Networks. In Game Theory—Applications in Logistics and Economy; Tuljak-Suban, D., Ed.; IntechOpen: London, UK, 2018. [Google Scholar] [CrossRef]
- Paul, C.; Bhanu, D.; Dhanapal, R.; Jebakumar Immanuel, D. An Efficient Authentication Using Monitoring Scheme for Node Misbehaviour Detection In MANET. In International Conference on Computing, Communication, Electrical and Biomedical Systems; Springer: Cham, Switzerland, 2022; pp. 627–633. [Google Scholar] [CrossRef]
- Behfarnia, A.; Eslami, A. Misbehavior Detection in Ephemeral Networks: A Local Voting Game in Presence of Uncertainty. IEEE Access 2019, 7, 184629–184642. [Google Scholar] [CrossRef]
- Abhishek, N.; Tandon, A.; Lim, T.; Sikdar, B. A GLRT-Based Mechanism for Detecting Relay Misbehavior in Clustered IoT Networks. IEEE Trans. Inf. Forensics Secur. 2020, 15, 435–446. [Google Scholar] [CrossRef]
- Sharma, P.; Liu, H. A Machine-Learning-Based Data-Centric Misbehavior Detection Model for Internet of Vehicles. IEEE Internet Things J. 2021, 8, 4991–4999. [Google Scholar] [CrossRef]
- Astillo, P.; Kim, J.; Sharma, V.; You, I. SGF-MD: Behavior Rule Specification-Based Distributed Misbehavior Detection of Embedded IoT Devices in A Closed-Loop Smart Greenhouse Farming System. IEEE Access 2020, 8, 196235–196252. [Google Scholar] [CrossRef]
- Zhang, X.; Lyu, C.; Shi, Z.; Li, D.; Xiong, N.; Chi, C. Reliable multiservice delivery in fog-enabled VANETs: Integrated misbehavior detection and tolerance. IEEE Access 2019, 7, 95762–95778. [Google Scholar] [CrossRef]
- Nguyen, V.; Lin, P.; Hwang, R. Enhancing misbehavior detection in 5G vehicle-to-vehicle communications. IEEE Trans. Veh. Technol. 2020, 69, 9417–9430. [Google Scholar] [CrossRef]
- Gyawali, S.; Qian, Y.; Hu, R. Machine learning and reputation based misbehavior detection in vehicular communication networks. IEEE Trans. Veh. Technol. 2020, 69, 8871–8885. [Google Scholar] [CrossRef]
- Ding, X.; Wang, Y. Misbehavior detection and optimal threshold analysis in DF cooperative relay networks. IEEE Wirel. Commun. Lett. 2021, 10, 2718–2721. [Google Scholar] [CrossRef]
- Shah, H.; Kakkad, V.; Patel, R.; Doshi, N. A survey on game theoretic approaches for privacy preservation in data mining and network security. Procedia Comput. Sci. 2019, 155, 686–691. [Google Scholar] [CrossRef]
- Jing, J. Applications of game theory and advanced machine learning methods for adaptive cyberdefense strategies in the digital music industry. Comput. Intell. Neurosci. 2022, 2022, 2266171. [Google Scholar] [CrossRef]
- Kiennert, C.; Ismail, Z.; Debar, H.; Leneutre, J. A survey on game-theoretic approaches for intrusion detection and response optimization. ACM Comput. Surv. 2019, 51, 1–31. [Google Scholar] [CrossRef]
- Kumar, R.; Singh, S.; Kela, R. Analyzing advanced persistent threats using game theory: A critical literature review. In International Conference on Critical Infrastructure Protection; Springer: Cham, Switzerland, 2021; pp. 45–69. [Google Scholar] [CrossRef]
- Jan, S.; Amin, N.; Shuja, J.; Abbas, A.; Maray, M.; Ali, M. SELWAK: A secure and efficient lightweight and anonymous authentication and key establishment scheme for IoT based vehicular ad hoc networks. Sensors 2022, 22, 4019. [Google Scholar] [CrossRef]
- Subba, B.; Biswas, S.; Karmakar, S. A game theory based multi layered intrusion detection framework for VANET. Future Gener. Comput. Syst. 2018, 82, 12–28. [Google Scholar] [CrossRef]
- Sun, Z.; Liu, Y.; Wang, J.; Mei, F.; Deng, W.; Ge, Y. Non-Cooperative game of throughput and hash length for adaptive Merkle tree in mobile wireless networks. IEEE Trans. Veh. Technol. 2019, 68, 4625–4650. [Google Scholar] [CrossRef]
- Liu, X.; Lim, T.; Huang, J. Optimal Byzantine attacker identification based on game theory in network coding enabled wireless ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2570–2583. [Google Scholar] [CrossRef]
- Li, Y.; Bai, S.; Gao, Z. A multi-domain anti-jamming strategy using Stackelberg game in wireless relay networks. IEEE Access 2020, 8, 173609–173617. [Google Scholar] [CrossRef]
- Qi, N.; Wang, W.; Zhou, F.; Jia, L.; Wu, Q.; Jin, S.; Xiao, M. Two birds with one stone: Simultaneous jamming and eavesdropping with the Bayesian-Stackelberg game. IEEE Trans. Commun. 2021, 69, 8013–8027. [Google Scholar] [CrossRef]
- Qi, N.; Wang, W.; Xiao, M.; Jia, L.; Jin, S.; Zhu, Q.; Tsiftsis, T. A Learning-based spectrum access Stackelberg game: Friendly jammer-assisted communication confrontation. IEEE Trans. Veh. Technol. 2021, 70, 700–713. [Google Scholar] [CrossRef]
- Ilavendhan, A.; Saruladha, K. Stackelberg security game to mitigate the DoS attack in vehicular ad-hoc networks. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 1–8. [Google Scholar] [CrossRef]
- Ilavendhan, A.; Saruladha, K. Comparative study of game theoretic approaches to mitigate network layer attacks in VANETs. ICT Express 2018, 4, 46–50. [Google Scholar] [CrossRef]
- Abdalzaher, M.; Samy, L.; Muta, O. Non-zero-sum game-based trust model to enhance wireless sensor networks security for IoT applications. IET Wirel. Sens. Syst. 2019, 9, 218–226. [Google Scholar] [CrossRef]
- Feng, S.; Xiong, Z.; Niyato, D.; Wang, P. Dynamic resource management to defend against advanced persistent threats in fog computing: A game theoretic approach. IEEE Trans. Cloud Comput. 2021, 9, 995–1007. [Google Scholar] [CrossRef]
- Wang, D.; Chen, I.; Al-Hamadi, H. Reliability of autonomous Internet of Things systems with intrusion detection attack-defense game design. IEEE Trans. Reliab. 2021, 70, 188–199. [Google Scholar] [CrossRef]
- Mehta, M.; Patel, K. A survey on IoT authentication security service. Int. J. Syst. Softw. Secur. Prot. 2022, 13, 13. [Google Scholar] [CrossRef]
- Chi, C.; Wang, Y.; Tong, X.; Siddula, M.; Cai, Z. Game theory in internet of things: A survey. IEEE Internet Things J. 2022, 9, 12125–12146. [Google Scholar] [CrossRef]
- Khan, B.; Olanrewaju, R.; Hadi Habaebi, M. Malicious behaviour of node and its significant security techniques in MANET-A review. Aust. J. Basic Appl. Sci. 2013, 7, 286–293. [Google Scholar]
- Khan, B.; Anwar, F.; Olanrewaju, R.; Pampori, B.; Mir, R. A game theory-based strategic approach to ensure reliable data transmission with optimized network operations in futuristic mobile adhoc networks. IEEE Access 2020, 8, 124097–124109. [Google Scholar] [CrossRef]
- Khan, B.; Anwar, F.; Olanrewaju, R.; Kiah, M.; Mir, R. Game theory analysis and modeling of sophisticated multi-collusion attack in MANETs. IEEE Access 2021, 9, 61778–61792. [Google Scholar] [CrossRef]
- Khan, B.; Olanrewaju, R.; Mir, R.; Baba, A.; Adebayo, B. Strategic profiling for behaviour visualization of malicious node in MANETs using game theory. J. Theor. Appl. Inf. Technol. 2015, 77, 25–43. [Google Scholar]
- Dafalla, M.E.M.; Mokhtar, R.; Saeed, R.; Alhumyani, H.; Abdel-Khalek, S.; Khayyat, M. An optimized link state routing protocol for real-time application over vehicular ad-hoc network. Alex. Eng. J. 2022, 61, 4541–4556. [Google Scholar] [CrossRef]
- Du, X.; Zhou, Z.; Zhang, Y. Energy-efficient data aggregation through the collaboration of cloud and edge computing in Internet of Thing’s networks. Procedia Comput. Sci. 2020, 174, 269–275. [Google Scholar] [CrossRef]



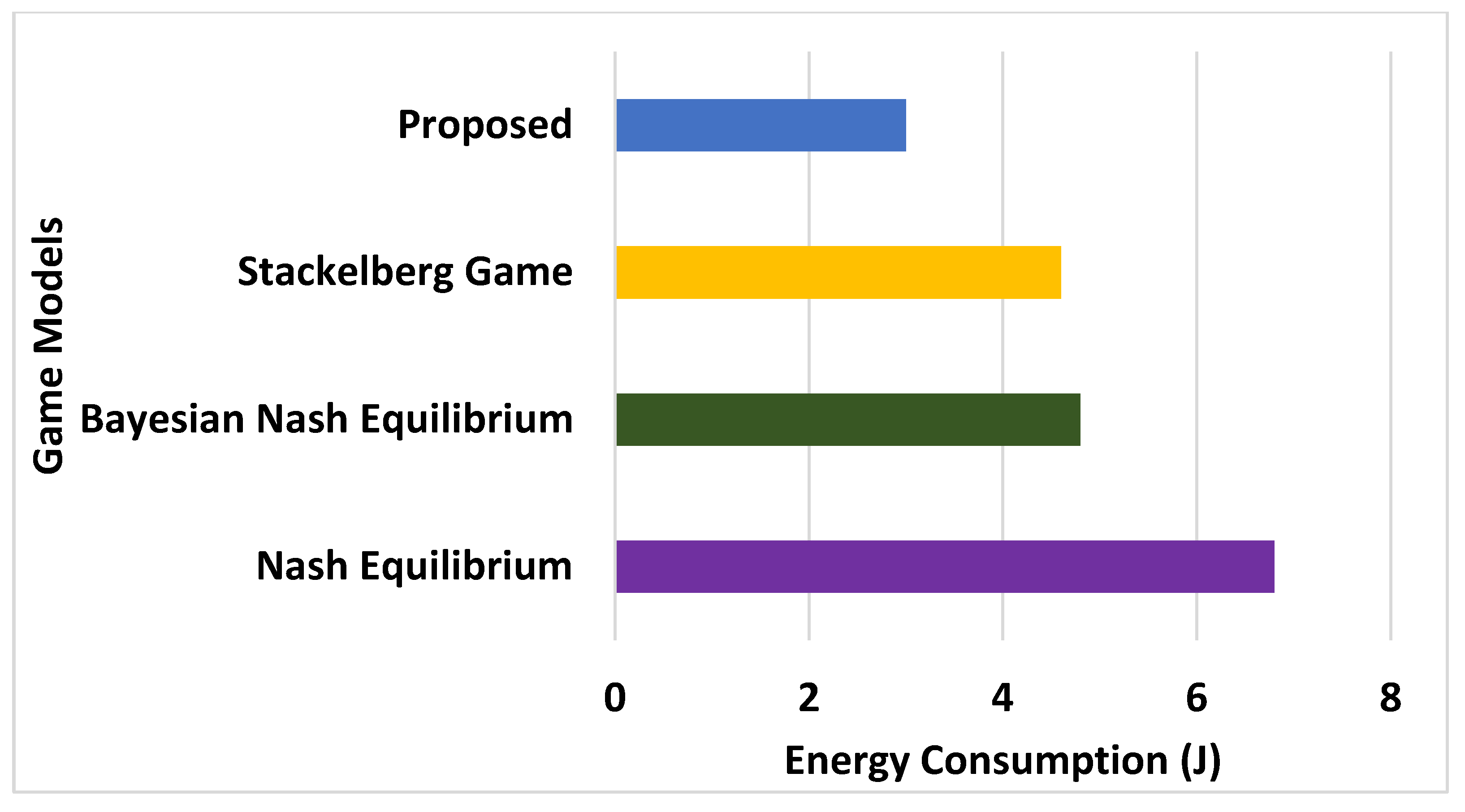
| # | Parameters | Values |
|---|---|---|
| 1 | Number of Nodes | 500–1000 |
| 2 | Node deployment | Random |
| 3 | Initialised Energy | 10 J |
| 4 | Iteration | 1000 |
| 5 | Sensing Range of Node | 10 m |
| 6 | Sensing range of IoT access point | 100 m |
| 7 | Dimension of one unit of IoT Cluster | 100 × 100 m2 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khan, B.U.I.; Anwar, F.; Rahman, F.D.B.A.; Olanrewaju, R.F.; Goh, K.W.; Janin, Z.; Rahman, M.A. SGM: Strategic Game Model for Resisting Node Misbehaviour in IoT-Cloud Ecosystem. Information 2022, 13, 544. https://doi.org/10.3390/info13110544
Khan BUI, Anwar F, Rahman FDBA, Olanrewaju RF, Goh KW, Janin Z, Rahman MA. SGM: Strategic Game Model for Resisting Node Misbehaviour in IoT-Cloud Ecosystem. Information. 2022; 13(11):544. https://doi.org/10.3390/info13110544
Chicago/Turabian StyleKhan, Burhan Ul Islam, Farhat Anwar, Farah Diyana Bt. Abdul Rahman, Rashidah Funke Olanrewaju, Khang Wen Goh, Zuriati Janin, and Md Arafatur Rahman. 2022. "SGM: Strategic Game Model for Resisting Node Misbehaviour in IoT-Cloud Ecosystem" Information 13, no. 11: 544. https://doi.org/10.3390/info13110544
APA StyleKhan, B. U. I., Anwar, F., Rahman, F. D. B. A., Olanrewaju, R. F., Goh, K. W., Janin, Z., & Rahman, M. A. (2022). SGM: Strategic Game Model for Resisting Node Misbehaviour in IoT-Cloud Ecosystem. Information, 13(11), 544. https://doi.org/10.3390/info13110544







